Construction Safety Plan
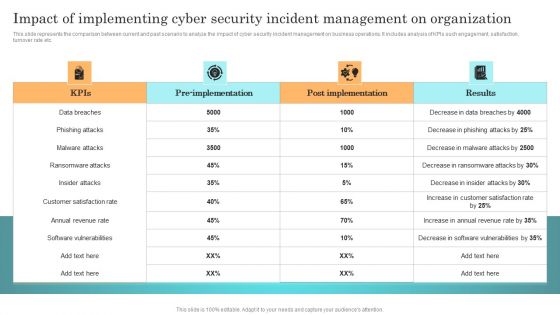
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
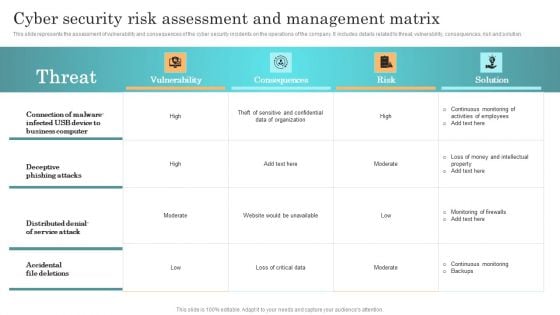
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
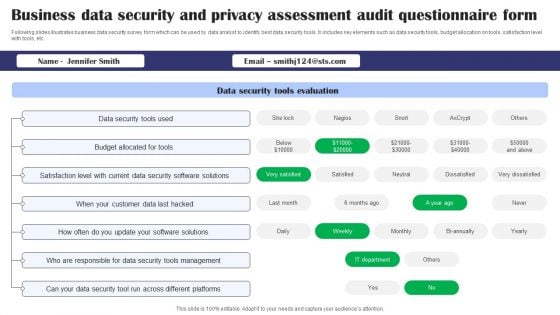
Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
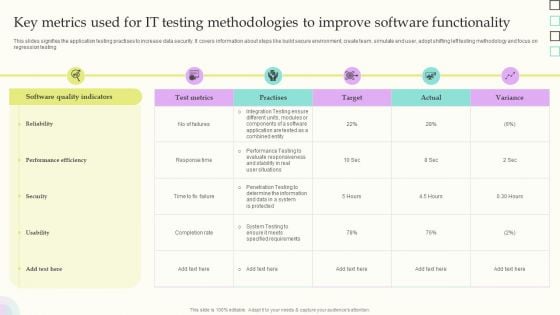
Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Showcasing this set of slides titled Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF. The topics addressed in these templates are Software Quality Indicators, Reliability, Performance Efficiency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
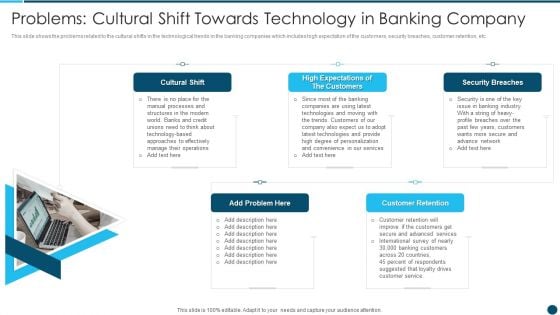
Digital Technology Adoption In Banking Industry Problems Cultural Shift Towards Technology Designs PDF
This slide shows the problems related to the cultural shifts in the technological trends in the banking companies which includes high expectation of the customers, security breaches, customer retention, etc.Presenting Digital Technology Adoption In Banking Industry Problems Cultural Shift Towards Technology Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like High Expectations Of The Customers, Security Breaches, Customer Retention In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
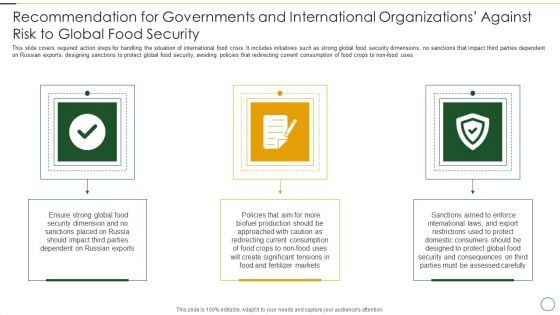
Recommendation For Governments And International Organizations Against Risk To Global Food Security Infographics PDF
This slide covers required action steps for handling the situation of international food crisis. It includes initiatives such as strong global food security dimensions, no sanctions that impact third parties dependent on Russian exports, designing sanctions to protect global food security, avoiding policies that redirecting current consumption of food crops to non food uses. Presenting recommendation for governments and international organizations against risk to global food security infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dependent on russian, ensure strong global, security dimension In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
