Cyber Security
Russian Cyber Attacks On Ukraine IT Website Defacements Ddos Template PDF
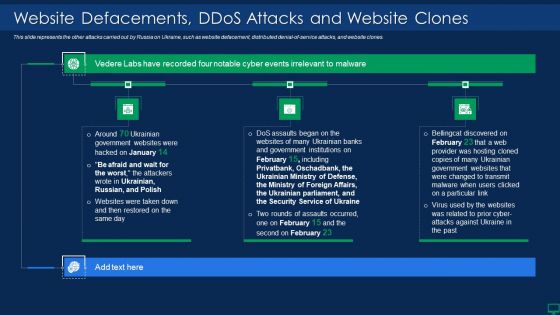
This slide represents the other attacks carried out by Russia on Ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. This is a russian cyber attacks on ukraine it website defacements ddos template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Russian Cyber Attacks On Ukraine IT Us Is Unmasking Russian Inspiration PDF
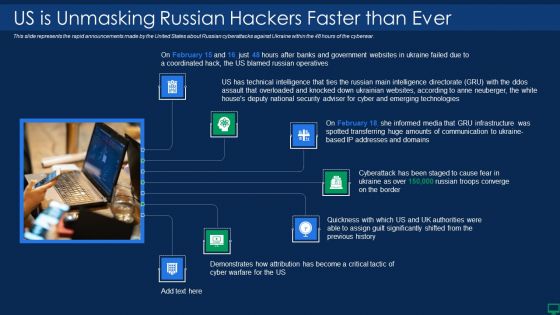
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. Presenting russian cyber attacks on ukraine it us is unmasking russian inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like technical, security, communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Germany Asks To Avoid Russias Sample PDF
This slide depicts the official announcement to avoid Russias Kaspersky antivirus tool by German officials as Kaspersky has been accused of working for the Russian government. This is a russian cyber attacks on ukraine it germany asks to avoid russias sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, portfolio. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Wiper Spyware Attack Cyclops Blink Cyber Attack Against Ukraine Background PDF
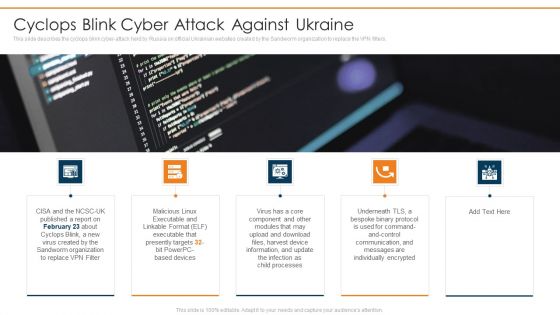
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters.Presenting data wiper spyware attack cyclops blink cyber attack against ukraine background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyclops blink cyber attack against ukraine In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Vector Showing Information Protection From Cyber Attack Ppt PowerPoint Presentation Gallery Guidelines PDF
Persuade your audience using this vector showing information protection from cyber attack ppt powerpoint presentation gallery guidelines pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing information protection from cyber attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Utilizing Cyber Technology For Change Process Challenges In Digital Transformation Introduction PDF
Digital transformation, especially in the healthcare sector, is a complex process and there are some hiccups that need to be addressed for complete success.Presenting utilizing cyber technology for change process challenges in digital transformation introduction pdf. to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like workforce training, technological gaps, lack connectivity, organizational culture, security, capital. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
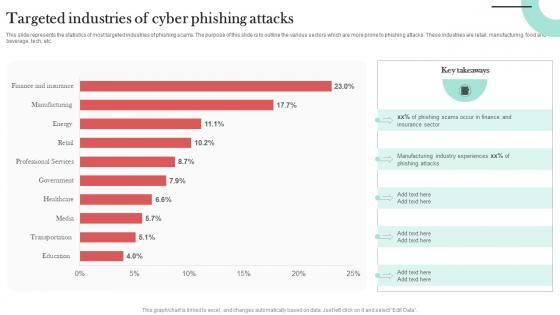
Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT
This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc.
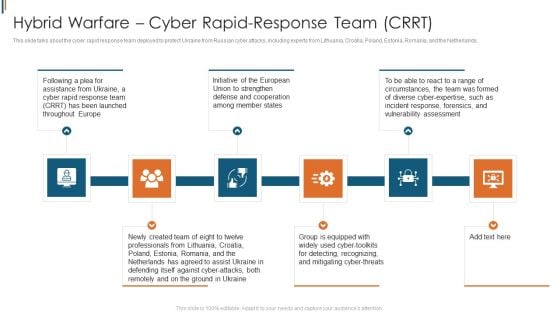
Ukraine Cyberwarfare Hybrid Warfare Cyber Rapid Response Team Crrt Structure Pdf
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyber attacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. Presenting ukraine cyberwarfare hybrid warfare cyber rapid response team crrt structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Initiative of the European Union to strengthen defense and cooperation among member states, Group is equipped with widely used cyber toolkits for detecting, recognizing, and mitigating cyber threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
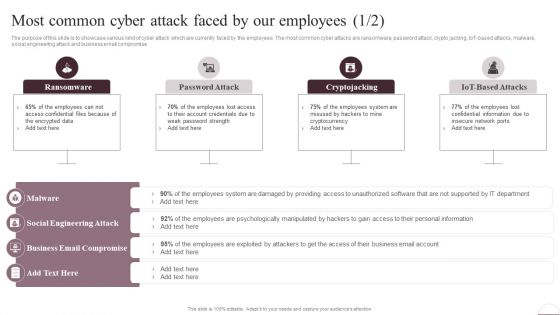
Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF from Slidegeeks today.

