Cyber Attack
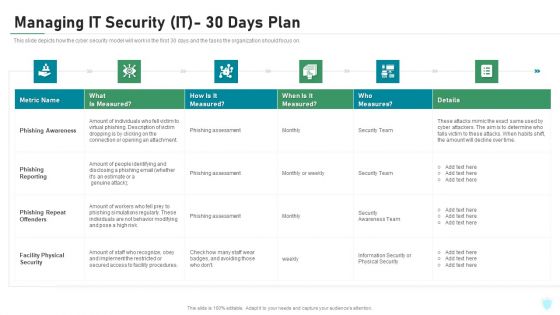
Managing IT Security IT 30 Days Plan Ppt Gallery Graphics Download PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing it security it 30 days plan ppt gallery graphics download pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
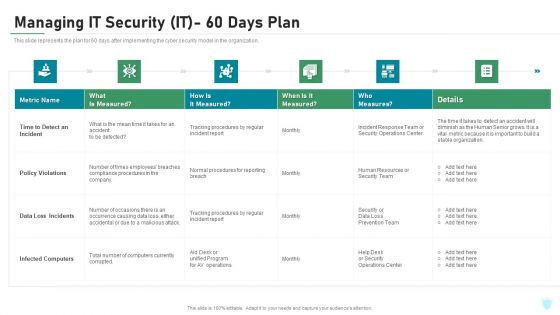
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
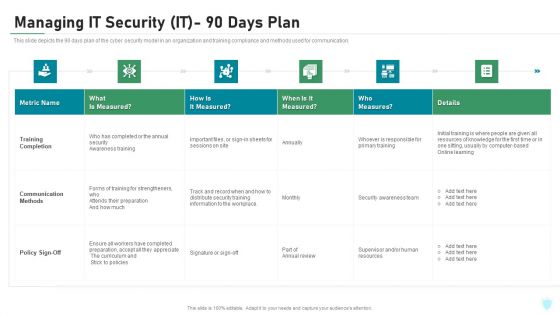
Managing IT Security IT 90 Days Plan Ppt Layouts Picture PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this managing it security it 90 days plan ppt layouts picture pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
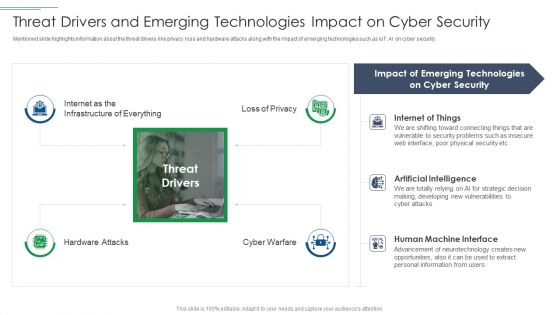
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Several Threat Actors Profile Clipart PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management determine several threat actors profile clipart pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF bundle. Topics like OT Security Functions, Security Architecture And Engineering, Primary Responsibility, Shared Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
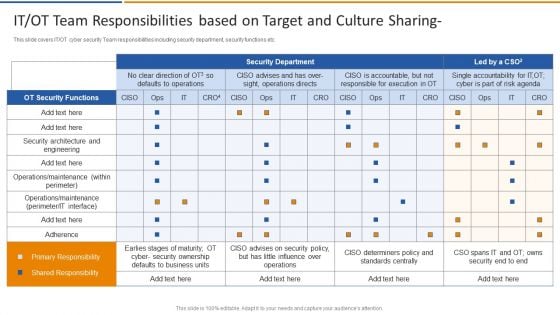
Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF bundle. Topics like OT Security Functions, Security architecture, Primary Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
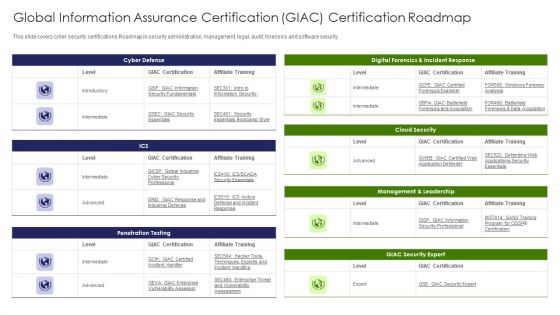
IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
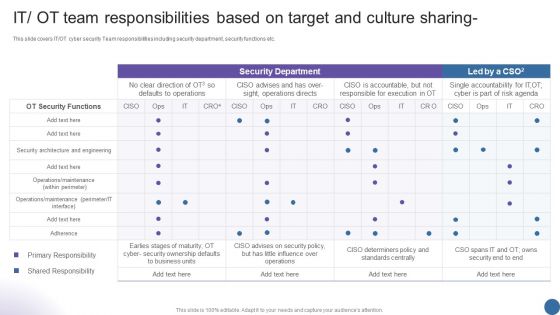
IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF bundle. Topics like Security Department, Team Responsibilities, Target can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Application Programming Interface Marketplace Cost Breakdown To Setup A Company In US Diagrams PDF
The description below is the professional summary of the company, includes information of features, license, pricing structure and size of users. Deliver and pitch your topic in the best possible manner with this application programming interface marketplace cost breakdown to setup a company in us diagrams pdf. Use them to share invaluable insights on cyber security plan, business operation, time frequency and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Examples Of Data Breaches Ppt PowerPoint Presentation Summary Portrait PDF
