Collateral Management

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.

Overview Of Security Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc. This Overview Of Security Tokenization In Data Security Securing Your Data Ppt Sample from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc.
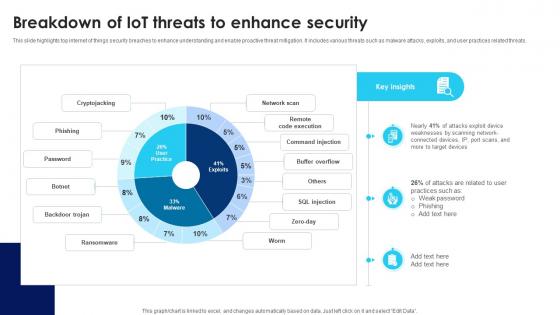
Building Trust With IoT Security Breakdown Of IoT Threats To Enhance Security IoT SS V
This slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats. Present like a pro with Building Trust With IoT Security Breakdown Of IoT Threats To Enhance Security IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats.

Scorecard To Check Cybersecurity And Digital Risk Preparedness Ppt Layouts Brochure PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this scorecard to check cybersecurity and digital risk preparedness ppt layouts brochure pdf. Use them to share invaluable insights on organization, management, measures, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
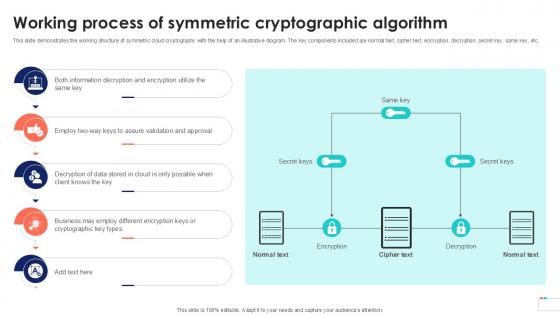
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

