Construction Safety Plan
Six Months Business Process Vertical Timeline Ppt Model Design Inspiration PDF
Presenting six months business process vertical timeline ppt model design inspiration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including conduct business process based security valuation, integrate modelling of business processes and security, define integration strategy plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
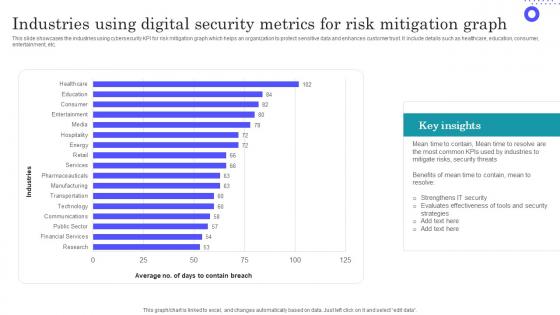
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.

Computer Data Storage Business Strategy PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Computer Data Storage Business Strategy PowerPoint Templates PPT Backgrounds For Slides 0313.Download our Technology PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Communication PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Use our Success PowerPoint Templates because These PowerPoint Templates and Slides will give the updraft to your ideas. See them soar to great heights with ease. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts.Use these PowerPoint slides for presentations relating to one computer server with a shape, concept of remote data storage, business, communication, technology, security, success. The prominent colors used in the PowerPoint template are Blue, White, Black. Bet a quid on our Computer Data Storage Business Strategy PowerPoint Templates Ppt Backgrounds For Slides 0313. You will end up a 49er.

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.
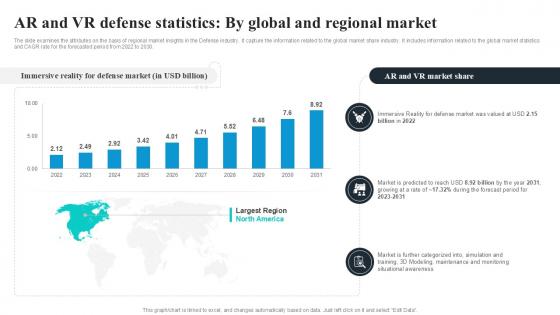
AR And VR Defense Statistics By Global Security Industry PPT Slide IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the global market share industry. It includes information related to the global market statistics and CAGR rate for the forecasted period from 2022 to 2030. Create an editable AR And VR Defense Statistics By Global Security Industry PPT Slide IR SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. AR And VR Defense Statistics By Global Security Industry PPT Slide IR SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the global market share industry. It includes information related to the global market statistics and CAGR rate for the forecasted period from 2022 to 2030.
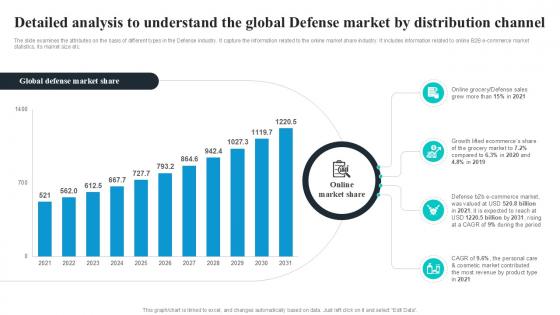
Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to the online market share industry. It includes information related to online B2B e-commerce market statistics, its market size etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V today and make your presentation stand out from the rest The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to the online market share industry. It includes information related to online B2B e-commerce market statistics, its market size etc.
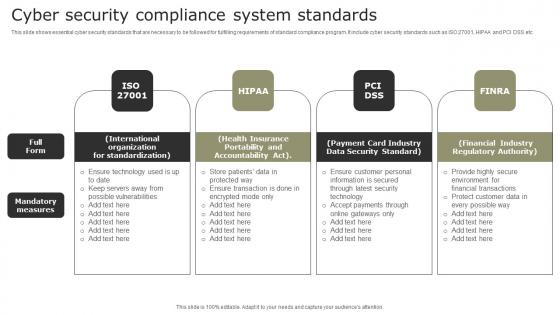
Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc.