Presenting this set of slides with name examples of data breaches ppt powerpoint presentation summary portrait pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
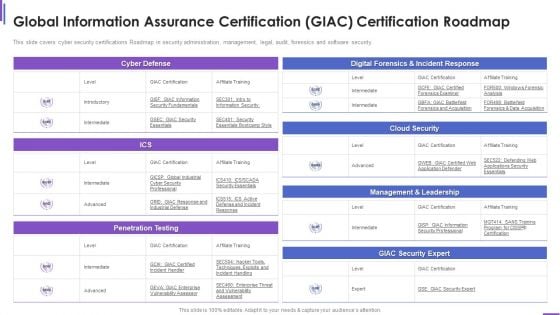
Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Minimizing Operational Cost Through Iot Virtual Twins Implementation Optimize And Digitalize Mockup PDF
This slide focuses on the optimization and digitalization of supply chain operations which covers cyber supply chain, risk analytics and physical supply chain, Deliver and pitch your topic in the best possible manner with this minimizing operational cost through iot virtual twins implementation optimize and digitalize mockup pdf. Use them to share invaluable insights on analysis, optimization, predicative, design, optimize and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Analysis Reporting Tools Ppt PowerPoint Presentation Professional Layout Cpb Pdf
Presenting this set of slides with name data analysis reporting tools ppt powerpoint presentation professional layout cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
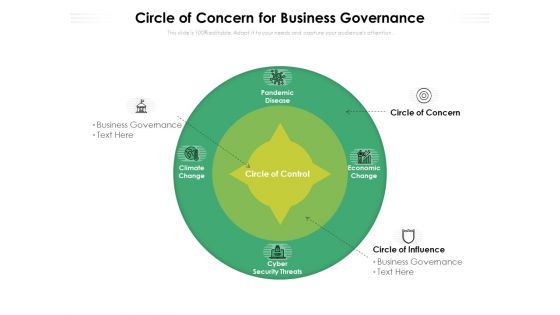
Circle Of Concern For Business Governance Ppt PowerPoint Presentation Gallery Format Ideas PDF
Persuade your audience using this circle of concern for business governance ppt powerpoint presentation gallery format ideas pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including economic, cyber security, pandemic disease. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agile Best Practices For Effective Team Prioritizing Agile Software Development Tasks Brochure PDF
Presenting agile best practices for effective team prioritizing agile software development tasks brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like communication, cyber security, collaboration, project deliverables. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
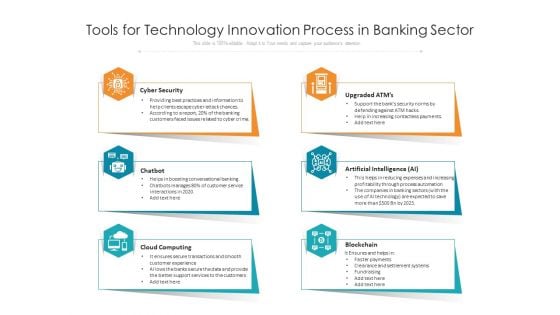
Tools For Technology Innovation Process In Banking Sector Ppt PowerPoint Presentation Show Inspiration PDF
