Construction Safety

Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
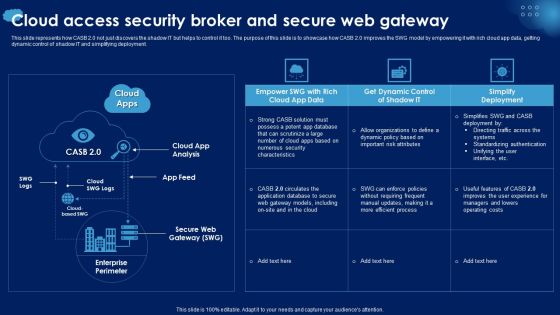
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
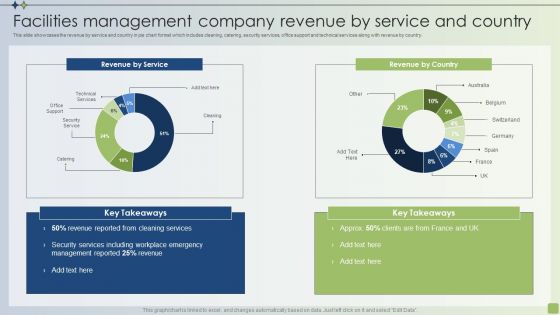
Strategic FM Services Facilities Management Company Revenue By Service And Country Topics PDF
This slide showcases the revenue by service and country in pie chart format which includes cleaning, catering, security services, office support and technical services along with revenue by country. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategic FM Services Facilities Management Company Revenue By Service And Country Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategic FM Services Facilities Management Company Revenue By Service And Country Topics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
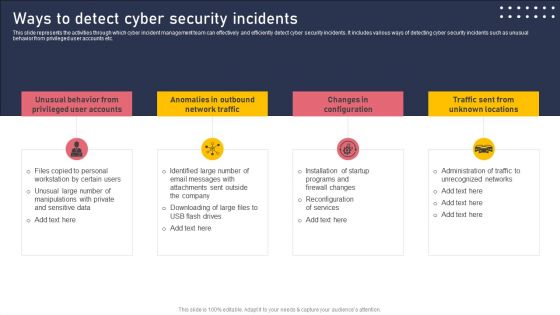
Ways To Detect Cyber Security Incidents Template PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Ways To Detect Cyber Security Incidents Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Ways To Detect Cyber Security Incidents Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Data Protection And Information Security Policy And Procedure Guidelines PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Protection And Information Security Policy And Procedure Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Protection And Information Security Policy And Procedure Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
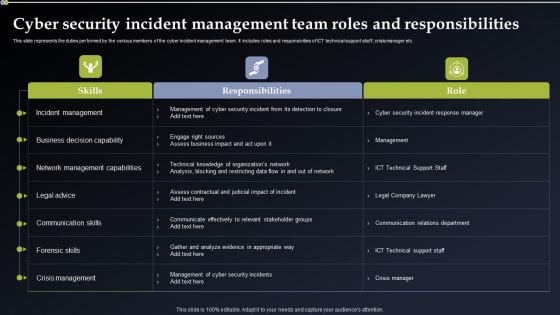
Cyber Security Incident Management Team Roles And Responsibilities Structure PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Incident Management Team Roles And Responsibilities Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Incident Management Team Roles And Responsibilities Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
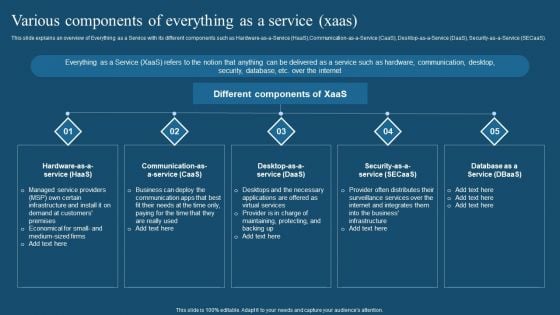
Recent Technologies In IT Industry Various Components Of Everything As A Service Xaas Brochure PDF