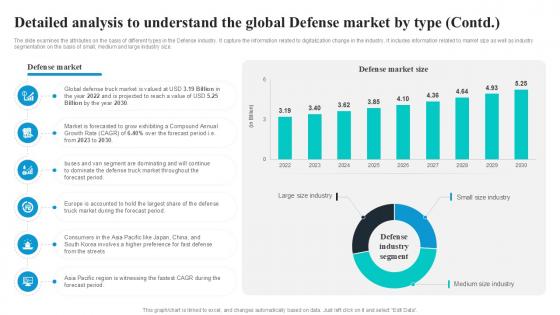
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.

Requirements For Successful Common Data Environment Ppt Infographics Summary PDF
The following slide showcases key requirements to build common data environment. The requirements covered are building information management, data security, data availability and defining roles and responsibilities. Presenting Requirements For Successful Common Data Environment Ppt Infographics Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Building Information Management, Data Availability, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
Icons Slide For Developing Cyber Security Threat Awareness Staff Training Program Information PDF
Introducing our well designed Icons Slide For Developing Cyber Security Threat Awareness Staff Training Program Information PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Developing Information Technology Security Awareness Training Program For Employees Rules PDF
Introducing our well designed Icons Slide For Developing Information Technology Security Awareness Training Program For Employees Rules PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
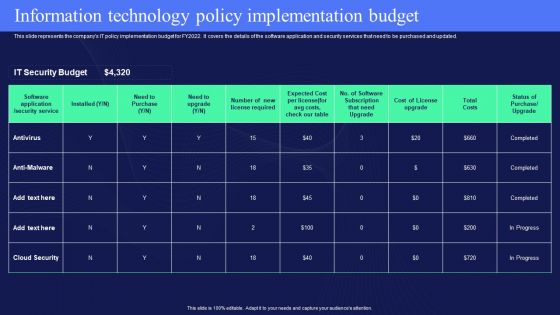
IT Policies And Procedures Information Technology Policy Implementation Budget Template PDF
This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. This modern and well-arranged IT Policies And Procedures Information Technology Policy Implementation Budget Template PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
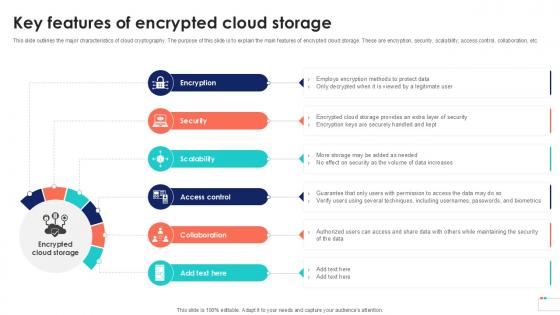
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.
Home Appliances Producer Seed Competitive Landscape For Major Consumers Electronics Players Existing Icons PDF
Deliver an awe inspiring pitch with this creative home appliances producer seed competitive landscape for major consumers electronics players existing icons pdf bundle. Topics like scalability, security, system configurator can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
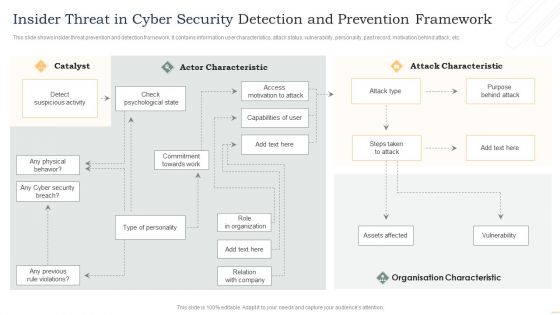
Insider Threat In Cyber Security Detection And Prevention Framework Information PDF
This slide shows insider threat prevention and detection framework. It contains information user characteristics, attack status, vulnerability, personality, past record, motivation behind attack, etc. Presenting Insider Threat In Cyber Security Detection And Prevention Framework Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Actor Characteristic, Attack Characteristic, Organisation Characteristic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Desktop Security Management Security Framework In Cloud Computing Demonstration PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a desktop security management security framework in cloud computing demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, detect, respond, recover, identify. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Framework Car Dashboard Indicator PowerPoint Presentation
Define the concept of target achievement and success with this exclusive PPT slide. To display this concept we have used graphic of target board and dart. This PPT slide also defines the concept of bull's eye condition. Use this PPT for business and marketing target related presentations.
