Cyber Security Icons

1 Network Diagram Showing Disaster Recovery To Remote Location Dr Ppt Slides
This image slide displays network diagram showing disaster recovery to remote locations. This image slide has been designed with graphic of cloud connected to various technology devices and database. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. This image may be used to explain concepts of database recovery through cloud computing. Use this PowerPoint template to express views on cloud computing, networking and security in your presentations. This image slide will enhance the quality of your presentations.
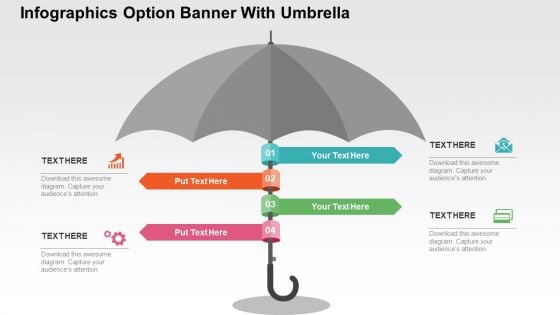
Infographics Option Banner With Umbrella Powerpoint Templates
Who doesn?t want to have a secure life? Be it financial security, safety of your child or safe environment at home and at work place. Well we hope for that but we can definitely save you from making ugly PowerPoint presentations. Above is the slide which is of umbrella with four options and along with it are four icons. This slide is one of our most downloaded PowerPoint slides and can be used to depict safety and security of any kind. The umbrella here can be used to indicate the safety, security, protection so you can choose this slide to show why it is safe to be associated with your company, or with your business, with your school, how your money is safe and secured in your bank or how it is safe if you pay online and much more. It is a multipurpose slide and can easily be modified as you want. Choose this slide to make your PowerPoint presentation look even more fantastic.
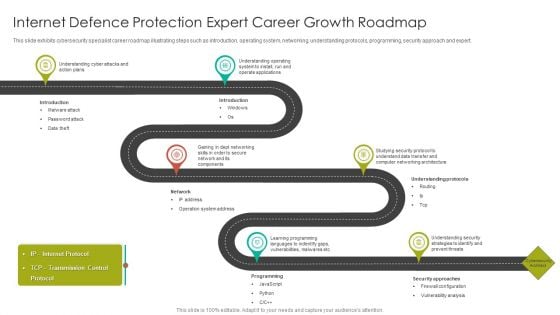
Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
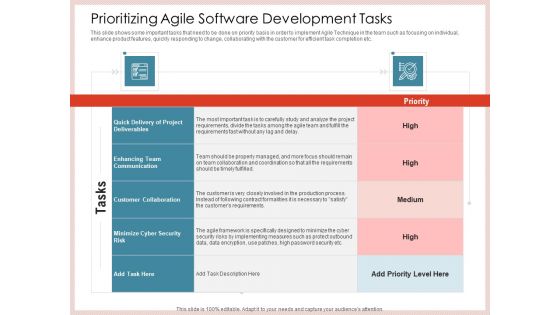
Agile Model Improve Task Team Performance Prioritizing Agile Software Development Tasks Themes PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc. Deliver an awe inspiring pitch with this creative agile model improve task team performance prioritizing agile software development tasks themes pdf bundle. Topics like communication, cyber security, collaboration, project deliverables can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
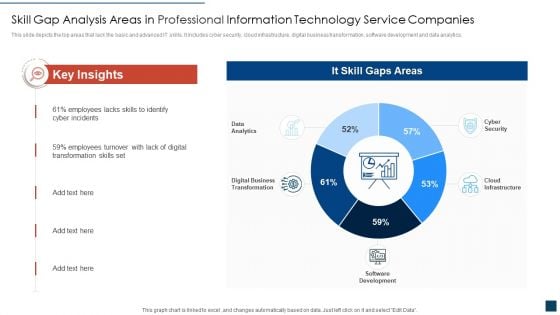
Skill Gap Analysis Areas In Professional Information Technology Service Companies Ideas PDF
This slide depicts the top areas that lack the basic and advanced IT skills. It includes cyber security, cloud infrastructure, digital business transformation, software development and data analytics. Showcasing this set of slides titled skill gap analysis areas in professional information technology service companies ideas pdf. The topics addressed in these templates are skill gap analysis areas in professional information technology service companies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
