Collateral Management

Security Software Company Investor Funding Pitch Deck Key Facts Template PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Security Software Company Investor Funding Pitch Deck Key Facts Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF today and make your presentation stand out from the rest.
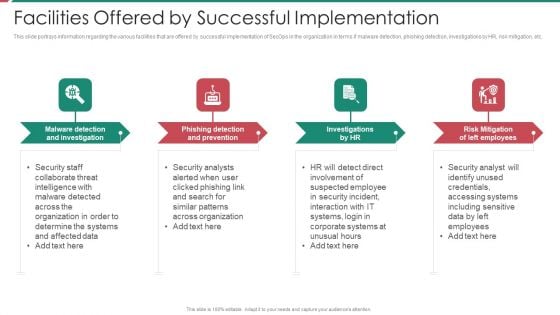
Security And Process Integration Facilities Offered By Successful Implementation Sample PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a security and process integration facilities offered by successful implementation sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
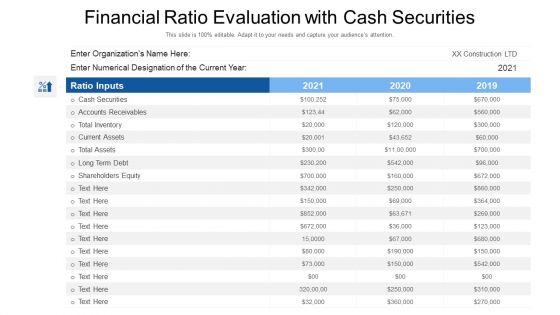
Financial Ratio Evaluation With Cash Securities Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled financial ratio evaluation with cash securities ppt powerpoint presentation file show pdf. The topics addressed in these templates are shareholders equity, current assets, accounts receivables. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
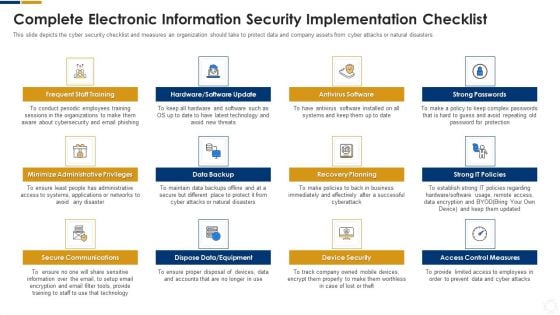
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hospital Administration Healthcare Industry Key Challenges Ppt Visual Aids Summary PDF
Deliver an awe inspiring pitch with this creative hospital administration healthcare industry key challenges ppt visual aids summary pdf bundle. Topics like rising us healthcare costs, rising patient expectations, security, privacy and compliance, ageing us demographics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our House And Question Mark Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Network diagrams PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download our Communication PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Question mark with house,business, finance, success, signs, marketing . The prominent colors used in the PowerPoint template are Blue, Gray, Blue. Specify paths to success with our House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.

Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Use Internet Security For Business PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Present our Globe PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Computer mouse is connected to a globe - surfing and browsing is blocked by a red do not enter sign that cuts the cable, technology, communication, signs, globe, business. The prominent colors used in the PowerPoint template are Blue, White, Black. Our Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413 will keep the faith. They will show allegiance to your thoughts.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Present like a pro with Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Online Business Challenges And Best Practices Brochure Pdf
The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc. Pitch your topic with ease and precision using this Online Business Challenges And Best Practices Brochure Pdf. This layout presents information on Pain Points, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc.

Data Integration Architecture Creation Best Practices Data Integration Strategies For Business
This slide highlights the best practices followed in data integration architecture. The purpose of this slide is to explain these practices, such as business objectives, collaboration, automation, flexibility, and security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Data Integration Architecture Creation Best Practices Data Integration Strategies For Business. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Data Integration Architecture Creation Best Practices Data Integration Strategies For Business today and make your presentation stand out from the rest This slide highlights the best practices followed in data integration architecture. The purpose of this slide is to explain these practices, such as business objectives, collaboration, automation, flexibility, and security.

