Computer Virus

Impact Of IT Cloud Services In Banking Industry Brochure PDF
This slide represents the cloud computing assistance use in banking sector. It includes stages like enhance security, reduced data, increase customer insight and risk safety. Persuade your audience using this impact of it cloud services in banking industry brochure pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including enhance security, data protection, increase customer insight, risk safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
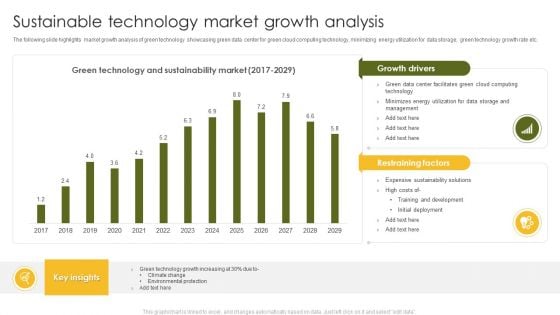
Sustainable Technology Market Growth Analysis Ppt Outline Slide Download PDF
The following slide highlights market growth analysis of green technology showcasing green data center for green cloud computing technology, minimizing energy utilization for data storage, green technology growth rate etc. Showcasing this set of slides titled Sustainable Technology Market Growth Analysis Ppt Outline Slide Download PDF. The topics addressed in these templates are Climate Change, Environmental Protection, Green Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
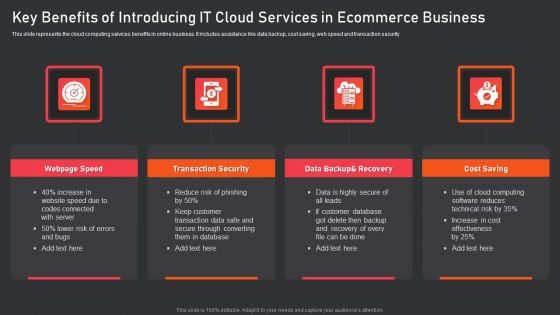
Key Benefits Of Introducing IT Cloud Services In Ecommerce Business Introduction PDF
This slide represents the cloud computing services benefits in online business. It includes assistance like data backup, cost saving, web speed and transaction security. Presenting key benefits of introducing it cloud services in ecommerce business introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including webpage speed, transaction security, data backup and recovery, cost saving. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Technology Adoption In Banking Industry Case Competition Emerging Technological Infographics PDF
This slide shows the latest technological trends which should be adopted by the ABC Bank which includes cyber security, upgraded ATMs, Chatbot, Artificial Intelligence etc.Presenting Digital Technology Adoption In Banking Industry Case Competition Emerging Technological Infographics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Cyber Security, Artificial Intelligence, Cloud Computing In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Impact Of Cloud Services In Banking Sector Background PDF