Table Of Contents For Russian Cyber Attacks On Ukraine Cell Summary PDF
This is a table of contents for russian cyber attacks on ukraine cell summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, cybersecurity, cyber cell, concerned. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Does Ukraine And Russia Cyber Warfare Kill People Professional PDF
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts.Deliver an awe inspiring pitch with this creative data wiper spyware attack does ukraine and russia cyber warfare kill people professional pdf bundle. Topics like result of misinformation, protection become, susceptible targets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
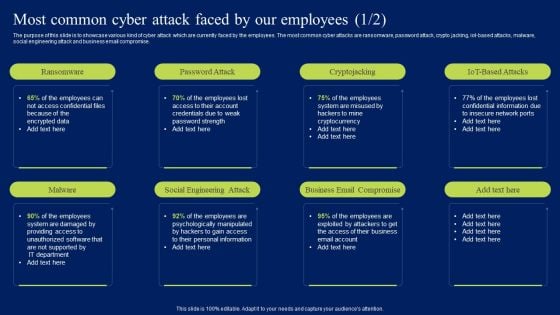
Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, iot-based attacks, malware, social engineering attack and business email compromise. This Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Cyber Phishing Scams And Attacks Dashboard With Improvement Curve Sample PDF
Mentioned slide showcases a comprehensive dashboard used to measure the cyber phishing attacks. Information covered in this slide is related to organization health risk, attack vendors, most vulnerable employees to attacks, improvement curve. Pitch your topic with ease and precision using this cyber phishing scams and attacks dashboard with improvement curve sample pdf. This layout presents information on cyber phishing scams and attacks dashboard with improvement curve. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
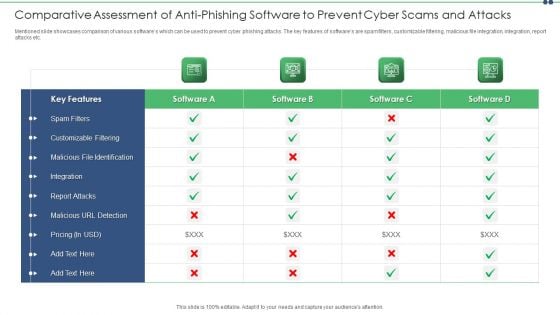
Comparative Assessment Of Anti Phishing Software To Prevent Cyber Scams And Attacks Structure PDF
Mentioned slide showcases comparison of various softwares which can be used to prevent cyber phishing attacks. The key features of softwares are spam filters, customizable filtering, malicious file integration, integration, report attacks etc. Showcasing this set of slides titled comparative assessment of anti phishing software to prevent cyber scams and attacks structure pdf. The topics addressed in these templates are comparative assessment of anti phishing software to prevent cyber scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
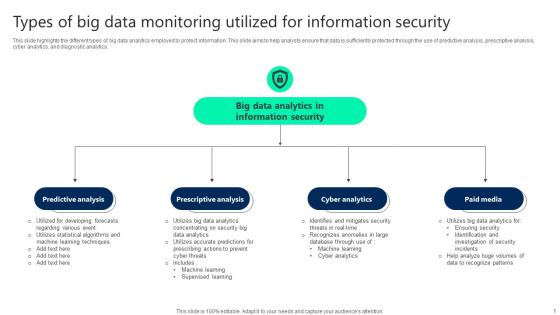
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics.
