Cyber Security

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
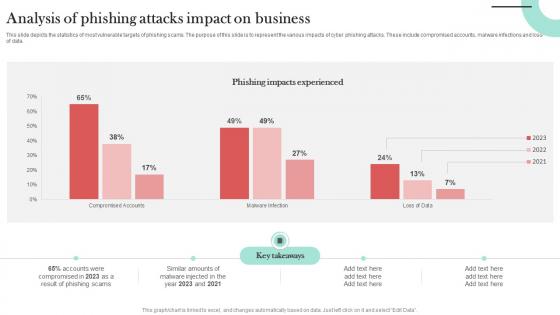
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.
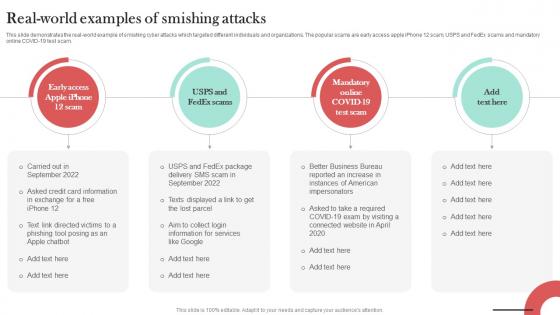
Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam.
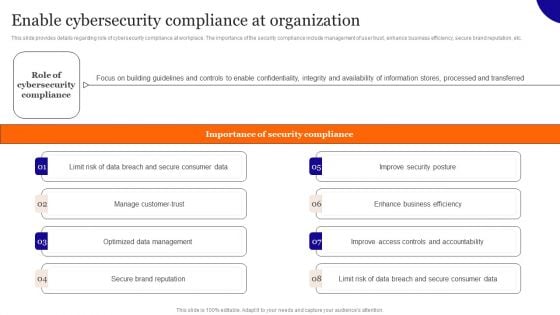
Enable Cybersecurity Compliance At Organization Mockup PDF
This slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Enable Cybersecurity Compliance At Organization Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
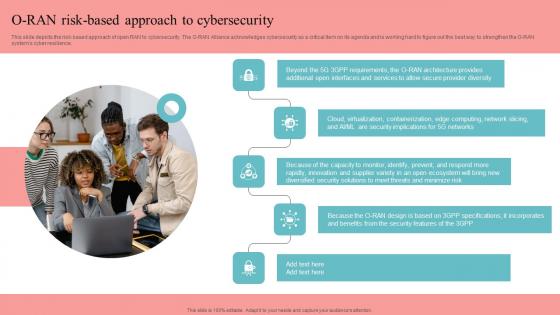
O RAN Risk Based Approach To Cybersecurity Unlocking The Potential Of Open RAN Information Pdf
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward O RAN Risk Based Approach To Cybersecurity Unlocking The Potential Of Open RAN Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal O RAN Risk Based Approach To Cybersecurity Unlocking The Potential Of Open RAN Information Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience.
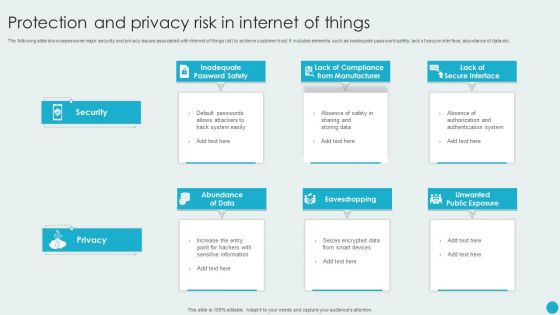
Protection And Privacy Risk In Internet Of Things Topics PDF
The following slide showcases some major security and privacy issues associated with internet of things iot to achieve customer trust. It includes elements such as inadequate password safety, lack of secure interface, abundance of data etc. Presenting Protection And Privacy Risk In Internet Of Things Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Abundance Of Data, Eavesdropping, Unwanted Public Exposure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
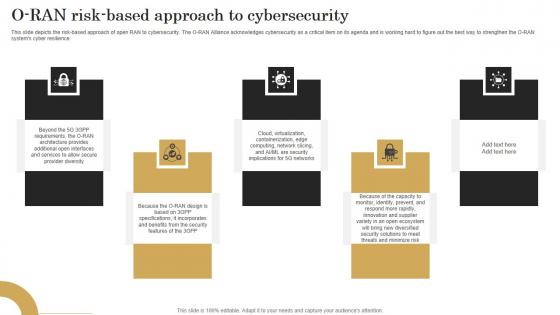
O Ran Risk Based Approach To Cybersecurity Revolutionizing Mobile Networks Guidelines PDF
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download O Ran Risk Based Approach To Cybersecurity Revolutionizing Mobile Networks Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience.
