Computer Security

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Presenting Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Current Value, Risk, Risk Level. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
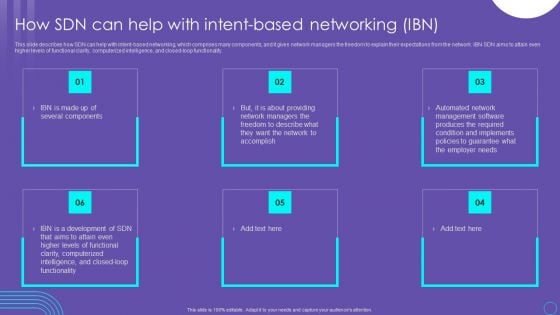
SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF
This slide describes how SDN can help with intent based networking, which comprises many components, and it gives network managers the freedom to explain their expectations from the network. IBN SDN aims to attain even higher levels of functional clarity, computerized intelligence, and closed loop functionality. Explore a selection of the finest SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Distributed Computing Dashboard For Edge Computing Tracking Brochure PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details.Deliver and pitch your topic in the best possible manner with this Distributed Computing Dashboard For Edge Computing Tracking Brochure PDF Use them to share invaluable insights on Device Recommendation, Most Prevalent, Device Recommendation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
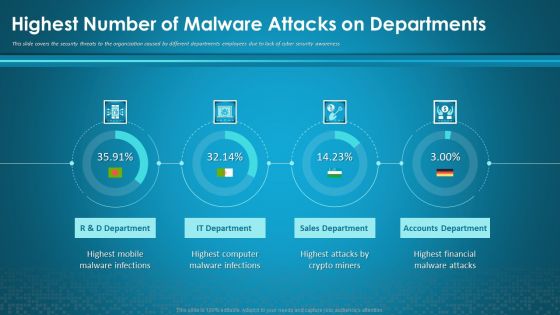
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slide For Network Security Using Firewall As A Service Clipart Pdf
Introducing our well designed Icons Slide For Network Security Using Firewall As A Service Clipart Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Network Security Using Firewall As A Service Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
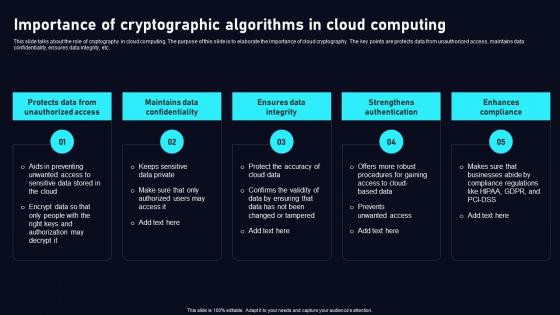
Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
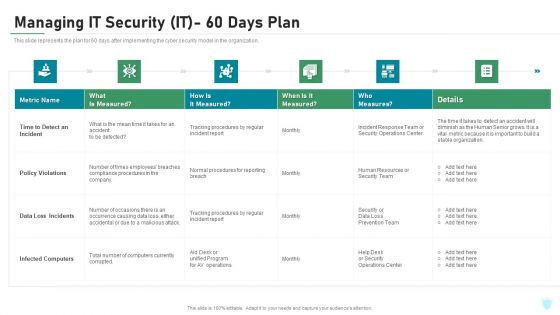
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
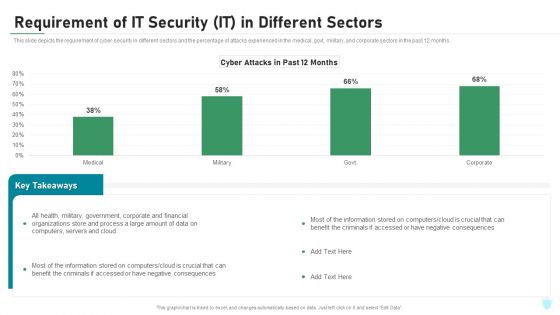
Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Website Programming IT What Is The Cyber Security Ppt PowerPoint Presentation Gallery Example File PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks. This is a website programming it what is the cyber security ppt powerpoint presentation gallery example file pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, digital assets, computers, servers, mobile devices, networks, and resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
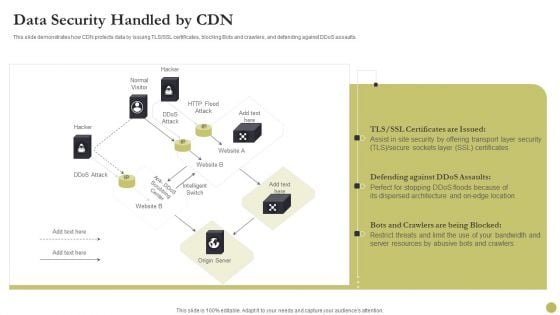
Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
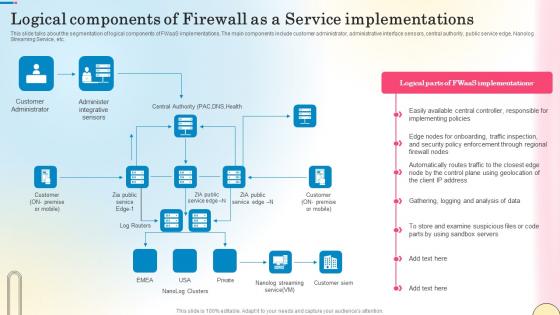
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.
