Cyber Security
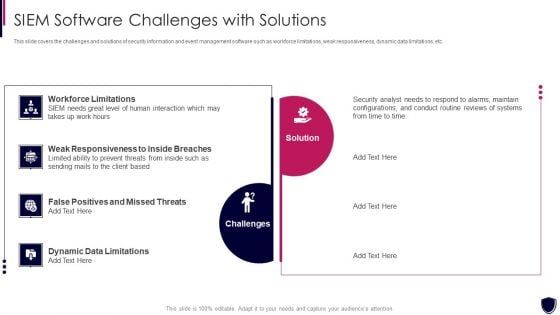
Enhancing Cyber Safety With Vulnerability Administration SIEM Software Challenges Slides PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a enhancing cyber safety with vulnerability administration siem software challenges slides pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like workforce limitations, challenges, solution, weak responsiveness to inside breaches, dynamic data limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
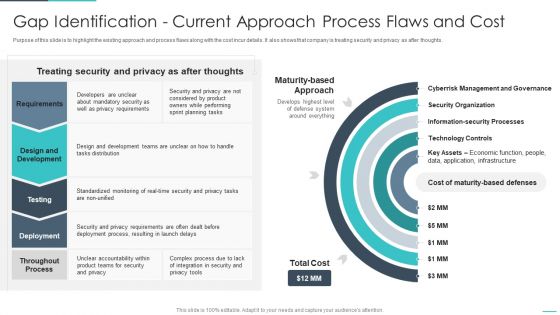
Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
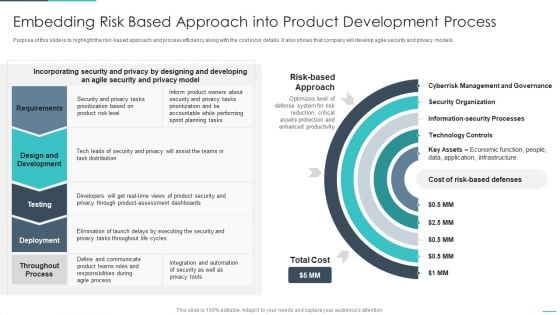
Handling Cyber Threats Digital Era Embedding Risk Based Approach Into Product Ppt Gallery Designs PDF
Purpose of this slide is to highlight the risk-based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative handling cyber threats digital era embedding risk based approach into product ppt gallery designs pdf bundle. Topics like embedding risk based approach into product development process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Handling Cyber Threats Digital Era Categorization Worksheet For Assets Ppt Icon Outline PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting handling cyber threats digital era categorization worksheet for assets ppt icon outline pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like server computer, system location, system accessibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF from Slidegeeks today.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
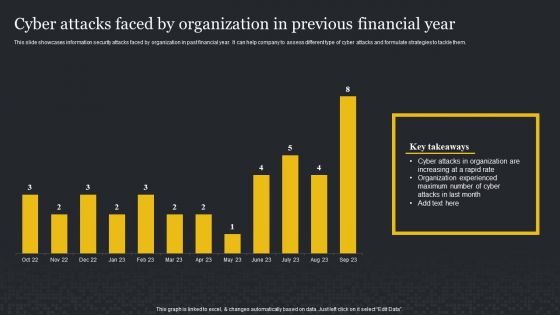
Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
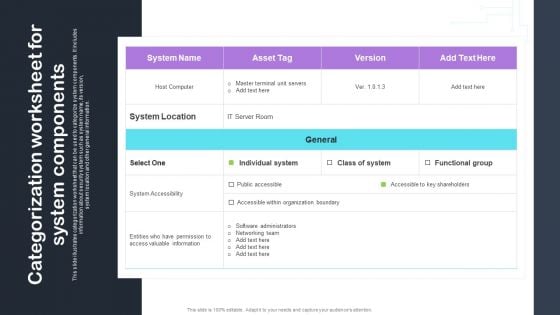
Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information. Get a simple yet stunning designed Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
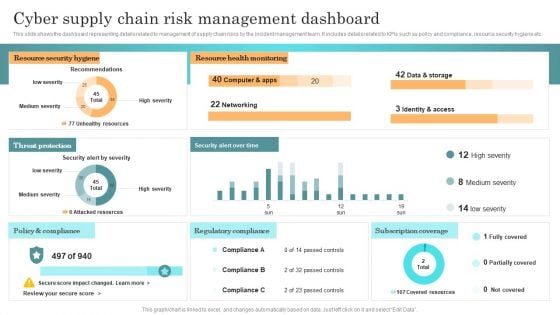
Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF can be your best option for delivering a presentation. Represent everything in detail using Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