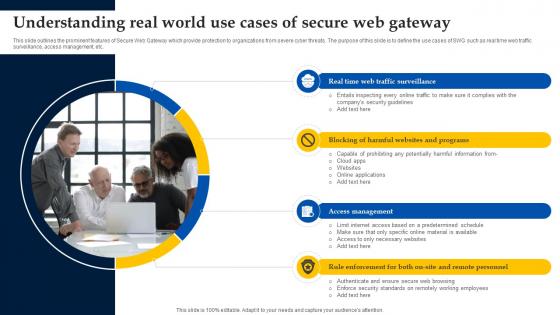
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
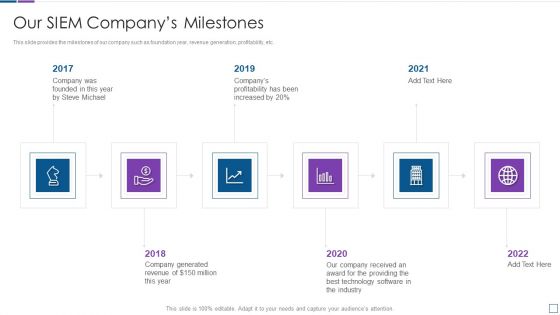
Real Time Assessment Of Security Threats Our SIEM Companys Milestones Slides PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Presenting real time assessment of security threats our siem companys milestones slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like our siem companys milestones. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
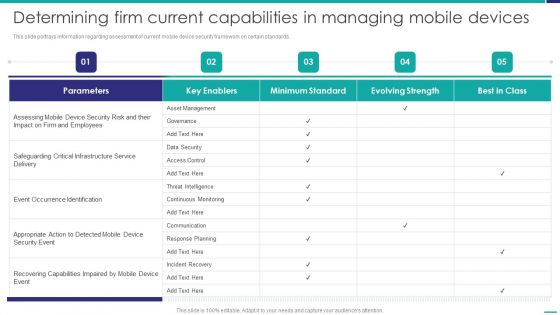
Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Deliver and pitch your topic in the best possible manner with this Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF. Use them to share invaluable insights on Asset Management, Critical Infrastructure, Recovering Capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
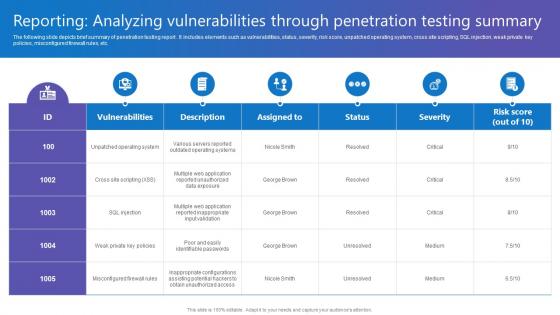
Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf
The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Do you know about Slidesgeeks Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc.
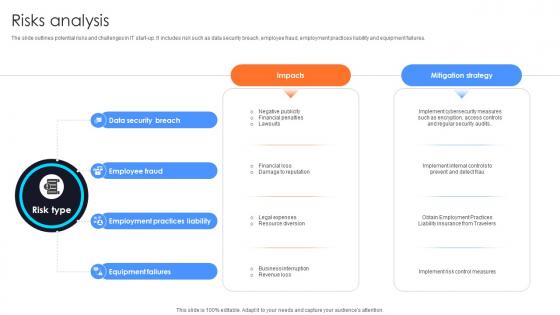
Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V
The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.This modern and well-arranged Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.
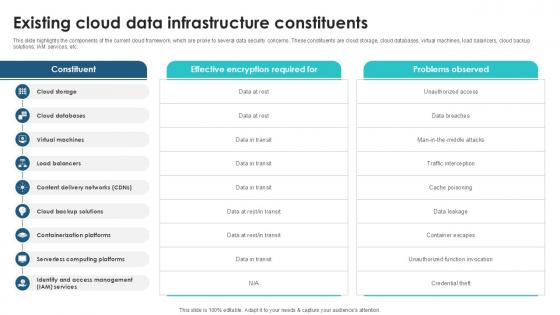
Existing Cloud Data Infrastructure Client Side Encryption PPT Sample
This slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Existing Cloud Data Infrastructure Client Side Encryption PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc.
