Construction Safety
Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF
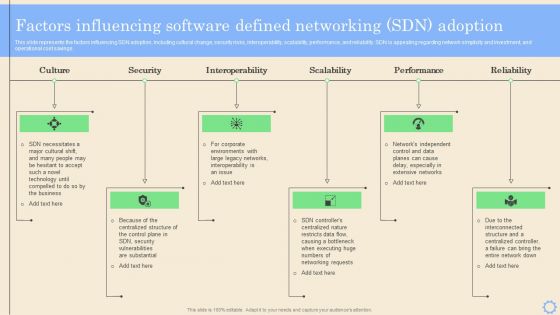
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
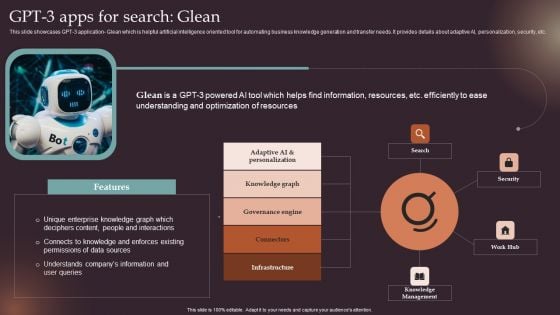
Comprehensive Resource Guide To Master GPT 3 GPT 3 Apps For Search Glean Inspiration PDF
Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF
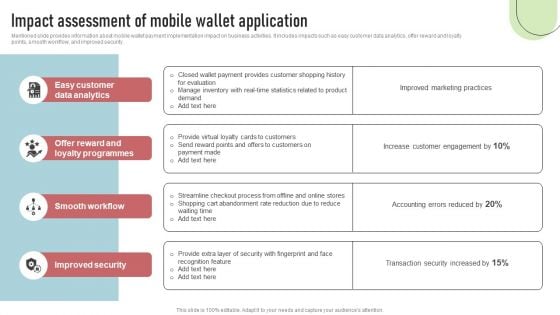
Mentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Retail Outlet Opening To Enhance Product Sale Crafting Comprehensive Business Graphics PDF
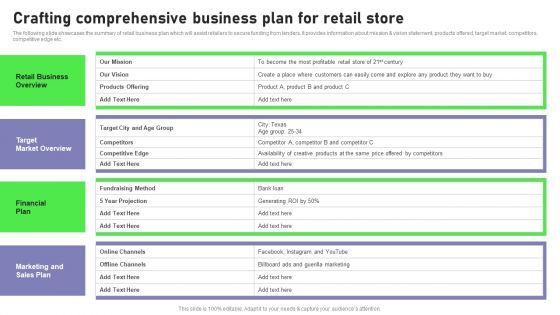
The following slide showcases the summary of retail business plan which will assist retailers to secure funding from lenders. It provides information about mission and vision statement, products offered, target market, competitors, competitive edge etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Retail Outlet Opening To Enhance Product Sale Crafting Comprehensive Business Graphics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Retail Outlet Opening To Enhance Product Sale Crafting Comprehensive Business Graphics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
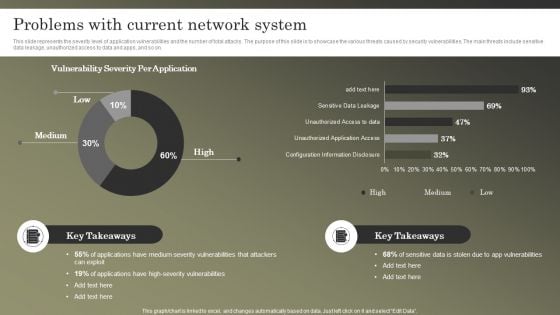
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
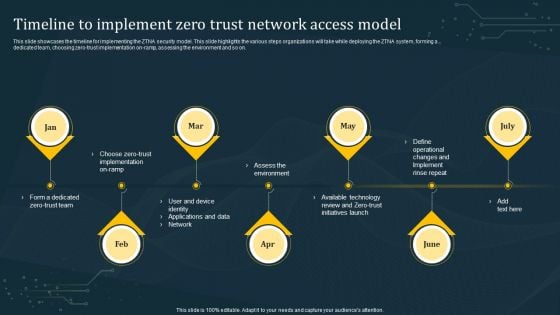
Timeline To Implement Zero Trust Network Access Model Rules PDF
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline To Implement Zero Trust Network Access Model Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline To Implement Zero Trust Network Access Model Rules PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Agile Approach In Information Technology Projects Seven Properties Of Crystal Clear Themes PDF
