Construction Safety Plan
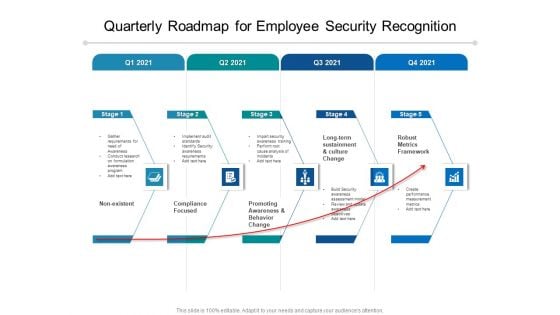
Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
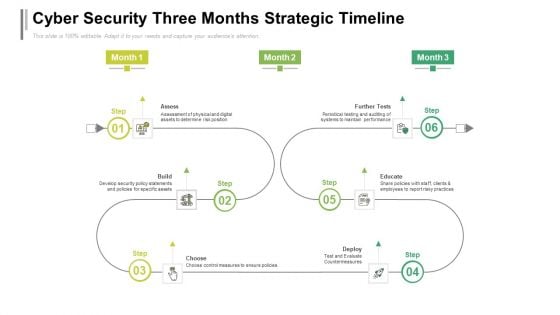
Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
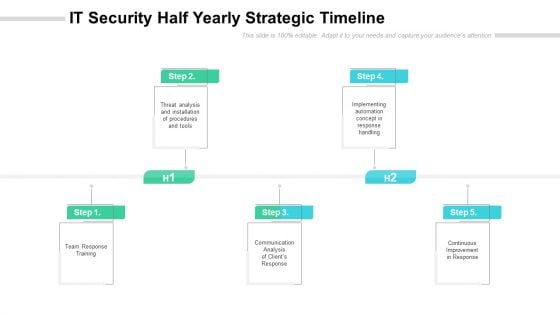
IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
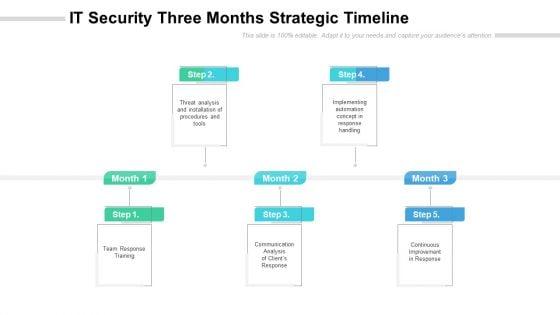
IT Security Three Months Strategic Timeline Portrait
Presenting our jaw dropping it security three months strategic timeline portrait. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
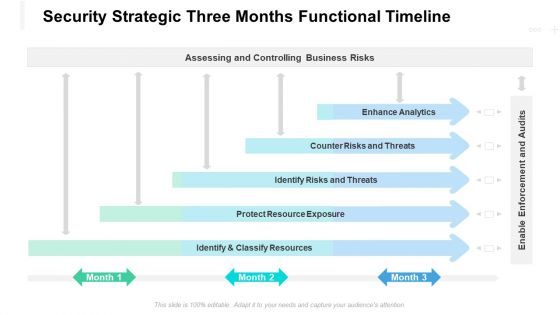
Security Strategic Three Months Functional Timeline Introduction
Presenting our jaw dropping security strategic three months functional timeline introduction. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
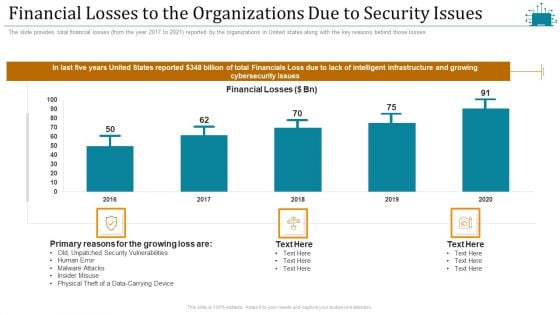
Cloud Intelligence Framework For Application Consumption Financial Losses To The Organizations Due To Security Issues Mockup PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption financial losses to the organizations due to security issues mockup pdf bundle. Topics like security vulnerabilities, primary reasons for the growing, physical theft of a data-carrying device, 2016 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document brilliant piece now.

Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document brilliant piece now.
Stock Photo 3d Globe Inside The Chain Security PowerPoint Slide
3d globe is covered with chain in this business image. This image is specially designed for displaying global security issues. Use this image for business and defense related presentations and create a good impact on viewers.
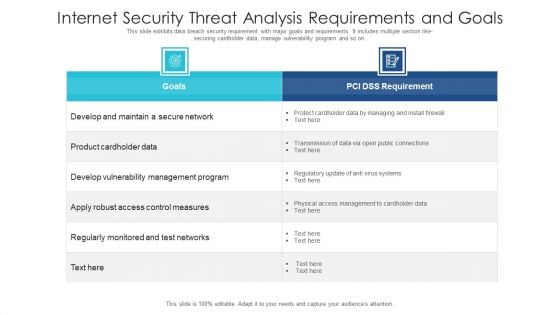
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Devops Configuration Management IT Addressing Various Trends Associated To Devops Implementation Mockup PDF
This slide provides information regarding various trends associated to DevOps implementation in terms of DevOps automation, using serverless architecture, etc. Presenting devops configuration management it addressing various trends associated to devops implementation mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like devops automation, serverless architecture, embedded security. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
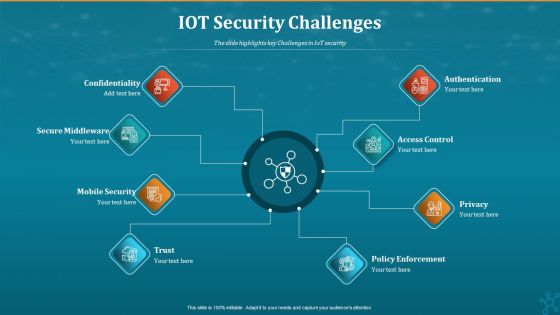
Machine To Machine Communication IOT Security Challenges Pictures PDF
The slide highlights key Challenges in IoT security.Presenting machine to machine communication iot security challenges pictures pdf. to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like confidentiality, secure middleware, policy enforcement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
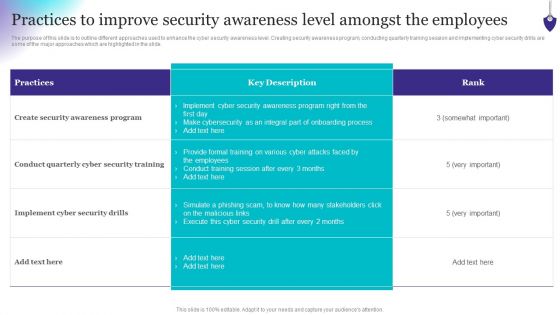
Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. This Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
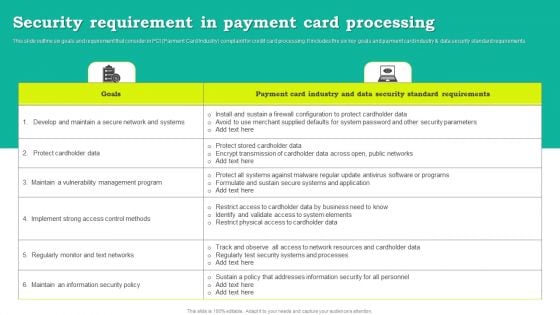
Security Requirement In Payment Card Processing Download PDF
This slide outline six goals and requirement that consider in PCI Payment Card Industry complaint for credit card processing. It includes the six key goals and payment card industry and data security standard requirements. Showcasing this set of slides titled Security Requirement In Payment Card Processing Download PDF. The topics addressed in these templates are Goals, Payment Card Industry, Data Security Standard Requirements. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Ring With A Key Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Key Ring With A Key Security PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Chains PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Security PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Shapes PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Present our Ring charts PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners.Use these PowerPoint slides for presentations relating to Key ring with a key, Chains, Security, Shapes, Ring charts, Business. The prominent colors used in the PowerPoint template are Red, Gray, Black. Go as far as you want with our Key Ring With A Key Security PowerPoint Templates Ppt Backgrounds For Slides 0213. They are designed to go the distance.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
