Cybercrime
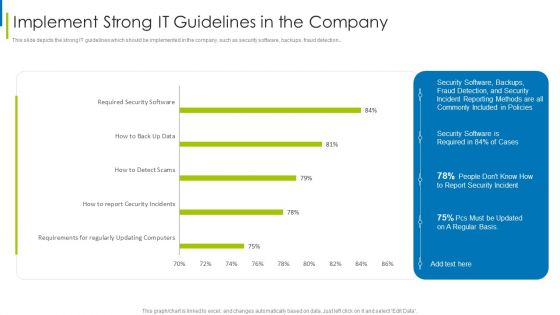
Cyber Terrorism Assault Implement Strong IT Guidelines In The Company Themes PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault implement strong it guidelines in the company themes pdf Use them to share invaluable insights on requirements regularly, updating computers, required security software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
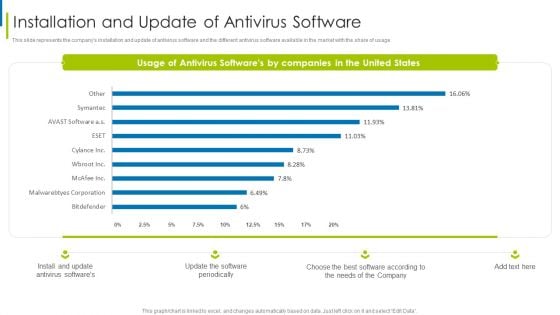
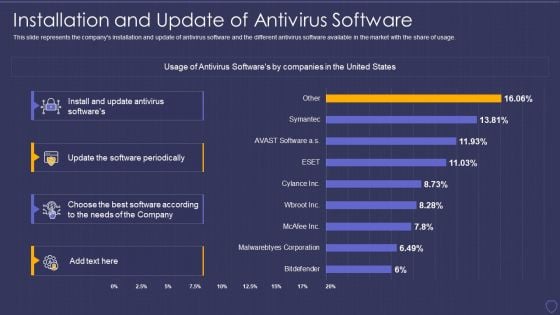
Cyber Terrorism Assault Installation And Update Of Antivirus Software Slides PDF
This slide represents the companys installation and update of antivirus software and the different antivirus software available in the market with the share of usage.Deliver an awe inspiring pitch with this creative cyber terrorism assault installation and update of antivirus software slides pdf bundle. Topics like antivirus softwares, software periodically, softwares by companies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
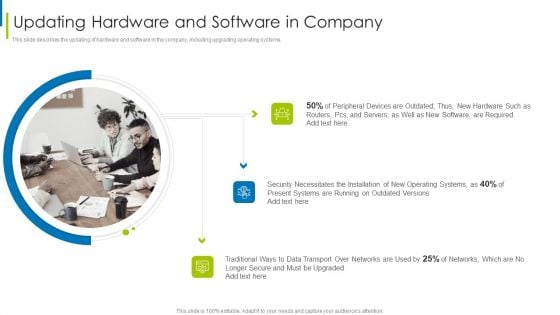
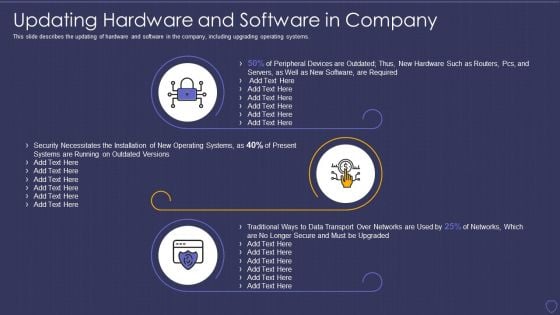
Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
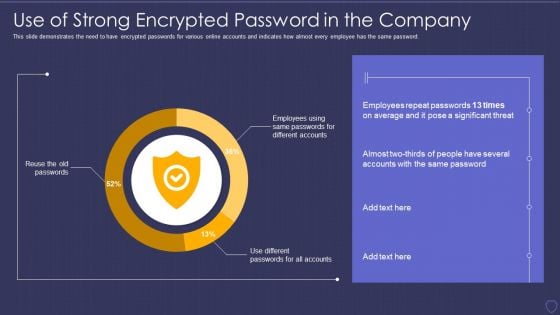
Cyber Terrorism Assault Use Of Strong Encrypted Password In The Company Icons PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault use of strong encrypted password in the company icons pdf Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
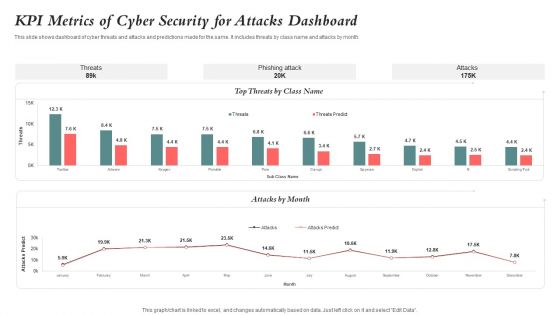
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
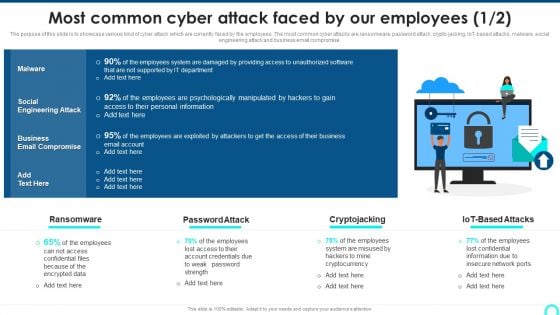
Most Common Cyber Attack Faced By Our Employees Clipart PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. This is a Most Common Cyber Attack Faced By Our Employees Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Psychologically, Personal Information, Psychologically Manipulated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
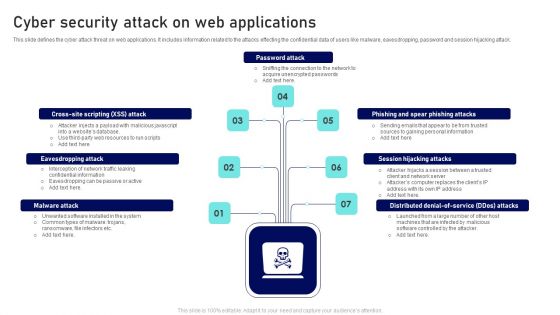
Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Cyber Terrorism Incidents On The Rise IT Ppt PowerPoint Presentation Complete With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This global cyber terrorism incidents on the rise it ppt powerpoint presentation complete with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of seventy five slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Global Cyber Terrorism Incidents On The Rise IT Disaster Recovery Plan For The Business Template PDF
