Cyber Security Strategy
Email Advertising Verbal Communication Timeline Ppt Model
This is a email advertising verbal communication timeline ppt model. This is a four stage process. The stages in this process are time planning, business, marketing.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF
This slide illustrates the roles and responsibilities of the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Explore a selection of the finest Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
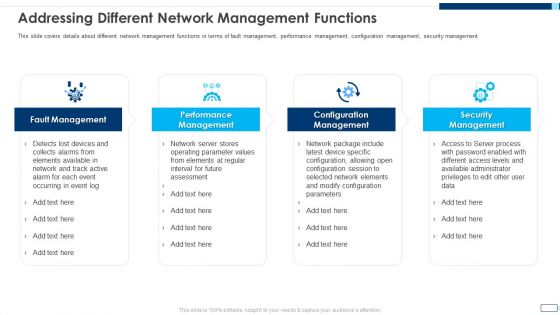
Evolving BI Infrastructure Addressing Different Network Management Functions Rules PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a evolving bi infrastructure addressing different network management functions rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
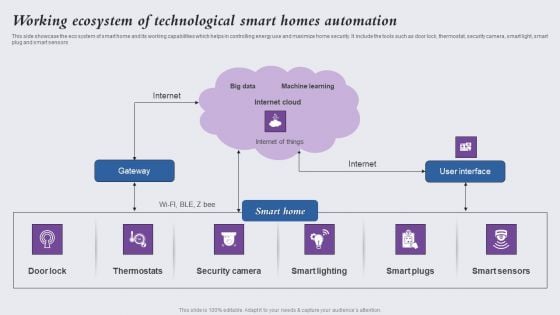
Working Ecosystem Of Technological Smart Homes Automation Elements PDF
This side showcase the eco system of smart home and its working capabilities which helps in controlling energy use and maximize home security. It include the tools such as door lock, thermostat, security camera, smart light, smart plug and smart sensors. Showcasing this set of slides titled Working Ecosystem Of Technological Smart Homes Automation Elements PDF. The topics addressed in these templates are Internet, Gateway, Thermostats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
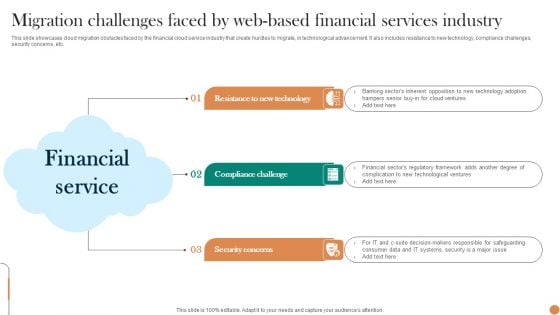
Migration Challenges Faced By Web Based Financial Services Industry Professional PDF
This slide showcases cloud migration obstacles faced by the financial cloud service industry that create hurdles to migrate, in technological advancement. It also includes resistance to new technology, compliance challenges, security concerns, etc. Presenting Migration Challenges Faced By Web Based Financial Services Industry Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Resistance To New Technology, Compliance Challenge, Security Concerns. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
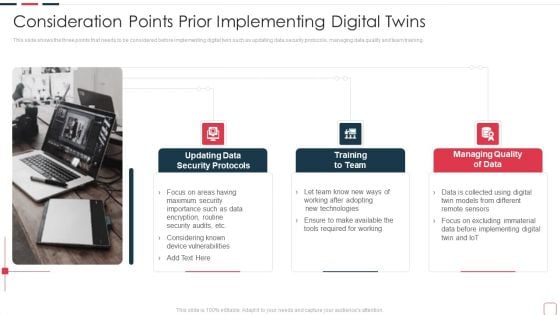
Price Benefit Internet Things Digital Twins Execution After Covid Consideration Points Prior Ideas PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. This is a price benefit internet things digital twins execution after covid consideration points prior ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security protocol, training team, managing quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Open Source WAF Features Ppt Portfolio Influencers PDF
This slide represents the characteristics of an open-source Web Application Firewall. The purpose of this slide is to give an overview of the primary features of open-source WAF, including continuous passive security assessment, real-time application security monitoring, full HTTP traffic logging, and web application hardening. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Open Source WAF Features Ppt Portfolio Influencers PDF from Slidegeeks and deliver a wonderful presentation.