This slide covers properties of crystal clear programming such as easy access to users, personal safety, focus, agile technical environment, frequent delivery, reflection improvement, osmotic communication etc., Slidegeeks has constructed Agile Approach In Information Technology Projects Seven Properties Of Crystal Clear Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
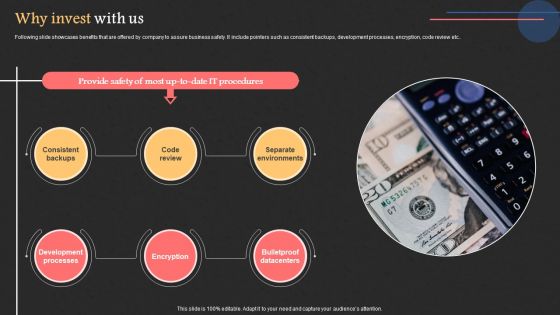
Project Management Software Capital Raising Deck Why Invest With Us Download PDF
Following slide showcases benefits that are offered by company to assure business safety. It include pointers such as consistent backups, development processes, encryption, code review etc. Slidegeeks has constructed Project Management Software Capital Raising Deck Why Invest With Us Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
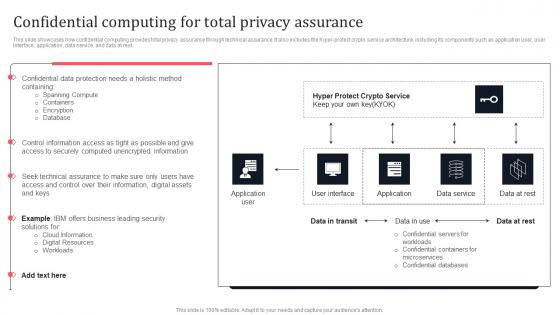
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc.
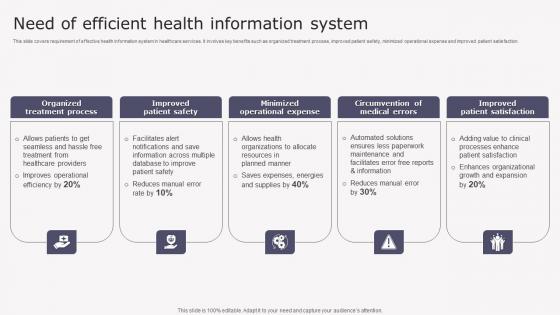
Need Of Efficient Health Transforming Medicare Services Using Health Brochure Pdf
This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction. Slidegeeks has constructed Need Of Efficient Health Transforming Medicare Services Using Health Brochure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction.

Space Exploration By Integrating IoT Technology IoT In Orbit Unleashing The Power IoT SS V
This slide outlines internet of things technology use cases in exploring space and completing mission. It includes use cases such as astronaut safety, surrounding monitoring, autonomous rovers, and astronauts health monitoring. Slidegeeks has constructed Space Exploration By Integrating IoT Technology IoT In Orbit Unleashing The Power IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines internet of things technology use cases in exploring space and completing mission. It includes use cases such as astronaut safety, surrounding monitoring, autonomous rovers, and astronauts health monitoring.
