Cyber
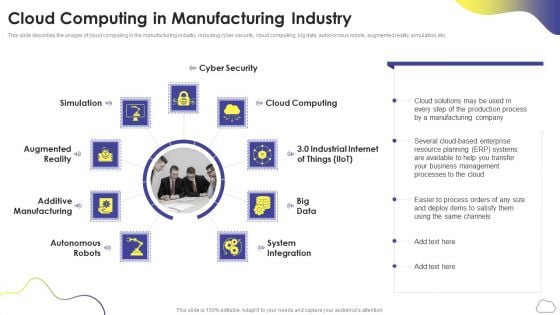
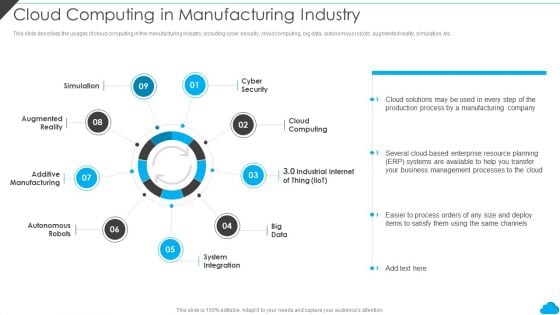
Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. Presenting Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cyber Security, Cloud Computing, System Integration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
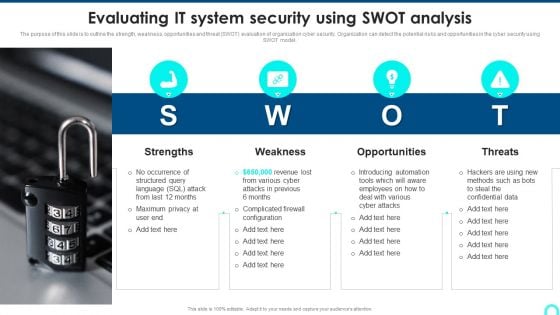
Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
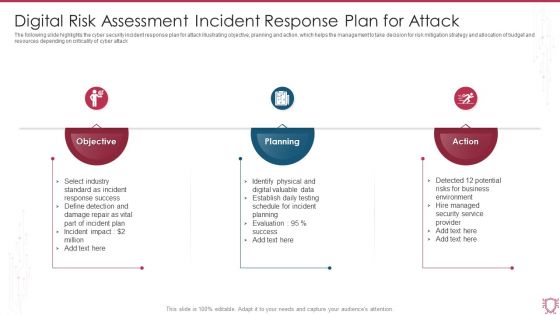
Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
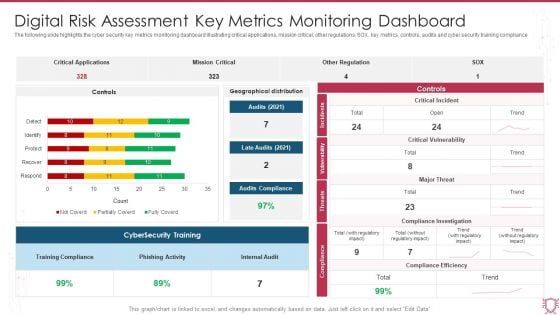
Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF
The following slide highlights the cyber security key metrics monitoring dashboard illustrating critical applications, mission critical, other regulations, SOX, key metrics, controls, audits and cyber security training compliance. Showcasing this set of slides titled Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF. The topics addressed in these templates are Critical Applications, Mission Critical, Other Regulation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
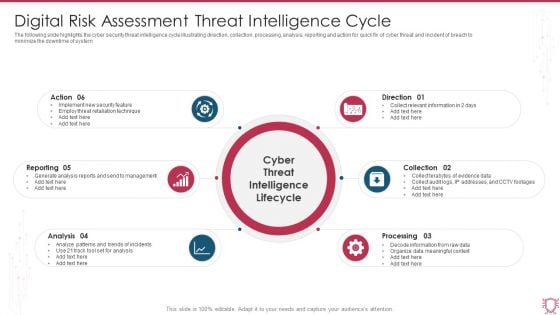
Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
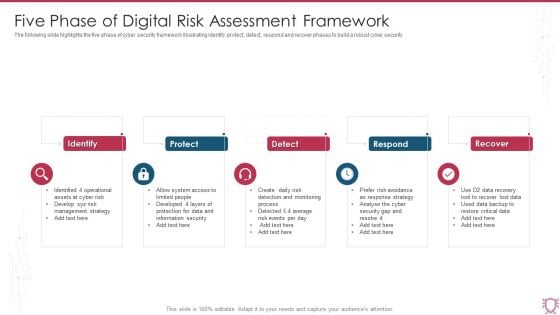
Five Phase Of Digital Risk Assessment Framework Ppt Inspiration Model PDF
The following slide highlights the five phase of cyber security framework illustrating identify, protect, detect, respond and recover phases to build a robust cyber security. Persuade your audience using this Five Phase Of Digital Risk Assessment Framework Ppt Inspiration Model PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Protect, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cloud Distribution Service Models Cloud Computing In Manufacturing Industry Brochure PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. This is a Cloud Distribution Service Models Cloud Computing In Manufacturing Industry Brochure PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Additive Manufacturing, Augmented Reality, Cyber Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF
