Cyber
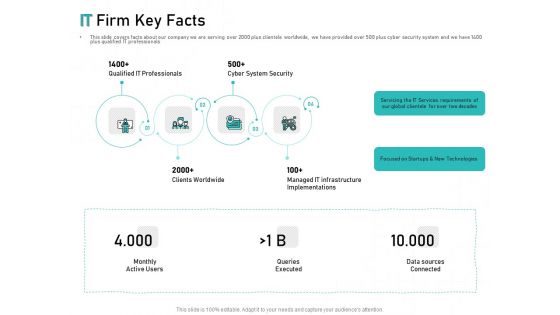
Tech Support Services Cost And Pricing IT Firm Key Facts Ppt PowerPoint Presentation Slides File Formats
Presenting this set of slides with name tech support services cost and pricing it firm key facts ppt powerpoint presentation slides file formats. This is a four stage process. The stages in this process are technologies, services, implementations, infrastructure, cyber system security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
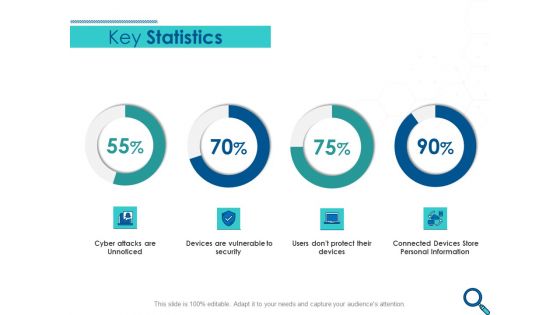
Evaluating Competitive Marketing Effectiveness Key Statistics Ppt Portfolio Ideas PDF
Presenting this set of slides with name evaluating competitive marketing effectiveness key statistics ppt portfolio ideas pdf. The topics discussed in these slides are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Managed Services Pricing Guide IT Firm Key Facts Ppt Infographics Visuals PDF
Presenting this set of slides with name cloud managed services pricing guide it firm key facts ppt infographics visuals pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Managed Services Pricing Guide Agenda For Managed Services Pricing Guidelines Ppt Infographics Background PDF
Presenting this set of slides with name cloud managed services pricing guide agenda for managed services pricing guidelines ppt infographics background pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
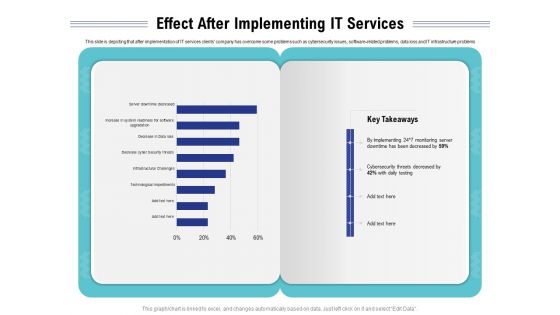
Cloud Managed Services Pricing Guide Effect After Implementing IT Services Ppt Styles Mockup PDF
Presenting this set of slides with name cloud managed services pricing guide effect after implementing it services ppt styles mockup pdf. The topics discussed in these slides are technological, cyber security, implementing, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
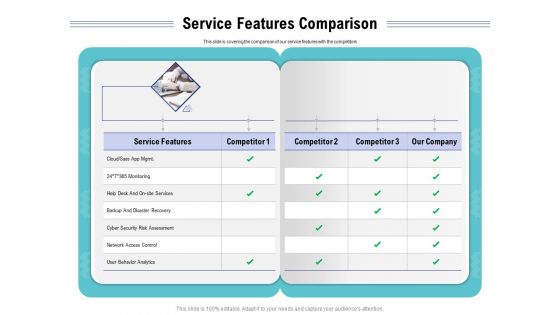
Cloud Managed Services Pricing Guide Service Features Comparison Ppt Gallery Infographic Template PDF
Presenting this set of slides with name cloud managed services pricing guide service features comparison ppt gallery infographic template pdf. This is a three stage process. The stages in this process are service, cyber security, analytics, monitoring, disaster recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
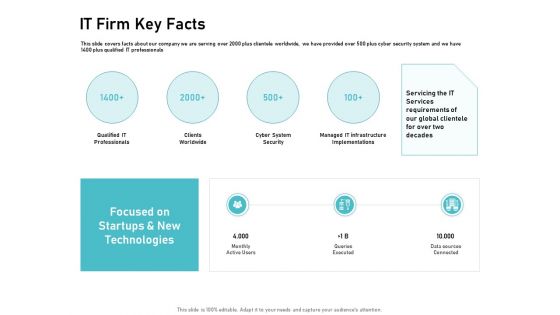
IT Support And Monitoring Services Pricing IT Firm Key Facts Ppt Portfolio Styles PDF
Presenting this set of slides with name it support and monitoring services pricing it firm key facts ppt portfolio styles pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