Automated Government Procedures Government To Consumer Services Demonstration PDF
Our IT Solutions enable seamless and secure interactions between governments and citizens. We support these interactions through powerful government IT applications and a robust infrastructure. Deliver an awe-inspiring pitch with this creative automated government procedures government to consumer services demonstration pdf bundle. Topics like government to consumer services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Locked Money Future Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Locked Money Future Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Money PowerPoint Templates because you have the product you need. Download our Technology PowerPoint Templates because they have always been a source of inspiration for us all. Download our Business PowerPoint Templates because watch the excitement levels rise as they realise their worth. Use our Marketing PowerPoint Templates because you can Amplify your views, ideas and thoughts from very basic aspects to the highly technical and complicated issus using this template as a tool. Download our Services PowerPoint Templates because they are the indicators of the path you have in mind.Use these PowerPoint slides for presentations relating to Money for security and investment, money, technology,business, marketing, services. The prominent colors used in the PowerPoint template are Orange, Gray, White. We assure you our Locked Money Future Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Glamorous. Customers tell us our investment PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. You can be sure our Locked Money Future Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Luxuriant. People tell us our security PowerPoint templates and PPT Slides are Energetic. Presenters tell us our Locked Money Future Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Luxurious. People tell us our money PowerPoint templates and PPT Slides are visually appealing. Your team will get faithfully behind you. Assume control with our Locked Money Future Security PowerPoint Templates Ppt Backgrounds For Slides 1212.
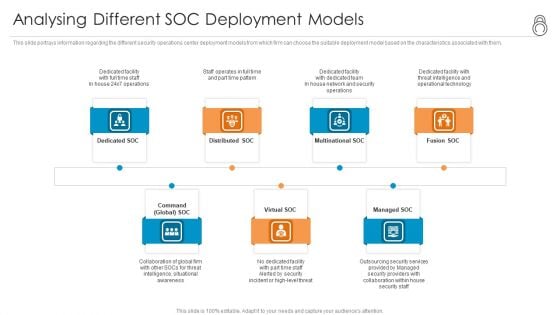
Enhanced Protection Corporate Event Administration Analysing Different SOC Deployment Models Information PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a enhanced protection corporate event administration analysing different soc deployment models information pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Social Media Hiring Strategic Procedure Job Description Form To Target Right Candidate Graphics PDF
This slide focuses on job description form to target right candidate by defining job title, department name, supervisor, location, contact number, key responsibilities and accountabilities, etc. Deliver and pitch your topic in the best possible manner with this Social Media Hiring Strategic Procedure Job Description Form To Target Right Candidate Graphics PDF. Use them to share invaluable insights on Financial Procedures, Ensuring Inventory, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.
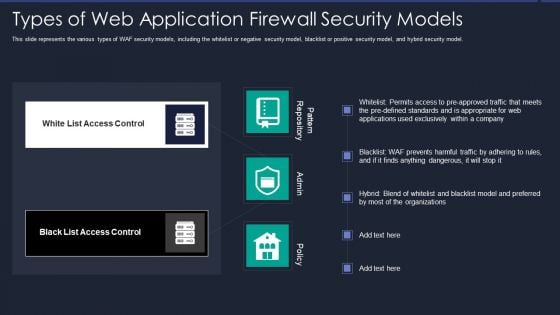
Web App Firewall Services IT Types Of Web Application Firewall Security Models Background PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting web app firewall services it types of web application firewall security models background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like applications, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Application Development Best Practices Ppt Inspiration Tips Pdf
This slide represents best practices of web application development for users. It includes various practices such as take right tech stack, build attractive design, use robust CMS and ensure security. Showcasing this set of slides titled Web Application Development Best Practices Ppt Inspiration Tips Pdf. The topics addressed in these templates are Right Tech Stack, Build Attractive Design, Use Robust CMS. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents best practices of web application development for users. It includes various practices such as take right tech stack, build attractive design, use robust CMS and ensure security.
