Cyber Security Strategy
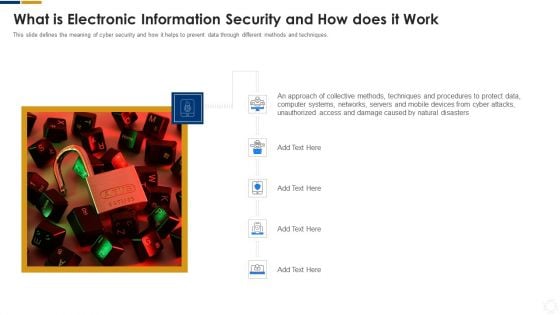
Cybersecurity What Is Electronic Information Security And How Does It Work Ppt Model Shapes PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting cybersecurity what is electronic information security and how does it work ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, devices, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
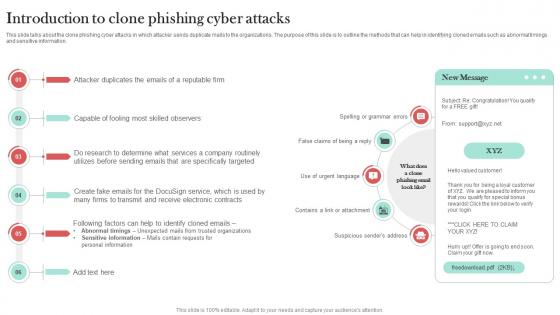
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.
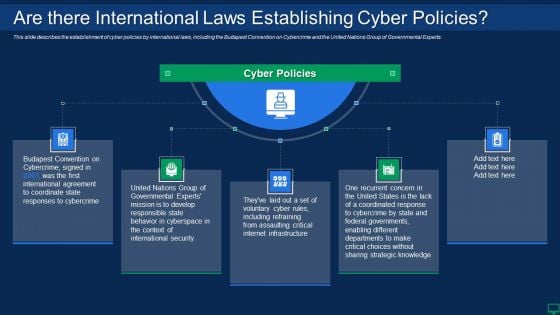
Russian Cyber Attacks On Ukraine IT Are There International Mockup PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts. This is a russian cyber attacks on ukraine it are there international mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, strategic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
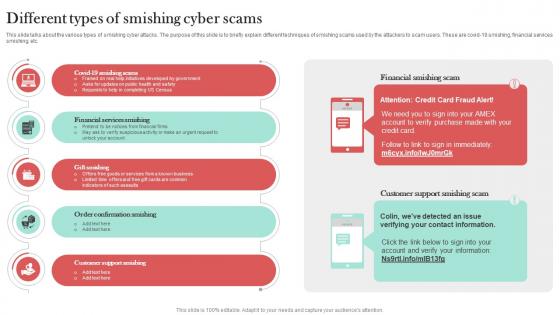
Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc.
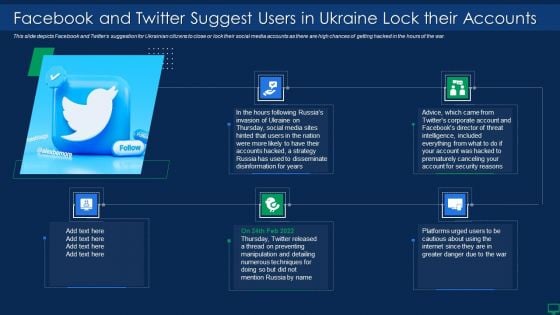
Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Slidegeeks has constructed Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.