Secure Web Gateway Set Up Configuration And Implementation Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. There are so many reasons you need a Secure Web Gateway Set Up Configuration And Implementation Web Threat Protection System. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc.
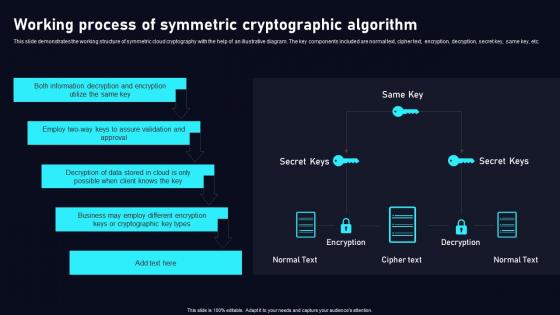
Working Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Want to ace your presentation in front of a live audience OurWorking Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.
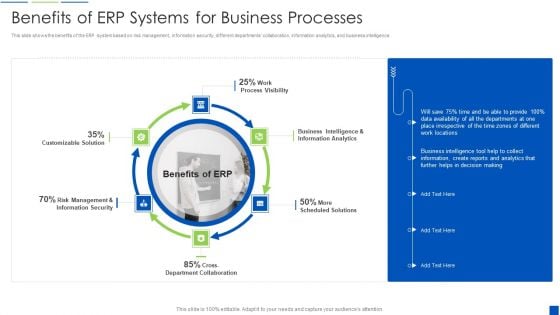
Corporate Resource Planning Benefits Of ERP Systems For Business Processes Download PDF
This slide shows the benefits of the ERP system based on risk management, information security, different departments collaboration, information analytics, and business intelligence.Presenting Corporate Resource Planning Benefits Of ERP Systems For Business Processes Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Customizable Solution, Information Security, Business Intelligence In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
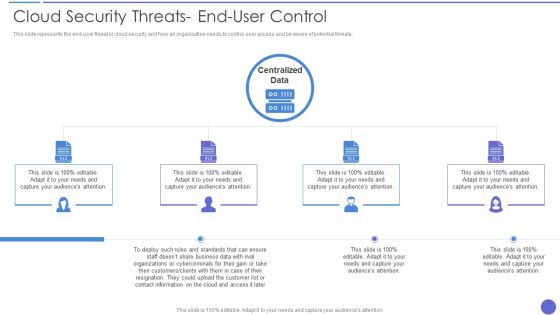
Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Job Responsibilities Ceo Operations And Marketing Landscaping Business Plan Ppt Sample BP SS V
The goal of this slide is to emphasize the important work duties and obligations of the personnel in order to guarantee operational effectiveness and efficiency. It comprises the gardener, marketing executive, lawn care workers, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Key Job Responsibilities Ceo Operations And Marketing Landscaping Business Plan Ppt Sample BP SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Key Job Responsibilities Ceo Operations And Marketing Landscaping Business Plan Ppt Sample BP SS V The goal of this slide is to emphasize the important work duties and obligations of the personnel in order to guarantee operational effectiveness and efficiency. It comprises the gardener, marketing executive, lawn care workers, etc.
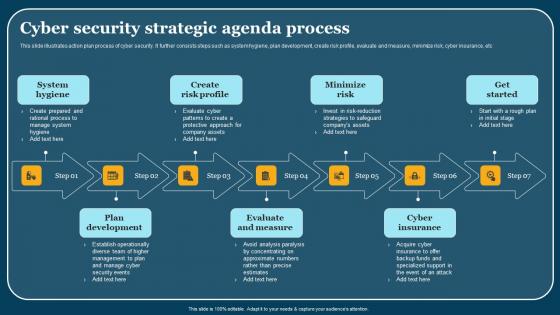
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.
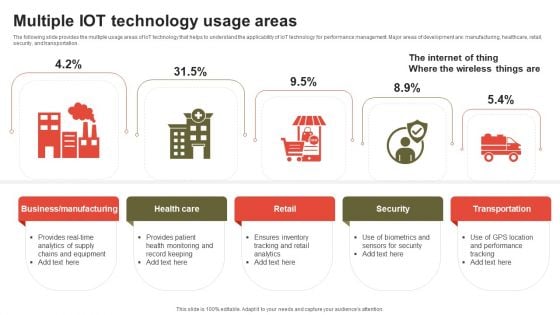
Multiple IOT Technology Usage Areas Sample PDF
The following slide provides the multiple usage areas of IoT technology that helps to understand the applicability of IoT technology for performance management. Major areas of development are manufacturing, healthcare, retail, security, and transportation. Presenting Multiple IOT Technology Usage Areas Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Health Care, Retail, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
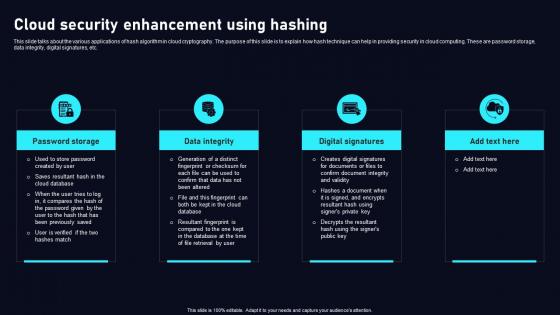
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.

Introduction Of Application Security For Data Privacy Application Security Testing
This slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc. Explore a selection of the finest Introduction Of Application Security For Data Privacy Application Security Testing here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Application Security For Data Privacy Application Security Testing to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc.

Security Testing Types Vulnerability Scanning Application Security Testing
This slide outlines the overview of vulnerability scanning in security testing for application security. Do you know about Slidesgeeks Security Testing Types Vulnerability Scanning Application Security Testing These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the overview of vulnerability scanning in security testing for application security.

Security Testing Types Penetration Testing Application Security Testing
This slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing. Take your projects to the next level with our ultimate collection of Security Testing Types Penetration Testing Application Security Testing. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing.
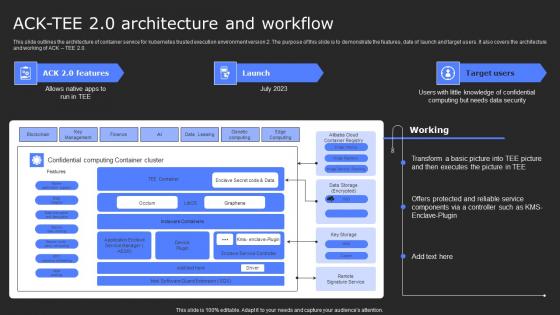
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
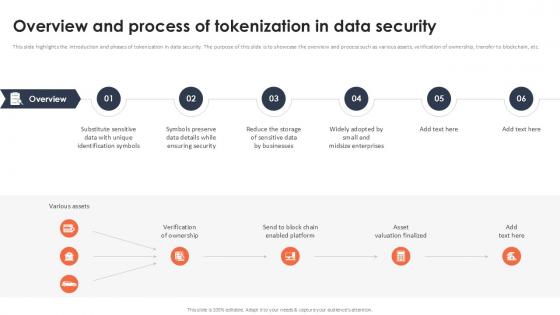
Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Slidegeeks has constructed Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.

