Cyber Attack
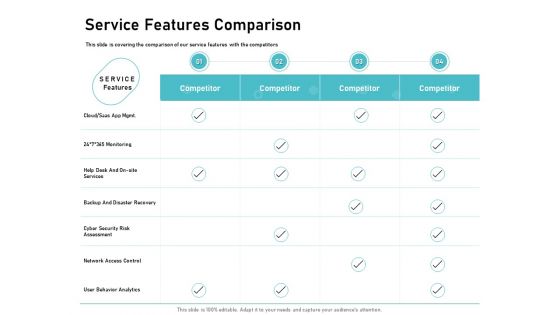
IT Support And Monitoring Services Pricing Service Features Comparison Guidelines PDF
Presenting this set of slides with name it support and monitoring services pricing service features comparison guidelines pdf. The topics discussed in these slides are monitoring, analytics, network, cyber security, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
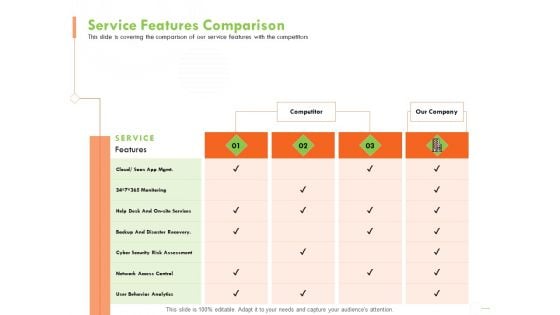
Welfare Work Value Service Features Comparison Ppt Outline Themes PDF
Presenting this set of slides with name welfare work value service features comparison ppt outline themes pdf. The topics discussed in these slides are monitoring, services, cyber security, analytics, network access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Email Security Market Research Report Ppt PowerPoint Presentation Complete Deck With Slides

Global Cloud Based Email Security Market Ppt PowerPoint Presentation Complete Deck With Slides