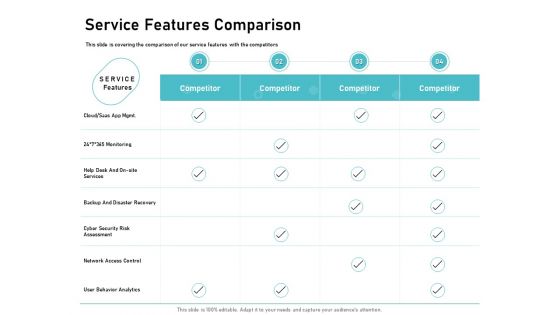
IT Support And Monitoring Services Pricing Service Features Comparison Guidelines PDF
Presenting this set of slides with name it support and monitoring services pricing service features comparison guidelines pdf. The topics discussed in these slides are monitoring, analytics, network, cyber security, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Support And Monitoring Services Pricing Agenda For IT Support And Monitoring Services Pricing Elements PDF
Presenting this set of slides with name it support and monitoring services pricing agenda for it support and monitoring services pricing elements pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
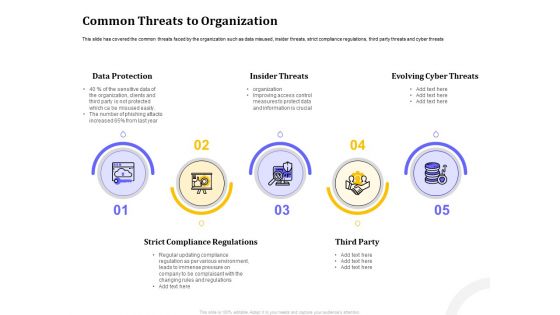
Managing Work Relations In Business Common Threats To Organization Ppt Styles Graphics Example PDF
Presenting this set of slides with name managing work relations in business common threats to organization ppt styles graphics example pdf. This is a five stage process. The stages in this process are data protection, insider threats, evolving cyber threats, strict compliance regulations, third party. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
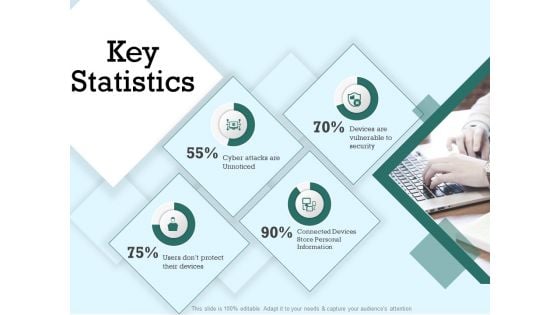
Survey Analysis Gain Marketing Insights Key Statistics Sample PDF
Presenting this set of slides with name survey analysis gain marketing insights key statistics sample pdf. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Welfare Work Value Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name welfare work value ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are infrastructure, analyzing, cyber security, implementing, service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Welfare Work Value IT Firm Key Facts Ppt Pictures Icon PDF
Presenting this set of slides with name welfare work value it firm key facts ppt pictures icon pdf. This is a four stage process. The stages in this process are clients worldwide, cyber system security, infrastructure, implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Welfare Work Value Agenda For Welfare Work Value Ppt Professional Show PDF
Presenting this set of slides with name welfare work value agenda for welfare work value ppt professional show pdf. This is a six stage process. The stages in this process are analyzing, infrastructure, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
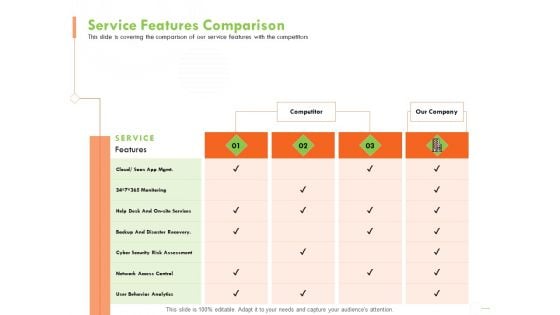
Welfare Work Value Service Features Comparison Ppt Outline Themes PDF
