Cyber Security Strategy
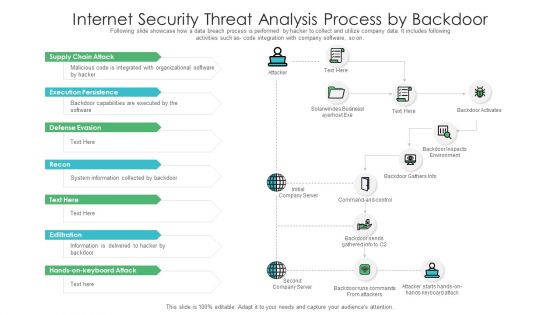
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812
Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with bank with computer mouse Evoke surprise in your audience with our Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812. See them realise how clever your plan is.
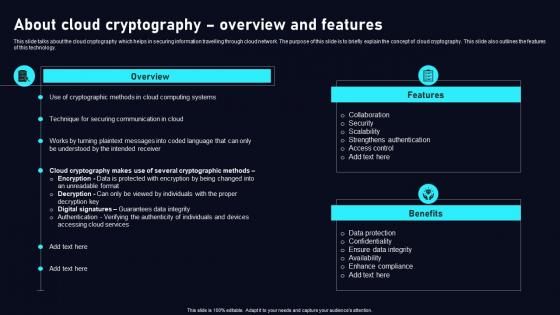
About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Present like a pro with About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.
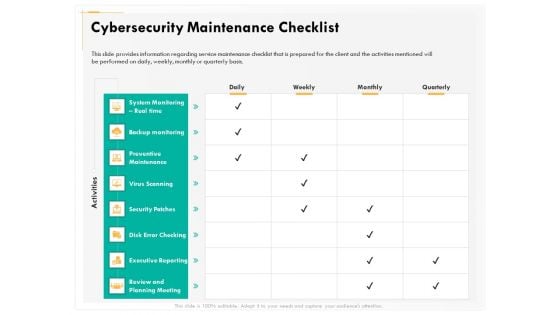
Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
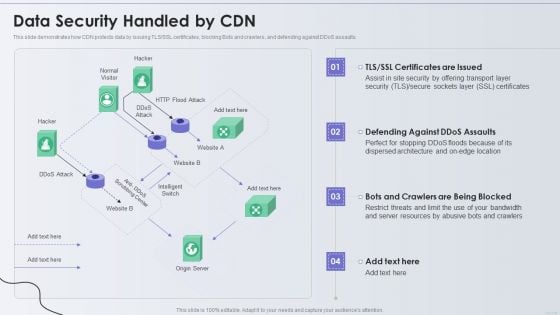
Distribution Network Data Security Handled By CDN Topics PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
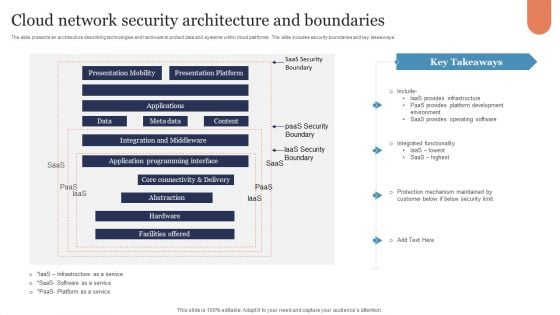
Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
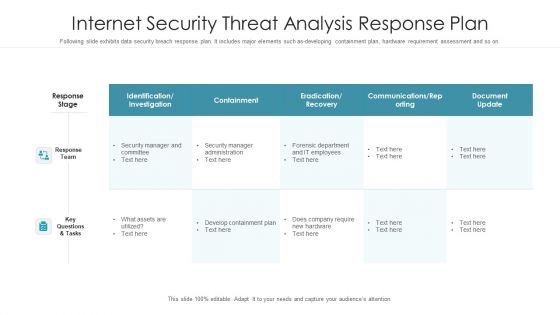
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
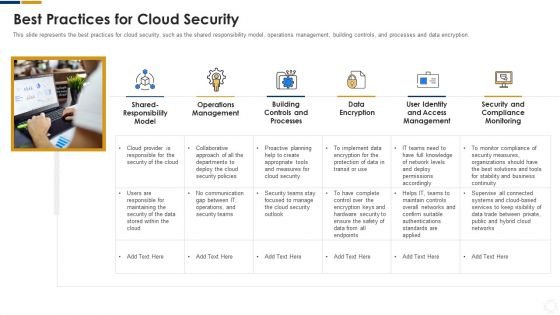
Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
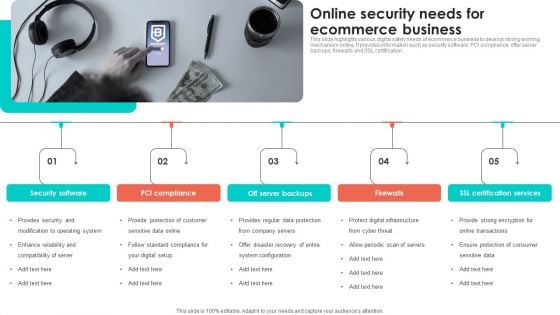
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
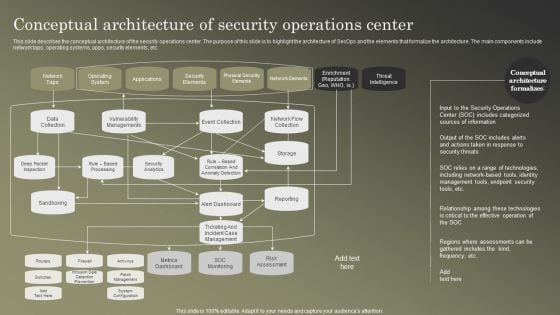
Cybersecurity Operations Cybersecops Conceptual Architecture Of Security Operations Summary PDF
