Cyber Security

Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf
The following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc. Are you searching for a Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf from Slidegeeks today. The following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.
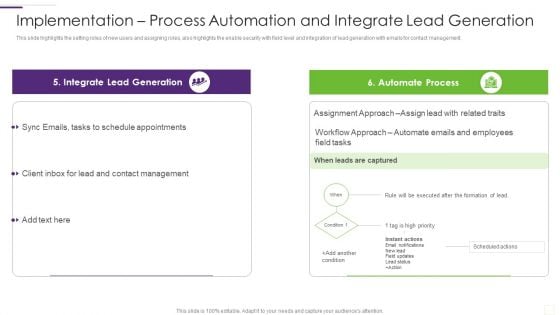
CRM Implementation Strategy Implementation Process Automation And Integrate Infographics PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Implementation Strategy Implementation Process Automation And Integrate Infographics PDF bundle. Topics like Lead Generation, Automate Process, Assignment Approach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cybersecurity Monitoring Plan Steps In Detail Aligning The Incident Management Policies Sample PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Presenting cybersecurity monitoring plan steps in detail aligning the incident management policies sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security monitoring solutions, ongoing management, incident logging, incident categorization, incident prioritization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
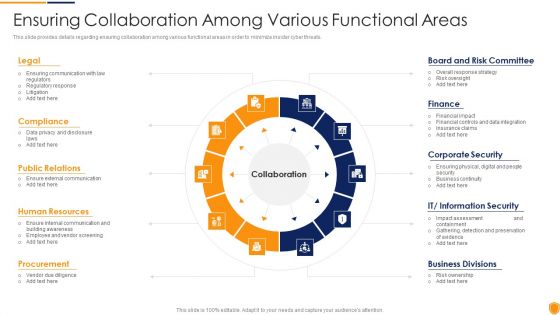
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Collaboration Among Elements PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting mitigating cybersecurity threats and vulnerabilities ensuring collaboration among elements pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like compliance, public relations, human resources, procurement, board and risk committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack For The First Time In History Anyone Can Join A War Clipart PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare.This is a data wiper spyware attack for the first time in history anyone can join a war clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global digital volunteers, connected to the ukraine russia, official from check You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
