Construction Safety Plan

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Business Architecture Diagrams 3d Man Front Of Three Doors PowerPoint Slides
We present our business architecture diagrams 3d man front of three doors PowerPoint Slides.Download our People PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Present our Shapes PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Use our Success PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Download our Metaphors-Visual Concepts PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way.Use these PowerPoint slides for presentations relating to 3d, access, accessibility, aspirations, background, businessman, character,close, close-up, concept, conceptual, door, doorknob, doorway, elegance,entrance, estate, exit, figure, gate, guest, guy, help, home, house, human, icon,idea, illustration, input, knock, knocker, lock, man, opportunity, opulence, people,person, puppet, real, rich, ring, security, shiny, target, up, visitor, wealth,welcome. The prominent colors used in the PowerPoint template are Blue light, Yellow, Green. Customers tell us our business architecture diagrams 3d man front of three doors PowerPoint Slides will make the presenter look like a pro even if they are not computer savvy. We assure you our background PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Customers tell us our business architecture diagrams 3d man front of three doors PowerPoint Slides will make the presenter look like a pro even if they are not computer savvy. Use our accessibility PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. PowerPoint presentation experts tell us our business architecture diagrams 3d man front of three doors PowerPoint Slides will help them to explain complicated concepts. You can be sure our aspirations PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Achieve strategic & tactical operations with our Business Architecture Diagrams 3d Man Front Of Three Doors PowerPoint Slides. They will make you look good.
Vector Illustration Of IT Security Measures For Strong Protection Ppt PowerPoint Presentation File Outline PDF
Persuade your audience using this vector illustration of it security measures for strong protection ppt powerpoint presentation file outline pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustration of it security measures for strong protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
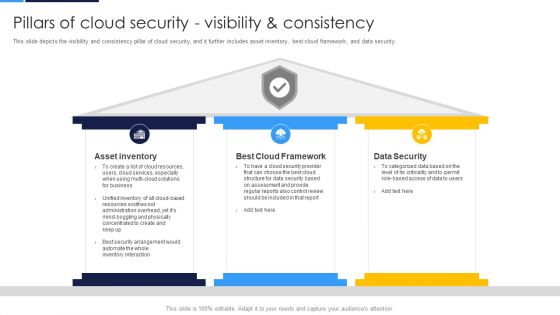
Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
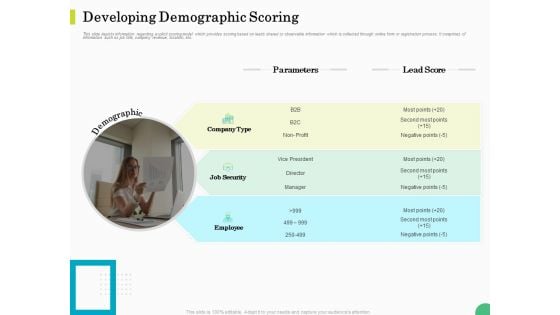
Evaluating Rank Prospects Developing Demographic Scoring Ppt Layouts Objects PDF
This slide depicts information regarding explicit scoring model which provides scoring based on leads shared or observable information which is collected through online form or registration process. It comprises of information such as job title, company revenue, location, etc. Presenting evaluating rank prospects developing demographic scoring ppt layouts objects pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like parameters, lead score, job security, employee, demographic. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
App Design Model Icon For Security Optimization Ppt PowerPoint Presentation Inspiration PDF
Showcasing this set of slides titled app design model icon for security optimization ppt powerpoint presentation inspiration pdf. The topics addressed in these templates are app design model icon for security optimization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Types Of Employee Value Proposition With Rewards And Opportunity Ppt PowerPoint Presentation Icon Skills PDF
Persuade your audience using this types of employee value proposition with rewards and opportunity ppt powerpoint presentation icon skills pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including rewards, work, organization, opportunity, people. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Incident Handling Agenda For Cybersecurity Management Slides PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity management slides pdf. The topics discussed in these slides are determining roles and responsibilities of senior management and executives who are responsible in risk management, presenting optimize cybersecurity risk framework to senior management and executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Stock Photo Business Strategy Execution Umbrella With Flag Design Stock Photo Pictures Images
Our stock photo business strategy execution umbrella with flag design stock photo pictures images Let You Put Your Feet Up. Enjoy The Comforts They Will Bring. Get Your Team To Follow In Your Footsteps. Our Americana Will Blaze The Trail.
