Collateral Management

Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V
This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc.

Three Level Business Continuity Diagram Ppt Slides
This is a three level business continuity diagram ppt slides. This is a three stage process. The stages in this process are business continuity planning, security management, disaster recovery, technology, roles, testing, risk management, data assessment, coordination, communicating plan, policy, technology, services, procedures, incident response.
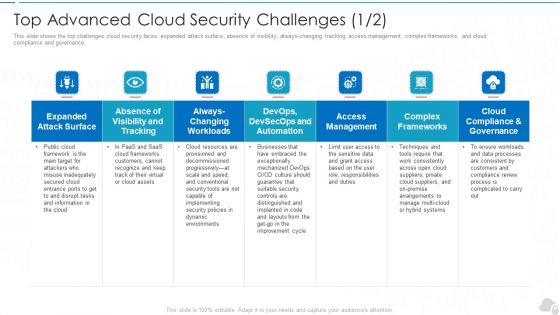
Top Advanced Cloud Security Challenges Cloud Computing Security IT Ppt Slides Clipart Images PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver and pitch your topic in the best possible manner with this top advanced cloud security challenges cloud computing security it ppt slides clipart images pdf. Use them to share invaluable insights on cloud compliance and governance, access management, complex frameworks, visibility and tracking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
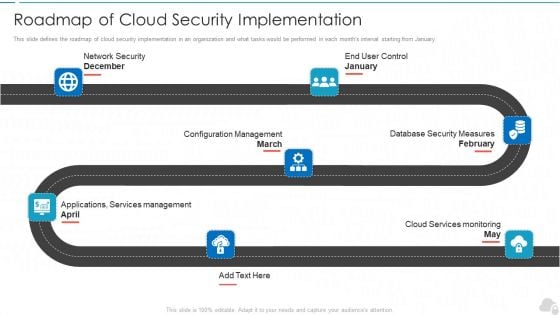
Roadmap Of Cloud Security Implementation Cloud Computing Security IT Ppt Outline Files PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. This is a roadmap of cloud security implementation cloud computing security it ppt outline files pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration management, database security measures, cloud services monitoring, applications, services management, network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
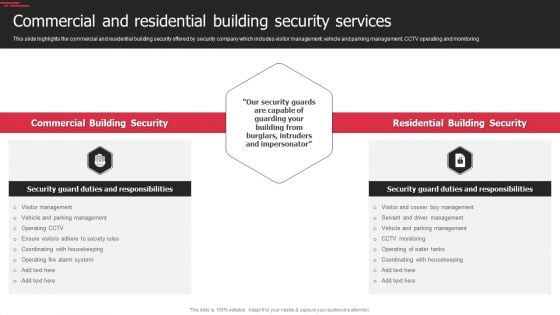
Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Presenting Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Expanded Attack, Access Management, Complex Frameworks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.

Safety Guidelines To Control Fire At Workplace Safety Protocol And Security Practices Microsoft Pdf
This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Safety Guidelines To Control Fire At Workplace Safety Protocol And Security Practices Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
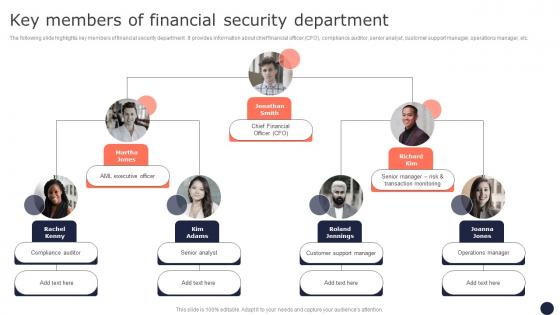
Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc.
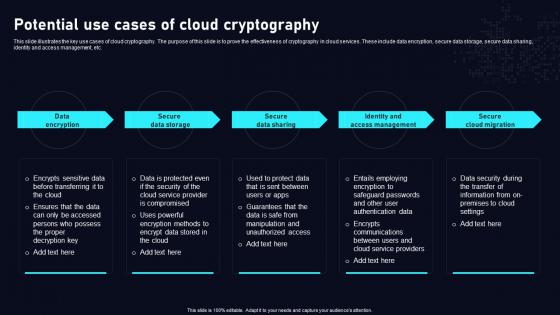
Potential Use Cases Of Cloud Cryptography Cloud Data Security Using Cryptography Information Pdf
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Present like a pro with Potential Use Cases Of Cloud Cryptography Cloud Data Security Using Cryptography Information Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc.

Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
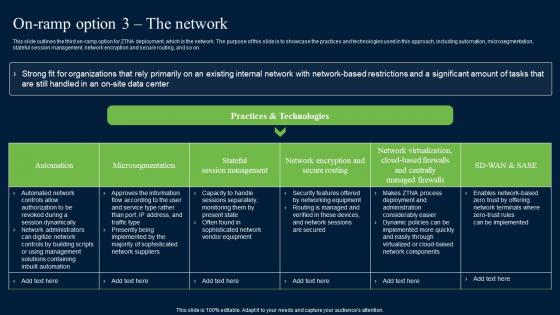
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
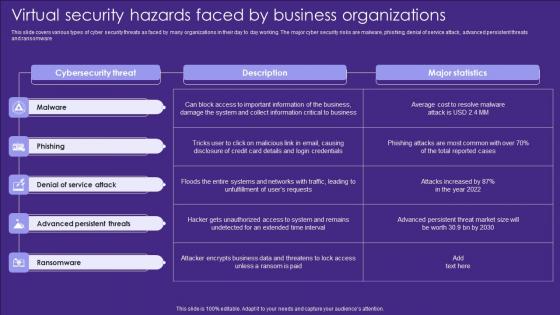
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
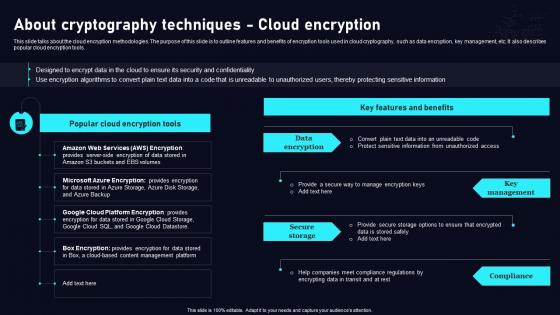
Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf
This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
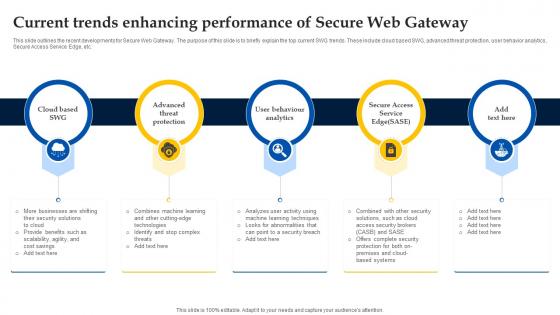
Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.
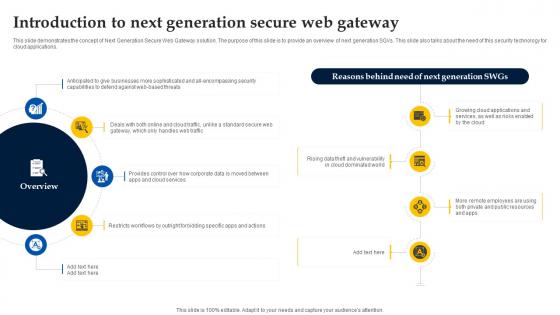
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.