Challenge And Solutions 1 Malware And Ransomware Attacks Ppt Model Objects PDF
This slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Deliver and pitch your topic in the best possible manner with this challenge and solutions 1 malware and ransomware attacks ppt model objects pdf. Use them to share invaluable insights on access management, security software and ensure, comprehensive security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Transformation Toolkit Accounting Finance Accounting And Financial Software Features Slides PDF
In this slide, we have showcased key specifications and features that can help in achieving maximum efficiency in business operations like sales invoice, registration, advance security and input tax credit. This is a digital transformation toolkit accounting finance accounting and financial software features slides pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like export management, client authentication, latest security features. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
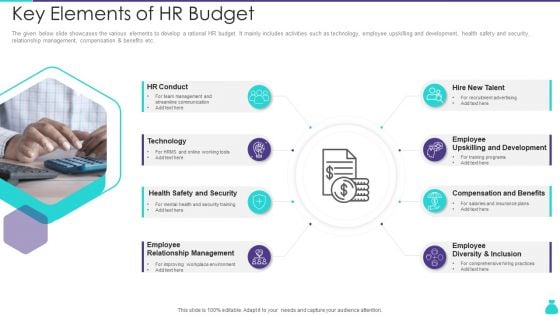
Key Elements Of HR Budget Ppt PowerPoint Presentation File Infographics PDF
The given below slide showcases the various elements to develop a rational HR budget. It mainly includes activities such as technology, employee upskilling and development, health safety and security, relationship management, compensation and benefits etc. Presenting Key Elements Of HR Budget Ppt PowerPoint Presentation File Infographics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including HR Conduct, Technology, Health Safety And Security, Employee Diversity And Inclusion. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

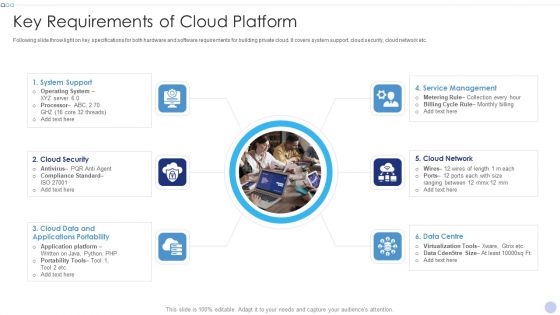
Cloud Optimization Infrastructure Model Key Requirements Of Cloud Platform Download PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Presenting Cloud Optimization Infrastructure Model Key Requirements Of Cloud Platform Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Service Management, Applications Portability, Cloud Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Techniques To Implement Cloud Infrastructure Key Requirements Of Cloud Platform Download PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Presenting Techniques To Implement Cloud Infrastructure Key Requirements Of Cloud Platform Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Service Management, Applications Portability, Cloud Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