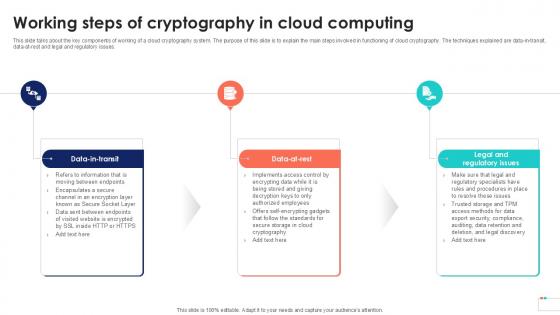
Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues.

Computer Security Incident Handling Optimizing Cybersecurity Framework Roadmap Designs PDF
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
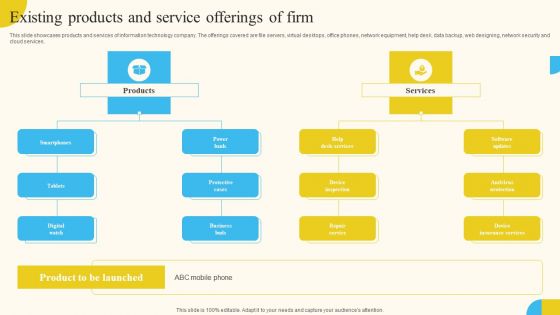
Existing Products And Service Offerings Of Firm Activities For Successful Launch Event Professional PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Want to ace your presentation in front of a live audience Our Existing Products And Service Offerings Of Firm Activities For Successful Launch Event Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
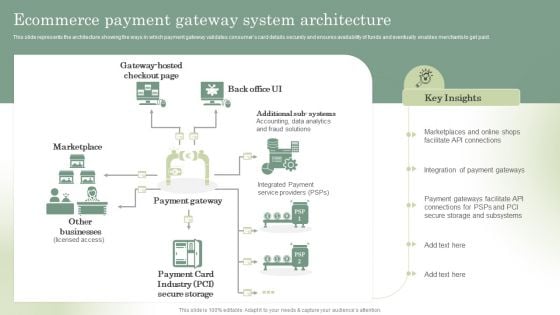
Optimizing Online Stores Ecommerce Payment Gateway System Architecture Diagrams PDF
This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Optimizing Online Stores Ecommerce Payment Gateway System Architecture Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Promotion Techniques To Grow Small Businesses Economically Formats PDF
This slide represents marketing approaches utilized by small businesses industries to secure and build customer base along with brand image. Elements included in this slide are marketing strategies, action plan, estimated budget and impact. Pitch your topic with ease and precision using this Promotion Techniques To Grow Small Businesses Economically Formats PDF. This layout presents information on Techniques, Action Steps, Budget, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

The Comprehensive Billing Solution Cost Management Cloud Computing Complexities And Solutions Professional PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services.Want to ace your presentation in front of a live audience Our The Comprehensive Billing Solution Cost Management Cloud Computing Complexities And Solutions Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
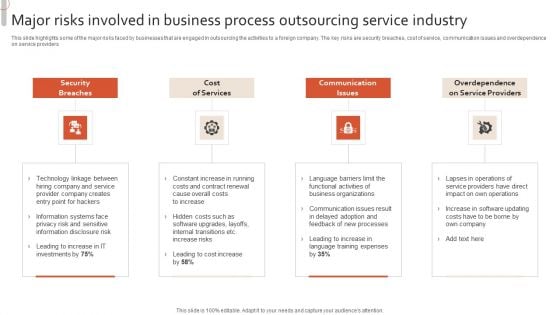
Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF
This slide highlights some of the major risks faced by businesses that are engaged in outsourcing the activities to a foreign company. The key risks are security breaches, cost of service, communication issues and overdependence on service providers. Presenting Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Breaches, Cost Services, Communicationi Ssues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
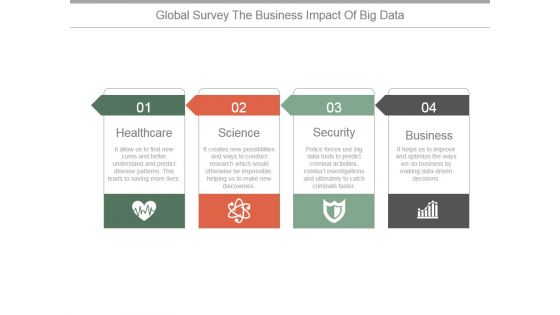
Global Survey The Business Impact Of Big Data Ppt PowerPoint Presentation Example 2015
This is a global survey the business impact of big data ppt powerpoint presentation example 2015. This is a four stage process. The stages in this process are healthcare, science, security, business.