The following slide showcases various courses associated with cyber security training to aware workforce with latest security threats. It includes elements such as course name, features, cost, duration etc. Presenting Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Introduction To Cybersecurity, Cyber Online, IT And Cybersecurity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Projected Budget For IT Project Management Summary PDF
This slide shows the comparison between actual and projected budget for information technology improvement plan. It includes various costs such as hardware and software cost, cyber security, antivirus, etc. Presenting Projected Budget For IT Project Management Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Software Cost, Hardware Cost, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
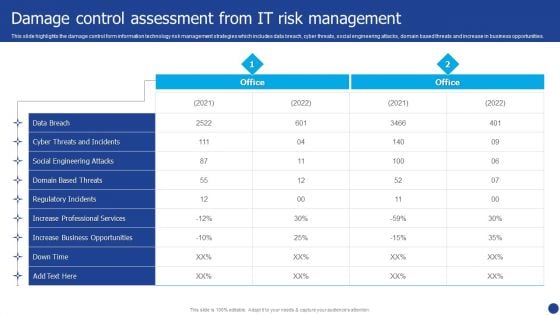
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
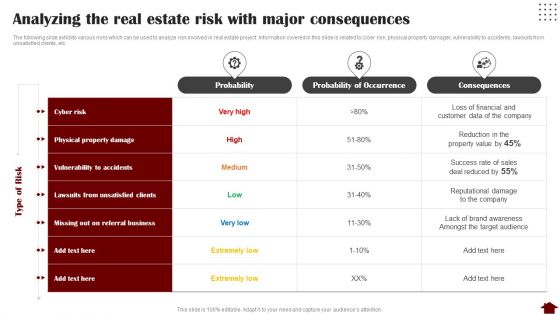
Analyzing The Real Estate Risk With Major Consequences Graphics PDF
The following slide exhibits various risks which can be used to analyze risk involved in real estate project. Information covered in this slide is related to cyber risk, physical property damager, vulnerability to accidents, lawsuits from unsatisfied clients, etc. Deliver an awe inspiring pitch with this creative Analyzing The Real Estate Risk With Major Consequences Graphics PDF bundle. Topics like Cyber Risk, Referral Business, Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
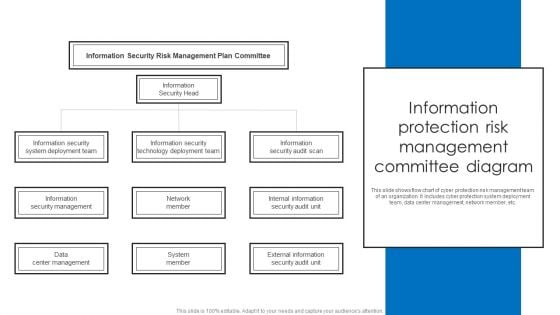
Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
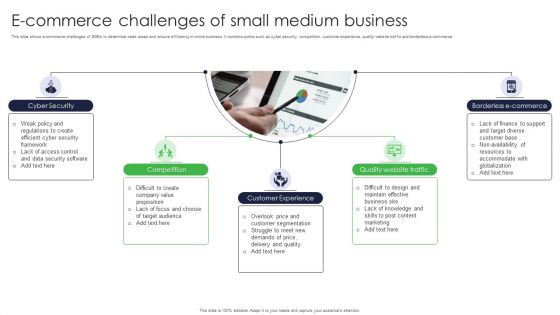
E Commerce Challenges Of Small Medium Business Ppt Infographic Template Inspiration PDF
This slide shows e-commerce challenges of SMEs to determine weak areas and ensure efficiency in online business. It contains points such as cyber security, competition, customer experience, quality website traffic and borderless e-commerce. Persuade your audience using this E Commerce Challenges Of Small Medium Business Ppt Infographic Template Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Customer Experience, Quality Website Traffic. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
