Cybercrime
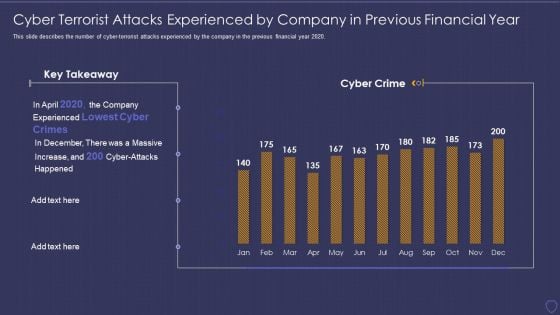
Global Cyber Terrorism Incidents On The Rise IT Cyber Terrorist Attacks Experienced Formats PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2020. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it cyber terrorist attacks experienced formats pdf bundle. Topics like cyber terrorist attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
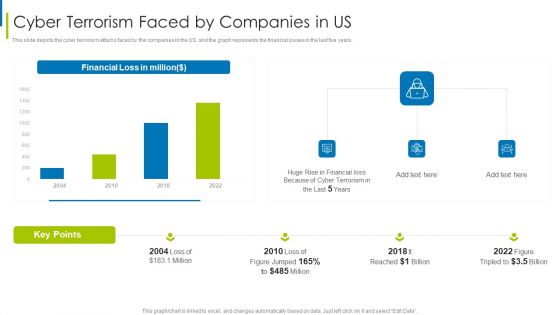
Cyber Terrorism Assault Cyber Terrorism Faced By Companies In US Mockup PDF
This slide depicts the cyber terrorism attacks faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault cyber terrorism faced by companies in us mockup pdf Use them to share invaluable insights on Consequences Of Cyber Attacks, Response Planning, Recovery Strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
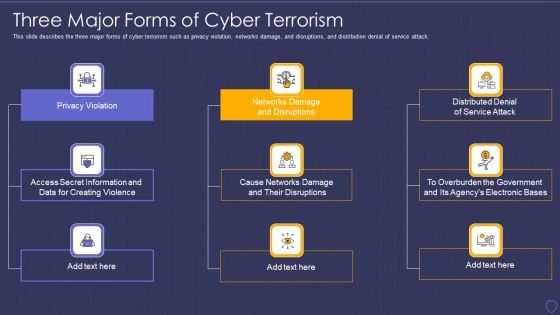
Global Cyber Terrorism Incidents On The Rise IT Three Major Forms Of Cyber Terrorism Topics PDF
This slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Presenting global cyber terrorism incidents on the rise it three major forms of cyber terrorism topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like privacy violation, networks damage and disruptions, distributed denial of service attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
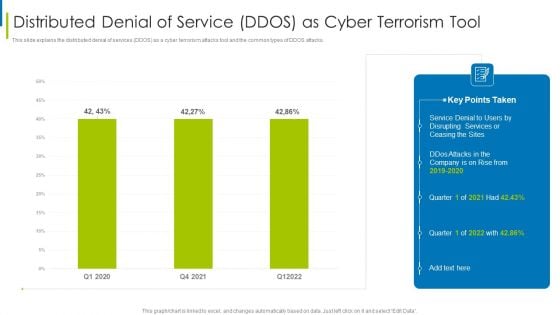
Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
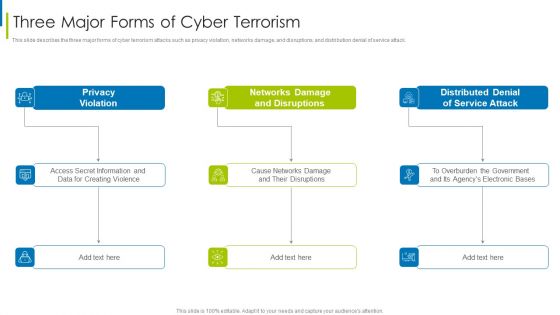
Cyber Terrorism Assault Three Major Forms Of Cyber Terrorism Brochure PDF
This slide describes the three major forms of cyber terrorism attacks such as privacy violation, networks damage, and disruptions, and distribution denial of service attack.This is a cyber terrorism assault three major forms of cyber terrorism brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy violation, networks damage and disruptions, distributed denial You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
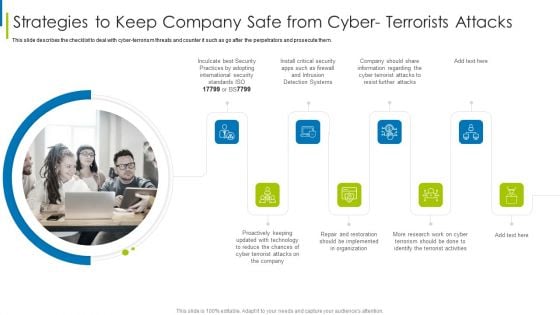
Cyber Terrorism Assault Strategies To Keep Company Safe From Cyber Terrorists Attacks Pictures PDF
This slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them.Presenting cyber terrorism assault strategies to keep company safe from cyber terrorists attacks pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like inculcate best security, practices by adopting, international security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
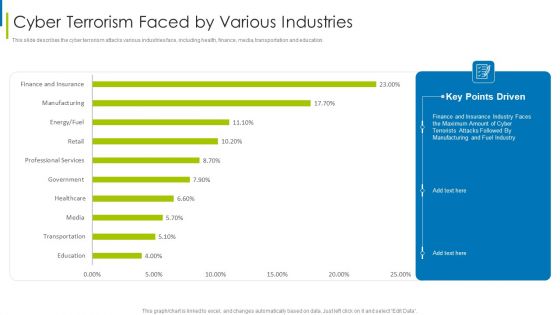
Cyber Terrorism Assault Cyber Terrorism Faced By Various Industries Pictures PDF
This slide describes the cyber terrorism attacks various industries face, including health, finance, media, transportation and education.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism faced by various industries pictures pdf bundle. Topics like Cyber Terrorism Faced By Companies In US can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
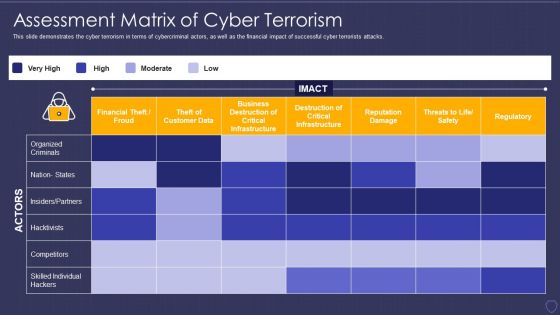
Global Cyber Terrorism Incidents On The Rise IT Assessment Matrix Of Cyber Terrorism Ideas PDF
This slide demonstrates the cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it assessment matrix of cyber terrorism ideas pdf bundle. Topics like financial theft or froud, reputation damage, regulatory, competitors, destruction of critical infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Terrorism Assault Dashboard For Threat Tracking Of Cyber Terrorism Themes PDF
This slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault dashboard for threat tracking of cyber terrorism themes pdf Use them to share invaluable insights on Massive Increase, Cyber Attacks Happened, Company Experienced and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
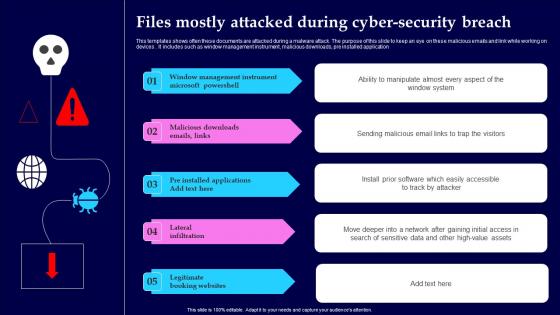
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application
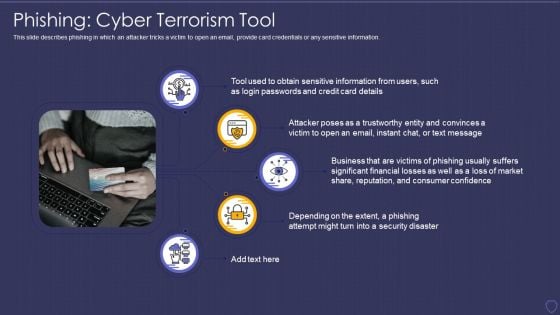
Global Cyber Terrorism Incidents On The Rise IT Phishing Cyber Terrorism Tool Rules PDF
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Presenting global cyber terrorism incidents on the rise it phishing cyber terrorism tool rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like phishing cyber terrorism tool. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Malicious Code Malware Misused For Cyber Terrorism Pictures PDF