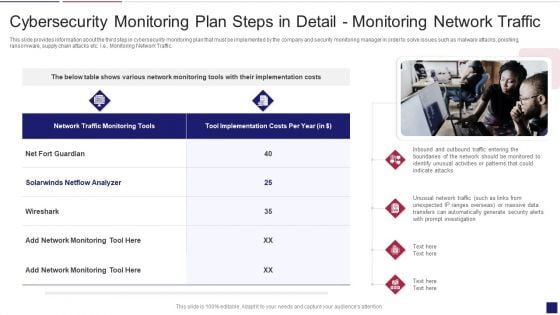
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
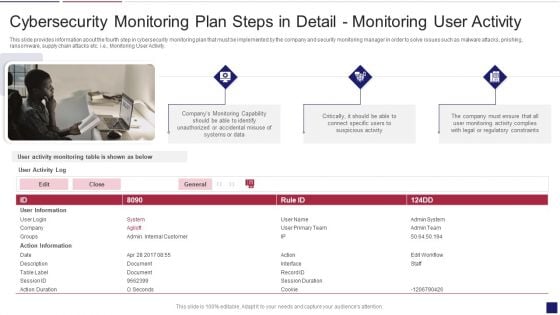
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Ukraine Cyberwarfare Cyber Officials Urge Agencies To Armor Up For Potential Russian Attacks Guidelines Pdf
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting ukraine cyberwarfare cyber officials urge agencies to armor up for potential russian attacks guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like amid russias escalating invasion of ukraine, us cybersecurity experts are warning government agencies, major corporations to be cautious against the potential of russian cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
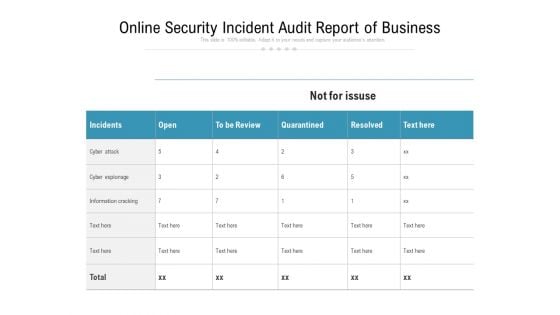
Online Security Incident Audit Report Of Business Ppt PowerPoint Presentation Inspiration Layout Ideas PDF
Pitch your topic with ease and precision using this online security incident audit report of business ppt powerpoint presentation inspiration layout ideas pdf. This layout presents information on incidents, cyber attack, cyber espionage, information cracking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
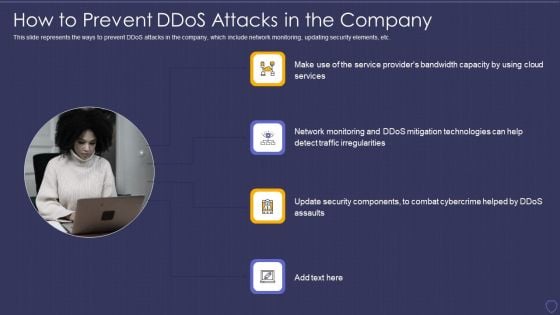
Global Cyber Terrorism Incidents On The Rise IT How To Prevent Ddos Attacks In The Company Designs PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Presenting global cyber terrorism incidents on the rise it how to prevent ddos attacks in the company designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mitigation technologies, service, traffic irregularities, network monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
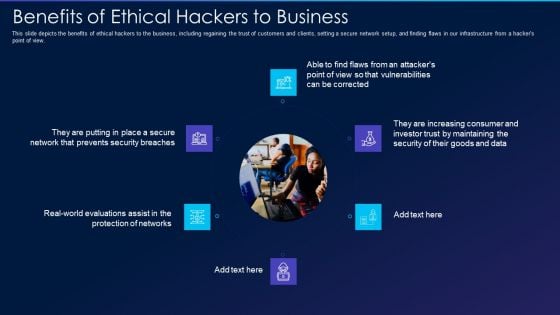
Cyber Exploitation IT Benefits Of Ethical Hackers To Business Brochure PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view. Presenting cyber exploitation it benefits of ethical hackers to business brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, evaluations, maintaining. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
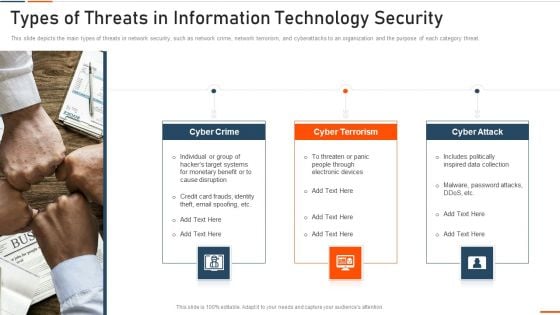
