Collateral Management
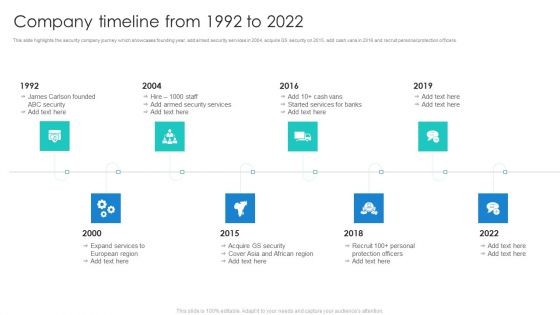
Manpower Corporate Security Business Profile Company Timeline From 1992 To 2022 Demonstration PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Manpower Corporate Security Business Profile Company Timeline From 1992 To 2022 Demonstration PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Protection Officers, Recruit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
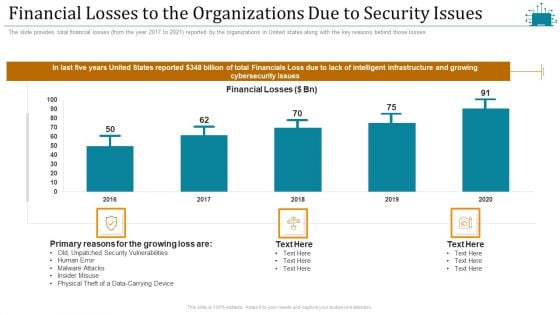
Cloud Intelligence Framework For Application Consumption Financial Losses To The Organizations Due To Security Issues Mockup PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption financial losses to the organizations due to security issues mockup pdf bundle. Topics like security vulnerabilities, primary reasons for the growing, physical theft of a data-carrying device, 2016 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
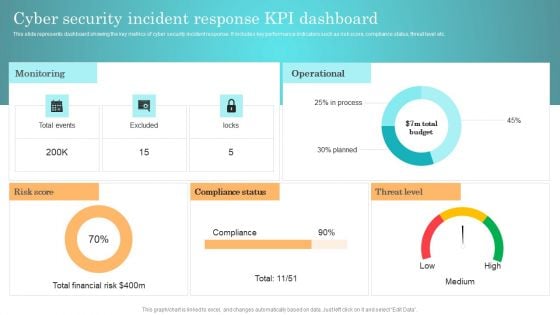
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
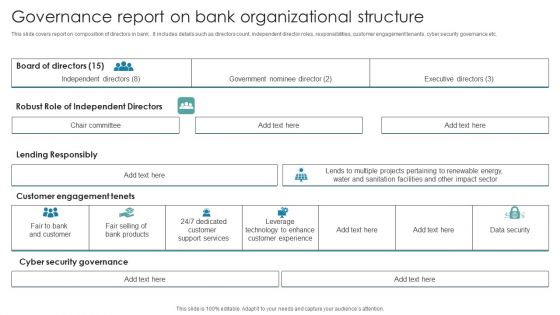
Governance Report On Bank Organizational Structure Slides PDF
This slide covers report on composition of directors in bank . It includes details such as directors count, independent director roles, responsibilities, customer engagement tenants, cyber security governance etc. Showcasing this set of slides titled Governance Report On Bank Organizational Structure Slides PDF. The topics addressed in these templates are Executive Directors, Leverage Technology, Customer Support Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
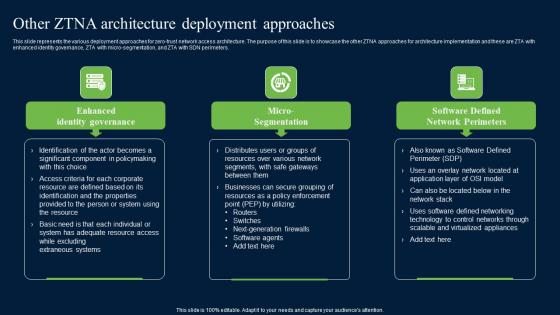
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
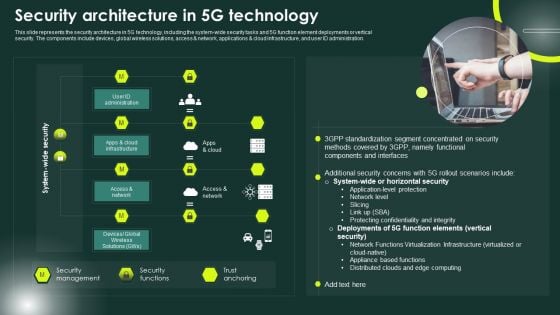
5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Internet Security Kpis And Metrics Ppt PowerPoint Presentation Gallery Outline PDF
Showcasing this set of slides titled internet security kpis and metrics ppt powerpoint presentation gallery outline pdf. The topics addressed in these templates are threat detection, risk and compliance, services compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