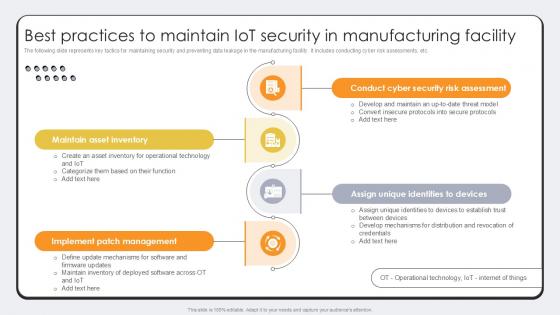
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
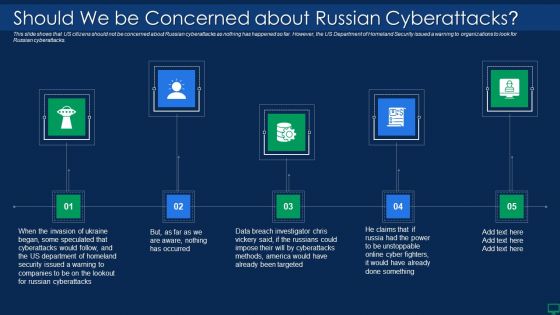
Russian Cyber Attacks On Ukraine IT Should We Be Concerned Slides PDF
Presenting russian cyber attacks on ukraine it should we be concerned slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like targeted, methods, security, cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
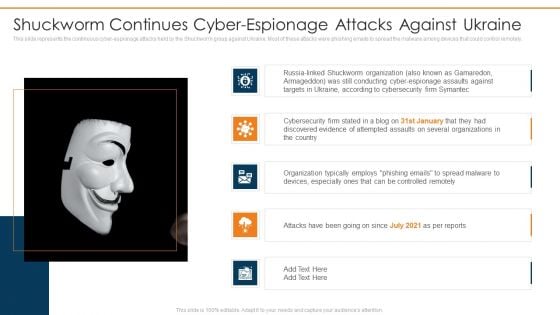
Data Wiper Spyware Attack Shuckworm Continues Cyber Espionage Attacks Against Ukraine Diagrams PDF
This slide represents the continuous cyber-espionage attacks held by the Shuckworm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely.Deliver an awe inspiring pitch with this creative data wiper spyware attack shuckworm continues cyber espionage attacks against ukraine diagrams pdf bundle. Topics like shuckworm continues cyber espionage attacks against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
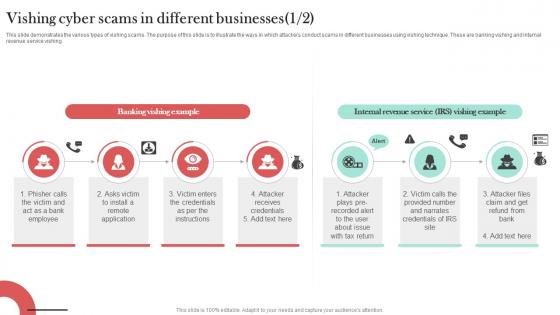
Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT
This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Are you searching for a Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT from Slidegeeks today. This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.
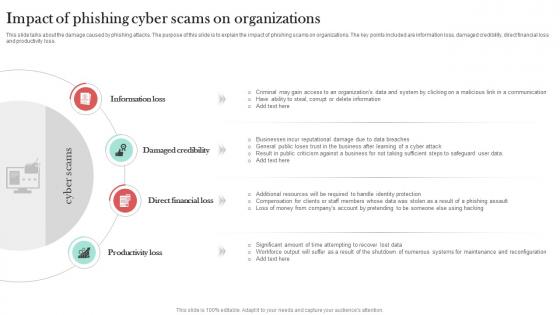
Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT. This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss.

Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF from Slidegeeks today.

