Cyber Security Risk
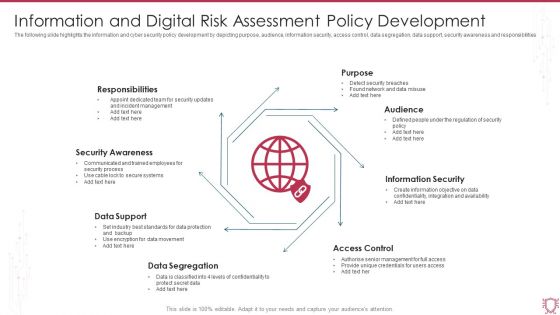
Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
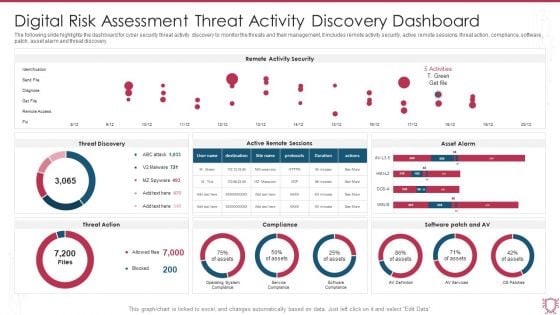
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
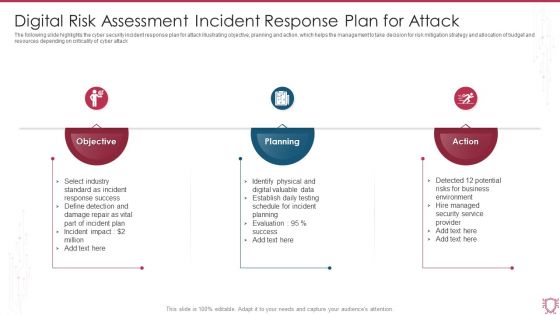
Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
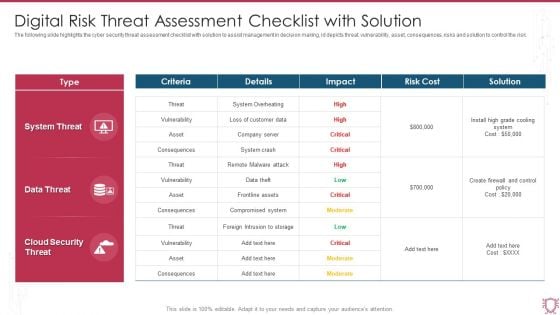
Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Evaluate Impact And Probability Of Risk Occurrence Ppt PowerPoint Presentation Diagram Images PDF
The following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Evaluate Impact And Probability Of Risk Occurrence Ppt PowerPoint Presentation Diagram Images PDF from Slidegeeks and deliver a wonderful presentation.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF
The following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
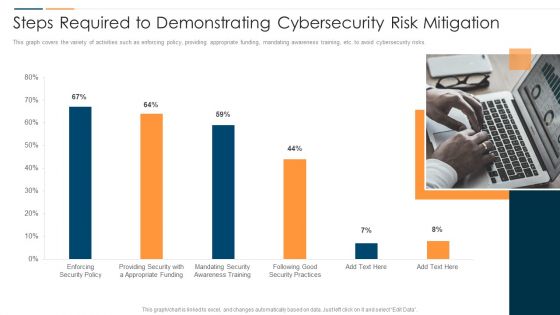
Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
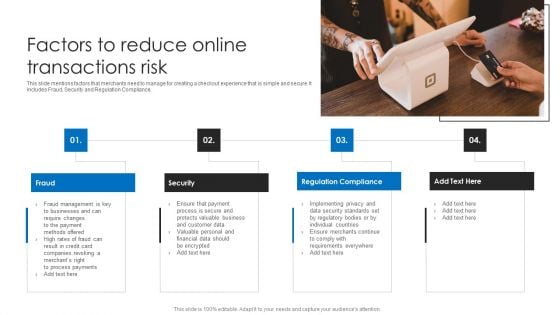
Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF
This slide mentions factors that merchants need to manage for creating a checkout experience that is simple and secure. It includes Fraud, Security and Regulation Compliance. Presenting Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fraud, Security, Regulation Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Evaluation Results Showing Bank Risk Ppt PowerPoint Presentation File Influencers PDF
Presenting evaluation results showing bank risk ppt powerpoint presentation file influencers pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including cyber security, perform, legal audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
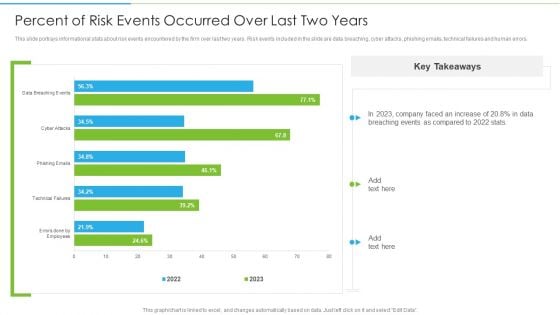
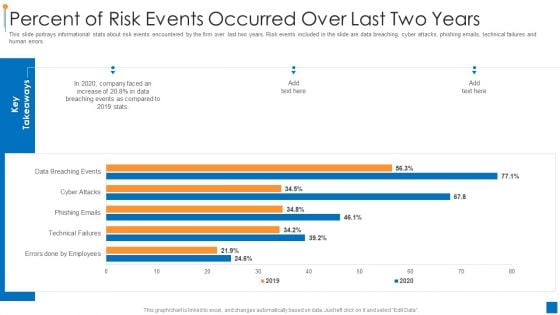
Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