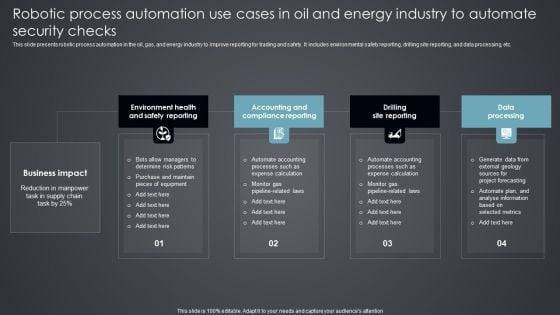
Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF
This slide presents robotic process automation in the oil, gas, and energy industry to improve reporting for trading and safety. It includes environmental safety reporting, drilling site reporting, and data processing, etc. Presenting Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Environment Health, Accounting Compliance Reporting, Drilling Site Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
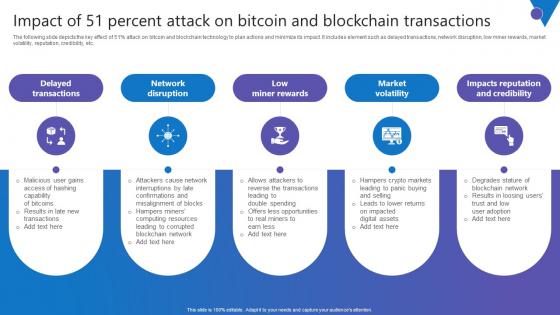
Impact Of 51 Percent Attack Comprehensive Guide To Blockchain Digital Security Infographics Pdf
The following slide depicts the key effect of 51percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc. Present like a pro with Impact Of 51 Percent Attack Comprehensive Guide To Blockchain Digital Security Infographics Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide depicts the key effect of 51percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc.

Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V
This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign. Present like a pro with Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign.
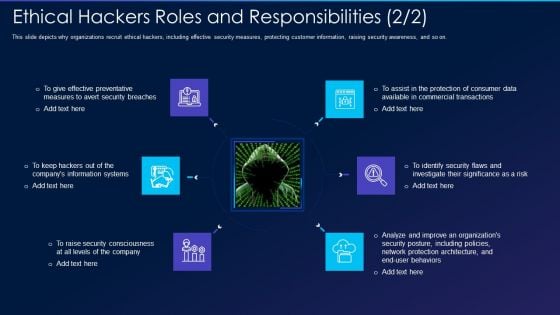
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
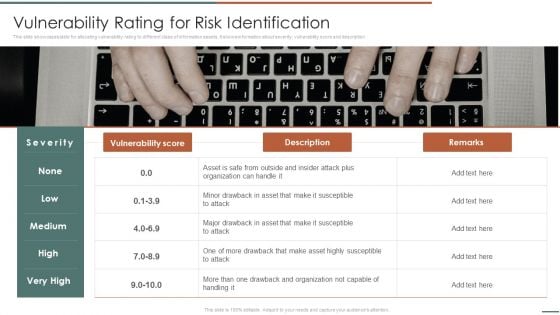
Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
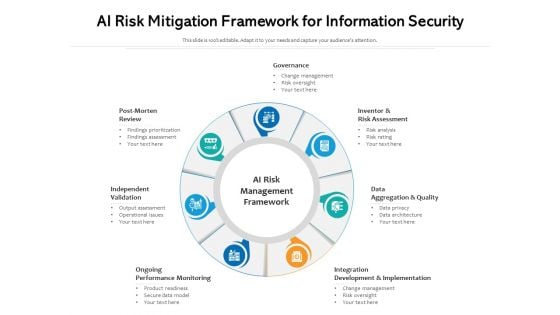
AI Risk Mitigation Framework For Information Security Ppt PowerPoint Presentation Gallery Slides PDF
Presenting ai risk mitigation framework for information security ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including governance, independent validation, ongoing performance monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF
This slide represents the continuous cyber espionage attacks held by the shuckworm group against ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF.