Data Wiper Spyware Attack Does Ukraine And Russia Cyber Warfare Kill People Professional PDF
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts.Deliver an awe inspiring pitch with this creative data wiper spyware attack does ukraine and russia cyber warfare kill people professional pdf bundle. Topics like result of misinformation, protection become, susceptible targets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
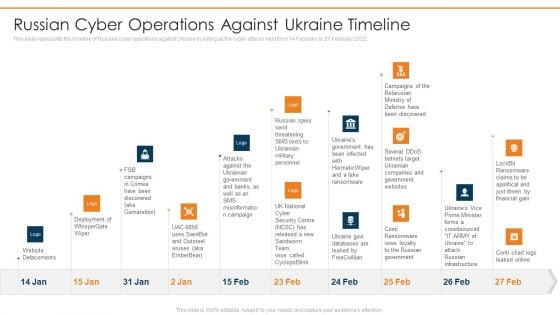
Data Wiper Spyware Attack Russian Cyber Operations Against Ukraine Timeline Clipart PDF
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack russian cyber operations against ukraine timeline clipart pdf Use them to share invaluable insights on website defacements, deployment of whisper gate, attacks against the ukrainian and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
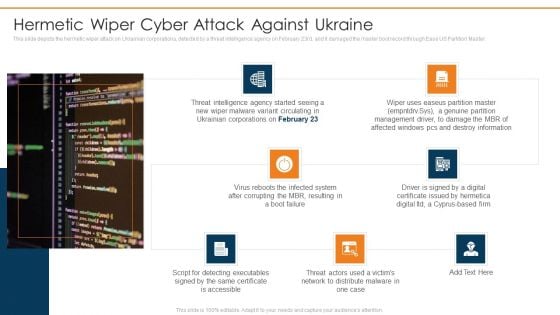
Data Wiper Spyware Attack Hermetic Wiper Cyber Attack Against Ukraine Slides PDF
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Ease US Partition Master.Deliver an awe inspiring pitch with this creative data wiper spyware attack hermetic wiper cyber attack against ukraine slides pdf bundle. Topics like hermetic wiper cyber attack against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.There are so many reasons you need a Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
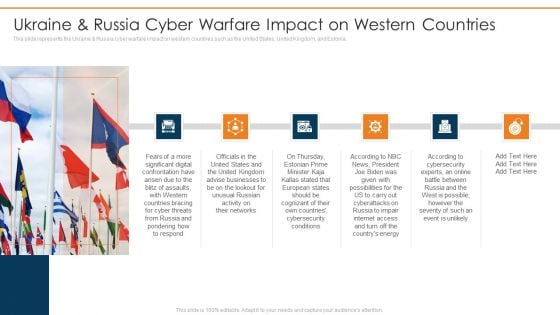
Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Impact On Western Countries Themes PDF
This slide represents the Ukraine and Russia cyber warfare impact on western countries such as the United States, United Kingdom, and Estonia.Deliver an awe inspiring pitch with this creative data wiper spyware attack ukraine and russia cyber warfare impact on western countries themes pdf bundle. Topics like united kingdom advise, businesses lookout for unusual, russian activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Russian Cyber Attacks On Ukraine Cell Summary PDF
This is a table of contents for russian cyber attacks on ukraine cell summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, cybersecurity, cyber cell, concerned. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
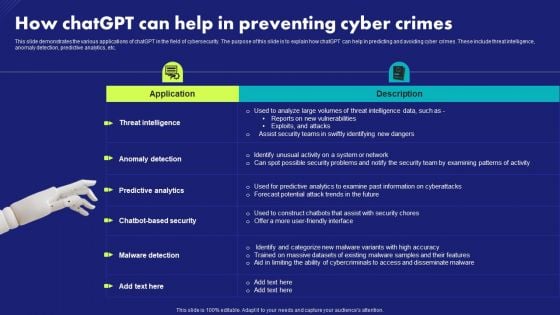
How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Agenda For Continuous Development Evaluation Plan To Eliminate Cyber Attacks Mockup PDF
This is a agenda for continuous development evaluation plan to eliminate cyber attacks mockup pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for continuous development evaluation plan to eliminate cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Safety Awareness Training Program Icon Ppt Inspiration Graphics Download PDF
Presenting Cyber Safety Awareness Training Program Icon Ppt Inspiration Graphics Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Safety, Awareness Training, Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
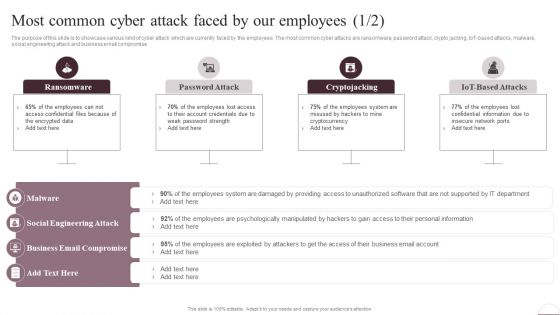
Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF from Slidegeeks today.