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Safety Audits To Stop Cyber Attacks Ppt PowerPoint Presentation File Example Topics PDF
Persuade your audience using this key safety audits to stop cyber attacks ppt powerpoint presentation file example topics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including inventory, secure configurations, continuous vulnerability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps like identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Persuade your audience using this Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Recover, Respond, Detect, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Statistical Analysis Of IT Security In Small Enterprise Ppt PowerPoint Presentation Ideas Design Inspiration PDF
Persuade your audience using this statistical analysis of it security in small enterprise ppt powerpoint presentation ideas design inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber attack and breaches, cyber attack and breach type, spear phishing, web attacks, spam, ransomware, identity theft. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
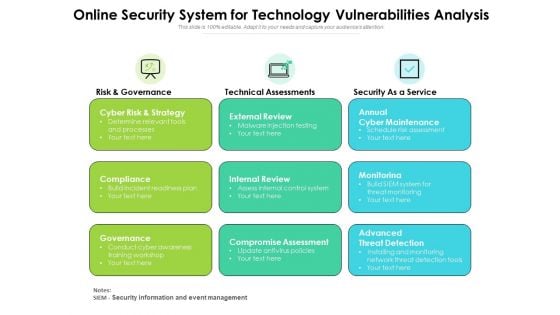
Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT
This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk.
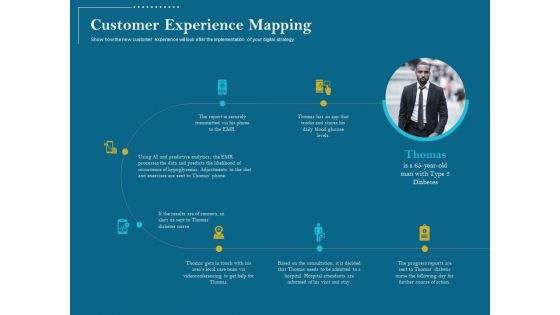
Utilizing Cyber Technology For Change Process Customer Experience Mapping Mockup PDF
Show how the new customer experience will look after the implementation of your digital strategy. This is a utilizing cyber technology for change process customer experience mapping mockup pdf. template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like thomas has an app that tracks and stores his daily blood glucose levels, if the results are of concern, an alert us sent to thomas diabetes nurse, the report is securely transmitted via his phone to the emr You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
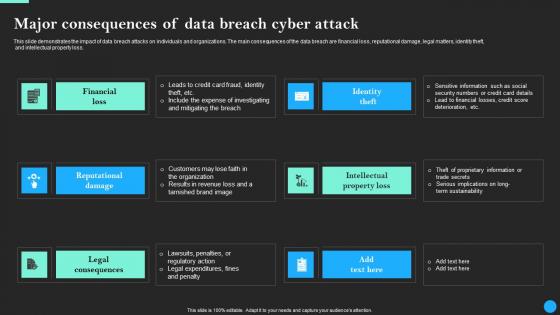
Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Presenting this PowerPoint presentation, titled Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.