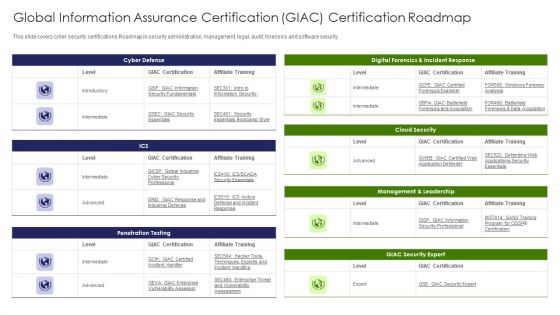
IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
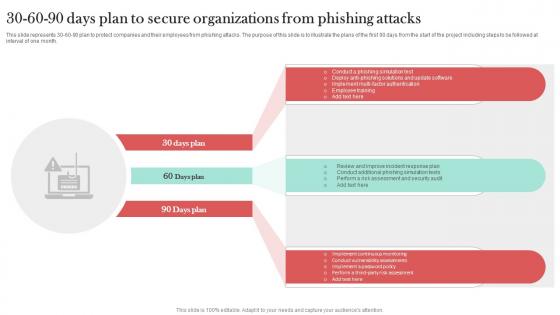
30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT
This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
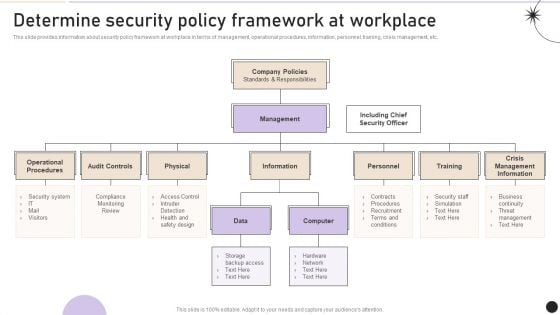
Determine Security Policy Framework At Workplace Pictures PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Get a simple yet stunning designed Determine Security Policy Framework At Workplace Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Security Policy Framework At Workplace Pictures PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Information Security Program Values To Business Ppt File Smartart PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting information security program values to business ppt file smartart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reduce, security, network, environment, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
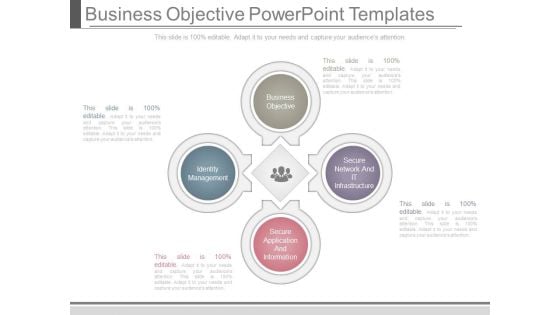
Business Objective Powerpoint Templates
This is a business objective powerpoint templates. This is a four stage process. The stages in this process are business objective, secure network and it infrastructure, secure application and information, identity management.
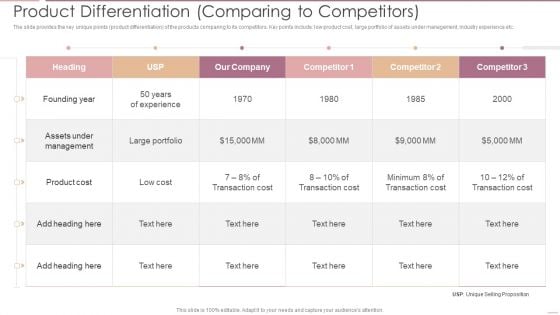
Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF
The slide provides the key unique points product differentiation of the products comparing to its competitors. Key points include low product cost, large portfolio of assets under management, industry experience etc. Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF. Use them to share invaluable insights on Under Management, Transaction Cost, Minimum Transaction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
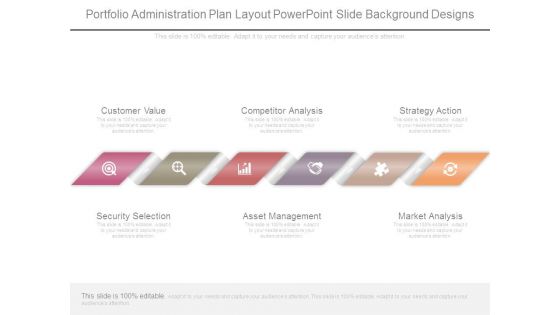
Portfolio Administration Plan Layout Powerpoint Slide Background Designs
This is a portfolio administration plan layout powerpoint slide background designs. This is a six stage process. The stages in this process are customer value, competitor analysis, strategy action, market analysis, asset management, security selection.
International Organization Standardization 270001 Security Domains That Will Be Addressed By Isms Icons PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a international organization standardization 270001 security domains that will be addressed by isms icons pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization of information security, human resources security, asset management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Example Of Security Testing Services Ppt Powerpoint Guide
This is a example of security testing services ppt powerpoint guide. This is a eight stage process. The stages in this process are security management, access security, application security, networking security, test delivery, results and analysis, technology enablement, test development and publishing.