This slide depicts the malicious code or malware misused for cyber terrorism attacks to hijack or access information from computers.Presenting cyber terrorism assault malicious code malware misused for cyber terrorism pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like broad spectrum, executed by changing, programmer by stopping In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
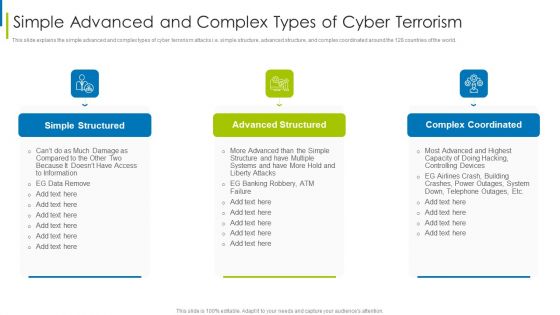
Cyber Terrorism Assault Simple Advanced And Complex Types Of Cyber Terrorism Structure PDF
This slide explains the simple advanced and complex types of cyber terrorism attacks i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world.This is a cyber terrorism assault simple advanced and complex types of cyber terrorism structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simple structured, advanced structured, complex coordinated You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Types Of Trojans Misused In Cyber Terrorism Background PDF
This slide describes the types of trojans misused in cyber terrorism attacks such as downloader trojan, spyware, backdoor trojan, and rootkit trojans. Presenting cyber terrorism assault types of trojans misused in cyber terrorism background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like backdoor trojan, downloader trojan, rootkit trojans In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
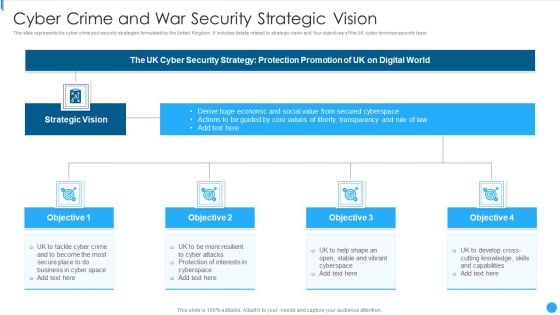
Cyber Crime And War Security Strategic Vision Designs PDF
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team.Persuade your audience using this Cyber Crime And War Security Strategic Vision Designs PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Strategy, Protection Promotion, Secured Cyberspace Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
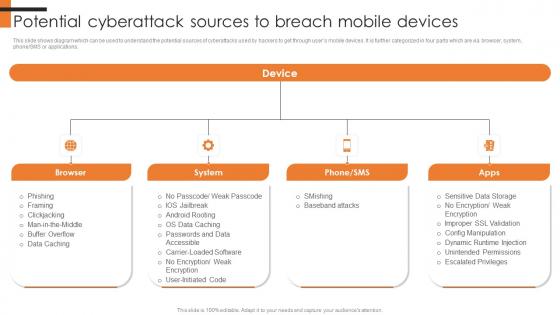
Potential Cyberattack Sources To Breach Mobile Comprehensive Smartphone Banking Microsoft Pdf
This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phoneorSMS or applications.If you are looking for a format to display your unique thoughts, then the professionally designed Potential Cyberattack Sources To Breach Mobile Comprehensive Smartphone Banking Microsoft Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Potential Cyberattack Sources To Breach Mobile Comprehensive Smartphone Banking Microsoft Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phoneorSMS or applications.