Persuade your audience using this tools for technology innovation process in banking sector ppt powerpoint presentation show inspiration pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security, upgraded atms, artificial intelligence ai, chatbot, cloud computing, blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
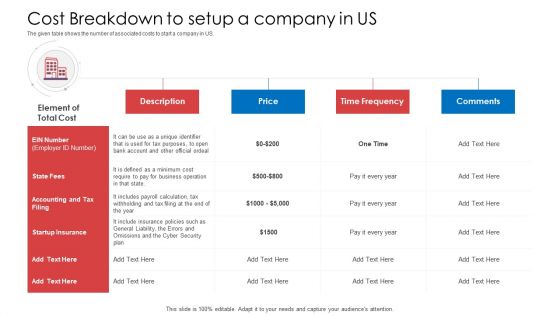
API Administration Solution Cost Breakdown To Setup A Company In US Ppt Ideas Summary PDF
The given table shows the number of associated costs to start a company in US. Deliver an awe inspiring pitch with this creative api administration solution cost breakdown to setup a company in us ppt ideas summary pdf bundle. Topics like business, policies, price, cost, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
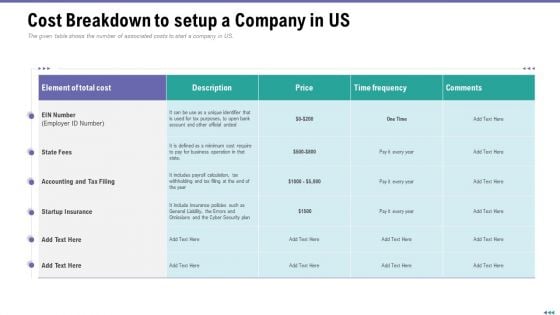
Market Viewpoint Application Programming Interface Governance Cost Breakdown To Setup A Company In Us Template PDF
The given table shows the number of associated costs to start a company in US. Deliver an awe inspiring pitch with this creative market viewpoint application programming interface governance cost breakdown to setup a company in us template pdf bundle. Topics like business, policies, price, cost, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
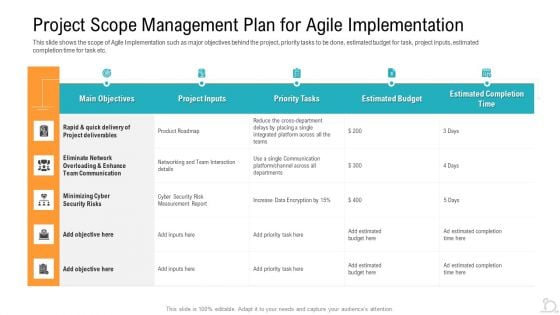
Project Scope Management Plan For Agile Implementation Formats PDF
This slide shows the scope of Agile Implementation such as major objectives behind the project, priority tasks to be done, estimated budget for task, project inputs, estimated completion time for task etc. Deliver an awe inspiring pitch with this creative project scope management plan for agile implementation formats pdf bundle. Topics like overloading and enhance, minimizing cyber security, project deliverables can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
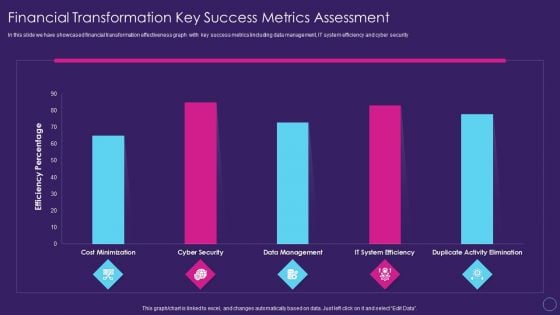
Financial Transformation Key Success Metrics Assessment Digital Transformation Toolkit Accounting Finance Introduction PDF