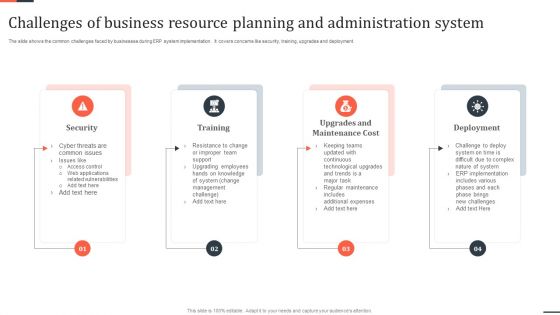
Challenges Of Business Resource Planning And Administration System Download PDF
The slide shows the common challenges faced by businesses during ERP system implementation. It covers concerns like security, training, upgrades and deployment. Persuade your audience using this Challenges Of Business Resource Planning And Administration System Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Training, Security, Deployment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
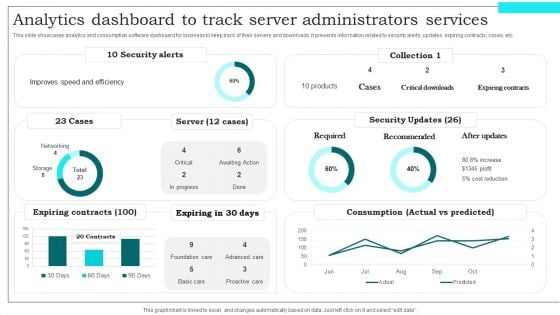
Analytics Dashboard To Track Server Administrators Services Demonstration PDF
This slide showcases analytics and consumption software dashboard for business to keep track of their servers and downloads. It presents information related to security alerts, updates, expiring contracts, cases, etc. Showcasing this set of slides titled Analytics Dashboard To Track Server Administrators Services Demonstration PDF. The topics addressed in these templates are Expiring Contracts, Security Updates, Required. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
International Finance Corporation With World Bank Strategy Diagram Ppt Icon
This is a international finance corporation with world bank strategy diagram ppt icon. This is a five stage process. The stages in this process are international finance corporation, international development association, international bank for reconstruction and development, international finance cooperation, multilateral investment guarantee agency, international center for settlement of investment disputes.

Keyhole Circular Infographic Design Powerpoint Templates
This slide has been designed with circular infographic with key hole in center. This PowerPoint template is suitable to present key steps of success. This professional slide helps in making an instant impact on viewers.
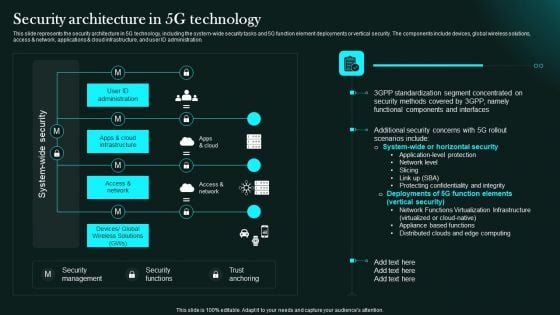
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
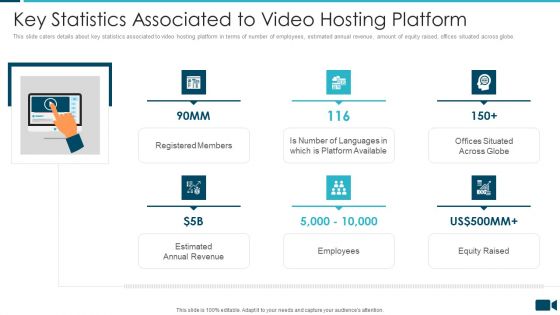
Secured Video Hosting Platform Investor Capital Funding Key Statistics Associated To Video Hosting Platform Rules PDF
This slide caters details about key statistics associated to video hosting platform in terms of number of employees, estimated annual revenue, amount of equity raised, offices situated across globe. Presenting secured video hosting platform investor capital funding key statistics associated to video hosting platform rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like registered members, employees, equity raised, estimated annual revenue. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
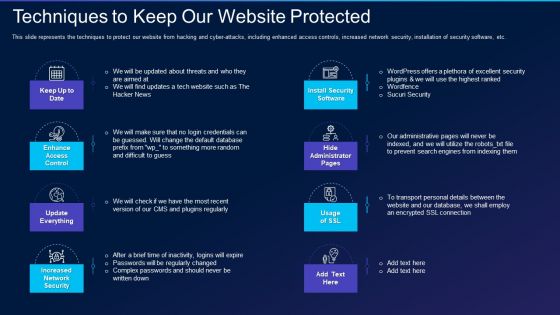
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. This Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc.