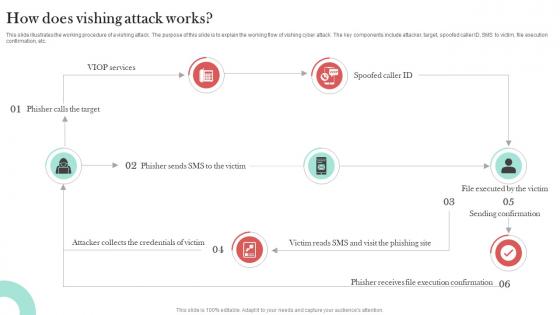
How Does Vishing Attack Works Man In The Middle Phishing IT
This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. The How Does Vishing Attack Works Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc.

About Phishing Attacks Overview And Impact Man In The Middle Phishing IT
This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Get a simple yet stunning designed About Phishing Attacks Overview And Impact Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit About Phishing Attacks Overview And Impact Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc.
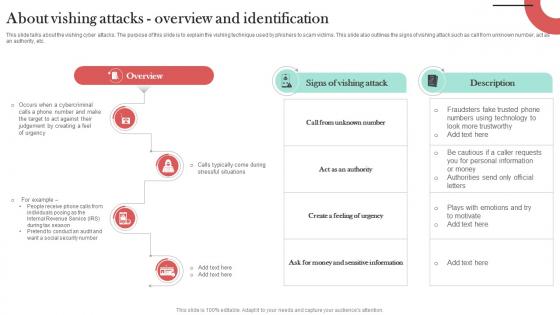
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.
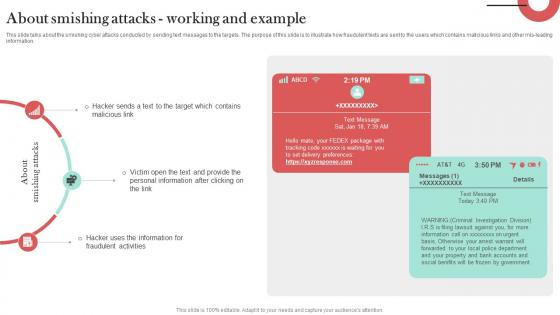
About Smishing Attacks Working And Example Man In The Middle Phishing IT
This slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Slidegeeks is here to make your presentations a breeze with About Smishing Attacks Working And Example Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information.
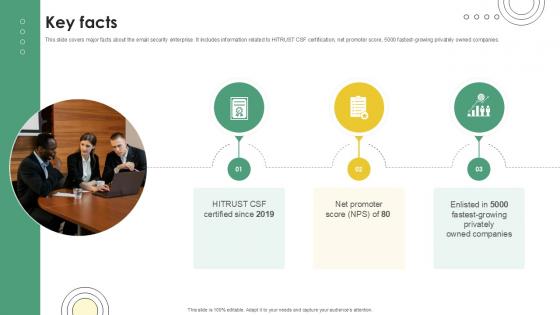
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
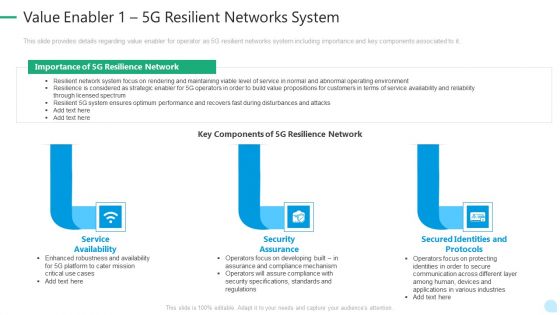
5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
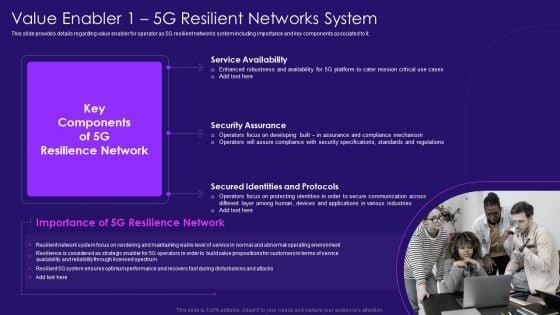
Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. Presenting Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Availability, Security Assurance, Secured Identities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis For Effective Threat Graphics PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. This is a mitigating cybersecurity threats and vulnerabilities impact analysis for effective threat graphics pdf template with various stages. Focus and dispense information one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis for effective threat management in securing workplace. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Value Enabler 1 5G Resilient Networks System Professional PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Value Enabler 1 5G Resilient Networks System Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Availability, Security Assurance, Secured Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
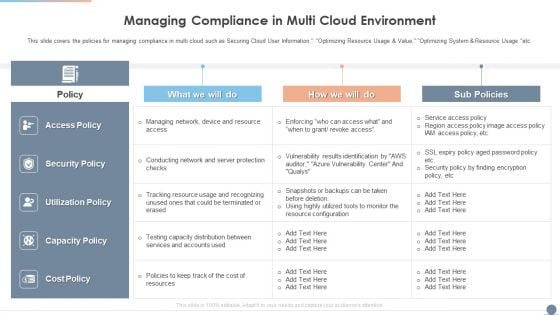
Multi Cloud Complexity Management Managing Compliance In Multi Cloud Environment Pictures PDF
This slide covers the policies for managing compliance in multi cloud such as Securing Cloud User Information, Optimizing Resource Usage And Value, Optimizing System And Resource Usage etc. Deliver and pitch your topic in the best possible manner with this Multi Cloud Complexity Management Managing Compliance In Multi Cloud Environment Pictures PDF. Use them to share invaluable insights on Security Policy, Device And Resource, Network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cryptocurrency Ledger Public Blockchain Technology Infographics PDF
This slide depicts the public blockchain technology framework and how data is stored in the public blockchain, bitcoin, voting are few examples of the public blockchain. Presenting Cryptocurrency Ledger Public Blockchain Technology Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Network, Secure Method, Security Protocols Sincerely. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
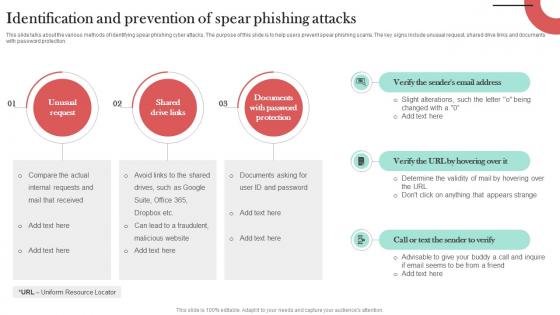
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.
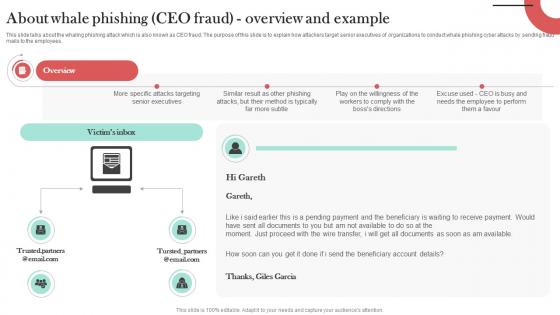
About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT
This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Find highly impressive About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees.
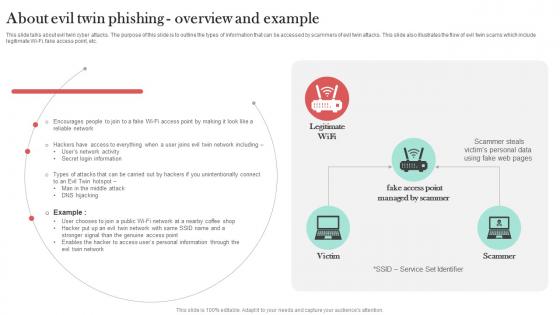
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc.

Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. If you are looking for a format to display your unique thoughts, then the professionally designed Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.
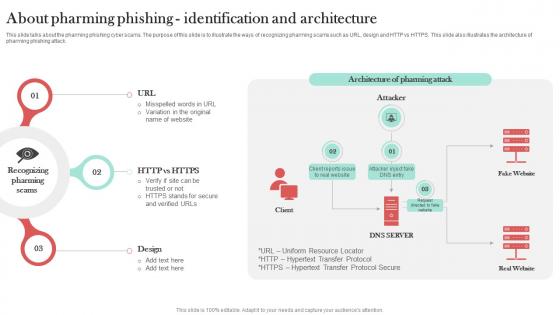
About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack.

Tools Provided By Google To Prevent Man In The Middle Phishing IT
This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Welcome to our selection of the Tools Provided By Google To Prevent Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc.

Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf
Showcasing this set of slides titled Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf The topics addressed in these templates are Organizations Network, Security Assessments, Provides Privileged All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the benefits of using cybersecurity key performance indicators which help an organization to provide a snapshot to its relevant stakeholders, managers. It include details such as removes unknown devices on an organizations network, etc.

Cybersecurity Guidelines IT Internet Usage Policy Password Guidelines Download PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Guidelines IT Internet Usage Policy Password Guidelines Download PDF from Slidegeeks and deliver a wonderful presentation.

Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
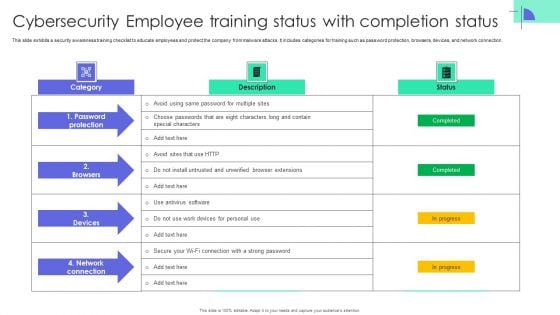
Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
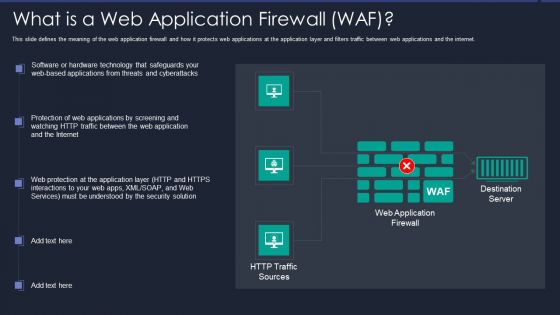
Web App Firewall Services IT What Is A Web Application Firewall WAF Graphics PDF
This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. Deliver and pitch your topic in the best possible manner with this web app firewall services it what is a web application firewall waf graphics pdf. Use them to share invaluable insights on applications, technology, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF. Use them to share invaluable insights on Reduce Ransomware, Reduce Distributed, Approaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
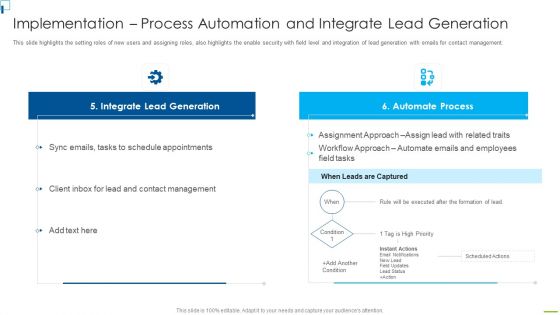
Designing And Deployment Implementation Process Automation And Integrate Themes PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Deliver and pitch your topic in the best possible manner with this designing and deployment implementation process automation and integrate themes pdf. Use them to share invaluable insights on integrate lead generation, automate process, schedule appointments, contact management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