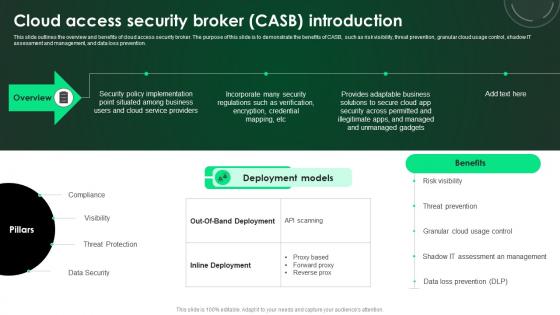
CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention.

Retail Operations Process Improvement Flowchart Ppt Model
This is a retail operations process improvement flowchart ppt model. This is a five stage process. The stages in this process are enterprise security, supply chain management, recruitment process outsource, human resources, finance and administration.

Determine New Roles Pivotal For Successful Devops Security Designs PDF
This slide provides information regarding the new roles considered as pivotal for successful DevOps in terms of DevOps evangelist, release manager, automation architect integration specialist. Presenting determine new roles pivotal for successful devops security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like manager, management, coordination. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
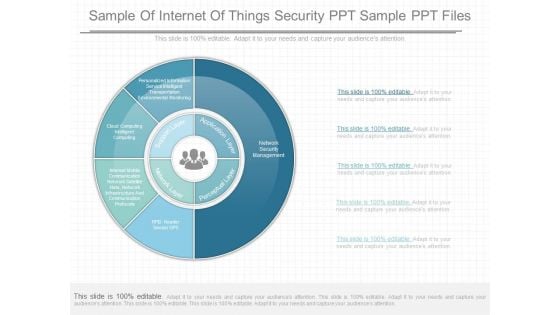
Sample Of Internet Of Things Security Ppt Sample Ppt Files
This is a sample of internet of things security ppt sample ppt files. This is a five stage process. The stages in this process are personalized information service intelligent transportation environmental monitoring, cloud computing intelligent computing, interest mobile communication network satellite nets, network infrastructure and communication protocols, supports layer, network layer, perceptual layer, application layer, network security management, rfid reader sensor gpb.
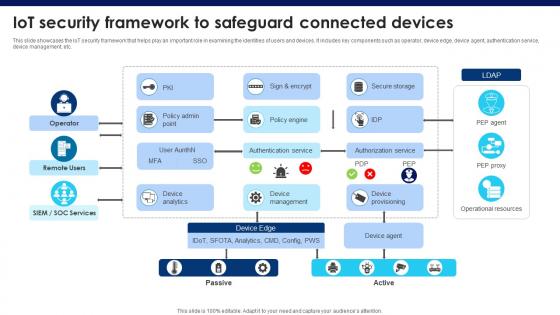
Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V
This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc. This Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc.

Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Presenting Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Security Policy, Asset Management, Physical And Environmental Security, Operational Security, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Table Of Contents Designs PDF
Deliver an awe inspiring pitch with this creative security and process integration table of contents designs pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
This slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Styles Gridlines
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation styles gridlines. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Icon Show
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation icon show. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
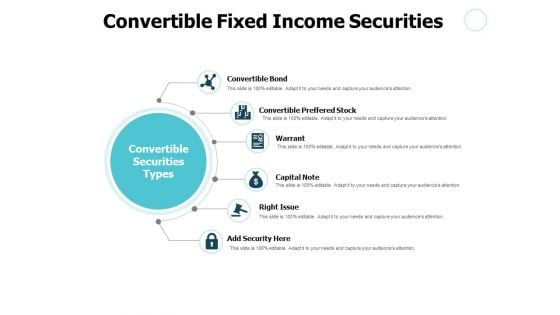
Convertible Fixed Income Securities Ppt PowerPoint Presentation Pictures Inspiration
Presenting this set of slides with name convertible fixed income securities ppt powerpoint presentation pictures inspiration. This is a six stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