This slide illustrates the elements that will be taken into account when establishing a recovery plan for company to go back to business swiftly and successfully. This is a global cyber terrorism incidents on the rise it disaster recovery plan for the business template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a complete inventory of all assets, make a risk assessment, determine the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
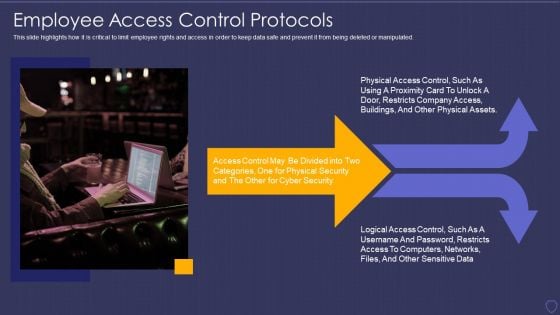
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
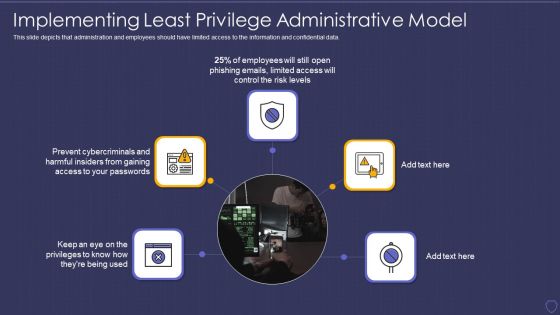
Global Cyber Terrorism Incidents On The Rise IT Implementing Least Privilege Inspiration PDF
This slide depicts that administration and employees should have limited access to the information and confidential data. Presenting global cyber terrorism incidents on the rise it implementing least privilege inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like implementing least privilege administrative model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Global Cyber Terrorism Incidents On The Rise IT Installation And Update Of Antivirus Brochure PDF
This slide represents the companys installation and update of antivirus software and the different antivirus software available in the market with the share of usage. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it installation and update of antivirus brochure pdf. Use them to share invaluable insights on installation and update of antivirus software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Global Cyber Terrorism Incidents On The Rise IT Use Of Strong Encrypted Password Download PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it use of strong encrypted password download pdf. Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
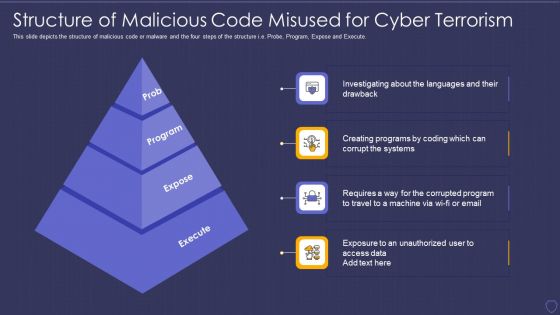
Global Cyber Terrorism Incidents On The Rise IT Structure Of Malicious Diagrams PDF
This slide depicts the structure of malicious code or malware and the four steps of the structure i.e. Probe, Program, Expose and Execute. Presenting global cyber terrorism incidents on the rise it structure of malicious diagrams pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like prob, program, expose, execute. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Global Cyber Terrorism Incidents On The Rise IT Updating Hardware And Software Demonstration PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems. Presenting global cyber terrorism incidents on the rise it updating hardware and software demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like updating hardware and software in company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