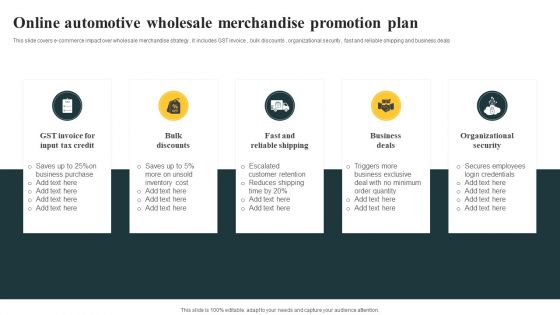
Online Automotive Wholesale Merchandise Promotion Plan Slides PDF
This slide covers e commerce impact over wholesale merchandise strategy . it includes GST invoice , bulk discounts , organizational security , fast and reliable shipping and business deals. Presenting Online Automotive Wholesale Merchandise Promotion Plan Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Merchandise Promotion Plan, Drive Target Audience. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Cost Management Model Components Clipart PDF
This slide shows cloud cost optimization components to make coordination between complex operations of cloud system. It include elements like orchestration, cloud network security and compliance setup etc. Presenting Cloud Cost Management Model Components Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Orchestration Automation, Cloud Network Security, Compliance Governance Setup. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
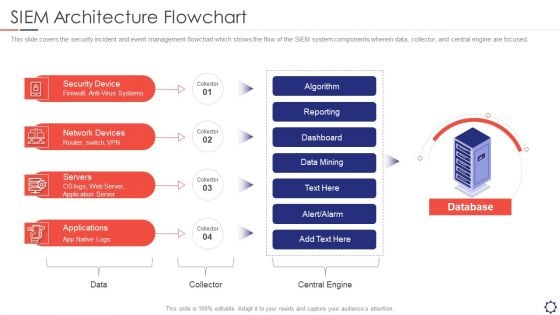
SIEM Architecture Flowchart Ppt Show Introduction PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart ppt show introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Different Training Formats For Different Organization Levels Brochure PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting different training formats for different organization levels brochure pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like automated security awareness platform, interactive protection simulation, cybersecurity for it online. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Revenue Streams Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection. This modern and well-arranged Revenue Streams Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection.
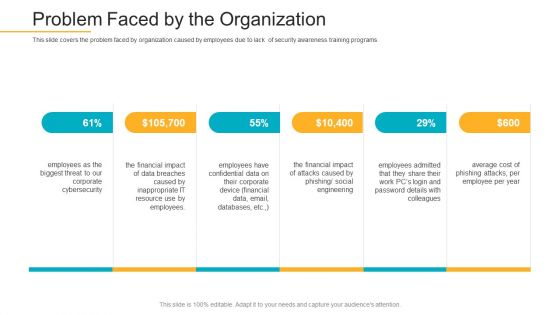
Data Breach Prevention Recognition Problem Faced By The Organization Elements PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a data breach prevention recognition problem faced by the organization elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, organization, problem, security awareness, training programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
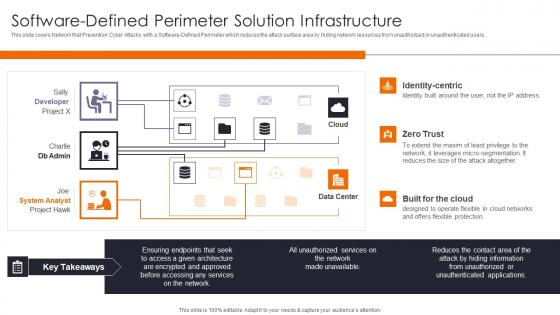
Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Present like a pro with Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.