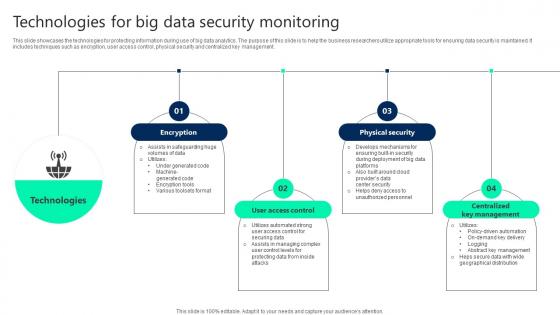
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.

Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
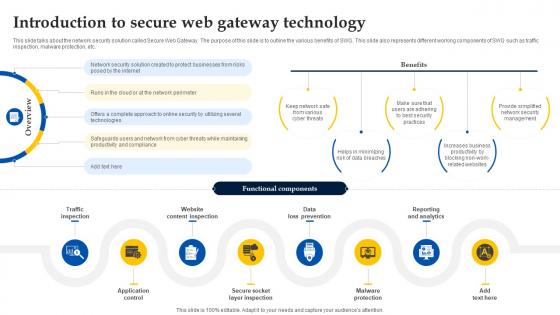
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
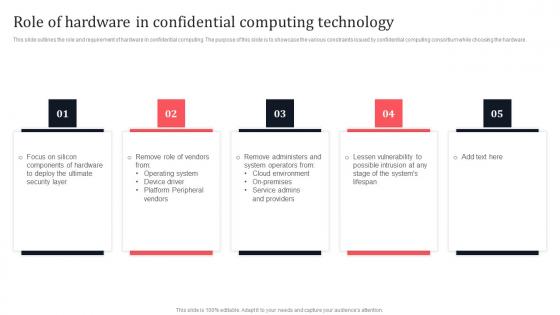
Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf today and make your presentation stand out from the rest. This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.

Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.
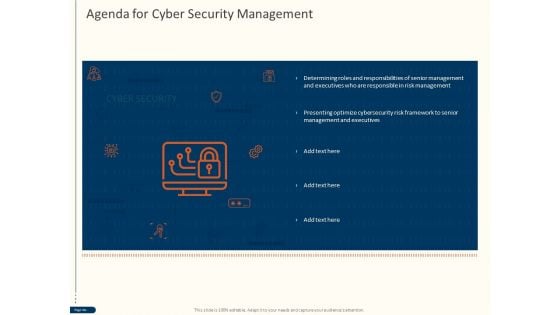
Cyber Security For Your Organization Agenda For Cyber Security Management Ppt Tips PDF
Presenting this set of slides with name cyber security for your organization agenda for cyber security management ppt tips pdf. This is a one stage process. The stages in this process are roles and responsibilities, management, executives responsible, risk management, optimize cybersecurity risk framework, executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
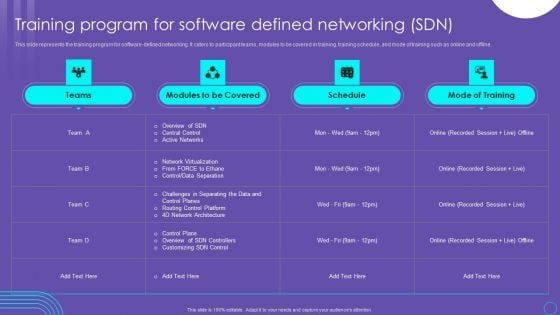
SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF
This slide represents the training program for software defined networking. It caters to participant teams, modules to be covered in training, training schedule, and mode of training such as online and offline. There are so many reasons you need a SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
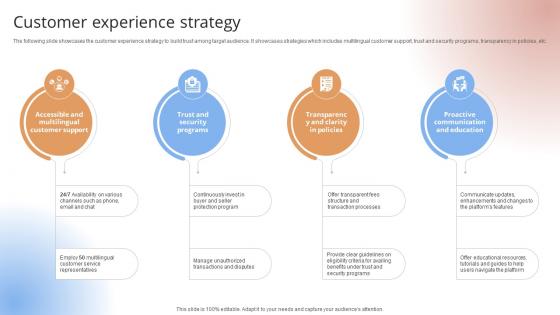
Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.Get a simple yet stunning designed Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
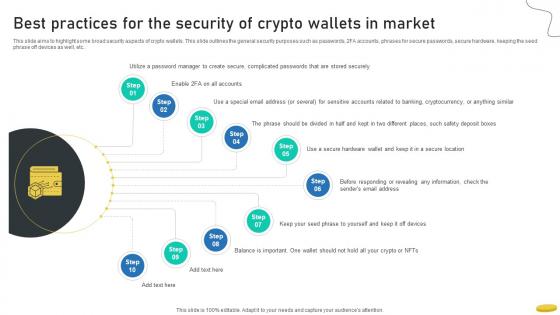
Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain today and make your presentation stand out from the rest This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.
