Collateral Management
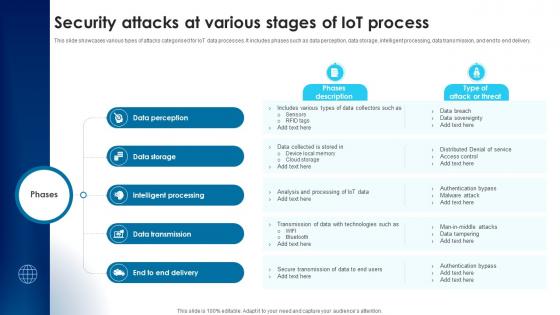
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.
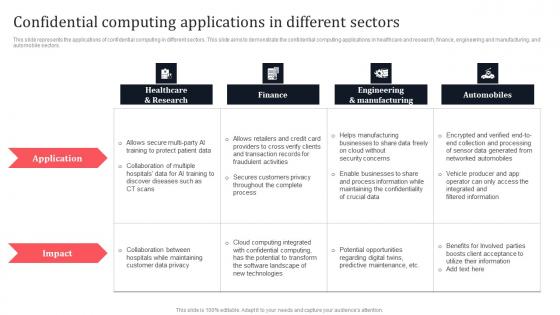
Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Present like a pro with Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.

Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name. Make sure to capture your audiences attention in your business displays with our gratis customizable Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name.
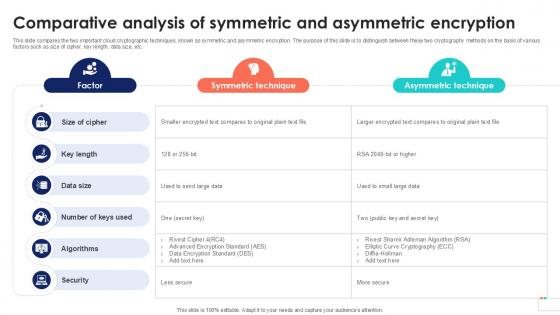
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
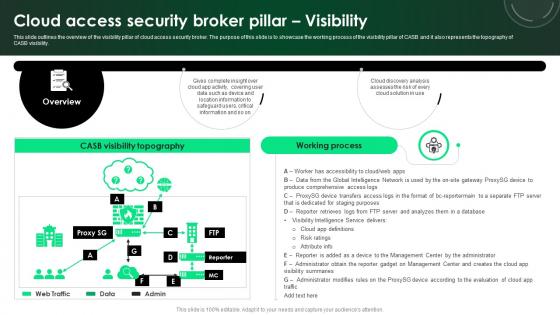
CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility.
PowerPoint Slides List Circular Growth Ppt Theme
PowerPoint Slides List Circular Growth PPT Theme-Use to awesome List and text boxes powerpoint templates to create awesome marketing and sales priority lists or any other types of lists.-PowerPoint Slides List Circular Growth PPT Theme-Account, Advertise, Analyze, Arrow, Brochure, Business, Catalog, Chart, Circular, Commercial, Competition, Concentric, Cyclic, Demonstration, Description, Diagram, Financial, Goals, Illustration, Information, Label, List, Management, Marketing, Note, Organization, Plan, Profit, Promote, Records, Recursive, Registry, Report, Research, Ring, Sale, Six, Spherical, Statement, Strategy, Structure, Success, Symbol Our PowerPoint Slides List Circular Growth Ppt Theme motivate your listeners. With our money back guarantee you have nothing to lose.
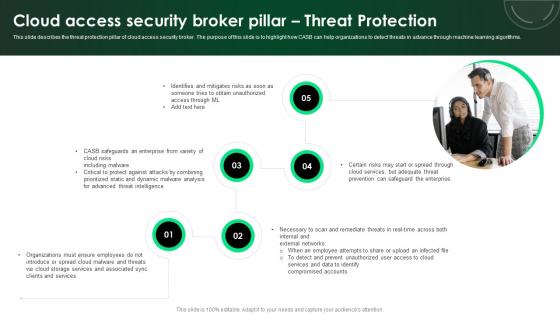
CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Retrieve professionally designed CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms.

Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. There are so many reasons you need a Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
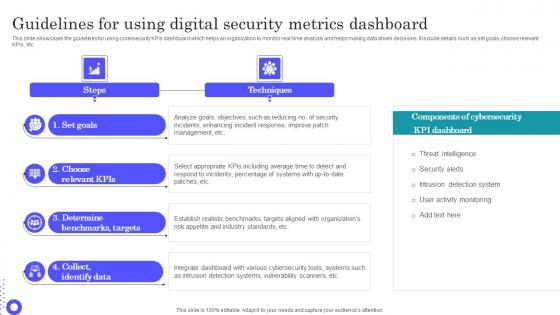
Guidelines For Using Digital Security Metrics Dashboard Introduction Pdf
Pitch your topic with ease and precision using this Guidelines For Using Digital Security Metrics Dashboard Introduction Pdf This layout presents information on Benchmarks Targets, Integrate Dashboard, Incidents Enhancing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the guidelines for using cybersecurity KPIs dashboard which helps an organization to monitor real time analysis and helps making data driven decisions. It include details such as set goals, choose relevant KPIs, etc.