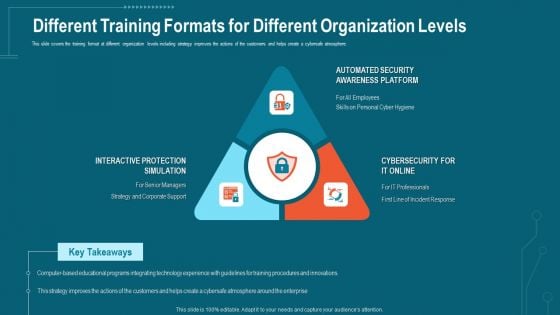
Companys Data Safety Recognition Different Training Formats For Different Organization Levels Structure PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a companys data safety recognition different training formats for different organization levels structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
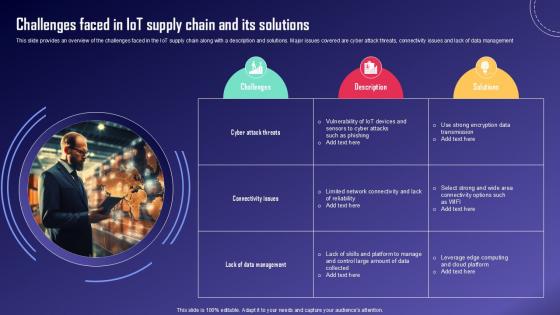
Challenges Faced In IoT Supply IoT Fleet Monitoring Ppt Slide IoT SS V
This slide provides an overview of the challenges faced in the IoT supply chain along with a description and solutions. Major issues covered are cyber attack threats, connectivity issues and lack of data management From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Challenges Faced In IoT Supply IoT Fleet Monitoring Ppt Slide IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides an overview of the challenges faced in the IoT supply chain along with a description and solutions. Major issues covered are cyber attack threats, connectivity issues and lack of data management

Implementation Challenges And Solutions Of Smart Grid Smart Grid Working
This slide represents the implementation challenges and solutions of smart grid technology, including cyber attacks on energy networks, terrorist attacks on power grids, and the requirement for new skills and knowledge. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementation Challenges And Solutions Of Smart Grid Smart Grid Working and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the implementation challenges and solutions of smart grid technology, including cyber attacks on energy networks, terrorist attacks on power grids, and the requirement for new skills and knowledge.
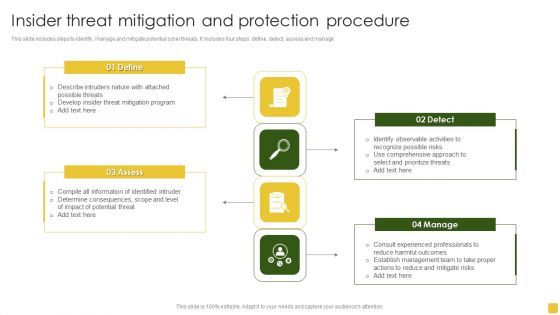
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
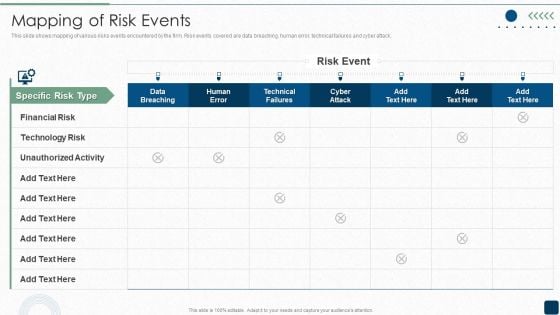
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Digital Terrorism Types And Categories With Examples Sample PDF
This slide shows various categories of cyber terrorism attacks according to their severity . It include categories such as simple unstructured, advance structured, complex coordinated etc. Showcasing this set of slides titled Digital Terrorism Types And Categories With Examples Sample PDF. The topics addressed in these templates are Advance Structured, Complex Coordinated, Simple Unstructured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
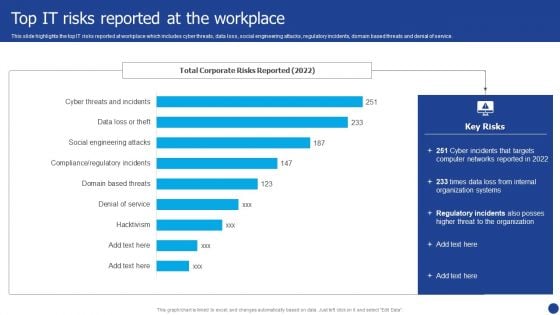
Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
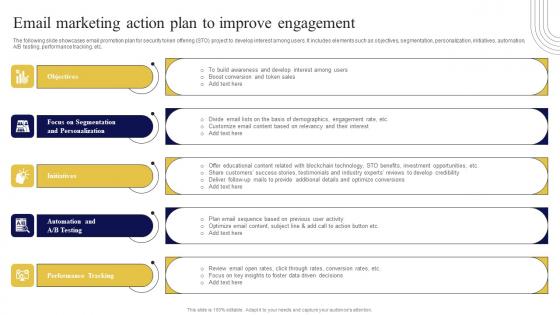
Email Marketing Action Plan To Improve Exploring Investment Opportunities Infographics Pdf
The following slide showcases email promotion plan for security token offering STO project to develop interest among users. It includes elements such as objectives, segmentation, personalization, initiatives, automation, A B testing, performance tracking, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Email Marketing Action Plan To Improve Exploring Investment Opportunities Infographics Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide showcases email promotion plan for security token offering STO project to develop interest among users. It includes elements such as objectives, segmentation, personalization, initiatives, automation, A B testing, performance tracking, etc.