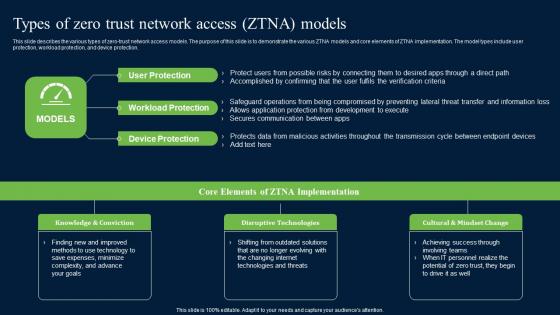
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
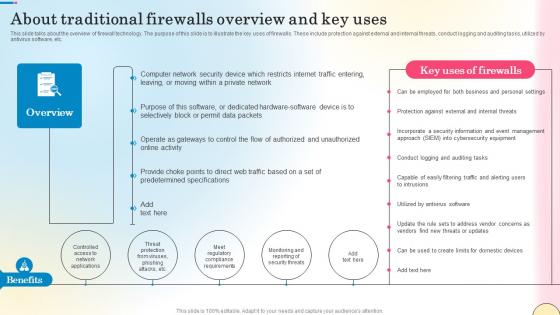
About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc.

Securing Market Leadership Through Competitive Excellence Company Overview Apple Themes PDF
The following slide exhibits general overview of Apple company. Mission and vision statement, key stakeholders, details, products and services offered and major facts and figures are the key elements of Apple company which is mentioned in the slide. There are so many reasons you need a Securing Market Leadership Through Competitive Excellence Company Overview Apple Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Series Of Cyber Security Attacks Against Ukraine 2022 Should We Be Concerned About Russian Cyberattacks Information PDF
This slide shows that US citizens should not be concerned about russian cyberattacks as nothing has happened so far. However, the US department of homeland security issued a warning to organizations to look for russian cyberattacks. Make sure to capture your audiences attention in your business displays with our gratis customizable Series Of Cyber Security Attacks Against Ukraine 2022 Should We Be Concerned About Russian Cyberattacks Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
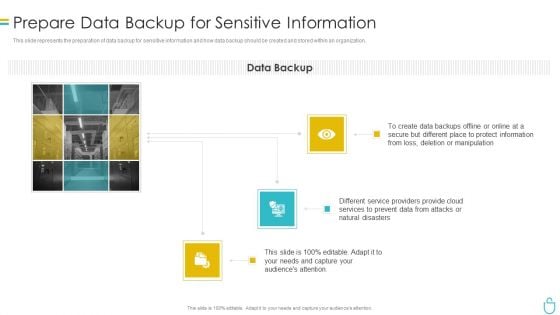
Information Security Prepare Data Backup For Sensitive Information Ppt Introduction PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information security prepare data backup for sensitive information ppt introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, manipulation, services, natural disasters, secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
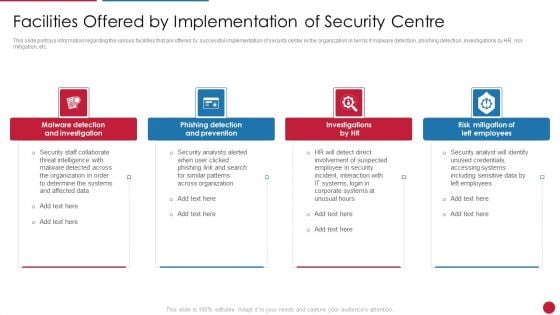
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V
This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols. Slidegeeks is here to make your presentations a breeze with Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
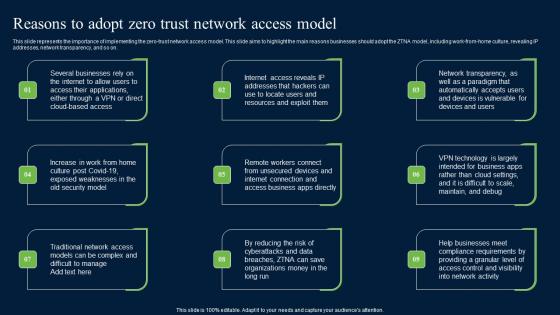
Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
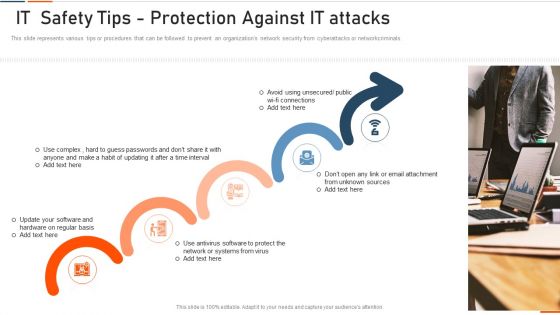
Information Technology Security IT Safety Tips Protection Against IT Attacks Ppt Layouts Outfit PDF