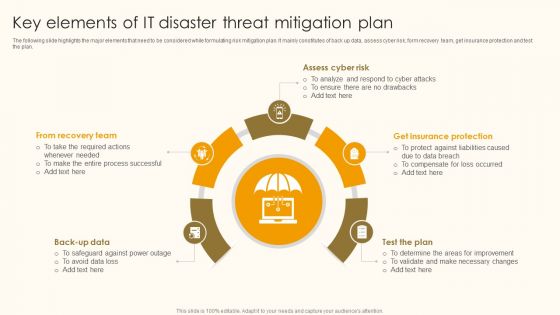
Key Elements Of IT Disaster Threat Mitigation Plan Ppt Show Files PDF
The following slide highlights the major elements that need to be considered while formulating risk mitigation plan. It mainly constitutes of back up data, assess cyber risk, form recovery team, get insurance protection and test the plan. Persuade your audience using this Key Elements Of IT Disaster Threat Mitigation Plan Ppt Show Files PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including From Recovery Team, Assess Cyber Risk, Get Insurance Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
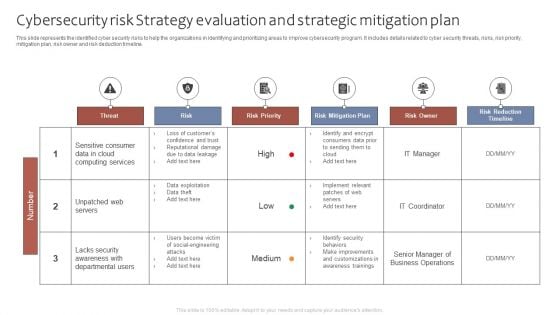
Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF
This slide represents the identified cyber security risks to help the organizations in identifying and prioritizing areas to improve cybersecurity program. It includes details related to cyber security threats, risks, risk priority, mitigation plan, risk owner and risk deduction timeline. Showcasing this set of slides titled Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF. The topics addressed in these templates are Threat, Risk, Risk Priority, Risk Mitigation Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Production Supply Chain Risk Management Strategies Professional PDF
This slide shows the three strategies to manage the supply chain management risks faced by the manufacturing industry. It includes three supply chain risk management strategies such as manage environmental risks, improve cyber supply chain risk management and track right freight carrier metrics. Pitch your topic with ease and precision using this Production Supply Chain Risk Management Strategies Professional PDF. This layout presents information on Manage Environmental Risks, Improve Cyber Supply, Chain Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
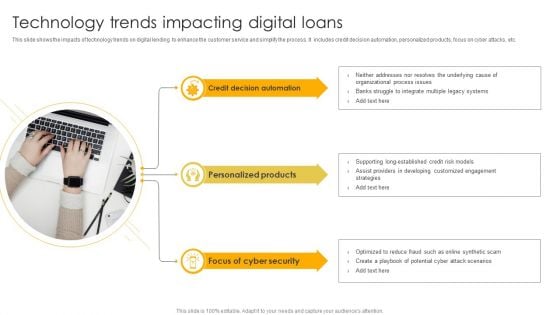