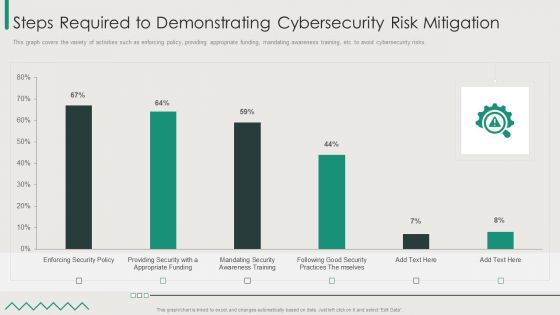
Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
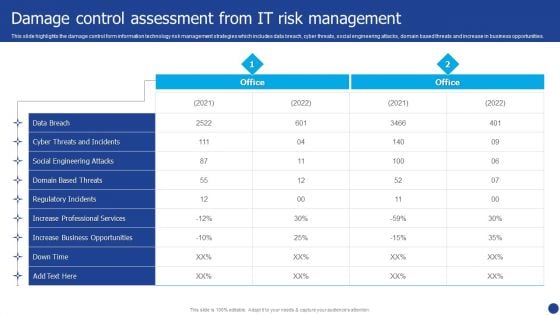
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
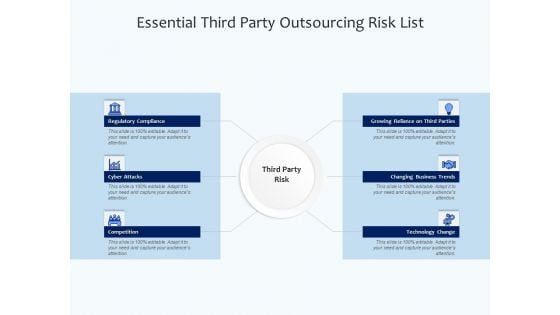
Essential Third Party Outsourcing Risk List Ppt PowerPoint Presentation File Sample PDF
Presenting essential third party outsourcing risk list ppt powerpoint presentation file sample pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including regulatory compliance, cyber attacks, competition, changing business trends, technology change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
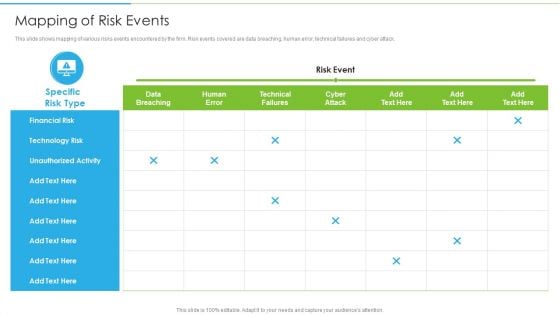
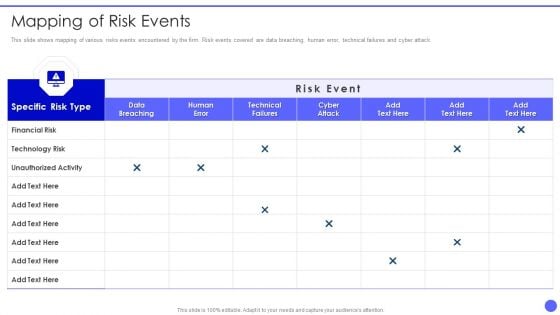
Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF bundle. Topics like Financial Risk, Technology Risk, Unauthorized Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
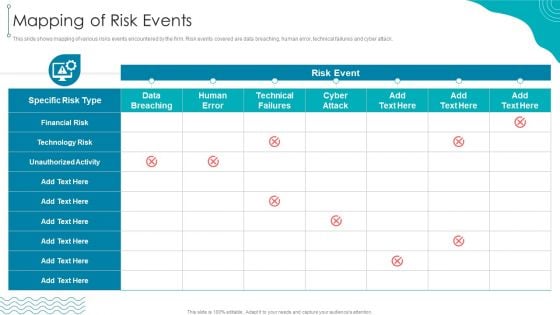
ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Optimizing Tasks Team Collaboration Agile Operations Prioritizing Agile Software Development Tasks Guidelines PDF
Presenting this set of slides with name optimizing tasks team collaboration agile operations prioritizing agile software development tasks guidelines pdf. This is a five stage process. The stages in this process are quick delivery of project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
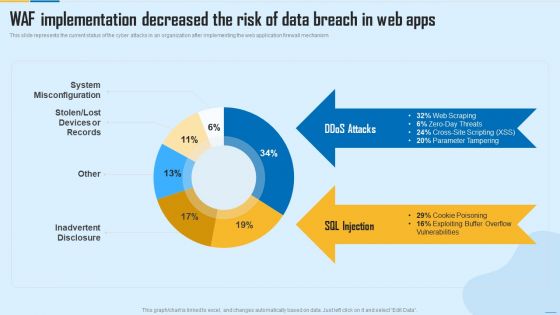
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF. Use them to share invaluable insights on Specific Risk Type, Financial Risk, Technology Risk, Unauthorized Activity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Online Risk Management Dashboard For Tracking Threats And Attacks Icons PDF