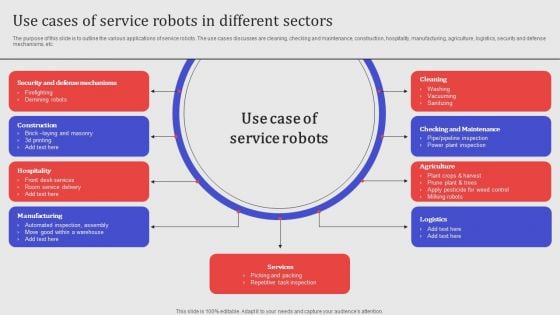
Use Cases Of Service Robots In Different Sectors Ideas PDF
The purpose of this slide is to outline the various applications of service robots. The use cases discusses are cleaning, checking and maintenance, construction, hospitality, manufacturing, agriculture, logistics, security and defense mechanisms, etc. Slidegeeks has constructed Use Cases Of Service Robots In Different Sectors Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
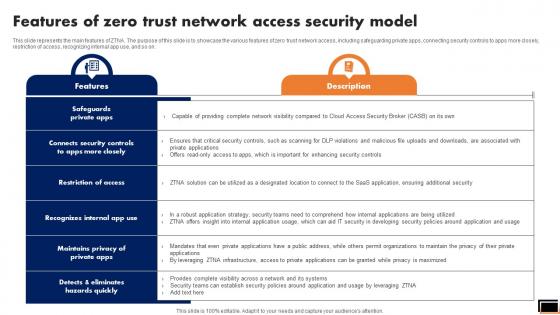
Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
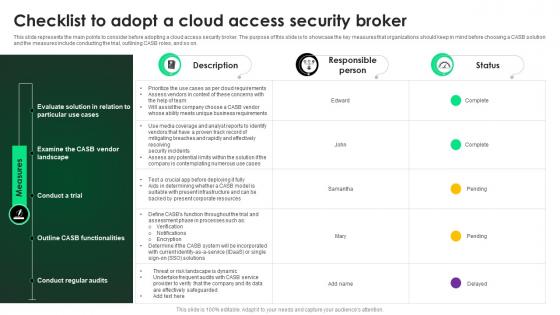
CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers. This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on.

CASB 2 0 IT Steps To Deploy Cloud Access Security Broker
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Steps To Deploy Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Steps To Deploy Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model.

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication.
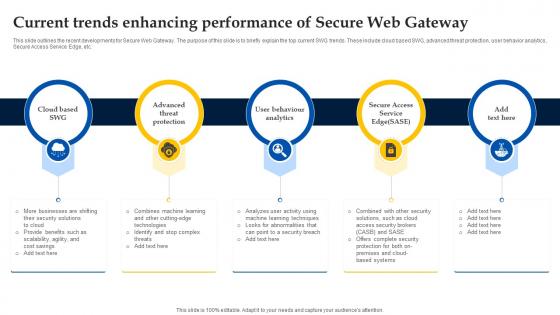
Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.
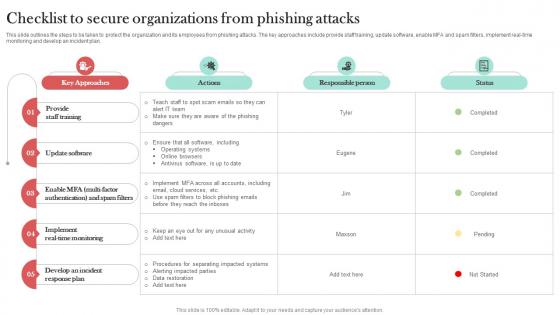
Checklist To Secure Organizations From Man In The Middle Phishing IT
This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Checklist To Secure Organizations From Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Checklist To Secure Organizations From Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan.
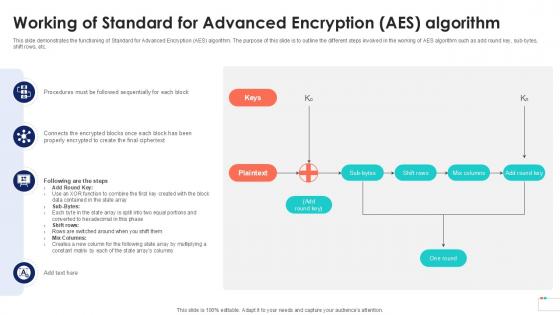
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.