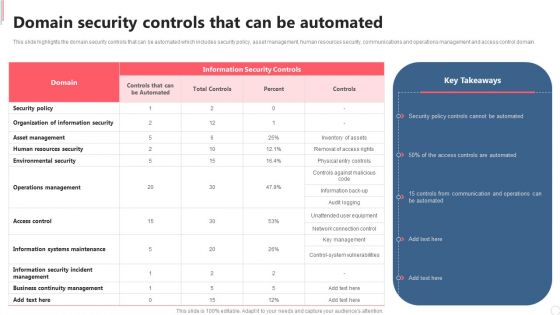
Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.
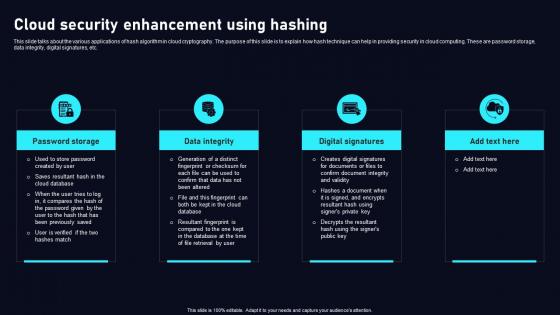
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
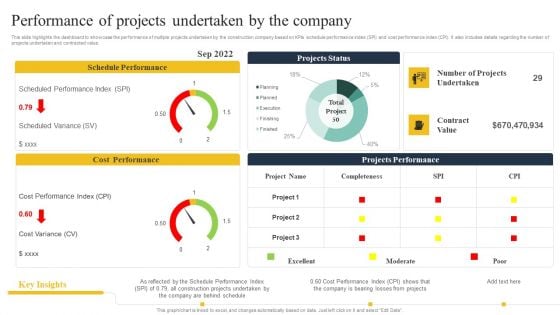
Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF
Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
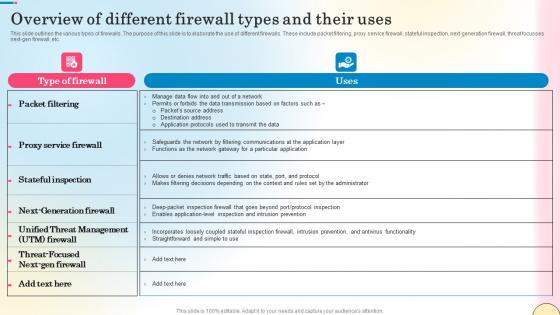
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.
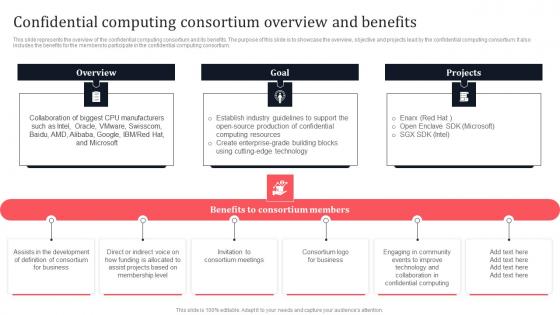
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
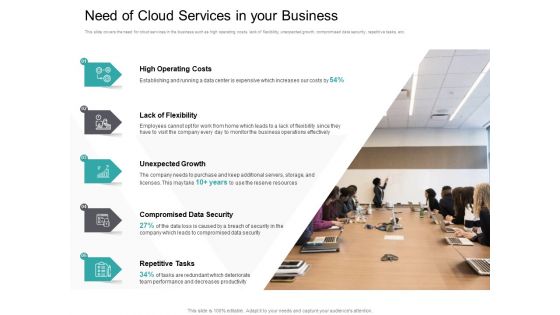
Cloud Based Marketing Need Of Cloud Services In Your Business Ppt PowerPoint Presentation Professional Show PDF
This slide covers the need for cloud services in the business such as high operating costs, lack of flexibility, unexpected growth, compromised data security, repetitive tasks, etc. Presenting cloud based marketing need of cloud services in your business ppt powerpoint presentation professional show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high operating costs, lack flexibility, unexpected growth, compromised data security, repetitive tasks. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
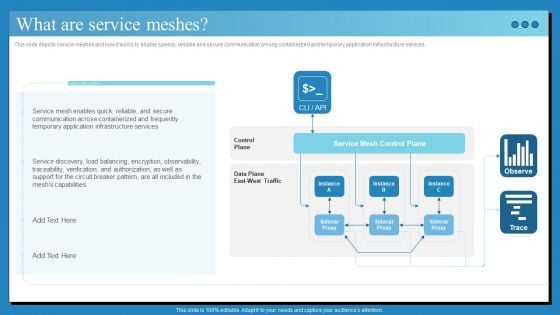
Data Center Infrastructure Technologies What Are Service Meshes Topics PDF