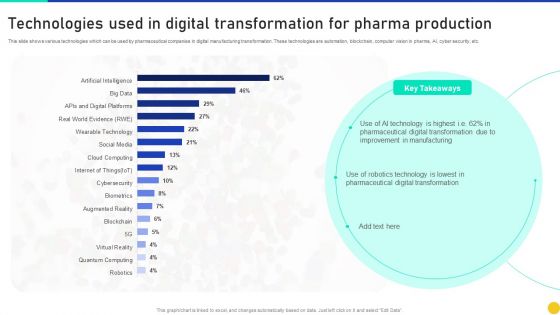
Technologies Used In Digital Transformation For Pharma Production Information PDF
This slide shows various technologies which can be used by pharmaceutical companies in digital manufacturing transformation. These technologies are automation, blockchain, computer vision in pharma, AI, cyber security, etc. Showcasing this set of slides titled Technologies Used In Digital Transformation For Pharma Production Information PDF. The topics addressed in these templates are Technologies Used Digital Transformation, Pharma Production. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
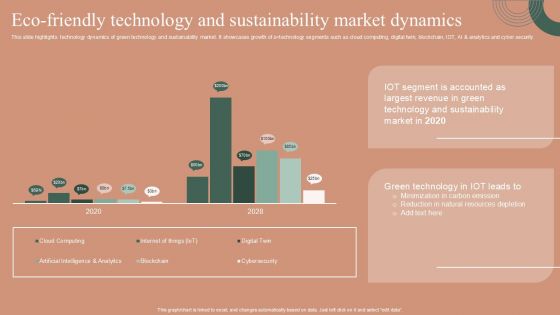
Eco Friendly Technology And Sustainability Market Dynamics Designs PDF

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security

Web Consulting Business Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. The Web Consulting Business Estimated Annual Budget Plan For Web Company is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.
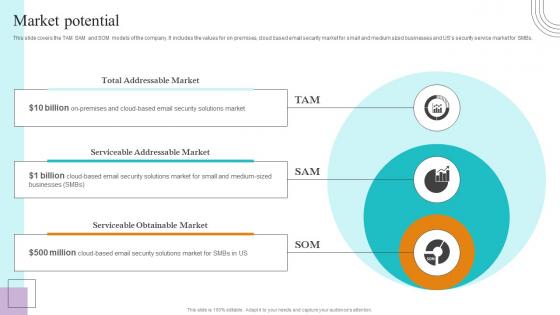
Market Potential Paubox Capital Funding Pitch Deck Diagrams Pdf
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. This modern and well arranged Market Potential Paubox Capital Funding Pitch Deck Diagrams Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
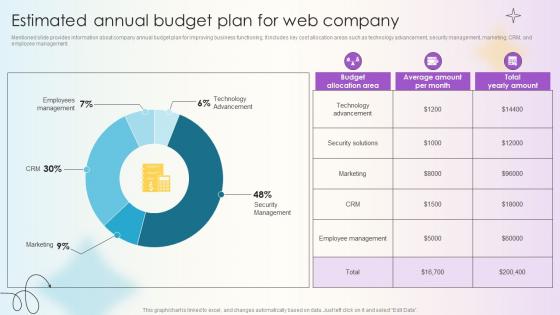
Managing Technical And Non Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. Explore a selection of the finest Managing Technical And Non Estimated Annual Budget Plan For Web Company here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Managing Technical And Non Estimated Annual Budget Plan For Web Company to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.
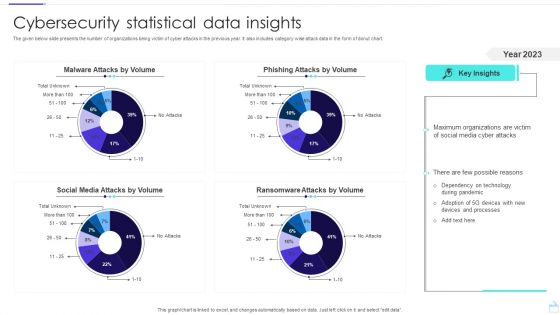
Cybersecurity Statistical Data Insights Sample PDF
The given below slide presents the number of organizations being victim of cyber attacks in the previous year. It also includes category wise attack data in the form of donut chart. Pitch your topic with ease and precision using this Cybersecurity Statistical Data Insights Sample PDF. This layout presents information on Social Media Attacks, Malware Attacks, Phishing Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
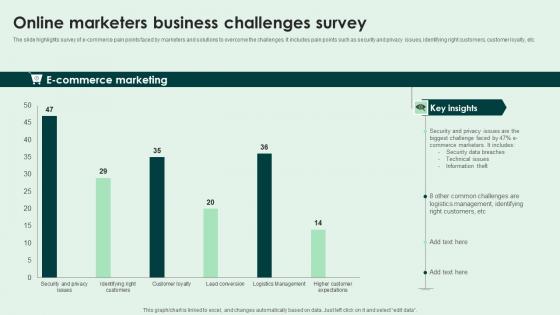
Online Marketers Business Challenges Survey Slides Pdf
The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc. Pitch your topic with ease and precision using this Online Marketers Business Challenges Survey Slides Pdf. This layout presents information on E Commerce Marketing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc.