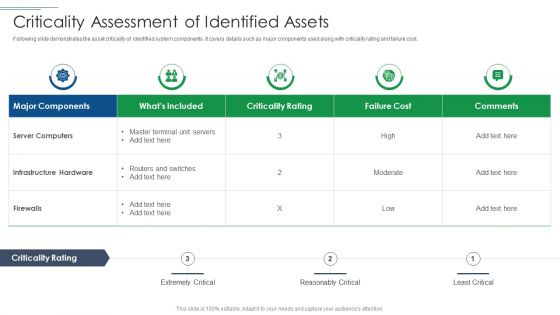
IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF bundle. Topics like Server Computers, Infrastructure Hardware, Failure Cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
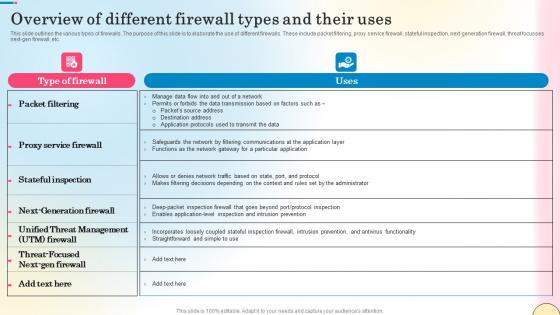
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.
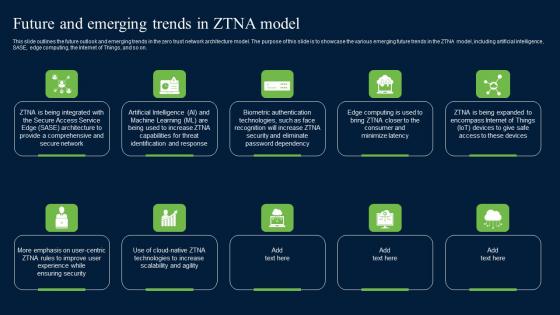
Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.
Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF
Introducing our well designed Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF
Introducing our well designed Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Cloud Computing Service Models IT Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. This is a cloud computing service models it cloud computing in manufacturing industry inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simulation, cyber security, cloud computing, system integration, autonomous robots. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
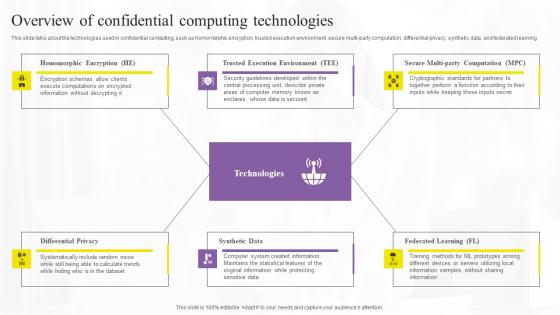
Overview Of Confidential Computing Technologies Elements Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. The Overview Of Confidential Computing Technologies Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
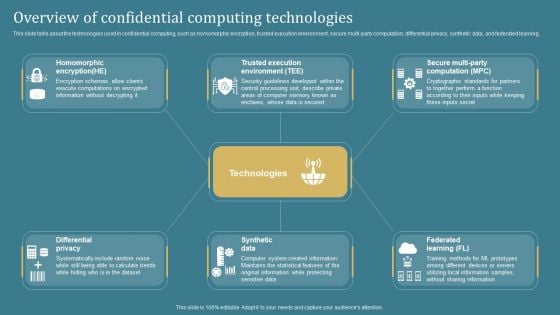
Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Welcome to our selection of the Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
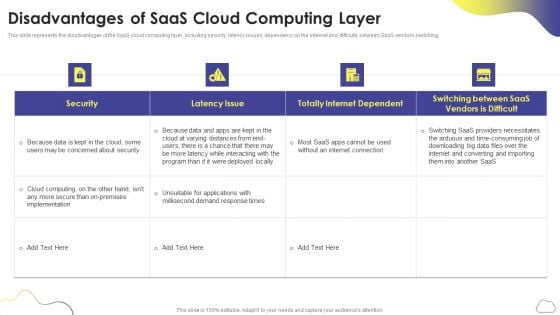
Cloud Computing Services Disadvantages Of Saas Cloud Computing Layer Slides PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. Deliver and pitch your topic in the best possible manner with this Cloud Computing Services Disadvantages Of Saas Cloud Computing Layer Slides PDF. Use them to share invaluable insights on Security, Latency Issue, Totally Internet Dependent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
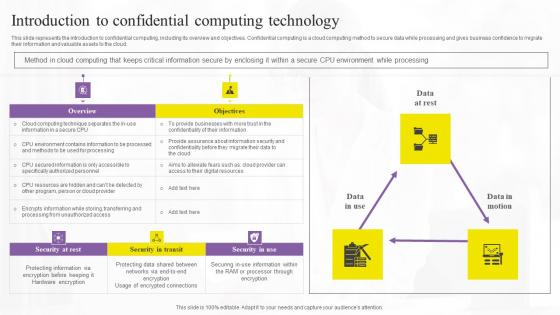
Introduction To Confidential Computing Technology Structure Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Structure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
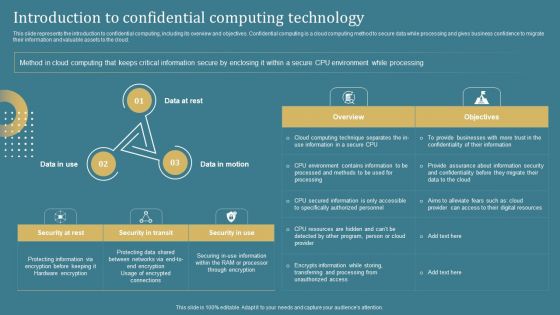
Confidential Computing System Technology Introduction To Confidential Computing Microsoft PDF
Info Sphere Streams Streaming Computing Example Of Ppt
This is a info sphere streams streaming computing example of ppt. This is a four stage process. The stages in this process are security directory server, security access, streaming computing, info sphere streams.