Regenerative Artificial Intelligence Systems How Chatgpt Can Help In Preventing Cyber Crimes Diagrams PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Regenerative Artificial Intelligence Systems How Chatgpt Can Help In Preventing Cyber Crimes Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Managing Electronic Information Security 60 Days Plan Ppt Ideas Graphics Tutorials PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative cybersecurity managing electronic information security 60 days plan ppt ideas graphics tutorials pdf bundle. Topics like measured, security, team, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
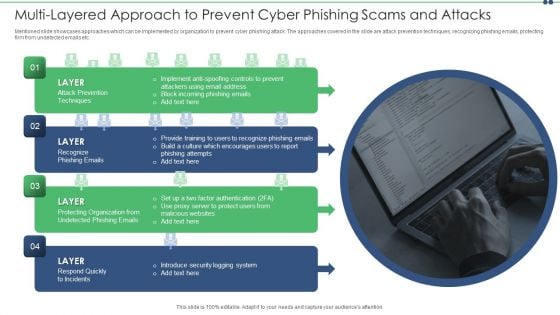
Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
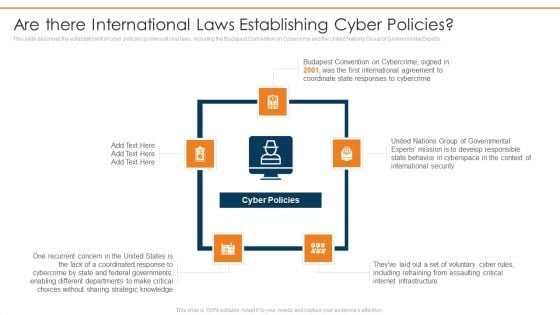
Data Wiper Spyware Attack Are There International Laws Establishing Cyber Policies Professional PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts.Presenting data wiper spyware attack are there international laws establishing cyber policies professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like international agreement, coordinate state, responses to cybercrime In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
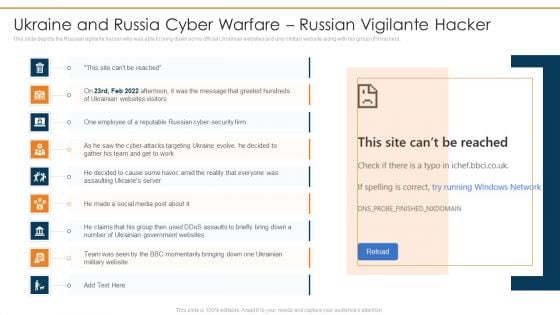
Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Sample PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack ukraine and russia cyber warfare russian vigilante hacker sample pdf Use them to share invaluable insights on ukraine and russia cyber warfare russian vigilante hacker and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
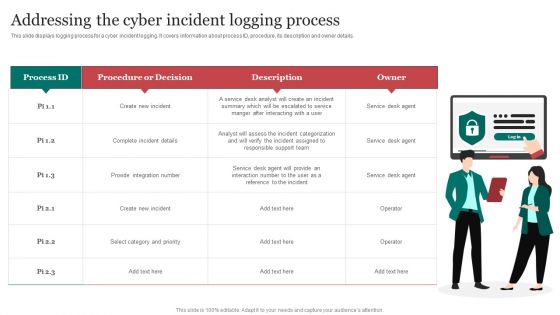
Addressing The Cyber Incident Logging Process Improving Cybersecurity Incident Summary PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Find a pre-designed and impeccable Addressing The Cyber Incident Logging Process Improving Cybersecurity Incident Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Icons Slide For Continuous Development Evaluation Plan To Eliminate Cyber Attacks Structure PDF
Introducing our well designed icons slide for continuous development evaluation plan to eliminate cyber attacks structure pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
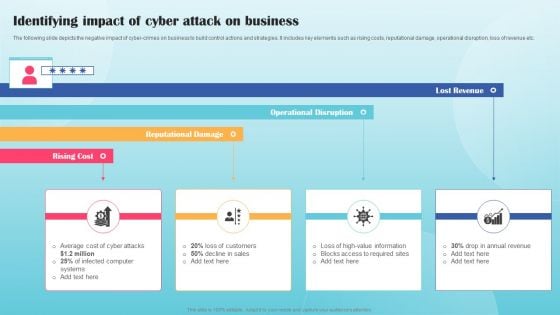
Identifying Impact Of Cyber Attack On Business Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Retrieve professionally designed Identifying Impact Of Cyber Attack On Business Ppt PowerPoint Presentation File Infographic Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents For Russian Cyber Attacks On Ukraine Elements PDF