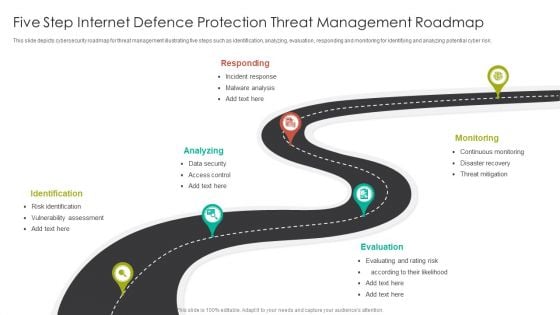
Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF
This slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk.Persuade your audience using this Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Analyzing, Responding. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
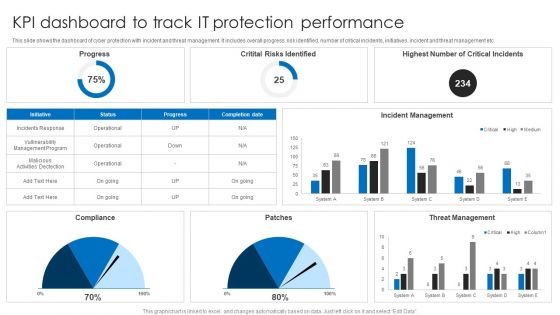
KPI Dashboard To Track IT Protection Performance Elements PDF
This slide shows the dashboard of cyber protection with incident and threat management. It includes overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Pitch your topic with ease and precision using this KPI Dashboard To Track IT Protection Performance Elements PDF. This layout presents information on Incident Management, Threat Management, Critital Risks Identified. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
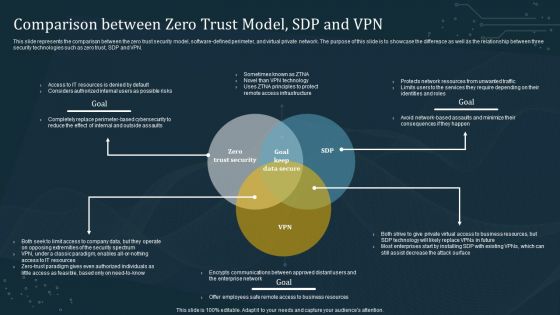
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
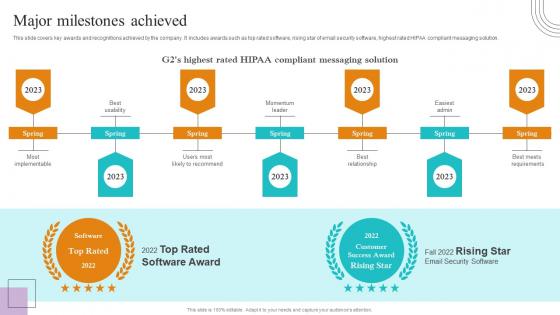
Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.

Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf
The following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc. Are you searching for a Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf from Slidegeeks today. The following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
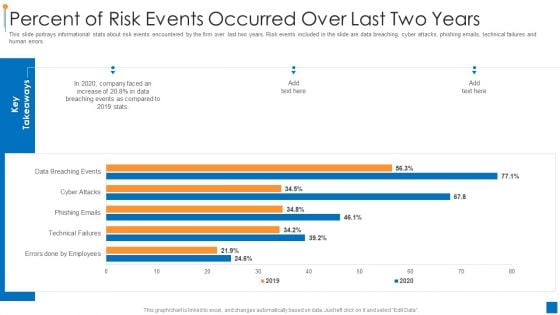
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
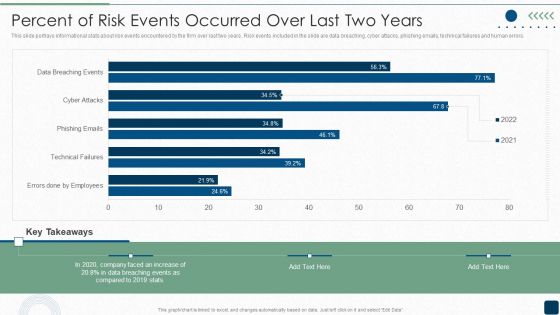
Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
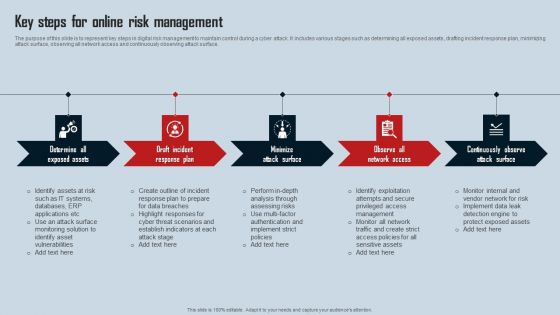
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
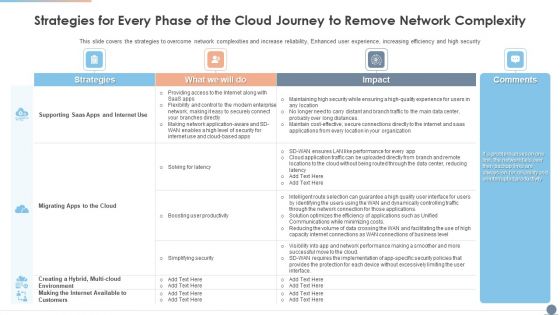
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Deliver and pitch your topic in the best possible manner with this Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF. Use them to share invaluable insights on Environment, Strategies, Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Web App Firewall Services IT Impact Of Web Application Firewall Sample PDF