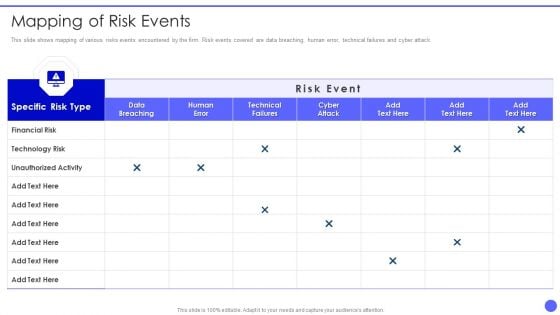
Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF. Use them to share invaluable insights on Specific Risk Type, Financial Risk, Technology Risk, Unauthorized Activity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
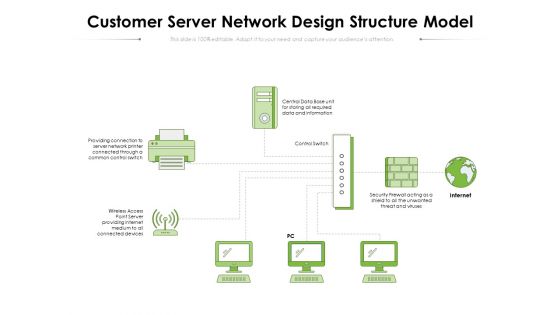
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
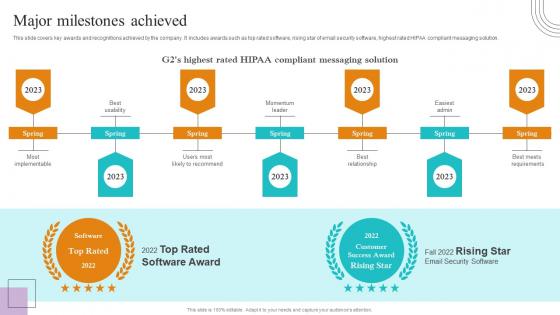
Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
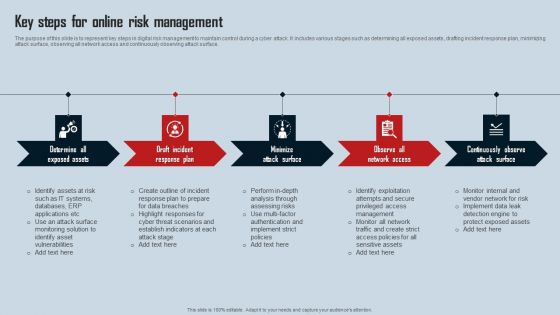
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
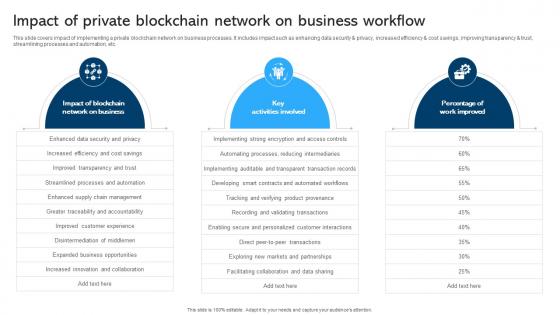
Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V
This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc.

Softwaredefined Perimeter Solution Infrastructure Managing Complexity Of Multiple Cloud Platforms Inspiration PDF
This slide covers network that prevention cyber attacks with a software-defined perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.Make sure to capture your audiences attention in your business displays with our gratis customizable Softwaredefined Perimeter Solution Infrastructure Managing Complexity Of Multiple Cloud Platforms Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
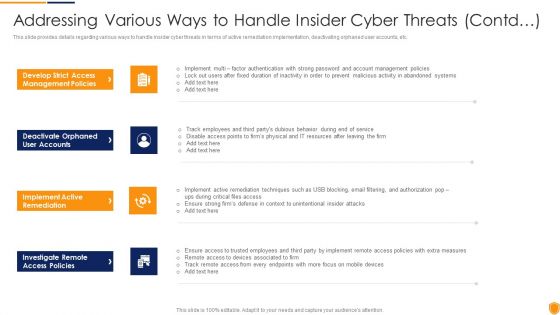
Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
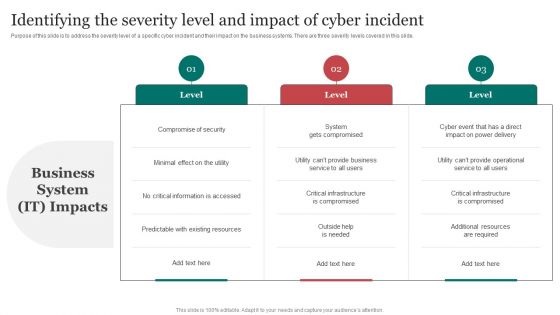
Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Make sure to capture your audiences attention in your business displays with our gratis customizable Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
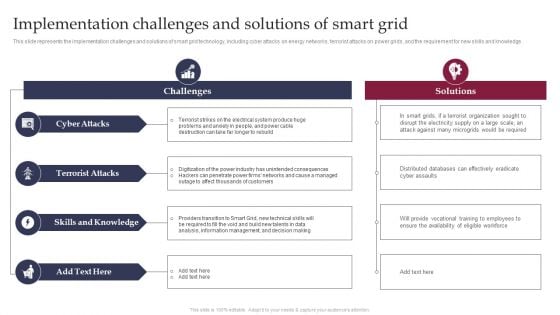
Smart Grid Technology Implementation Challenges And Solutions Designs PDF
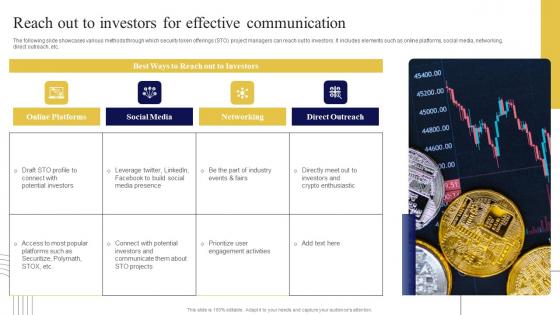
Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf
The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc. Slidegeeks is here to make your presentations a breeze with Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc.