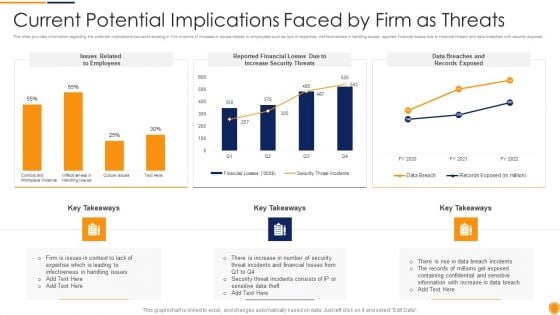
Mitigating Cybersecurity Threats And Vulnerabilities Current Potential Implications Formats PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities current potential implications formats pdf bundle. Topics like employees, increase security threats, data breaches and records exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
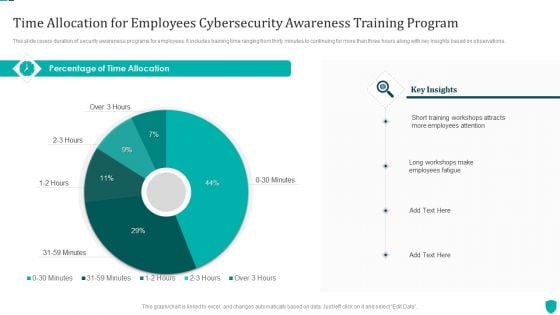
Time Allocation For Employees Cybersecurity Awareness Training Program Themes PDF
This slide covers duration of security awareness programs for employees. It includes training time ranging from thirty minutes to continuing for more than three hours along with key insights based on observations.Pitch your topic with ease and precision using this Time Allocation For Employees Cybersecurity Awareness Training Program Themes PDF. This layout presents information on Training Workshops, Employees Attention, Employees Fatigue. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF
The slide showcases various steps of Nist RMF process which instructs in monitoring, selecting and implementing security controls. It covers identify, select, implement, assess, authorize and monitor. Persuade your audience using this Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF.zip. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
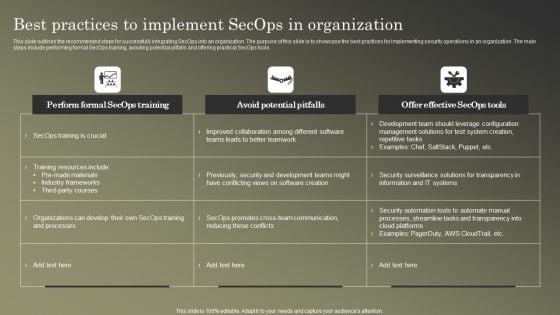
Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF
This slide outlines the recommended steps for successfully integrating SecOps into an organization. The purpose of this slide is to showcase the best practices for implementing security operations in an organization. The main steps include performing formal SecOps training, avoiding potential pitfalls and offering practical SecOps tools. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
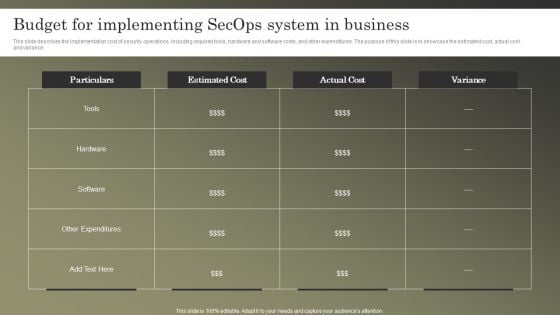
Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF
This slide describes the implementation cost of security operations, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Boost your pitch with our creative Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
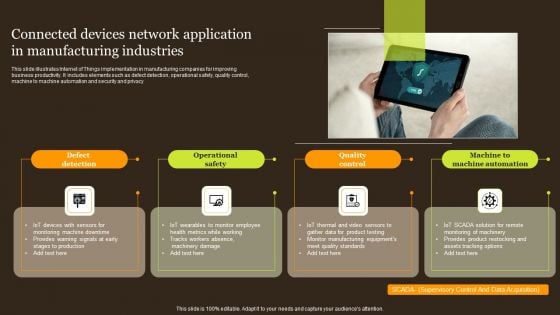
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
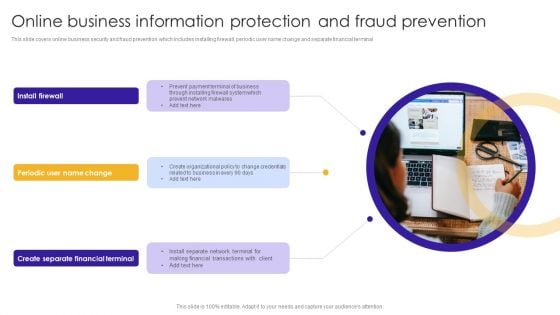
Online Business Information Protection And Fraud Prevention Topics PDF