Presenting this set of slides with name welfare work value service features comparison ppt outline themes pdf. The topics discussed in these slides are monitoring, services, cyber security, analytics, network access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
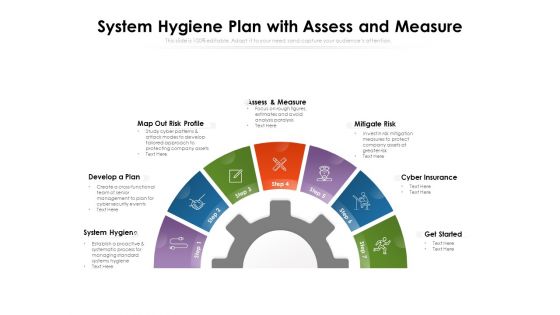
System Hygiene Plan With Assess And Measure Ppt PowerPoint Presentation File Graphics PDF
Presenting this set of slides with name system hygiene plan with assess and measure ppt powerpoint presentation file graphics pdf. This is a seven stage process. The stages in this process are develop, plan, cyber insurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
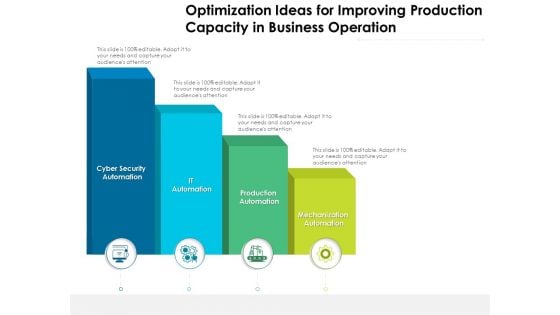
Optimization Ideas For Improving Production Capacity In Business Operation Ppt PowerPoint Presentation Outline Visual Aids PDF
Presenting this set of slides with name optimization ideas for improving production capacity in business operation ppt powerpoint presentation outline visual aids pdf. This is a four stage process. The stages in this process are mechanization automation, production automation, it automation, cyber security automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
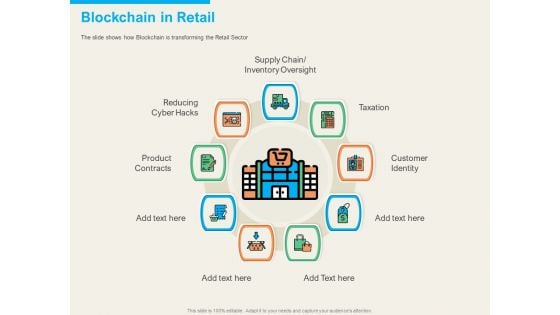
Understanding Blockchain Basics Use Cases Blockchain In Retail Ppt Inspiration Background Designs PDF
Presenting this set of slides with name understanding blockchain basics use cases blockchain in retail ppt inspiration background designs pdf. This is a nine stage process. The stages in this process are taxation, customer identity, product contracts, reducing cyber hacks, supply chain or inventory oversight. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Mechanization Symbol Technology Growth Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name mechanization symbol technology growth ppt powerpoint presentation complete deck. The topics discussed in these slides are technology, growth, data storage, communication, cyber brain. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
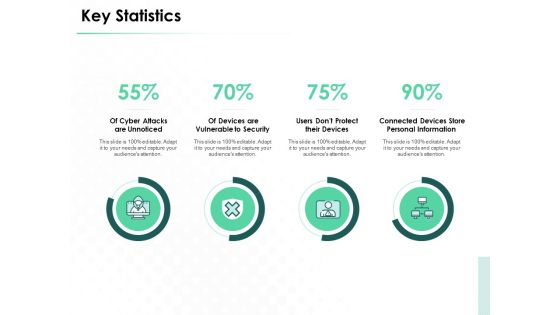
Market Approach To Business Valuation Key Statistics Summary PDF
Presenting this set of slides with name market approach to business valuation key statistics summary pdf. This is a four stage process. The stages in this process are cyber attacks unnoticed, devices vulnerable security, users dont protect devices, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
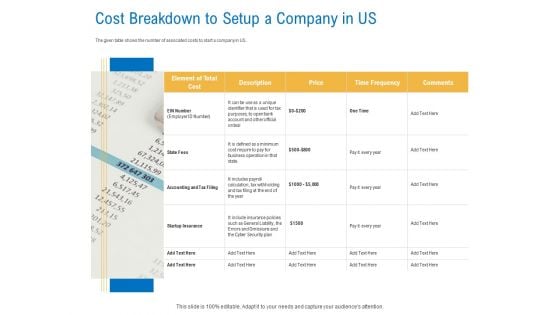