This slide represents the Web Application Firewall deployment pricing, and it covers the price list for resource types such as bot control, requests, and management. Deliver an awe inspiring pitch with this creative web app firewall services it impact of web application firewall sample pdf bundle. Topics like reduced, security expenses, revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
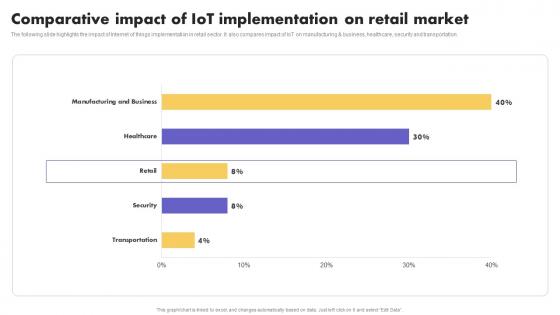
IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Create an editable IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
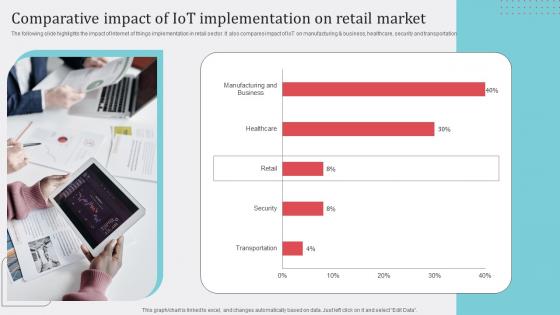
Comparative Impact IoT How Industrial IoT Is Changing Worldwide Microsoft Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation Boost your pitch with our creative Comparative Impact IoT How Industrial IoT Is Changing Worldwide Microsoft Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
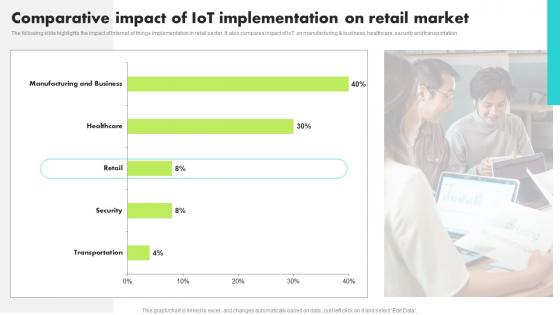
Comparative Impact Of IoT Implementation Guide For Retail IoT Solutions Analysis Demonstration Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation Find a pre designed and impeccable Comparative Impact Of IoT Implementation Guide For Retail IoT Solutions Analysis Demonstration Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
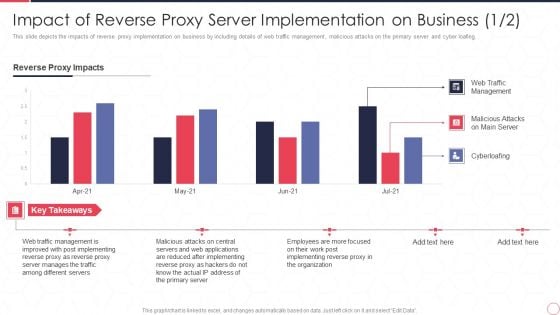
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy Server IT Ppt Professional Slides PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Deliver an awe inspiring pitch with this creative impact of reverse proxy server implementation on business reverse proxy server it ppt professional slides pdf bundle. Topics like reverse proxy impacts, web traffic management, malicious attacks on main server, cyberloafing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
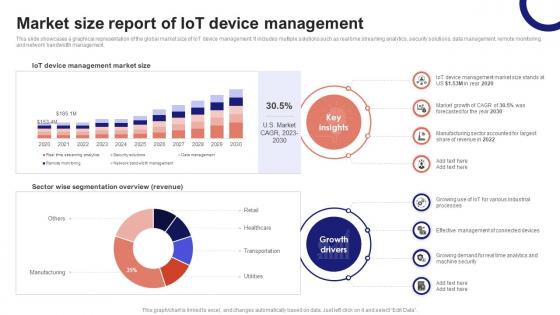
IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT Ss V
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. Slidegeeks has constructed IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management.