This slide describes the conceptual architecture of the security operations center. The purpose of this slide is to highlight the architecture of SecOps and the elements that formalize the architecture. The main components include network taps, operating systems, apps, security elements, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cybersecurity Operations Cybersecops Conceptual Architecture Of Security Operations Summary PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

IT Security Awareness Training Program Plan Ppt Show Tips PDF
This slide covers cybersecurity awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public wi-fi, phishing attacks, mobile device security and passwords and authentication. Showcasing this set of slides titled IT Security Awareness Training Program Plan Ppt Show Tips PDF. The topics addressed in these templates are Training Topic, Mode Of Training, Training Hours. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
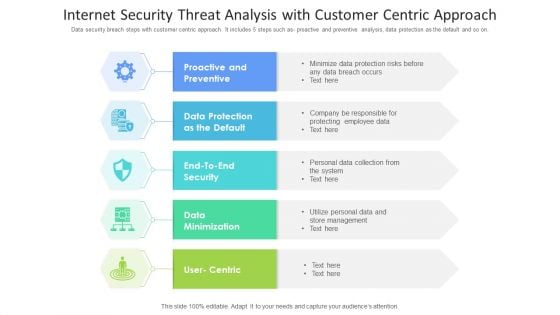
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
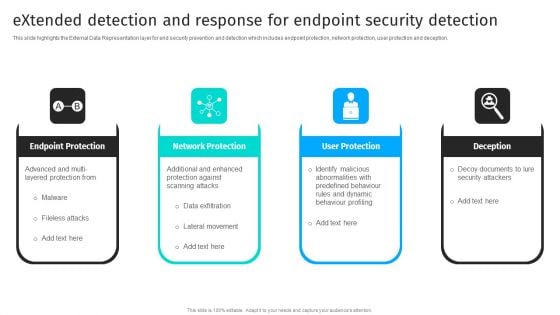
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
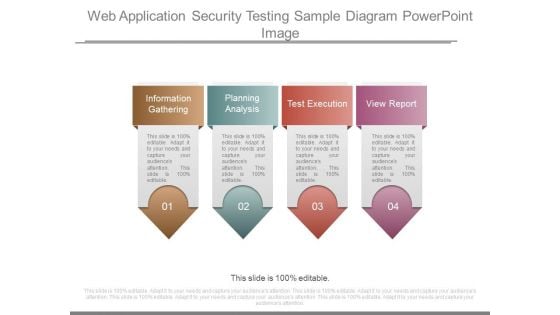
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.