Digital Businesses Ecosystems Cost Breakdown To Setup A Company In Us Professional PDF
Deliver an awe inspiring pitch with this creative digital businesses ecosystems cost breakdown to setup a company in us professional pdf bundle. Topics like cyber security, plan, business, cost, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agile Best Practices For Effective Team Project Scope Management Plan For Agile Implementation Pictures PDF
Deliver an awe inspiring pitch with this creative agile best practices for effective team project scope management plan for agile implementation pictures pdf bundle. Topics like team communication, cyber security, budget, measurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Evaluation Results Showing Bank Risk Ppt PowerPoint Presentation File Influencers PDF
Presenting evaluation results showing bank risk ppt powerpoint presentation file influencers pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including cyber security, perform, legal audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Different Methods Of Blockchain Technology In Banking Ppt PowerPoint Presentation Gallery Icon PDF
Presenting different methods of blockchain technology in banking ppt powerpoint presentation gallery icon pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including management, cost effective, cyber crime reduction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
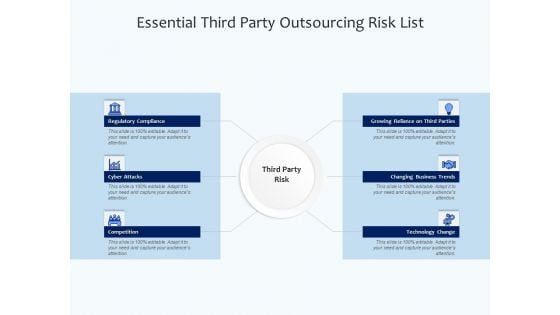
Essential Third Party Outsourcing Risk List Ppt PowerPoint Presentation File Sample PDF
Presenting essential third party outsourcing risk list ppt powerpoint presentation file sample pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including regulatory compliance, cyber attacks, competition, changing business trends, technology change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Incident Response Planning And Reporting Chart With Primary Skills Ppt PowerPoint Presentation Icon Ideas PDF
Pitch your topic with ease and precision using this incident response planning and reporting chart with primary skills ppt powerpoint presentation icon ideas pdf. This layout presents information on management, technical, cyber security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Incident Response Planning And Reporting Matrix With Activities Ppt PowerPoint Presentation Gallery Slide Download PDF
Pitch your topic with ease and precision using this incident response planning and reporting matrix with activities ppt powerpoint presentation gallery slide download pdf. This layout presents information on cyber security, technical, accountable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