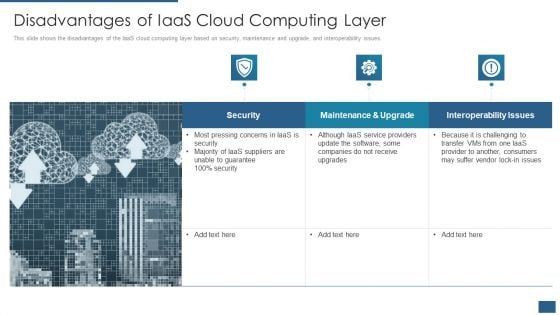
Cloud Computing Service Models IT Disadvantages Of Iaas Cloud Computing Layer Rules PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. Deliver an awe inspiring pitch with this creative cloud computing service models it disadvantages of iaas cloud computing layer rules pdf bundle. Topics like security, maintenance and upgrade, interoperability issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
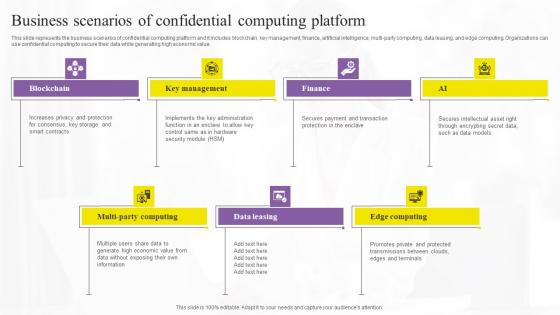
Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
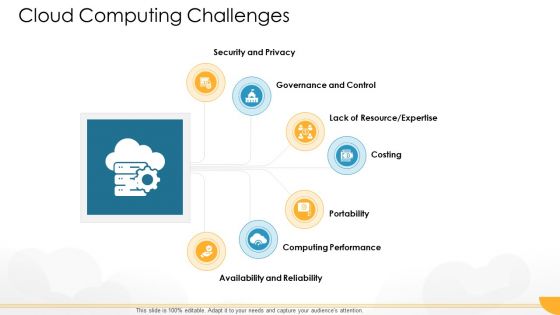
Technology Guide For Serverless Computing Cloud Computing Challenges Infographics PDF
Presenting technology guide for serverless computing cloud computing challenges infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like security and privacy, governance and control, portability, costing, computing performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
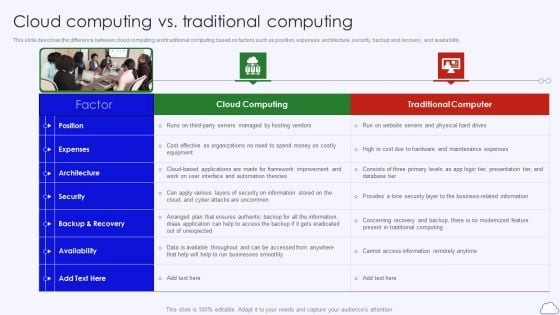
Cloud Computing Vs Traditional Computing Google Cloud Computing System Slides PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability.This is a Cloud Computing Vs Traditional Computing Google Cloud Computing System Slides PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Traditional Computer, Architecture, Availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
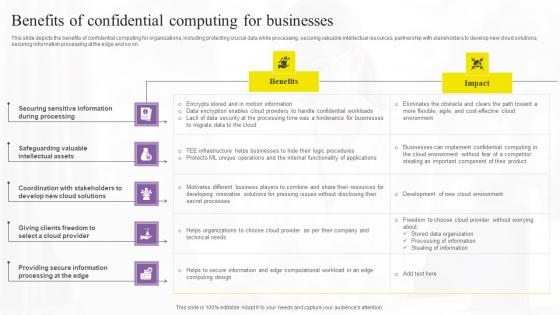
Benefits Of Confidential Computing Confidential Computing Technologies Professional Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing Confidential Computing Technologies Professional Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.

Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
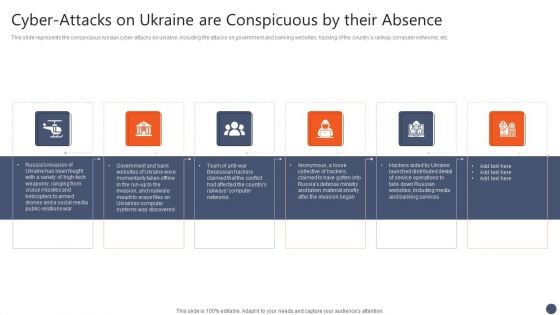
Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
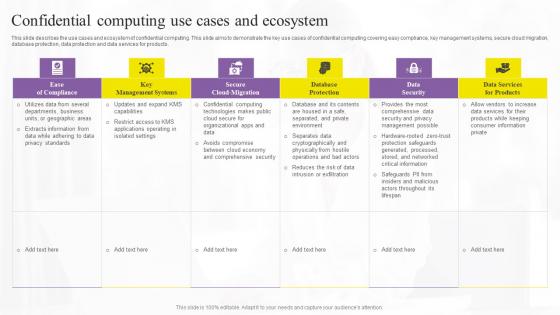
Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Slidegeeks has constructed Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.