This slide represents various tips or procedures that can be followed to prevent an organizations network security from cyberattacks or networkcriminals. This is a information technology security it safety tips protection against it attacks ppt layouts outfit pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, antivirus, systems, sources, unsecured. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Critical Security Concerns Issues On Overall Firms Performance Elements PDF
This slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Critical Security Concerns Issues On Overall Firms Performance Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Critical Security Concerns Issues On Overall Firms Performance Elements PDF today and make your presentation stand out from the rest.
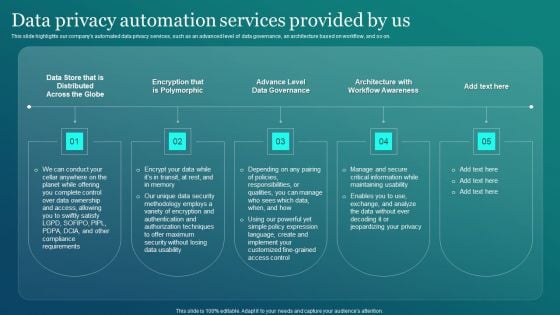
Information Security Data Privacy Automation Services Provided By Us Sample PDF
This slide highlights our companys automated data privacy services, such as an advanced level of data governance, an architecture based on workflow, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Information Security Data Privacy Automation Services Provided By Us Sample PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Information Security Data Privacy Automation Services Provided By Us Sample PDF.
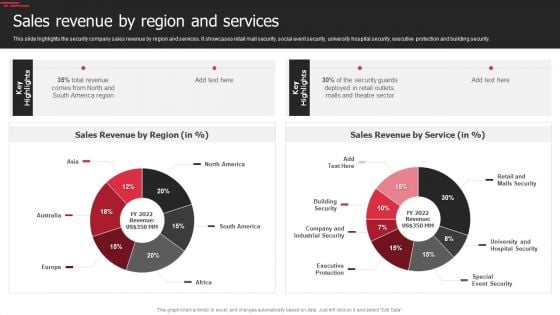
Security Agency Business Profile Sales Revenue By Region And Services Slides PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Sales Revenue By Region And Services Slides PDF. Use them to share invaluable insights on Revenue, Security, Executive Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

IT Security IT Awareness Training For Staff Ppt Gallery Example Introduction PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this it security it awareness training for staff ppt gallery example introduction pdf. Use them to share invaluable insights on developers, organizations, senior executives, planning, strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
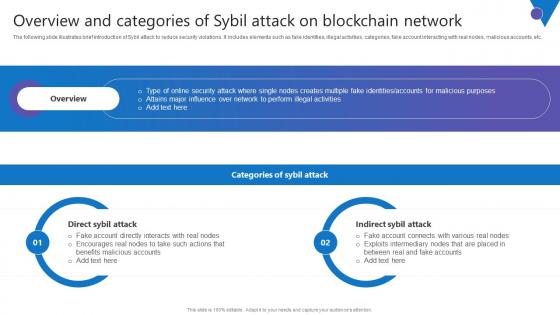
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.