This slide covers online business security and fraud prevention which includes installing firewall, periodic user name change and separate financial terminal. Persuade your audience using this Online Business Information Protection And Fraud Prevention Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Create Separate, Financial Terminal, Prevent Network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
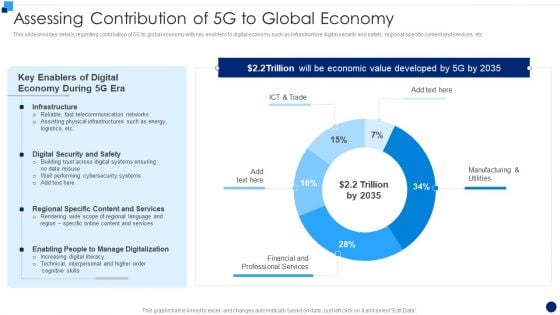
Developing 5G Wireless Cellular Network Assessing Contribution Of 5G To Global Economy Rules PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Developing 5G Wireless Cellular Network Assessing Contribution Of 5G To Global Economy Rules PDF. Use them to share invaluable insights on Telecommunication Networks, Cybersecurity Systems, Content And Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
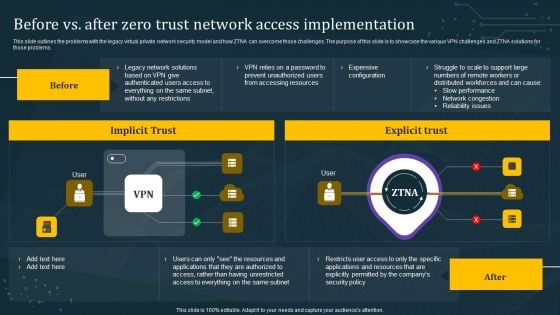
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

1 Network Diagram Showing Disaster Recovery To Remote Location Dr Ppt Slides
This image slide displays network diagram showing disaster recovery to remote locations. This image slide has been designed with graphic of cloud connected to various technology devices and database. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. This image may be used to explain concepts of database recovery through cloud computing. Use this PowerPoint template to express views on cloud computing, networking and security in your presentations. This image slide will enhance the quality of your presentations.
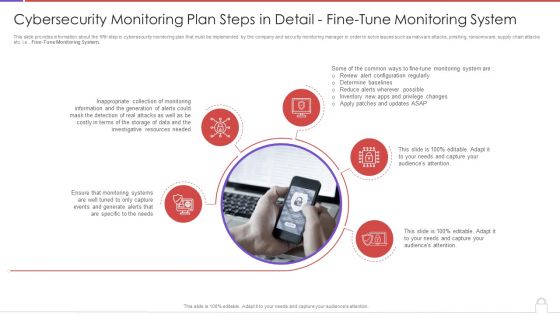
Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System Slides PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine-Tune Monitoring System. Presenting cybersecurity monitoring plan steps in detail fine tune monitoring system slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like inappropriate collection, monitoring information, investigative resources needed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Guidelines PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
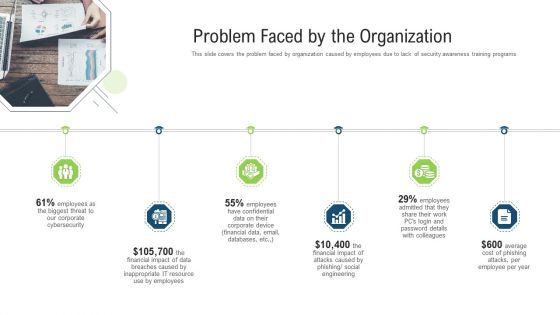
Problem Faced By The Organization Ppt Styles Layouts PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. Presenting problem faced by the organization ppt styles layouts pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like financial impact, email databases, financial data, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