Technology Trends Impacting Digital Loans Ppt Summary Model PDF
This slide shows the impacts of technology trends on digital lending to enhance the customer service and simplify the process. It includes credit decision automation, personalized products, focus on cyber attacks, etc. Persuade your audience using this Technology Trends Impacting Digital Loans Ppt Summary Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Credit Decision Automation, Personalized Products, Focus Cyber Security . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
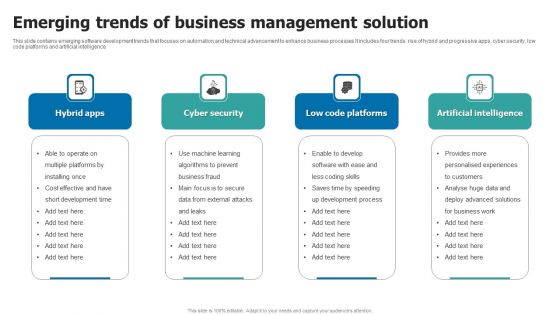
Emerging Trends Of Business Management Solution Template PDF
This slide contains emerging software development trends that focuses on automation and technical advancement to enhance business processes It includes four trends rise of hybrid and progressive apps, cyber security, low code platforms and artificial intelligence. Persuade your audience using this Emerging Trends Of Business Management Solution Template PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Hybrid Apps, Cyber Security, Low Code Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
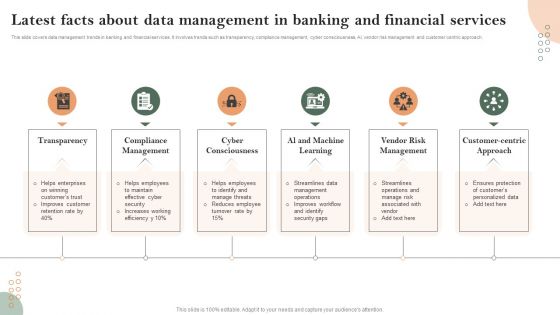
Latest Facts About Data Management In Banking And Financial Services Formats PDF
This slide covers data management trends in banking and financial services. It involves trends such as transparency, compliance management, cyber consciousness, AI, vendor risk management and customer centric approach. Persuade your audience using this Latest Facts About Data Management In Banking And Financial Services Formats PDF. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Compliance Management, Cyber Consciousness, Vendor Risk Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
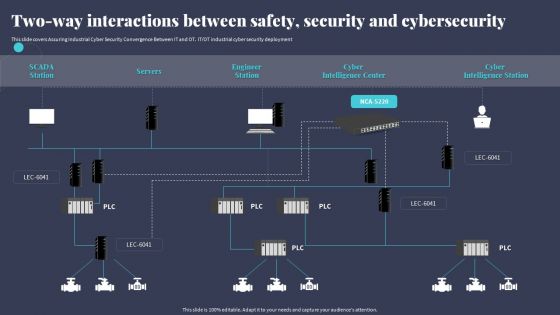
Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. ITOT industrial cyber security deployment. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
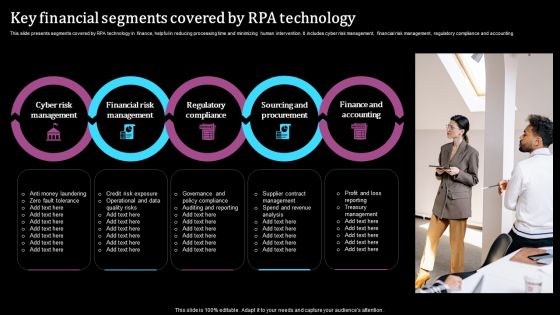
Key Financial Segments Covered By RPA Technology Pictures PDF