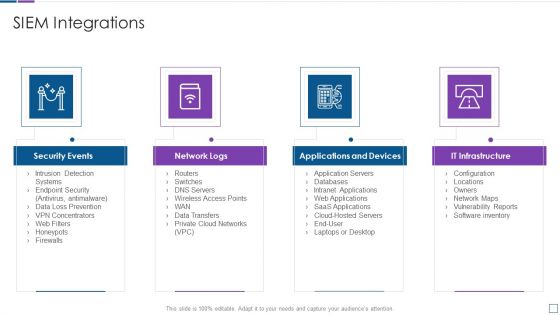
Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
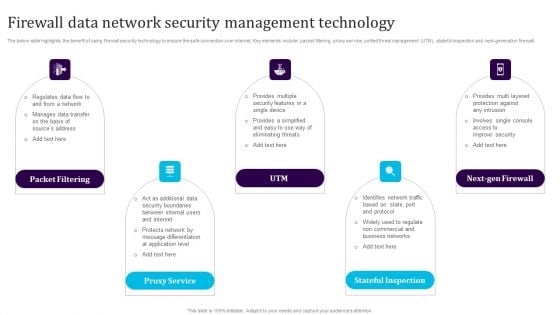
Firewall Data Network Security Management Technology Template PDF
The below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Persuade your audience using this Firewall Data Network Security Management Technology Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Packet Filtering, Proxy Service, Utm, Next Gen Firewall, Stateful Inspection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
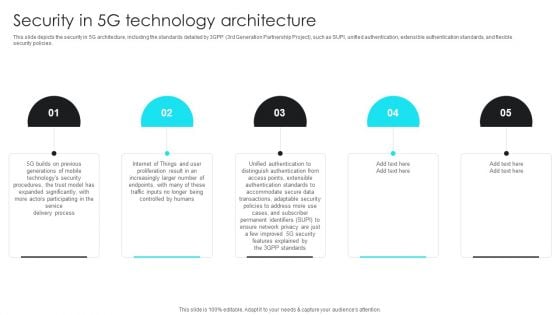
5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.
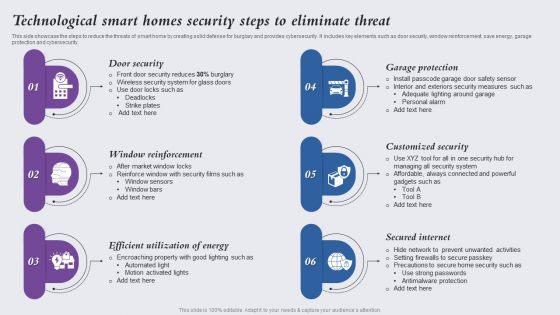
Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
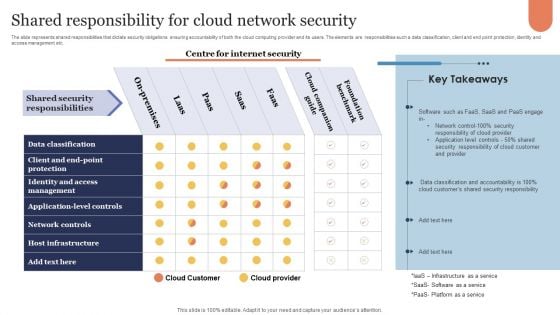
Shared Responsibility For Cloud Network Security Microsoft PDF
The slide represents shared responsibilities that dictate security obligations ensuring accountability of both the cloud computing provider and its users. The elements are responsibilities such a data classification, client and end point protection, identity and access management etc. Showcasing this set of slides titled Shared Responsibility For Cloud Network Security Microsoft PDF. The topics addressed in these templates are Cloud Companion Guide, Foundation Benchmark, On Premises. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Online Payment Techniques Best Practices To Maintain Digital Wallet Security
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Online Payment Techniques Best Practices To Maintain Digital Wallet Security template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Online Payment Techniques Best Practices To Maintain Digital Wallet Security that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.