Piggy Over A Stack Of Books PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Education PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download our Future PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Finance PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Piggy bank over a stack of colorful books, education, future, success, security, finance. The prominent colors used in the PowerPoint template are Green, Red, Green. You can be sure our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Use our colorful PowerPoint templates and PPT Slides look good visually. You can be sure our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113 will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Customers tell us our books PowerPoint templates and PPT Slides have awesome images to get your point across. People tell us our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals People tell us our over PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Make unique presentations with our Piggy Over A Stack Of Books PowerPoint Templates Ppt Backgrounds For Slides 0113. You'll always stay ahead of the game.
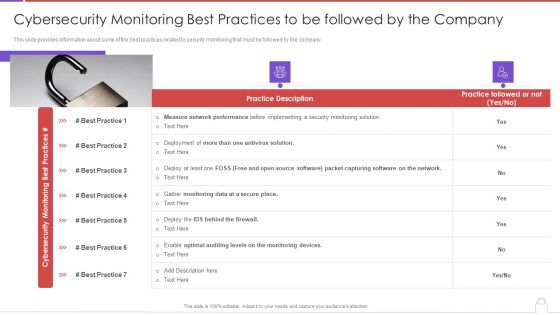
Methods To Develop Cybersecurity Monitoring Best Practices To Be Followed By The Company Demonstration PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Presenting methods to develop cybersecurity monitoring best practices to be followed by the company demonstration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like practice description, gather monitoring data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
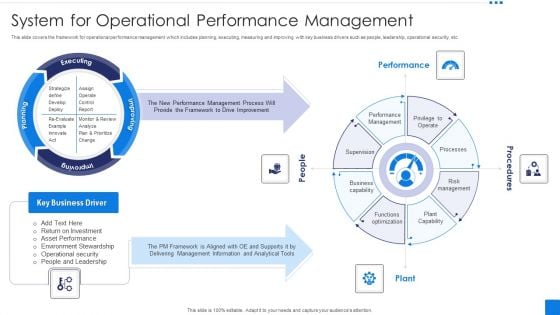
System For Operational Performance Management Infographics PDF
This slide covers the framework for operational performance management which includes planning, executing, measuring and improving with key business drivers such as people, leadership, operational security, etc. Presenting System For Operational Performance Management Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Performance, Procedures, People, Plant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Visionary Guide To Blockchain Scope Of Using Blockchain Technology In Cloud BCT SS V
This slide mentions the scope of integrating blockchain technology in cloud computing. It includes elevated security measures, immutable data integrity, decentralization and data recovery or backup. Get a simple yet stunning designed Visionary Guide To Blockchain Scope Of Using Blockchain Technology In Cloud BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Visionary Guide To Blockchain Scope Of Using Blockchain Technology In Cloud BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide mentions the scope of integrating blockchain technology in cloud computing. It includes elevated security measures, immutable data integrity, decentralization and data recovery or backup.