This slide presents segments covered by RPA technology in finance, helpful in reducing processing time and minimizing human intervention. It includes cyber risk management, financial risk management, regulatory compliance and accounting. Presenting Key Financial Segments Covered By RPA Technology Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Cyber Risk Management, Regulatory Compliance, Finance And Accounting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
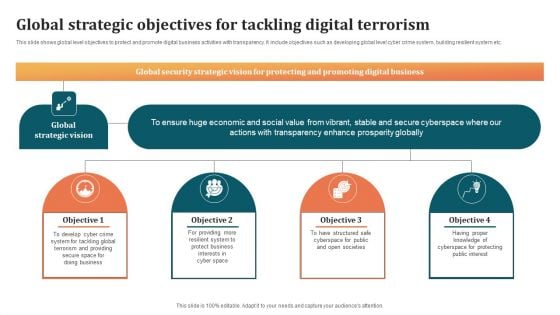
Global Strategic Objectives For Tackling Digital Terrorism Structure PDF
This slide shows global level objectives to protect and promote digital business activities with transparency. It include objectives such as developing global level cyber crime system, building resilient system etc. Presenting Global Strategic Objectives For Tackling Digital Terrorism Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Cyber Crime System, Global, Economic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
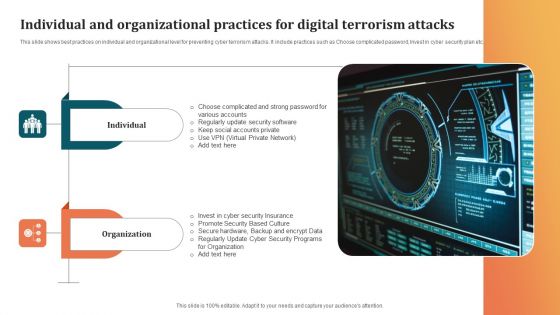
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
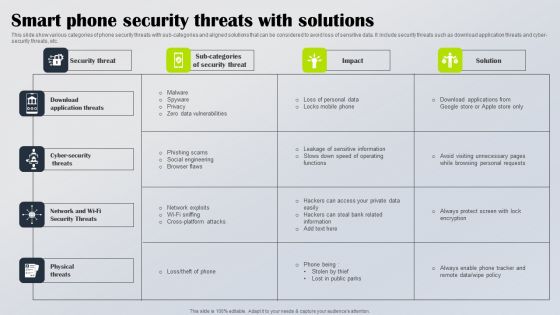
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
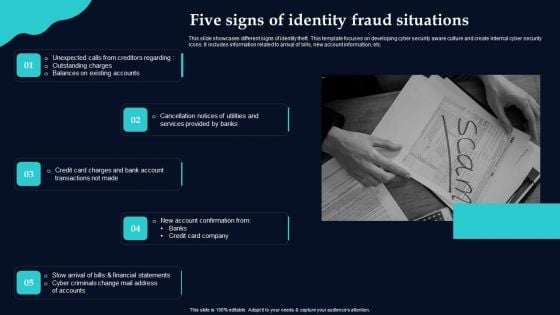
Five Signs Of Identity Fraud Situations Brochure PDF
This slide showcases different signs of identity theft. This template focuses on developing cyber security aware culture and create internal cyber security icons. It includes information related to arrival of bills, new account information, etc. Presenting Five Signs Of Identity Fraud Situations Brochure PDF to dispense important information. This template comprises yyyyyyyyyyyyyyyyyyyyyy stages. It also presents valuable insights into the topics including Unexpected Calls, Cancellation Notices Utilities, Credit Card Charges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Store Management Challenges With Solutions Demonstration PDF