The purpose of this slide is to represent dashboard to monitor risks and cyber threats for efficient risk management. It includes various types of key performance indicators such as types of risks, severities, sources and risk meter. Showcasing this set of slides titled Online Risk Management Dashboard For Tracking Threats And Attacks Icons PDF. The topics addressed in these templates are Attack, Indication Severities, Sources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
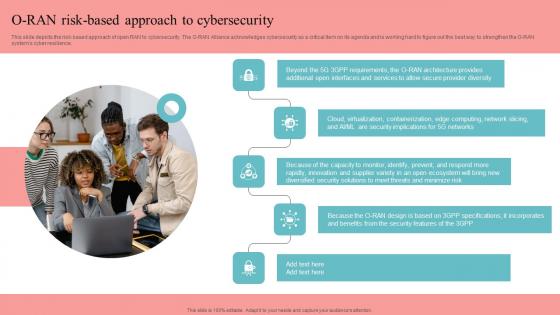
O RAN Risk Based Approach To Cybersecurity Unlocking The Potential Of Open RAN Information Pdf
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward O RAN Risk Based Approach To Cybersecurity Unlocking The Potential Of Open RAN Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal O RAN Risk Based Approach To Cybersecurity Unlocking The Potential Of Open RAN Information Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience.
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
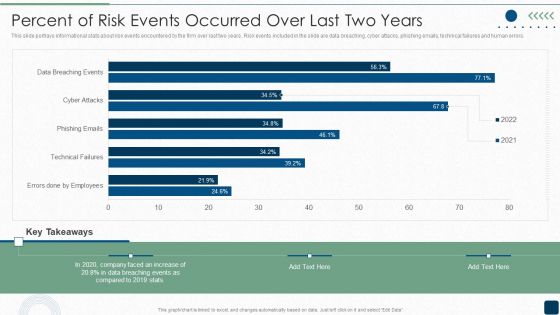
Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management For Organization Essential Assets Addressing Various Ways To Handle Insider Graphics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a risk management for organization essential assets addressing various ways to handle insider graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, track baseline behavior networks and individuals, render least amount of privilege, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
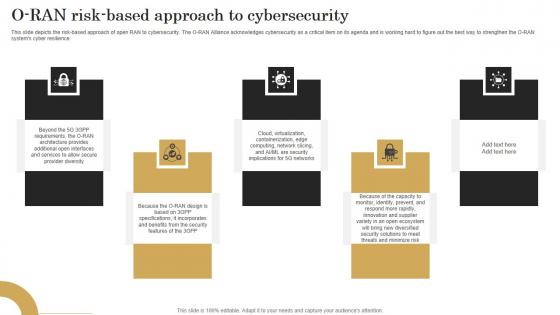
O Ran Risk Based Approach To Cybersecurity Revolutionizing Mobile Networks Guidelines PDF
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download O Ran Risk Based Approach To Cybersecurity Revolutionizing Mobile Networks Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience.