API Management For Building Software Applications Present Application Programming Interface Issues Guidelines PDF
Presenting this set of slides with name api management for building software applications present application programming interface issues guidelines pdf. This is a four stage process. The stages in this process are technological complexity, security risks, high consumption time, expensive. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
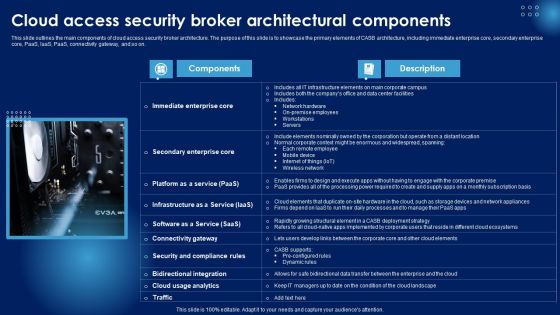
Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Get a simple yet stunning designed Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF
The following slide showcases the impact of software as a service SaaS security in developing business. It includes key elements such as scalability, security, customization, maintenance, availability, IT cost etc. Showcasing this set of slides titled Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF. The topics addressed in these templates are Scalability, Security, Customization, Maintenance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Kubernetes Containers Architecture Overview Table Of Content Ppt Summary Layout Ideas PDF
Presenting this set of slides with name kubernetes containers architecture overview table of content ppt summary layout ideas pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
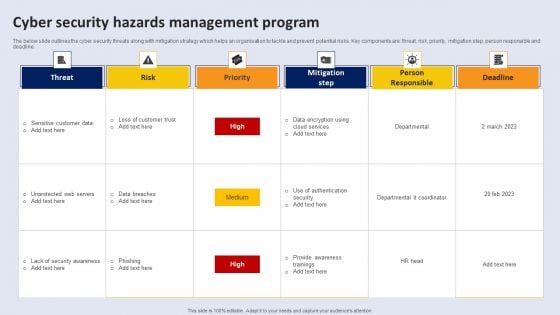
Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security IT Prepare And Deploy Strong IT Policies Ppt Icon Design Ideas PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security it prepare and deploy strong it policies ppt icon design ideas pdf bundle. Topics like it policies, management, access, policies, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
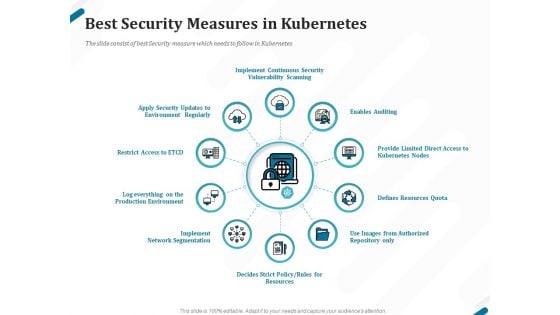
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
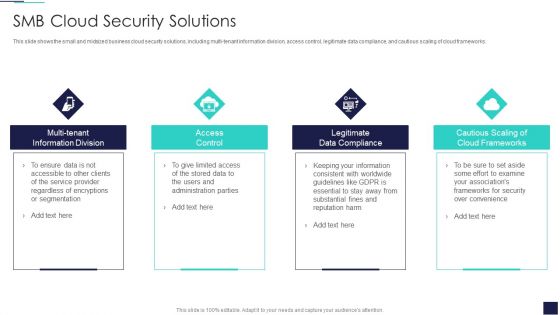
Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Presenting Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multi Tenant, Access Control, Information Division. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
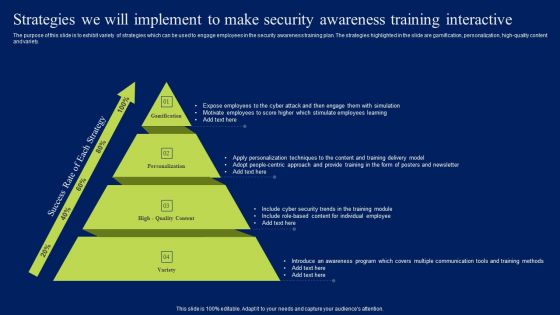
Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Slidegeeks is here to make your presentations a breeze with Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