In this slide we have showcased financial transformation effectiveness graph with key success metrics lincluding data management, IT system efficiency and cyber security Deliver an awe inspiring pitch with this creative financial transformation key success metrics assessment digital transformation toolkit accounting finance introduction pdf bundle. Topics like financial transformation key success metrics assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
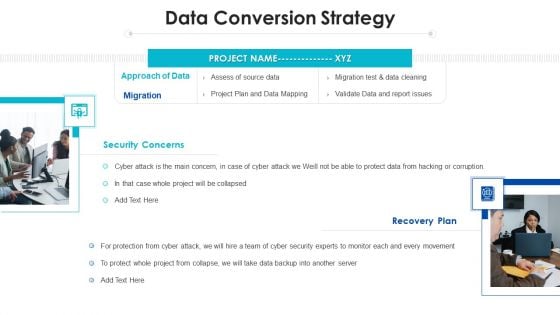
Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF
Presenting Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Approach Data, Recovery Plan, Cyber Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
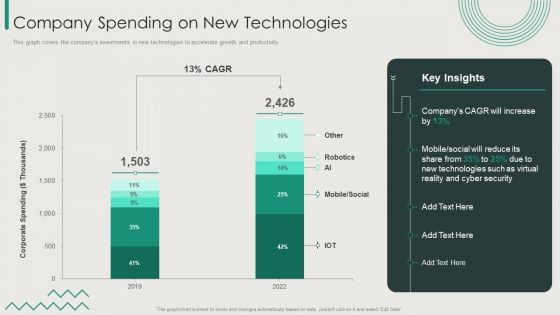
Organization Transition Company Spending On New Technologies Ppt PowerPoint Presentation Gallery Good PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Transition Company Spending On New Technologies Ppt PowerPoint Presentation Gallery Good PDF bundle. Topics like Mobile, Social, Cyber Security, New Technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
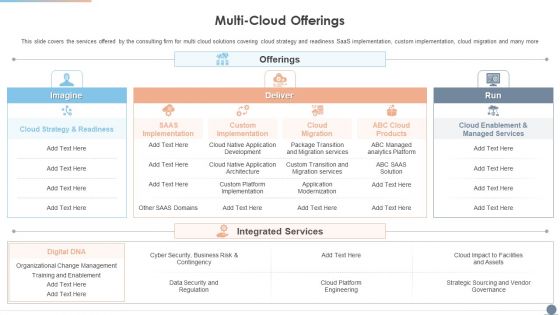
Multi Cloud Complexity Management Multi Cloud Offerings Inspiration PDF
This slide covers the services offered by the consulting firm for multi cloud solutions covering cloud strategy and readiness SaaS implementation, custom implementation, cloud migration and many more. Deliver and pitch your topic in the best possible manner with this Multi Cloud Complexity Management Multi Cloud Offerings Inspiration PDF. Use them to share invaluable insights on Cloud Strategy, Organizational Change Management, Cyber Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
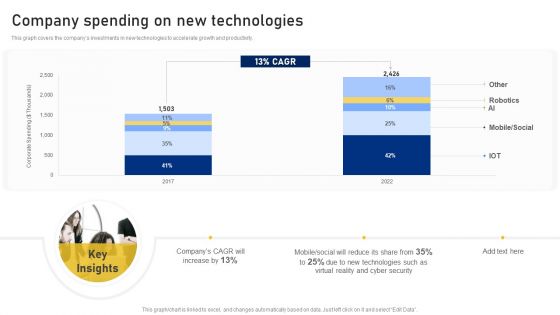
Reshaping Business In Digital Company Spending On New Technologies Clipart PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Company Spending On New Technologies Clipart PDF bundle. Topics like Corporate Spending, New Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
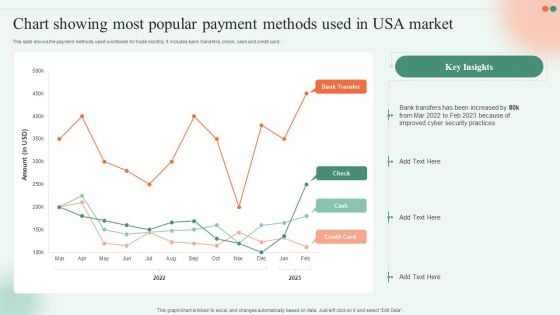
Chart Showing Most Popular Payment Methods Used In USA Market Ppt File Deck PDF
This slide shows the payment methods used worldwide for trade monthly. It includes bank transfers, check, cash and credit card. Showcasing this set of slides titled Chart Showing Most Popular Payment Methods Used In USA Market Ppt File Deck PDF. The topics addressed in these templates are Cyber Security Practices, Bank Transfers, 2022 To 2023. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