This slide exhibits benefits of adopting cloud computing in banking institutions that increase operational efficiency. It includes points data security, infrastructure cost, operational efficiency, business continuity and Green IT.Presenting Impact Of Cloud Services In Banking Sector Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Security, Infrastructure Cost, Operational Efficiency. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
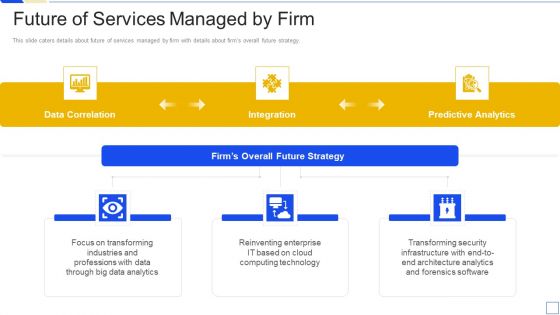
Service Marketing Fundraising Future Of Services Managed By Firm Background PDF
This slide caters details about future of services managed by firm with details about firms overall future strategy. This is a service marketing fundraising future of services managed by firm background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data analytics, cloud computing technology, transforming security infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
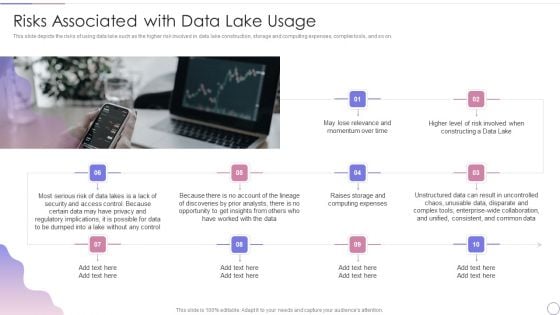
Data Lake Architecture Future Of Data Analysis Risks Associated With Data Lake Usage Rules PDF
This slide depicts the risks of using data lake such as the higher risk involved in data lake construction, storage and computing expenses, complex tools, and so on.This is a Data Lake Architecture Future Of Data Analysis Risks Associated With Data Lake Usage Rules PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Regulatory Implications, Security And Access, Enterprise Collaboration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
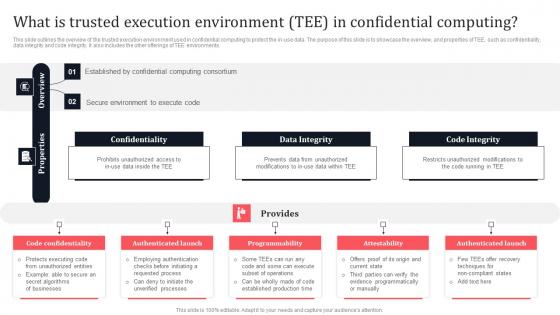
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
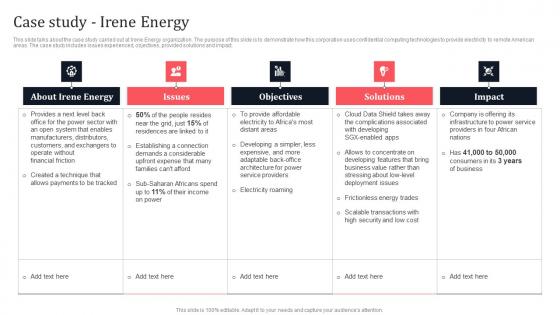
Case Study Irene Energy Secure Multi Party Sample Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Create an editable Case Study Irene Energy Secure Multi Party Sample Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Case Study Irene Energy Secure Multi Party Sample Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
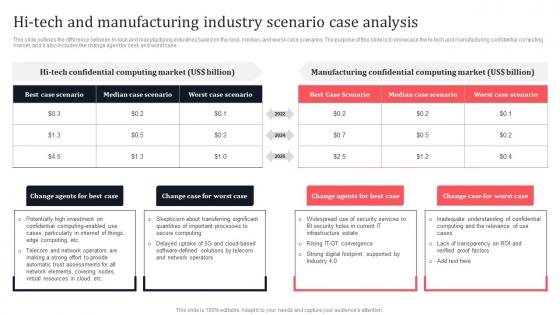
Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Presenting this PowerPoint presentation, titled Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
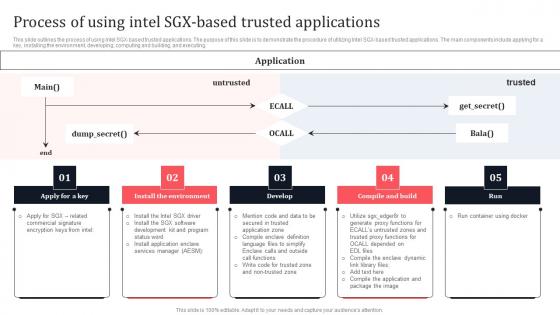
Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Present like a pro with Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
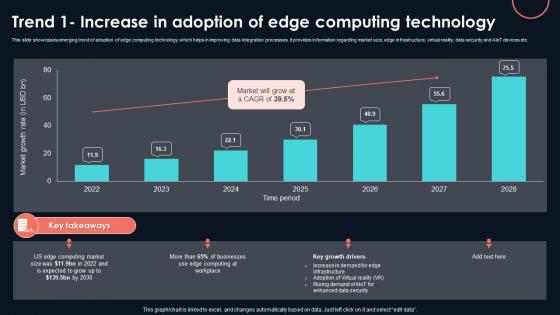
Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V. This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc.