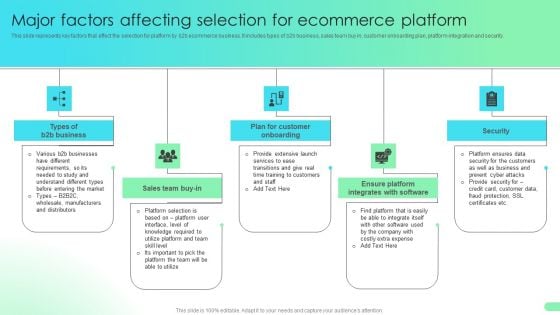
Major Factors Affecting Selection For Ecommerce Platform Comprehensive Guide For Developing Microsoft PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security.The Major Factors Affecting Selection For Ecommerce Platform Comprehensive Guide For Developing Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Strategies To Rebuild CIBIL To Prevent Bankruptcy Information PDF
This slide showcases ways to rebuild credit information bureau India limited score to overcome bankruptcy . It includes reviewing CIBIL reports regularly , not closing the amounts , applying for a secure credit card , avoid visiting credit repair service etc. Persuade your audience using this Strategies To Rebuild CIBIL To Prevent Bankruptcy Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information, Payments, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
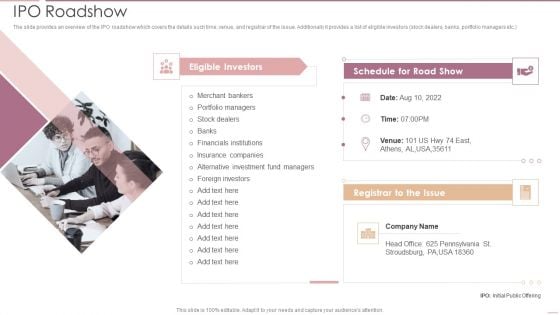
Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF
The slide provides an overview of the IPO roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc.Presenting Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Eligible Investors, Portfolio Managers, Alternative Investment In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
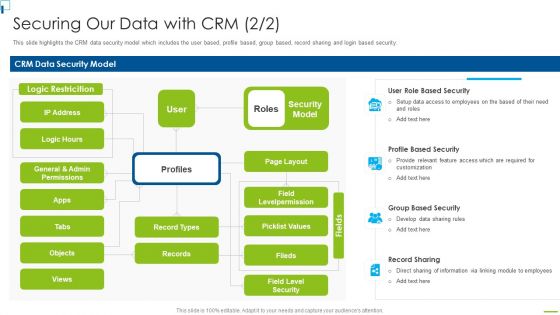
Designing And Deployment Securing Our Data With CRM Ppt PowerPoint Presentation File Backgrounds PDF
This slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. This is a designing and deployment securing our data with crm ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like crm data security model, security model, profile based security, record sharing, group based security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF
Retrieve professionally designed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
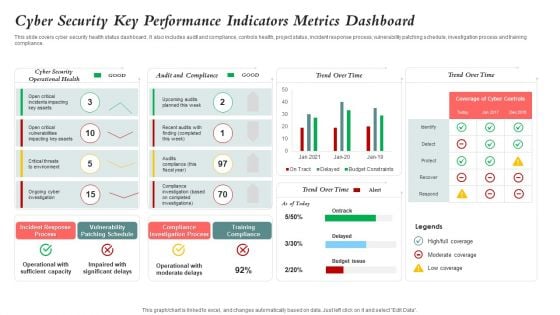
Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF
This slide covers cyber security health status dashboard . It also includes audit and compliance, controls health, project status, incident response process, vulnerability patching schedule, investigation process and training compliance. Pitch your topic with ease and precision using this Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF. This layout presents information on Cyber Security, Vulnerability Patching Schedule, Compliance Investigation Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
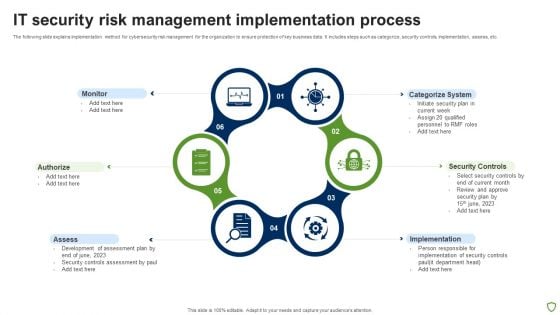
IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Cyber Security Components To Enhance Processes Template PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Cyber Security Components To Enhance Processes Template PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Cyber Security Components To Enhance Processes Template PDF today and make your presentation stand out from the rest.

Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals This Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals
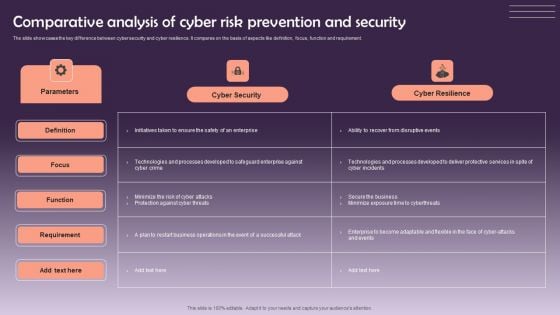
Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF
The slide showcases the key difference between cyber security and cyber resilience. It compares on the basis of aspects like definition, focus, function and requirement. Showcasing this set of slides titled Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF. The topics addressed in these templates are Cyber Security, Cyber Resilience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Successful Risk Administration Key Benefits Post Implementing Risk Mitigation Strategies Elements PDF
The following slide exhibits the positive impact of implementing risk management strategies in real estate business. Customer satisfaction, improved data security, operational process improvement and reduced catastrophic events are some of the major benefits which are outlined in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Successful Risk Administration Key Benefits Post Implementing Risk Mitigation Strategies Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Successful Risk Administration Key Benefits Post Implementing Risk Mitigation Strategies Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.If you are looking for a format to display your unique thoughts, then the professionally designed Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
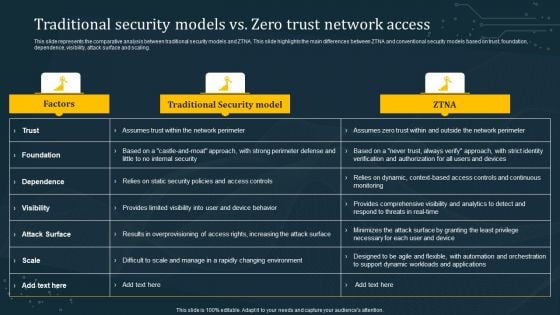
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
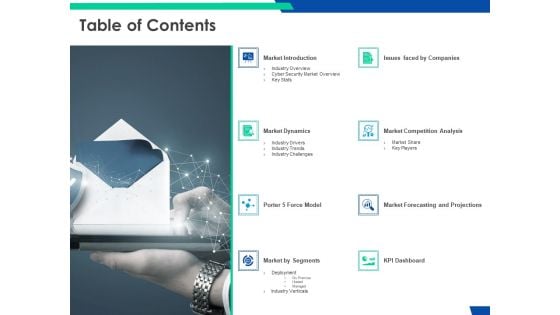
Cloud Based Email Security Market Report Table Of Contents Ppt Inspiration Vector PDF
Presenting cloud based email security market report table of contents ppt inspiration vector pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like market introduction, market dynamics, issues faced by companies, kpi dashboard, market by segments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Investment Banking Security Underwriting Pitchbook Guidelines PDF
Presenting Table Of Contents For Investment Banking Security Underwriting Pitchbook Guidelines PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Deal Overview, Senior Management, Consolidated IncomeIn addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF
Presenting Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Automation Throughout, Automated Sequences, Reporting Dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Practices For Secure Online Transactions Processing Ppt Icon Themes PDF
This slide mentions practices for online transactions processing to ensure secure checkout process. It includes matching IP and billing address, Encrypt data and use payment tokenization method. Persuade your audience using this Practices For Secure Online Transactions Processing Ppt Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Encrypt Data, Use Payment Tokenization, IP And Billing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
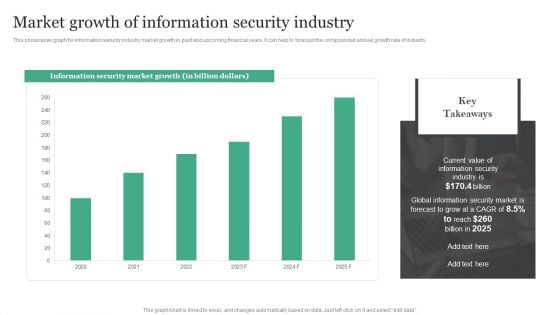
Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF
This showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. This Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
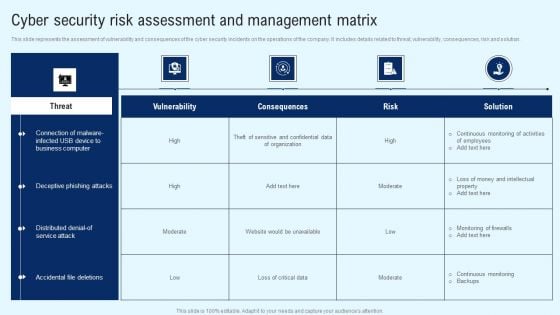
Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Get a simple yet stunning designed Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
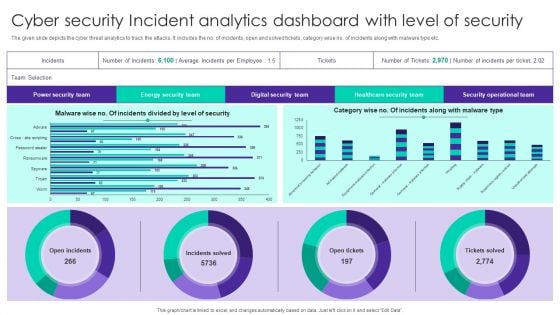
Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF
The given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Pitch your topic with ease and precision using this Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF. This layout presents information on Power Security Team, Open Incidents, Incidents Solved, Open Tickets. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
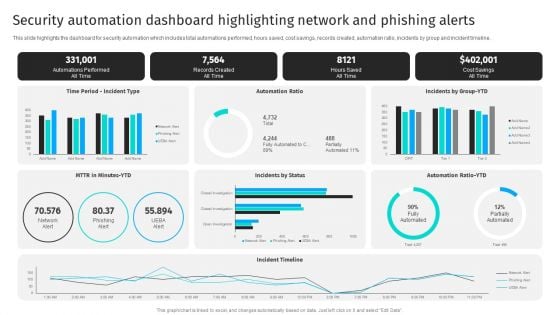
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
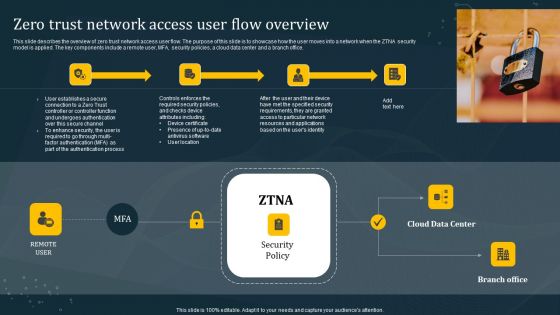
Zero Trust Network Access User Flow Overview Mockup PDF
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Create an editable Zero Trust Network Access User Flow Overview Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access User Flow Overview Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
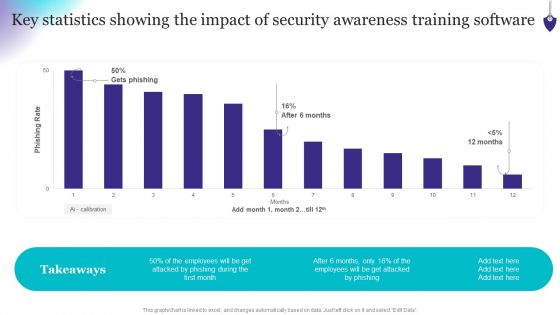
Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
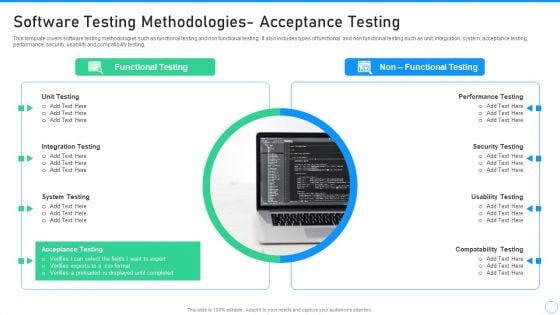
Application Designing And Programming Playbook Software Testing Methodologies Template PDF