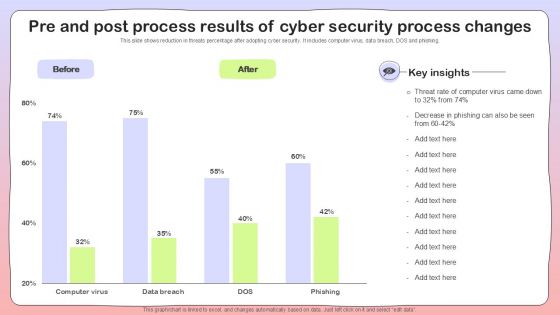
Pre And Post Process Results Of Cyber Security Process Changes Sample PDF

Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. Get a simple yet stunning designed Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF. Use them to share invaluable insights on Security And Compliance, SAML Authentication, Data Subject Requests and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
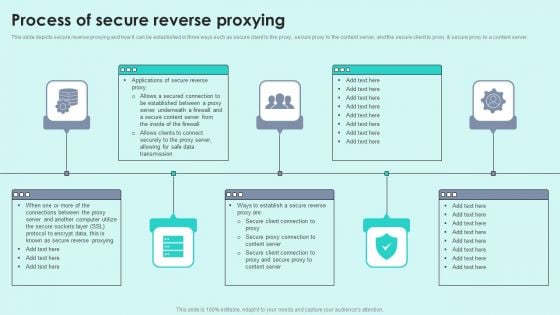
Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy secure proxy to a content server.This is a Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secured Connection, Established Between, Underneath Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF
Pitch your topic with ease and precision using this Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF. This layout presents information on Compliance Trend, Risk Status, Risk Severity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
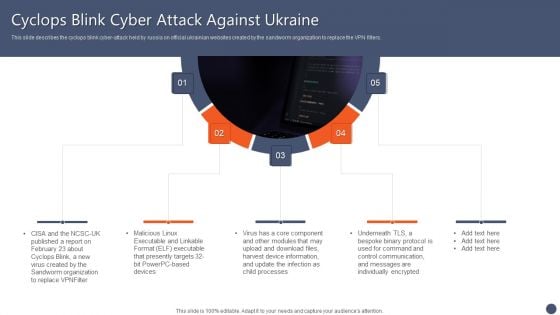
Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF
This slide describes the cyclops blink cyber attack held by russia on official ukrainian websites created by the sandworm organization to replace the VPN filters. Get a simple yet stunning designed Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
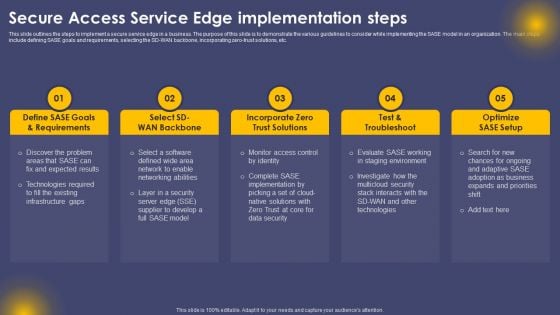
Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF
This slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Get a simple yet stunning designed Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Implementation Steps Ppt Visual Aids Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
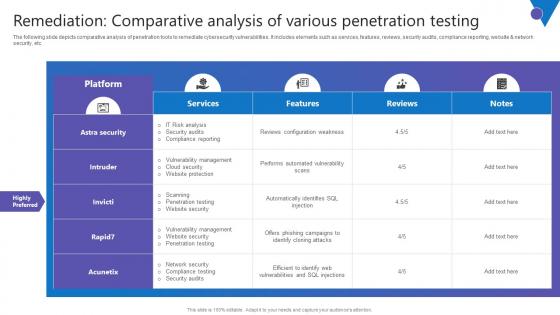
Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf
The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Take your projects to the next level with our ultimate collection of Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc.

Major Focus Of White Box Testing Gray Box Testing Best Practices
This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Focus Of White Box Testing Gray Box Testing Best Practices and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on.