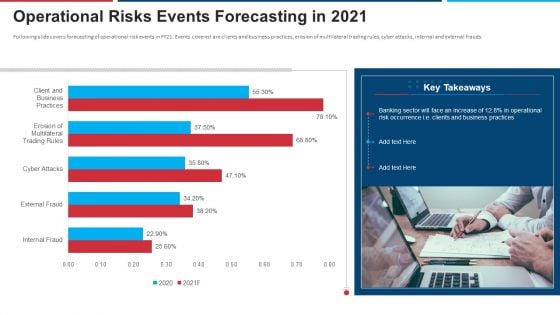
Mitigation Strategies For Operational Threat Operational Risks Events Forecasting In 2021 Ppt Infographic Template Microsoft PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks events forecasting in 2021 ppt infographic template microsoft pdf. Use them to share invaluable insights on banking, operational risk, occurrence, business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
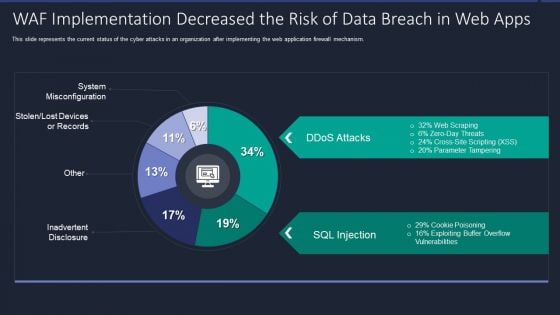
Web App Firewall Services IT WAF Implementation Decreased The Risk Of Data Breach In Web Apps Portrait PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this web app firewall services it waf implementation decreased the risk of data breach in web apps portrait pdf. Use them to share invaluable insights on waf implementation decreased the risk of data breach in web apps and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing
The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern. Retrieve professionally designed Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern
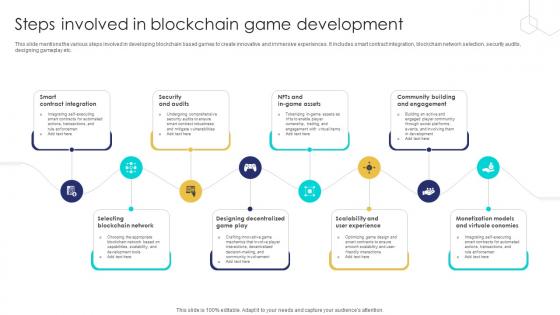
Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V
This slide mentions the various steps involved in developing blockchain based games to create innovative and immersive experiences. It includes smart contract integration, blockchain network selection, security audits, designing gameplay etc. Are you searching for a Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V from Slidegeeks today. This slide mentions the various steps involved in developing blockchain based games to create innovative and immersive experiences. It includes smart contract integration, blockchain network selection, security audits, designing gameplay etc.
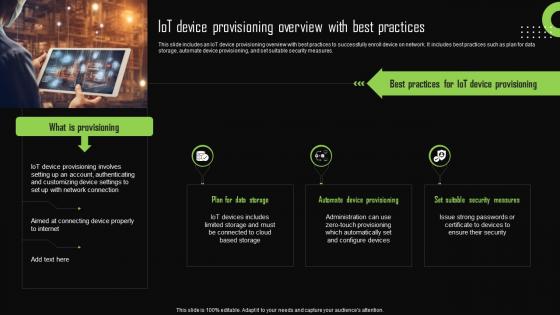
Iot Device Provisioning Overview With Best Practices Iot Device Management Sample Pdf
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Do you know about Slidesgeeks Iot Device Provisioning Overview With Best Practices Iot Device Management Sample Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures.