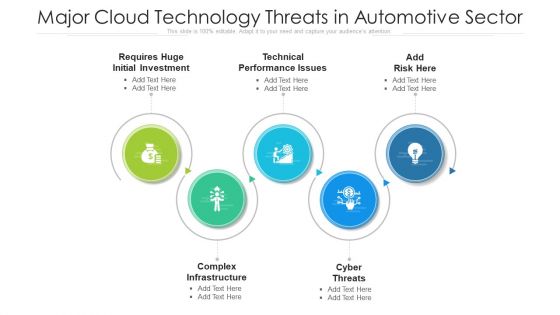
Major Cloud Technology Threats In Automotive Sector Ppt PowerPoint Presentation Gallery Templates PDF
Presenting major cloud technology threats in automotive sector ppt powerpoint presentation gallery templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including technical performance issues, complex infrastructure, cyber threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
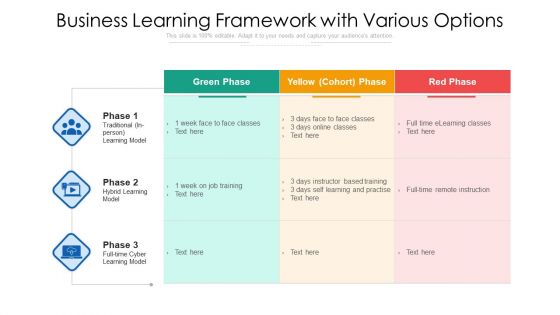
Business Learning Framework With Various Options Ppt PowerPoint Presentation Gallery Graphics Template PDF
Showcasing this set of slides titled business learning framework with various options ppt powerpoint presentation gallery graphics template pdf. The topics addressed in these templates are traditional learning model, hybrid learning model, full time cyber learning model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Threat Analysis Plan With Agents And Tactics Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled internet security threat analysis plan with agents and tactics ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are corporations, hacktivists, cyber fighters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
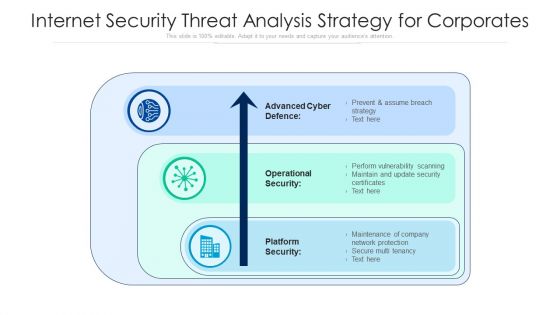
Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
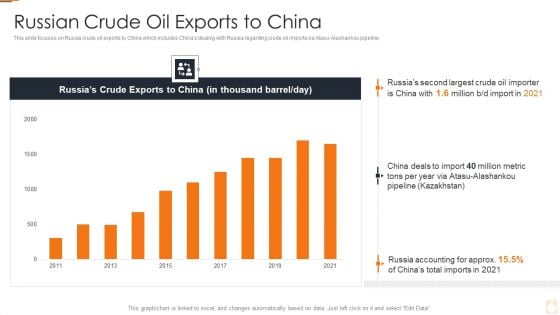
Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF
Deliver an awe inspiring pitch with this creative Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF bundle. Topics like Higher Energy Prices, Trade And Supply Chains, Increase In Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
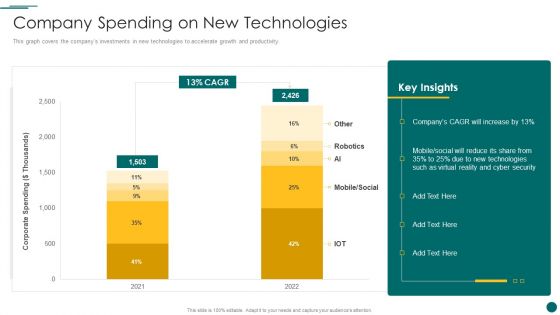
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF. Use them to share invaluable insights on Cyber Security, Globally, Measurement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf today and make your presentation stand out from the rest. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.
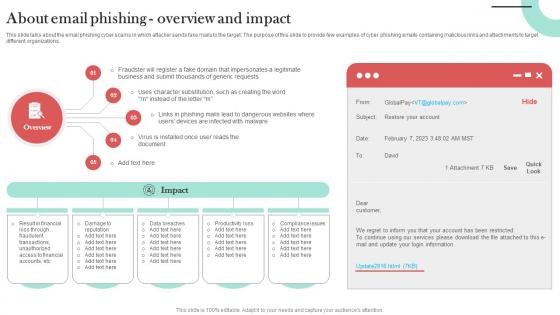
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations.

About Spear Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Spear Phishing Overview And Example Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Spear Phishing Overview And Example Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks.

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices.