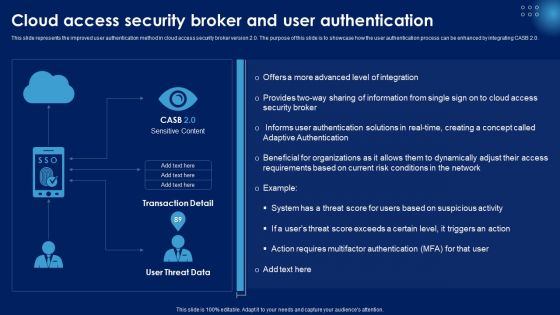
Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

How Is Automation Used In Cybersecurity IT Security IT Ppt Topics PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. This is a how is automation used in cybersecurity it security it ppt topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat detection, threat response, human augmentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Dispose Data And Equipment Properly Ppt Infographics Styles PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information security dispose data and equipment properly ppt infographics styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
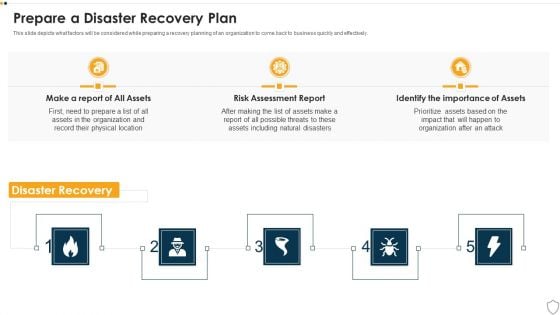
IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Prepare Data Backup For Sensitive Information Ppt Portfolio Slide Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Presenting it security prepare data backup for sensitive information ppt portfolio slide download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prepare data backup for sensitive information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
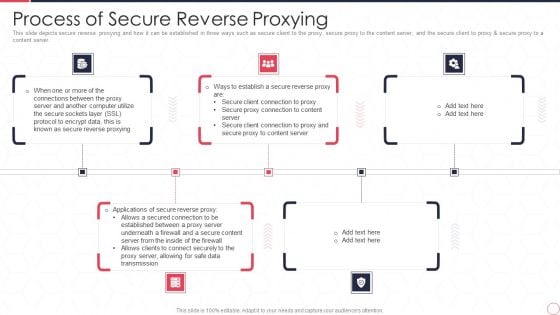
Reverse Proxy Server IT Process Of Secure Reverse Proxying Ppt Slides Mockup PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Presenting reverse proxy server it process of secure reverse proxying ppt slides mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like proxy server, data transmission, secure content server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
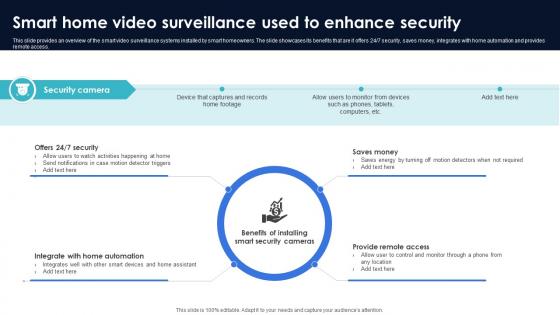
Optimization Of IoT Remote Monitoring Smart Home Video Surveillance Used To Enhance Security IoT SS V
This slide provides an overview of the smart video surveillance systems installed by smart homeowners. The slide showcases its benefits that are it offers 24x7 security, saves money, integrates with home automation and provides remote access. Slidegeeks has constructed Optimization Of IoT Remote Monitoring Smart Home Video Surveillance Used To Enhance Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide provides an overview of the smart video surveillance systems installed by smart homeowners. The slide showcases its benefits that are it offers 24x7 security, saves money, integrates with home automation and provides remote access.
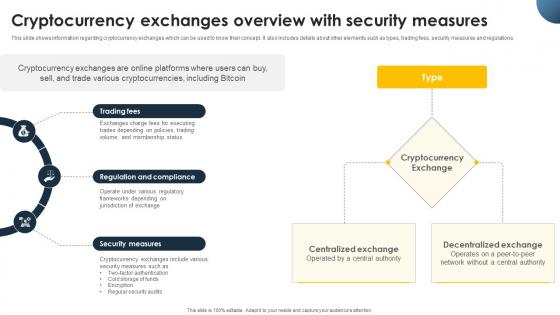
Complete Beginners Guide Cryptocurrency Exchanges Overview With Security Fin SS V
This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Complete Beginners Guide Cryptocurrency Exchanges Overview With Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations.