International Organization Standardization 270001 Risk Assessment Worksheet Information PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. This is a international organization standardization 270001 risk assessment worksheet information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk encountered, vulnerability, asset and consequences. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
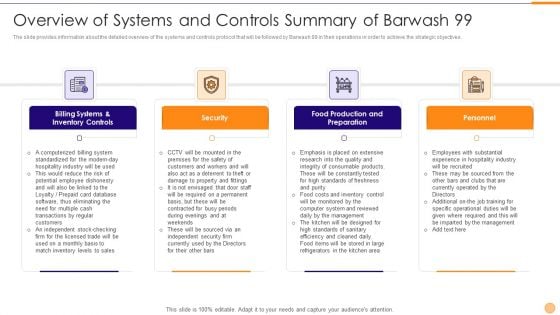
Classified Data Memo Record With Strategic Goals Overview Of Systems And Controls Summary Of Barwash 99 Rules PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting classified data memo record with strategic goals overview of systems and controls summary of barwash 99 rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems and inventory controls, security, food production and preparation, personnel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Technology Facilities Governance Client Standards Checklist Contd Icons PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a information technology facilities governance client standards checklist contd icons pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect servers, high speed internet access, secured encryption, wireless data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
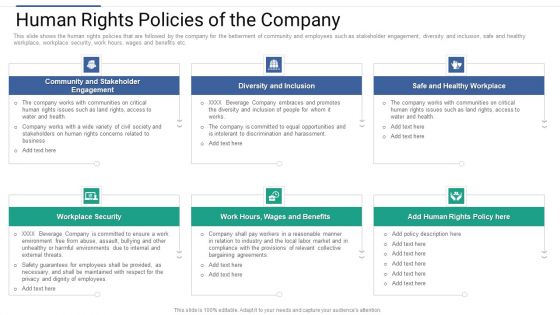
Shareholder Governance Enhance Comprehensive Corporate Performance Human Rights Policies Download PDF
This slide shows the human rights policies that are followed by the company for the betterment of community and employees such as stakeholder engagement, diversity and inclusion, safe and healthy workplace, workplace security, work hours, wages and benefits etc. Presenting shareholder governance enhance comprehensive corporate performance human rights policies download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like stakeholder, engagement, community, diversity, workplace, benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
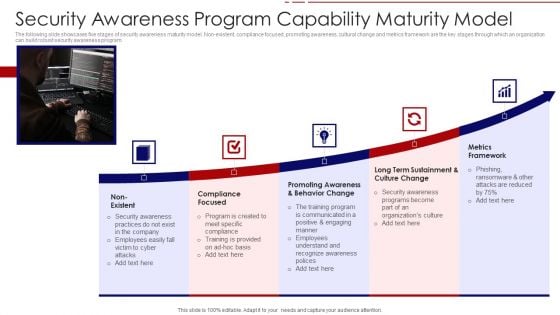
Security Awareness Program Capability Maturity Model Ppt PowerPoint Presentation File Portfolio PDF
The following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Persuade your audience using this security awareness program capability maturity model ppt powerpoint presentation file portfolio pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including non existent, compliance focused, promoting awareness and behavior change, long term sustainment and culture change, metrics framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
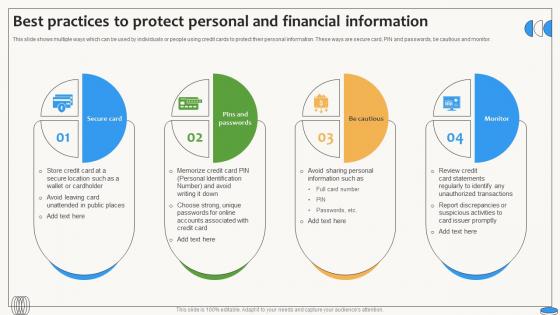
Best Practices To Protect Personal And Financial Swipe Smartly A Practical Guide Fin SS V
This slide shows multiple ways which can be used by individuals or people using credit cards to protect their personal information. These ways are secure card, PIN and passwords, be cautious and monitor. Want to ace your presentation in front of a live audience Our Best Practices To Protect Personal And Financial Swipe Smartly A Practical Guide Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows multiple ways which can be used by individuals or people using credit cards to protect their personal information. These ways are secure card, PIN and passwords, be cautious and monitor.