This slide explains an overview of Everything as a Service with its different components such as Hardware-as-a-Service HaaS,Communication-as a Service CaaS, Desktop-as a Service DaaS, Security as a Service SECaaS. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Recent Technologies In IT Industry Various Components Of Everything As A Service Xaas Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Recent Technologies In IT Industry Various Components Of Everything As A Service Xaas Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
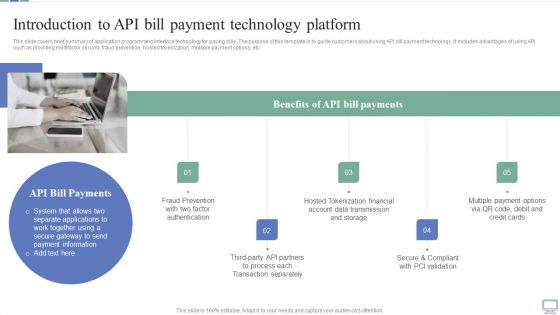
Omnichannel Banking Services Platform Introduction To API Bill Payment Technology Platform Elements PDF
This slide covers brief summary of application programming interface technology for paying bills. The purpose of this template is to guide customers about using API bill payment technology. It includes advantages of using API such as providing multifactor security, fraud prevention, hosted tokenization, multiple payment options, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Omnichannel Banking Services Platform Introduction To API Bill Payment Technology Platform Elements PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Omnichannel Banking Services Platform Introduction To API Bill Payment Technology Platform Elements PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
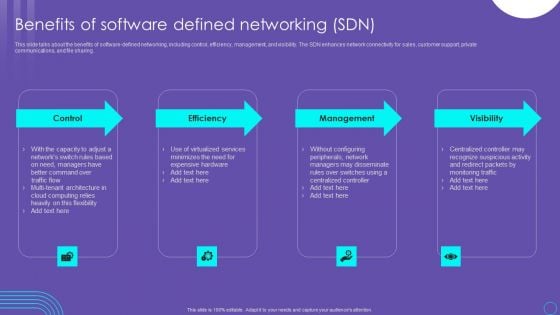
SDN Security Architecture Benefits Of Software Defined Networking SDN Information PDF
This slide talks about the benefits of software defined networking, including control, efficiency, management, and visibility. The SDN enhances network connectivity for sales, customer support, private communications, and file sharing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward SDN Security Architecture Benefits Of Software Defined Networking SDN Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal SDN Security Architecture Benefits Of Software Defined Networking SDN Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
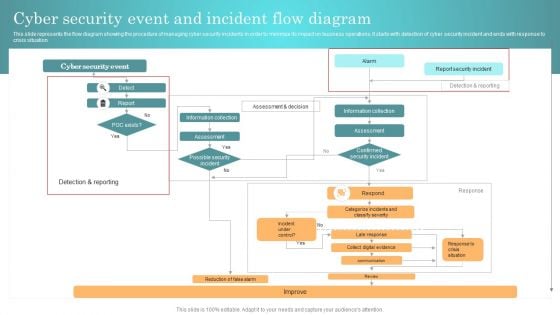
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
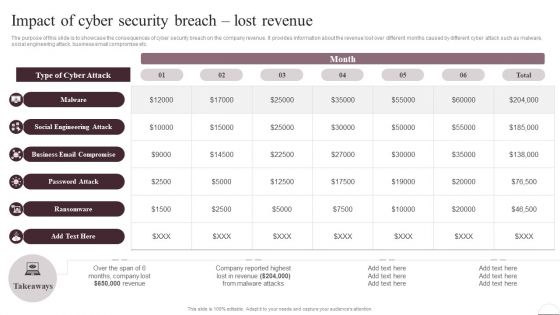