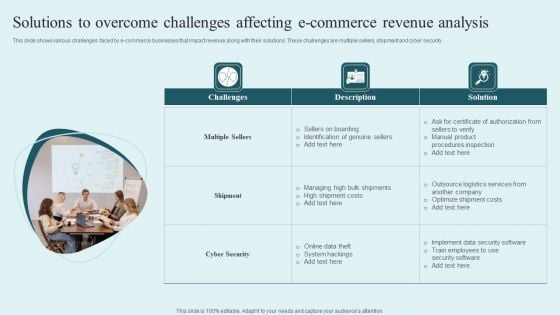
Solutions To Overcome Challenges Affecting E Commerce Revenue Analysis Summary PDF
This slide shows various challenges faced by e-commerce businesses that impact revenue along with their solutions. These challenges are multiple sellers, shipment and cyber security. Presenting Solutions To Overcome Challenges Affecting E Commerce Revenue Analysis Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Challenges, Solution, Multiple Sellers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
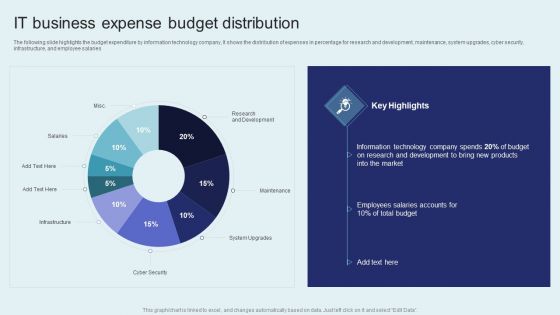
IT Firm Financial Statement IT Business Expense Budget Distribution Pictures PDF
The following slide highlights the budget expenditure by information technology company, It shows the distribution of expenses in percentage for research and development, maintenance, system upgrades, cyber security, infrastructure, and employee salaries. There are so many reasons you need a IT Firm Financial Statement IT Business Expense Budget Distribution Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents For Convergence Strategy For Information And Operational Technology Ideas PDF
This is a Table Of Contents For Convergence Strategy For Information And Operational Technology Ideas PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Convergence Strategy, Team Responsibilities, Launch Cyber IT, OT Strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
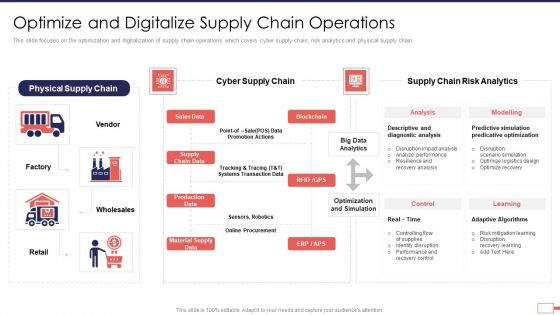
Iot Digital Twin Technology Post Covid Expenditure Management Optimize Digitalize Supply Template PDF
This slide focuses on the optimization and digitalization of supply chain operations which covers cyber supply chain, risk analytics and physical supply chain. Deliver an awe inspiring pitch with this creative iot digital twin technology post covid expenditure management optimize digitalize supply template pdf bundle. Topics like supply chain, promotion, risk, analytics, optimization, procurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.