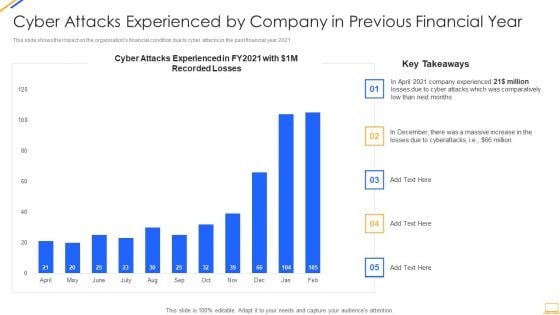
Desktop Security Management Cyber Attacks Experienced By Company Summary PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Deliver and pitch your topic in the best possible manner with this desktop security management cyber attacks experienced by company summary pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Major Statistics Of Cyber Phishing Scams And Attacks Designs PDF
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF from Slidegeeks today.

Ways To Stop Cyber Attacks Ppt PowerPoint Presentation Inspiration Outline
Presenting this set of slides with name ways to stop cyber attacks ppt powerpoint presentation inspiration outline. This is a one stage process. The stage in this process is ways to stop cyber attacks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Risk Icon Indicating Malware Attack Elements PDF
Presenting cyber risk icon indicating malware attack elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber risk icon indicating malware attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Survey Insights On Cyber War Attacks Icons Demonstration PDF
Presenting Survey Insights On Cyber War Attacks Icons Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Survey Insights ,Cyber War, Attacks Icons This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Botnet Attack Cyber Criminal Activity Icon Ideas PDF
Showcasing this set of slides titled Botnet Attack Cyber Criminal Activity Icon Ideas PDF. The topics addressed in these templates are Botnet Attack Cyber, Criminal Activity Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon For Minimizing Online Risk And Cyber Attacks Mockup PDF
Presenting Icon For Minimizing Online Risk And Cyber Attacks Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon Minimizing, Online Risk, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
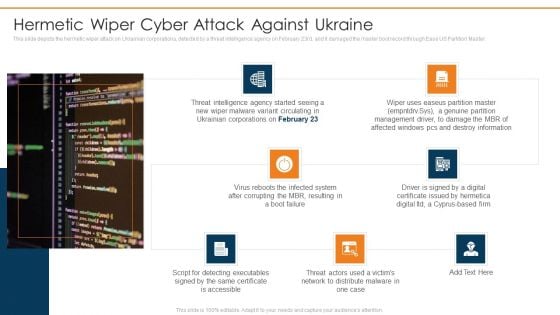
Data Wiper Spyware Attack Hermetic Wiper Cyber Attack Against Ukraine Slides PDF
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Ease US Partition Master.Deliver an awe inspiring pitch with this creative data wiper spyware attack hermetic wiper cyber attack against ukraine slides pdf bundle. Topics like hermetic wiper cyber attack against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
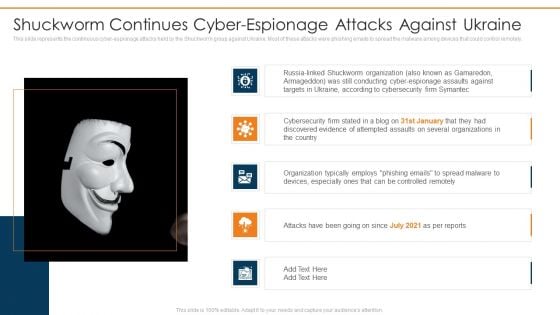