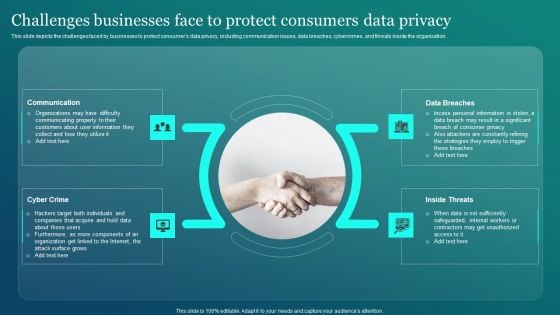
Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
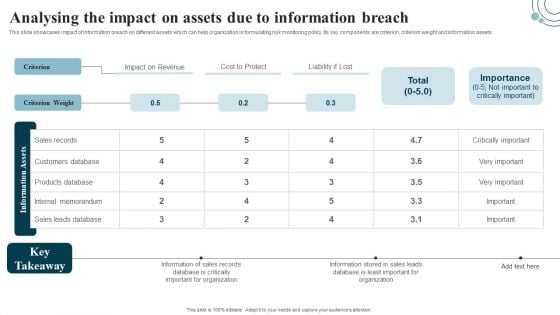
Developing IT Security Strategy Analysing The Impact On Assets Due To Information Breach Sample PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Analysing The Impact On Assets Due To Information Breach Sample PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Make sure to capture your audiences attention in your business displays with our gratis customizable Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Addressing Various Food Processing System Food Security Excellence Ppt Infographic Template Templates PDF
This slide provides information regarding various food handling and processing systems such as drying and curing, fermentation, etc. on various parameters such as longer shelf life, micro organism inactivation, etc. Deliver an awe inspiring pitch with this creative addressing various food processing system food security excellence ppt infographic template templates pdf bundle. Topics like mechanical handling, extrudation, irradiation, fermentation, organisms inactivation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
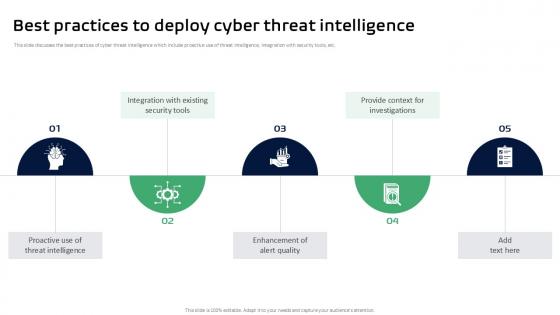
Best Practices To Deploy Cyber Threat Intelligence Ppt Slides
This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Deploy Cyber Threat Intelligence Ppt Slides for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.

Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf
The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc.

Folder And Alarm Clock Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Time Planning PowerPoint Templates because the vision of being the market leader is clear to you. Download our Internet PowerPoint Templates because there are a bucketful of brilliant ideas swirling around within your group. Download our Computer PowerPoint Templates because you can Transmit your thoughts via our slides and proud your team to action. Download and present our Success PowerPoint Templates because the success of your venture depends on the performance of every team member. Present our Business PowerPoint Templates because everybody knows The world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised.Use these PowerPoint slides for presentations relating to Alarm clock and folder, business, time planning, internet, computer, success. The prominent colors used in the PowerPoint template are Red, Yellow, White. Professionals tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Stylish. Use our folder PowerPoint templates and PPT Slides are Fantastic. We assure you our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficient. We assure you our time PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Presenters tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Reminiscent. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides are Cheerful. Analyze growth with our Folder And Alarm Clock Security PowerPoint Templates Ppt Backgrounds For Slides 1212. Download without worries with our money back guaranteee.

Diagram Business Process Beside The Word Future PowerPoint Templates Ppt Backgrounds For Slides
We present our diagram business process beside the word future PowerPoint templates PPT backgrounds for slides.Use our Future PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our People PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Use our Government PowerPoint Templates because You have a driving passion to excel in your field. Our PowerPoint Templates and Slides will prove ideal vehicles for your ideas. Present our Advertising PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there.Use these PowerPoint slides for presentations relating to 3d, better, brighter, candidate, change, choice, consideration, considering, debate, debating, decide, decision, elect, electing, election, figure, future, government, human, illustrated, illustration, man, new, opt, opting, option, person, political, politics, ponder, pondering, revolution, select, selection, think, thinker, versus, vs, wonder, word. The prominent colors used in the PowerPoint template are Blue, Gray, White. Use our diagram business process beside the word future PowerPoint templates PPT backgrounds for slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our candidate PowerPoint templates and PPT Slides will help them to explain complicated concepts. Use our diagram business process beside the word future PowerPoint templates PPT backgrounds for slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. Customers tell us our brighter PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Presenters tell us our diagram business process beside the word future PowerPoint templates PPT backgrounds for slides are visually appealing. PowerPoint presentation experts tell us our candidate PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Our Diagram Business Process Beside The Word Future PowerPoint Templates Ppt Backgrounds For Slides are designed by an avant-garde team. They are always abreast of the state of the art.