Piggy Bank On Dollar Coins Savings PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Piggy Bank On Dollar Coins Savings PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Download our Business PowerPoint Templates because It can Bubble and burst with your ideas. Present our Marketing PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts.Use these PowerPoint slides for presentations relating to Business concept, security, money, business, marketing, finance. The prominent colors used in the PowerPoint template are Yellow, Pink, Black. Construct an enviable career for yourself. Lay the foundation with our Piggy Bank On Dollar Coins Savings PowerPoint Templates Ppt Backgrounds For Slides 0213.

Online Payment Techniques Best Practices To Maintain Digital Wallet Security
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Online Payment Techniques Best Practices To Maintain Digital Wallet Security template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Online Payment Techniques Best Practices To Maintain Digital Wallet Security that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.

Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf
The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties.
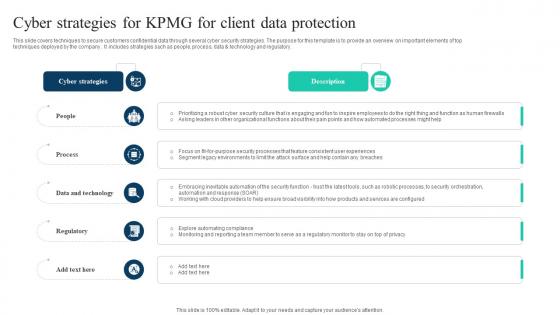
The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
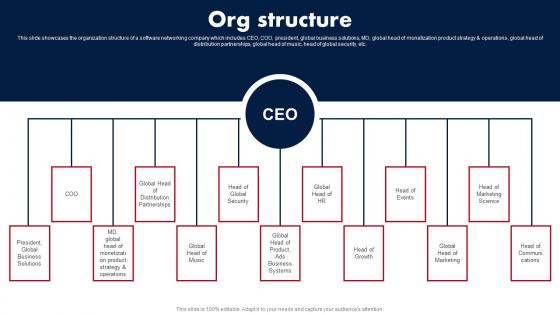
Org Structure E Media Platform Investor Fund Raising Pictures PDF
This slide showcases the organization structure of a software networking company which includes CEO, COO, president, global business solutions, MD, global head of monetization product strategy and operations, global head of distribution partnerships, global head of music, head of global security, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Org Structure E Media Platform Investor Fund Raising Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Org Structure E Media Platform Investor Fund Raising Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases the organization structure of a software networking company which includes CEO, COO, president, global business solutions, MD, global head of monetization product strategy and operations, global head of distribution partnerships, global head of music, head of global security, etc.
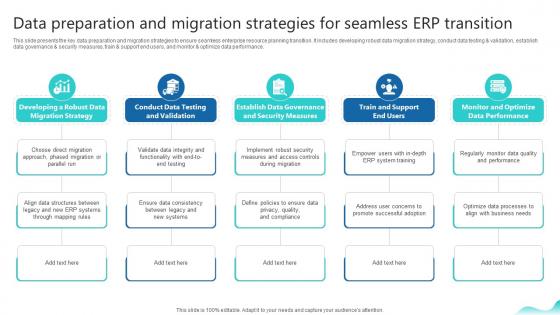
Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V
This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
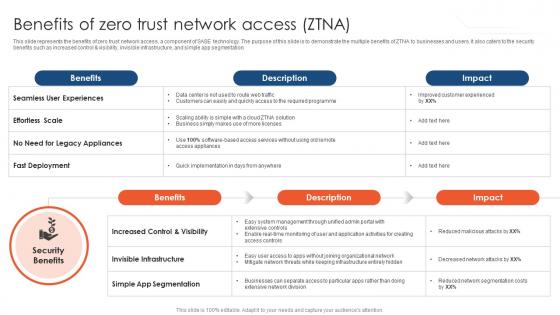
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
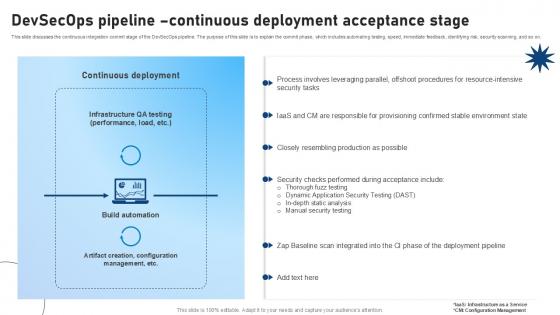
Devsecops Pipeline Continuous Deployment Acceptance Stage Role Of Devsecops Ppt Example
This slide discusses the continuous integration commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the commit phase, which includes automating testing, speed, immediate feedback, identifying risk, security scanning, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Devsecops Pipeline Continuous Deployment Acceptance Stage Role Of Devsecops Ppt Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Devsecops Pipeline Continuous Deployment Acceptance Stage Role Of Devsecops Ppt Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses the continuous integration commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the commit phase, which includes automating testing, speed, immediate feedback, identifying risk, security scanning, and so on.