Emotional Marketing Strategy To Nurture Key Strategies For Brands To Empower Customers Icons PDF
This slide showcases major branding techniques to empower customers which can assist managers in retaining them for long run. It provides details such as technology, support desk, security, feedback, compliance, etc. Take your projects to the next level with our ultimate collection of Emotional Marketing Strategy To Nurture Key Strategies For Brands To Empower Customers Icons PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
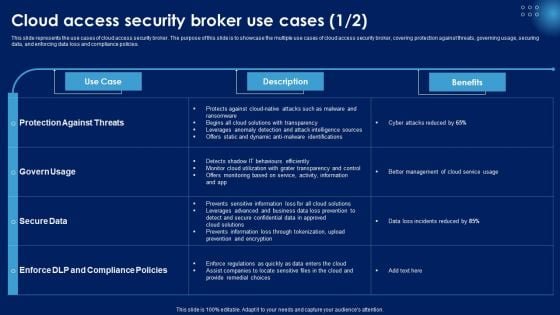
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Capital Raising Pitch Presentation Competitive Landscape For LBS App Designs PDF
Following slide differentiates the offering of companies with its competitors based on self-service features namely secure login, reward codes, customer support and popup notifications. Deliver and pitch your topic in the best possible manner with this Capital Raising Pitch Presentation Competitive Landscape For LBS App Designs PDF. Use them to share invaluable insights on Location Based Services, Offline Access To Content, Customer Support, Popup Notifications and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
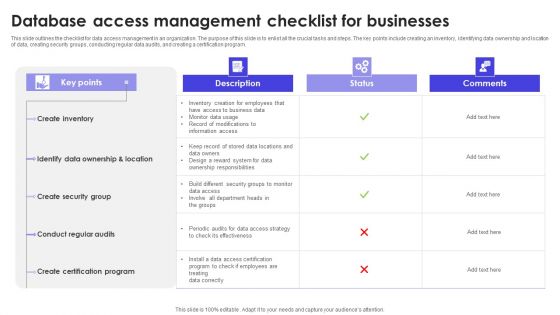
Database Access Management Checklist For Businesses Formats PDF
This slide outlines the checklist for data access management in an organization. The purpose of this slide is to enlist all the crucial tasks and steps. The key points include creating an inventory, identifying data ownership and location of data, creating security groups, conducting regular data audits, and creating a certification program. Showcasing this set of slides titled Database Access Management Checklist For Businesses Formats PDF. The topics addressed in these templates are Description, Status, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
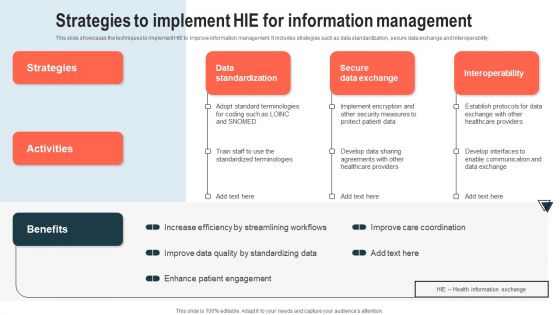
Strategies To Implement HIE For Information Management Graphics PDF
This slide showcases the techniques to implement HIE to improve information management. It includes strategies such as data standardization, secure data exchange and interoperability. If you are looking for a format to display your unique thoughts, then the professionally designed Strategies To Implement HIE For Information Management Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Strategies To Implement HIE For Information Management Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
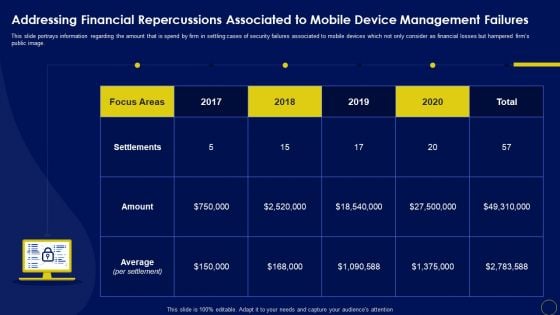
Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF.