Data Wiper Spyware Attack Shuckworm Continues Cyber Espionage Attacks Against Ukraine Diagrams PDF
This slide represents the continuous cyber-espionage attacks held by the Shuckworm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely.Deliver an awe inspiring pitch with this creative data wiper spyware attack shuckworm continues cyber espionage attacks against ukraine diagrams pdf bundle. Topics like shuckworm continues cyber espionage attacks against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
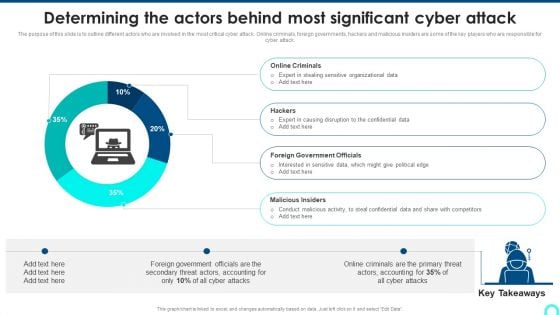
Determining The Actors Behind Most Significant Cyber Attack Download PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver and pitch your topic in the best possible manner with this Determining The Actors Behind Most Significant Cyber Attack Download PDF. Use them to share invaluable insights on Online Criminals, Causing Disruption, Government Officials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
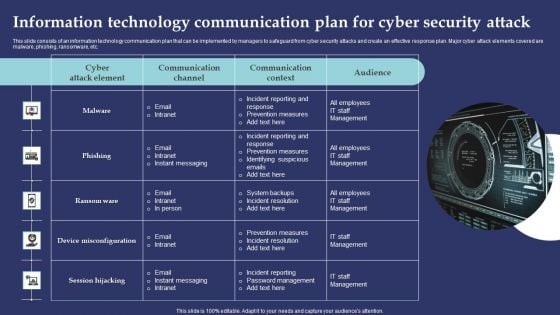
Information Technology Communication Plan For Cyber Security Attack Summary PDF
This slide consists of an information technology communication plan that can be implemented by managers to safeguard from cyber security attacks and create an effective response plan. Major cyber attack elements covered are malware, phishing, ransomware, etc. Presenting Information Technology Communication Plan For Cyber Security Attack Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Reporting Response, Prevention Measures, Incident Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
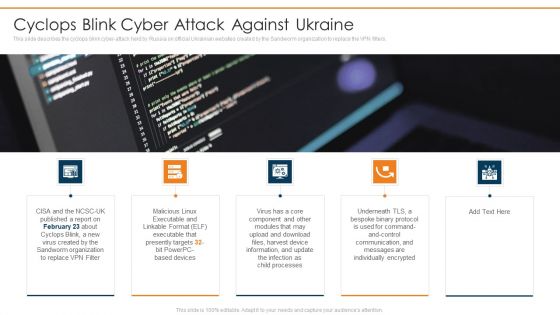
Data Wiper Spyware Attack Cyclops Blink Cyber Attack Against Ukraine Background PDF
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters.Presenting data wiper spyware attack cyclops blink cyber attack against ukraine background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyclops blink cyber attack against ukraine In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Attack Protection Ppt PowerPoint Presentation Model Inspiration Cpb Pdf
Presenting this set of slides with name cyber attack protection ppt powerpoint presentation model inspiration cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber attack protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Russian Cyber Attacks On Ukraine IT Technical Analysis Of Ddos Attacks Structure PDF