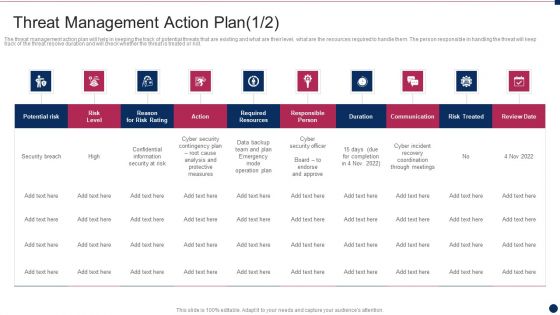
Threat Management At Workplace Threat Management Action Plan Responsible Person Template PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
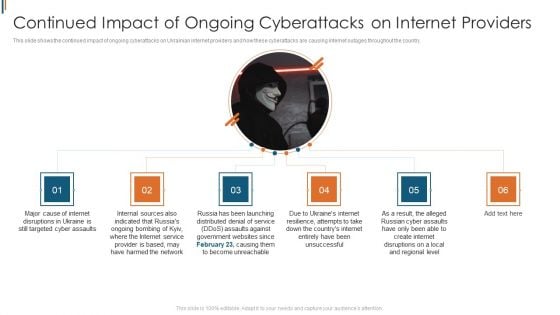
Ukraine Cyberwarfare Continued Impact Of Ongoing Cyberattacks On Internet Providers Elements Pdf
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. Presenting ukraine cyberwarfare continued impact of ongoing cyberattacks on internet providers elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like major cause of internet disruptions in ukraine is still targeted cyber assaults, as a result, the alleged russian cyber assaults have only been able to create internet disruptions on a local and regional level, internal sources also indicated that russias ongoing bombing of kyiv. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
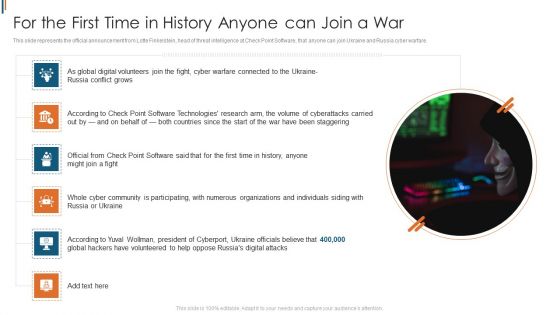
Ukraine Cyberwarfare For The First Time In History Anyone Can Join A War Mockup Pdf
This slide represents the official announcement from Lotte Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare. This is a ukraine cyberwarfare for the first time in history anyone can join a war mockup pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like as global digital volunteers join the fight, cyber warfare connected to the ukraine russia conflict grows, official from check point software said that for the first time in history, anyone might join a fight. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
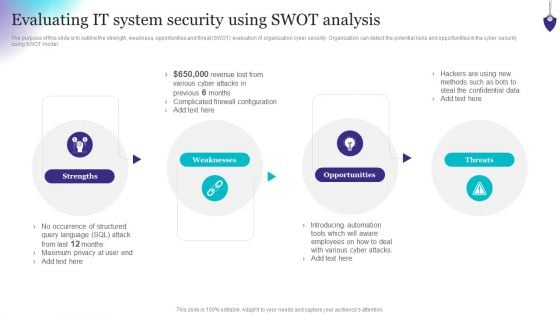
Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Slidegeeks is here to make your presentations a breeze with Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
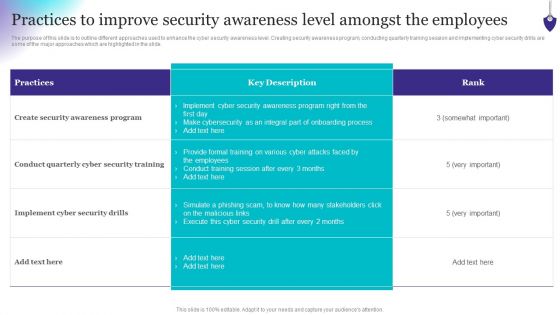
Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. This Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
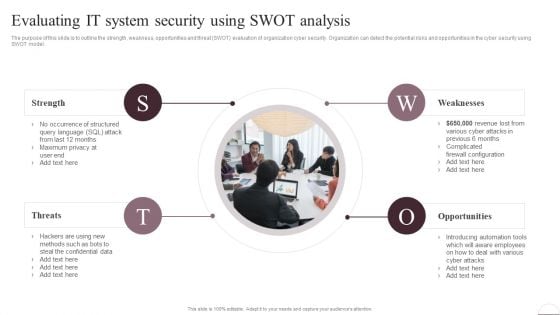
Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest
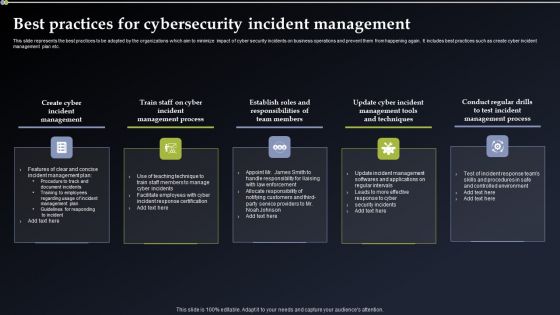
Best Practices For Cybersecurity Incident Management Infographics PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Boost your pitch with our creative Best Practices For Cybersecurity Incident Management Infographics PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
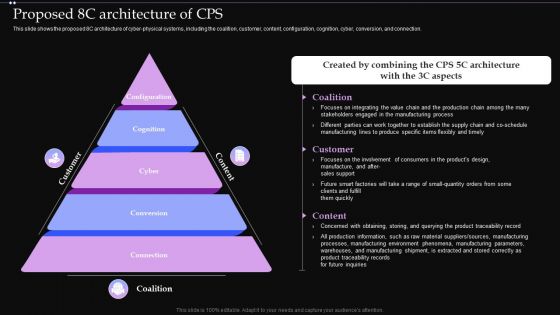
Proposed 8C Architecture Of CPS Ppt PowerPoint Presentation File Example PDF
This slide shows the proposed 8C architecture of cyber physical systems, including the coalition, customer, content, configuration, cognition, cyber, conversion, and connection. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Proposed 8C Architecture Of CPS Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Proposed 8C Architecture Of CPS Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.