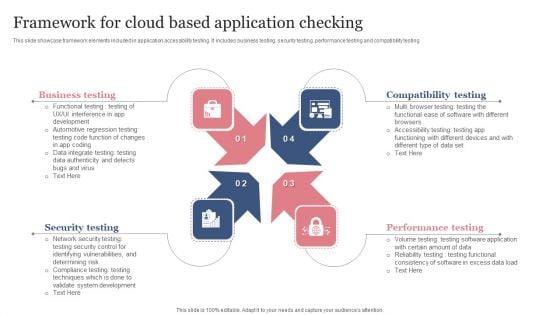
Framework For Cloud Based Application Checking Structure PDF
This slide showcase framework elements included in application accessibility testing. It includes business testing, security testing, performance testing and compatibility testing. Persuade your audience using this Framework For Cloud Based Application Checking Structure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Compatibility Testing, Performance Testing, Security Testing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
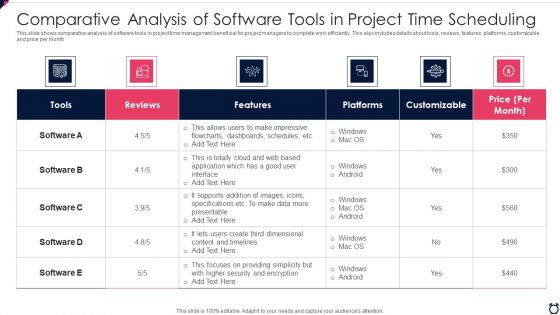
Comparative Analysis Of Software Tools In Project Time Scheduling Summary PDF
This slide shows comparative analysis of software tools in project time management beneficial for project managers to complete work efficiently. This also includes details about tools, reviews, features, platforms, customizable and price per month Showcasing this set of slides titled comparative analysis of software tools in project time scheduling summary pdf. The topics addressed in these templates are security, data, application. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
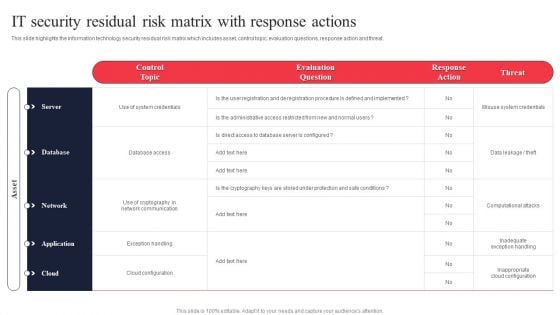
IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF.
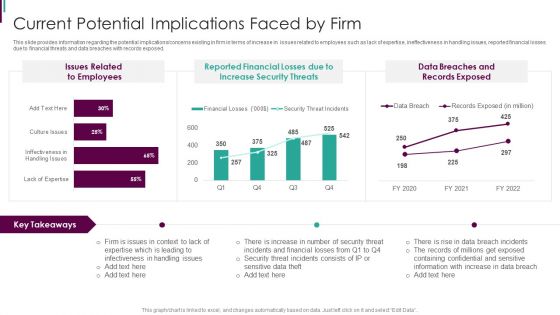
Developing Business Analytics Framework Current Potential Implications Faced By Firm Graphics PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this Developing Business Analytics Framework Current Potential Implications Faced By Firm Graphics PDF Use them to share invaluable insights on Reported Financial, Increase Security, Data Breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
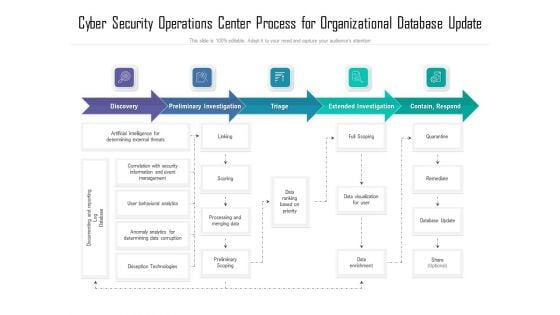
Cyber Security Operations Center Process For Organizational Database Update Ppt Show Deck PDF
Showcasing this set of slides titled cyber security operations center process for organizational database update ppt show deck pdf. The topics addressed in these templates are process, organizational, database. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Network Structure Analysis Model For Security Management Ppt Styles Icons PDF
Showcasing this set of slides titled network structure analysis model for security management ppt styles icons pdf. The topics addressed in these templates are structure, management, analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
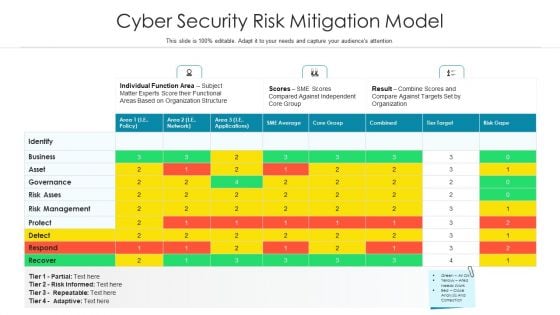
Cyber Security Risk Mitigation Model Ppt PowerPoint Presentation Infographics Sample PDF
Showcasing this set of slides titled cyber security risk mitigation model ppt powerpoint presentation infographics sample pdf. The topics addressed in these templates are risk management, functional areas based, subject matter experts score. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