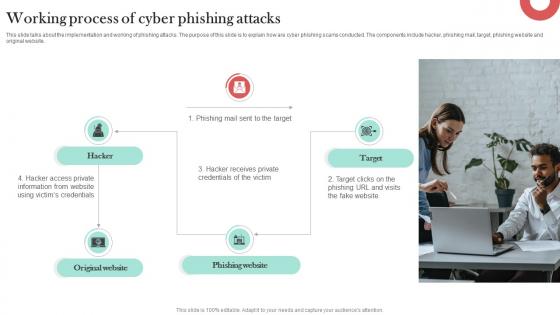
Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Table Of Contents Demonstration PDF
Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks table of contents demonstration pdf. Use them to share invaluable insights on security, market, elements, compromised, implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Key Safety Audits For Cyber Threat Prevention Ppt PowerPoint Presentation Icon Example PDF
Presenting key safety audits for cyber threat prevention ppt powerpoint presentation icon example pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security, awareness, training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For E Business And Cyber Risk Management Ppt Slides Layout PDF
Deliver an awe inspiring pitch with this creative table of contents for e business and cyber risk management ppt slides layout pdf bundle. Topics like global market, security, requirements, communication plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
E Business And Cyber Risk Management Table Of Contents Elements PDF
Deliver and pitch your topic in the best possible manner with this e business and cyber risk management table of contents elements pdf. Use them to share invaluable insights on global market, requirements, security, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT
This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. This modern and well-arranged Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc.
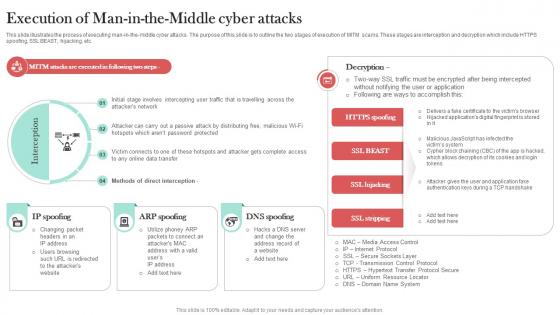
Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT
This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc. Welcome to our selection of the Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc.
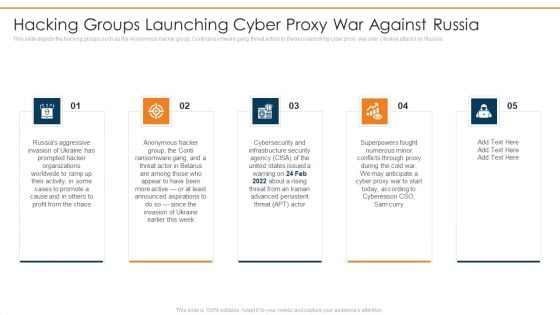
Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
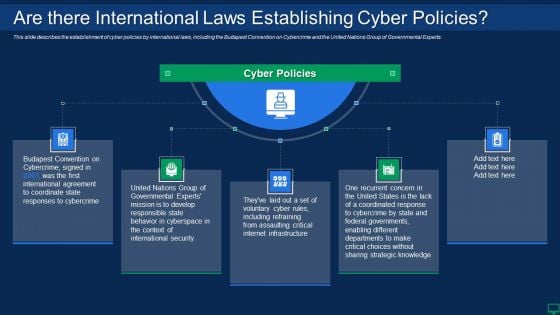
Russian Cyber Attacks On Ukraine IT Are There International Mockup PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts. This is a russian cyber attacks on ukraine it are there international mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, strategic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
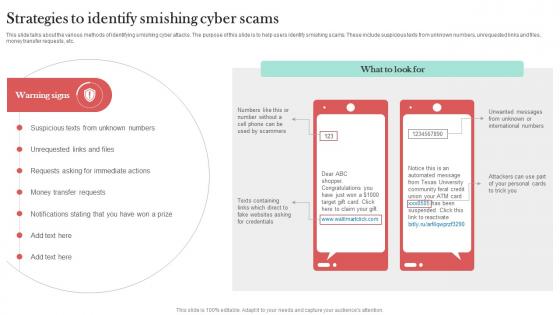
Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc.