This slide represents the technical analysis of DDoS attacks against Ukrainian websites by showing the internet traffic to the Oschad Bank website on 15-16 February 2022. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it technical analysis of ddos attacks structure pdf bundle. Topics like technical analysis of ddos attacks against ukrainian websites can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
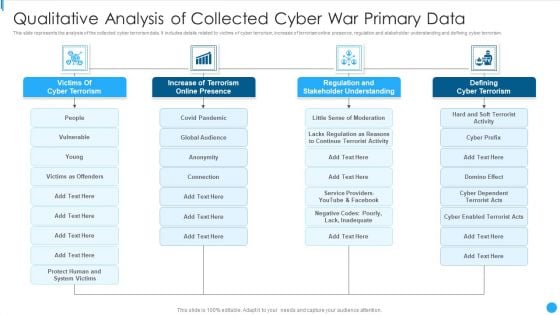
Qualitative Analysis Of Collected Cyber War Primary Data Ideas PDF
This slide represents the analysis of the collected cyber terrorism data. It includes details related to victims of cyber terrorism, increase of terrorism online presence, regulation and stakeholder understanding and defining cyber terrorism.Showcasing this set of slides titled Qualitative Analysis Of Collected Cyber War Primary Data Ideas PDF The topics addressed in these templates are Increase Terrorism, Stakeholder Understanding, Defining Terrorism All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
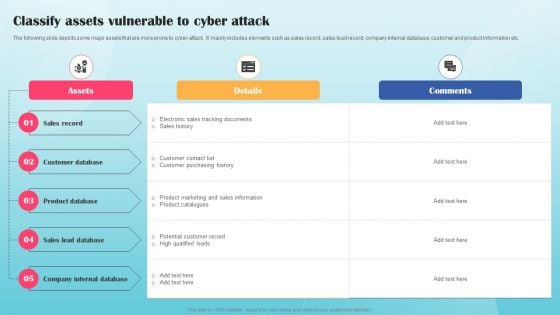
Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF
The following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. If you are looking for a format to display your unique thoughts, then the professionally designed Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF
This slide represents the continuous cyber espionage attacks held by the shuckworm group against ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF.
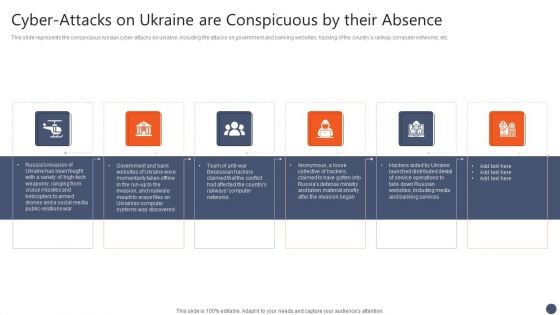
Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
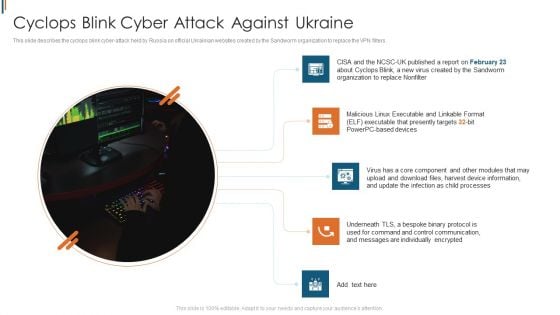
Ukraine Cyberwarfare Cyclops Blink Cyber Attack Against Ukraine Demonstration Pdf
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters. Presenting ukraine cyberwarfare cyclops blink cyber attack against ukraine demonstration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Virus has a core component and other modules that may upload and download files, harvest device information, and update the infection as child processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Data Wiper Spyware Attack Banks On Alert For Russian Reprisal Cyber Attacks On Swift Sample PDF
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a data wiper spyware attack banks on alert for russian reprisal cyber attacks on swift sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like payments messaging system, military industrial complex, institutions suspended You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
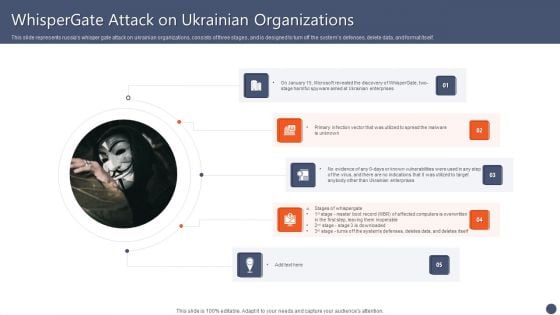
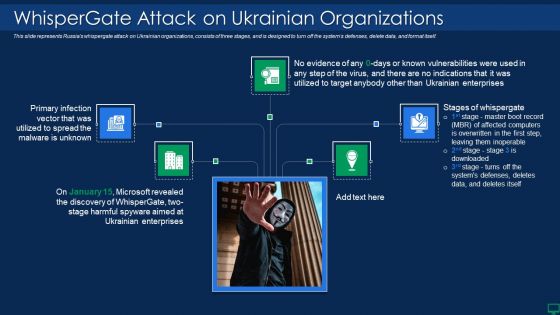
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.
