Cyber Security Icons

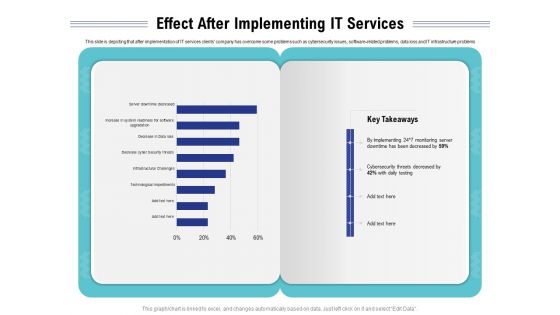
Tech Support Services Cost And Pricing Effect After Implementing IT Services Ppt PowerPoint Presentation Summary Background
Presenting this set of slides with name tech support services cost and pricing effect after implementing it services ppt powerpoint presentation summary background. The topics discussed in these slides are cyber security, infrastructure, technological, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cloud Managed Services Pricing Guide Effect After Implementing IT Services Ppt Styles Mockup PDF
Presenting this set of slides with name cloud managed services pricing guide effect after implementing it services ppt styles mockup pdf. The topics discussed in these slides are technological, cyber security, implementing, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
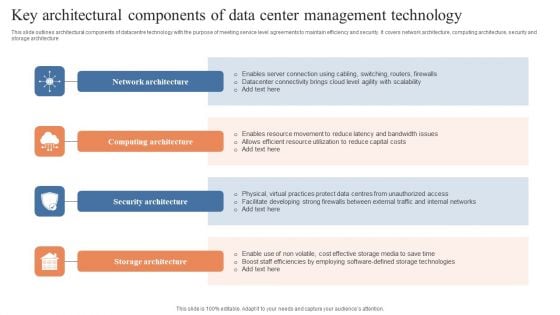
Key Architectural Components Of Data Center Management Technology Introduction PDF
This slide outlines architectural components of datacentre technology with the purpose of meeting service level agreements to maintain efficiency and security. It covers network architecture, computing architecture, security and storage architecture. Presenting Key Architectural Components Of Data Center Management Technology Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Network Architecture, Computing Architecture, Security Architecture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Evaluation Results Showing Bank Risk Ppt PowerPoint Presentation File Influencers PDF
Presenting evaluation results showing bank risk ppt powerpoint presentation file influencers pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including cyber security, perform, legal audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.
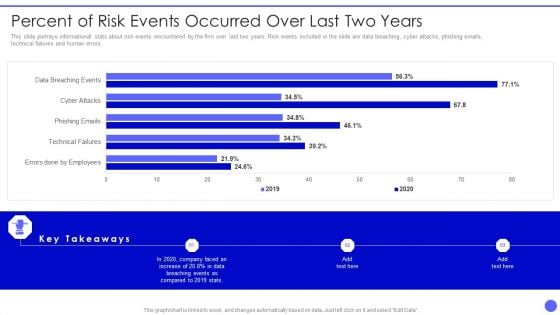
Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF bundle. Topics like Errors Done By Employees, Technical Failures, Phishing Emails, Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
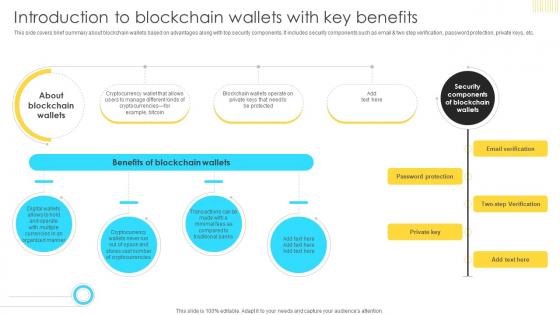
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc
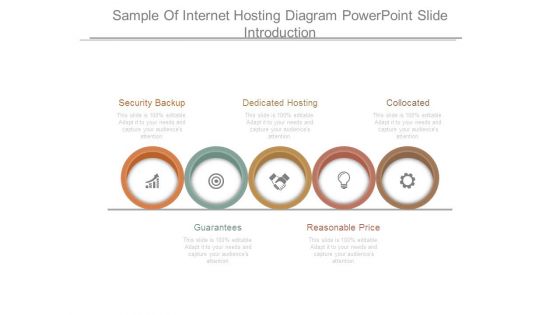
Sample Of Internet Hosting Diagram Powerpoint Slide Introduction
This is a sample of internet hosting diagram powerpoint slide introduction. This is a five stage process. The stages in this process are security backup, dedicated hosting, collocated, guarantees, reasonable price.