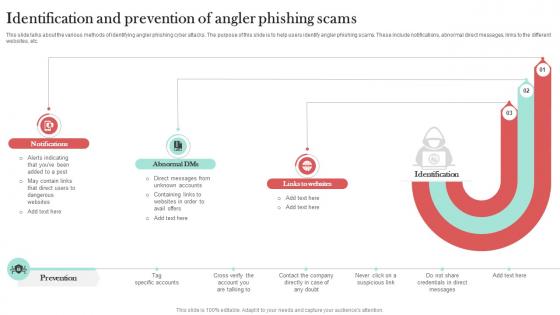
Identification And Prevention Of Angler Man In The Middle Phishing IT
This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Slidegeeks has constructed Identification And Prevention Of Angler Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
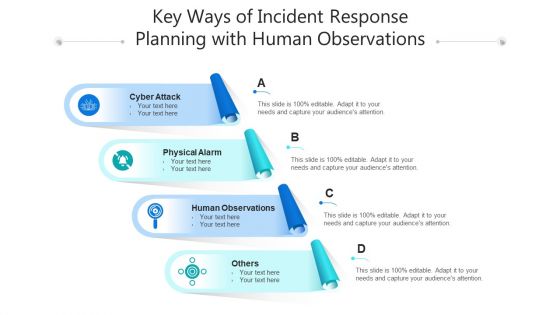
Key Ways Of Incident Response Planning With Human Observations Ppt PowerPoint Presentation File Sample PDF
Persuade your audience using this key ways of incident response planning with human observations ppt powerpoint presentation file sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including physical alarm, cyber attack, human observations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Model Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams. Boost your pitch with our creative Business Model Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams.
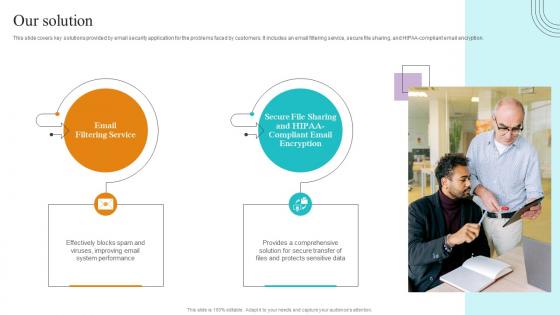
Our Solution Paubox Capital Funding Pitch Deck Summary Pdf
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA compliant email encryption. Welcome to our selection of the Our Solution Paubox Capital Funding Pitch Deck Summary Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA compliant email encryption.
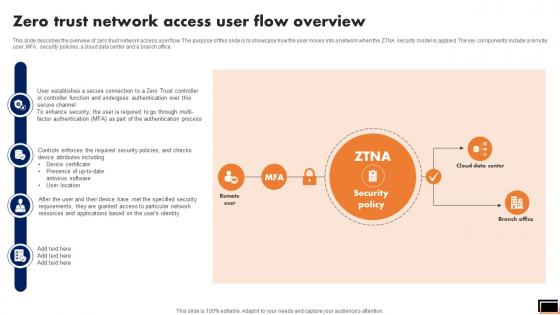
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf
This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file sharing options and spam and viruses overwhelming email systems. Explore a selection of the finest Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file sharing options and spam and viruses overwhelming email systems.