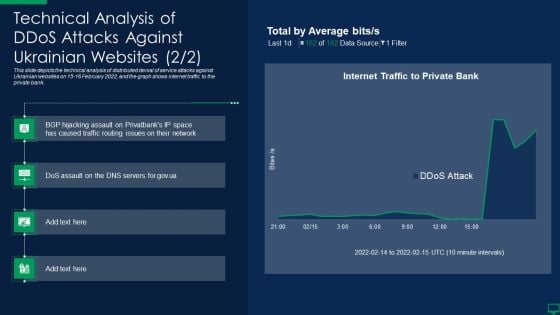
Russian Cyber Attacks On Ukraine IT Technical Analysis Of Ddos Attacks Against Designs PDF
This slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15 16 February 2022, and the graph shows internet traffic to the private bank. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it technical analysis of ddos attacks against designs pdf. Use them to share invaluable insights on technical analysis of ddos attacks against ukrainian websites and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
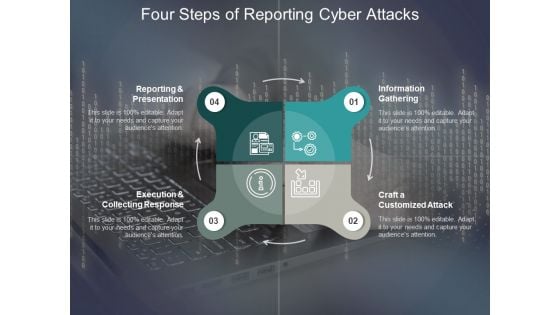
Four Steps Of Reporting Cyber Attacks Ppt PowerPoint Presentation Guidelines
Presenting this set of slides with name four steps of reporting cyber attacks ppt powerpoint presentation guidelines. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
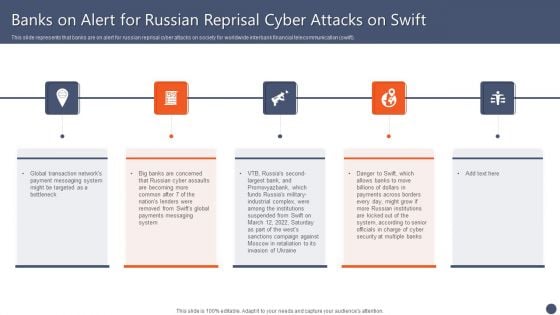
Series Of Cyber Security Attacks Against Ukraine 2022 Banks On Alert For Russian Reprisal Cyber Attacks On Swift Background PDF
This slide represents that banks are on alert for russian reprisal cyber attacks on society for worldwide interbank financial telecommunication swift. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 Banks On Alert For Russian Reprisal Cyber Attacks On Swift Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Present like a pro with Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
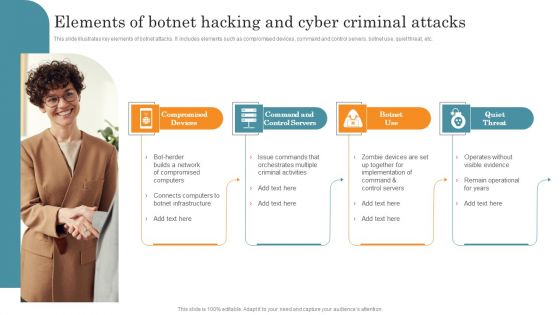
Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF
This slide illustrates key elements of botnet attacks. It includes elements such as compromised devices, command and control servers, botnet use, quiet threat, etc. Persuade your audience using this Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Compromised Devices, Command Control Servers, Botnet Use, Quiet Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Russian Cyber Attacks On Ukraine IT Whispergate Attack On Ukrainian Microsoft PDF
This is a russian cyber attacks on ukraine it whispergate attack on ukrainian microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like target, enterprises. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Impact Of Defacement Attacks Portrait PDF