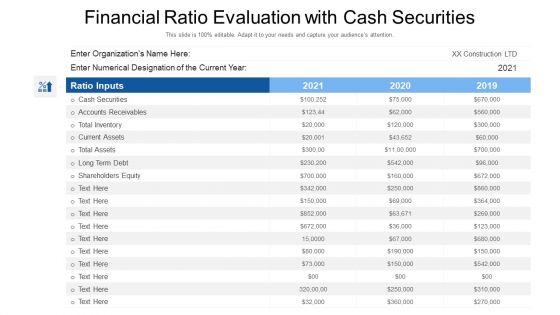
Financial Ratio Evaluation With Cash Securities Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled financial ratio evaluation with cash securities ppt powerpoint presentation file show pdf. The topics addressed in these templates are shareholders equity, current assets, accounts receivables. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
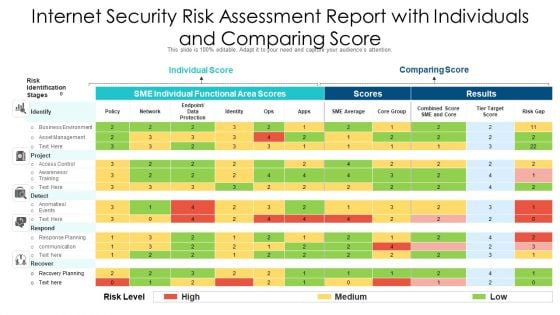
Internet Security Risk Assessment Report With Individuals And Comparing Score Ppt PowerPoint Presentation File Good PDF
Showcasing this set of slides titled internet security risk assessment report with individuals and comparing score ppt powerpoint presentation file good pdf. The topics addressed in these templates are individual score, comparing score, identify. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
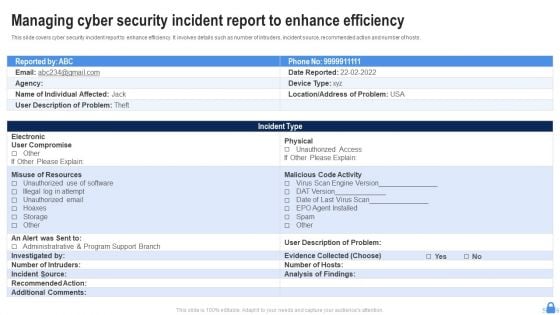
Managing Cyber Security Incident Report To Enhance Efficiency Ppt Professional Clipart PDF
Showcasing this set of slides titled Managing Cyber Security Incident Report To Enhance Efficiency Ppt Professional Clipart PDF. The topics addressed in these templates are Electronic, User Compromise, Misuse Resources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
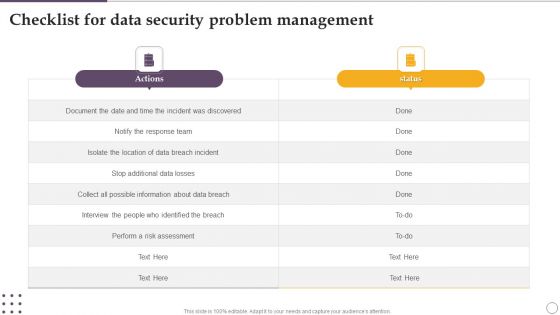
Checklist For Data Security Problem Management Ppt Visual Aids Deck PDF
Showcasing this set of slides titled Checklist For Data Security Problem Management Ppt Visual Aids Deck PDF. The topics addressed in these templates are Actions, Risk Assessment, About Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
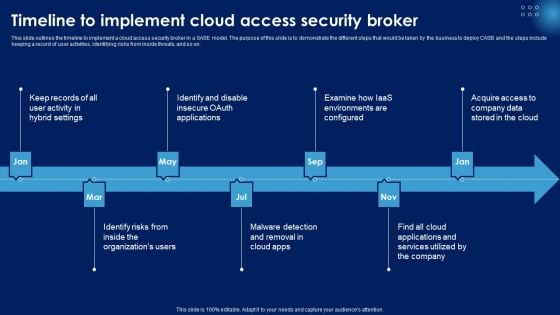
Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
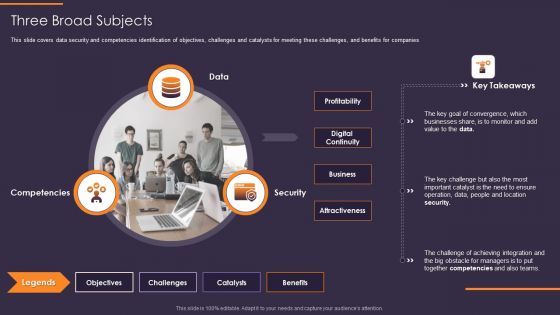
Convergence Strategy Information Three Broad Subjects Ppt Infographic Template Graphics Design PDF
This slide covers data security and competencies identification of objectives, challenges and catalysts for meeting these challenges, and benefits for companies. Presenting Convergence Strategy Information Three Broad Subjects Ppt Infographic Template Graphics Design PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Data, Security, Competencies, Objectives, Challenges, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Bluetooth Low Energy BLE Asset Tracking Technique Tech Asset Management Clipart Pdf
This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications.Do you know about Slidesgeeks Bluetooth Low Energy BLE Asset Tracking Technique Tech Asset Management Clipart Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications.

Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF
The following slide illustrates some SaaS security threats to enhance security practices and eliminate them. It includes elements such as phishing, account takeovers, lack of transparency etc. Showcasing this set of slides titled Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF. The topics addressed in these templates are Comprehending Risks, Phishing, Account Takeovers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.
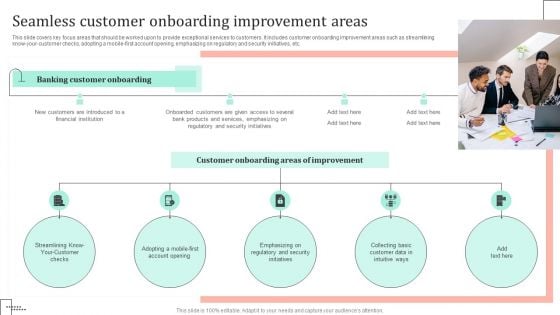
Omnichannel Strategy Implementation For Banking Solutions Seamless Customer Onboarding Improvement Areas Guidelines PDF
This slide covers key focus areas that should be worked upon to provide exceptional services to customers. It includes customer onboarding improvement areas such as streamlining know your customer checks, adopting a mobile first account opening, emphasizing on regulatory and security initiatives, etc. The Omnichannel Strategy Implementation For Banking Solutions Seamless Customer Onboarding Improvement Areas Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cash Flow Chart Invests Security Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this cash flow chart invests security ppt powerpoint presentation complete deck with slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
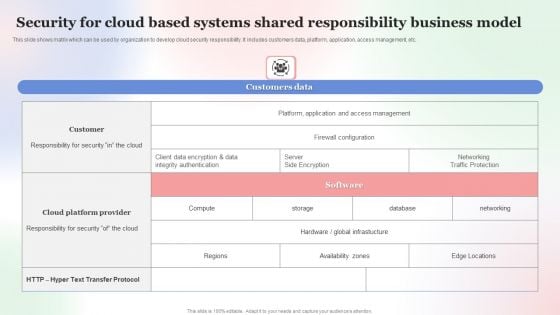
Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF
This slide shows matrix which can be used by organization to develop cloud security responsibility. It includes customers data, platform, application, access management, etc. Showcasing this set of slides titled Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF. The topics addressed in these templates are Security For Cloud Based, Systems Shared Responsibility, Business Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
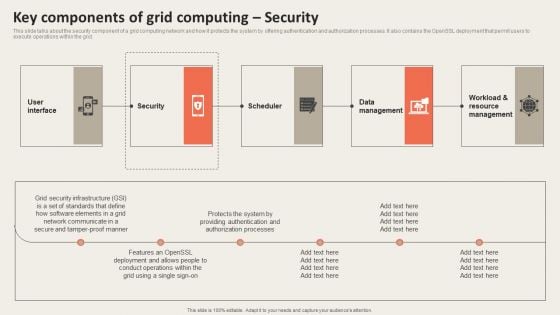
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
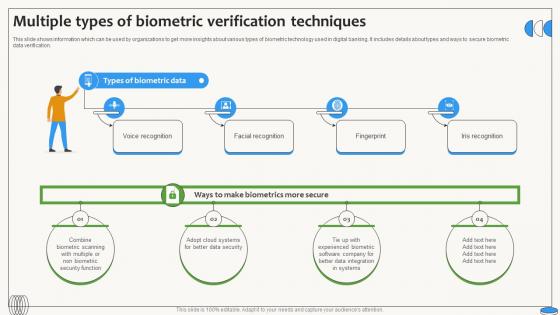
Multiple Types Of Biometric Verification Techniques Swipe Smartly A Practical Guide Fin SS V
This slide shows information which can be used by organizations to get more insights about various types of biometric technology used in digital banking. It includes details about types and ways to secure biometric data verification. Create an editable Multiple Types Of Biometric Verification Techniques Swipe Smartly A Practical Guide Fin SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiple Types Of Biometric Verification Techniques Swipe Smartly A Practical Guide Fin SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide shows information which can be used by organizations to get more insights about various types of biometric technology used in digital banking. It includes details about types and ways to secure biometric data verification.