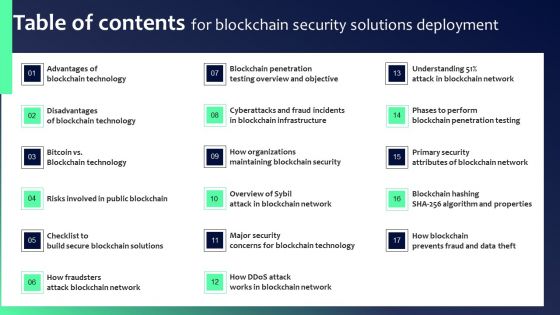
Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF
Slidegeeks has constructed Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
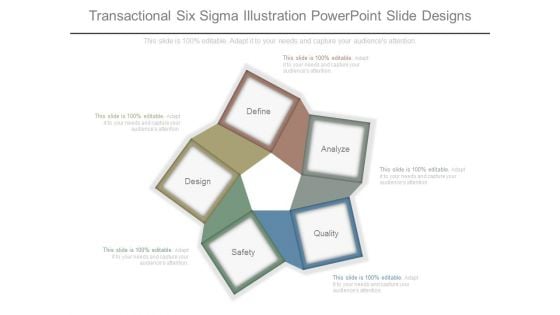
Transactional Six Sigma Illustration Powerpoint Slide Designs
This is a transactional six sigma illustration powerpoint slide designs. This is a five stage process. The stages in this process are define, design, safety, quality, analyze.

Building Positive Relationships Example Ppt Design
This is a building positive relationships example ppt design. This is a seven stage process. The stages in this process are safety, trust, respect, connect, identify, close, plan.
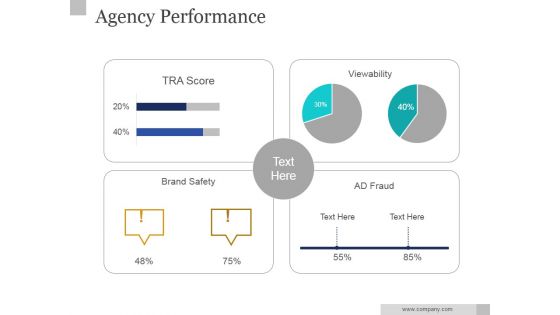
Agency Performance Ppt PowerPoint Presentation Background Designs
This is a agency performance ppt powerpoint presentation background designs. This is a four stage process. The stages in this process are transcore, viewability, brand safety, ad fraud.
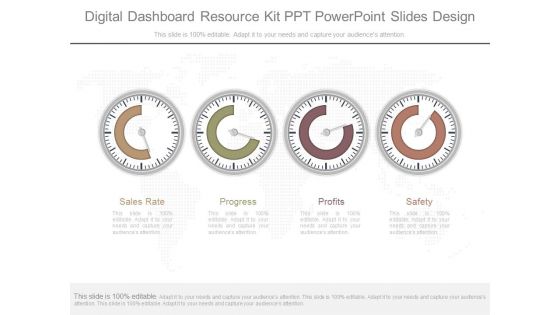
Digital Dashboard Resource Kit Ppt Powerpoint Slides Design
This is a digital dashboard resource kit ppt powerpoint slides design. This is a four stage process. The stages in this process are sales rate, progress, profits, safety.