Warehouse Security Checklist To Keep Check On Emergency Situations Professional Pdf
Following slide shows the a checklist for warehouse safety to monitor potential emergencies which will assist in to conduct proper assessment of warehouse location. It includes such as any damage in building, feasible to every stakeholders, fire safety measure , etc. Pitch your topic with ease and precision using this Warehouse Security Checklist To Keep Check On Emergency Situations Professional Pdf. This layout presents information on Warehouse Checklist, Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide shows the a checklist for warehouse safety to monitor potential emergencies which will assist in to conduct proper assessment of warehouse location. It includes such as any damage in building, feasible to every stakeholders, fire safety measure , etc.

Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V
The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies. There are so many reasons you need a Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies.
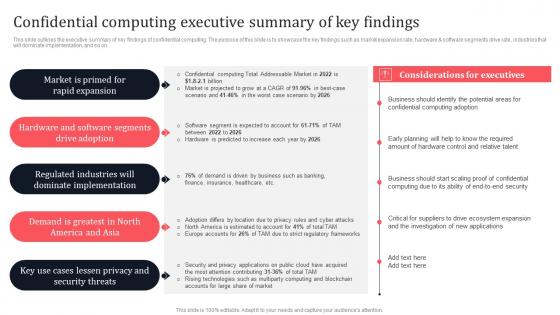
Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.
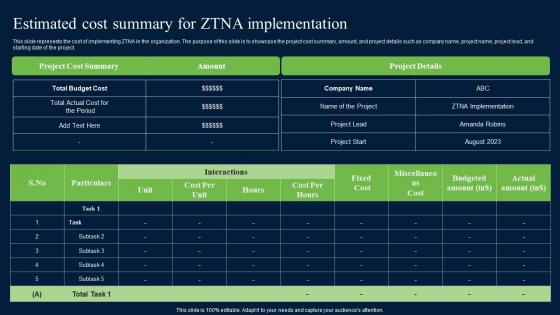
Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.
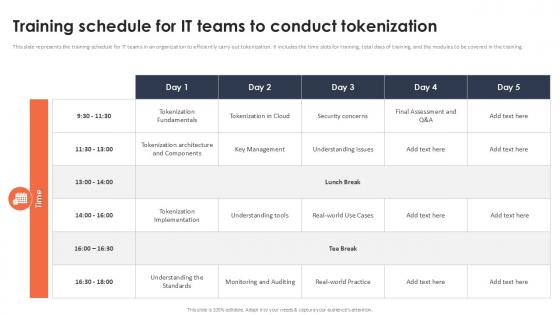
Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation
This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training. If you are looking for a format to display your unique thoughts, then the professionally designed Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training.
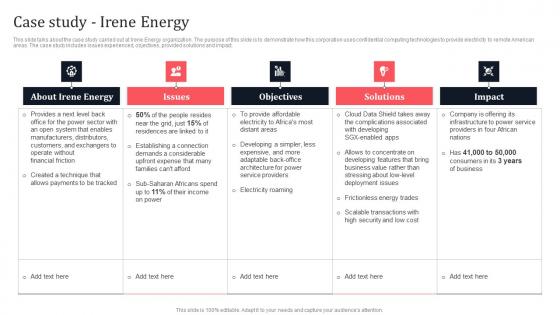
Case Study Irene Energy Secure Multi Party Sample Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Create an editable Case Study Irene Energy Secure Multi Party Sample Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Case Study Irene Energy Secure Multi Party Sample Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
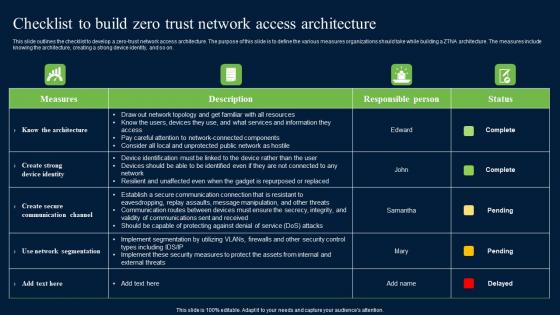
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
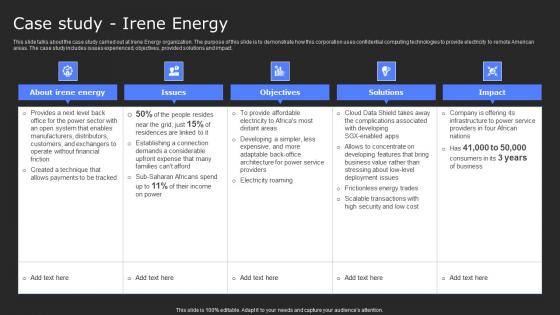
Case Study Irene Energy Secure Computing Framework Ideas Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Secure Computing Framework Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Secure Computing Framework Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
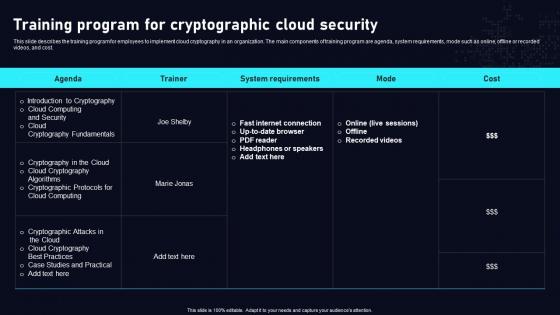
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template
This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor.
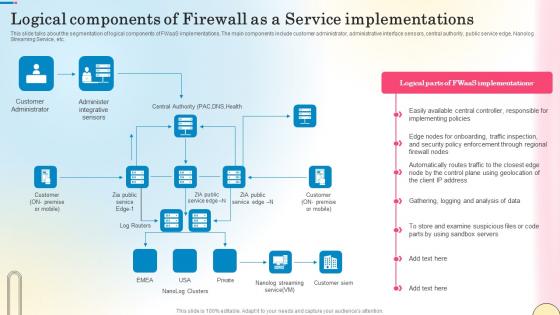
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.
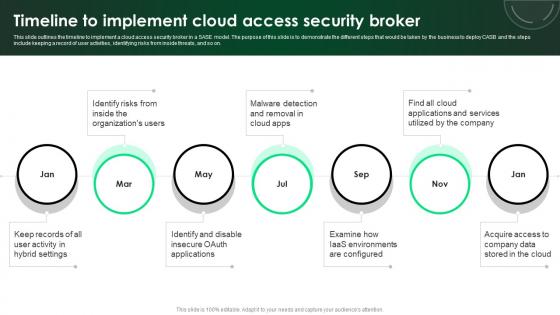
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.