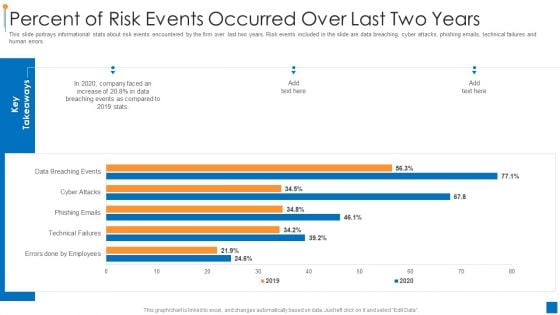
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
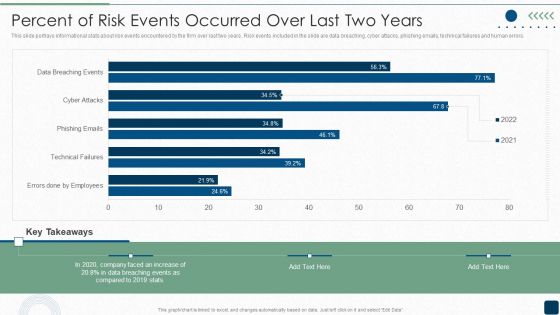
Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF
The slide showcases the interconnected functions of a framework used to guide the organizations security measures. It covers identify, protect, detect, respond and recover. Presenting Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify, Protect, Detect. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
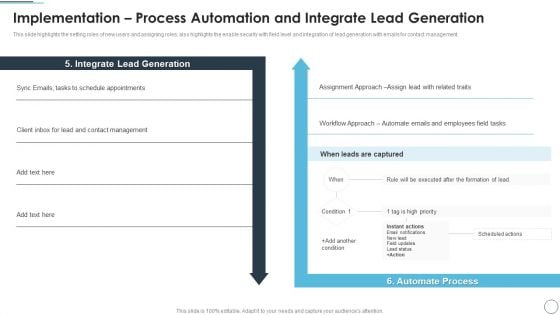
Implementation Process Automation And Integrate Lead Generation Demonstration PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Implementation Process Automation And Integrate Lead Generation Demonstration PDF bundle. Topics like Schedule Appointments, Contact Management, Lead Generation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Scorecard 30 60 90 Days Plan Topics PDF
This is a cybersecurity risk scorecard 30 60 90 days plan topics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 8 essential information security risk scorecard for organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF Use them to share invaluable insights on Accessible Within Organization, Individual System, Accessible To Key Shareholders and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan System Management Checklist Background PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Management Checklist Background PDF Use them to share invaluable insights on System Monitoring, Security Patches, Virus Scanning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Table Of Contents Topics PDF
This is a Cybersecurity Risk Administration Plan Table Of Contents Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing The Risk, Defining Risk Level, Setting Scenario For Security Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
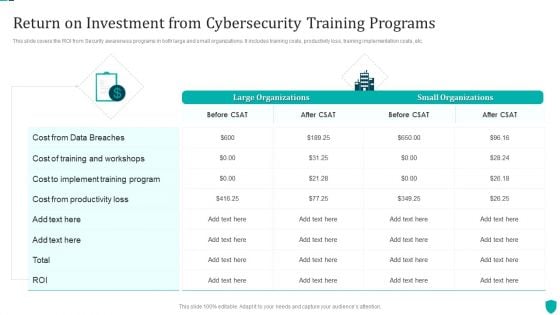
Return On Investment From Cybersecurity Training Programs Demonstration PDF