This slide showcase challenges faced by shop owner in management of online ecommerce store along with its solutions. It includes elements such as cyber and data security, online identity verification, customer loyalty and shipping cost. Showcasing this set of slides titled Digital Store Management Challenges With Solutions Demonstration PDF. The topics addressed in these templates are Cyber Data Security, Online Identity Verification, Customer Loyalty. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
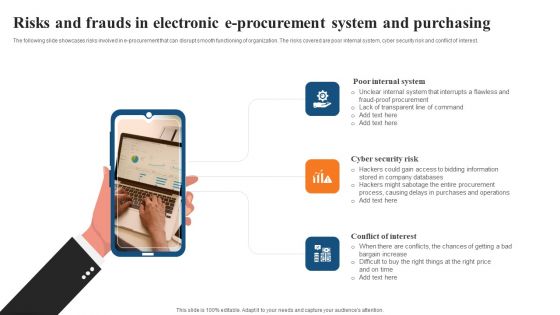
Risks And Frauds In Electronic E Procurement System And Purchasing Designs PDF

Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
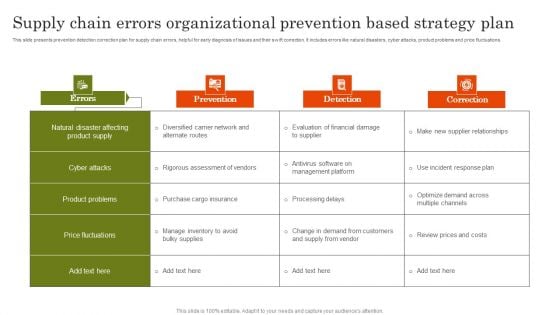
Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF
This slide presents prevention detection correction plan for supply chain errors, helpful for early diagnosis of issues and their swift correction. It includes errors like natural disasters, cyber attacks, product problems and price fluctuations. Present the topic in a bit more detail with this Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF. Use it as a tool for discussion and navigation on Cyber Attacks, Product Problems, Price Fluctuations. This template is free to edit as deemed fit for your organization. Therefore download it now.
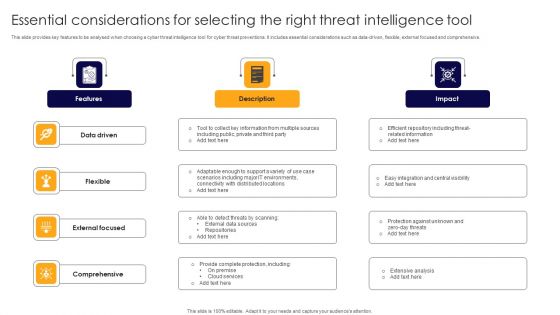
Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF
This slide provides key features to be analysed when choosing a cyber threat intelligence tool for cyber threat preventions. It includes essential considerations such as data-driven, flexible, external focused and comprehensive. Presenting Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Driven, Flexible, External Focused. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
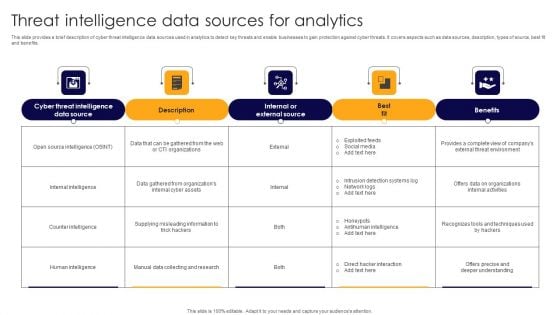
Threat Intelligence Data Sources For Analytics Ideas PDF
This slide provides a brief description of cyber threat intelligence data sources used in analytics to detect key threats and enable businesses to gain protection against cyber threats. It covers aspects such as data sources, description, types of source, best fit and benefits. Showcasing this set of slides titled Threat Intelligence Data Sources For Analytics Ideas PDF. The topics addressed in these templates are Exploited Feeds, Social Media, Intrusion Detection Systems Log. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