Confidential Computing System Technology Benefits Of Confidential Computing Topics PDF
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Want to ace your presentation in front of a live audience Our Confidential Computing System Technology Benefits Of Confidential Computing Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
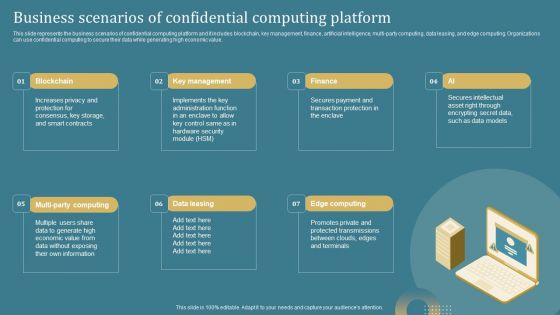
Confidential Computing System Technology Business Scenarios Of Confidential Computing Portrait PDF
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Confidential Computing System Technology Business Scenarios Of Confidential Computing Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Confidential Computing System Technology Business Scenarios Of Confidential Computing Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
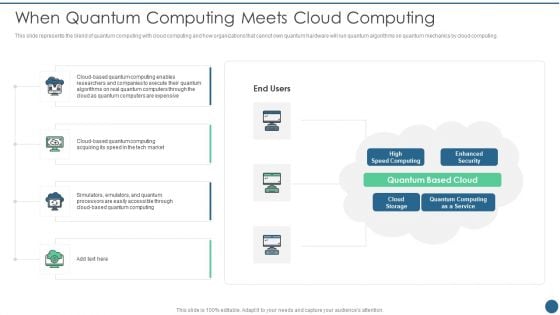
Quantum Key Distribution When Quantum Computing Meets Cloud Computing Summary PDF
This slide represents the blend of quantum computing with cloud computing and how organizations that cannot own quantum hardware will run quantum algorithms on quantum mechanics by cloud computing. Deliver and pitch your topic in the best possible manner with this Quantum Key Distribution When Quantum Computing Meets Cloud Computing Summary PDF Use them to share invaluable insights on Enhanced Security, Quantum Computing, Speed Computing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
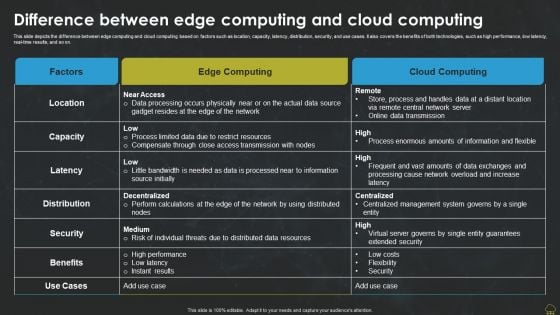
Difference Between Edge Computing And Cloud Computing Professional PDF
This slide depicts the difference between edge computing and cloud computing based on factors such as location, capacity, latency, distribution, security, and use cases. It also covers the benefits of both technologies, such as high performance, low latency, real-time results, and so on. Find a pre designed and impeccable Difference Between Edge Computing And Cloud Computing Professional PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
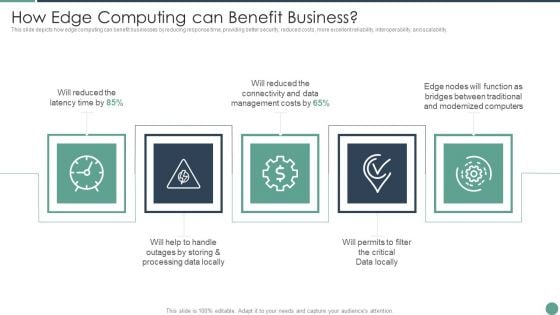
Distributed Computing How Edge Computing Can Benefit Business Elements PDF