VID Benefits Of End User Computing To Business Sample PDF
This slide depicts the benefits of the end user computing to business and it includes centralized management, BYOD support, secure end user environment and built in disaster recovery.Presenting VID Benefits Of End User Computing To Business Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Significantly Higher, Centralized In Secure, Disaster Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
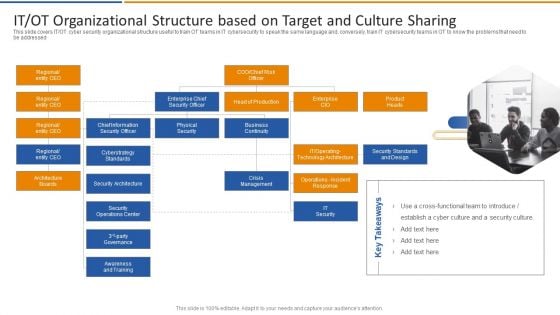
Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. This is a Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise CIO, Product Heads, Crisis Management, IT Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
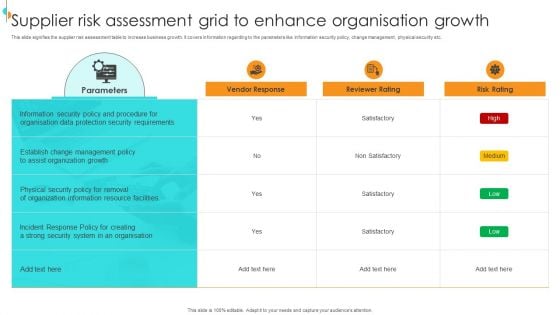
Supplier Risk Assessment Grid To Enhance Organisation Growth Download PDF
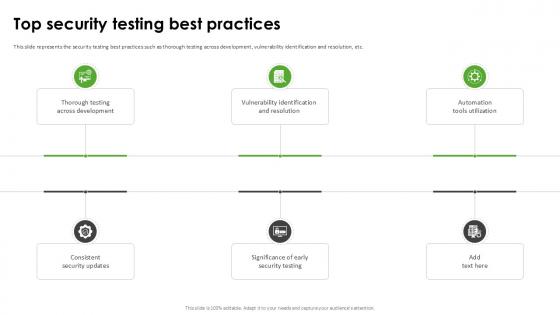
Top Security Testing Best Harnessing The World Of Ethical Ppt Presentation
This slide represents the security testing best practices such as thorough testing across development, vulnerability identification and resolution, etc. Take your projects to the next level with our ultimate collection of Top Security Testing Best Harnessing The World Of Ethical Ppt Presentation Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the security testing best practices such as thorough testing across development, vulnerability identification and resolution, etc.
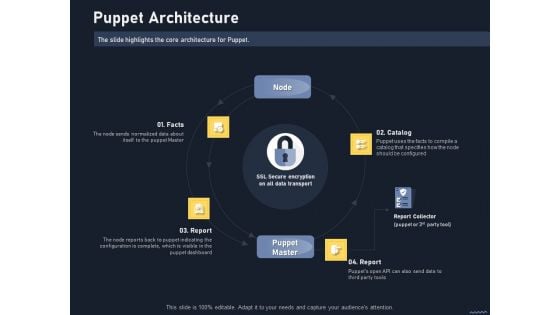
Puppet Tool For Server Configuration Administration Puppet Architecture Demonstration PDF
The slide highlights a brief Puppet workflow. Presenting puppet tool for server configuration administration puppet architecture demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like facts, report, catalog, report collector. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.
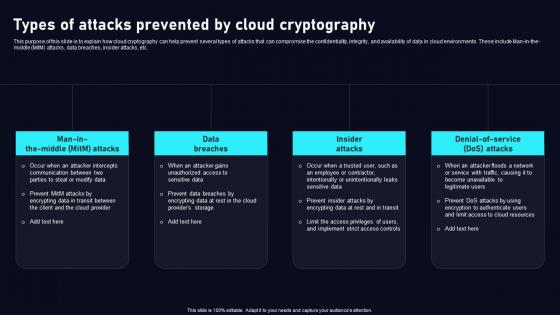
Types Of Attacks Prevented By Cloud Data Security Using Cryptography Guidelines Pdf
This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man in the middle MitM attacks, data breaches, insider attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Attacks Prevented By Cloud Data Security Using Cryptography Guidelines Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man in the middle MitM attacks, data breaches, insider attacks, etc.

Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V
The slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High R and D cost, legal and ethical challenges. Create an editable Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High R and D cost, legal and ethical challenges.

Importance Of 5G Network Security Policies Portrait Pdf
This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc. Showcasing this set of slides titled Importance Of 5G Network Security Policies Portrait Pdf. The topics addressed in these templates are Access Network Security, Core Network Security, Security Enablers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc.

Top Five Application Security Trends Application Security Testing
This slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc. Slidegeeks has constructed Top Five Application Security Trends Application Security Testing after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc.
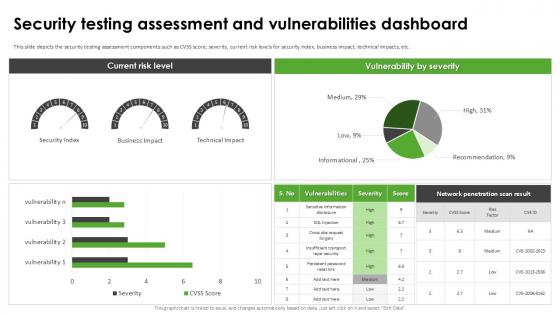
Security Testing Assessment Harnessing The World Of Ethical Ppt Example
This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc. This Security Testing Assessment Harnessing The World Of Ethical Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Testing Assessment Harnessing The World Of Ethical Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc.
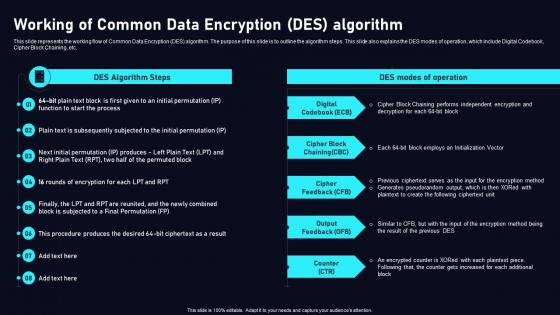
Working Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Boost your pitch with our creativeWorking Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.

Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System a try. Our experts have put a lot of knowledge and effort into creating this impeccable Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.

Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Overview Of Secure Access Service Edge Network Security Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
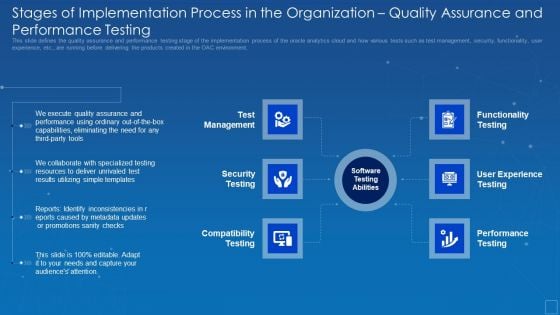
Oracle Cloud Data Analytics Administration IT Stages Implementation Organization Sample PDF
This slide defines the quality assurance and performance testing stage of the implementation process of the oracle analytics cloud and how various tests such as test management, security, functionality, user experience, etc., are running before delivering the products created in the OAC environment. This is a oracle cloud data analytics administration it stages implementation organization sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like eliminating, quality, assurance, performance, capabilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
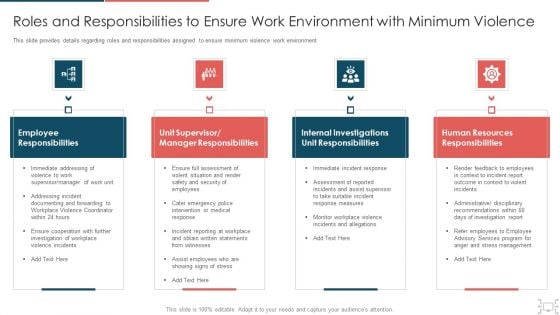
cyber security administration in organization roles and responsibilities to ensure work environment slides pdf
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a cyber security administration in organization roles and responsibilities to ensure work environment slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsibilities, manager, assessment, manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait
This slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait This slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
Security System In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security System In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security System that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security System In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Security Program In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Application Security Program In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Application Security Program that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Application Security Program In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification. Find highly impressive Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification.
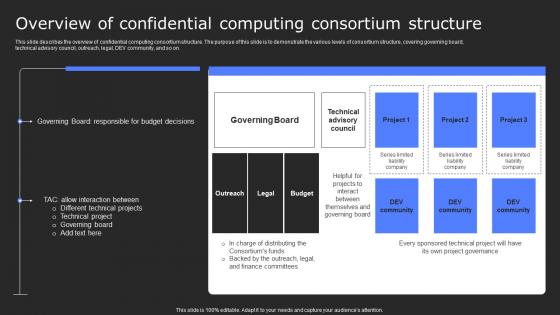
Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.
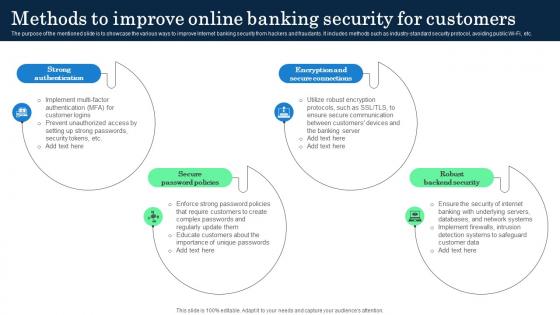
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.
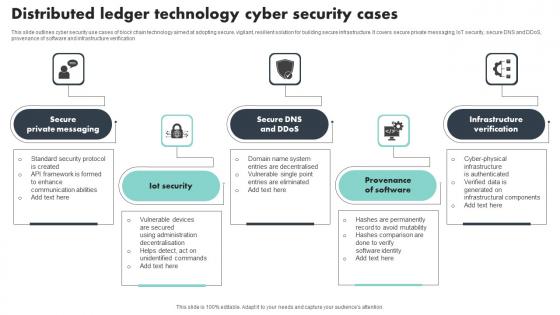
Distributed Ledger Technology Cyber Security Cases Brochure Pdf
This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification Showcasing this set of slides titled Distributed Ledger Technology Cyber Security Cases Brochure Pdf The topics addressed in these templates are Private Messaging, Provenance Of Software, Infrastructure Verification All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification
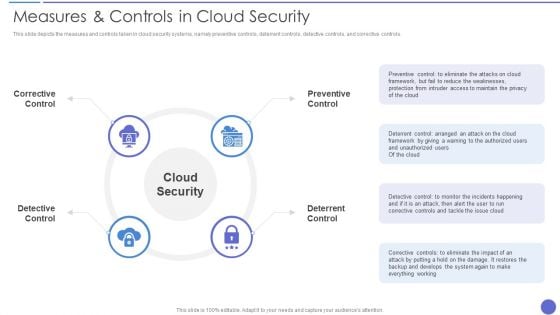
Measures And Controls In Cloud Security Ideas PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Measures And Controls In Cloud Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.