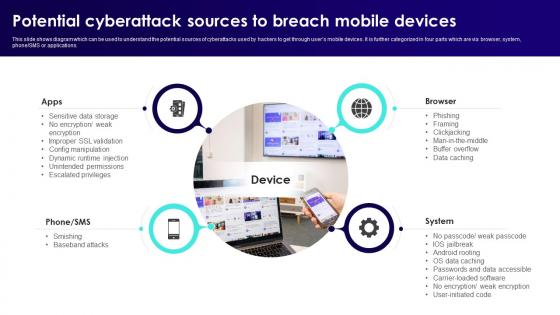
Wireless Banking To Improve Potential Cyberattack Sources To Breach Mobile Fin SS V
This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Wireless Banking To Improve Potential Cyberattack Sources To Breach Mobile Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Wireless Banking To Improve Potential Cyberattack Sources To Breach Mobile Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications.
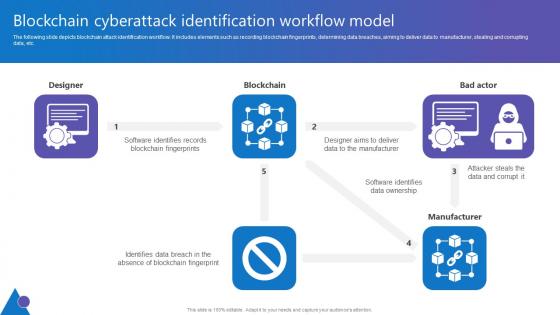
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.
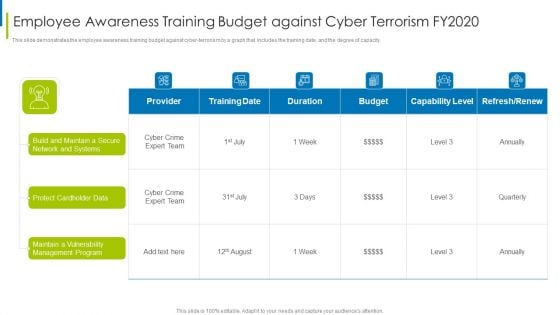
Cyber Terrorism Assault Employee Awareness Training Budget Against Cyber Terrorism FY2020 Inspiration PDF
This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Deliver an awe inspiring pitch with this creative cyber terrorism assault employee awareness training budget against cyber terrorism fy2020 inspiration pdf bundle. Topics like Protect Cardholder Data, Maintain A Vulnerability, Management Program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
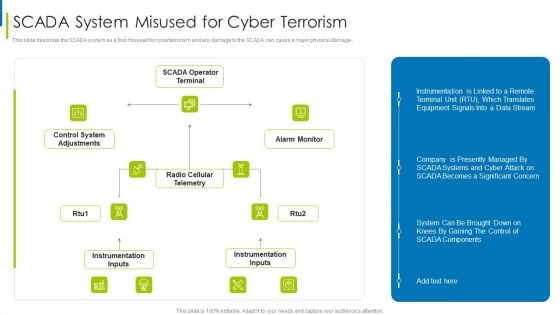
Cyber Terrorism Assault SCADA System Misused For Cyber Terrorism Themes PDF
This slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage.Deliver an awe inspiring pitch with this creative cyber terrorism assault scada system misused for cyber terrorism themes pdf bundle. Topics like instrumentation inputs, control system adjustments, radio cellular telemetry can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault Types Of Ddos Attacks In The Company Sample PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application layer attacks. This is a cyber terrorism assault types of ddos attacks in the company sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like volume based attacks, protocol based attacks, application layer attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
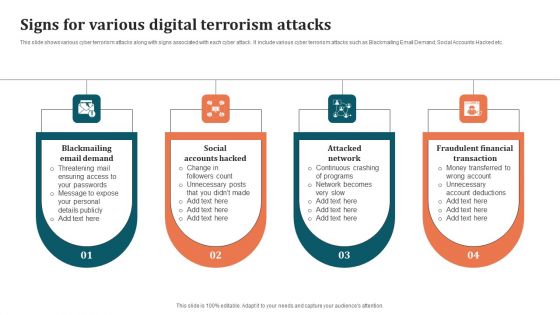
Signs For Various Digital Terrorism Attacks Brochure PDF
This slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc. Presenting Signs For Various Digital Terrorism Attacks Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Attacked Network, Fraudulent Financial Transaction, Social Accounts Hacked. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