Presenting table of contents for russian cyber attacks on ukraine elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cybersecurity, websites, technical, analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
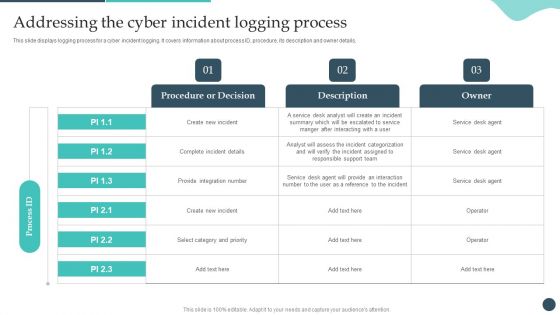
Safety Breach Response Playbook Addressing The Cyber Incident Logging Process Ideas PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details. Make sure to capture your audiences attention in your business displays with our gratis customizable Safety Breach Response Playbook Addressing The Cyber Incident Logging Process Ideas PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Key Metrics To Manage Cyber Risk With Application Control Ppt PowerPoint Presentation Pictures Slide PDF
This slide covers cyber risk measure dashboard. It also includes application control, patch application, patch operating system, restrict admin privileges, disable untrusted Microsoft office macros, user application hardening, multi factor authentication and daily backup of important data. Pitch your topic with ease and precision using this key metrics to manage cyber risk with application control ppt powerpoint presentation pictures slide pdf. This layout presents information on disable untrusted microsoft office macros, application control, patch operating systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
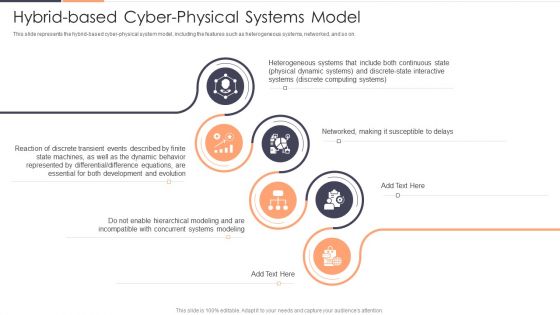
Hybrid Based Cyber Physical Systems Model Ppt Infographic Template Layout Ideas PDF
This slide represents the hybrid based cyber physical system model, including the features such as heterogeneous systems, networked, and so on. Presenting Hybrid Based Cyber Physical Systems Model Ppt Infographic Template Layout Ideas PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Dynamic Behavior, Development, Concurrent Systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
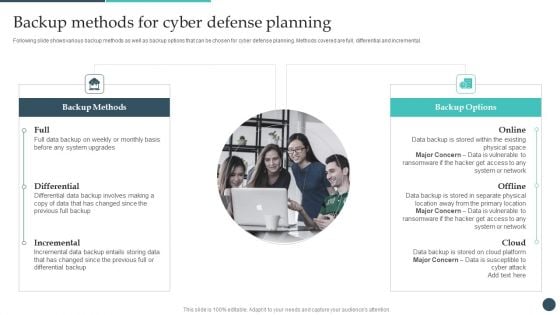
Safety Breach Response Playbook Backup Methods For Cyber Defense Planning Demonstration PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental. Welcome to our selection of the Safety Breach Response Playbook Backup Methods For Cyber Defense Planning Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF
The following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Find highly impressive Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For Russian Cyber Attacks On Ukraineteam Mockup PDF
This is a table of contents for russian cyber attacks on ukraineteam mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, technology, potential, accounts, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