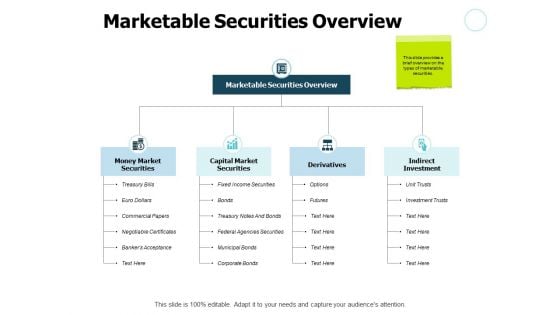
Marketable Securities Overview Investment Ppt PowerPoint Presentation Styles Graphic Images
Presenting this set of slides with name marketable securities overview investment ppt powerpoint presentation styles graphic images. This is a two stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
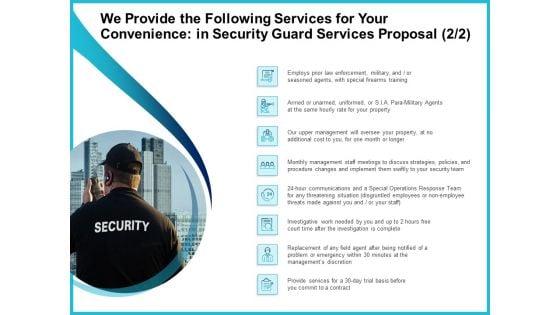
Uniformed Security We Provide The Following Services For Your Convenience In Security Guard Services Proposal Formats PDF
Deliver an awe inspiring pitch with this creative uniformed security we provide the following services for your convenience in security guard services proposal formats pdf bundle. Topics like training, strategies, policies, management, investigative can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Formation Of Acquired Entities Security Ppt PowerPoint Presentation Portfolio Images
Presenting this set of slides with name formation of acquired entities security ppt powerpoint presentation portfolio images. This is a four stage process. The stages in this process are formation, entities, business, development, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
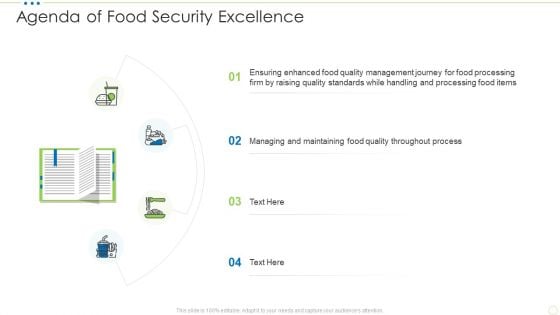
Agenda Of Food Security Excellence Ppt Model Visuals PDF
Presenting agenda of food security excellence ppt model visuals pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like maintaining, process, management, raising quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.

Wan Optimization Template Powerpoint Slides Rules
This is a wan optimization template powerpoint slides rules. This is a five stage process. The stages in this process are data center, remote office, application visibility, wan security, central management.

Fixed Income Securities Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name fixed income securities ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizational Security Solutions Table Of Contents Summary PDF
Deliver an awe inspiring pitch with this creative organizational security solutions table of contents summary pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
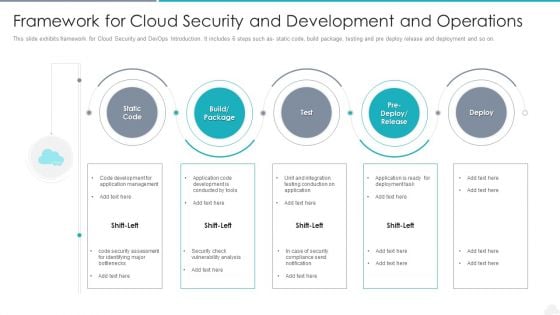
Framework For Cloud Security And Development And Operations Elements PDF
Presenting framework for cloud security and development and operations elements pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including management, application, development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
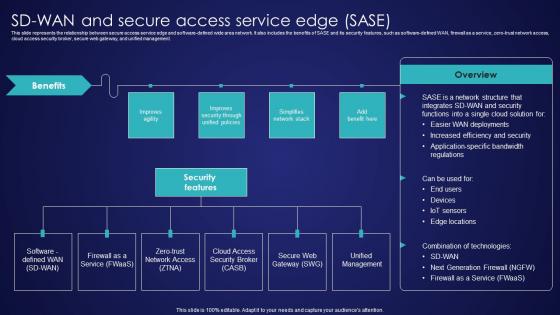
SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Welcome to our selection of the SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management.