Unified Security Management Ppt Template Example Of Ppt Presentation
This is a unified security management ppt template example of ppt presentation. This is a four stage process. The stages in this process are assess the network, find threats, data loss prevention, gateway anti virus.

Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V
This slide presents the emerging trends and future applications of IoT. It incorporates edge computing in IoT, AI, and ML in IoT data analysis, IoT in smart cities, and Blockchain technology for security and privacy. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V. This slide presents the emerging trends and future applications of IoT. It incorporates edge computing in IoT, AI, and ML in IoT data analysis, IoT in smart cities, and Blockchain technology for security and privacy.
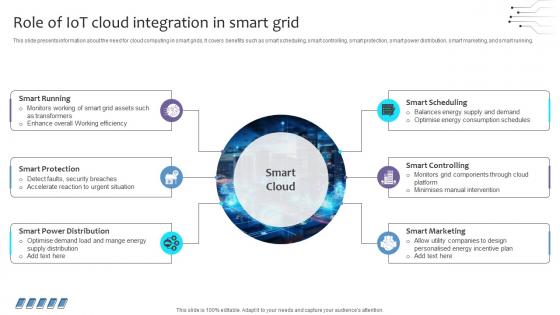
Empowering The Future Role Of IoT Cloud Integration In Smart Grid IoT SS V
This slide presents information about the need for cloud computing in smart grids. It covers benefits such as smart scheduling, smart controlling, smart protection, smart power distribution, smart marketing, and smart running. If you are looking for a format to display your unique thoughts, then the professionally designed Empowering The Future Role Of IoT Cloud Integration In Smart Grid IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Empowering The Future Role Of IoT Cloud Integration In Smart Grid IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents information about the need for cloud computing in smart grids. It covers benefits such as smart scheduling, smart controlling, smart protection, smart power distribution, smart marketing, and smart running.

Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck
This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches.
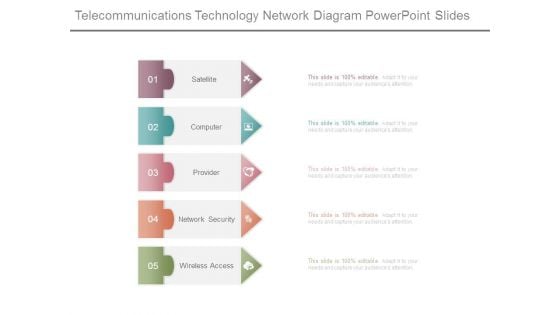
Telecommunications Technology Network Diagram Powerpoint Slides
This is a telecommunications technology network diagram powerpoint slides. This is a five stage process. The stages in this process are satellite, computer, provider, network security, wireless access.

Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb
Introducing our well designed Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Security App Two Factor Authentication. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
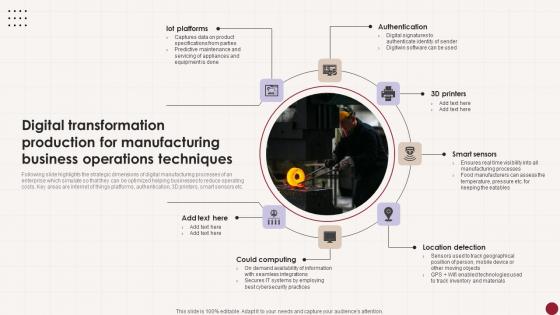
Digital Transformation Production For Manufacturing Business Operations Techniques Designs Pdf
Following slide highlights the strategic dimensions of digital manufacturing processes of an enterprise which simulate so that they can be optimized helping businesses to reduce operating costs. Key areas are internet of things platforms, authentication, 3D printers, smart sensors etc. Showcasing this set of slides titled Digital Transformation Production For Manufacturing Business Operations Techniques Designs Pdf The topics addressed in these templates are Authentication, Smart Sensors, Location Detection, Could Computing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide highlights the strategic dimensions of digital manufacturing processes of an enterprise which simulate so that they can be optimized helping businesses to reduce operating costs. Key areas are internet of things platforms, authentication, 3D printers, smart sensors etc.