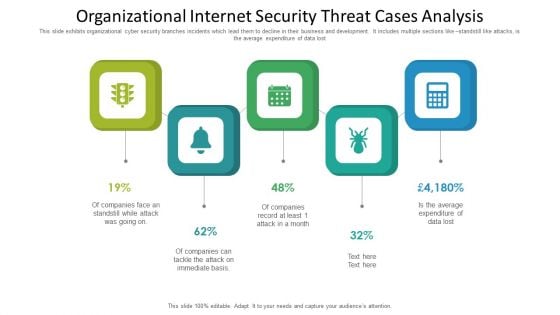
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
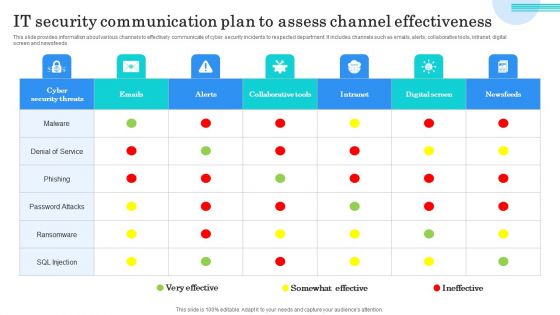
IT Security Communication Plan To Assess Channel Effectiveness Themes PDF
This slide provides information about various channels to effectively communicate of cyber security incidents to respected department. It includes channels such as emails, alerts, collaborative tools, intranet, digitalscreen and newsfeeds. Showcasing this set of slides titled IT Security Communication Plan To Assess Channel Effectiveness Themes PDF. The topics addressed in these templates are Denial Service, Phishing, Password Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
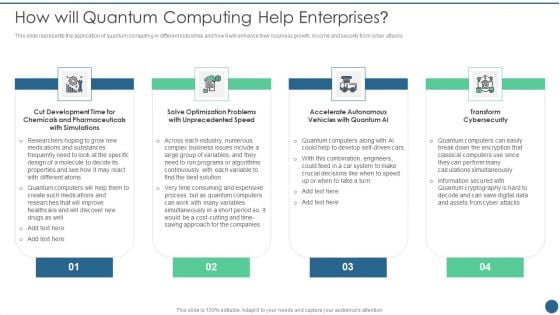
Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks.This is a Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Optimization Problems, Accelerate Autonomous, Vehicles Quantum You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
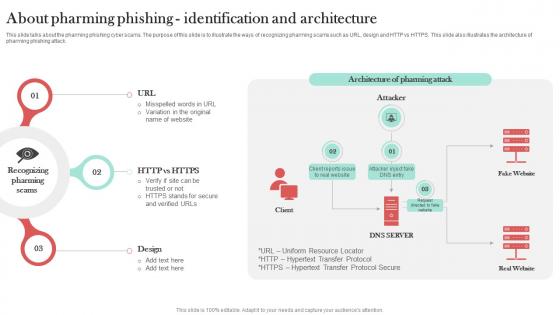
About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack.
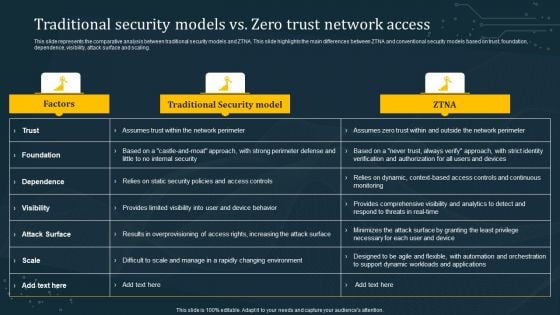
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Global Data Security Industry Report Executive Summary Of Cybersecurity Industry Report IR SS V
The purpose of the slide is to provide a concise overview of the cybersecurity industry, serving as a valuable resource for industry professionals, investors, and policymakers. It includes a short description of the market, growth factors, restraints, and competitive landscape. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Global Data Security Industry Report Executive Summary Of Cybersecurity Industry Report IR SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Global Data Security Industry Report Executive Summary Of Cybersecurity Industry Report IR SS V today and make your presentation stand out from the rest The purpose of the slide is to provide a concise overview of the cybersecurity industry, serving as a valuable resource for industry professionals, investors, and policymakers. It includes a short description of the market, growth factors, restraints, and competitive landscape.