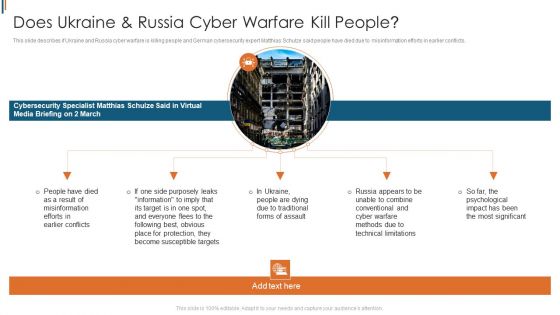
Ukraine Cyberwarfare Does Ukraine Russia Cyber Warfare Kill People Summary Pdf
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts. This is a ukraine cyberwarfare does ukraine russia cyber warfare kill people summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people have died as a result of misinformation efforts in earlier conflicts, in ukraine, people are dying due to traditional forms of assault, russia appears to be unable to combine conventional and cyber warfare methods due to technical limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
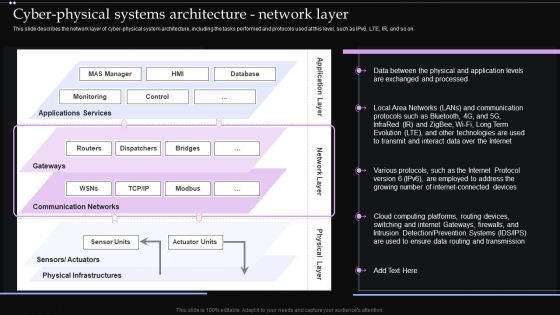
Cyber Physical Systems Architecture Network Layer Ppt PowerPoint Presentation Diagram Images PDF
This slide describes the network layer of cyber physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Physical Systems Architecture Network Layer Ppt PowerPoint Presentation Diagram Images PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
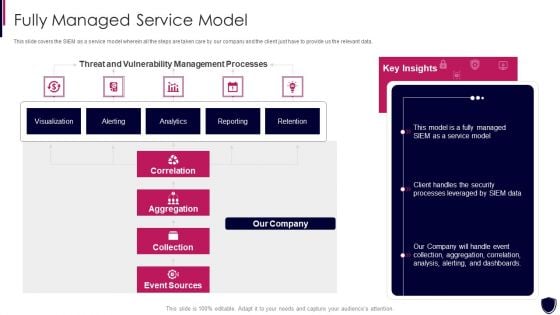
Enhancing Cyber Safety With Vulnerability Administration Fully Managed Service Model Clipart PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration fully managed service model clipart pdf bundle. Topics like correlation, aggregation, collection, event sources, our company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
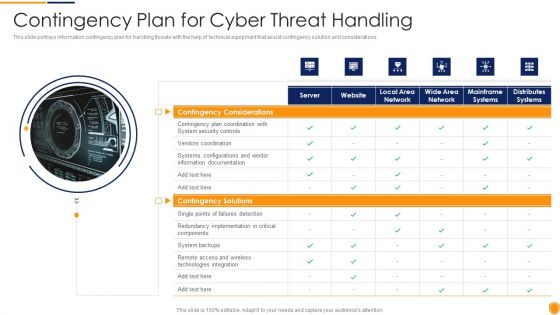
Mitigating Cybersecurity Threats And Vulnerabilities Contingency Plan For Cyber Infographics PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities contingency plan for cyber infographics pdf. Use them to share invaluable insights on contingency solutions, contingency considerations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Present like a pro with Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
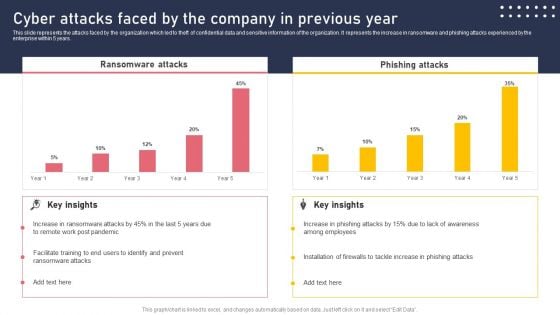
Cyber Attacks Faced By The Company In Previous Year Portrait PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Attacks Faced By The Company In Previous Year Portrait PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Physical Systems In Smart Transportation Systems Ppt PowerPoint Presentation File Model PDF
This slide depicts the application of CPS in transportation systems, including its benefits such as traffic control, boosting operational efficiency, and safety for road traffic systems. This Cyber Physical Systems In Smart Transportation Systems Ppt PowerPoint Presentation File Model PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Physical Systems In Smart Transportation Systems Ppt PowerPoint Presentation File Model PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