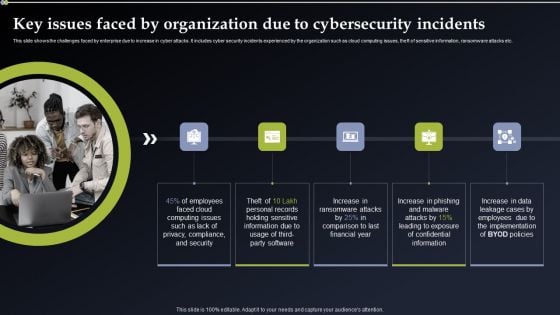
Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
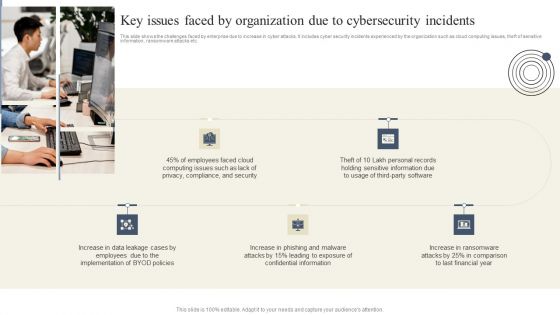
Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Create an editable Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
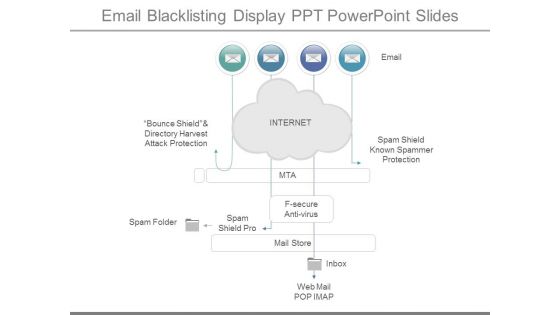
Email Blacklisting Display Ppt Powerpoint Slides
This is a email blacklisting display ppt powerpoint slides. This is a one stage process. The stages in this process are email, spam shield known spammer protection, internet, bounce shield and directory harvest attack protection, mta, spam folder, spam shield pro, f secure anti virus, mail store, inbox, web mail pop imap.
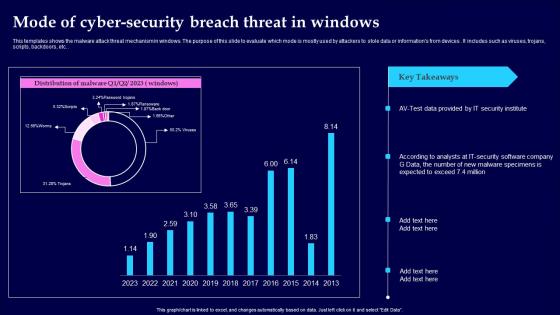
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.

Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.

Types Of Website Security Threats And Vulnerabilities Step By Step Guide Structure PDF
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. There are so many reasons you need a Types Of Website Security Threats And Vulnerabilities Step By Step Guide Structure PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.