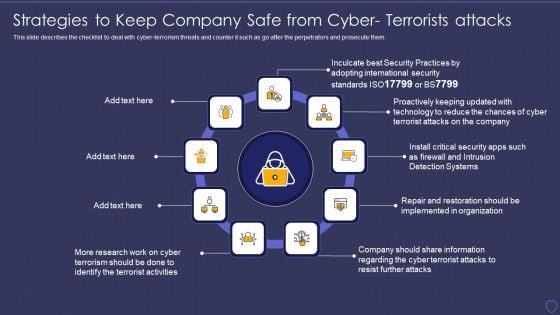
Global Cyber Terrorism Incidents On The Rise IT Strategies To Keep Company Safes Portrait PDF
This slide describes the checklist to deal with cyber-terrorism threats and counter it such as go after the perpetrators and prosecute them. This is a global cyber terrorism incidents on the rise it strategies to keep company safes portrait pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implemented, organization, technology, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
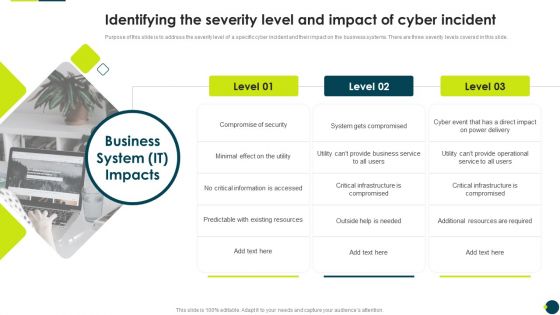
IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
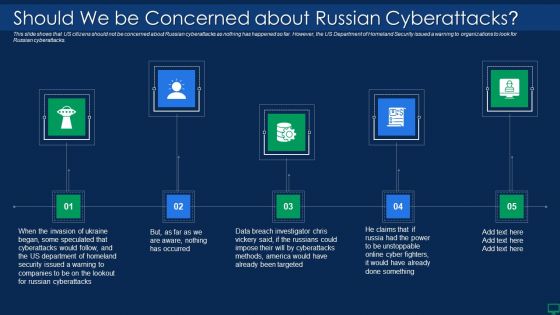
Russian Cyber Attacks On Ukraine IT Should We Be Concerned Slides PDF
Presenting russian cyber attacks on ukraine it should we be concerned slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like targeted, methods, security, cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
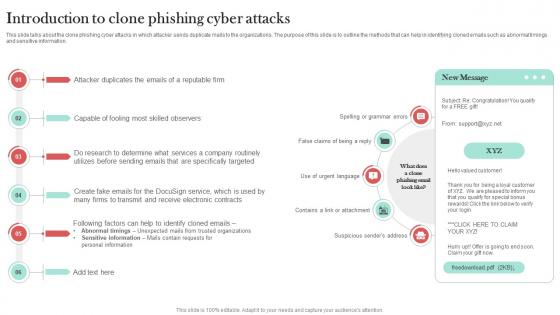
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.