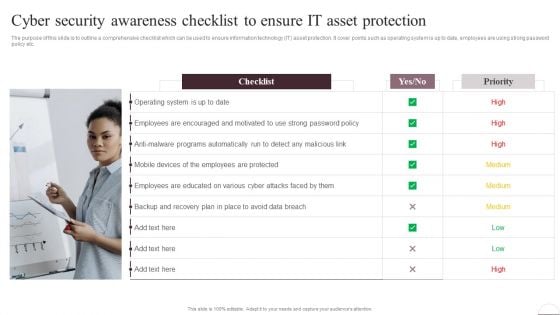
Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
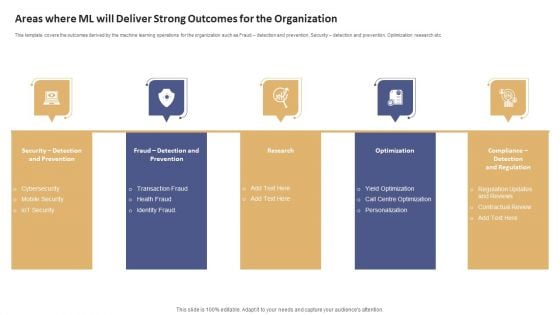
Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Layer Based Integrate IOT Blockchain Platform Architecture Microsoft PDF
This slide covers multiple layers of architectural system based on IoT blockchain platforms. It includes layers such as application, connectivity, IoT physical layers and service layers comprising of device management, data visualization, big data analytics, consensus management, distributed ledger, smart contracts, API interface, message broker, security management, etc. Showcasing this set of slides titled Layer Based Integrate IOT Blockchain Platform Architecture Microsoft PDF. The topics addressed in these templates are Application Layer, Connectivity Layers, IOT Physical Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Implementation Framework Present Concerns Impeding Cybersecurity Clipart PDF
Presenting this set of slides with name cyber security implementation framework present concerns impeding cybersecurity clipart pdf. The topics discussed in these slides are data breaches and records exposed, reported financial losses due to increase cybercrimes, financial losses, cybercrimes incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
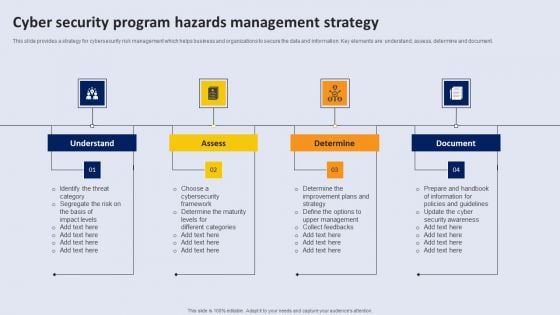
Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
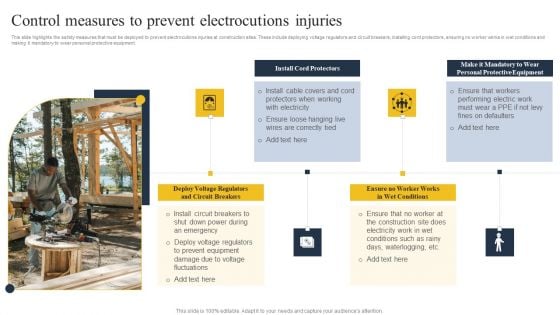
Security Control Techniques For Real Estate Project Control Measures To Prevent Electrocutions Injuries Ideas PDF
Explore a selection of the finest Security Control Techniques For Real Estate Project Control Measures To Prevent Electrocutions Injuries Ideas PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Control Techniques For Real Estate Project Control Measures To Prevent Electrocutions Injuries Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
PowerPoint Template Company Chains Process Ppt Designs
PowerPoint Template Company chains process PPT Designs-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go. Fan your dreams with our PowerPoint Template Company Chains Process Ppt Designs. Dare to achieve with your thoughts.