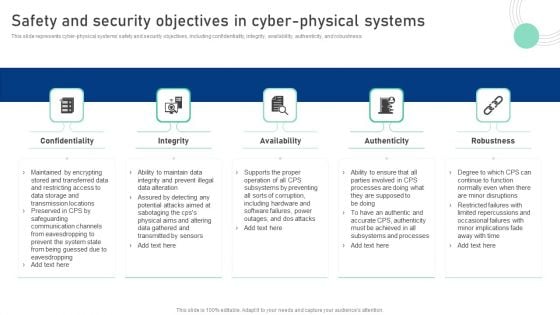
Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF
This slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present like a pro with Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
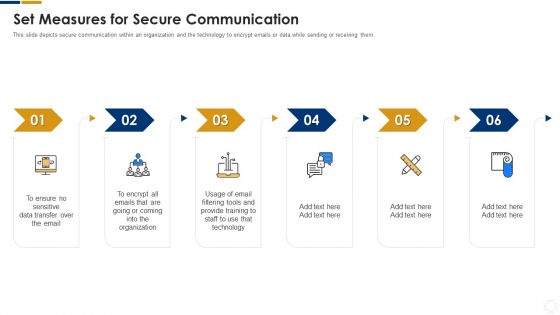
Cybersecurity Set Measures For Secure Communication Ppt Visual Aids Show PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting cybersecurity set measures for secure communication ppt visual aids show pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like organization, technology, email. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
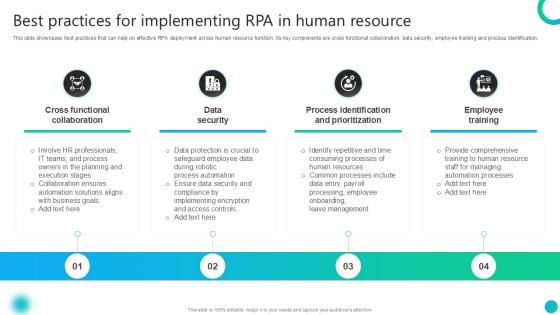
Best Practices For Implementing RPA In Human Resource PPT PowerPoint AI SS V
This slide showcases best practices that can help on effective RPA deployment across human resource function. Its key components are cross functional collaboration, data security, employee training and process identification. Slidegeeks is here to make your presentations a breeze with Best Practices For Implementing RPA In Human Resource PPT PowerPoint AI SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases best practices that can help on effective RPA deployment across human resource function. Its key components are cross functional collaboration, data security, employee training and process identification.

Implementation Best Practices For IaaS Cloud Transforming Business With IaaS Download Pdf
This slide outlines the best practices for Infrastructure as a Service cloud model implementation. The guidelines include developing and testing the strategy, planning a long-term budget, leveraging expertise, and securing everything. There are so many reasons you need a Implementation Best Practices For IaaS Cloud Transforming Business With IaaS Download Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the best practices for Infrastructure as a Service cloud model implementation. The guidelines include developing and testing the strategy, planning a long-term budget, leveraging expertise, and securing everything.
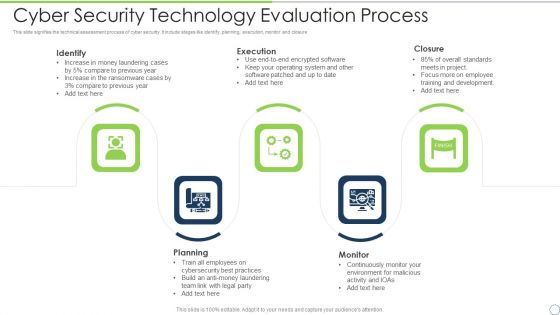
Cyber Security Technology Evaluation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
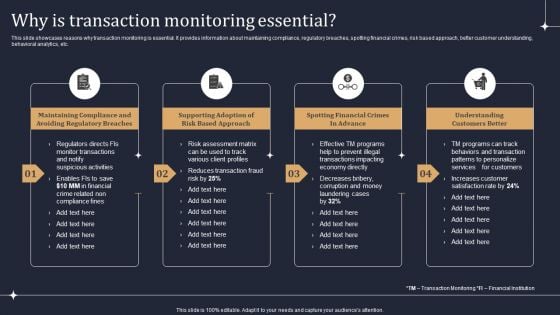
KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Present like a pro with KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
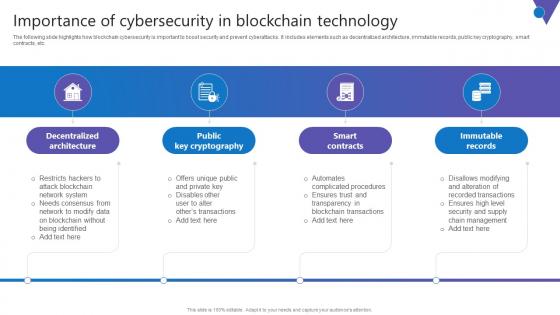
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.

Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF
The following slide will assist an IT company to show the investors or audience a complete view of its competitive landscape based on elements like leaders by category, company, their market capitalization and revenue. There are so many reasons you need a Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc.
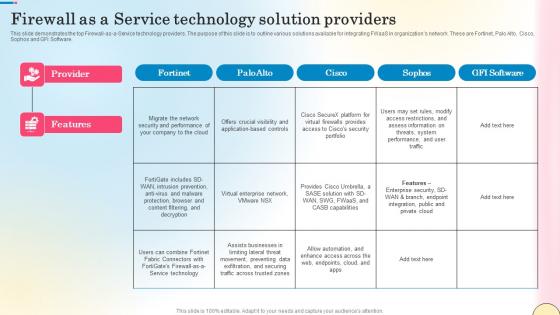
Firewall As A Service Technology Solution Providers Network Security Pictures Pdf
This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software. Make sure to capture your audiences attention in your business displays with our gratis customizable Firewall As A Service Technology Solution Providers Network Security Pictures Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software.
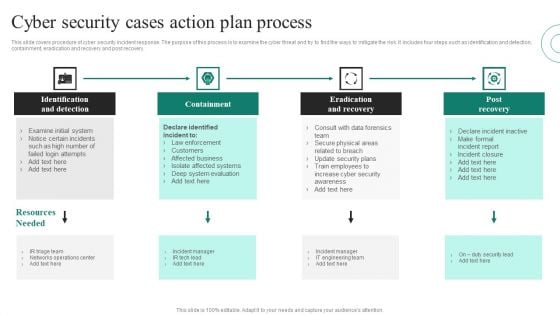
Cyber Security Cases Action Plans Process Ppt PowerPoint Presentation File Show PDF
This slide covers procedure of cyber security incident response. The purpose of this process is to examine the cyber threat and try to find the ways to mitigate the risk. It includes four steps such as identification and detection, containment, eradication and recovery and post recovery. Presenting Cyber Security Cases Action Plans Process Ppt PowerPoint Presentation File Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identification And Detection, Containment, Eradication And Recovery, Post Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
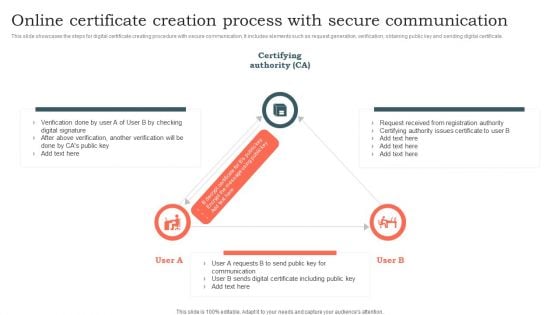
Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF
This slide showcases the steps for digital certificate creating procedure with secure communication. It includes elements such as request generation, verification, obtaining public key and sending digital certificate. Showcasing this set of slides titled Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF. The topics addressed in these templates are Certifying Authority, Key Communication, Digital Certificate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
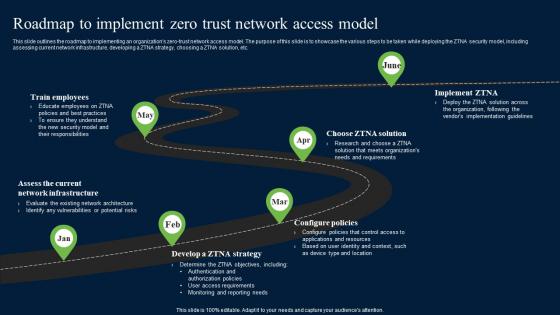
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
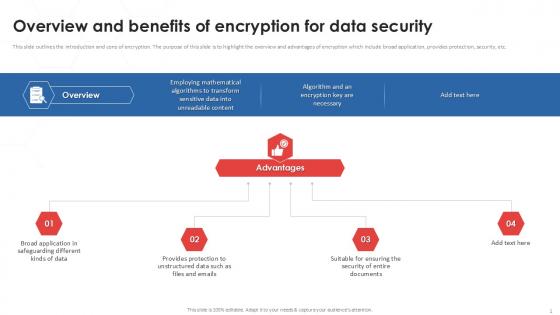
Overview And Benefits Of Tokenization Strategies For Data Security PPT Sample
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Boost your pitch with our creative Overview And Benefits Of Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc.