This slide shows the impact of defacement attacks and fake news on the public, and Meta has banned Russian media on its platforms, and Russia has restricted access to Facebook. This is a russian cyber attacks on ukraine it impact of defacement attacks portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, fundamental, method, material, social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
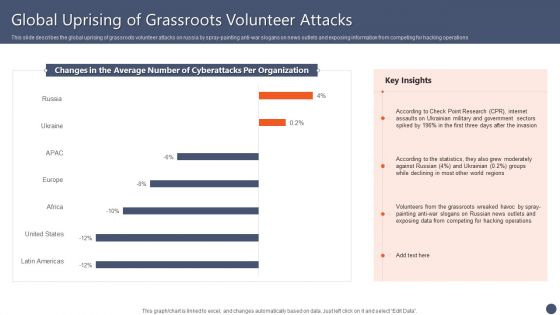
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
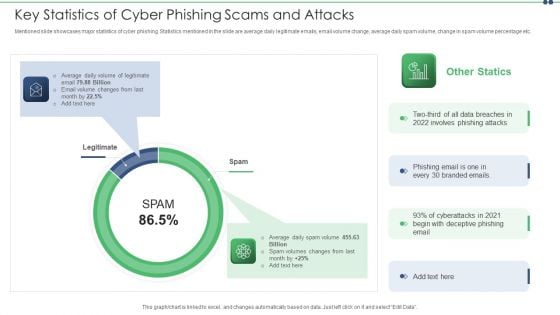
Key Statistics Of Cyber Phishing Scams And Attacks Pictures PDF
Mentioned slide showcases major statistics of cyber phishing. Statistics mentioned in the slide are average daily legitimate emails, email volume change, average daily spam volume, change in spam volume percentage etc. Persuade your audience using this key statistics of cyber phishing scams and attacks pictures pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including average, email. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Russian Cyber Attacks On Ukraine Summary PDF
This is a agenda for russian cyber attacks on ukraine summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technical, analysis, websites, globally. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF
Persuade Your Audience Using This Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF. This PPT Design Covers Five Stages, Thus Making It A Great Tool To Use. It Also Caters To A Variety Of Topics Including Updating Security Software, Backing Up Data, Block Unreliable Websites. Download This PPT Design Now To Present A Convincing Pitch That Not Only Emphasizes The Topic But Also Showcases Your Presentation Skills.
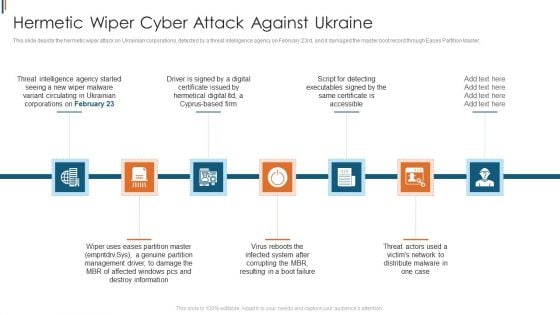
Ukraine Cyberwarfare Hermetic Wiper Cyber Attack Against Ukraine Designs Pdf
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Eases Partition Master. This is a ukraine cyberwarfare hermetic wiper cyber attack against ukraine designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like script for detecting executables signed by the same certificate is accessible, virus reboots the infected system after corrupting the mbr, resulting in a boot failure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Reverse Proxy Server IT Cyber Attacks On The Main Server Of Company Ppt Icon Graphics Tutorials PDF