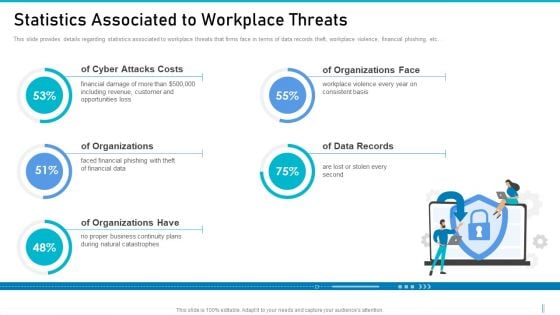
Risk Management For Organization Essential Assets Statistics Associated To Workplace Threats Structure PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Presenting risk management for organization essential assets statistics associated to workplace threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cyber attacks costs, data records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Case Of Online Risk Management For Health Care Sector Background PDF
This slide represents a use case of digital risk management in health care sector to understand its impact. It includes components like goal, issues faced by hospital, risk mitigation action steps and result. Presenting Use Case Of Online Risk Management For Health Care Sector Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Threats, Risk Mitigation Action Steps, Results. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF. Use them to share invaluable insights on Reduce Ransomware, Reduce Distributed, Approaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
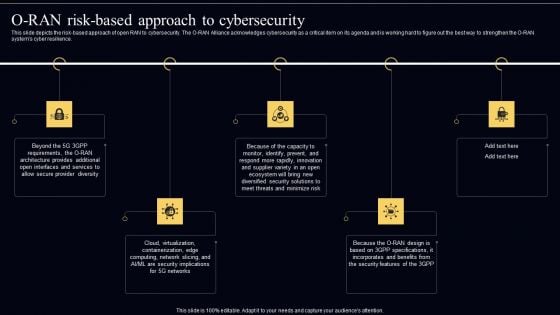
Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF
This slide depicts the risk based approach of open RAN to cybersecurity. The O RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O RAN systems cyber resilience. Get a simple yet stunning designed Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF today and make your presentation stand out from the rest.

Risk Recognition Automation Need For Siem Software In Your Company Ppt Styles Gridlines PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management This is a risk recognition automation need for siem software in your company ppt styles gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add-ons, using a customized web application firewall etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF today and make your presentation stand out from the rest.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF
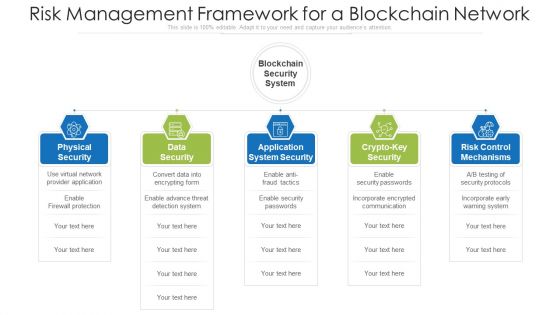
Risk Management Framework For A Blockchain Network Ppt PowerPoint Presentation Portfolio Format Ideas PDF
Persuade your audience using this risk management framework for a blockchain network ppt powerpoint presentation portfolio format ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application system security, risk control mechanisms, physical security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
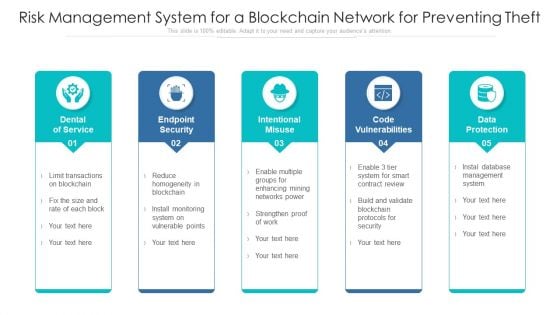
Risk Management System For A Blockchain Network For Preventing Theft Ppt PowerPoint Presentation Layouts Deck PDF
Presenting risk management system for a blockchain network for preventing theft ppt powerpoint presentation layouts deck pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including endpoint security, intentional misuse, code vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF
This slide represents risk assessment software dashboard for cybersecurity. It includes risk percentage, number of risks, risk analysis progress, risk response progress, risk rating etc. Showcasing this set of slides titled Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF. The topics addressed in these templates are Risk Rating Breakdown, Action Plan Breakdown, Top 5 Entities Prone To Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF. Use them to share invaluable insights on Risk Encountered, Affected Asset, Phishing Emails and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF bundle. Topics like Steps Required Demonstrating, Cybersecurity Risk Mitigation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comprehensive Business Digitization