Prevention Of Information Impact Of Cyber Security Breach Lost Revenue Slides PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Prevention Of Information Impact Of Cyber Security Breach Lost Revenue Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Prevention Of Information Impact Of Cyber Security Breach Lost Revenue Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
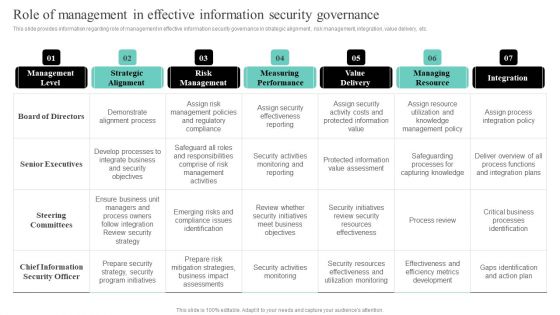
IT Cost Reduction Strategiesrole Of Management In Effective Information Security Clipart PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Cost Reduction Strategiesrole Of Management In Effective Information Security Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Cost Reduction Strategiesrole Of Management In Effective Information Security Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
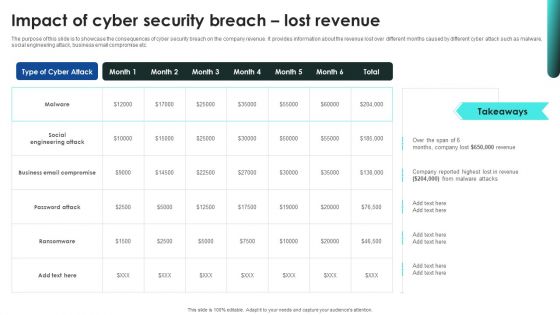
Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach Lost Revenue Template PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach Lost Revenue Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach Lost Revenue Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
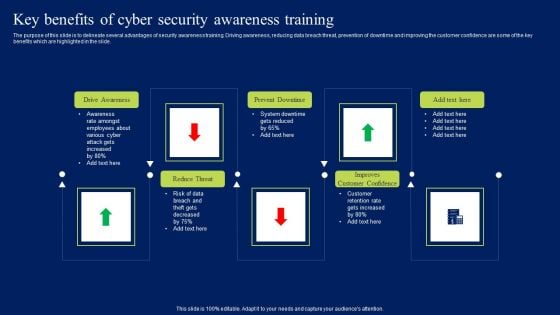
Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
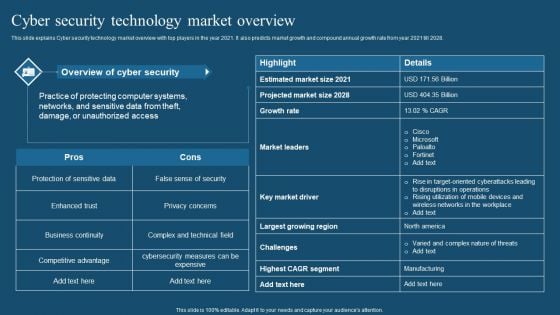
Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF
This slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
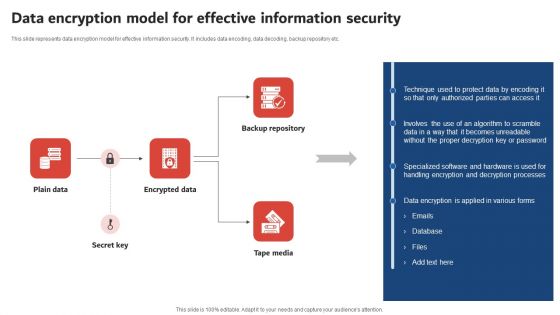
Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF
This slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
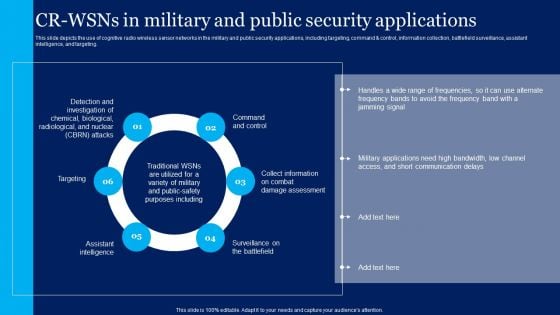
Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
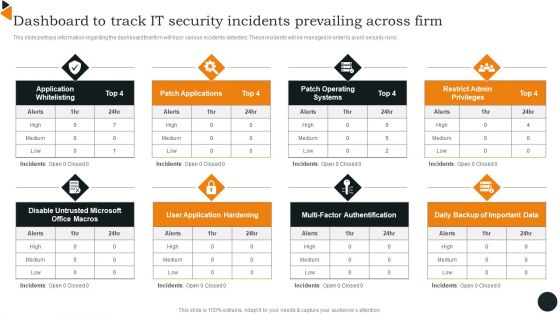
Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
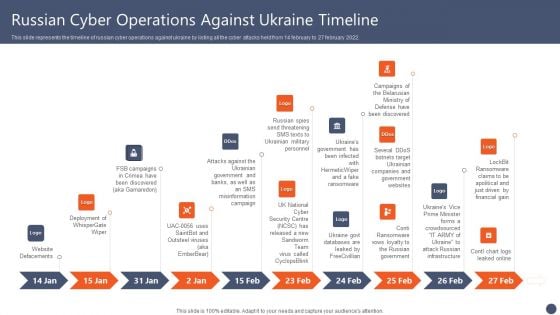
Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
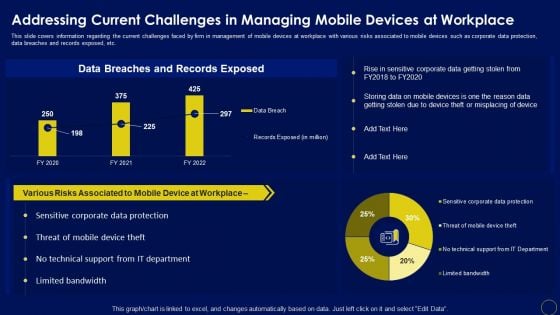
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
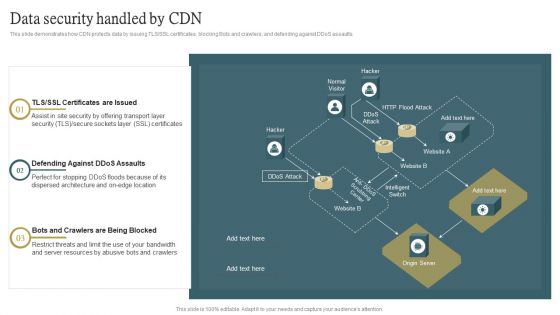
Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
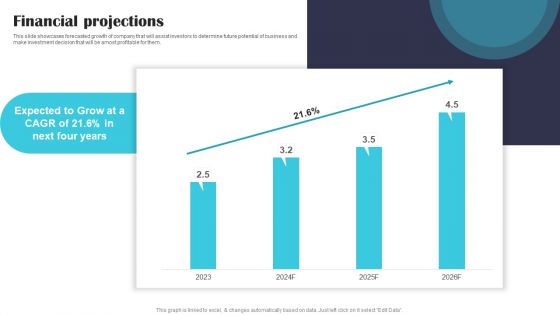
Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF
This slide showcases forecasted growth of company that will assist investors to determine future potential of business and make investment decision that will be amost profitable for them. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