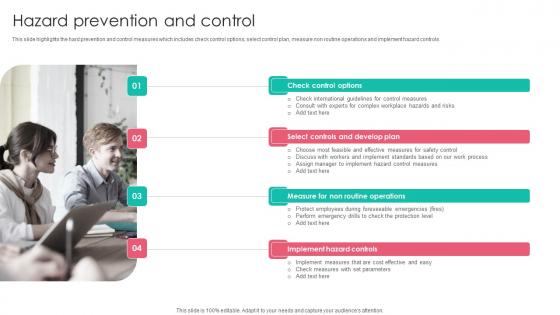
Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the hard prevention and control measures which includes check control options, select control plan, measure non routine operations and implement hazard controls. This Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights the hard prevention and control measures which includes check control options, select control plan, measure non routine operations and implement hazard controls.
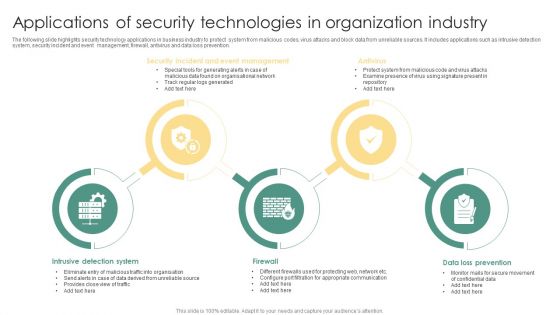
Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF
The following slide highlights security technology applications in business industry to protect system from malicious codes, virus attacks and block data from unreliable sources. It includes applications such as intrusive detection system, security incident and event management, firewall, antivirus and data loss prevention. Presenting Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Incident, Event Management, Antivirus, Firewall. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
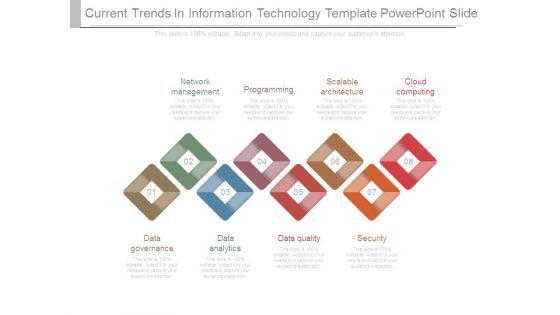
Current Trends In Information Technology Template Powerpoint Slide
This is a current trends in information technology template powerpoint slide. This is a eight stage process. The stages in this process are network management, programming, scalable architecture, cloud computing, data governance, data analytics, data quality, security.
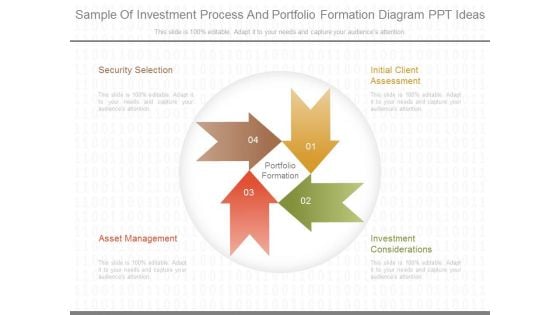
Sample Of Investment Process And Portfolio Formation Diagram Ppt Ideas
This is a sample of investment process and portfolio formation diagram ppt ideas. This is a four stage process. The stages in this process are portfolio formation, security selection, asset management, initial client assessment, investment considerations.
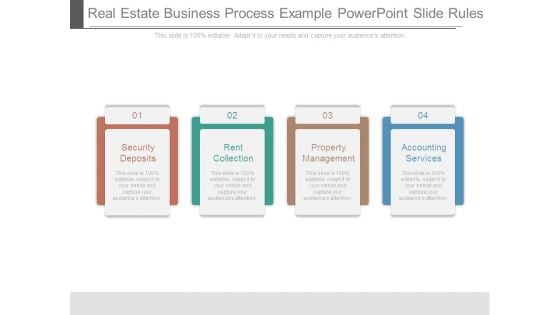
Real Estate Business Process Example Powerpoint Slide Rules
This is a real estate business process example powerpoint slide rules. This is a four stage process. The stages in this process are security deposits, rent collection, property management, accounting services.