Internet Security Threat Analysis Plan With Agents And Tactics Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled internet security threat analysis plan with agents and tactics ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are corporations, hacktivists, cyber fighters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Tech Support Services Cost And Pricing Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name tech support services cost and pricing ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are monitoring, cyber security, infrastructure, implementing, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
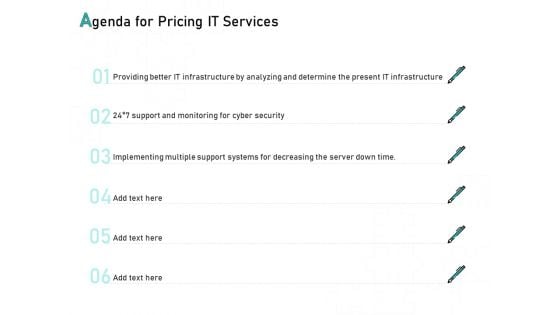
Tech Support Services Cost And Pricing Agenda For Pricing IT Services Ppt PowerPoint Presentation Summary Diagrams
Presenting this set of slides with name tech support services cost and pricing agenda for pricing it services ppt powerpoint presentation summary diagrams. The topics discussed in these slides are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Tech Support Services Cost And Pricing Effect After Implementing IT Services Ppt PowerPoint Presentation Summary Background
Presenting this set of slides with name tech support services cost and pricing effect after implementing it services ppt powerpoint presentation summary background. The topics discussed in these slides are cyber security, infrastructure, technological, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
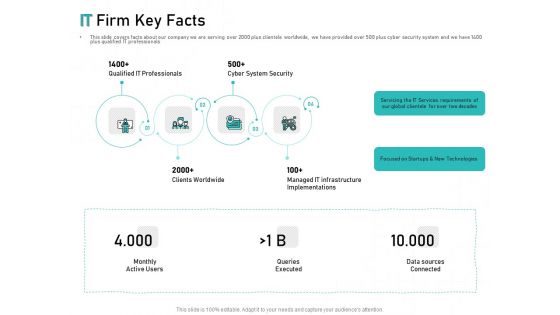
Tech Support Services Cost And Pricing IT Firm Key Facts Ppt PowerPoint Presentation Slides File Formats
Presenting this set of slides with name tech support services cost and pricing it firm key facts ppt powerpoint presentation slides file formats. This is a four stage process. The stages in this process are technologies, services, implementations, infrastructure, cyber system security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Managed Services Pricing Guide IT Firm Key Facts Ppt Infographics Visuals PDF
Presenting this set of slides with name cloud managed services pricing guide it firm key facts ppt infographics visuals pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Managed Services Pricing Guide Agenda For Managed Services Pricing Guidelines Ppt Infographics Background PDF
Presenting this set of slides with name cloud managed services pricing guide agenda for managed services pricing guidelines ppt infographics background pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
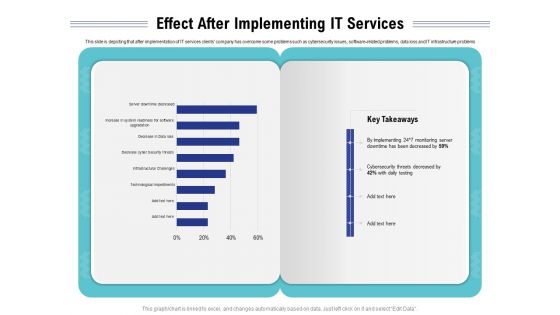
Cloud Managed Services Pricing Guide Effect After Implementing IT Services Ppt Styles Mockup PDF
Presenting this set of slides with name cloud managed services pricing guide effect after implementing it services ppt styles mockup pdf. The topics discussed in these slides are technological, cyber security, implementing, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
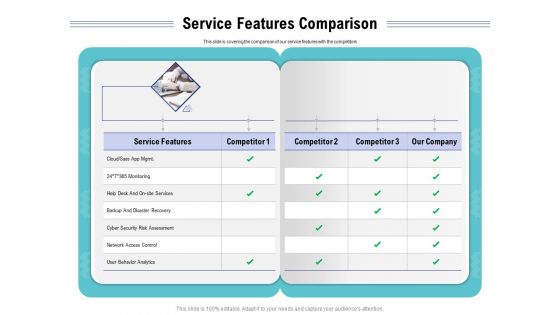
Cloud Managed Services Pricing Guide Service Features Comparison Ppt Gallery Infographic Template PDF
Presenting this set of slides with name cloud managed services pricing guide service features comparison ppt gallery infographic template pdf. This is a three stage process. The stages in this process are service, cyber security, analytics, monitoring, disaster recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
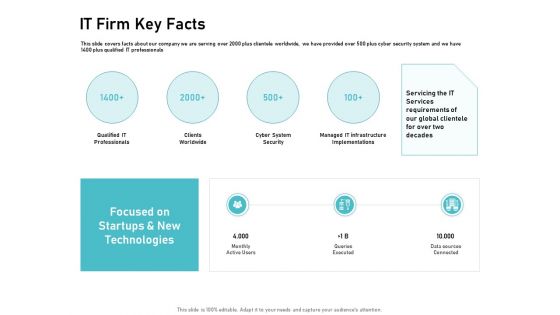
IT Support And Monitoring Services Pricing IT Firm Key Facts Ppt Portfolio Styles PDF
Presenting this set of slides with name it support and monitoring services pricing it firm key facts ppt portfolio styles pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Support And Monitoring Services Pricing Agenda For IT Support And Monitoring Services Pricing Elements PDF