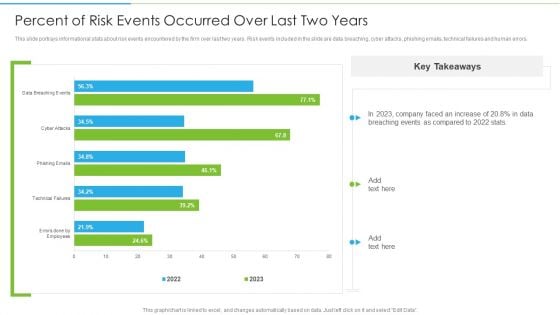
Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
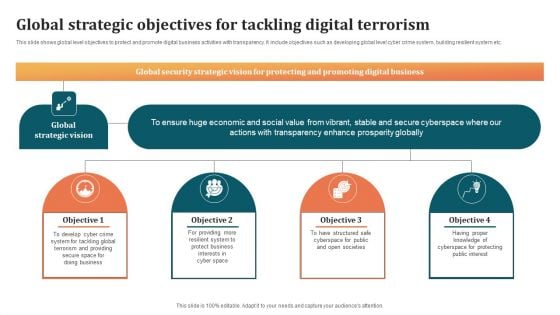
Global Strategic Objectives For Tackling Digital Terrorism Structure PDF
This slide shows global level objectives to protect and promote digital business activities with transparency. It include objectives such as developing global level cyber crime system, building resilient system etc. Presenting Global Strategic Objectives For Tackling Digital Terrorism Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Cyber Crime System, Global, Economic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
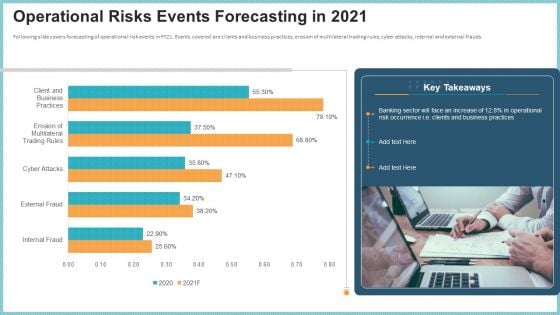
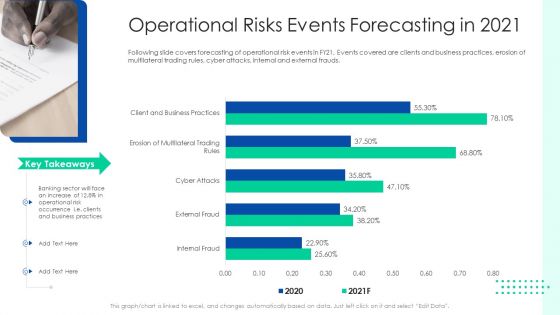
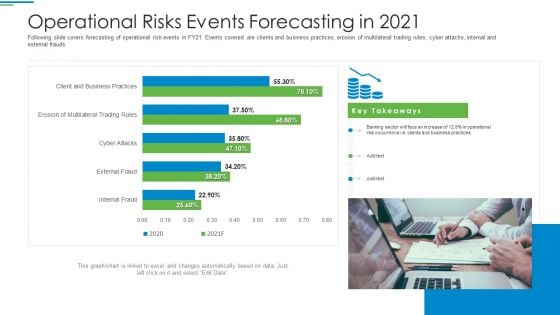
OP Risk Management Operational Risks Events Forecasting In 2021 Designs PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver an awe inspiring pitch with this creative op risk management operational risks events forecasting in 2021 designs pdf bundle. Topics like client and business practices, erosion of multilateral trading rules, cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Initiating Hazard Managing Structure Firm Operational Risks Events Forecasting In 2021 Designs PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this initiating hazard managing structure firm operational risks events forecasting in 2021 designs pdf. Use them to share invaluable insights on operational risk events, clients, business practices, cyber attacks, internal and external frauds and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Operational Risk Management Structure In Financial Companies Operational Risks Events Forecasting In 2021 Rules PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risks events forecasting in 2021 rules pdf bundle. Topics like business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
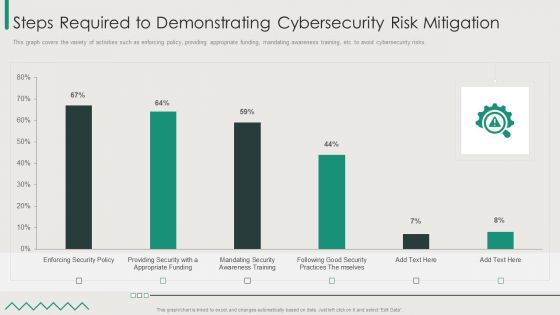
Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
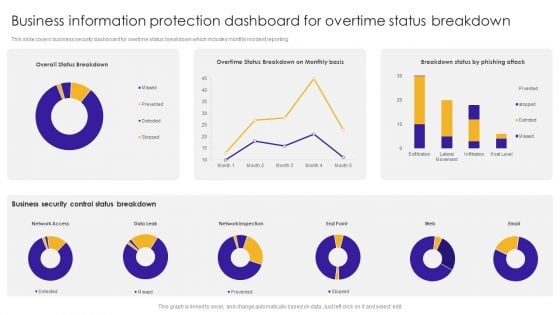
Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Evolving BI Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Demonstration PDF