This slide depicts service meshes and how it works to enable speedy, reliable and secure communication among containerized and temporary application infrastructure services. Explore a selection of the finest Data Center Infrastructure Technologies What Are Service Meshes Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Center Infrastructure Technologies What Are Service Meshes Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
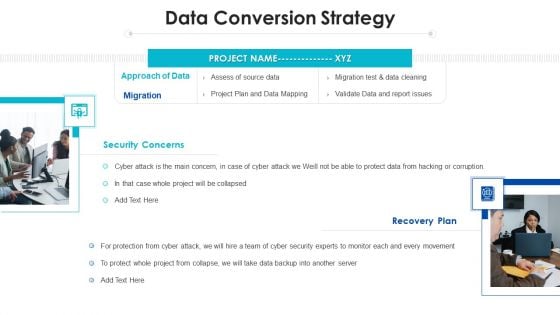
Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF
Presenting Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Approach Data, Recovery Plan, Cyber Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
PowerPoint Presentation Designs Strategy Pie Chart Ppt Presentation
PowerPoint Presentation Designs Strategy Pie Chart PPT PresentationBusiness PPT templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Secure your promotion with our PowerPoint Presentation Designs Strategy Pie Chart Ppt Presentation. Download without worries with our money back guaranteee.

Facilitating IT Intelligence Architecture Determine Capabilities Enabling Intelligent Infrastructure Graphics PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting Facilitating IT Intelligence Architecture Determine Capabilities Enabling Intelligent Infrastructure Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Configuration Automation, Connection Of Devices And Desktops, Infrastructure Services Analysis In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
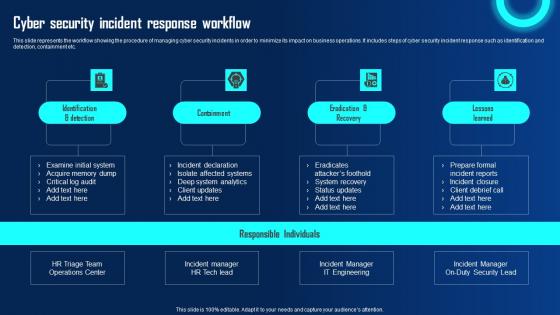
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.
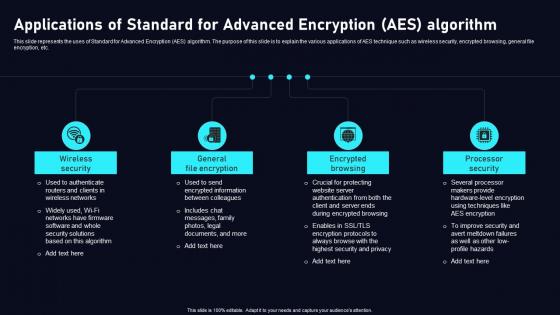
Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.