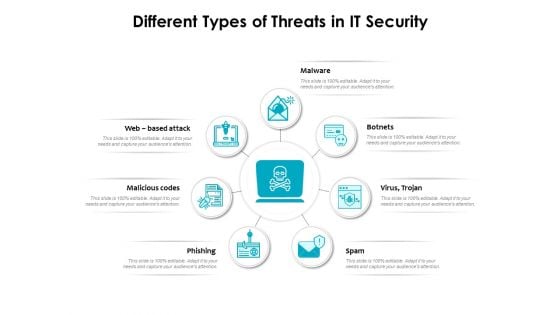
Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Initiatives Taken To Protect Identity Fraud Professional PDF
This slide showcases scenarios in which different strategies can be undertaken to prevent identity fraud. This template focuses on reducing tendency of crime related to identity theft. It includes information related to protecting banks, computer, etc. Showcasing this set of slides titled Initiatives Taken To Protect Identity Fraud Professional PDF. The topics addressed in these templates are Protect Phone, Protect Bank Accounts, Protect Computer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

COVID 19 Mitigating Impact On High Tech Industry Risk Of Civil Unrest During COVID 19 Ideas PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry risk of civil unrest during covid 19 ideas pdf. This is a five stage process. The stages in this process are risk harassment, measures to combat virus, security forces, anti government sentiment, protesting coronavirus. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
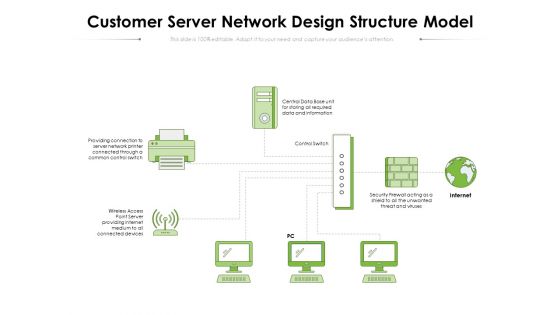
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Password Protection Programs In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Password Protection Programs In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Password Protection Programs that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Password Protection Programs In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Best Way Protect Passwords In Powerpoint And Google Slides Cpb
Introducing our well designed Best Way Protect Passwords In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Way Protect Passwords. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Best Way Protect Passwords In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Authentication In Application Security For Data Protection Application Security Testing
This slide discusses about the overview of authentication in application security and the various elements of MFA. Present like a pro with Authentication In Application Security For Data Protection Application Security Testing. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses about the overview of authentication in application security and the various elements of MFA.
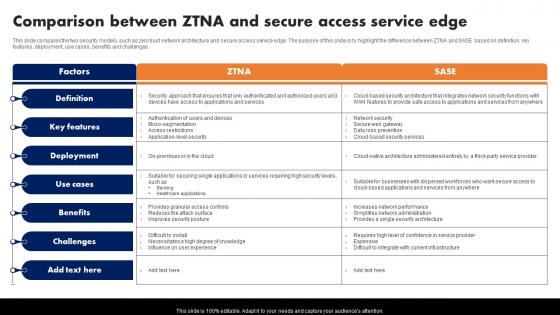
Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
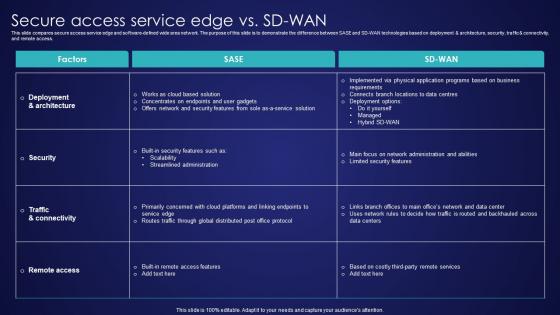
Secure Access Service Edge Vs SD Wan Wide Area Network Services Structure Pdf
This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Take your projects to the next level with our ultimate collection of Secure Access Service Edge Vs SD Wan Wide Area Network Services Structure Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access.