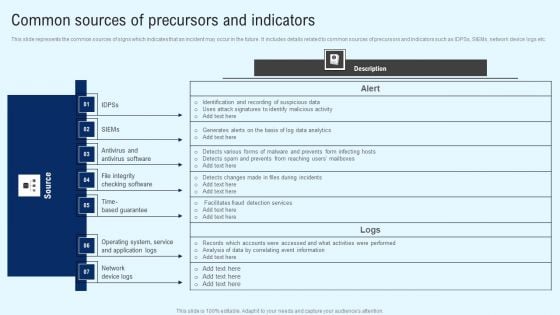
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
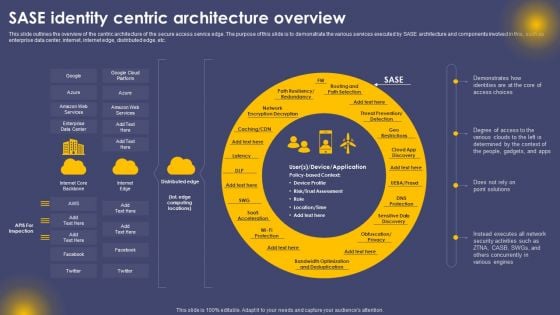
SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF
This slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
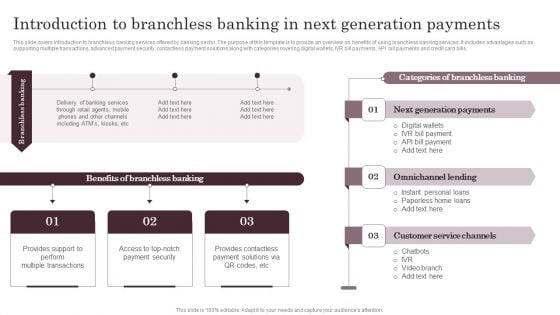
Introduction To Branchless Banking In Next Generation Payments Structure PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Introduction To Branchless Banking In Next Generation Payments Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Introduction To Branchless Banking In Next Generation Payments Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Omnichannel Strategy Implementation For Banking Solutions Factors Driving Usability Of Omnichannel Inspiration PDF
This slide covers imperative drivers that helps in usability of omnichannel banking services. It includes factors such a multi-channel experience, ease of integration, customizable, highly secure and easy adaptability. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Omnichannel Strategy Implementation For Banking Solutions Factors Driving Usability Of Omnichannel Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Omnichannel Strategy Implementation For Banking Solutions Factors Driving Usability Of Omnichannel Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
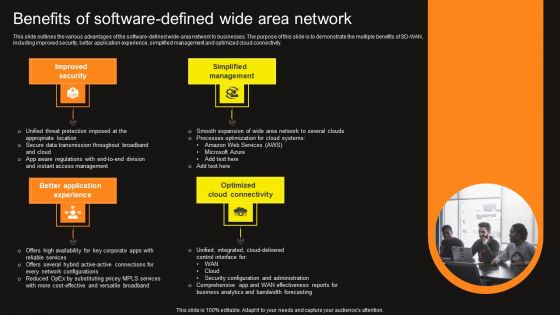
Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF
This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
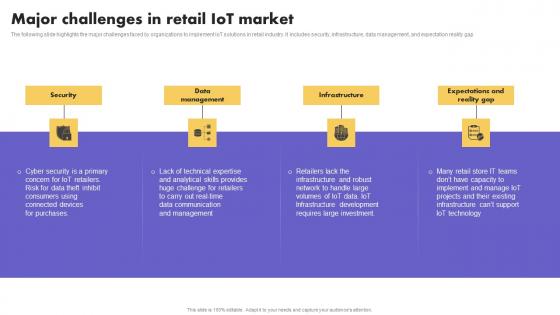
IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap
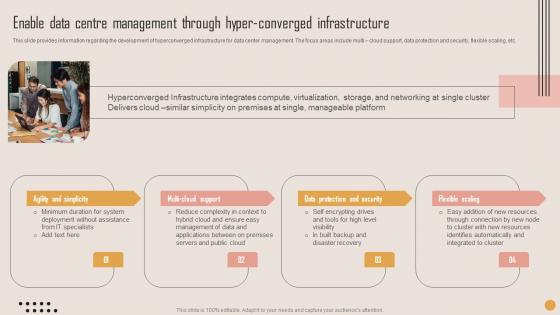
Enable Data Centre Management Playbook For Strategic Actions To Improve IT Performance Structure Pdf
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Enable Data Centre Management Playbook For Strategic Actions To Improve IT Performance Structure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Enable Data Centre Management Playbook For Strategic Actions To Improve IT Performance Structure Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc.

Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf
This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation.