This slide shows the current situation of the organization through the total losses in millions experienced because of different types of the cyber attacks. Deliver an awe inspiring pitch with this creative reverse proxy server it cyber attacks on the main server of company ppt icon graphics tutorials pdf bundle. Topics like losses organization, due to cyberattacks, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Attack Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Cyber Security Attack Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
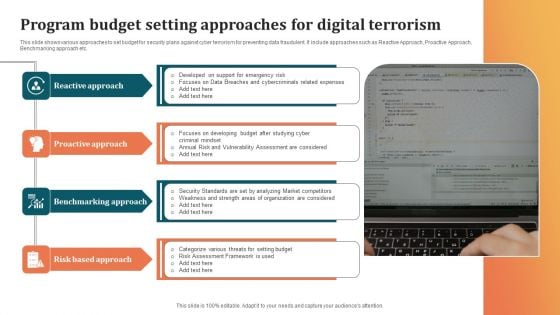
Program Budget Setting Approaches For Digital Terrorism Background PDF
This slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc. Presenting Program Budget Setting Approaches For Digital Terrorism Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benchmarking Approach, Risk Based Approach, Proactive Approach. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
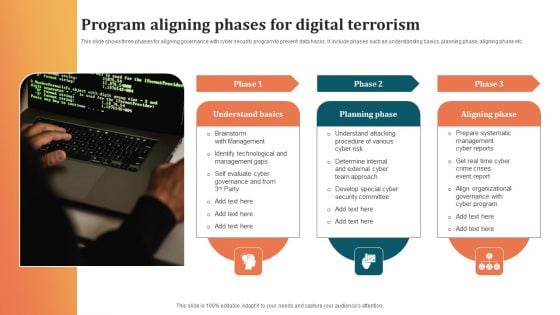
Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Russian Cyber Attacks On Ukraine IT Hybrid Warfare Cyber Rapid Structure PDF
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyber attacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. Presenting russian cyber attacks on ukraine it hybrid warfare cyber rapid structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hybrid warfare cyber rapid response team crrt. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
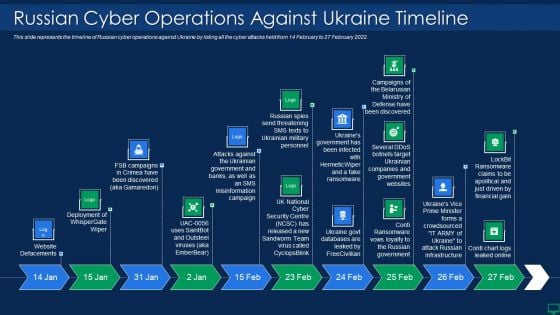
Russian Cyber Attacks On Ukraine IT Russian Cyber Operations Against Themes PDF
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. This is a russian cyber attacks on ukraine it russian cyber operations against themes pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like russian cyber operations against ukraine timeline. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
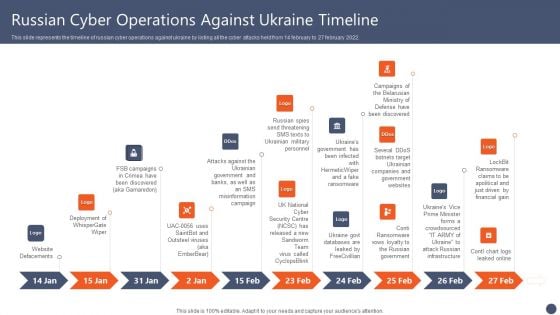
Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
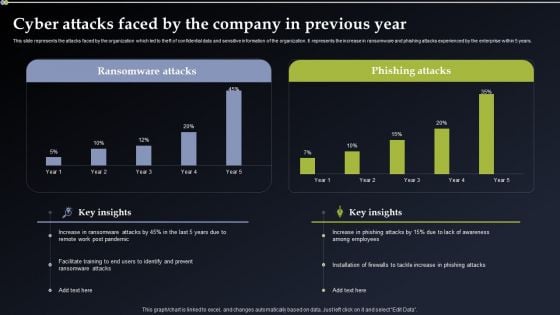
Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
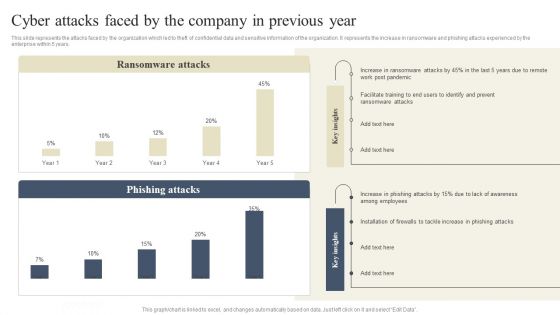
CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.


 Continue with Email
Continue with Email

 Home
Home


