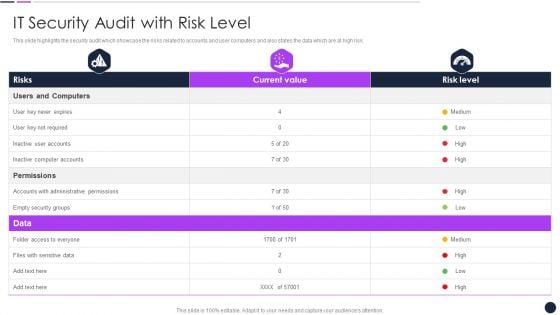
Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF
Deliver an awe inspiring pitch with this creative Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF bundle. Topics like Inactive Computer, Administrative Permissions, Security Groups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
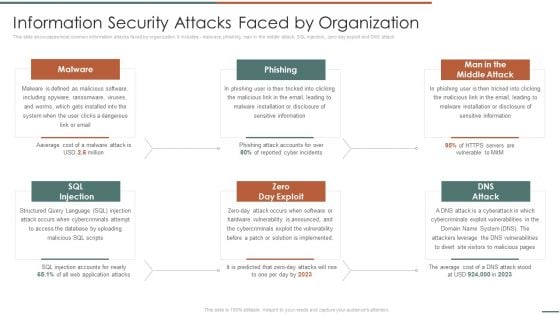
Information Security Risk Evaluation Information Security Attacks Faced By Organization Download PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack.Presenting Information Security Risk Evaluation Information Security Attacks Faced By Organization Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Malicious Software, Including Spyware, Ransomware Viruses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Feedback Star Rating Vector Icon Ppt PowerPoint Presentation Show Visual Aids
Presenting this set of slides with name feedback star rating vector icon ppt powerpoint presentation show visual aids. The topics discussed in these slides are finger, technology, computer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Illustration Of Colorful Diverging 8 Arrows Ppt Cycle Motion Chart PowerPoint Slides
We present our illustration of colorful diverging 8 arrows ppt Cycle Motion Chart PowerPoint Slides.Present our Shapes PowerPoint Templates because you can Ring them out loud with your brilliant ideas. Present our Flow charts PowerPoint Templates because it outlines the process with this innovative graphic to authenticate your plan of achieving the goal of added value/profit. Use our Process and Flows PowerPoint Templates because this diagram provides range of options to garner your interest. Present our Arrows PowerPoint Templates because this an appropriate template to get your ideas across to your target audience. Use our Success PowerPoint Templates because in our day to day pursuits we tend to overlook the fundamentals.Use these PowerPoint slides for presentations relating to Arrow, business, circle, circular, color,colorful, concept, cycle, eco, ecologic,graphic, green, icon, illustration, light,multicolor, presentation, process,rainbow, recycle, recycling, repeat,repetitive, round, spectrum, symbol,special,speech, strategy . The prominent colors used in the PowerPoint template are Purple, Gray, Black. People tell us our illustration of colorful diverging 8 arrows ppt Cycle Motion Chart PowerPoint Slides are Efficient. Customers tell us our colorful PowerPoint templates and PPT Slides are Magnificent. Professionals tell us our illustration of colorful diverging 8 arrows ppt Cycle Motion Chart PowerPoint Slides effectively help you save your valuable time. Presenters tell us our cycle PowerPoint templates and PPT Slides are Versatile. Use our illustration of colorful diverging 8 arrows ppt Cycle Motion Chart PowerPoint Slides are topically designed to provide an attractive backdrop to any subject. Presenters tell us our concept PowerPoint templates and PPT Slides are Beautiful. Compute growth with our Illustration Of Colorful Diverging 8 Arrows Ppt Cycle Motion Chart PowerPoint Slides. Download without worries with our money back guaranteee.
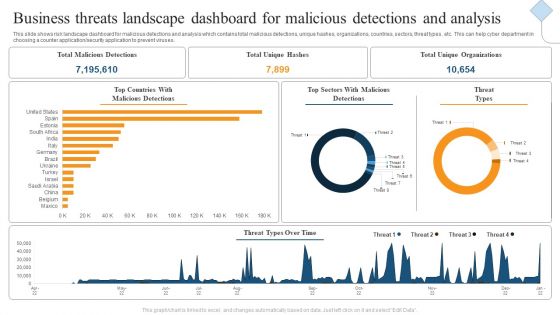
Business Threats Landscape Dashboard For Malicious Detections And Analysis Ppt Gallery Show PDF
This slide shows risk landscape dashboard for malicious detections and analysis which contains total malicious detections, unique hashes, organizations, countries, sectors, threat types, etc. This can help cyber department in choosing a counter application or security application to prevent viruses. Showcasing this set of slides titled Business Threats Landscape Dashboard For Malicious Detections And Analysis Ppt Gallery Show PDF. The topics addressed in these templates are Total Malicious Detections, Total Unique Hashes, Total Unique Organizations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Password Protection Information Security Icon Ppt Powerpoint Presentation Visual Aids Portfolio
This is a password protection information security icon ppt powerpoint presentation visual aids portfolio. This is a three stage process. The stages in this process are password, access approval, authentication icon.