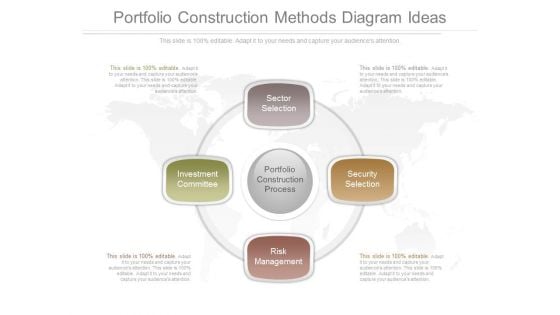
Portfolio Construction Methods Diagram Ideas
This is a portfolio construction methods diagram ideas. This is a four stage process. The stages in this process are portfolio construction process, sector selection, investment committee, risk management, security selection.
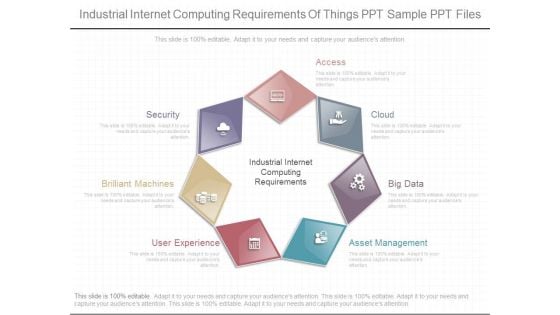
Industrial Internet Computing Requirements Of Things Ppt Sample Ppt Files
This is a industrial internet computing requirements of things ppt sample ppt files. This is a seven stage process. The stages in this process are industrial internet computing requirements, brilliant machines, user experience, asset management, big data, cloud, access, security.
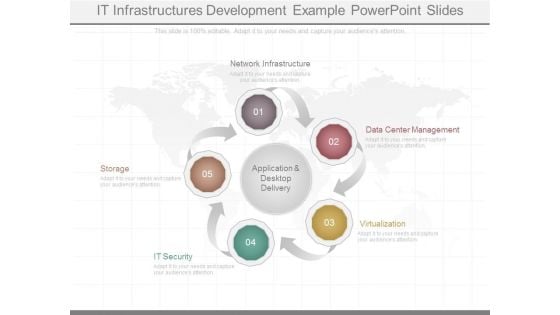
It Infrastructures Development Example Powerpoint Slides
This is a it infrastructures development example powerpoint slides. This is a five stage process. The stages in this process are application and desktop delivery, network infrastructure, data center management, storage, it security, virtualization.
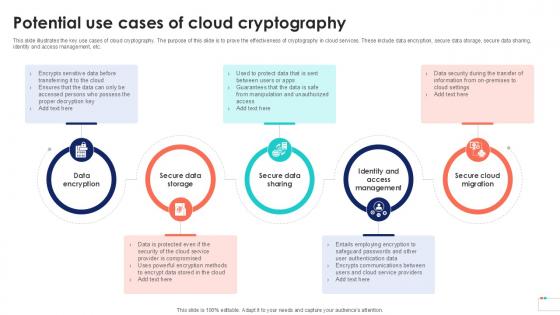
Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc.
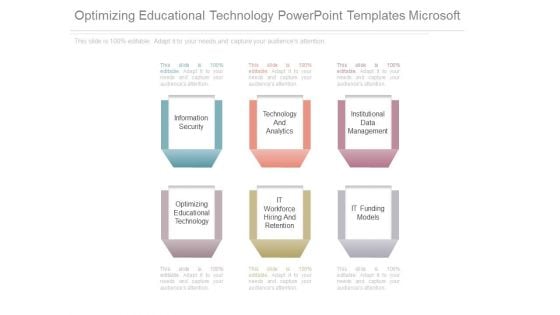
Optimizing Educational Technology Powerpoint Templates Microsoft
This is a optimizing educational technology powerpoint templates microsoft. This is a six stage process. The stages in this process are information security, technology and analytics, institutional data management, optimizing educational technology, it workforce hiring and retention, it funding models.


 Continue with Email
Continue with Email

 Home
Home


