Presenting this set of slides with name it support and monitoring services pricing agenda for it support and monitoring services pricing elements pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Welfare Work Value Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name welfare work value ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are infrastructure, analyzing, cyber security, implementing, service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Welfare Work Value IT Firm Key Facts Ppt Pictures Icon PDF
Presenting this set of slides with name welfare work value it firm key facts ppt pictures icon pdf. This is a four stage process. The stages in this process are clients worldwide, cyber system security, infrastructure, implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Welfare Work Value Agenda For Welfare Work Value Ppt Professional Show PDF
Presenting this set of slides with name welfare work value agenda for welfare work value ppt professional show pdf. This is a six stage process. The stages in this process are analyzing, infrastructure, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
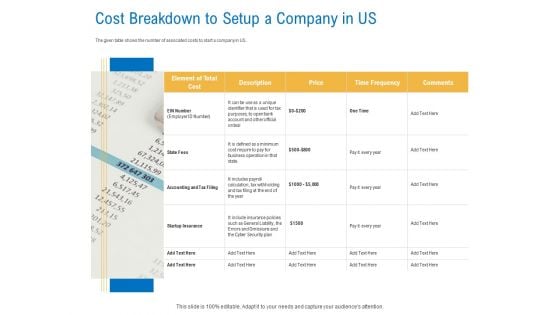
Digital Businesses Ecosystems Cost Breakdown To Setup A Company In Us Professional PDF
Deliver an awe inspiring pitch with this creative digital businesses ecosystems cost breakdown to setup a company in us professional pdf bundle. Topics like cyber security, plan, business, cost, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agile Best Practices For Effective Team Project Scope Management Plan For Agile Implementation Pictures PDF
Deliver an awe inspiring pitch with this creative agile best practices for effective team project scope management plan for agile implementation pictures pdf bundle. Topics like team communication, cyber security, budget, measurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Evaluation Results Showing Bank Risk Ppt PowerPoint Presentation File Influencers PDF
Presenting evaluation results showing bank risk ppt powerpoint presentation file influencers pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including cyber security, perform, legal audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Incident Response Planning And Reporting Chart With Primary Skills Ppt PowerPoint Presentation Icon Ideas PDF
Pitch your topic with ease and precision using this incident response planning and reporting chart with primary skills ppt powerpoint presentation icon ideas pdf. This layout presents information on management, technical, cyber security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Incident Response Planning And Reporting Matrix With Activities Ppt PowerPoint Presentation Gallery Slide Download PDF
Pitch your topic with ease and precision using this incident response planning and reporting matrix with activities ppt powerpoint presentation gallery slide download pdf. This layout presents information on cyber security, technical, accountable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
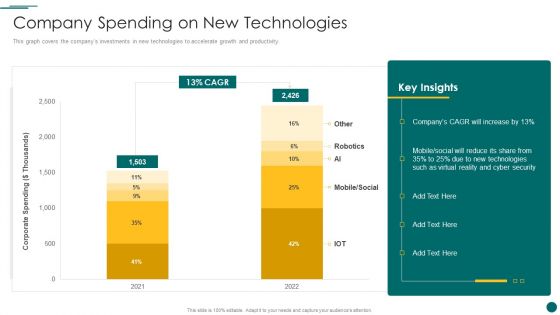
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
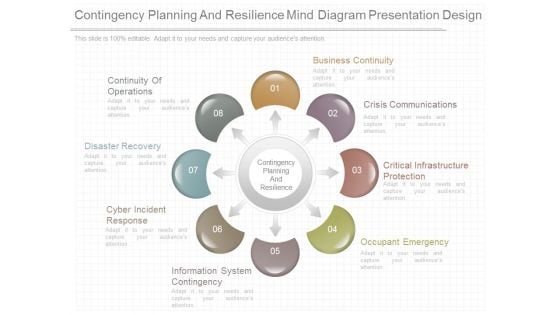
Contingency Planning And Resilience Mind Diagram Presentation Design
This is a contingency planning and resilience mind diagram presentation design. This is a eight stage process. The stages in this process are contingency planning and resilience, business continuity, crisis communications, critical infrastructure protection, occupant emergency, information system contingency, cyber incident response, disaster recovery, continuity of operations.