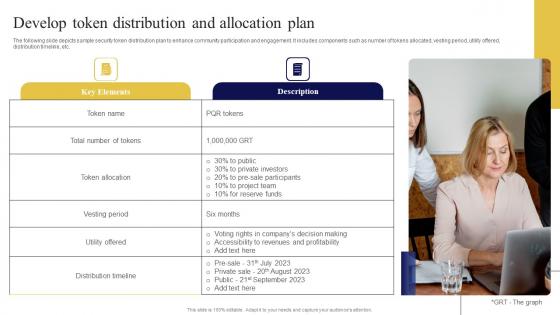
Develop Token Distribution And Exploring Investment Opportunities Template Pdf
The following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc. Cafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Develop Token Distribution And Exploring Investment Opportunities Template Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Develop Token Distribution And Exploring Investment Opportunities Template Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc.

Benefits And Features Of Healthcare Deploying IoT Solutions For Enhanced Healthcare Microsoft Pdf
Following slide showcases essential features and benefits of using IoT based healthcare asset tracking. It includes pointers such as real time asset location, asset security, maintenance, optimization etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Benefits And Features Of Healthcare Deploying IoT Solutions For Enhanced Healthcare Microsoft Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Benefits And Features Of Healthcare Deploying IoT Solutions For Enhanced Healthcare Microsoft Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide showcases essential features and benefits of using IoT based healthcare asset tracking. It includes pointers such as real time asset location, asset security, maintenance, optimization etc.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
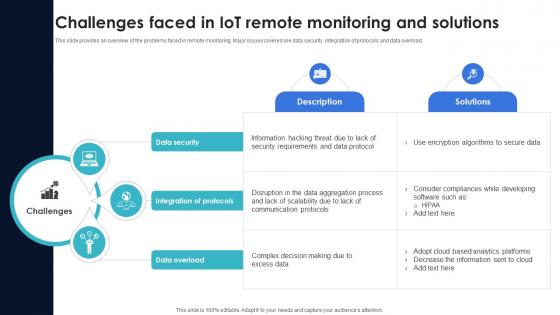
Optimization Of IoT Remote Monitoring Challenges Faced In IoT Remote Monitoring And Solutions IoT SS V
This slide provides an overview of the problems faced in remote monitoring. Major issues covered are data security, integration of protocols and data overload. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Optimization Of IoT Remote Monitoring Challenges Faced In IoT Remote Monitoring And Solutions IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Optimization Of IoT Remote Monitoring Challenges Faced In IoT Remote Monitoring And Solutions IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides an overview of the problems faced in remote monitoring. Major issues covered are data security, integration of protocols and data overload.