This slide covers the ROI from Security awareness programs in both large and small organizations. It includes training costs, productivity loss, training implementation costs, etc.Showcasing this set of slides titled Return On Investment From Cybersecurity Training Programs Demonstration PDF. The topics addressed in these templates are Training And Workshops, Implement Training, Cost From Productivity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
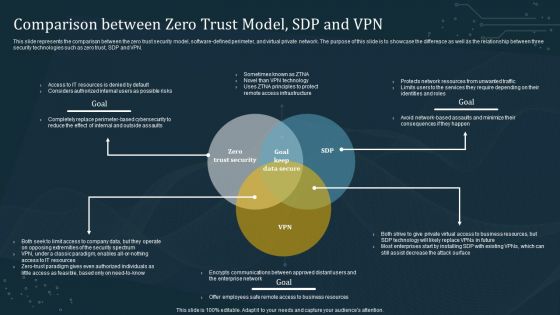
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Table Of Contents For Accelerate Online Journey Now Slide Slides PDF
This is a Table Of Contents For Accelerate Online Journey Now Slide Slides PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cybersecurity, Security Organization, Demonstrating Cybersecurity You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
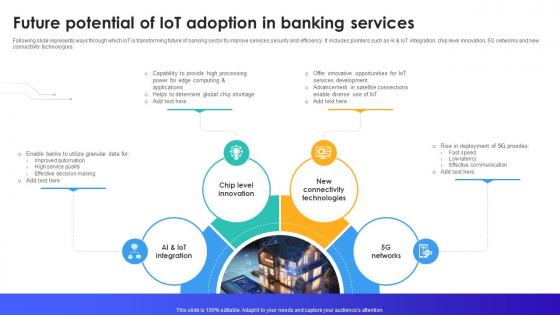
Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.

Web App Firewall Services IT Impact Of Web Application Firewall Sample PDF
This slide represents the Web Application Firewall deployment pricing, and it covers the price list for resource types such as bot control, requests, and management. Deliver an awe inspiring pitch with this creative web app firewall services it impact of web application firewall sample pdf bundle. Topics like reduced, security expenses, revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing
The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern. Retrieve professionally designed Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern

IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V
This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc. Explore a selection of the finest IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc.
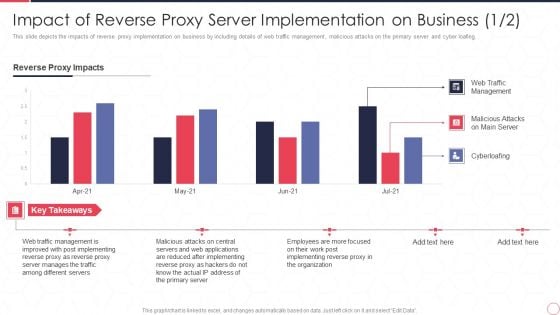
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy Server IT Ppt Professional Slides PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Deliver an awe inspiring pitch with this creative impact of reverse proxy server implementation on business reverse proxy server it ppt professional slides pdf bundle. Topics like reverse proxy impacts, web traffic management, malicious attacks on main server, cyberloafing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
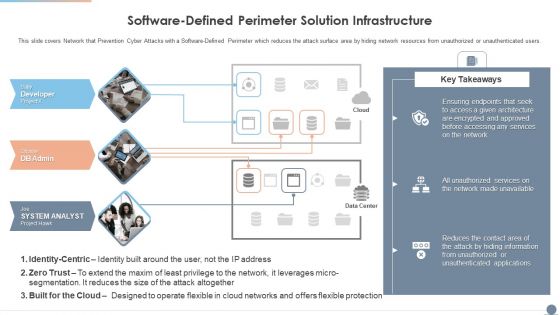
Multi Cloud Complexity Management Software Defined Perimeter Solution Infrastructure Summary PDF