This slide portrays information regarding tracking essential activities in intelligence infrastructure dashboard in terms of IT operations, security, business analytics, internet of things, etc. Deliver an awe inspiring pitch with this creative evolving bi infrastructure tracking intelligence infrastructure activities dashboard demonstration pdf bundle. Topics like application delivery, business analytics, internet of things, it operations, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Distributed Computing IT Dashboard For Edge Computing Tracking Template PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver and pitch your topic in the best possible manner with this distributed computing it dashboard for edge computing tracking template pdf. Use them to share invaluable insights on monitoring, security, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
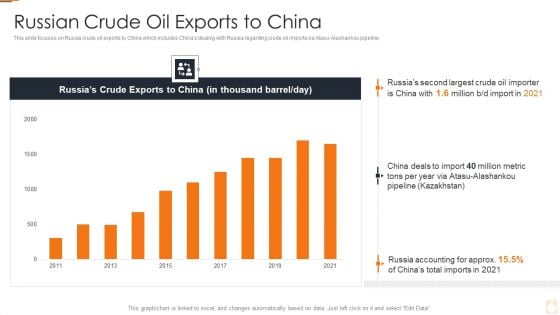
Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF
Deliver an awe inspiring pitch with this creative Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF bundle. Topics like Higher Energy Prices, Trade And Supply Chains, Increase In Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
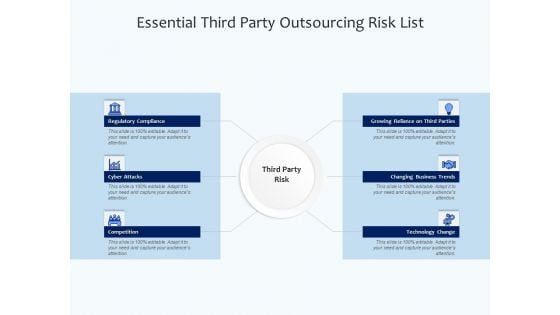
Essential Third Party Outsourcing Risk List Ppt PowerPoint Presentation File Sample PDF
Presenting essential third party outsourcing risk list ppt powerpoint presentation file sample pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including regulatory compliance, cyber attacks, competition, changing business trends, technology change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
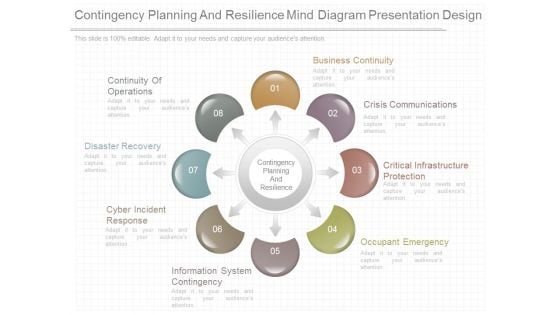
Contingency Planning And Resilience Mind Diagram Presentation Design
This is a contingency planning and resilience mind diagram presentation design. This is a eight stage process. The stages in this process are contingency planning and resilience, business continuity, crisis communications, critical infrastructure protection, occupant emergency, information system contingency, cyber incident response, disaster recovery, continuity of operations.