Transactional Six Sigma Illustration Ppt Inspiration
This is a transactional six sigma illustration ppt inspiration. This is a six stage process. The stages in this process are safety, quality, design, measure, analyze, control.
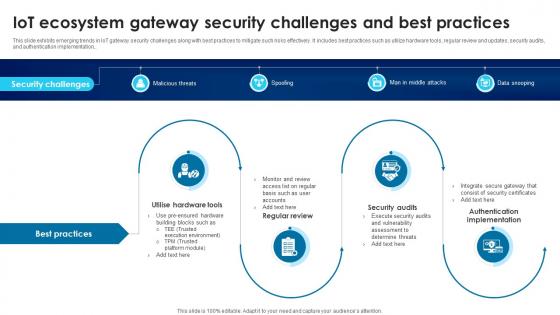
Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V
This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation. Slidegeeks has constructed Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation.
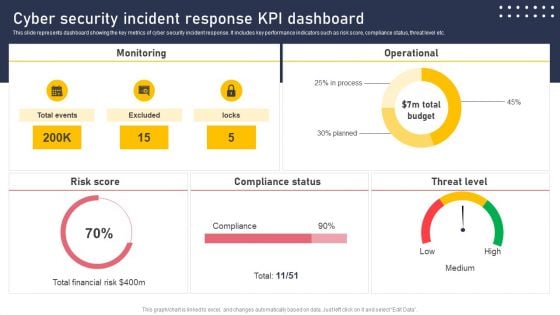
Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
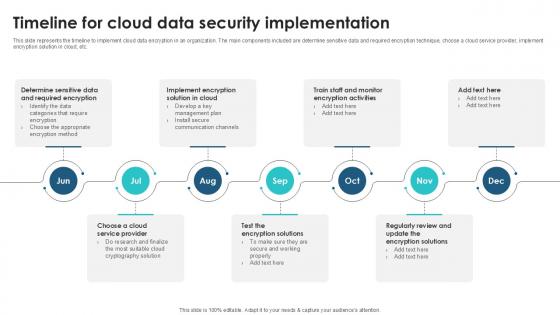
Timeline For Cloud Data Security Client Side Encryption PPT Example
This slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Slidegeeks has constructed Timeline For Cloud Data Security Client Side Encryption PPT Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc.
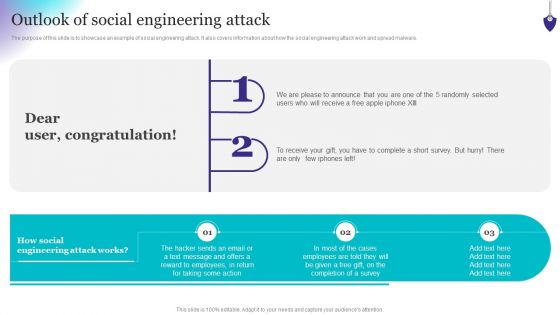
Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Slidegeeks has constructed Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
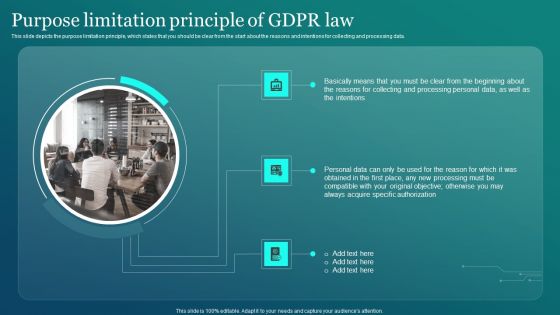
Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Slidegeeks has constructed Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Information Systems Security And Risk Management Plan Timeline Professional PDF
Slidegeeks has constructed Information Systems Security And Risk Management Plan Timeline Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
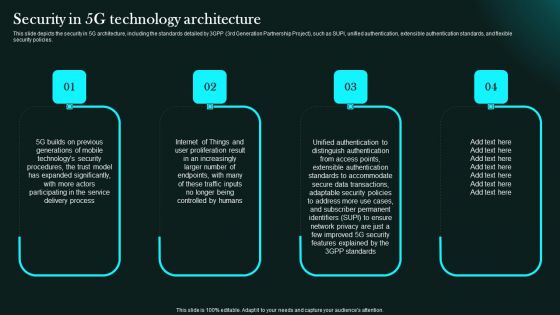
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
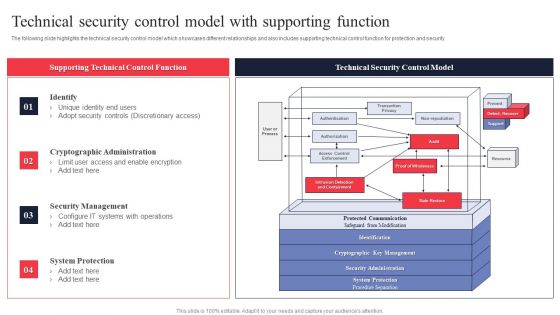
IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.Slidegeeks has constructed Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF
Slidegeeks has constructed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF
Slidegeeks has constructed Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

IT Policies And Procedures Password Creation And Management Policy Diagrams PDF
This slide depicts the password creation and management policy that explains how to create, implement, and review a defined procedure for establishing, updating, and maintaining strong and secure passwords. Slidegeeks has constructed IT Policies And Procedures Password Creation And Management Policy Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