E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
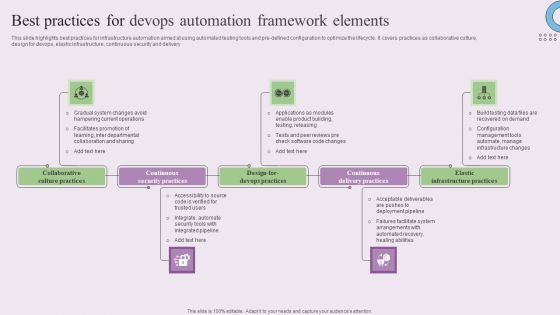
Best Practices For Devops Automation Framework Elements Themes PDF
This slide highlights best practices for infrastructure automation aimed at using automated testing tools and pre-defined configuration to optimize the lifecycle. It covers practices as collaborative culture, design for devops, elastic infrastructure, continuous security and delivery. Presenting Best Practices For Devops Automation Framework Elements Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Collaborative Culture Practices, Continuous Security Practices, Continuous Delivery Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Explore a selection of the finest CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in sixty four slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
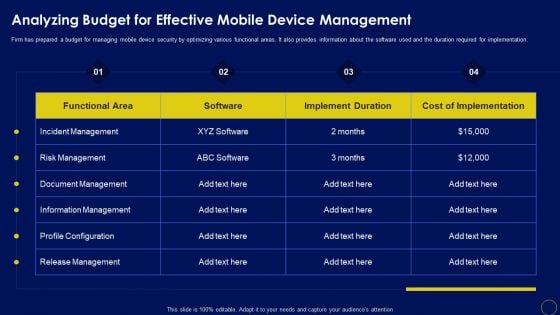
Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Integrating Data Privacy System Why Choose Us For Data Privacy Icons PDF
This slide explains why you should choose us, including faster product delivery to market, decreased complexity, and secured integrations. This slide explains why you should choose us, including faster product delivery to market, decreased complexity, and secured integrations. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Integrating Data Privacy System Why Choose Us For Data Privacy Icons PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Present our Arrows PowerPoint Templates because You can Bind your ideas with our PowerPoint Templates and Slides. They will add great value to the worth of your package. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Finance PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Success PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level.Use these PowerPoint slides for presentations relating to Internet Virus, technology, arrows, signs, finance, success. The prominent colors used in the PowerPoint template are Yellow, Black, White. Professionals tell us our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. You can be sure our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 will make you look like a winner. PowerPoint presentation experts tell us our arrows PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Our Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113 are like angels. They take extraordinary care of your thoughts.
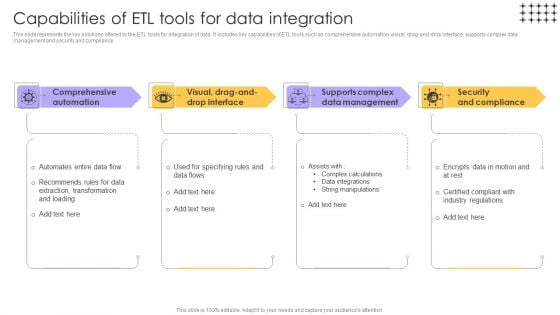
Tools For HR Business Analytics Capabilities Of ETL Tools For Data Integration Elements PDF
This slide represents the key solutions offered by the ETL tools for integration of data. It includes key capabilities of ETL tools such as comprehensive automation, visual, drag-and-drop interface, supports complex data management and security and compliance. Slidegeeks is here to make your presentations a breeze with Tools For HR Business Analytics Capabilities Of ETL Tools For Data Integration Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Company Inward Marketing Strategy Key Barriers Statistics Icons PDF