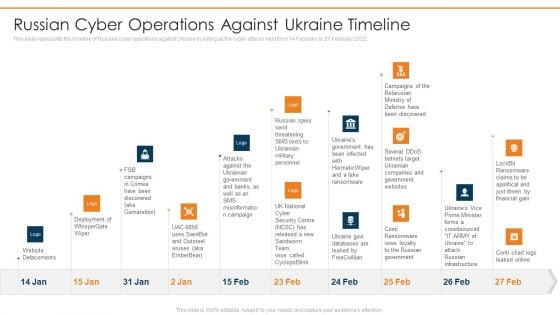
Data Wiper Spyware Attack Russian Cyber Operations Against Ukraine Timeline Clipart PDF
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack russian cyber operations against ukraine timeline clipart pdf Use them to share invaluable insights on website defacements, deployment of whisper gate, attacks against the ukrainian and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
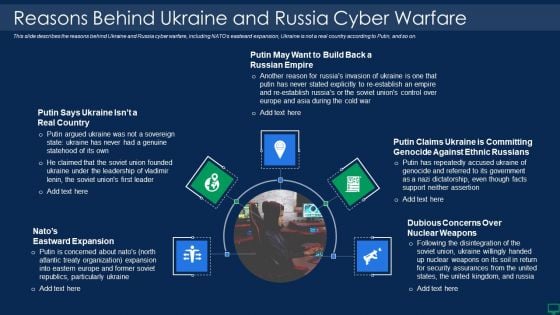
Russian Cyber Attacks On Ukraine IT Reasons Behind Ukraine And Russia Graphics PDF
This slide describes the reasons behind Ukraine and Russia cyber warfare, including NATOs eastward expansion, Ukraine is not a real country according to Putin, and so on. Presenting russian cyber attacks on ukraine it reasons behind ukraine and russia graphics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reasons behind ukraine and russia cyber warfare. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
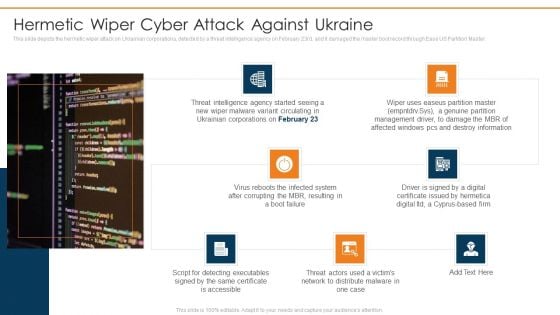
Data Wiper Spyware Attack Hermetic Wiper Cyber Attack Against Ukraine Slides PDF
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Ease US Partition Master.Deliver an awe inspiring pitch with this creative data wiper spyware attack hermetic wiper cyber attack against ukraine slides pdf bundle. Topics like hermetic wiper cyber attack against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Safety Awareness Training Program Icon Ppt Inspiration Graphics Download PDF
Presenting Cyber Safety Awareness Training Program Icon Ppt Inspiration Graphics Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Safety, Awareness Training, Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Online Cyber Safety Awareness Program Ppt Show Good PDF
Presenting Icon For Online Cyber Safety Awareness Program Ppt Show Good PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon, Online Cyber Safety, Awareness Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
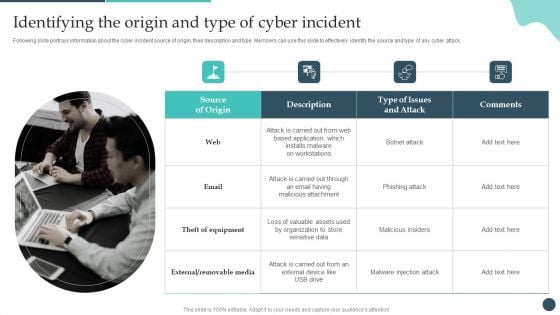
Safety Breach Response Playbook Identifying The Origin And Type Of Cyber Incident Structure PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Want to ace your presentation in front of a live audience Our Safety Breach Response Playbook Identifying The Origin And Type Of Cyber Incident Structure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
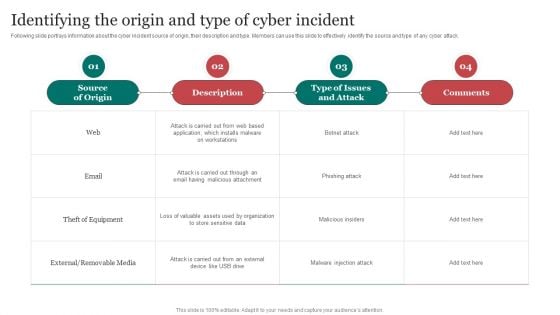
Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Cybersecurity Assessment Matrix Of Cyber Risks Ppt Icon Graphics Pictures PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative cybersecurity assessment matrix of cyber risks ppt icon graphics pictures pdf bundle. Topics like assessment matrix of cyber risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