Impact Of Web Application Firewall Deployment On Client Company WAF Platform Professional PDF
This slide represents the Web Application Firewall deployment pricing, and it covers the price list for resource types such as bot control, requests, and management. Deliver an awe inspiring pitch with this creative Impact Of Web Application Firewall Deployment On Client Company WAF Platform Professional PDF bundle. Topics like Web Application, Revenue, Security Expenses can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
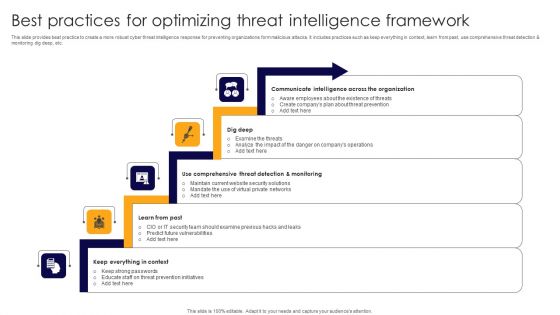
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
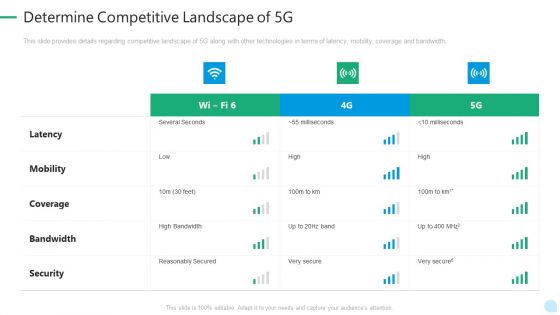
5G Network Technology Determine Competitive Landscape Of 5G Ppt Summary Visual Aids PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver and pitch your topic in the best possible manner with this 5g network technology determine competitive landscape of 5g ppt summary visual aids pdf. Use them to share invaluable insights on latency, mobility, coverage, bandwidth, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
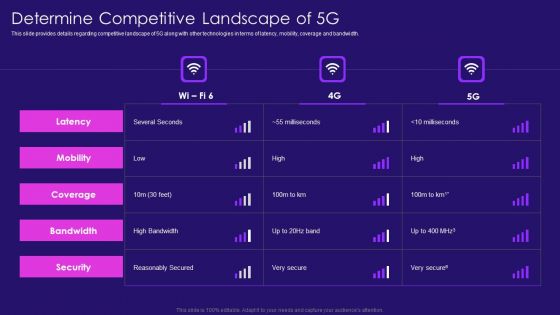
Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver an awe inspiring pitch with this creative Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF bundle. Topics like Bandwidth, Coverage, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
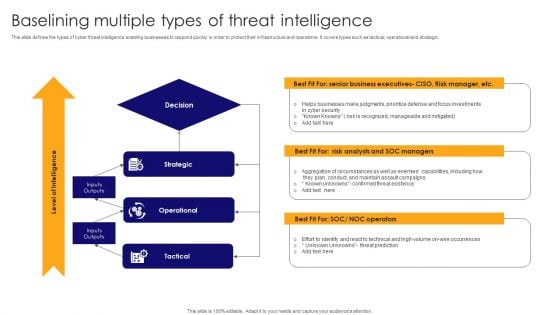
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
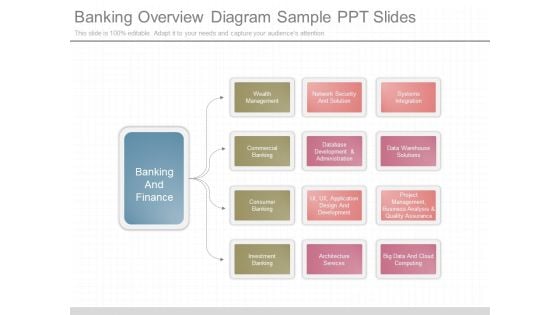
Banking Overview Diagram Sample Ppt Slides
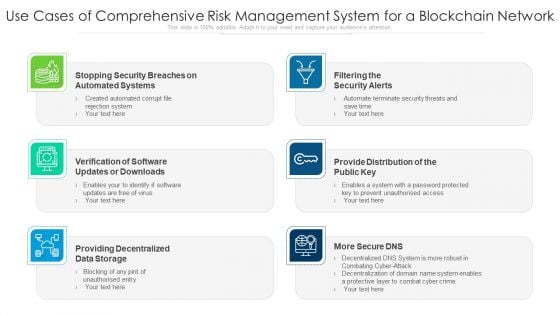
Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
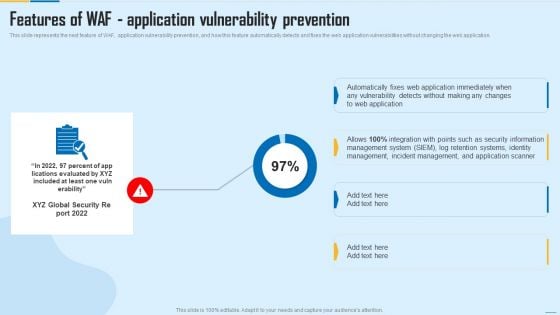
Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Deliver and pitch your topic in the best possible manner with this Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF. Use them to share invaluable insights on Management System, Incident Management, Security Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
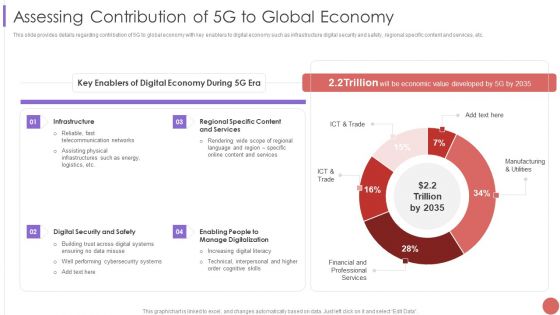
Assessing Contribution Of 5G To Global Economy Pictures PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc.Deliver an awe inspiring pitch with this creative Assessing Contribution Of 5G To Global Economy Pictures PDF bundle. Topics like Telecommunication Networks, Across Digital Systems, Manage Digitalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Understanding The Kubernetes Components Through Diagram Table Of Contents Ppt Ideas Graphic Images
Presenting this set of slides with name understanding the kubernetes components through diagram table of contents ppt ideas graphic images. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