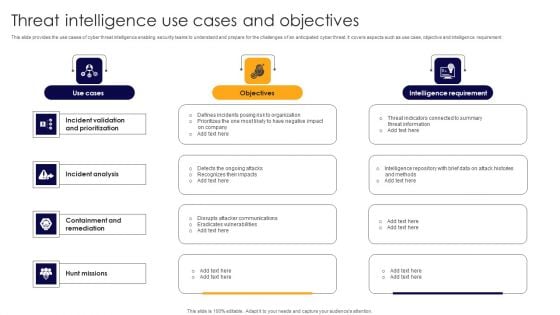
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
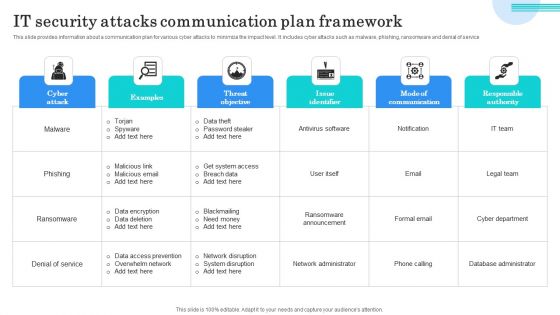
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
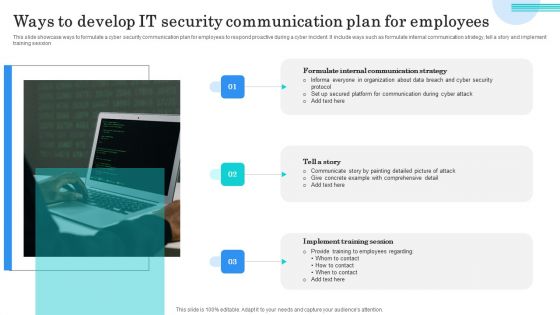
Ways To Develop IT Security Communication Plan For Employees Elements PDF
This slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting Ways To Develop IT Security Communication Plan For Employees Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Formulate Internal Communication, Tell Story, Implement Training Session. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Online Risk Management Graphics PDF
The purpose of this slide is to represent digital risk areas and solutions for effective risk management. It includes various risks such as mitigating cyber risk attack, managing third party, handling dynamic workforce, securing cloud migration etc. Presenting Best Practices For Online Risk Management Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigating Cyber Risk Attack, Managing Third Party, Handling Dynamic Workforce. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf
Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences. There are so many reasons you need a Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences.

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.
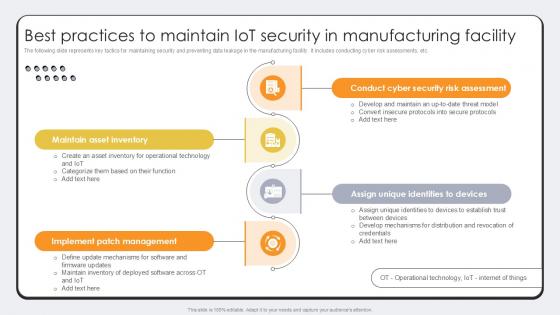
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
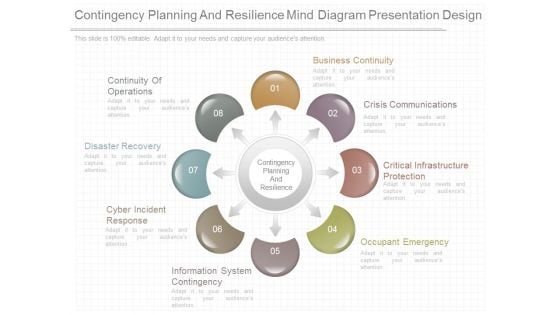
Contingency Planning And Resilience Mind Diagram Presentation Design
This is a contingency planning and resilience mind diagram presentation design. This is a eight stage process. The stages in this process are contingency planning and resilience, business continuity, crisis communications, critical infrastructure protection, occupant emergency, information system contingency, cyber incident response, disaster recovery, continuity of operations.