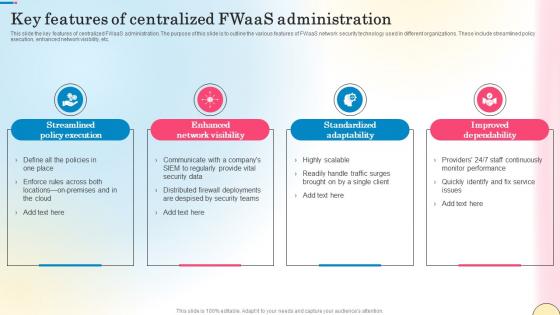
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc.
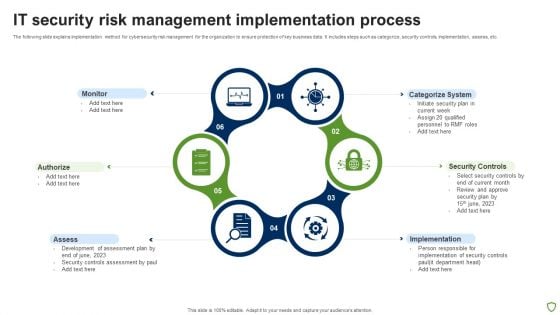
IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Incident Handling Cybersecurity Management Action Plan Graphics PDF
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
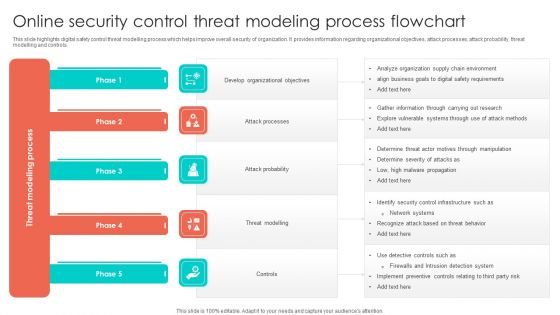
Online Security Control Threat Modeling Process Flowchart Structure PDF
This slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Presenting Online Security Control Threat Modeling Process Flowchart Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Develop Organizational Objectives, Attack Probability, Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
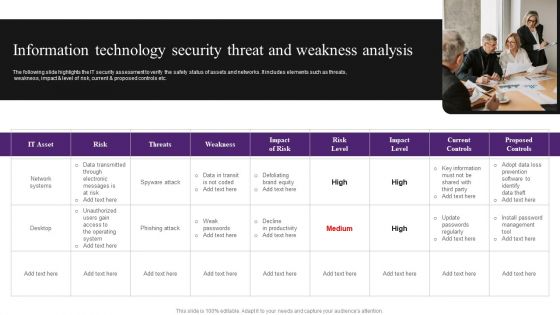
Information Technology Security Threat And Weakness Analysis Diagrams PDF
The following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Persuade your audience using this Information Technology Security Threat And Weakness Analysis Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Risk, Network Systems, Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
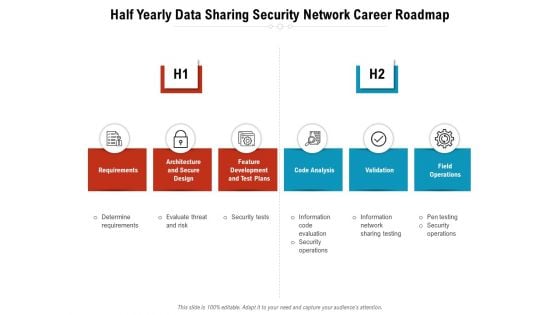
Half Yearly Data Sharing Security Network Career Roadmap Rules
We present our half yearly data sharing security network career roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly data sharing security network career roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Information Security Program Values To Business Ppt File Smartart PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting information security program values to business ppt file smartart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reduce, security, network, environment, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
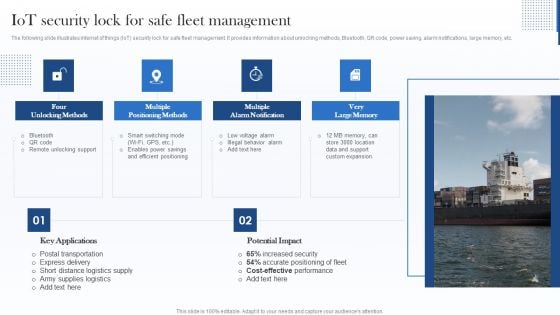
Iot Security Lock For Safe Fleet Management Sample PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
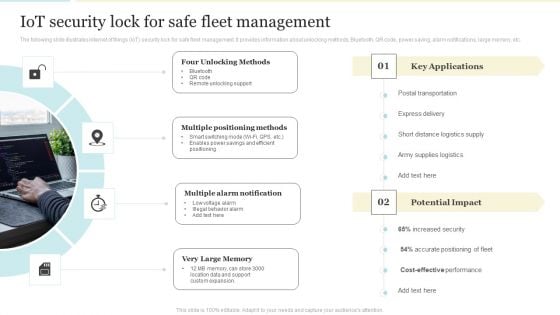