This template covers software testing methodologies such as functional testing and non functional testing. It also includes types of functional and non functional testing such as unit, integration, system, acceptance testing, performance, security, usability and compatibility testing. This is a Application Designing And Programming Playbook Software Testing Methodologies Template PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Performance Testing, Usability Testing, Compatibility Testing You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Human Rights Policies Of The Company Icons PDF
This slide shows the human rights policies that are followed by the company for the betterment of community and employees such as stakeholder engagement, diversity and inclusion, safe and healthy workplace, workplace security, work hours, wages and benefits etc. Presenting human rights policies of the company icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like community and stakeholder engagement, diversity and inclusion, safe and healthy workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
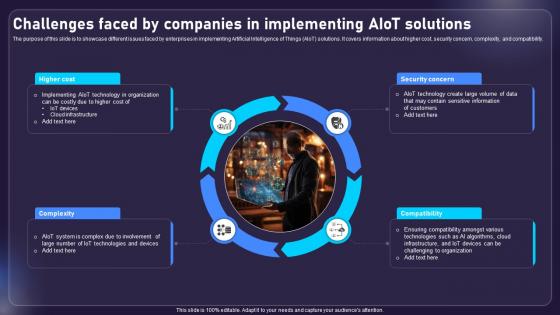
Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility. Find highly impressive Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility.
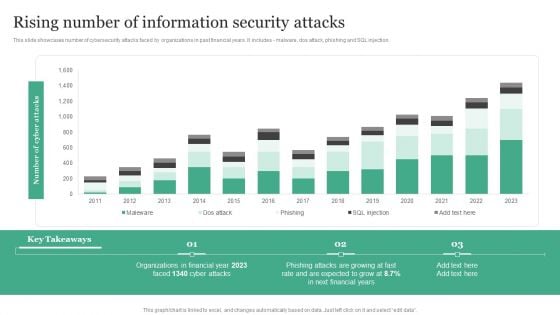
Rising Number Of Information Security Attacks Information Security Risk Administration Information PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, dos attack, phishing and SQL injection.Find a pre-designed and impeccable Rising Number Of Information Security Attacks Information Security Risk Administration Information PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
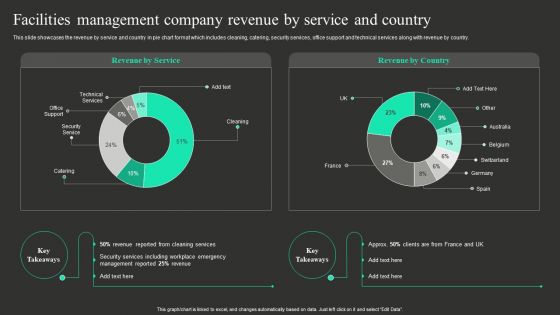
Facilities Management Company Revenue By Service And Country Information PDF
This slide showcases the revenue by service and country in pie chart format which includes cleaning, catering, security services, office support and technical services along with revenue by country. If you are looking for a format to display your unique thoughts, then the professionally designed Facilities Management Company Revenue By Service And Country Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Facilities Management Company Revenue By Service And Country Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
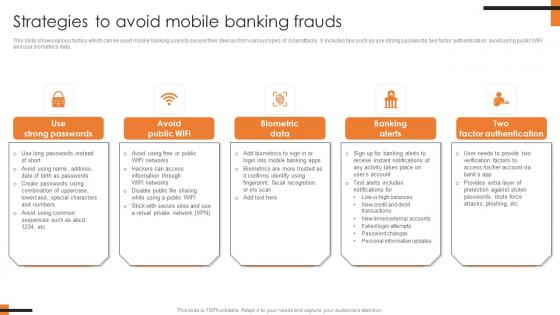
Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.This modern and well-arranged Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
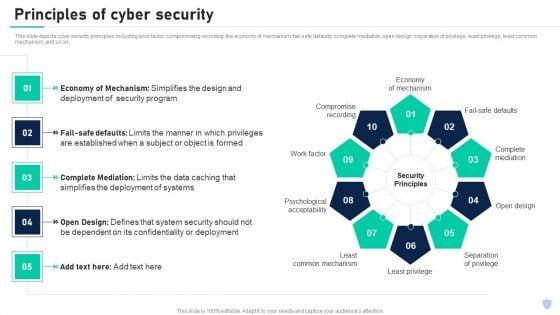
Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF
This slide depicts cyber security principles, including work factor, compromising recording, the economy of mechanism, fail-safe defaults, complete mediation, open design, separation of privilege, least privilege, least common mechanism, and so on. Get a simple yet stunning designed Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
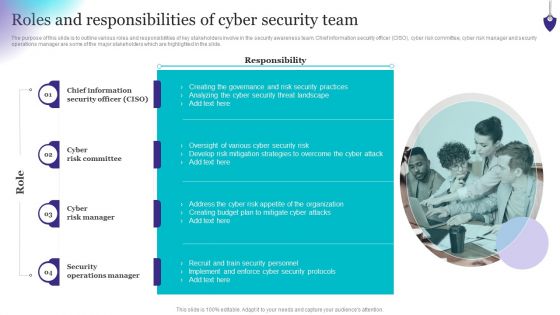
Organizing Security Awareness Roles And Responsibilities Of Cyber Security Team Slides PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Find a pre-designed and impeccable Organizing Security Awareness Roles And Responsibilities Of Cyber Security Team Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
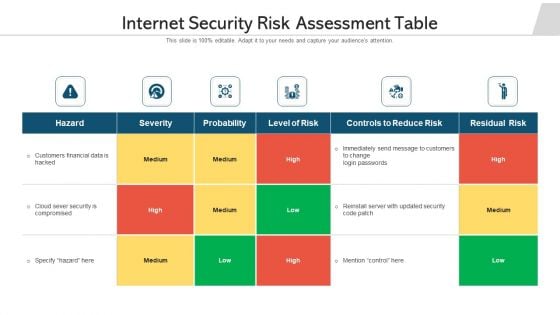
Internet Security Risk Assessment Table Ppt PowerPoint Presentation Gallery Design Inspiration PDF
Showcasing this set of slides titled internet security risk assessment table ppt powerpoint presentation gallery design inspiration pdf. The topics addressed in these templates are probability, level of risk, residual risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Financing Catalogue For Security Underwriting Agreement Leadership Senior Executive Team Designs PDF
The slide provides the name and designation of the key management team members CEO, CFO, Department head etc. of the company. It also provides the Major Transaction Experience work experience of the executives. This is a financing catalogue for security underwriting agreement leadership senior executive team designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like leadership senior executive team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
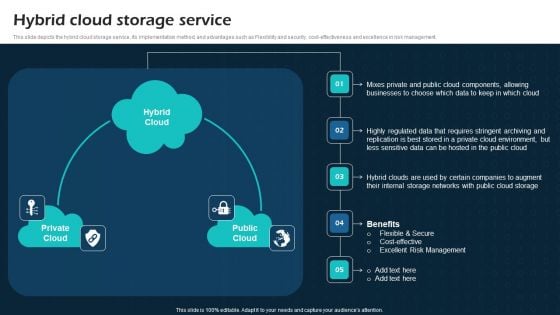
Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost effectiveness and excellence in risk management. If you are looking for a format to display your unique thoughts, then the professionally designed Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.


 Continue with Email
Continue with Email

 Home
Home


