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Presenting Multi Cloud Complexity Management Software Defined Perimeter Solution Infrastructure Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cloud Networks, Services, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
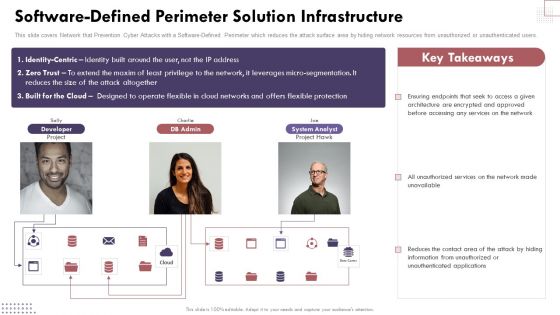
Software Defined Perimeter Solution Infrastructure Cloud Computing Complexities And Solutions Infographics PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Software Defined Perimeter Solution Infrastructure Cloud Computing Complexities And Solutions Infographics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
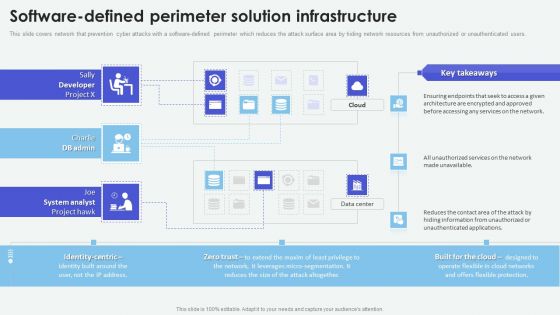
Cloud Based Computing Analysis Software Defined Perimeter Solution Infrastructure Summary PDF
This slide covers network that prevention cyber attacks with a software-defined perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Take your projects to the next level with our ultimate collection of Cloud Based Computing Analysis Software Defined Perimeter Solution Infrastructure Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest
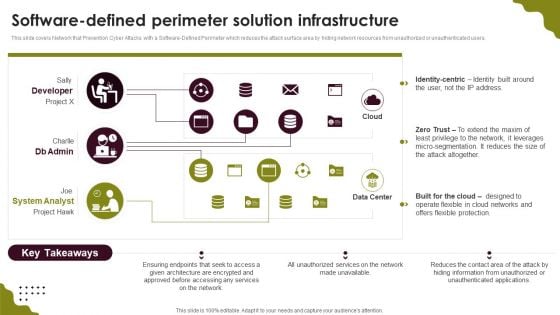
Cloud Computing Scalability Software Defined Perimeter Solution Infrastructure Guidelines PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Take your projects to the next level with our ultimate collection of Cloud Computing Scalability Software Defined Perimeter Solution Infrastructure Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.
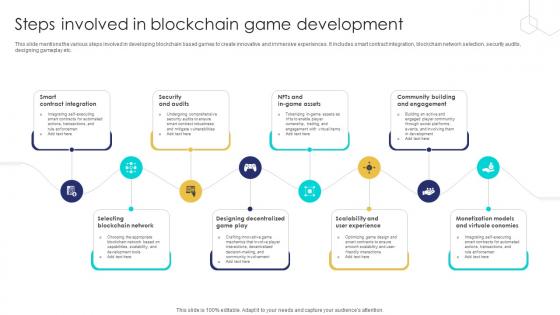
Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V
This slide mentions the various steps involved in developing blockchain based games to create innovative and immersive experiences. It includes smart contract integration, blockchain network selection, security audits, designing gameplay etc. Are you searching for a Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V from Slidegeeks today. This slide mentions the various steps involved in developing blockchain based games to create innovative and immersive experiences. It includes smart contract integration, blockchain network selection, security audits, designing gameplay etc.