This slide covers top challenges of inbound marketing strategy that reduces its effectiveness. It includes generation of traffic, proving ROI for marketing activities, securing budget, technology update, website management, hiring talent and training team.Pitch your topic with ease and precision using this Company Inward Marketing Strategy Key Barriers Statistics Icons PDF. This layout presents information on Difficult To Search, Insufficient Traffic, Setting Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Ppt Pictures File Formats PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technologies, financial control procedures, operating system maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
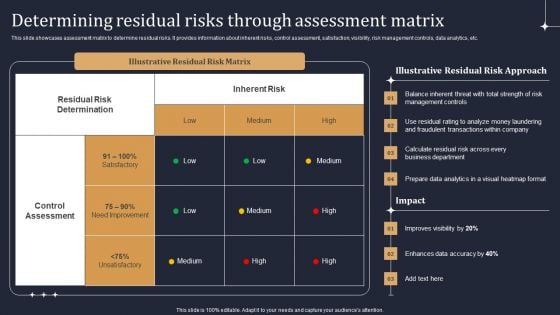
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
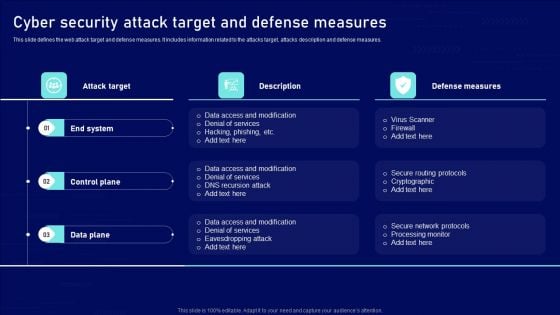
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
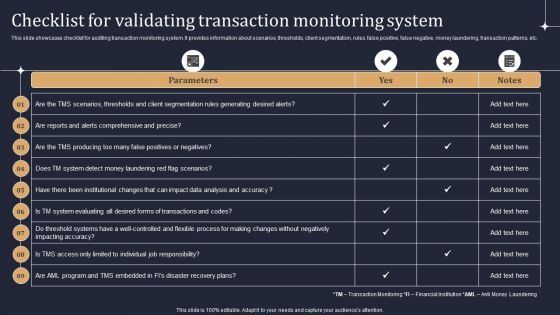
KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF
This slide showcases checklist for auditing transaction monitoring system. It provides information about scenarios, thresholds, client segmentation, rules, false positive, false negative, money laundering, transaction patterns, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Government Strategies To Tackle Identity Fraud Background PDF
This slide showcases approaches followed by government to prevent fraud. This template focuses on following techniques to keep personal information safe and secure. It includes information related to reliable identity checks, early detection of fraud, etc. Persuade your audience using this Government Strategies To Tackle Identity Fraud Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Reliable Identity Checks, Early Detection Identity Fraud, Fast Assistance Victims Identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
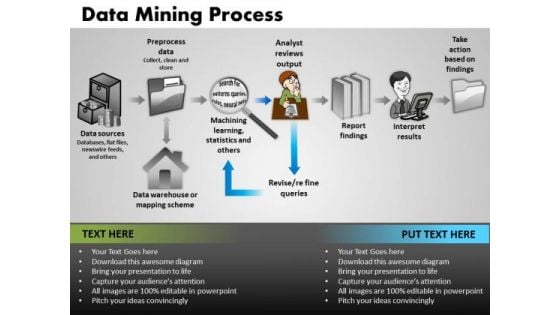
PowerPoint Presentation Designs Sales Data Mining Process Ppt Slides
PowerPoint Presentation Designs Sales Data Mining Process PPT Slides backgrounds-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Secure your promotion with our PowerPoint Presentation Designs Sales Data Mining Process Ppt Slides. Download without worries with our money back guaranteee.
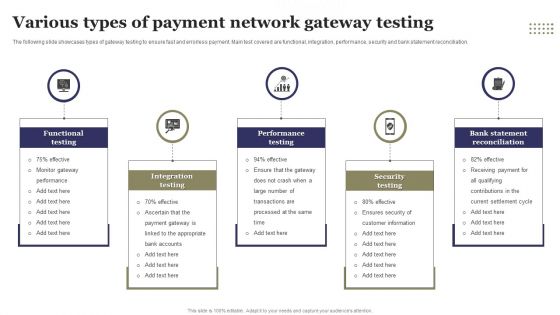
Various Types Of Payment Network Gateway Testing Ppt File Objects PDF
The following slide showcases types of gateway testing to ensure fast and errorless payment. Main test covered are functional, integration, performance, security and bank statement reconciliation. Persuade your audience using this Various Types Of Payment Network Gateway Testing Ppt File Objects PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Functional Testing, Integration Testing, Performance Testing, Security Testing . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
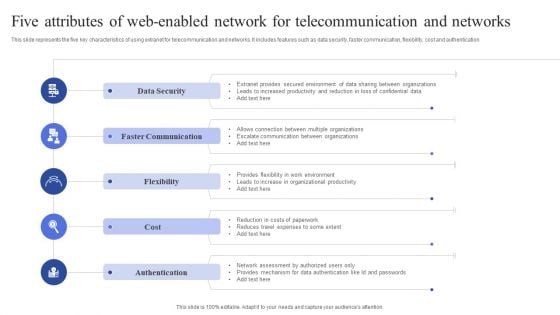
Five Attributes Of Web Enabled Network For Telecommunication And Networks Guidelines PDF
This slide represents the five key characteristics of using extranet for telecommunication and networks. It includes features such as data security, faster communication, flexibility, cost and authentication. Persuade your audience using this Five Attributes Of Web Enabled Network For Telecommunication And Networks Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Security, Faster Communication, Flexibility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