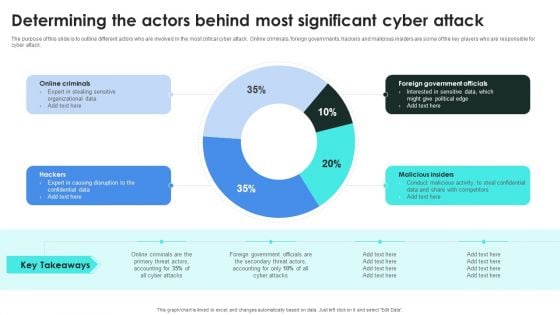
Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.

Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
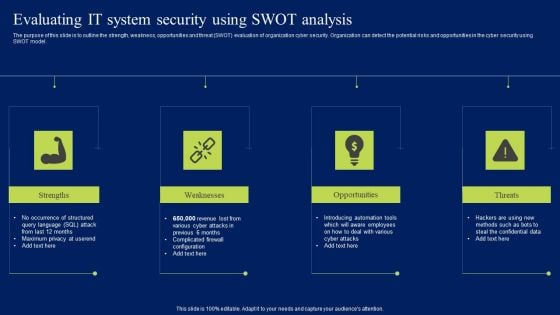
Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
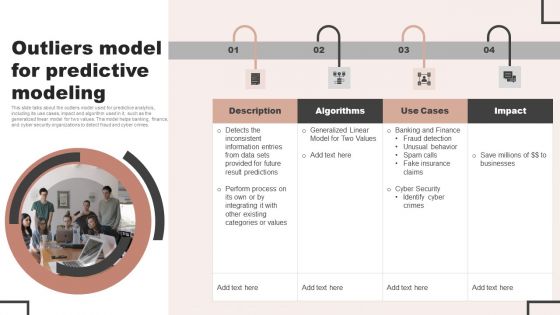
Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
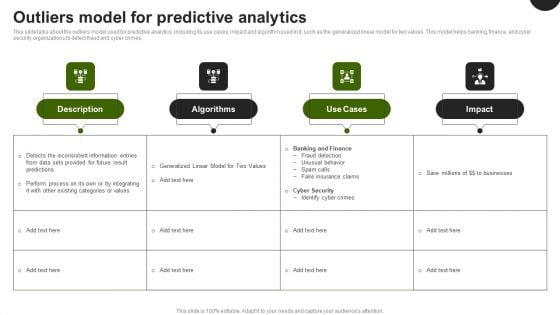
Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Projection Model Outliers Model For Predictive Analytics Topics PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Welcome to our selection of the Projection Model Outliers Model For Predictive Analytics Topics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Best Practices For Cybersecurity Incident Management Summary PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Cybersecurity Incident Management Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Cybersecurity Incident Management Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
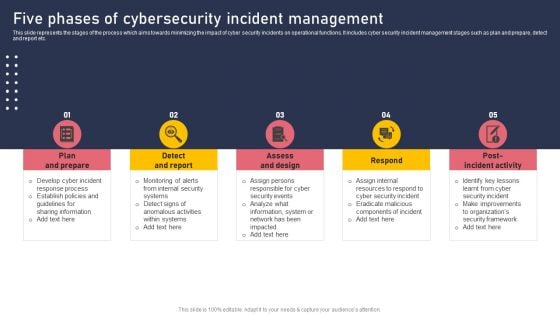
Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.


 Continue with Email
Continue with Email

 Home
Home


