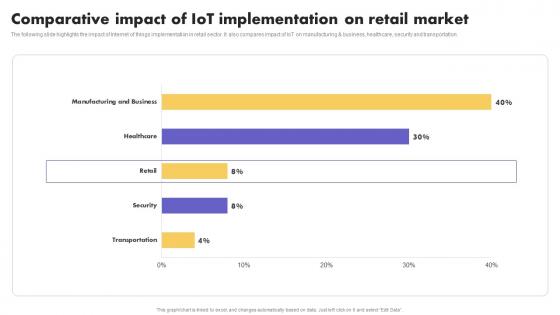
IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Create an editable IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
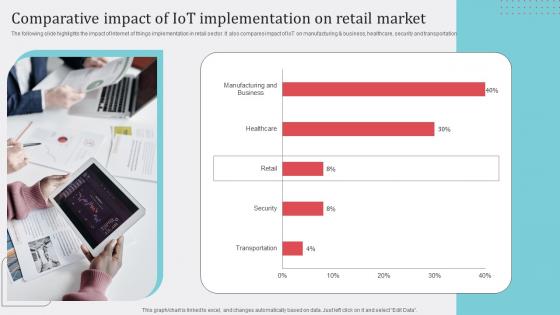
Comparative Impact IoT How Industrial IoT Is Changing Worldwide Microsoft Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation Boost your pitch with our creative Comparative Impact IoT How Industrial IoT Is Changing Worldwide Microsoft Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
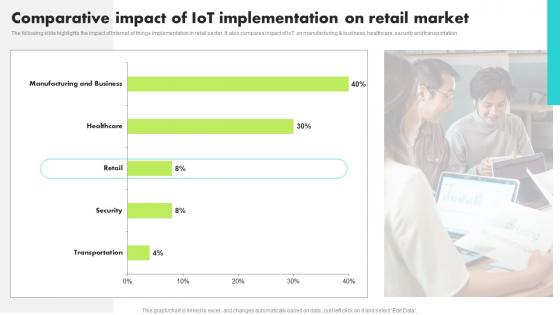
Comparative Impact Of IoT Implementation Guide For Retail IoT Solutions Analysis Demonstration Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation Find a pre designed and impeccable Comparative Impact Of IoT Implementation Guide For Retail IoT Solutions Analysis Demonstration Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
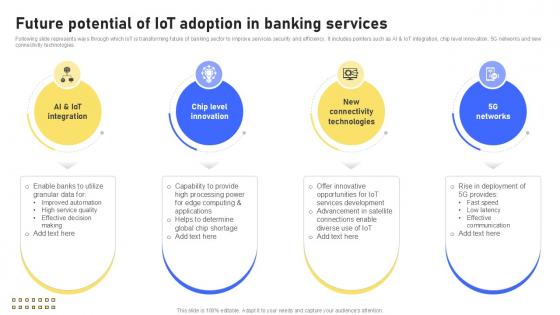
Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.
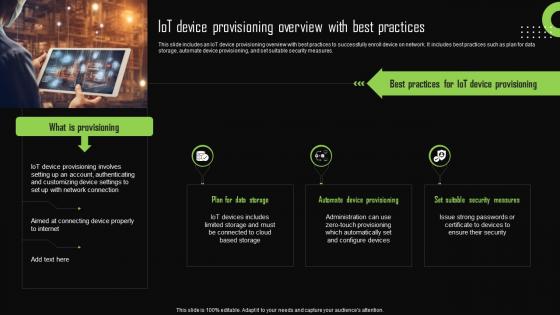
Iot Device Provisioning Overview With Best Practices Iot Device Management Sample Pdf
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Do you know about Slidesgeeks Iot Device Provisioning Overview With Best Practices Iot Device Management Sample Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures.