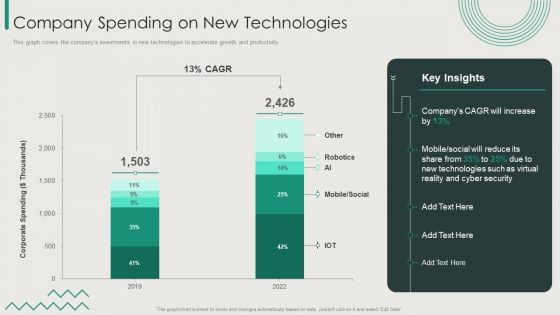
Organization Transition Company Spending On New Technologies Ppt PowerPoint Presentation Gallery Good PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Transition Company Spending On New Technologies Ppt PowerPoint Presentation Gallery Good PDF bundle. Topics like Mobile, Social, Cyber Security, New Technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
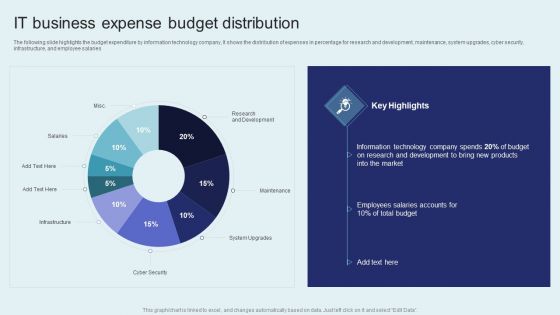
IT Firm Financial Statement IT Business Expense Budget Distribution Pictures PDF
The following slide highlights the budget expenditure by information technology company, It shows the distribution of expenses in percentage for research and development, maintenance, system upgrades, cyber security, infrastructure, and employee salaries. There are so many reasons you need a IT Firm Financial Statement IT Business Expense Budget Distribution Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
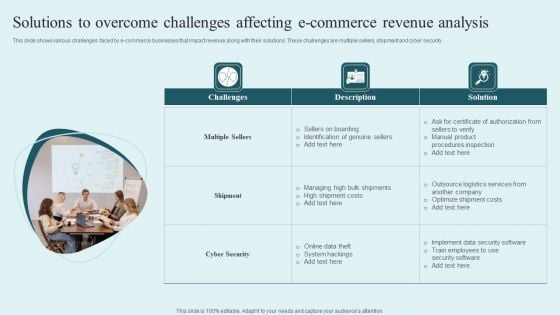
Solutions To Overcome Challenges Affecting E Commerce Revenue Analysis Summary PDF
This slide shows various challenges faced by e-commerce businesses that impact revenue along with their solutions. These challenges are multiple sellers, shipment and cyber security. Presenting Solutions To Overcome Challenges Affecting E Commerce Revenue Analysis Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Challenges, Solution, Multiple Sellers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
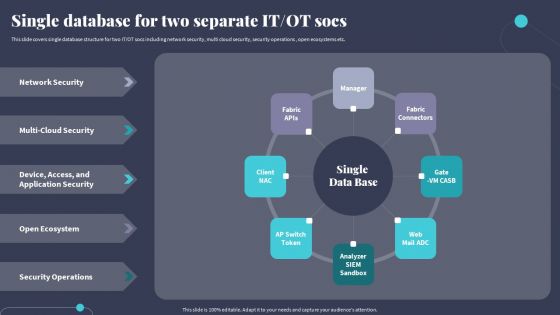
Tactics For Incorporating OT And IT With The Latest PI System Single Database For Two Separate It Ot Socs Template PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Retrieve professionally designed Tactics For Incorporating OT And IT With The Latest PI System Single Database For Two Separate It Ot Socs Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
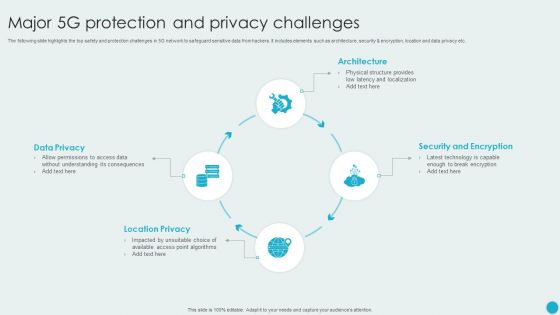
Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
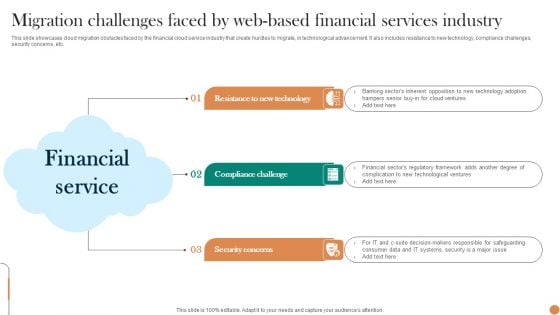
Migration Challenges Faced By Web Based Financial Services Industry Professional PDF
This slide showcases cloud migration obstacles faced by the financial cloud service industry that create hurdles to migrate, in technological advancement. It also includes resistance to new technology, compliance challenges, security concerns, etc. Presenting Migration Challenges Faced By Web Based Financial Services Industry Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Resistance To New Technology, Compliance Challenge, Security Concerns. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
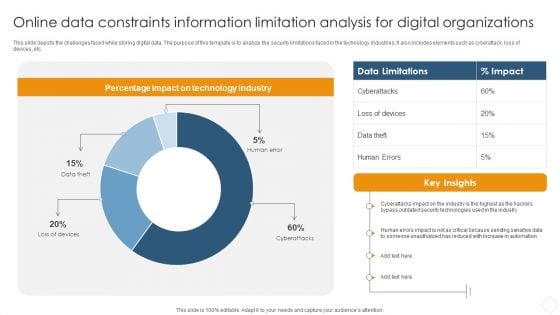