Cybersecurity Elements Of Electronic Information Security End User Education Ppt Show Brochure PDF
This is a cybersecurity elements of electronic information security end user education ppt show brochure pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, measures, security, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
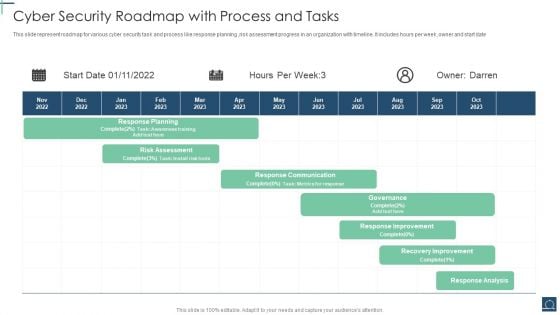
Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF
This slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date. Pitch your topic with ease and precision using this Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF. This layout presents information on Response Planning, Risk Assessment, Response Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Companys Data Safety Recognition Security Awareness Tracking Kpis Culture Mockup PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis culture mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Prepare A Disaster Recovery Plan Ppt Model Aids PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting information security prepare a disaster recovery plan ppt model aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, location, risk assessment report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

House And Alarm Clock Security PowerPoint Templates Ppt Background For Slides 1112
We present our House And Alarm clock Security PowerPoint Templates PPT Background For Slides 1112.Use our Real estate PowerPoint Templates because,Stable ideas are the building blocks of a sucessful structure. Use our Business PowerPoint Templates because,This template can project the path to sucess that you have charted. Use our Money PowerPoint Templates because,You can Enlighten them with your brilliant understanding of mental health. Use our Finance PowerPoint Templates because, You can Refine them all as you take them through the numerous filtering stages of the funnel of your quality control process. Use our Clocks PowerPoint Templates because, This is Aesthetically designed to make a great first impression this template highlights .Use these PowerPoint slides for presentations relating to House and alarm clock, real estate, business, money, finance, clocks. The prominent colors used in the PowerPoint template are Green, White, Blue Get your fill of applause with our House And Alarm Clock Security PowerPoint Templates Ppt Background For Slides 1112. The claps will just continue to come.
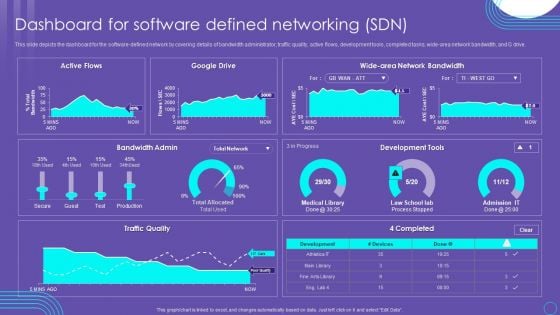
SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF
This slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide area network bandwidth, and G drive. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
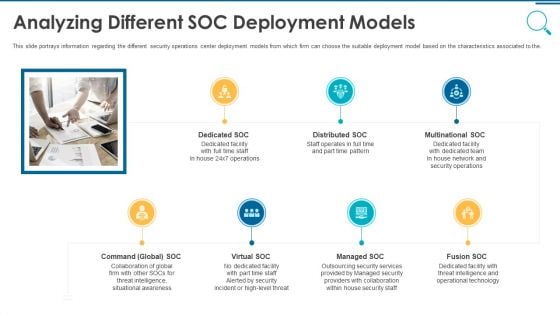
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Critical Measures For Ensuring Business Security Formats PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Table Of Contents Critical Measures For Ensuring Business Security Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.


 Continue with Email
Continue with Email

 Home
Home


