Information Technology Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Design PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this information technology security prepare and deploy strong it policies ppt icon graphics design pdf. Use them to share invaluable insights on v and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
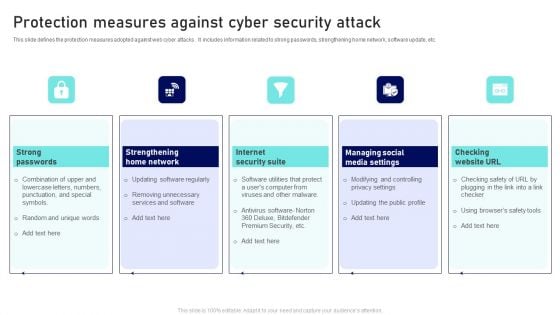
Protection Measures Against Cyber Security Attack Ppt Infographic Template Template PDF
This slide defines the protection measures adopted against web cyber attacks . It includes information related to strong passwords, strengthening home network, software update, etc. Presenting Protection Measures Against Cyber Security Attack Ppt Infographic Template Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Strong Passwords, Internet Security Suite, Checking Website URL. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5G Evolution Architectural Technology Determine Competitive Landscape Of 5G Icons PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver an awe inspiring pitch with this creative 5G Evolution Architectural Technology Determine Competitive Landscape Of 5G Icons PDF bundle. Topics like Reasonably Secured, Several Seconds, Coverage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
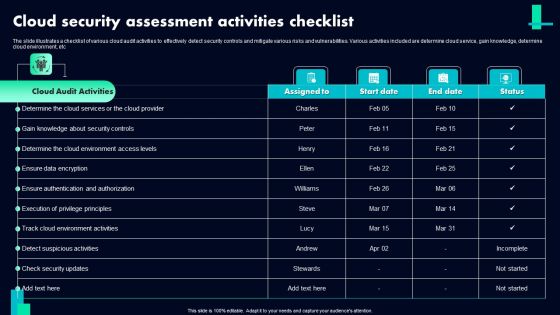
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal.Create an editable Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Cyber Security Governance Ppt PowerPoint Presentation Layouts Master Slide PDF
Presenting this set of slides with name cyber security implementation framework cyber security governance ppt powerpoint presentation layouts master slide pdf. The topics discussed in these slides are senior management, steering committee and executive management, business strategy, organisation objectives, security requirements. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
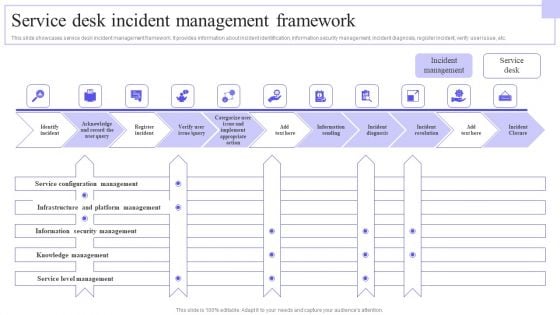
Service Desk Incident Management Framework Brochure PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Service Desk Incident Management Framework Brochure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Service Desk Incident Management Framework Brochure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
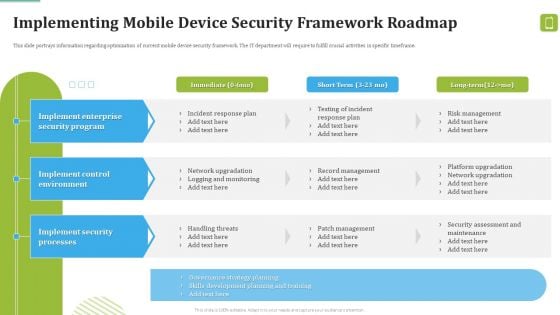
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
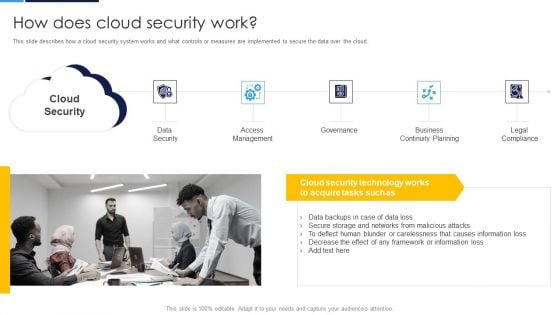
Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
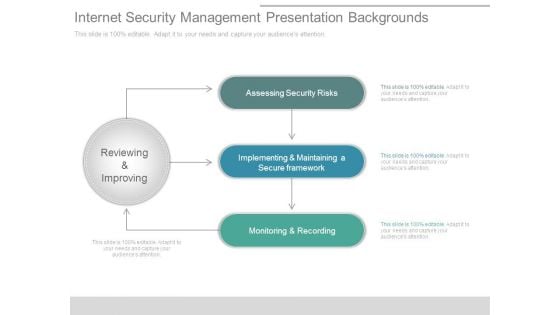
Internet Security Management Presentation Backgrounds
This is a internet security management presentation backgrounds. This is a three stage process. The stages in this process are assessing security risks, implementing and maintaining a secure framework, monitoring and recording, reviewing and improving.