Iot Security Lock For Safe Fleet Management Mockup PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
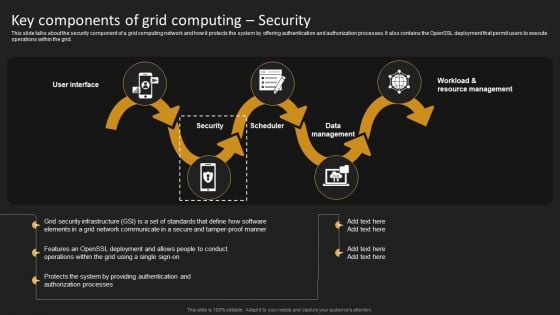
Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Allocating Budget For Information Security Risk Management Programme Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Allocating Budget For Information Security Risk Management Programme Brochure PDF from Slidegeeks and deliver a wonderful presentation.

Desktop Security Management Implementation Of Strong Password Policy Brochure PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a desktop security management implementation of strong password policy brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
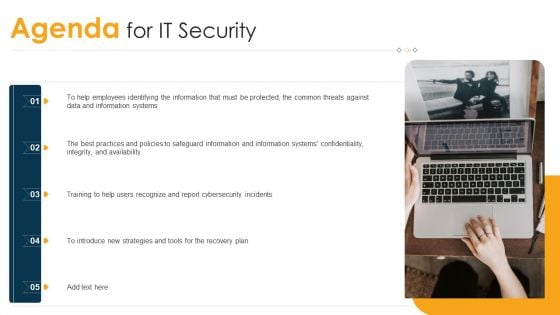
Agenda For IT Security Ppt Example File PDF
This is a agenda for it security ppt example file pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategies, cybersecurity, plan, safeguard, policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
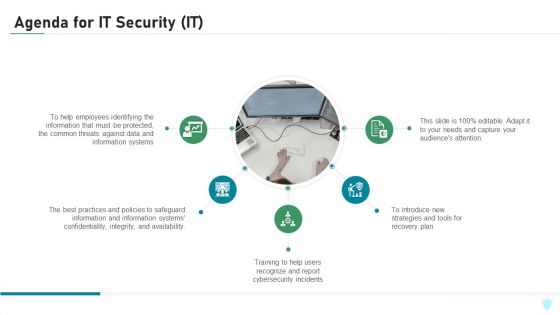
Agenda For IT Security IT Ppt Infographics Demonstration PDF
This is a agenda for it security it ppt infographics demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like training, cybersecurity, strategies, plan, integrity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
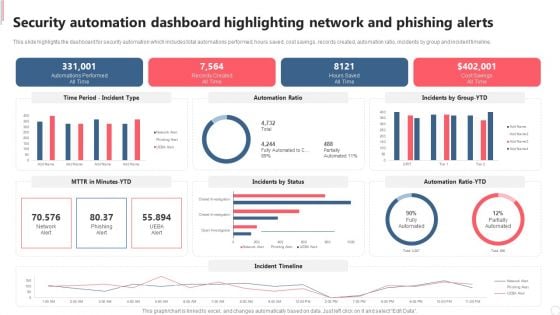
Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Welcome to our selection of the Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
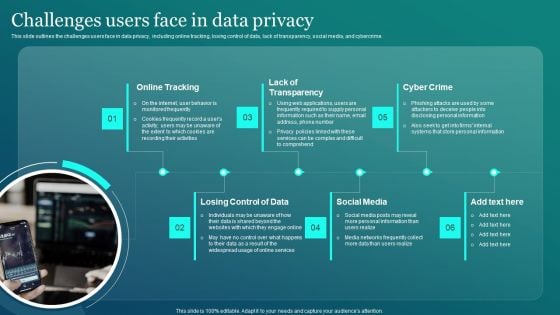
Information Security Challenges Users Face In Data Privacy Sample PDF
This slide outlines the challenges users face in data privacy, including online tracking, losing control of data, lack of transparency, social media, and cybercrime. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Challenges Users Face In Data Privacy Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Challenges Users Face In Data Privacy Sample PDF.