Successful Risk Administration Real Estate Development Project Prioritization Slides PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Successful Risk Administration Real Estate Development Project Prioritization Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Successful Risk Administration Real Estate Development Project Prioritization Slides PDF.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.
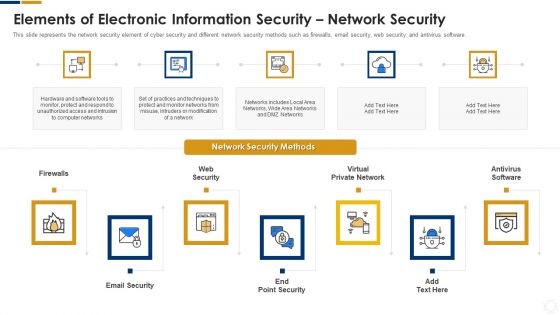
Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Access Control Solution Reasons Behind Need For Secure Web Gateway
Find a pre-designed and impeccable Web Access Control Solution Reasons Behind Need For Secure Web Gateway. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.
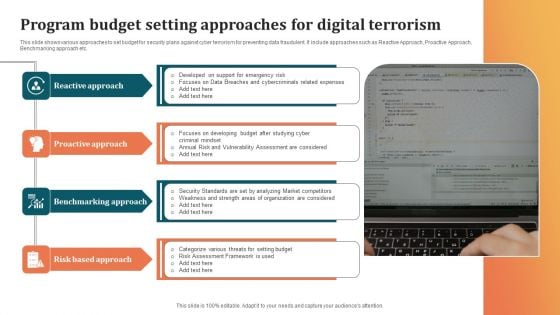
Program Budget Setting Approaches For Digital Terrorism Background PDF
This slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc. Presenting Program Budget Setting Approaches For Digital Terrorism Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benchmarking Approach, Risk Based Approach, Proactive Approach. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
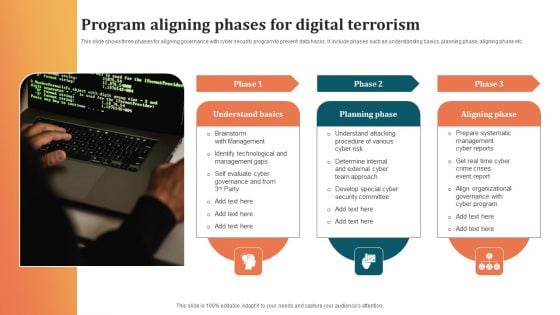
Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Key Elements Of Electronic Information Security Ppt Styles Smartart PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a cybersecurity key elements of electronic information security ppt styles smartart pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
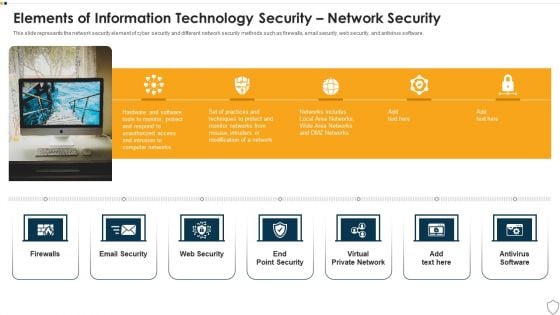
IT Security Elements Of Information Technology Security Network Security Ppt Pictures Graphics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting it security elements of information technology security network security ppt pictures graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like web security, end point security, virtual private network, email security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