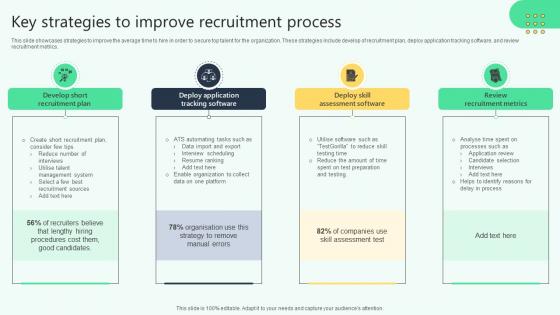
Key Strategies To Improve Recruitment Process Analysing Hr Data For Effective Decision Making
This slide showcases strategies to improve the average time to hire in order to secure top talent for the organization. These strategies include develop of recruitment plan, deploy application tracking software, and review recruitment metrics. Find a pre-designed and impeccable Key Strategies To Improve Recruitment Process Analysing Hr Data For Effective Decision Making. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases strategies to improve the average time to hire in order to secure top talent for the organization. These strategies include develop of recruitment plan, deploy application tracking software, and review recruitment metrics.
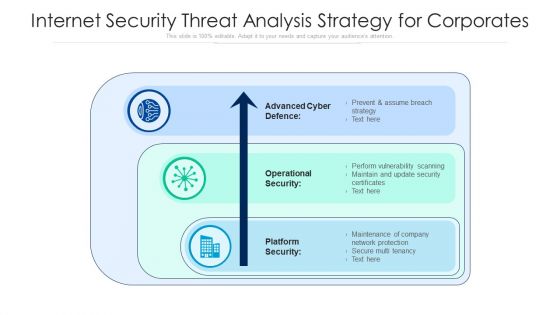
Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
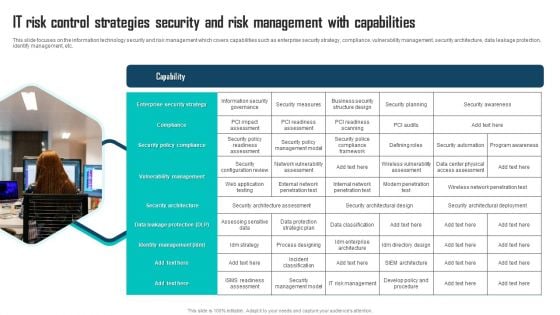
IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
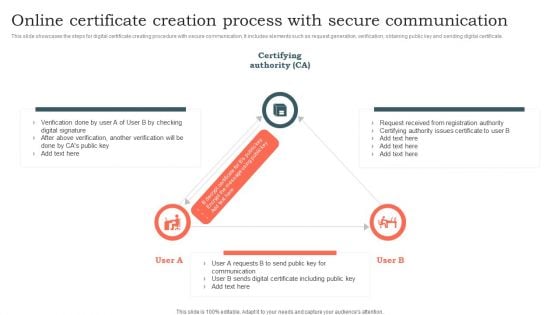
Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF
This slide showcases the steps for digital certificate creating procedure with secure communication. It includes elements such as request generation, verification, obtaining public key and sending digital certificate. Showcasing this set of slides titled Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF. The topics addressed in these templates are Certifying Authority, Key Communication, Digital Certificate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
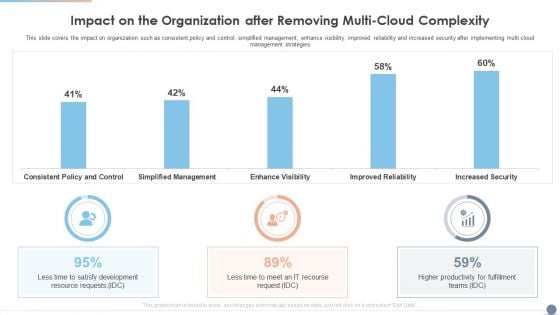
Multi Cloud Complexity Management Impact On The Organization After Removing Multi Cloud Complexity Information PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Deliver an awe inspiring pitch with this creative Multi Cloud Complexity Management Impact On The Organization After Removing Multi Cloud Complexity Information PDF bundle. Topics like Satisfy Development, Resource Requests, Fulfillment Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Understanding The Kubernetes Concepts And Architecture Table Of Contents Ppt Summary Inspiration PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture table of contents ppt summary inspiration pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