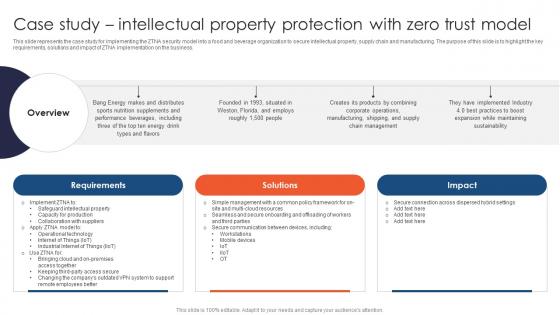
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
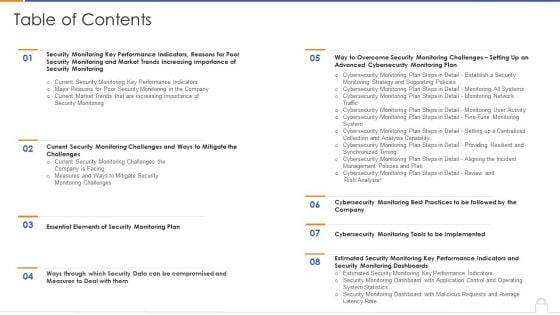
Approaches To Implement Advanced Cybersecurity Monitoring Plan Table Of Contents Information PDF
Deliver an awe inspiring pitch with this creative approaches to implement advanced cybersecurity monitoring plan table of contents information pdf bundle. Topics like essential elements, estimated security monitoring, advanced cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
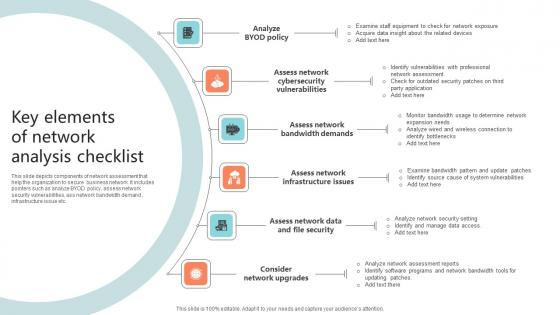
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.

Digital Marketing Roadmap Ppt PowerPoint Presentation Deck
This is a digital marketing roadmap ppt powerpoint presentation deck. This is a four stage process. The stages in this process are email marketing, social media, paid organic search, projected coat to date.
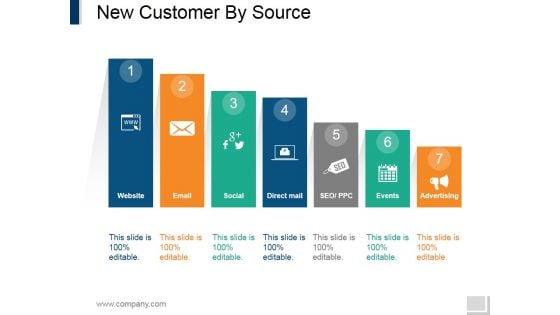
New Customer By Source Ppt PowerPoint Presentation Infographic Template Graphic Tips
This is a new customer by source ppt powerpoint presentation infographic template graphic tips. This is a seven stage process. The stages in this process are website, email, social, direct mail, seo ppc, events, advertising.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
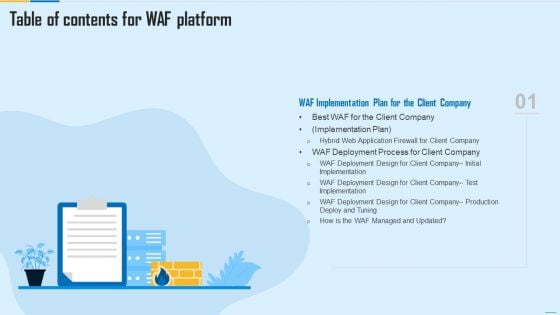
Table Of Contents For WAF Platform Plan Guidelines PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For WAF Platform Plan Guidelines PDF bundle. Topics like Web Application Firewall, Centralized Management System, Firewall Security Models can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
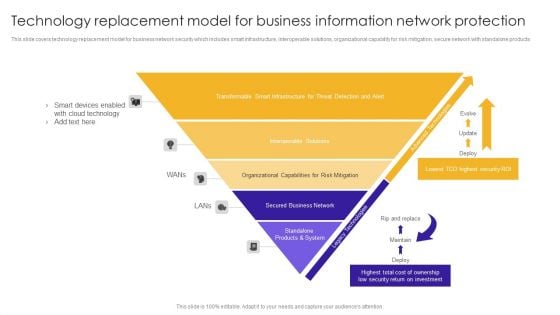