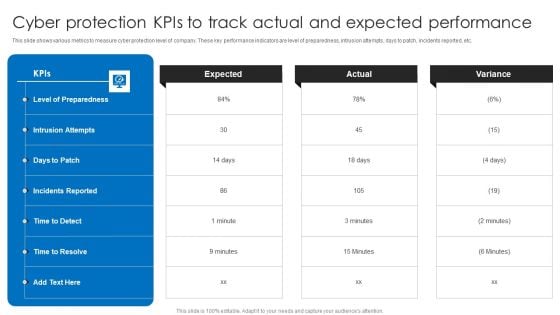
Cyber Protection Kpis To Track Actual And Expected Performance Structure PDF
This slide shows various metrics to measure cyber protection level of company. These key performance indicators are level of preparedness, intrusion attempts, days to patch, incidents reported, etc. Pitch your topic with ease and precision using this Cyber Protection Kpis To Track Actual And Expected Performance Structure PDF. This layout presents information on Cyber Protection Kpis, Track Actual Expected Performance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
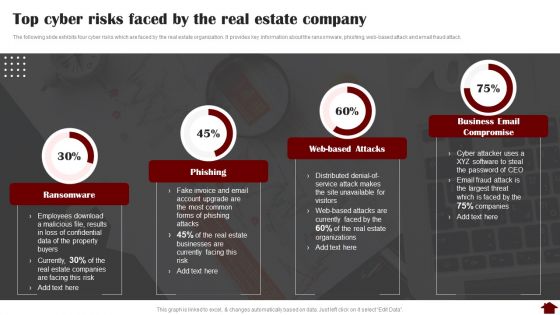
Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Deliver an awe inspiring pitch with this creative Top Cyber Risks Faced By The Real Estate Company Pictures PDF bundle. Topics like Ransomware, Phishing, Business Email Compromise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
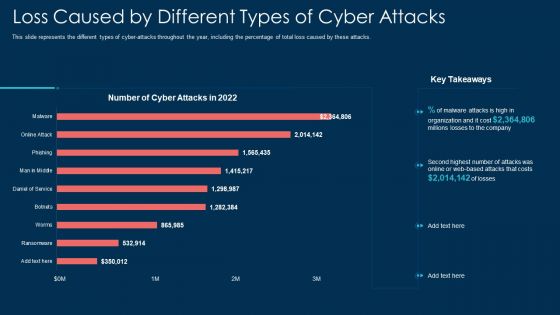
Loss Caused By Different Types Of Cyber Attacks Ppt File Good PDF
This slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative loss caused by different types of cyber attacks ppt file good pdf bundle. Topics like organization, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
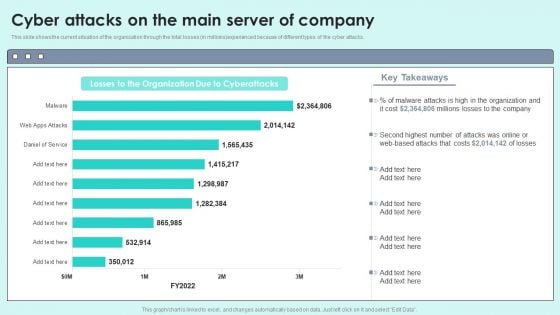
Cyber Attacks On The Main Server Of Company Reverse Proxy For Load Balancing Mockup PDF
This slide shows the current situation of the organization through the total losses in millionsexperienced because of different types of the cyber attacks.Deliver an awe inspiring pitch with this creative Cyber Attacks On The Main Server Of Company Reverse Proxy For Load Balancing Mockup PDF bundle. Topics like Losses Organization, Due Cyberattacks, Based Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Digital Investigation Icon For Cyber Attack Prevention Ppt PowerPoint Presentation Gallery Summary PDF
Persuade your audience using this digital investigation icon for cyber attack prevention ppt powerpoint presentation gallery summary pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including digital investigation icon for cyber attack prevention. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Continuous Development Evaluation Plan To Eliminate Cyber Attacks Mockup PDF
This is a agenda for continuous development evaluation plan to eliminate cyber attacks mockup pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for continuous development evaluation plan to eliminate cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
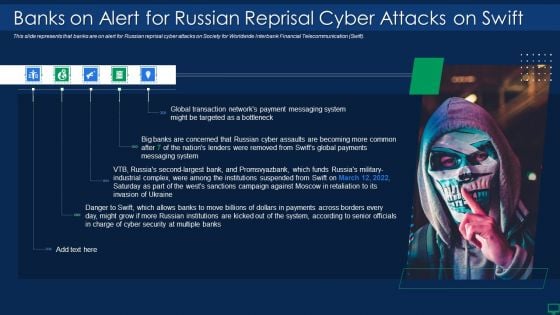
Russian Cyber Attacks On Ukraine IT Banks On Alert For Russian Infographics PDF