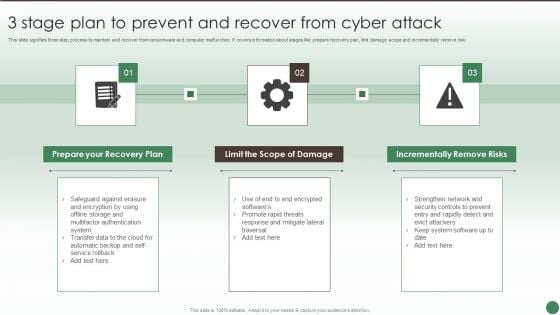
3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Continuous Development Evaluation Plan To Eliminate Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This continuous development evaluation plan to eliminate cyber attacks ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of forty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Enhancing Cyber Safety With Vulnerability Administration Various SIEM Cost Plans Pictures PDF
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration various siem cost plans pictures pdf bundle. Topics like annual costs of tools, annual cost of personnel, one time cost of implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Russian Cyber Attacks On Ukraine IT Impact Of Defacement Attacks Portrait PDF
This slide shows the impact of defacement attacks and fake news on the public, and Meta has banned Russian media on its platforms, and Russia has restricted access to Facebook. This is a russian cyber attacks on ukraine it impact of defacement attacks portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, fundamental, method, material, social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
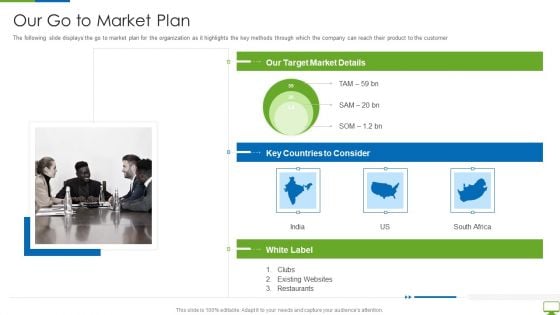
Cyber Network Simulation Platform Capital Funding Pitch Deck Our Go To Market Plan Slides PDF
The following slide displays the go to market plan for the organization as it highlights the key methods through which the company can reach their product to the customer Presenting cyber network simulation platform capital funding pitch deck our go to market plan slides pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like our go to market plan In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Physical Systems In Water Distribution Systems Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Welcome to our selection of the Cyber Physical Systems In Water Distribution Systems Ppt PowerPoint Presentation File Backgrounds PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Table Of Contents For Cyber Network Simulation Platform Capital Funding Pitch Deck Slides PDF
Deliver and pitch your topic in the best possible manner with this table of contents for cyber network simulation platform capital funding pitch deck slides pdf Use them to share invaluable insights on our go to market plan, our key team members, key growth drivers for vr industry and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Threat Management Action Plan Risk Professional PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this cyber safety incident management threat management action plan risk professional pdf. Use them to share invaluable insights on potential risk, risk level, action, responsible person, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