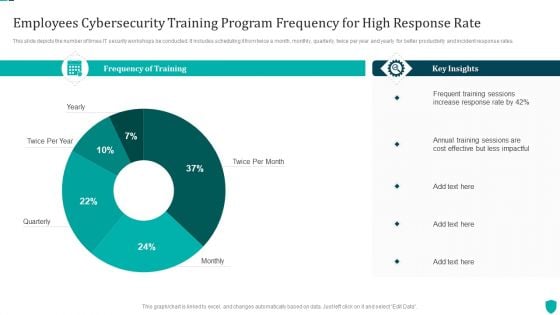
Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF
This slide depicts the number of times IT security workshops be conducted. It includes scheduling it from twice a month, monthly, quarterly, twice per year and yearly for better productivity and incident response rates.Showcasing this set of slides titled Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF. The topics addressed in these templates are Frequency Of Training, Key Insights, Frequent Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF
This slide illustrates impact of security training programs on workforces incident report rate. It includes mass mailed phishing , targeted mails, malware and social media scams.Pitch your topic with ease and precision using this Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF. This layout presents information on Training Sessions, Phishing Identification, Malware Reporting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
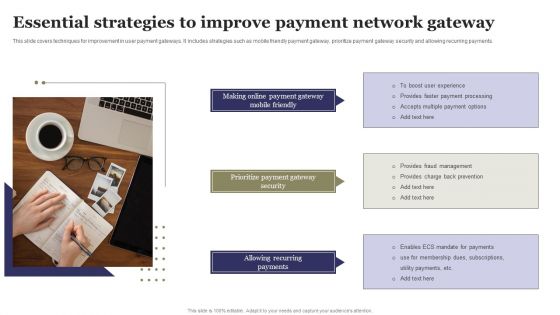
Essential Strategies To Improve Payment Network Gateway Ppt Gallery Background Designs PDF
This slide covers techniques for improvement in user payment gateways. It includes strategies such as mobile friendly payment gateway, prioritize payment gateway security and allowing recurring payments. Presenting Essential Strategies To Improve Payment Network Gateway Ppt Gallery Background Designs PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Making Online, Payment Gateway, Prioritize Payment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
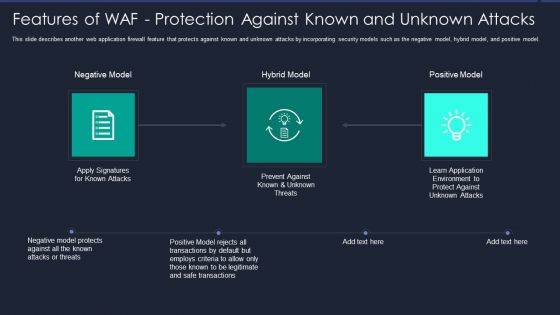
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
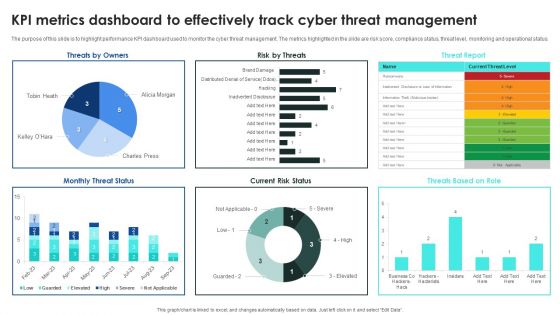
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
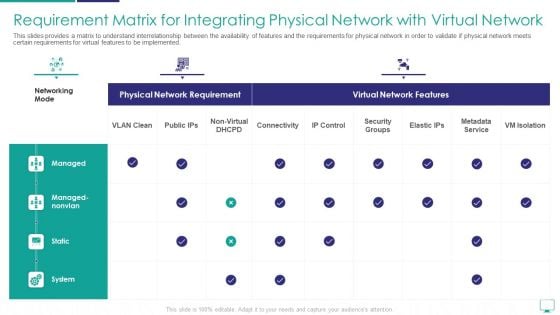
Requirement Matrix For Integrating Physical Network With Virtual Network Sample PDF
This slides provides a matrix to understand interrelationship between the availability of features and the requirements for physical network in order to validate if physical network meets certain requirements for virtual features to be implemented.Deliver an awe inspiring pitch with this creative requirement matrix for integrating physical network with virtual network sample pdf bundle. Topics like metadata service, security groups, managed nonvlan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