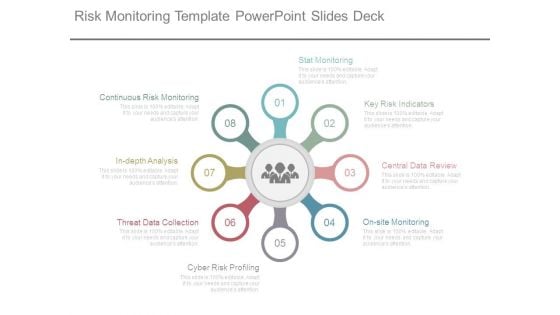
Risk Monitoring Template Powerpoint Slides Deck
This is a risk monitoring template powerpoint slides deck. This is a eight stage process. The stages in this process are stat monitoring, key risk indicators, central data review, on site monitoring, cyber risk profiling, threat data collection, in depth analysis, continuous risk monitoring.
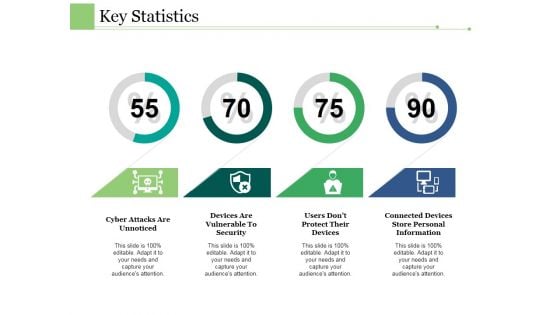
Key Statistics Ppt PowerPoint Presentation Show Sample
This is a key statistics ppt powerpoint presentation show sample. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users do not protect their devices, connected devices store personal information.
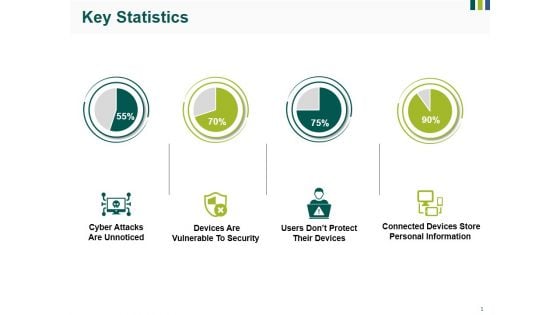
Key Statistics Ppt PowerPoint Presentation Gallery Format Ideas
This is a key statistics ppt powerpoint presentation gallery format ideas. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users dont protect their devices, connected devices store personal information.

Email Security Market Research Report Ppt PowerPoint Presentation Complete Deck With Slides

Global Cloud Based Email Security Market Ppt PowerPoint Presentation Complete Deck With Slides

Tech Support Services Cost And Pricing Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name tech support services cost and pricing ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are monitoring, cyber security, infrastructure, implementing, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
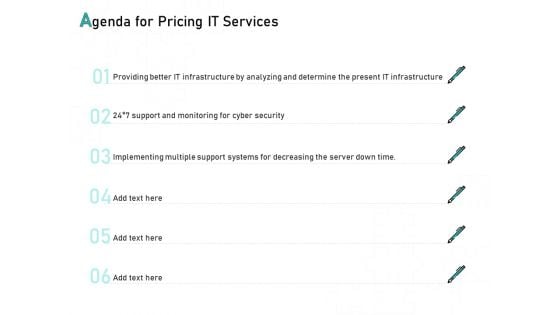
Tech Support Services Cost And Pricing Agenda For Pricing IT Services Ppt PowerPoint Presentation Summary Diagrams
Presenting this set of slides with name tech support services cost and pricing agenda for pricing it services ppt powerpoint presentation summary diagrams. The topics discussed in these slides are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Tech Support Services Cost And Pricing Effect After Implementing IT Services Ppt PowerPoint Presentation Summary Background
Presenting this set of slides with name tech support services cost and pricing effect after implementing it services ppt powerpoint presentation summary background. The topics discussed in these slides are cyber security, infrastructure, technological, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