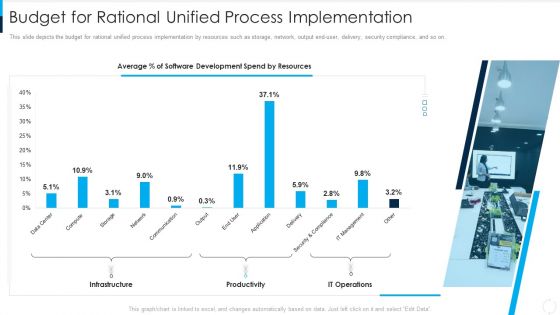
RUP Model Budget For Rational Unified Process Implementation Ppt Outline Layout PDF
This slide depicts the budget for rational unified process implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process implementation ppt outline layout pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Dashboard For Concurrent Computing Tracking Ppt Visual Aids Ideas PDF
picts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver an awe inspiring pitch with this creative dashboard for concurrent computing tracking ppt visual aids ideas pdf bundle. Topics like dashboard for concurrent computing tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
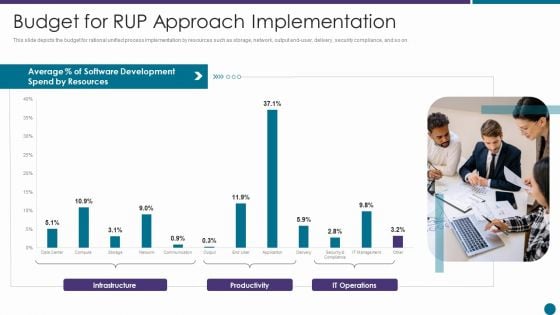
Budget For RUP Approach Implementation Ppt Professional Designs PDF
This slide depicts the budget for rational unified process implementation by resources such as storage, network, output end user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative budget for rup approach implementation ppt professional designs pdf bundle. Topics like resources, average, development, productivity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
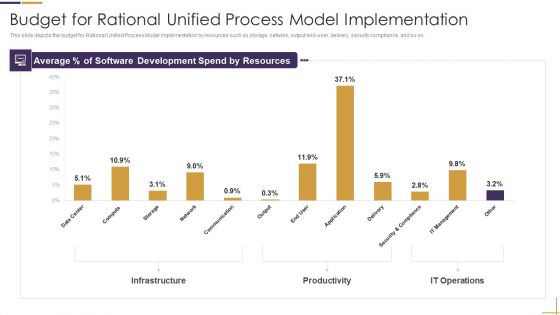
RUP Model Budget For Rational Unified Process Model Implementation Ppt Styles Inspiration PDF
This slide depicts the budget for Rational Unified Process Model implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process model implementation ppt styles inspiration pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
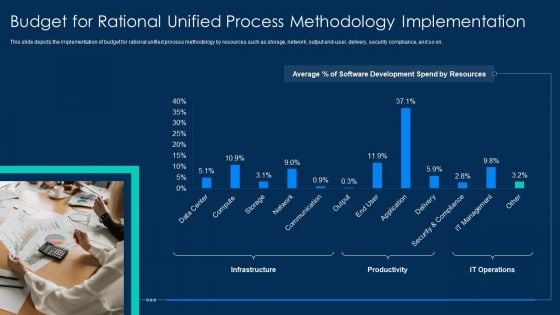
RUP Methodology Budget For Rational Unified Process Methodology Implementation Professional PDF
This slide depicts the implementation of budget for rational unified process methodology by resources such as storage, network, output end-user, delivery, security compliance, and so on.Deliver and pitch your topic in the best possible manner with this RUP Methodology Budget For Rational Unified Process Methodology Implementation Professional PDF Use them to share invaluable insights on Budget For Rational Unified Process Methodology Implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Distributed Computing Dashboard For Edge Computing Tracking Brochure PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details.Deliver and pitch your topic in the best possible manner with this Distributed Computing Dashboard For Edge Computing Tracking Brochure PDF Use them to share invaluable insights on Device Recommendation, Most Prevalent, Device Recommendation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
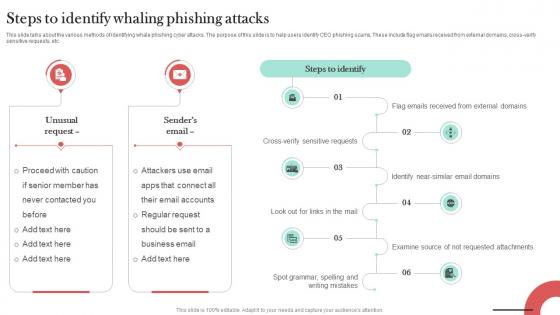
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.