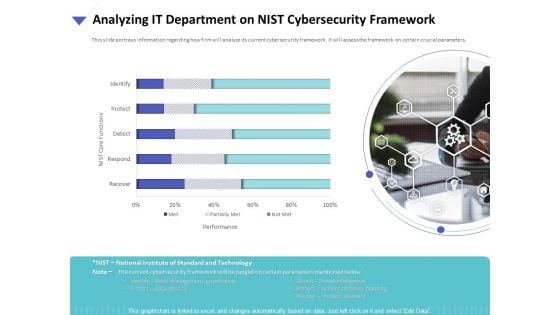
Strategies To Mitigate Cyber Security Risks Analyzing IT Department On NIST Cybersecurity Framework Ppt Slides Background Designs PDF
Presenting this set of slides with name strategies to mitigate cyber security risks analyzing it department on nist cybersecurity framework ppt slides background designs pdf. The topics discussed in these are performance, nist core functions, identify, protect, detect, recover, respond. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
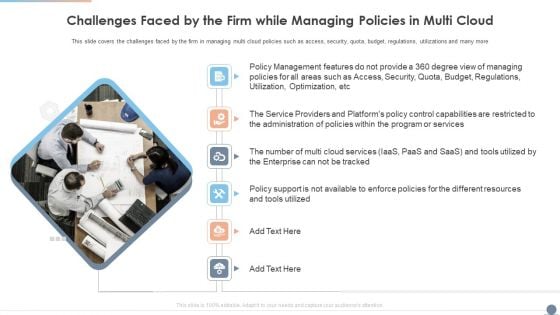
Multi Cloud Complexity Management Challenges Faced By The Firm While Managing Policies In Multi Cloud Topics PDF
This slide covers the challenges faced by the firm in managing multi cloud policies such as access, security, quota, budget, regulations, utilizations and many more. Presenting Multi Cloud Complexity Management Challenges Faced By The Firm While Managing Policies In Multi Cloud Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Service, Budget, Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Hacking Prevention Awareness Training For IT Security Icons Slide Hacking Prevention Awareness Training For IT Security Information PDF
Introducing our well designed hacking prevention awareness training for it security icons slide hacking prevention awareness training for it security information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Information And Technology Security Operations Icons Slide Elements PDF
Introducing our well designed information and technology security operations icons slide elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Organizational Security Solutions Icons Slide Ppt Gallery Layout PDF
Introducing our well designed organizational security solutions icons slide ppt gallery layout pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Security Functioning Centre Icons Slide Ppt Template PDF
Introducing our well designed security functioning centre icons slide ppt template pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Security And Process Integration Icon Slide Background PDF
Introducing our well designed security and process integration icon slide background pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Cloud Computing Security IT Icons Slide Ppt Inspiration Guidelines PDF
Introducing our well designed cloud computing security it icons slide ppt inspiration guidelines pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Food Security Excellence Ppt Icon Introduction PDF
Introducing our well designed icons slide for food security excellence ppt icon introduction pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Project Security Administration IT Infographics PDF
Introducing our well designed icons slide for project security administration it infographics pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Cloud Information Security Ppt Icon Portfolio PDF
Icons Slide For Cloud Security Assessment Download PDF
Introducing our well designed Icons Slide For Cloud Security Assessment Download PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide IT Security Automation Systems Guide Mockup PDF
Introducing our well designed Icons Slide IT Security Automation Systems Guide Mockup PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slides Organizations Risk Management And IT Security Template PDF
Introducing our well designed Icons Slides Organizations Risk Management And IT Security Template PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Security Training Program Frameworks Hacking Prevention Awareness Training For IT Security Themes PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on target, training, maintain, secure, implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Marketing Concepts Many To 5 Stages Process Diagram Business Strategy Consultant
We present our marketing concepts many to 5 stages process diagram business strategy consultant.Download our Marketing PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Process and Flows PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Use our Curves and Lines PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds.Use these PowerPoint slides for presentations relating to Development, Web, Design, Building, Plan, Hand, Success, Successful, Internet, Visitor, Site, Website, Network, White, Innovation, Formula, Media, Business, Server, Concept, Characteristic, Organizing, Diagram, Drawing, Marketing, Word, Starting, Technology, Security, Blogging, Strategy, Technique, Young, Writing, Domain, Text, Quality, Organization, Brainstorming, Information, Background, Hosting, Blog, Database, Software, Component, White Board, Entrepreneur, Communication. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Attain promotions with our Marketing Concepts Many To 5 Stages Process Diagram Business Strategy Consultant. You will come out on top.


 Continue with Email
Continue with Email

 Home
Home


