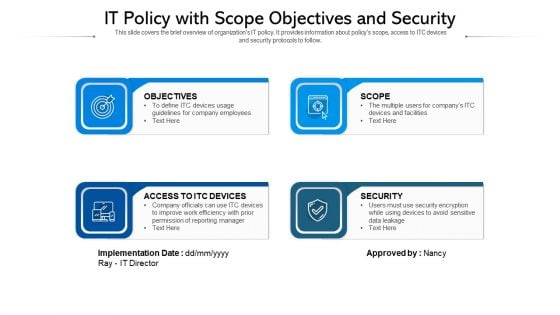
IT Policy With Scope Objectives And Security Ppt PowerPoint Presentation Infographics Show PDF
This slide covers the brief overview of organizations IT policy. It provides information about policys scope, access to ITC devices and security protocols to follow. Persuade your audience using this IT policy with scope objectives and security ppt powerpoint presentation infographics show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including objectives, access to itc devices, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
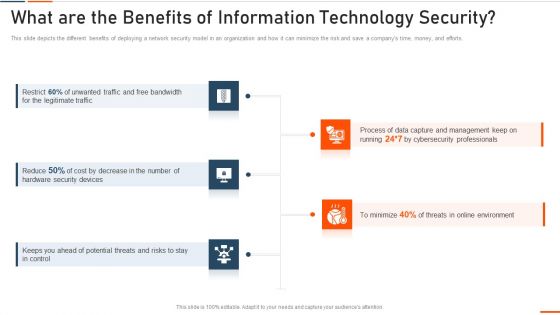
What Are The Benefits Of Information Technology Security Ppt Styles Model PDF
This slide depicts the different benefits of deploying a network security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting what are the benefits of information technology security ppt styles model pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like bandwidth, legitimate, security devices, potential . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
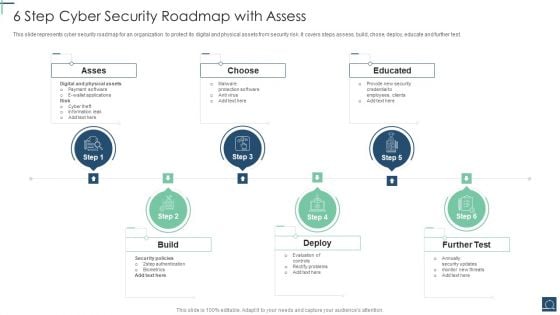
6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF
This slide represents cyber security roadmap for an organization to protect its digital and physical assets from security risk .It covers steps assess, build, chose, deploy, educate and further test. Persuade your audience using this 6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Asses, Choose, Educated, Build. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
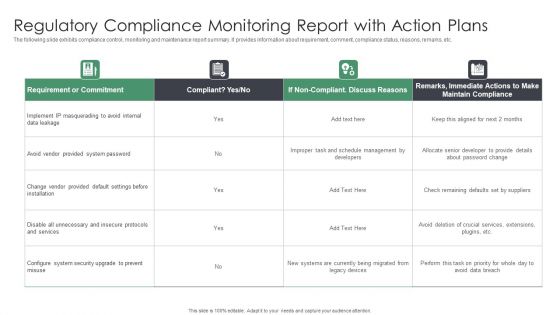
Regulatory Compliance Monitoring Report With Action Plans Download PDF
The following slide exhibits compliance control, monitoring and maintenance report summary. It provides information about requirement, comment, compliance status, reasons, remarks, etc. Showcasing this set of slides titled Regulatory Compliance Monitoring Report With Action Plans Download PDF. The topics addressed in these templates are Requirement Or Commitment, System, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