Online Data Constraints Information Limitation Analysis For Digital Organizations Information PDF
This slide depicts the challenges faced while storing digital data. The purpose of this template is to analyze the security limitations faced in the technology industries. It also includes elements such as cyberattack, loss of devices, etc.Pitch your topic with ease and precision using this Online Data Constraints Information Limitation Analysis For Digital Organizations Information PDF. This layout presents information on Percentage Impact, Technology Industry, Security Technologies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Website Hosting Service Package Requisites Themes PDF
This slide mentions the requisites for choosing web hosting service package which ensure smoother accessibility and provides security to transactions. It includes file transfer protocol, adequate storage space, reasonable bandwidth , 99.9 percentage uptime and security factors. Persuade your audience using this Website Hosting Service Package Requisites Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Adequate Storage Space, Reasonable Bandwidth, Transfer Protocol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
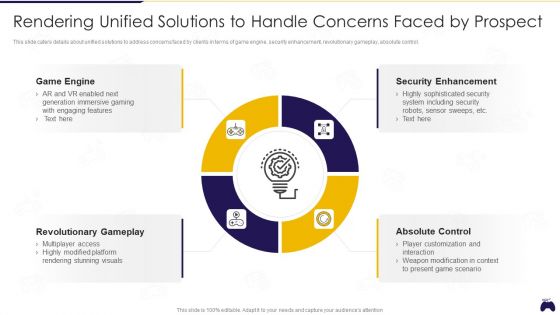
Online Gaming Fundraising Pitch Deck Rendering Unified Solutions To Handle Concerns Faced By Prospect Structure PDF
This slide caters details about unified solutions to address concerns faced by clients in terms of game engine, security enhancement, revolutionary gameplay, absolute control. This is a online gaming fundraising pitch deck rendering unified solutions to handle concerns faced by prospect structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like game engine, revolutionary gameplay, absolute control, security enhancement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
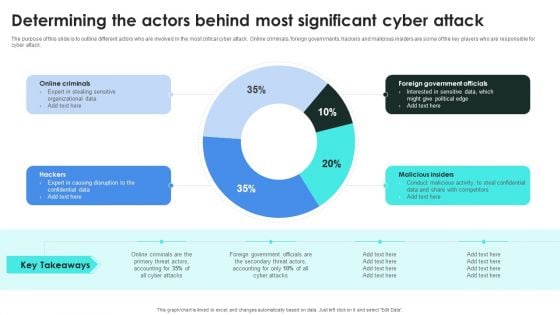
Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
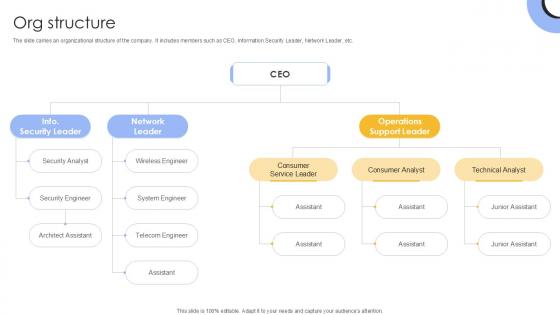
Org Structure Investment Company Investor Funding Elevator Ppt Presentation
The slide carries an organizational structure of the company. It includes members such as CEO, Information Security Leader, Network Leader, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Org Structure Investment Company Investor Funding Elevator Ppt Presentation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide carries an organizational structure of the company. It includes members such as CEO, Information Security Leader, Network Leader, etc.
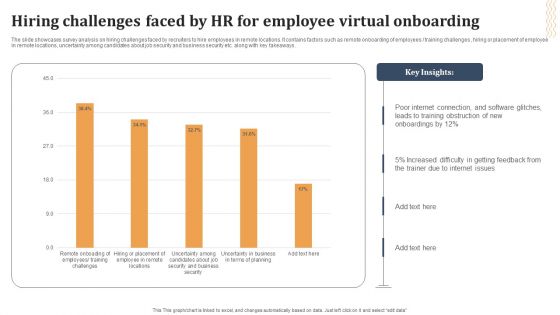
Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF
The slide showcases survey analysis on hiring challenges faced by recruiters to hire employees in remote locations. It contains factors such as remote onboarding of employees training challenges , hiring or placement of employee in remote locations, uncertainty among candidates about job security and business security etc. along with key takeaways. Showcasing this set of slides titled Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF. The topics addressed in these templates are Internet Connection, Software Glitches, Internet Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
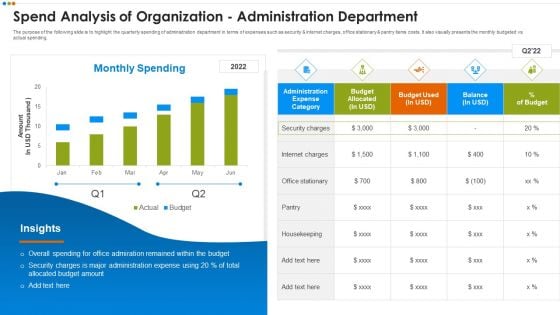
Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending.Deliver an awe inspiring pitch with this creative Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF bundle. Topics like Overall Spending, Admiration Remained, Security Administration Expense can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
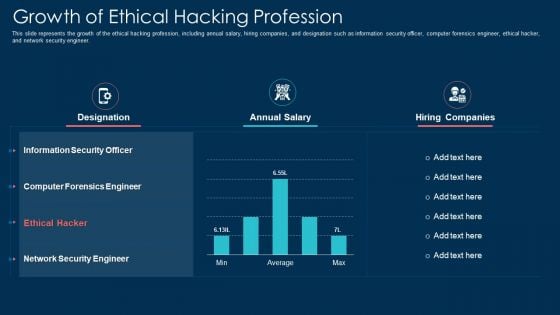
Growth Of Ethical Hacking Profession Ppt Infographic Template Templates PDF
This slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer. Deliver and pitch your topic in the best possible manner with this growth of ethical hacking profession ppt infographic template templates pdf. Use them to share invaluable insights on growth of ethical hacking profession and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Cost Management Model Components Clipart PDF
This slide shows cloud cost optimization components to make coordination between complex operations of cloud system. It include elements like orchestration, cloud network security and compliance setup etc. Presenting Cloud Cost Management Model Components Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Orchestration Automation, Cloud Network Security, Compliance Governance Setup. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
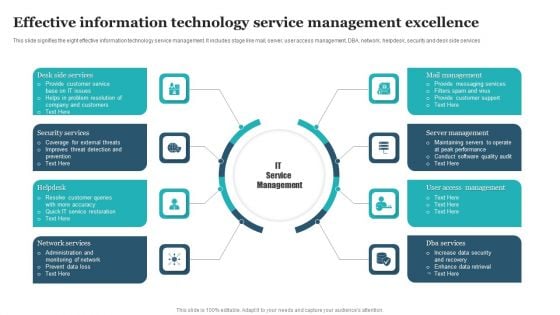
Effective Information Technology Service Management Excellence Rules PDF
This slide signifies the eight effective information technology service management. It includes stage like mail, server, user access management, DBA, network, helpdesk, security and desk side services. Presenting Effective Information Technology Service Management Excellence Rules PDF to dispense important information. This template comprises Eight stages. It also presents valuable insights into the topics including Desk Side Services, Mail Management, Security Services, Server Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
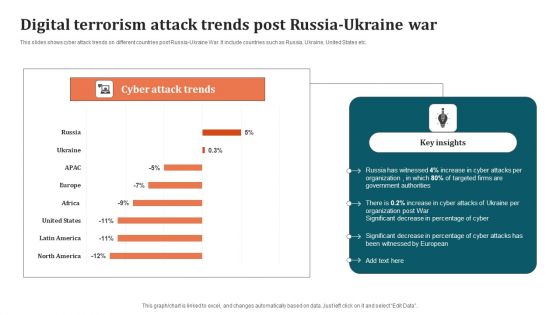
Digital Terrorism Attack Trends Post Russia Ukraine War Graphics PDF