Password Protect In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Protect In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Protect. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Protect In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Password Protect Gmail Attachment In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Protect Gmail Attachment In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Manager Android Windows. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Protect Gmail Attachment In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
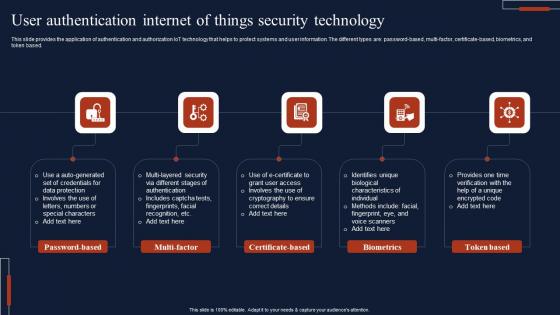
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.
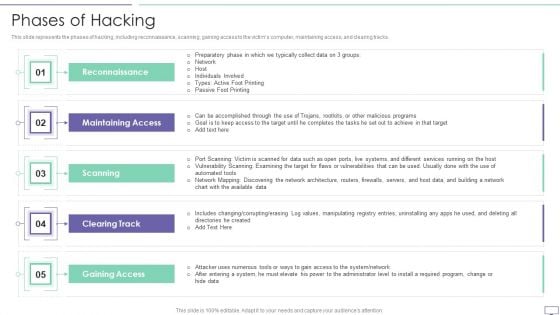
IT Security Hacker Phases Of Hacking Topics PDF
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Phases Of Hacking Topics PDF. Use them to share invaluable insights on Maintaining Access, Reconnaissance, Gaining Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Imessage Login Android In Powerpoint And Google Slides Cpb
Introducing our well designed Imessage Login Android In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Imessage Login Android. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Imessage Login Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
User Login Report In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled User Login Report In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits User Login Report that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our User Login Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
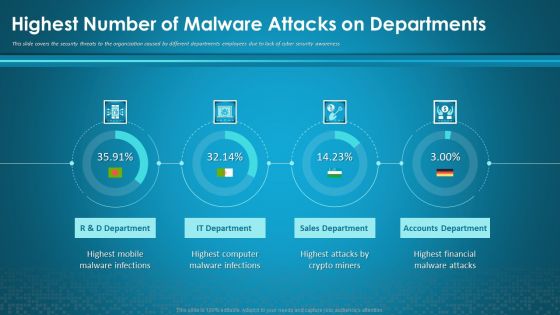
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Authentication In Application Security PPT Example
Tablet With Login Username And Password Powerpoint Template
This power point template contains graphics of tablet with login page. Download this diagram slide to display internet and security concepts. Make outstanding presentation by using this creative diagram.

Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF
This slide showcases cyber security risk landscape which can benefit various users around the world to be proactive of potential outcomes. It includes information about target, purpose, possible outcome, social media phishing, system viruses, configuration and passcodes, allocated service denial, hacking devices and structured query language. Persuade your audience using this Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Landscape, Target, Purpose, Possible Outcome. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Web Application Login Screen In Powerpoint And Google Slides Cpb
Introducing our well designed Web Application Login Screen In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Web Application Login Screen. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Web Application Login Screen In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Password Management Best Password Application In Powerpoint And Google Slides Cpb
Introducing our well-designed Secure Password Management Best Password Application In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Password Management Best Password Application. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Password Management Best Password Application In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Checklist To Ensure Strong Authentication Icons Pdf
Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Showcasing this set of slides titled Cyber Security Checklist To Ensure Strong Authentication Icons Pdf. The topics addressed in these templates are Cyber Security Checklist, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security.
Secure Password Manager Android In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Password Manager Android In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Password Manager Android that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Password Manager Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0.

Difference Between Authentication And Authorization Application Security Testing
This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. This modern and well-arranged Difference Between Authentication And Authorization Application Security Testing provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc.


 Continue with Email
Continue with Email

 Home
Home


