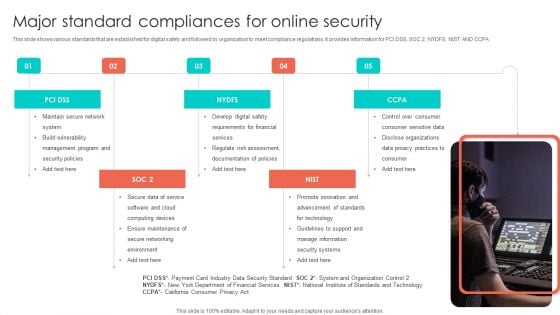
Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
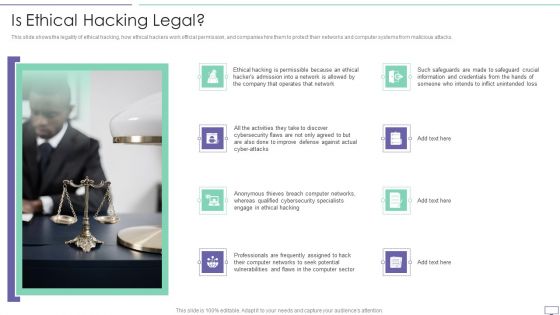
IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
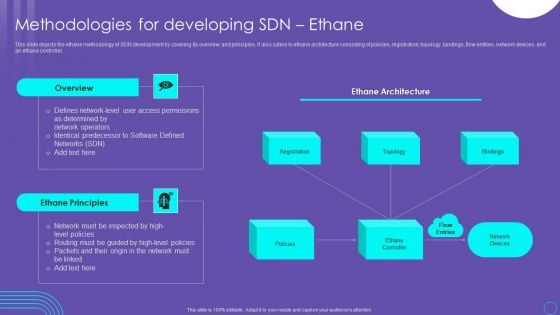
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Framework Of IT Security Awareness Training Program Information PDF
This slide covers framework of cybersecurity awareness training program. It involves five steps such as analyse, plan, deploy, measure and optimize. Presenting Framework Of IT Security Awareness Training Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Analyze, Plan, Deploy, Measure, Optimize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

SDN Security Architecture Infrastructure Layer And Apis Professional PDF
This slide represents the infrastructure layer and Application programming interfaces of SDN architecture. The layer contains the physical switches and other devices that help redirect the network traffic, and APIs are used to interact between the three layers of the SDN architecture. Slidegeeks has constructed SDN Security Architecture Infrastructure Layer And Apis Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
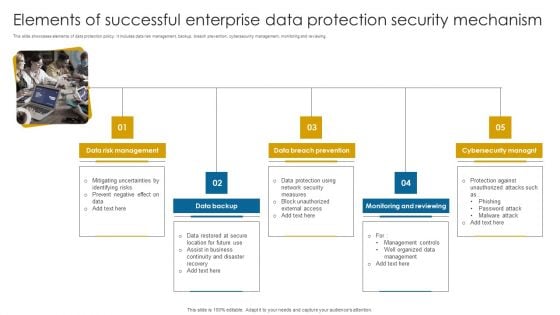
Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF
This slide showcases elements of data protection policy. It includes data risk management, backup, breach prevention, cybersecurity management, monitoring and reviewing.Persuade your audience using this Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Breach Prevention, Monitoring Reviewing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Building Trust With IoT Security Types Of Intrusion Detection System To Detect Security Threats IoT SS V
This slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Building Trust With IoT Security Types Of Intrusion Detection System To Detect Security Threats IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Building Trust With IoT Security Types Of Intrusion Detection System To Detect Security Threats IoT SS V today and make your presentation stand out from the rest This slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
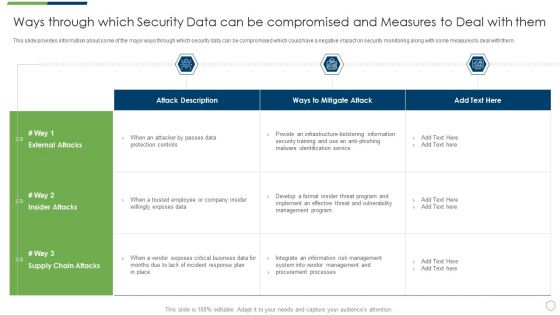
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
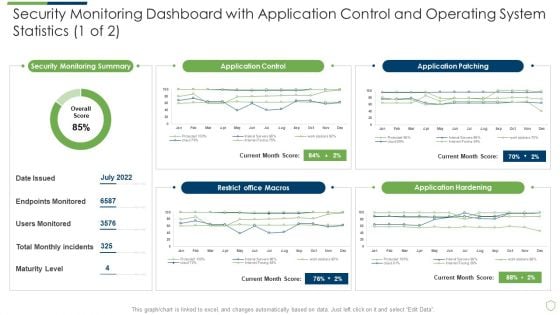
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
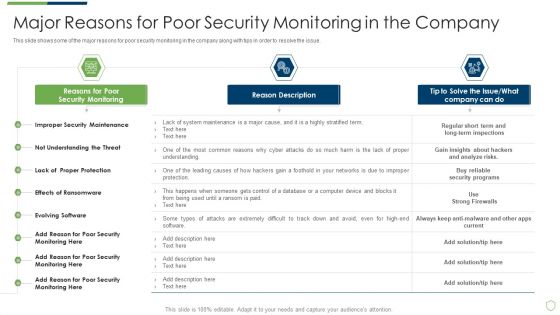
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
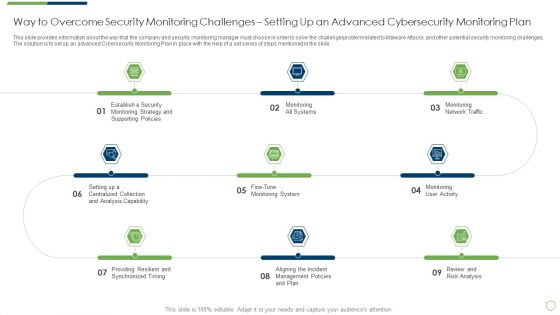
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Terrorism Assault How To Prevent Ddos Attacks In The Company Inspiration PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc.Presenting cyber terrorism assault how to prevent ddos attacks in the company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service providers bandwidth capacity, network monitoring, update security components In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
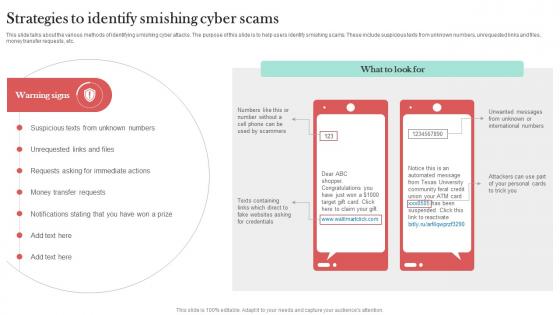
Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc.
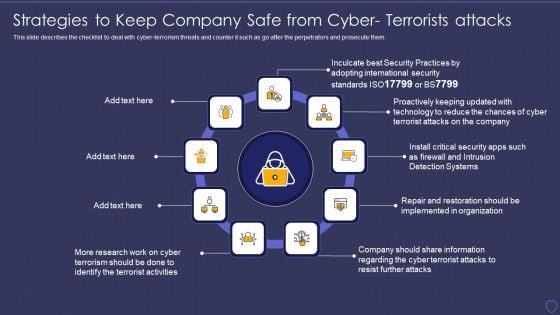
Global Cyber Terrorism Incidents On The Rise IT Strategies To Keep Company Safes Portrait PDF
This slide describes the checklist to deal with cyber-terrorism threats and counter it such as go after the perpetrators and prosecute them. This is a global cyber terrorism incidents on the rise it strategies to keep company safes portrait pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implemented, organization, technology, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