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
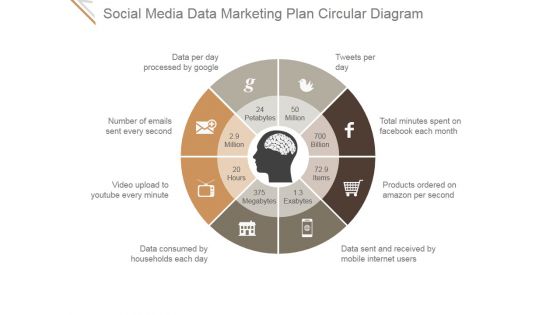
Social Media Data Marketing Plan Circular Diagram Ppt PowerPoint Presentation Pictures
This is a social media data marketing plan circular diagram ppt powerpoint presentation pictures. This is a eight stage process. The stages in this process are data per day processed by google, tweets per day, total minutes spent on facebook each month, products ordered on amazon per second, data sent and received by mobile internet users, number of emails sent every second, video upload to youtube every minute, data consumed by households each day.
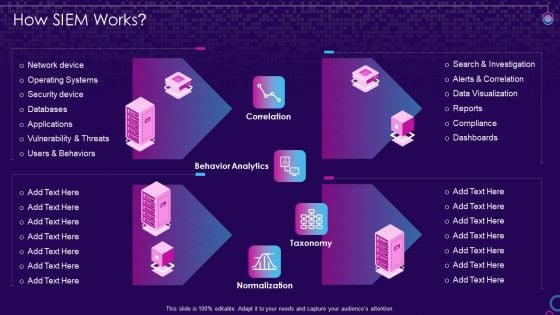
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
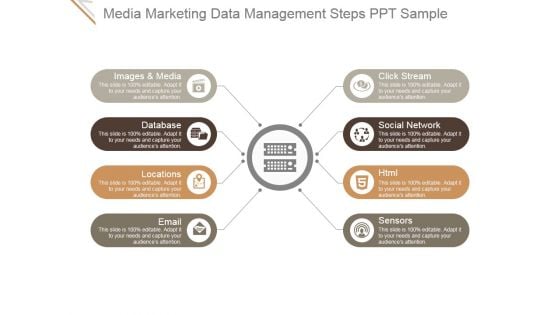
Media Marketing Data Management Steps Ppt PowerPoint Presentation Guide
This is a media marketing data management steps ppt powerpoint presentation guide. This is a eight stage process. The stages in this process are images and media, database, locations, email, click stream, social network, html, sensors.

Sales Process Workflow Funnel Diagram Ppt PowerPoint Presentation Microsoft
This is a sales process workflow funnel diagram ppt powerpoint presentation microsoft. This is a three stage process. The stages in this process are html, click stream, social, email, sensor data, database, location, images.
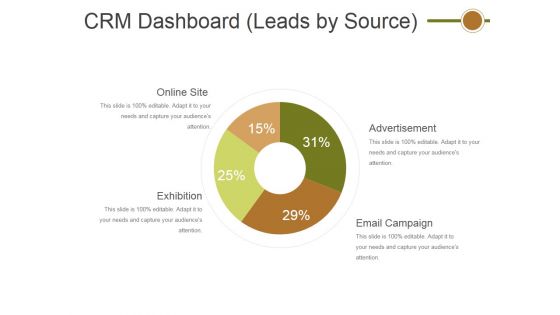
Crm Dashboard Leads By Source Ppt PowerPoint Presentation File Graphics Template
This is a crm dashboard leads by source ppt powerpoint presentation file graphics template. This is a four stage process. The stages in this process are online site, exhibition, advertisement, email campaign.