This slides shows cyber attack trends on different countries post Russia-Ukraine War. It include countries such as Russia, Ukraine, United States etc. Pitch your topic with ease and precision using this Digital Terrorism Attack Trends Post Russia Ukraine War Graphics PDF. This layout presents information on Organization, Digital Terrorism Attack Trends. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
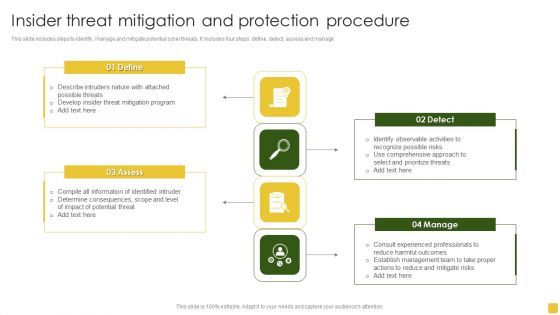
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
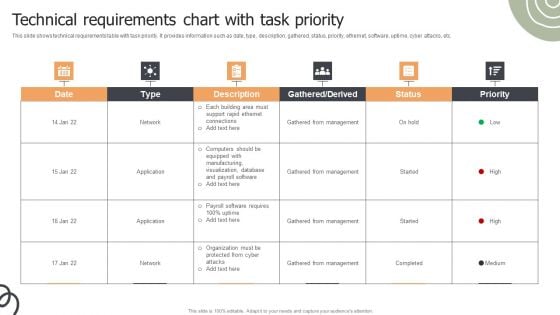
Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF
This slide shows technical requirements table with task priority. It provides information such as date, type, description, gathered, status, priority, ethernet, software, uptime, cyber attacks, etc. Pitch your topic with ease and precision using this Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF. This layout presents information on Gathered From Management, Network, Application. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
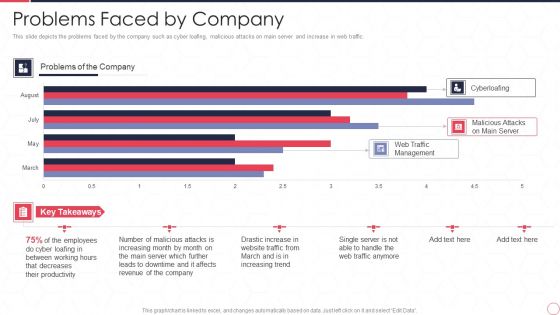
Reverse Proxy Server IT Problems Faced By Company Ppt Summary Inspiration PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Deliver and pitch your topic in the best possible manner with this reverse proxy server it problems faced by company ppt summary inspiration pdf. Use them to share invaluable insights on web traffic management, malicious attacks on main server, cyberloafing, employee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
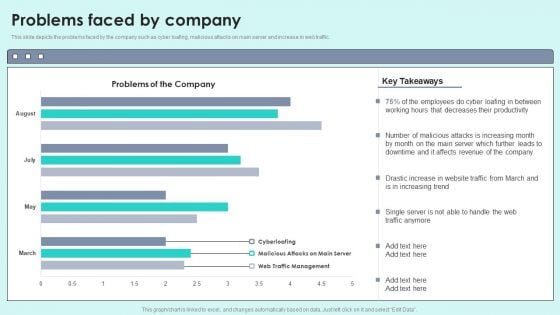
Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic.Deliver and pitch your topic in the best possible manner with this Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF. Use them to share invaluable insights on Decreases Productivity, Malicious Attacks, Affects Revenue and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Risks Events Forecasting In 2021 Ppt PowerPoint Presentation Ideas Picture PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.Deliver an awe-inspiring pitch with this creative operational risks events forecasting in 2021 ppt powerpoint presentation ideas picture pdf. bundle. Topics like operational risks events forecasting in 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
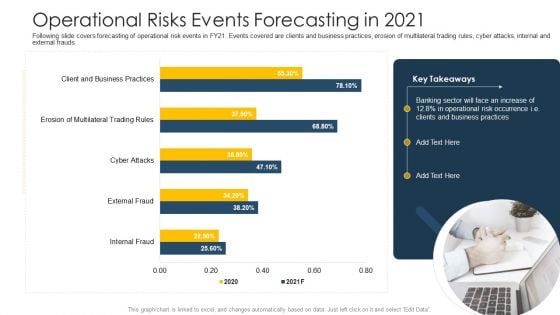
Establishing Operational Risk Framework Banking Operational Risks Events Forecasting In 2021 Portrait PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this establishing operational risk framework banking operational risks events forecasting in 2021 portrait pdf. Use them to share invaluable insights on business practices, operational risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