This slide depicts how edge computing can benefit businesses by reducing response time, providing better security, reduced costs, more excellent reliability, interoperability, and scalability.This is a Distributed Computing How Edge Computing Can Benefit Business Elements PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Costs, Processing Locally, Data Locally You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
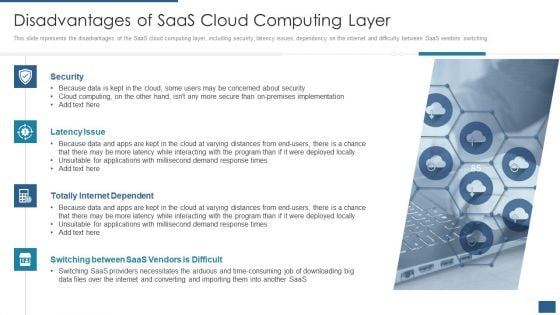
Cloud Computing Service Models IT Disadvantages Of Saas Cloud Computing Layer Elements PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. Presenting cloud computing service models it disadvantages of saas cloud computing layer elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, latency issue, totally internet dependent, switching between saas vendors is difficult. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
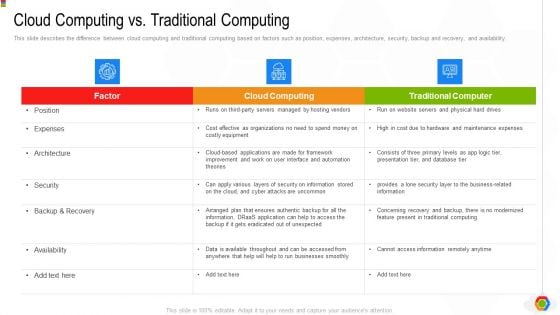
Google Cloud Console IT Cloud Computing Vs Traditional Computing Ppt File Ideas PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability. Deliver an awe inspiring pitch with this creative google cloud console it cloud computing vs traditional computing ppt file ideas pdf bundle. Topics like security, backup and recovery, architecture, expenses, position can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Motel Safety Computers Operator Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name motel safety computers operator ppt powerpoint presentation complete deck. The topics discussed in these slides are wireless security, card access, security guard, operator, computers. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
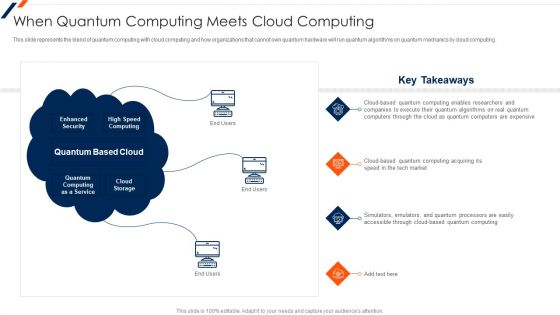
When Quantum Computing Meets Cloud Computing Ppt Model Example File PDF
This is a When Quantum Computing Meets Cloud Computing Ppt Model Example File PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enhanced Security, High Speed Computing, Quantum Based Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
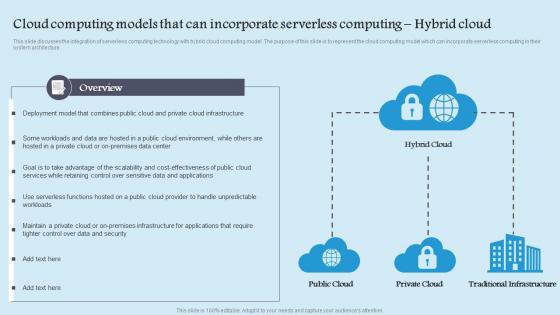
Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf
This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture. This Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture.

Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Maintenance And Upgrade, Security, Interoperability Issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computerized Framework For Cloud Management Topics PDF
This slide shows the automation architecture for cloud management which covers cloud portal, orchestration, tracking resources, automated provisioning, control panels, network management systems, etc. Pitch your topic with ease and precision using this computerized framework for cloud management topics pdf. This layout presents information on capacity and system management, configuration and asset management, network management systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

A Large Brass Key With Laptop PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our A Large Brass Key With Laptop PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will let you Leave a lasting impression to your audiences. They possess an inherent longstanding recall factor. Download our Computer PowerPoint Templates because the world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised. Download and present our Security PowerPoint Templates because this slide shows each path to the smallest detail. Download and present our Technology PowerPoint Templates because this is a wonderful graphics to see the smiles of happiness spread as your audience realizes the value of your words. Use our Future PowerPoint Templates because our creative template will lay down your views.Use these PowerPoint slides for presentations relating to Computer security concept, internet, computer, security, technology, future. The prominent colors used in the PowerPoint template are Blue, Black, Gray. You can be sure our A Large Brass Key With Laptop PowerPoint Templates PPT Backgrounds For Slides 1212 are Appealing. You can be sure our internet PowerPoint templates and PPT Slides are Radiant. The feedback we get is that our A Large Brass Key With Laptop PowerPoint Templates PPT Backgrounds For Slides 1212 are Tranquil. People tell us our concept PowerPoint templates and PPT Slides are Clever. Customers tell us our A Large Brass Key With Laptop PowerPoint Templates PPT Backgrounds For Slides 1212 are Precious. Customers tell us our technology PowerPoint templates and PPT Slides are Breathtaking. Arrive at your desired destination. Complete the distance with our A Large Brass Key With Laptop PowerPoint Templates Ppt Backgrounds For Slides 1212.

Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012
Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012-Microsoft Powerpoint Templates and Background with laptop and umbrella-Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Laptop and umbrella, computer, technology, security, internet, business Make interesting presentations no matter what the topic with our Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012. Dont waste time struggling with PowerPoint. Let us do it for you.
Dashboard For Concurrent Computing Tracking Ppt Visual Aids Ideas PDF
picts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver an awe inspiring pitch with this creative dashboard for concurrent computing tracking ppt visual aids ideas pdf bundle. Topics like dashboard for concurrent computing tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
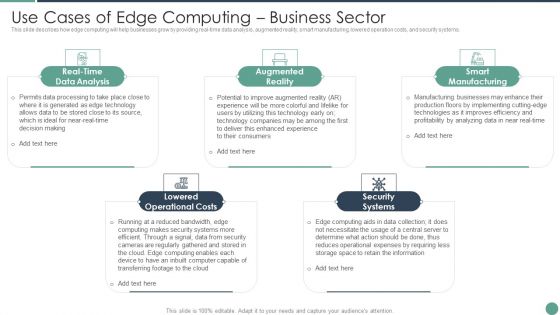
Distributed Computing Use Cases Of Edge Computing Business Sector Themes PDF
This slide describes how edge computing will help businesses grow by providing real-time data analysis, augmented reality, smart manufacturing, lowered operation costs, and security systems.This is a Distributed Computing Use Cases Of Edge Computing Business Sector Themes PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Augmented Reality, Smart Manufacturing, Security Systems You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secured Laptop And Information Technology PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secured Laptop And Information Technology PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind. Present our Finance PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Download our Future PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Download our Computer PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Internet PowerPoint Templates because It can Bubble and burst with your ideas.Use these PowerPoint slides for presentations relating to Computer security concept, security, finance, future, internet, computer. The prominent colors used in the PowerPoint template are Yellow, Black, Gray. Customers tell us our Secured Laptop And Information Technology PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. You can be sure our Secured Laptop And Information Technology PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Customers tell us our security PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Professionals tell us our Secured Laptop And Information Technology PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. You can be sure our PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. Speak confidently with our Secured Laptop And Information Technology PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.