Agenda Of E Business And Cyber Risk Management Ppt Outline Vector PDF
This is a agenda of e business and cyber risk management ppt outline vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, information, program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
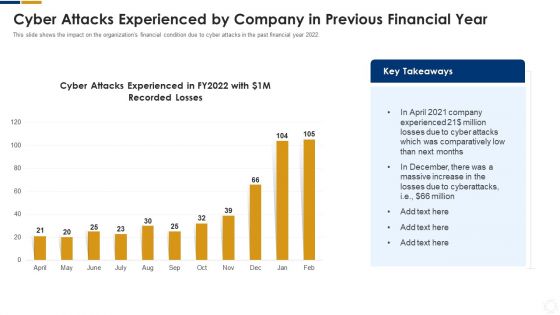
Cybersecurity Cyber Attacks Experienced By Company In Previous Financial Year Ppt Layouts Infographic Template PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver and pitch your topic in the best possible manner with this cybersecurity cyber attacks experienced by company in previous financial year ppt layouts infographic template pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
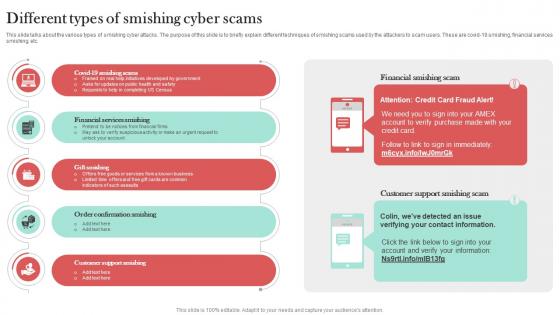
Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc.

Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT
This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. This Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams.

Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Slidegeeks has constructed Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.
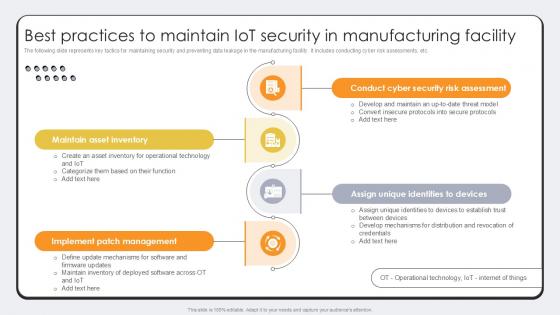
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
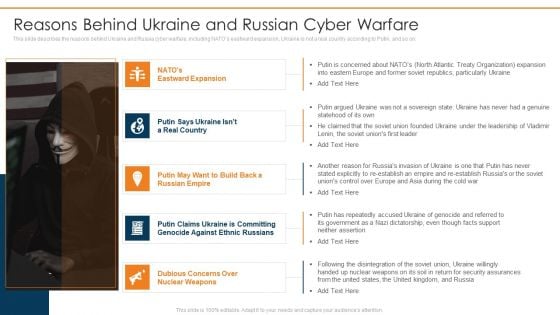
Data Wiper Spyware Attack Reasons Behind Ukraine And Russian Cyber Warfare Introduction PDF
This slide describes the reasons behind Ukraine and Russia cyber warfare, including NATOs eastward expansion, Ukraine is not a real country according to Putin, and so on.Deliver an awe inspiring pitch with this creative data wiper spyware attack reasons behind ukraine and russian cyber warfare introduction pdf bundle. Topics like reasons behind ukraine and russian cyber warfare can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF from Slidegeeks today.