Cloud Intelligence Framework For Application Consumption Major Cybersecurity Challenges With Required Actions Mockup PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption major cybersecurity challenges with required actions mockup pdf. Use them to share invaluable insights on cybersecurity strategy, performing effective oversight, protecting cyber critical infrastructure, telecommunications, management challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Management Elements Shown Through Three Gears Ppt PowerPoint Presentation Icon Files PDF
Presenting it management elements shown through three gears ppt powerpoint presentation icon files pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
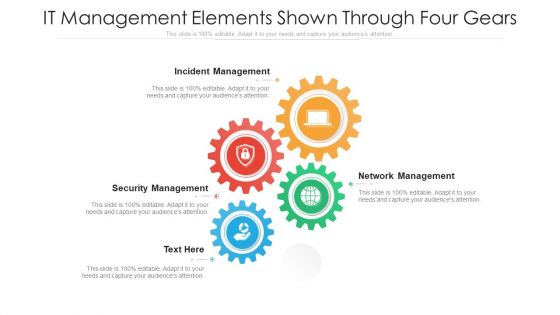
IT Management Elements Shown Through Four Gears Ppt PowerPoint Presentation Gallery Clipart Images PDF
Presenting it management elements shown through four gears ppt powerpoint presentation gallery clipart images pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
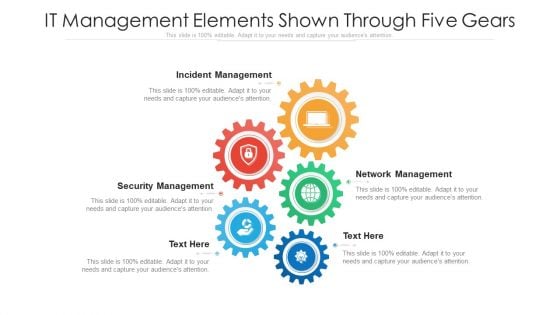
IT Management Elements Shown Through Five Gears Ppt PowerPoint Presentation File Portfolio PDF
Presenting it management elements shown through five gears ppt powerpoint presentation file portfolio pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
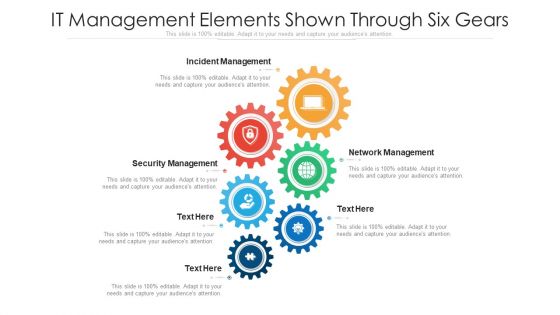
IT Management Elements Shown Through Six Gears Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting it management elements shown through six gears ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
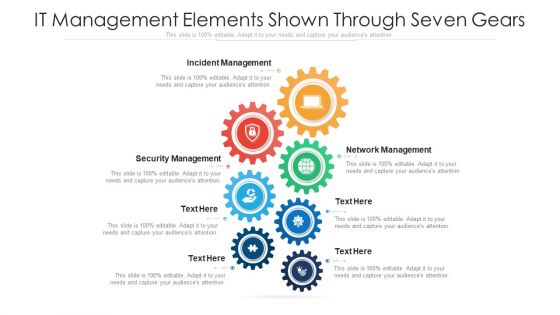
IT Management Elements Shown Through Seven Gears Ppt PowerPoint Presentation Gallery Example PDF
Presenting it management elements shown through seven gears ppt powerpoint presentation gallery example pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
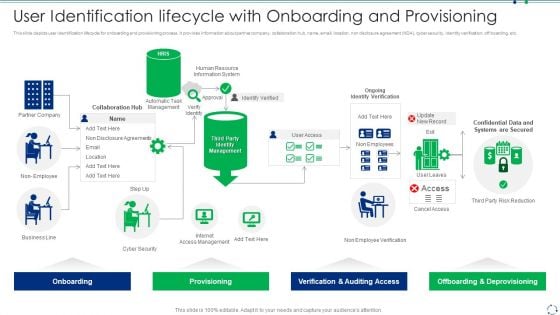
User Identification Lifecycle With Onboarding And Provisioning Introduction PDF
This slide depicts user identification lifecycle for onboarding and provisioning process. It provides information about partner company, collaboration hub, name, email, location, non disclosure agreement NDA cyber security, identity verification, off boarding, etc.Showcasing this set of slides titled user identification lifecycle with onboarding and provisioning introduction pdf The topics addressed in these templates are verification and auditing access, offboarding and deprovisioning, provisioning All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Telehealth Venture Capitalist Funding Elevator Why Invest On Our Organization Ideas PDF