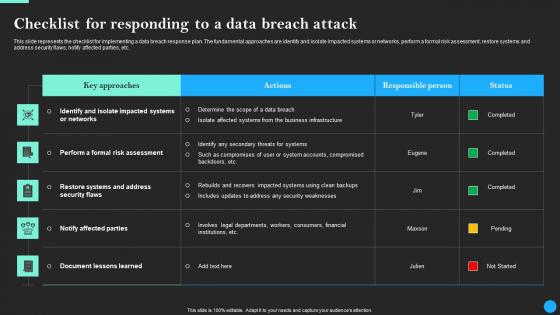
Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security
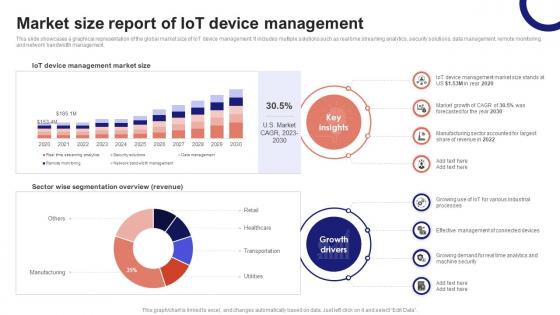
IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT Ss V
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. Slidegeeks has constructed IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management.
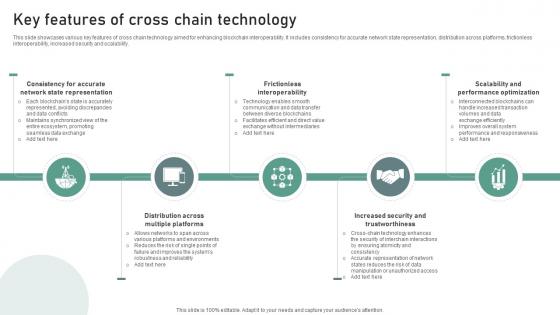
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.

Table Of Contents For Web Development Clipart PDF
This is a Table Of Contents For Web Development Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Technique, Embedded Web Development, Security Web Development You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Safety Breach Response Playbook Communication Plan For Effective Incident Guidelines PDF
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person. Slidegeeks has constructed Safety Breach Response Playbook Communication Plan For Effective Incident Guidelines PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Roles And Responsibilities For Managing Operational Risk Slides PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.This is a roles and responsibilities for managing operational risk slides pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
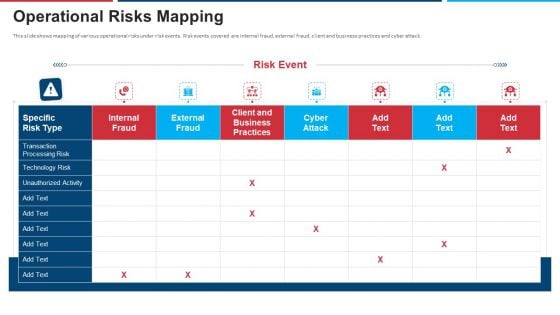
Mitigation Strategies For Operational Threat Operational Risks Mapping Ppt File Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks mapping ppt file graphics pdf. Use them to share invaluable insights on technology risk, transaction processing risk, unauthorized activity, business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
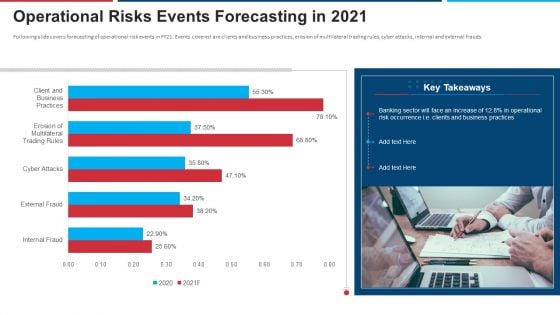
Mitigation Strategies For Operational Threat Operational Risks Events Forecasting In 2021 Ppt Infographic Template Microsoft PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks events forecasting in 2021 ppt infographic template microsoft pdf. Use them to share invaluable insights on banking, operational risk, occurrence, business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