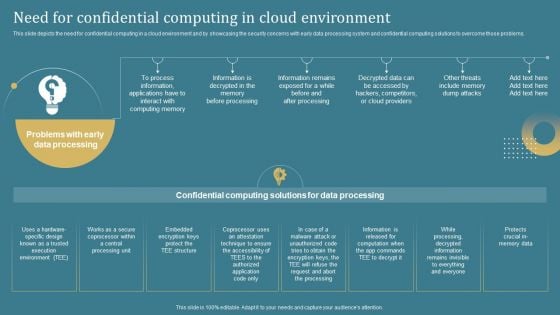
Confidential Computing System Technology Need For Confidential Computing In Cloud Guidelines PDF
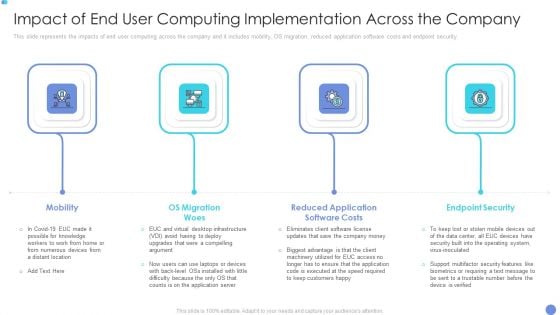
Customer Mesh Computing IT Impact Of End User Computing Implementation Across The Company Pictures PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security. Presenting customer mesh computing it impact of end user computing implementation across the company pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mobility, os migration woes, endpoint security. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
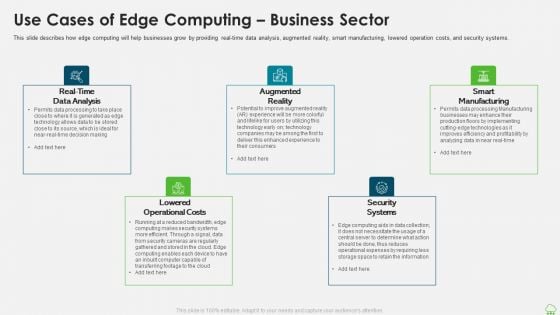
Distributed Computing IT Use Cases Of Edge Computing Business Sector Template PDF
This slide describes how edge computing will help businesses grow by providing real-time data analysis, augmented reality, smart manufacturing, lowered operation costs, and security systems. This is a distributed computing it use cases of edge computing business sector template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data analysis, smart manufacturing, lowered operational costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Advantages Of Mobile Cloud Computing In Application Areas Of Mobile Cloud Computing
The given slide outlines the potential benefits of using mobile cloud computing in healthcare to streamline concurrent processes. It includes collaboration, security, cost-effectiveness, speed, and scalability. Boost your pitch with our creative Advantages Of Mobile Cloud Computing In Application Areas Of Mobile Cloud Computing. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The given slide outlines the potential benefits of using mobile cloud computing in healthcare to streamline concurrent processes. It includes collaboration, security, cost-effectiveness, speed, and scalability

Secure Your Pc From Viruses PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Your PC From Viruses PowerPoint Templates PPT Backgrounds For Slides 0413.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download our Technology PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Use our Services PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Download our Marketing PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity.Use these PowerPoint slides for presentations relating to Computer security concept from viruses, security, technology, services, business, marketing. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. Formalize plans with our Secure Your Pc From Viruses PowerPoint Templates Ppt Backgrounds For Slides 0413. Download without worries with our money back guaranteee.

Protection Of Information Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Protection Of Information Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Use our Services PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team.Use these PowerPoint slides for presentations relating to Laptop with lock and key. Computer security, computer, technology, security, business, services. The prominent colors used in the PowerPoint template are Yellow, Gray, White. Enthral your listeners with your suggestions. Keep them clued in with our Protection Of Information Technology PowerPoint Templates Ppt Backgrounds For Slides 0213.
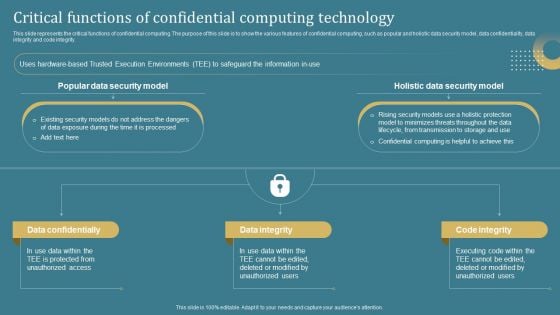
Confidential Computing System Technology Critical Functions Of Confidential Computing Template PDF
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Slidegeeks has constructed Confidential Computing System Technology Critical Functions Of Confidential Computing Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Quantum Computing For Everyone IT Applications Of Quantum Computing Infographics PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. Presenting quantum computing for everyone it applications of quantum computing infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like artificial intelligence and machine learning, drug design and development, financial modelling, weather forecasting, logistics optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Cyber Intelligent Computing System Infographics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Cyber Intelligent Computing System Infographics PDF bundle. Topics like Systems Development, Systems Implementation, Security Strategy Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