The following slide displays the key overview of the organization as it provides an overview of the industry verticals such as healthcare, life science, incubators etc. The following also displays the key capabilities of the industries. Deliver an awe inspiring pitch with this creative telehealth venture capitalist funding elevator why invest on our organization ideas pdf bundle. Topics like software, big data, cyber security, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
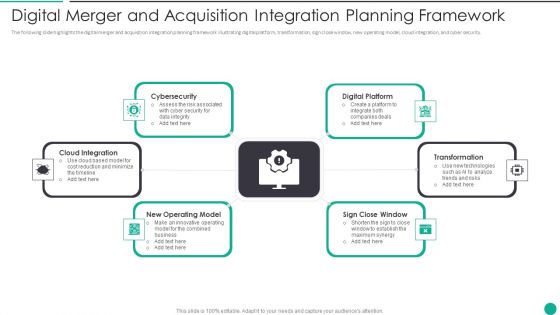
Digital Merger And Acquisition Integration Planning Framework Graphics PDF
The following slide highlights the digital merger and acquisition integration planning framework illustrating digital platform, transformation, sign close window, new operating model, cloud integration, and cyber security. Persuade your audience using this Digital Merger And Acquisition Integration Planning Framework Graphics PDF This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Integration, Digital Platform, Transformation Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Industry Transformation Approaches Banking Sector Employee Development Top Digital Industry Trends Of Banking Mockup PDF
This slide shows some of the top digital industry trends in banking that are most widely adopted such as seamless payments, next gen and digital banks, mobile applications, robotics process automation and ai artificial intelligence, cybersecurity etc. This is a industry transformation approaches banking sector employee development top digital industry trends of banking mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seamless payments, mobile applications, cyber security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

NIST Cybersecurity Framework Best Practices Topics PDF
The slide highlights the best practices to be followed in order to overcome various implementation challenges of Nist framework for cyber security. It covers understand, automate, prioritize and talent acquisition. Persuade your audience using this NIST Cybersecurity Framework Best Practices Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Automate, Talent Acquisition. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. There are so many reasons you need a Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
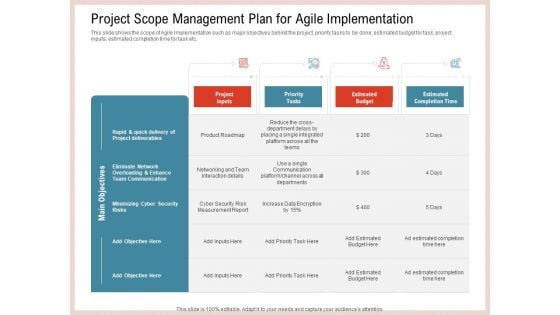
Agile Model Improve Task Team Performance Project Scope Management Plan For Agile Implementation Information PDF
This slide shows the scope of Agile Implementation such as major objectives behind the project, priority tasks to be done, estimated budget for task, project inputs, estimated completion time for task etc. Deliver an awe inspiring pitch with this creative agile model improve task team performance project scope management plan for agile implementation information pdf bundle. Topics like team communication, cyber security, budget, measurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
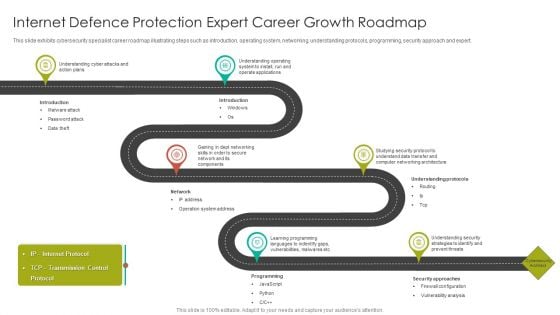
Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