Deck Steps Required To Demonstrating Cybersecurity Risk Mitigation Microsoft PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative comprehensive business digitization deck steps required to demonstrating cybersecurity risk mitigation microsoft pdf bundle. Topics like enforcing policy, providing appropriate funding, mandating awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver and pitch your topic in the best possible manner with this Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF Use them to share invaluable insights on Practices Themselves, Awareness Training, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
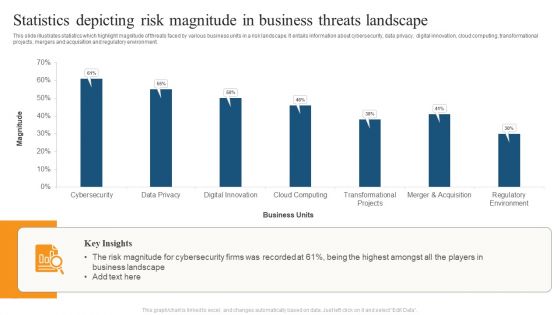
Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF
This slide illustrates statistics which highlight magnitude of threats faced by various business units in a risk landscape. It entails information about cybersecurity, data privacy, digital innovation, cloud computing, transformational projects, mergers and acquisition and regulatory environment. Pitch your topic with ease and precision using this Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF. This layout presents information on Business Units, Risk Magnitude, Business Landscape. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Data Safety Initiatives Responsibility Matrix To Ensure Effective Risk Management Summary PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver and pitch your topic in the best possible manner with this data safety initiatives responsibility matrix to ensure effective risk management summary pdf. Use them to share invaluable insights on cybersecurity strategy and program phase, technical team, leadership and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Analysing The Impact On Assets Due To Information Breach Cybersecurity Risk Assessment Summary PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Explore a selection of the finest Analysing The Impact On Assets Due To Information Breach Cybersecurity Risk Assessment Summary PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analysing The Impact On Assets Due To Information Breach Cybersecurity Risk Assessment Summary PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
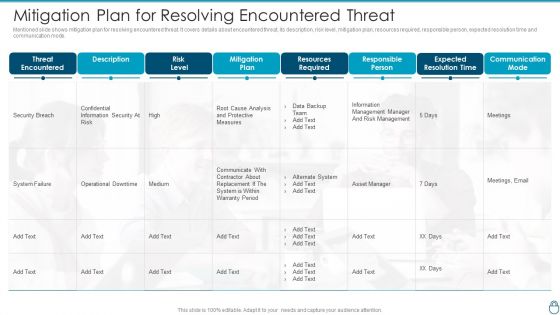
Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF Use them to share invaluable insights on Resources Required, Responsible Person, Expected Resolution Time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
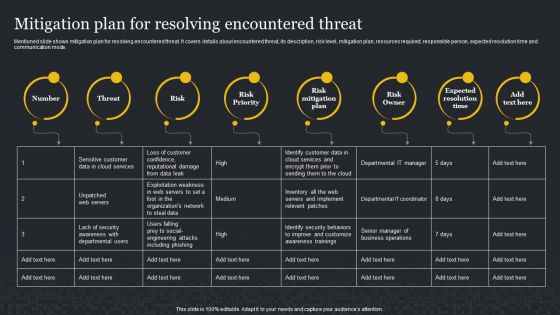
Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
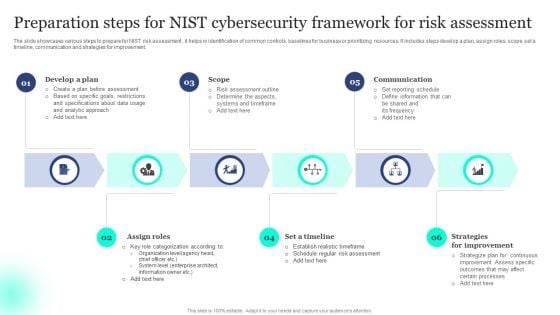
Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF
The slide showcases various steps to prepare for NIST risk assessment , it helps in identification of common controls, baselines for business or prioritizing resources. It includes steps develop a plan, assign roles, scope, set a timeline, communication and strategies for improvement. Presenting Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Scope, Communication, Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icons Slide For Cybersecurity Risk Assessment And Administration Plan Brochure PDF
Download our innovative and attention grabbing Icons Slide For Cybersecurity Risk Assessment And Administration Plan Brochure PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Designs PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail review and risk analysis designs pdf. Use them to share invaluable insights on ensure that systems, monitoring capabilities, involved allowing analysts and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