Cloud Security Implementation Strategy Ppt Presentation

Teamwork Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Teamwork Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Teamwork Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Teamwork Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Endpoint Security Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Endpoint Security Checklist In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Endpoint Security Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Endpoint Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
National Security Budget In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled National Security Budget In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits National Security Budget that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our National Security Budget In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ppt Green Section Highlighted In Circular PowerPoint Menu Template Manner Templates
PPT green section highlighted in circular powerpoint menu template manner Templates-This Diagram shows you the five factors responsible for economic growth in Business .It can be used for creating Business presentations where five factors combined to result in one factor.-Can be used for presentations on 5, around, arrows, border, center, circle, circular, concept, connect, connections, curve, cycle, distribution, five, flow, group, illustration, management, middle, objects, plan, process, recycle, rounded, sections, sectors, shape, symbol, workflow-PPT green section highlighted in circular powerpoint menu template manner Templates Our Ppt Green Section Highlighted In Circular PowerPoint Menu Template Manner Templates impress people. With our money back guarantee you have nothing to lose.

Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample today and make your presentation stand out from the rest This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V
The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa. Explore a selection of the finest Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa.
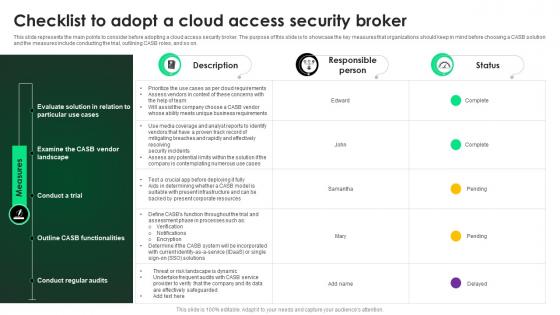
CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers. This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on.