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it banks on alert for russian infographics pdf bundle. Topics like system, global, payments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
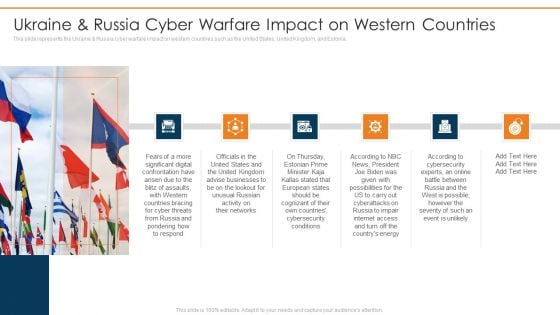
Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Impact On Western Countries Themes PDF
This slide represents the Ukraine and Russia cyber warfare impact on western countries such as the United States, United Kingdom, and Estonia.Deliver an awe inspiring pitch with this creative data wiper spyware attack ukraine and russia cyber warfare impact on western countries themes pdf bundle. Topics like united kingdom advise, businesses lookout for unusual, russian activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
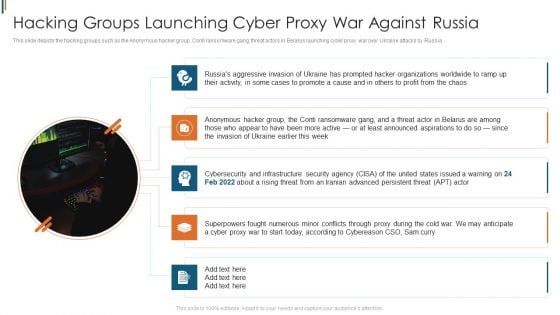
Ukraine Cyberwarfare Hacking Groups Launching Cyber Proxy War Against Russia Guidelines Pdf
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting ukraine cyberwarfare hacking groups launching cyber proxy war against russia guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
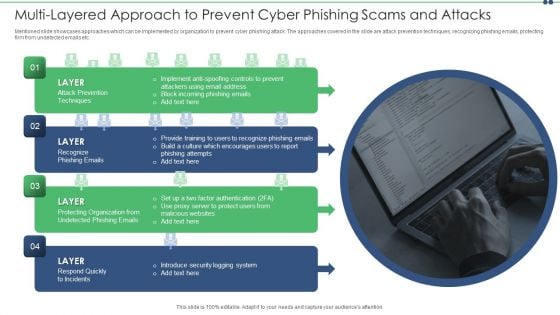
Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
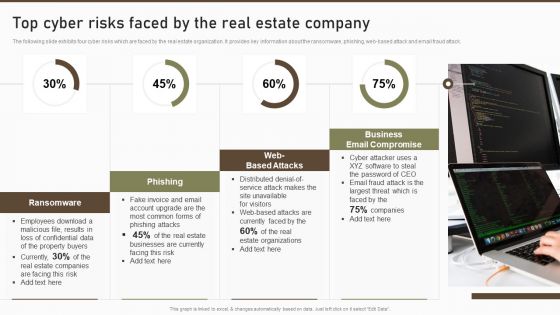
Top Cyber Risks Faced By The Real Estate Company Diagrams PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Deliver an awe inspiring pitch with this creative Top Cyber Risks Faced By The Real Estate Company Diagrams PDF bundle. Topics like Ransomware Business Compromise, Businesses Currently can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
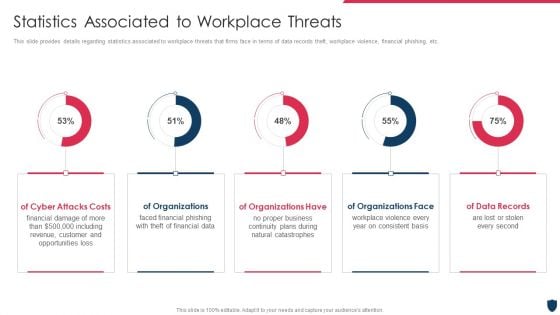
Cyber Safety Incident Management Statistics Associated To Workplace Threats Elements PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver and pitch your topic in the best possible manner with this cyber safety incident management statistics associated to workplace threats elements pdf. Use them to share invaluable insights on cyber attacks costs, organizations, organizations have, organizations face, data records and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
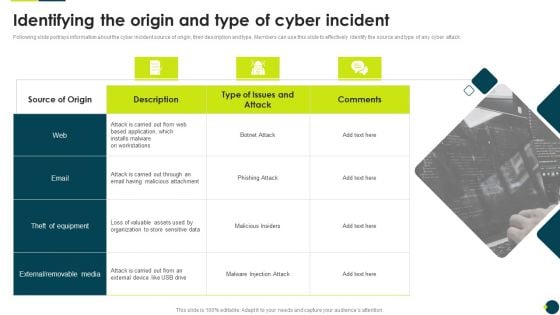
IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
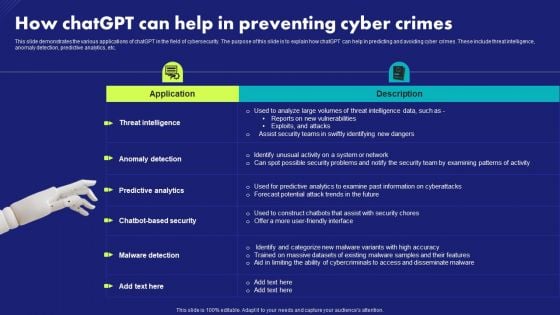
How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Regenerative Artificial Intelligence Systems How Chatgpt Can Help In Preventing Cyber Crimes Diagrams PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Regenerative Artificial Intelligence Systems How Chatgpt Can Help In Preventing Cyber Crimes Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Russian Cyber Attacks On Ukraine IT Cybersecurity Risks Of An Escalating Icons PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. This is a russian cyber attacks on ukraine it cybersecurity risks of an escalating icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like capabilities, economic, measures, severe, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