Process Phases Of Penetration Testing In Application Security Testing
This slide highlights the steps for implementing penetration testing which include planning and reconnaissance, gaining access, etc. Presenting this PowerPoint presentation, titled Process Phases Of Penetration Testing In Application Security Testing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Process Phases Of Penetration Testing In Application Security Testing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Process Phases Of Penetration Testing In Application Security Testing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights the steps for implementing penetration testing which include planning and reconnaissance, gaining access, etc.
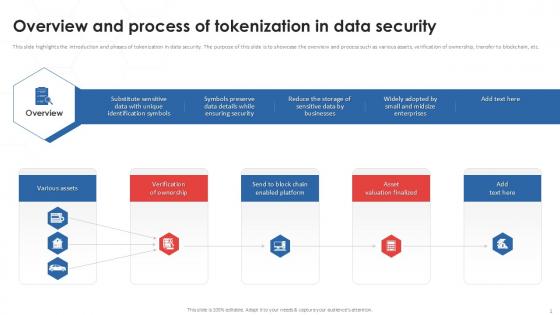
Overview And Process Of Tokenization In Data Security PPT Example
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Find a pre-designed and impeccable Overview And Process Of Tokenization In Data Security PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
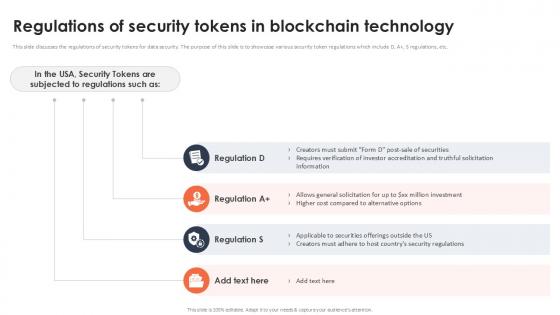
Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.

Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V
The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V can be your best option for delivering a presentation. Represent everything in detail using Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments.

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices.
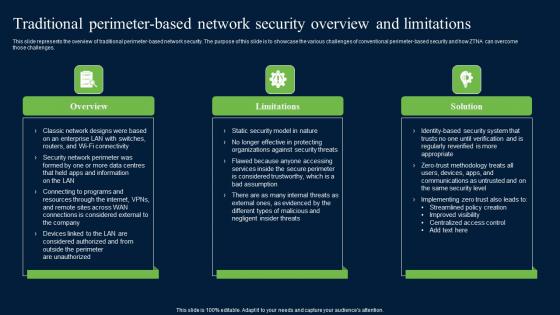
Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides
This slide discusses the two types of secure code review in application security which are automated code review and manual code review. This Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide discusses the two types of secure code review in application security which are automated code review and manual code review.
Secure Copy Protocolreport Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Copy Protocolreport Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Copy Protocolreport Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Copy Protocolreport Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Five Pillars Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Five Pillars Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Five Pillars Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Five Pillars Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Risk Dashboard In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Risk Dashboard In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Risk Dashboard. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Risk Dashboard In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