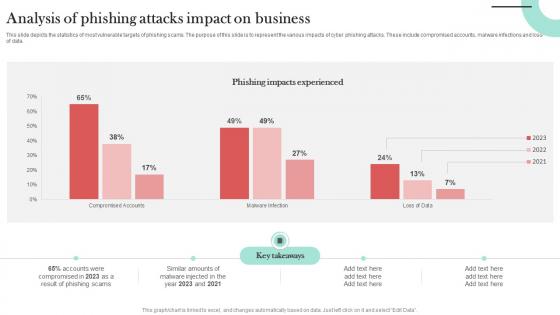
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
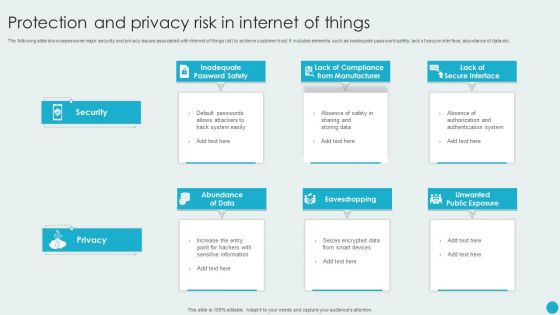
Protection And Privacy Risk In Internet Of Things Topics PDF
The following slide showcases some major security and privacy issues associated with internet of things iot to achieve customer trust. It includes elements such as inadequate password safety, lack of secure interface, abundance of data etc. Presenting Protection And Privacy Risk In Internet Of Things Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Abundance Of Data, Eavesdropping, Unwanted Public Exposure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
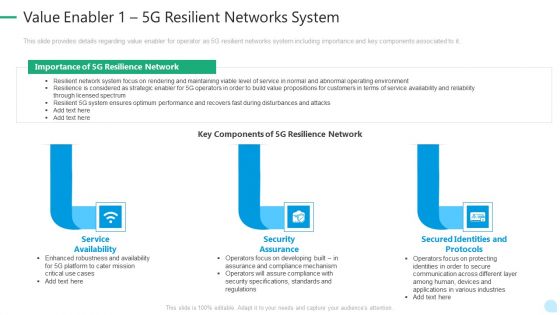
5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
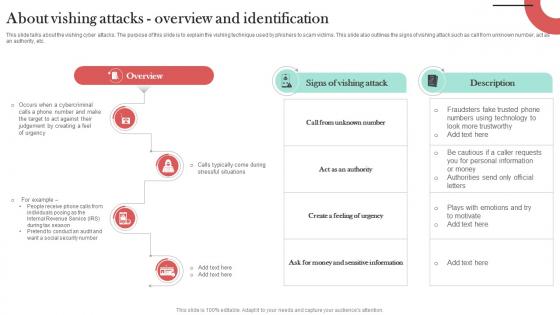
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.
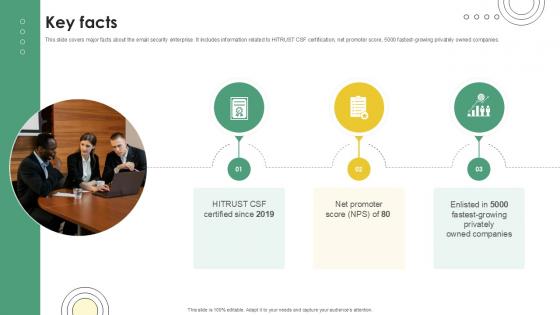
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.

Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. If you are looking for a format to display your unique thoughts, then the professionally designed Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.


 Continue with Email
Continue with Email

 Home
Home


