CASB 2 0 IT Steps To Deploy Cloud Access Security Broker
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Steps To Deploy Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Steps To Deploy Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model.
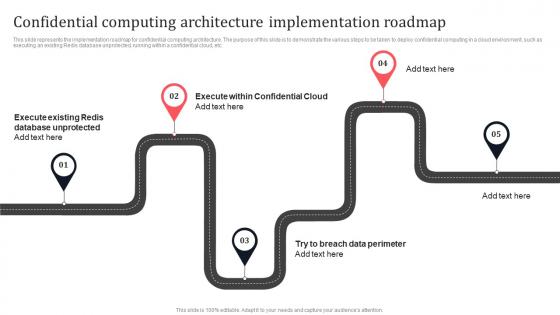
Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

Secure Computing Framework Table Of Contents Inspiration Pdf
Boost your pitch with our creative Secure Computing Framework Table Of Contents Inspiration Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Secure Computing Framework Table Of Contents Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V
The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK.
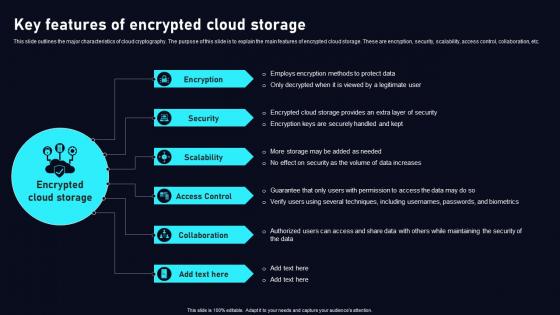
Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.

Global Data Security Industry Report Cybersecurity Industry Competitor Analysis With Attributes IR SS V
The slide presents the key players in the cybersecurity industry. The purpose of the slide is to provide glimpse and competitor analysis of major players in the cybersecurity industry to gain insight into their products, services, and sales. It covers companies such as Palo alto networks, Inc, Fortinet, CrowdStrike, Checkpoint, and Zscaler, Inc. Present like a pro with Global Data Security Industry Report Cybersecurity Industry Competitor Analysis With Attributes IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The slide presents the key players in the cybersecurity industry. The purpose of the slide is to provide glimpse and competitor analysis of major players in the cybersecurity industry to gain insight into their products, services, and sales. It covers companies such as Palo alto networks, Inc, Fortinet, CrowdStrike, Checkpoint, and Zscaler, Inc.
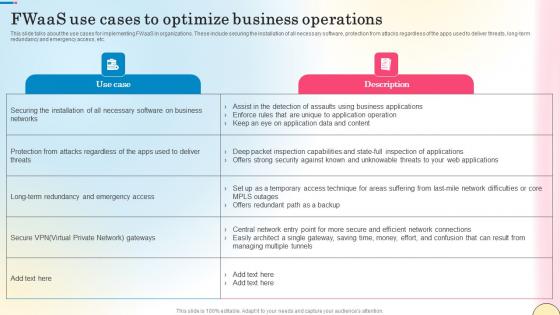
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc.

Secure Web Gateways Market In Powerpoint And Google Slides Cpb
Introducing our well-designed Secure Web Gateways Market In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Web Gateways Market. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Web Gateways Market In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IT Security Roadmap In Powerpoint And Google Slides Cpb
Introducing our well designed IT Security Roadmap In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like IT Security Roadmap. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our IT Security Roadmap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Personal Security Apps Android In Powerpoint And Google Slides Cpb
Introducing our well designed Personal Security Apps Android In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Personal Security Apps Android. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Personal Security Apps Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Analytics Use Cases In Powerpoint And Google Slides Cpb
Introducing our well designed Security Analytics Use Cases In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Analytics Use Cases. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Analytics Use Cases In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Gate Icon In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Gate Icon In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Gate Icon that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Gate Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Application Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Application Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Application Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Application Security Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Network Security Checklist Template In Powerpoint And Google Slides Cpb
Introducing our well designed Network Security Checklist Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Security Checklist Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Security Checklist Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Home Network Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Home Network Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Home Network Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Home Network Diagram In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Sdlc Policy Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Data Science In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Data Science In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Data Science. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Data Science In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Training Roadmap that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Global Security In Powerpoint And Google Slides Cpb
Introducing our well designed Icon Global Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Icon Global Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Icon Global Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Instalation Proposal In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Instalation Proposal In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Instalation Proposal that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Instalation Proposal In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Reporting Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Reporting Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Reporting Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Reporting Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Unblocked Online Security Extension In Powerpoint And Google Slides Cpb
Introducing our well-designed Unblocked Online Security Extension In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Unblocked Online Security Extension. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Unblocked Online Security Extension In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Android Security Malware Detection In Powerpoint And Google Slides Cpb
Introducing our well-designed Android Security Malware Detection In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Android Security Malware Detection. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Android Security Malware Detection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Protection Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Protection Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Spyware Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Spyware Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Communication Encrypted In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Communication Encrypted In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Communication Encrypted. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Communication Encrypted In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Mobile Android Devices Security In Powerpoint And Google Slides Cpb
Introducing our well designed Mobile Android Devices Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Mobile Android Devices Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Mobile Android Devices Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