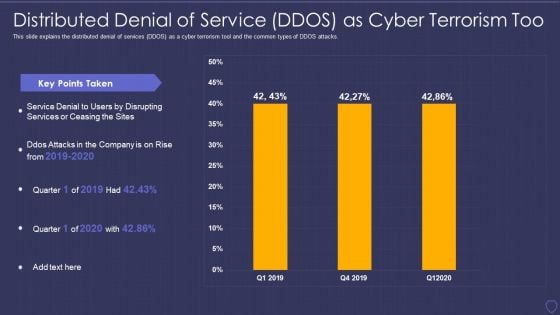
Global Cyber Terrorism Incidents On The Rise IT Distributed Denial Of Service Template PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it distributed denial of service template pdf bundle. Topics like distributed denial of service ddos as cyber terrorism too can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
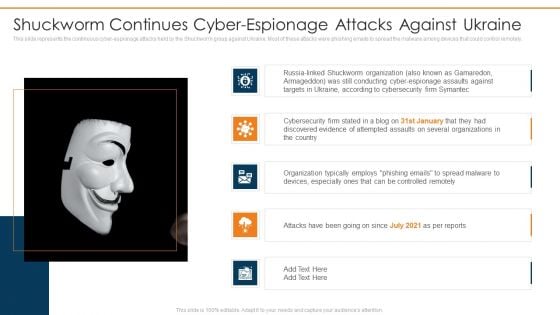
Data Wiper Spyware Attack Shuckworm Continues Cyber Espionage Attacks Against Ukraine Diagrams PDF
This slide represents the continuous cyber-espionage attacks held by the Shuckworm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely.Deliver an awe inspiring pitch with this creative data wiper spyware attack shuckworm continues cyber espionage attacks against ukraine diagrams pdf bundle. Topics like shuckworm continues cyber espionage attacks against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Picture Of Cyber Attack Warning Ppt PowerPoint Presentation Model Background Images PDF
Presenting this set of slides with name picture of cyber attack warning ppt powerpoint presentation model background images pdf. This is a three stage process. The stages in this process are picture of cyber attack warning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For Cyber Attack Ppt PowerPoint Presentation File Sample PDF
Presenting this set of slides with name threat assessment for cyber attack ppt powerpoint presentation file sample pdf. This is a three stage process. The stages in this process are threat assessment for cyber attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Hacker Performing Cyber Attack Vector Icon Ppt PowerPoint Presentation Icon Professional PDF
Presenting hacker performing cyber attack vector icon ppt powerpoint presentation icon professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hacker performing cyber attack vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Phishing Scams And Attacks Icon To Steal Confidential Data Elements PDF
Showcasing this set of slides titled cyber phishing scams and attacks icon to steal confidential data elements pdf. The topics addressed in these templates are cyber phishing scams and attacks icon to steal confidential data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon Of Hacker Launching Cyber Phishing Scams And Attacks Background PDF
Presenting icon of hacker launching cyber phishing scams and attacks background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including icon of hacker launching cyber phishing scams and attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
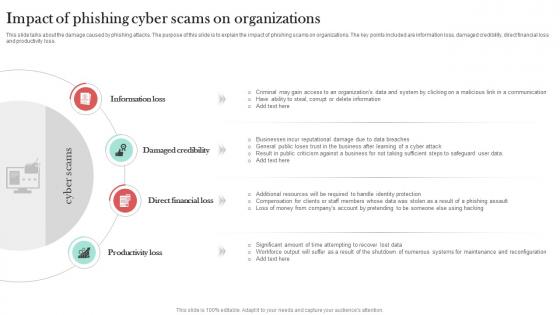
Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT. This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss.
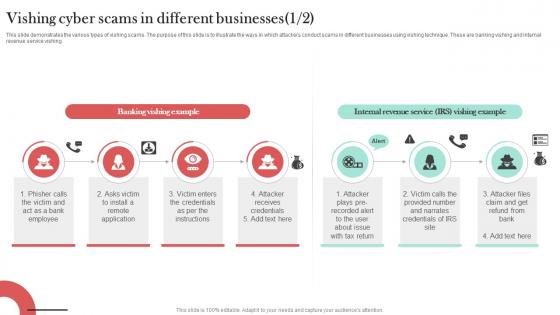
Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT
This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Are you searching for a Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT from Slidegeeks today. This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.
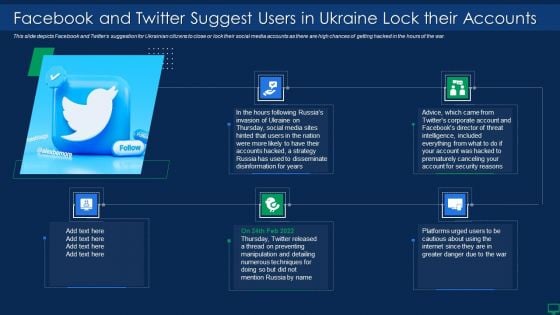
Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