Virtual Security Hazards Detection And Response Topics Pdf
This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Showcasing this set of slides titled Virtual Security Hazards Detection And Response Topics Pdf. The topics addressed in these templates are Security Centre, Access Time, Cybersecurity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps

Cybersecurity Training Program Budget And Schedule Dates Graphics PDF
This slide covers the training schedule for various cyber security incidents program. It further includes budget allocated, training duration, dates for training and review sessions.Showcasing this set of slides titled Cybersecurity Training Program Budget And Schedule Dates Graphics PDF. The topics addressed in these templates are Malware Attack, Emergency Report, Capability Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
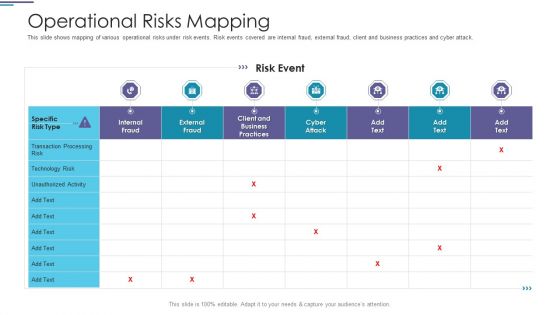
Operational Risks Mapping Ppt PowerPoint Presentation Ideas Graphics Example PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack.Deliver and pitch your topic in the best possible manner with this operational risks mapping ppt powerpoint presentation ideas graphics example pdf. Use them to share invaluable insights on transaction processing, technology risk, client and business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
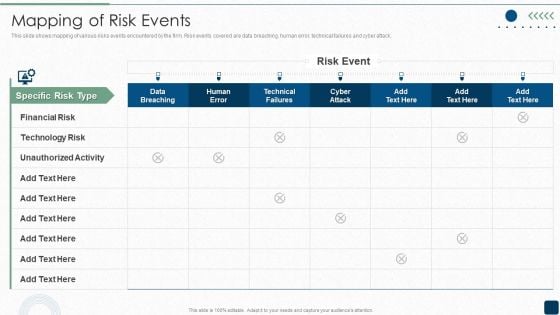
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
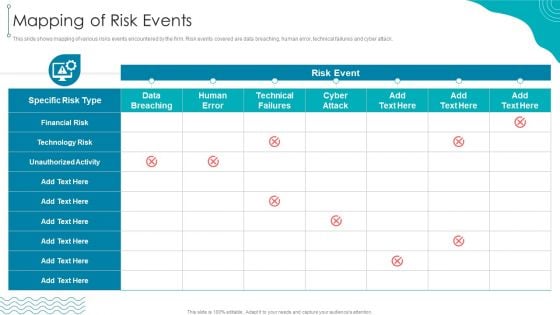
ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
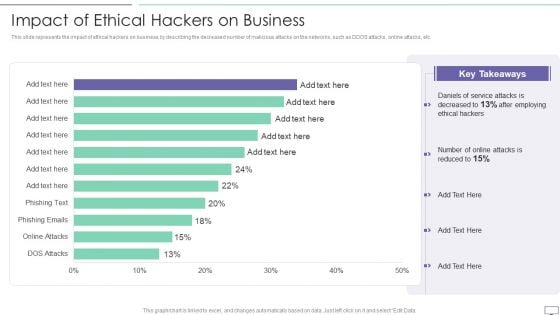
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