CRM Software Deployment Journey Implementation Steps Introduction For Identifying Introduction PDF
This slide covers the process of determining the CRM users and creating their roles and profiles in order to maintain data security. Slidegeeks has constructed CRM Software Deployment Journey Implementation Steps Introduction For Identifying Introduction PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Diagram Graphics Of Three Pen Drives Presentation Template
Graphic of three pen drives has been sued to craft this power point template diagram. This PPT contain the concept of data storage and safety. Use this PPT for business and technology related presentations.
Business Framework Entry Barrier PowerPoint Presentation
This business framework power point template has been crafted with graphic of traffic barrier and cones. This diagram template may be used for traffic rules related topics and build exclusive presentations on safety.
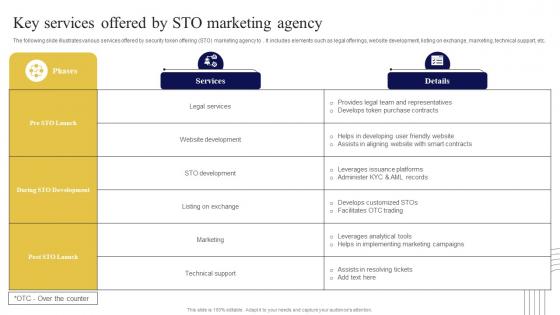
Key Services Offered By STO Exploring Investment Opportunities Topics Pdf
The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc. Slidegeeks has constructed Key Services Offered By STO Exploring Investment Opportunities Topics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc.
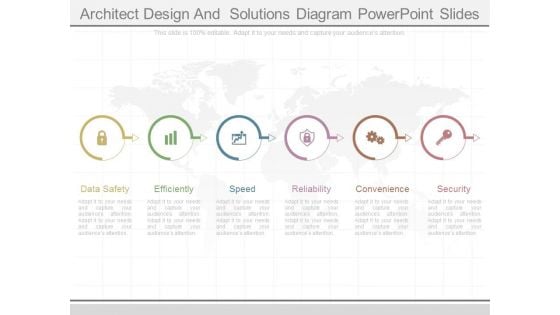
Architect Design And Solutions Diagram Powerpoint Slides
This is a architect design and solutions diagram powerpoint slides. This is a six stage process. The stages in this process are data safety, efficiently, speed, reliability, convenience, security.
Organizational Behaviour Structure Powerpoint Slide Design Ideas
This is a organizational behaviour structure powerpoint slide design ideas. This is a six stage process. The stages in this process are work groups and teams, development, organizational, compliance, maximizing your leadership, environment safety.


 Continue with Email
Continue with Email

 Home
Home


