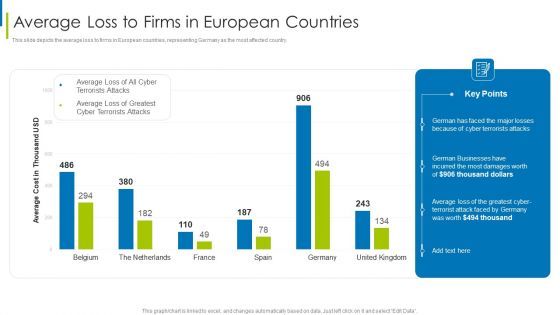
Cyber Terrorism Assault Average Loss To Firms In European Countries Slides PDF
This slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault average loss to firms in european countries slides pdf Use them to share invaluable insights on German businesses, average loss , cyber terrorist attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
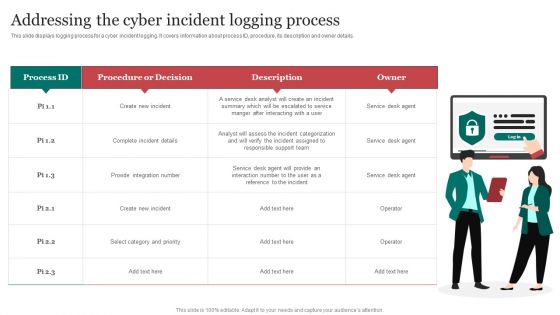
Addressing The Cyber Incident Logging Process Improving Cybersecurity Incident Summary PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Find a pre-designed and impeccable Addressing The Cyber Incident Logging Process Improving Cybersecurity Incident Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.There are so many reasons you need a Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
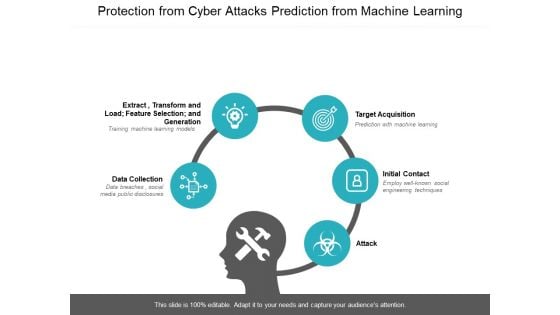
Protection From Cyber Attacks Prediction From Machine Learning Ppt PowerPoint Presentation File Show
Presenting this set of slides with name protection from cyber attacks prediction from machine learning ppt powerpoint presentation file show. This is a five stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
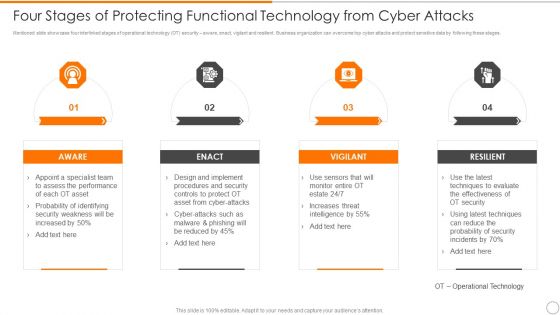
Four Stages Of Protecting Functional Technology From Cyber Attacks Guidelines PDF
Persuade your audience using this four stages of protecting functional technology from cyber attacks guidelines pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including aware, vigilant, resilient. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Cyber Phishing Scams And Attacks With Key Strategies Slides PDF
Mentioned slide showcases various cyber phishing attacks such as deceptive, spear, whaling and vishing. It provides detailed information about likelihood of attack, examples of attacks and strategies which can be implemented to overcome phishing attacks. Showcasing this set of slides titled major cyber phishing scams and attacks with key strategies slides pdf. The topics addressed in these templates are target, information, email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
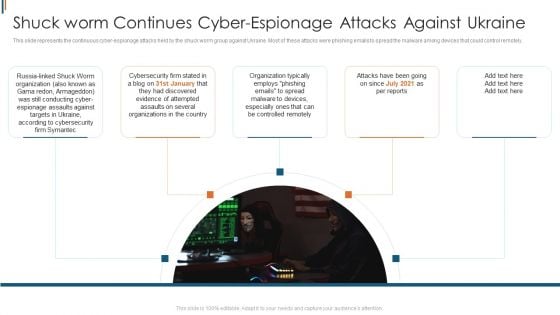
Ukraine Cyberwarfare Shuck Worm Continues Cyber Espionage Attacks Against Ukraine Pictures Pdf
This slide represents the continuous cyber espionage attacks held by the shuck worm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Presenting ukraine cyberwarfare shuck worm continues cyber espionage attacks against ukraine pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization typically, cybersecurity, evidence of attempted assaults. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