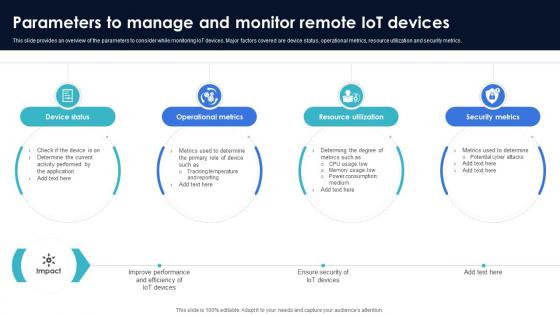
Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V
This slide provides an overview of the parameters to consider while monitoring IoT devices. Major factors covered are device status, operational metrics, resource utilization and security metrics. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides an overview of the parameters to consider while monitoring IoT devices. Major factors covered are device status, operational metrics, resource utilization and security metrics.
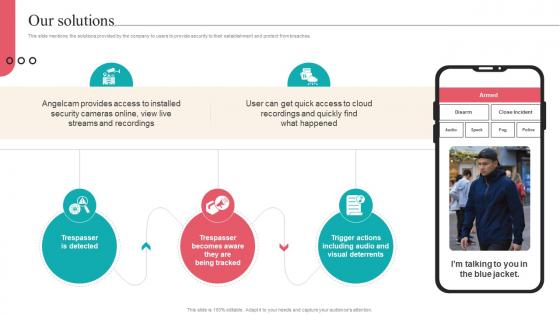
Our Solutions Camera Management Platform Investor Funding Elevator Pitch Deck
This slide mentions the solutions provided by the company to users to provide security to their establishment and protect from breaches. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Our Solutions Camera Management Platform Investor Funding Elevator Pitch Deck template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Our Solutions Camera Management Platform Investor Funding Elevator Pitch Deck that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide mentions the solutions provided by the company to users to provide security to their establishment and protect from breaches.
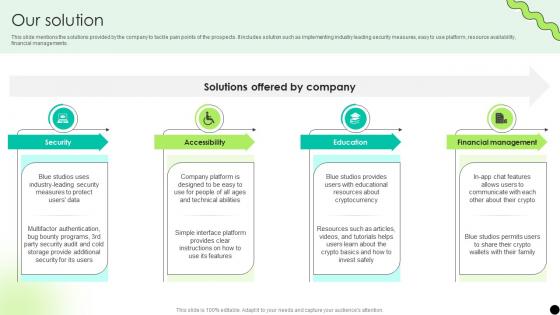
Our Solution Digital Payment Platform Pitch Deck
This slide mentions the solutions provided by the company to tackle pain points of the prospects. It includes solution such as implementing industry leading security measures, easy to use platform, resource availability, financial managements. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Our Solution Digital Payment Platform Pitch Deck template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Our Solution Digital Payment Platform Pitch Deck that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide mentions the solutions provided by the company to tackle pain points of the prospects. It includes solution such as implementing industry leading security measures, easy to use platform, resource availability, financial managements.

IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT Ss V
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc.

Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V
This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems.
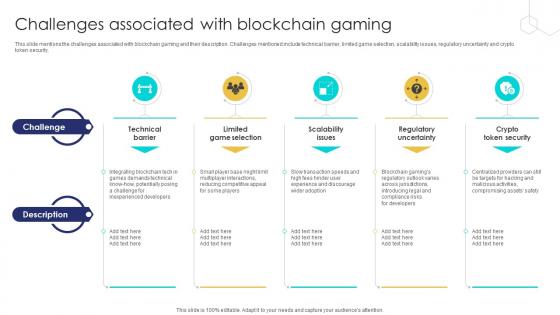
Unlocking The Potential Of Challenges Associated With Blockchain Gaming BCT SS V
This slide mentions the challenges associated with blockchain gaming and their description. Challenges mentioned include technical barrier, limited game selection, scalability issues, regulatory uncertainty and crypto token security. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Unlocking The Potential Of Challenges Associated With Blockchain Gaming BCT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Unlocking The Potential Of Challenges Associated With Blockchain Gaming BCT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide mentions the challenges associated with blockchain gaming and their description. Challenges mentioned include technical barrier, limited game selection, scalability issues, regulatory uncertainty and crypto token security.

Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses
This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc.
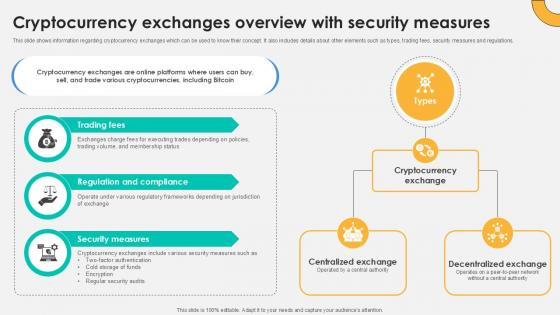
Cryptocurrency Exchanges Overview Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cryptocurrency Exchanges Overview Everything About Bitcoin PPT PowerPoint Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cryptocurrency Exchanges Overview Everything About Bitcoin PPT PowerPoint Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations.

Multiple Risks Associated With Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows detailed information which can be used to evaluate various types of risks associated with Bitcoin . These risks are price volatility, regulatory uncertainty, security vulnerabilities, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Multiple Risks Associated With Everything About Bitcoin PPT PowerPoint Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Multiple Risks Associated With Everything About Bitcoin PPT PowerPoint Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows detailed information which can be used to evaluate various types of risks associated with Bitcoin . These risks are price volatility, regulatory uncertainty, security vulnerabilities, etc.

Transforming Manufacturing With Automation Digital Twin Technology Download PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Transforming Manufacturing With Automation Digital Twin Technology Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Transforming Manufacturing With Automation Digital Twin Technology Download PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF
This slide covers the policies for managing compliance in multi cloud such as securing cloud user information, optimizing resource usage and value, optimizing system and resource usage etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
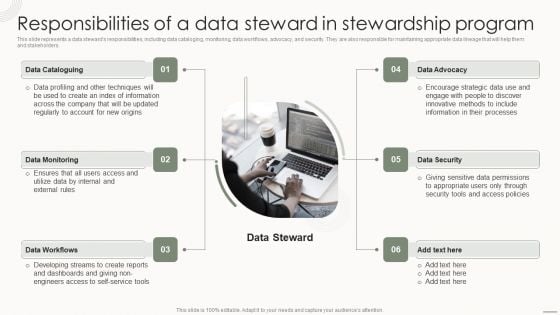
Data Governance IT Responsibilities Of A Data Steward In Stewardship Program Introduction PDF
This slide represents a data stewards responsibilities, including data cataloging, monitoring, data workflows, advocacy, and security. They are also responsible for maintaining appropriate data lineage that will help them and stakeholders. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Governance IT Responsibilities Of A Data Steward In Stewardship Program Introduction PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Governance IT Responsibilities Of A Data Steward In Stewardship Program Introduction PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Key Features And Benefits Of Cloud Project Management Topics PDF
The following slide depicts major features and benefits of cloud based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Features And Benefits Of Cloud Project Management Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Features And Benefits Of Cloud Project Management Topics PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
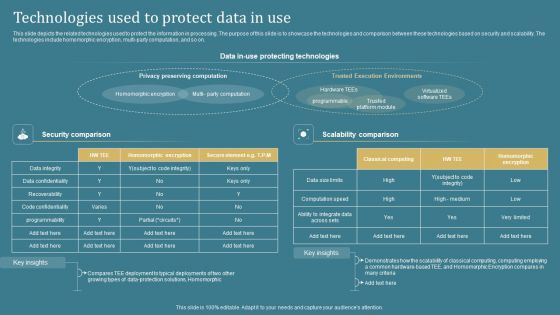
Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Improving Business Procedures Enterprise Resource Planning System Drafting ERP Budget To Plan Cost Professional PDF
The following slide covers the enterprise resource planning ERP budget to project and estimate software cost accurately. It includes elements such as hardware, software, facility, network, security, contingency etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Improving Business Procedures Enterprise Resource Planning System Drafting ERP Budget To Plan Cost Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Improving Business Procedures Enterprise Resource Planning System Drafting ERP Budget To Plan Cost Professional PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
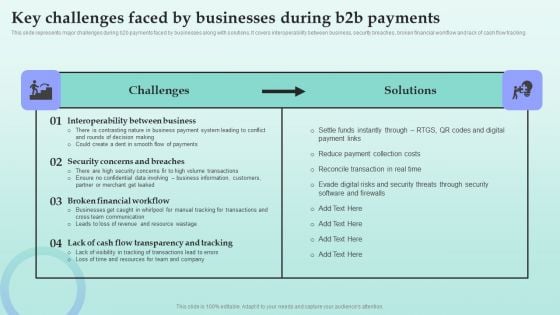
Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
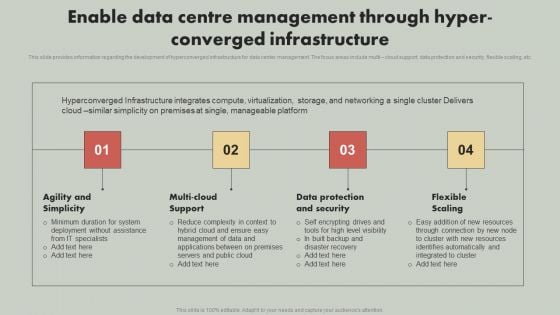
IT Reducing Costs And Management Tips Enable Data Centre Management Through Hyper Converged Infrastructure Elements PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Reducing Costs And Management Tips Enable Data Centre Management Through Hyper Converged Infrastructure Elements PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Reducing Costs And Management Tips Enable Data Centre Management Through Hyper Converged Infrastructure Elements PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
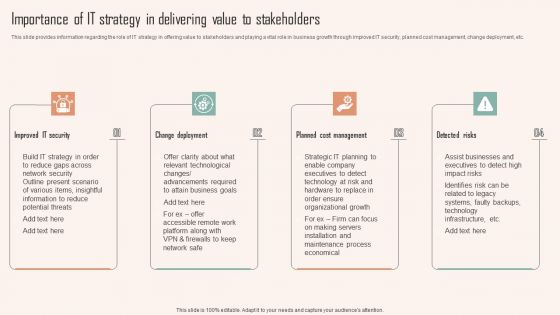
Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
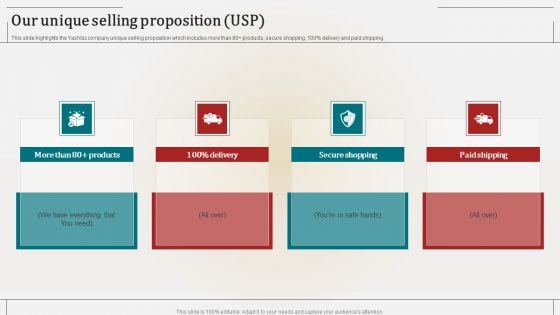
Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF
This slide highlights the Yashbiz company unique selling proposition which includes more than 80 products, secure shopping, 100 percent delivery and paid shipping. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF
This slide represents the steps to be considered by organizations to maximize the benefits of WAF. The purpose of this slide is to showcase the best practices businesses can consider for successful web application firewall implementation, such as support for app security goals, evaluation and testing, and resource listing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
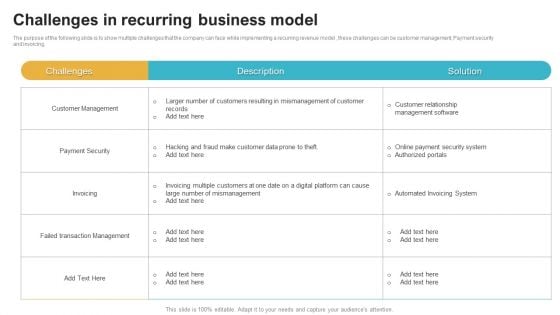
Saas Continuous Income Generation Model For Software Startup Challenges In Recurring Business Model Guidelines PDF
The purpose of the following slide is to show multiple challenges that the company can face while implementing a recurring revenue model , these challenges can be customer management, Payment security and invoicing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Saas Continuous Income Generation Model For Software Startup Challenges In Recurring Business Model Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Saas Continuous Income Generation Model For Software Startup Challenges In Recurring Business Model Guidelines PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.


 Continue with Email
Continue with Email

 Home
Home


