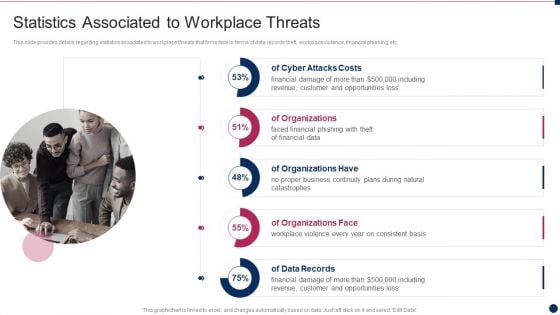
Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
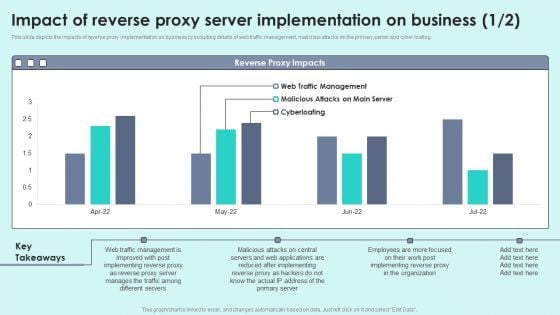
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing.Deliver an awe inspiring pitch with this creative Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF bundle. Topics like After Implementing, Manages Traffic, Different Servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
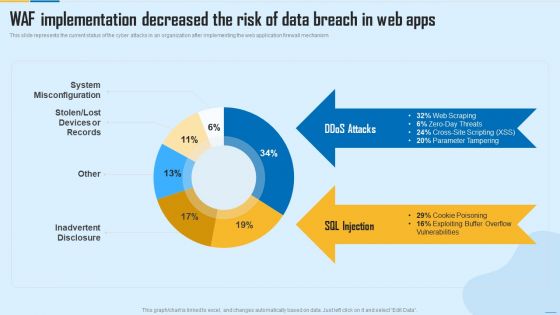
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
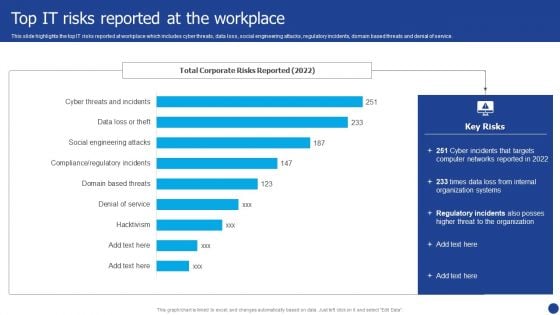
Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
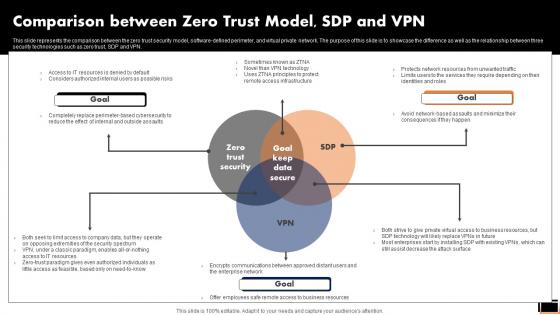
Comparison Between Zero Trust ModelSDP And Vpn Software Defined Perimeter SDP
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
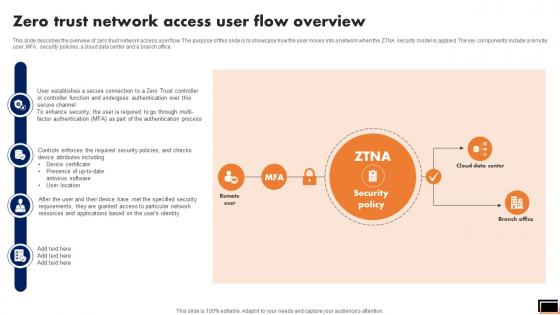
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Login For Income Statement Powerpoint Template
Our above slide display graphics of log in page on mobile phone with money flowing out of tap. Download this diagram slide to display security measures for money saving account. Adjust the above diagram in your business presentations to visually support your content.

Smart Metering Management Diagram Good Ppt Example
This is a smart metering management diagram good ppt example. This is a eight stage process. The stages in this process are reporting, customer information system, billing system, asset management, network information system, security manager, dc persistency, monitoring and control, meter data management.
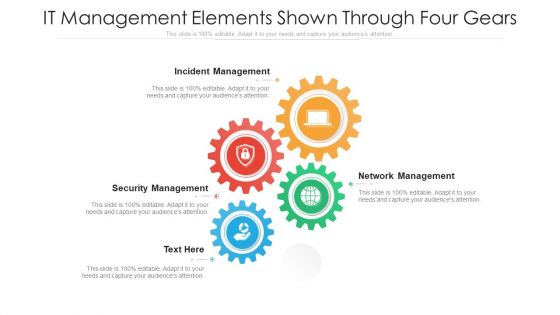
IT Management Elements Shown Through Four Gears Ppt PowerPoint Presentation Gallery Clipart Images PDF
Presenting it management elements shown through four gears ppt powerpoint presentation gallery clipart images pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
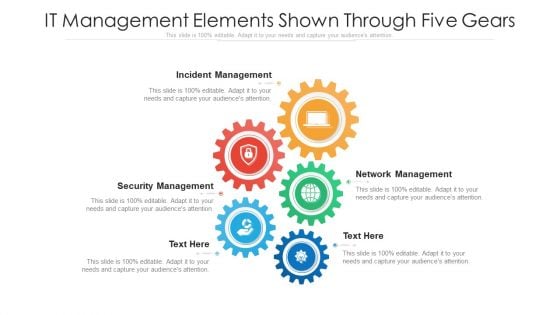
IT Management Elements Shown Through Five Gears Ppt PowerPoint Presentation File Portfolio PDF
Presenting it management elements shown through five gears ppt powerpoint presentation file portfolio pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
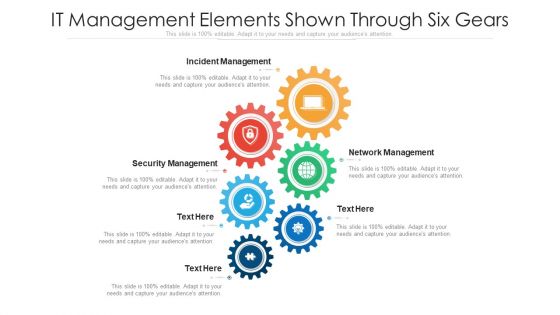
IT Management Elements Shown Through Six Gears Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting it management elements shown through six gears ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Management Elements Shown Through Seven Gears Ppt PowerPoint Presentation Gallery Example PDF
Presenting it management elements shown through seven gears ppt powerpoint presentation gallery example pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