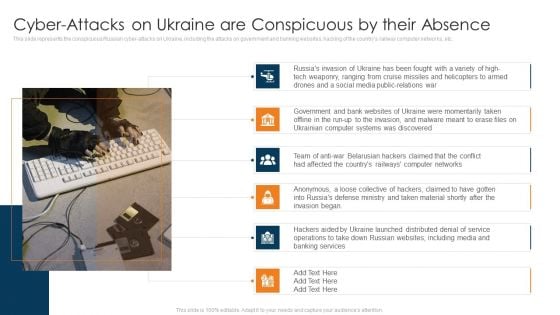
Data Wiper Spyware Attack Cyber Attacks On Ukraine Are Conspicuous Elements PDF
This slide represents the conspicuous Russian cyber-attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc.This is a data wiper spyware attack cyber attacks on ukraine are conspicuous elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine launched distributed, russian websites, belarusian hackers You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Banks On Alert For Russian Reprisal Cyber Attacks On Swift Sample PDF
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a data wiper spyware attack banks on alert for russian reprisal cyber attacks on swift sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like payments messaging system, military industrial complex, institutions suspended You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Several Threat Actors Profile Themes PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative cyber safety incident management determine several threat actors profile themes pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
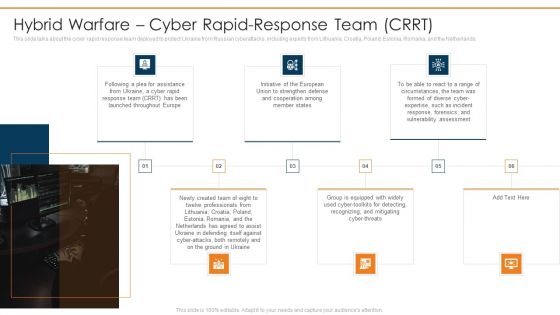
Data Wiper Spyware Attack Hybrid Warfare Cyber Rapid Response Download PDF
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyberattacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands.This is a data wiper spyware attack hybrid warfare cyber rapid response download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like launched throughout, cooperation among, vulnerability assessment You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
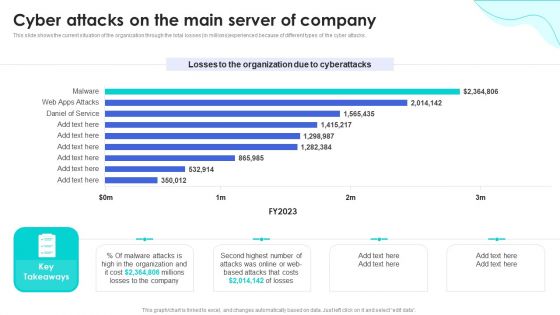
Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF
This slide shows the current situation of the organization through the total losses in millions experienced because of different types of the cyber attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF can be your best option for delivering a presentation. Represent everything in detail using Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
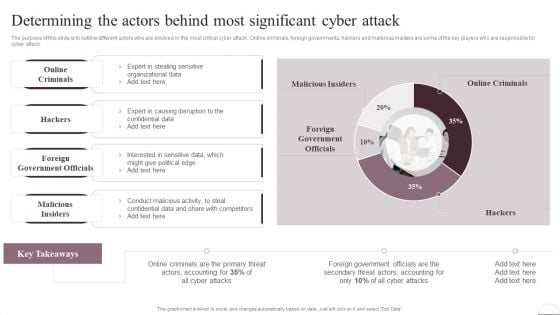
Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
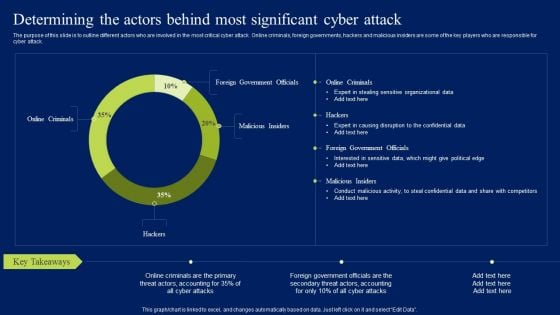
Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Want to ace your presentation in front of a live audience Our Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
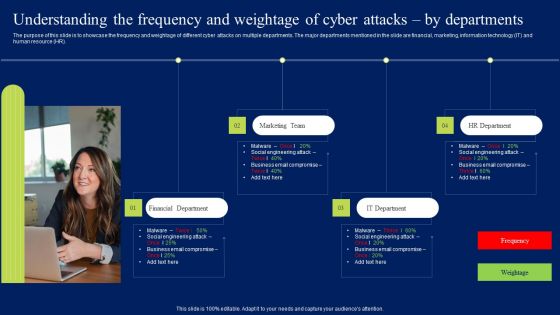
Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF today and make your presentation stand out from the rest.