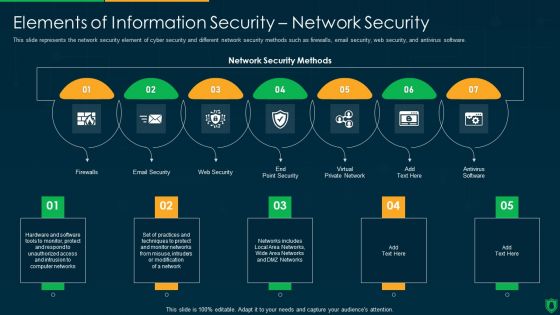
Info Security Elements Of Information Security Network Security Ppt PowerPoint Presentation File Vector PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting info security elements of information security network security ppt powerpoint presentation file vector pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like email security, web security, virtual private network, firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
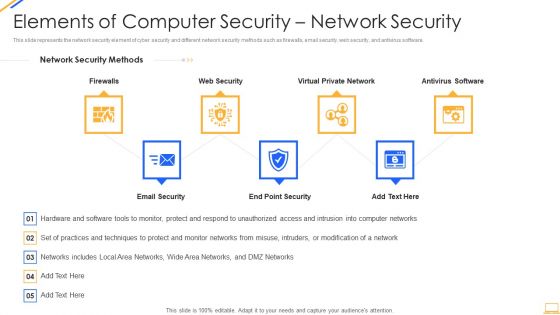
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
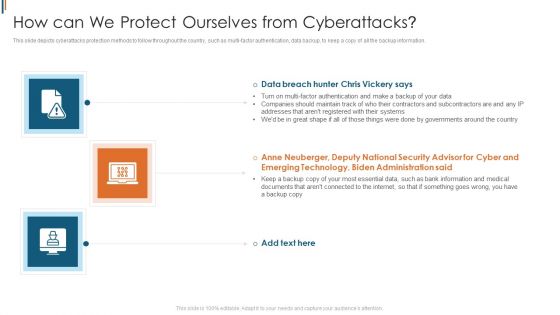
Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
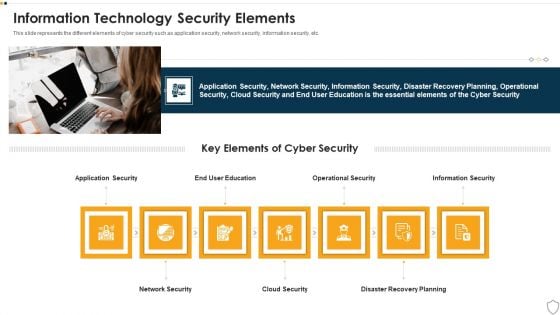
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
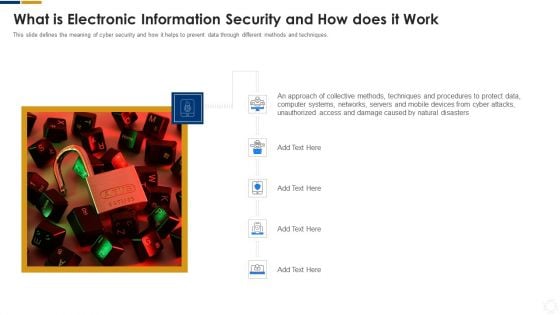
Cybersecurity What Is Electronic Information Security And How Does It Work Ppt Model Shapes PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting cybersecurity what is electronic information security and how does it work ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, devices, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
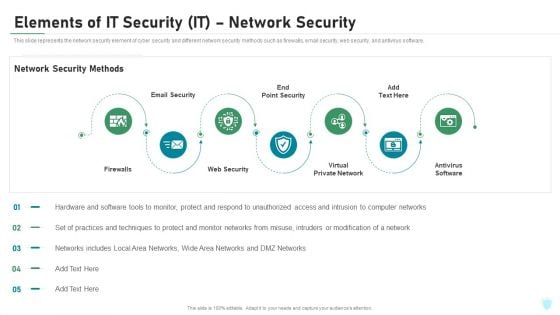
Elements Of IT Security IT Network Security Ppt Pictures Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a elements of it security it network security ppt pictures ideas pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like firewalls, email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
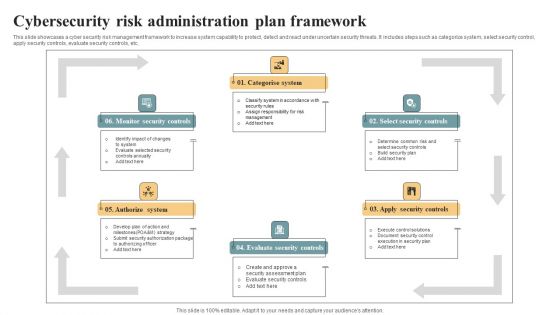
Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