White Hat Hacking Whats New In Cehv11 Ppt Pictures Sample PDF
This slide represents the new concepts added to the Certified Ethical Hacking program, including hacking challenges on a higher level, new attack techniques, enumeration, and others. Presenting white hat hacking whats new in cehv11 ppt pictures sample pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like techniques, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
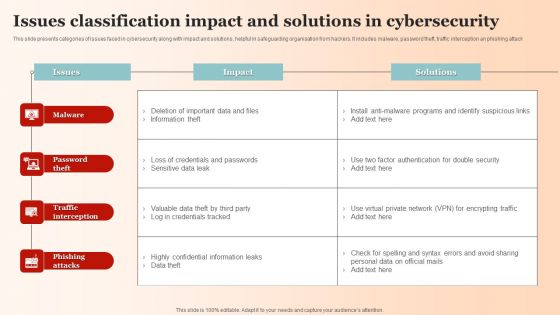
Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
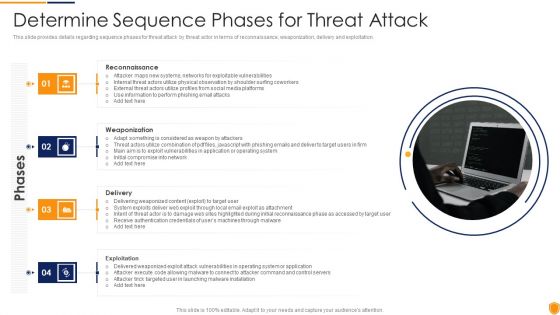
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Program Values To Business Ppt File Smartart PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting information security program values to business ppt file smartart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reduce, security, network, environment, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Estate Development Project Prioritization Slide Download PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide.Deliver and pitch your topic in the best possible manner with this Real Estate Development Project Prioritization Slide Download PDF. Use them to share invaluable insights on Ransomware, Phishing, Management Response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Estate Development Project Prioritization Contd Managing Commercial Property Risks Mockup PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide.Deliver and pitch your topic in the best possible manner with this Real Estate Development Project Prioritization Contd Managing Commercial Property Risks Mockup PDF. Use them to share invaluable insights on Ransomware, Business Compromise, Management Response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
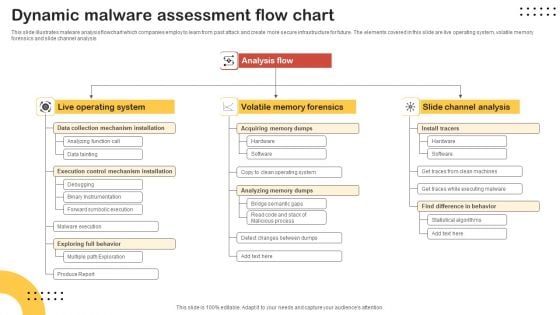
Dynamic Malware Assessment Flow Chart Infographics PDF
This slide illustrates malware analysis flowchart which companies employ to learn from past attack and create more secure infrastructure for future. The elements covered in this slide are live operating system, volatile memory forensics and slide channel analysis. Showcasing this set of slides titled Dynamic Malware Assessment Flow Chart Infographics PDF. The topics addressed in these templates are Live Operating System, Volatile Memory Forensics, Slide Channel Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
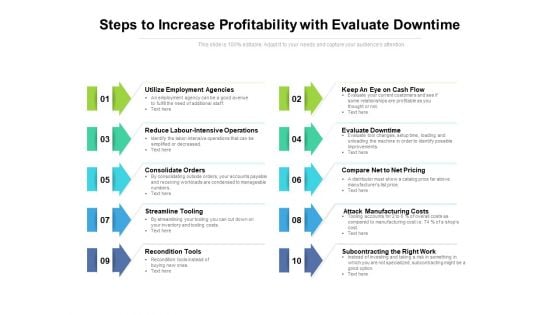
Steps To Increase Profitability With Evaluate Downtime Ppt PowerPoint Presentation Styles Example File PDF
Presenting this set of slides with name steps to increase profitability with evaluate downtime ppt powerpoint presentation styles example file pdf. This is a ten stage process. The stages in this process are utilize employment agencies, reduce labour intensive operations, consolidate orders, streamline tooling, recondition tools, keep an eye on cash flow, evaluate downtime, compare net to net pricing, attack manufacturing costs, subcontracting the right work. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
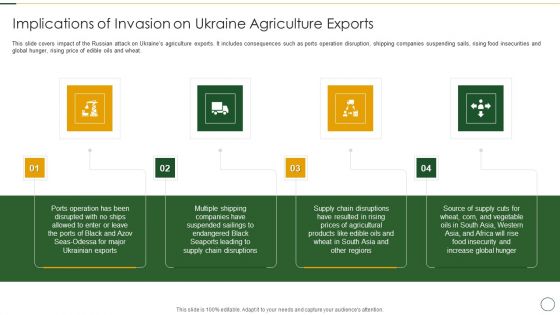
Analyzing The Impact Of Russia Ukraine Conflict On Agriculture Sector Implications Of Invasion Information PDF
This slide covers impact of the Russian attack on Ukraines agriculture exports. It includes consequences such as ports operation disruption, shipping companies suspending sails, rising food insecurities and global hunger, rising price of edible oils and wheat. Presenting analyzing the impact of russia ukraine conflict on agriculture sector implications of invasion information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like supply chain disruptions, multiple shipping, increase global hunger In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Global Cybersecurity Industry Segmentation Analysis Global Data Security Industry Report IR SS V
The slide showcases the cyber security industry segmentation based on attributes such as component, security type, deployment, organization size, end-user and region. This slide aims to identify, analyze and categorize the market to serve clients demands and meet their expectations. Boost your pitch with our creative Global Cybersecurity Industry Segmentation Analysis Global Data Security Industry Report IR SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The slide showcases the cyber security industry segmentation based on attributes such as component, security type, deployment, organization size, end-user and region. This slide aims to identify, analyze and categorize the market to serve clients demands and meet their expectations.

Complete Guide To Launch Website Security Management Strategic Plan
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Slidegeeks has constructed Complete Guide To Launch Website Security Management Strategic Plan after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.

Reasons Behind Need For Secure Web Gateway Web Threat Protection System
This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc. Slidegeeks has constructed Reasons Behind Need For Secure Web Gateway Web Threat Protection System after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.

Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
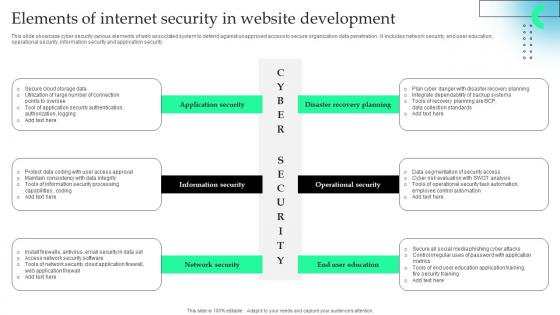
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.

Key Challenges To Medical Industry Cybersecurity Performance Background Pdf
This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness Showcasing this set of slides titled Key Challenges To Medical Industry Cybersecurity Performance Background Pdf. The topics addressed in these templates are Data Breaches, Service, Cloud Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness
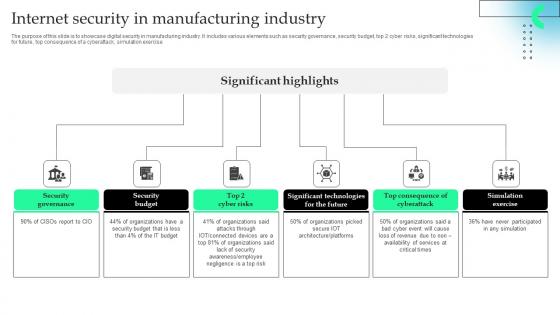
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.
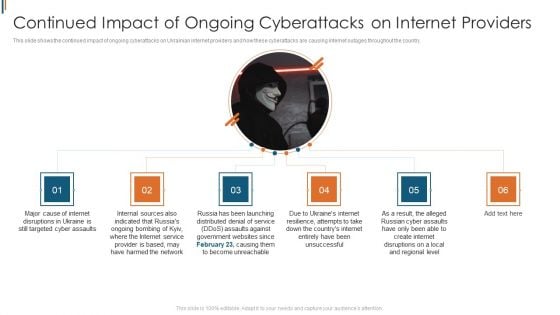
Ukraine Cyberwarfare Continued Impact Of Ongoing Cyberattacks On Internet Providers Elements Pdf
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. Presenting ukraine cyberwarfare continued impact of ongoing cyberattacks on internet providers elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like major cause of internet disruptions in ukraine is still targeted cyber assaults, as a result, the alleged russian cyber assaults have only been able to create internet disruptions on a local and regional level, internal sources also indicated that russias ongoing bombing of kyiv. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Model Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Traditional Security Models Vs Zero Trust Network Access and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.
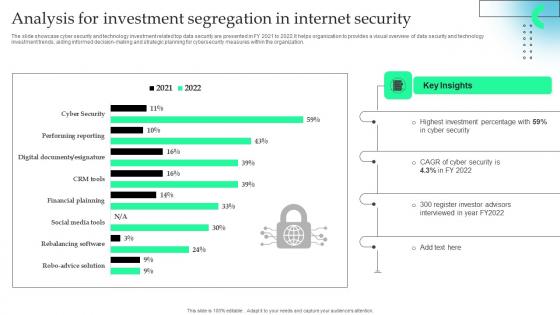
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
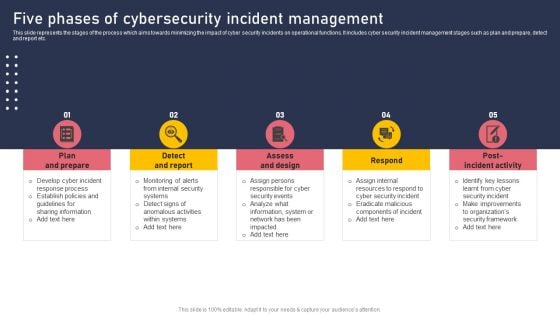
Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
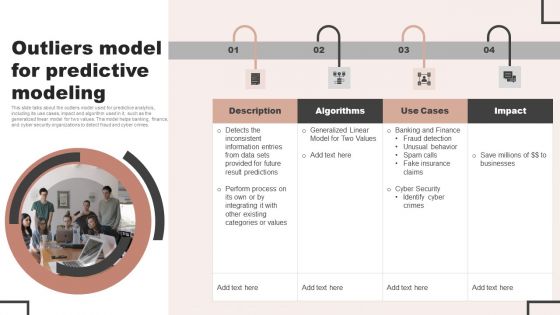
Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.


 Continue with Email
Continue with Email

 Home
Home


