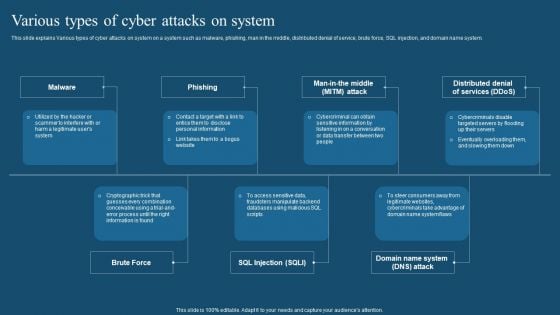
Recent Technologies In IT Industry Various Types Of Cyber Attacks On System Microsoft PDF
This slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Get a simple yet stunning designed Recent Technologies In IT Industry Various Types Of Cyber Attacks On System Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Recent Technologies In IT Industry Various Types Of Cyber Attacks On System Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
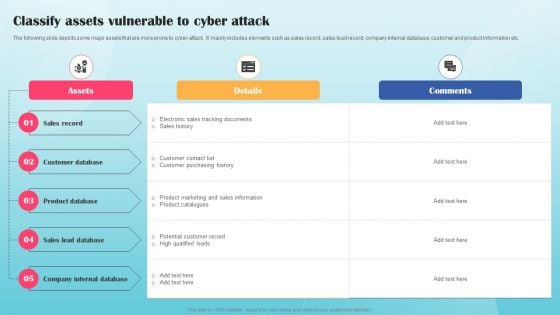
Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF
The following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. If you are looking for a format to display your unique thoughts, then the professionally designed Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
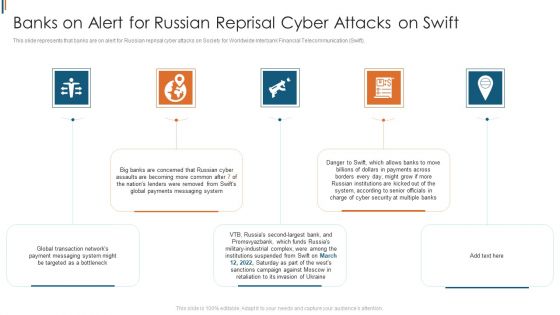
Ukraine Cyberwarfare Banks On Alert For Russian Reprisal Cyber Attacks On Swift Diagrams Pdf
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a ukraine cyberwarfare banks on alert for russian reprisal cyber attacks on swift diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global transaction networks payment messaging system might be targeted as a bottleneck, big banks are concerned that russian cyber assaults are becoming more common after seven of the nations, lenders were removed from swifts global payments messaging system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
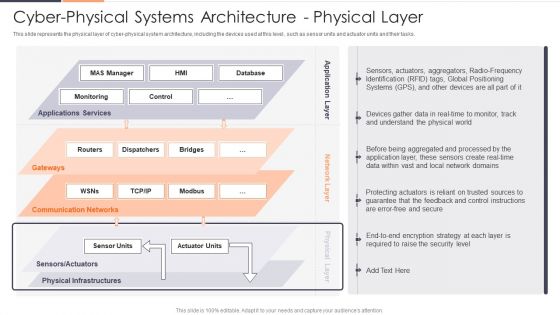
Cyber Physical Systems Architecture Physical Layer Ppt Infographics Infographic Template PDF
This slide represents the physical layer of cyber physical system architecture, including the devices used at this level, such as sensor units and actuator units and their tasks. Deliver and pitch your topic in the best possible manner with this Cyber Physical Systems Architecture Physical Layer Ppt Infographics Infographic Template PDF. Use them to share invaluable insights on Applications Services, Communication Networks, Physical Infrastructures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
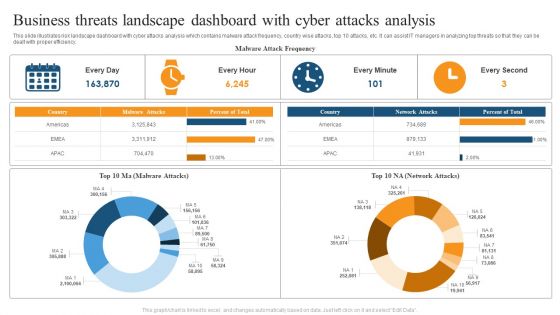
Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF
This slide illustrates risk landscape dashboard with cyber attacks analysis which contains malware attack frequency, country wise attacks, top 10 attacks, etc. It can assist IT managers in analyzing top threats so that they can be dealt with proper efficiency. Pitch your topic with ease and precision using this Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF. This layout presents information on Malware Attack Frequency, Every Minute, Every Second. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
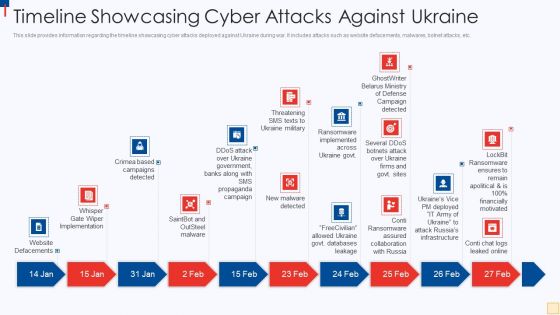
Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF
This slide provides information regarding the timeline showcasing cyber attacks deployed against Ukraine during war. It includes attacks such as website defacements, malwares, botnet attacks, etc. Presenting Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Website Defacements, Saintbot And Outsteel Malware, New Malware Detected, Threatening SMS Texts To Ukraine Military. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