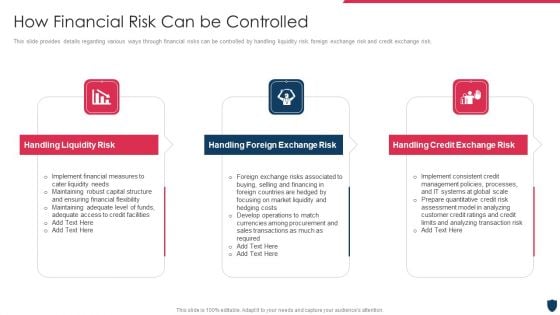
Cyber Safety Incident Management How Financial Risk Can Be Controlled Formats PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting cyber safety incident management how financial risk can be controlled formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
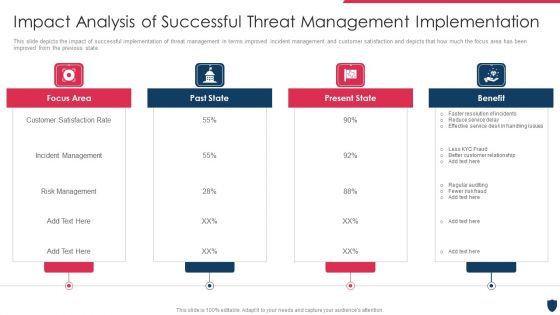
Cyber Safety Incident Management Impact Analysis Of Successful Threat Management Implementation Summary PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. This is a cyber safety incident management impact analysis of successful threat management implementation summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus area, past state, present state, benefit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
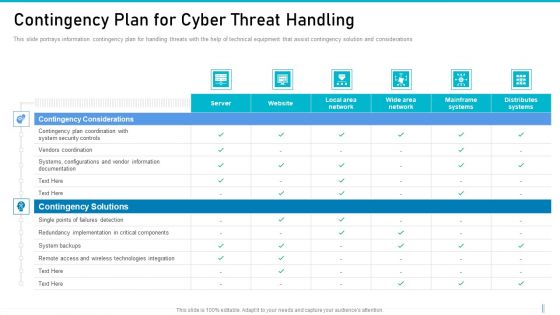
Risk Management For Organization Essential Assets Contingency Plan For Cyber Threat Handling Download PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets contingency plan for cyber threat handling download pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Network Simulation Platform Capital Funding Pitch Deck Understanding The Market Potential Icons PDF
Purpose of the following slide is to show the TAM SAM and SOM of the VR Industry market as it displays the total addressable market, the serviceable available market and the actual target market for the organization This is a cyber network simulation platform capital funding pitch deck understanding the market potential icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like total available market, serviceable available market, actual target market You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Incident Reporting By Different Departments Brochure PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting cyber safety incident management incident reporting by different departments brochure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
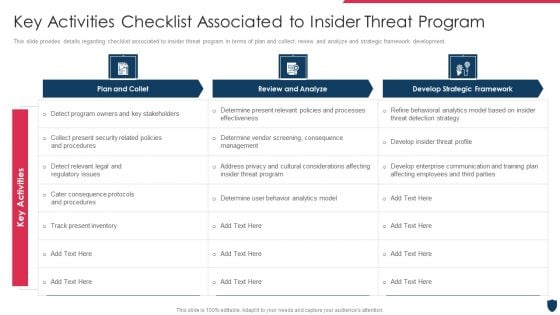
Cyber Safety Incident Management Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this cyber safety incident management key activities checklist associated to insider threat program download pdf. Use them to share invaluable insights on plan and collet, review and analyze, develop strategic framework, key activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