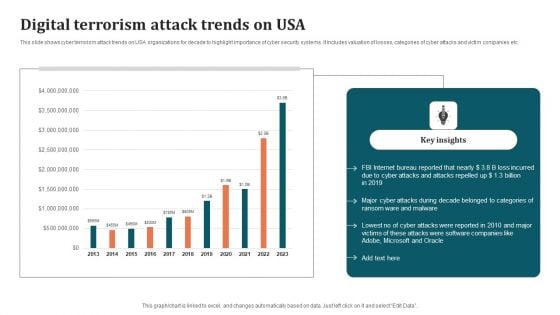
Digital Terrorism Attack Trends On USA Ideas PDF
This slide shows cyber terrorism attack trends on USA organizations for decade to highlight importance of cyber security systems. It includes valuation of losses, categories of cyber attacks and victim companies etc. Showcasing this set of slides titled Digital Terrorism Attack Trends On USA Ideas PDF. The topics addressed in these templates are Key Insights, Internet, Digital Terrorism Attack Trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
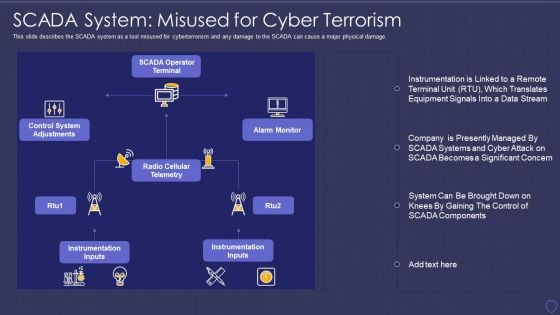
Global Cyber Terrorism Incidents On The Rise IT SCADA System Misused For Cyber Terrorism Professional PDF
This slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it scada system misused for cyber terrorism professional pdf bundle. Topics like instrumentation inputs, radio cellular telemetry, alarm monitor, scada operator terminal, control system adjustments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault How To Prevent Ddos Attacks In The Company Inspiration PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc.Presenting cyber terrorism assault how to prevent ddos attacks in the company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service providers bandwidth capacity, network monitoring, update security components In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault How To Protect Company From Trojan Attacks Demonstration PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a cyber terrorism assault how to protect company from trojan attacks demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device conventional, next generation antivirus, prevent trojan infection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
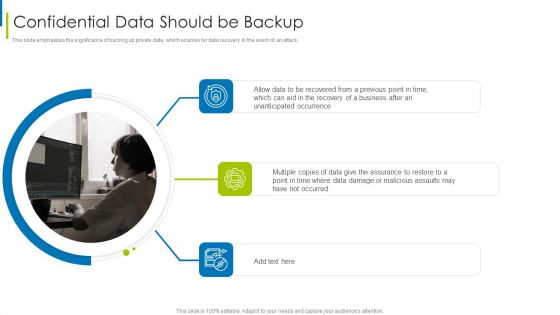
Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
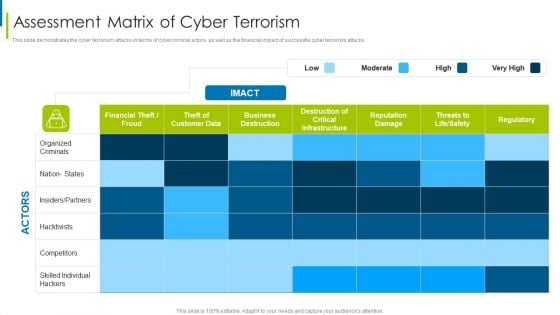
Cyber Terrorism Assault Assessment Matrix Of Cyber Terrorism Professional PDF
Deliver an awe inspiring pitch with this creative cyber terrorism assault assessment matrix of cyber terrorism professional pdf bundle. Topics like Business Destruction, Destruction Of Critical Infrastructure, Reputation Damage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
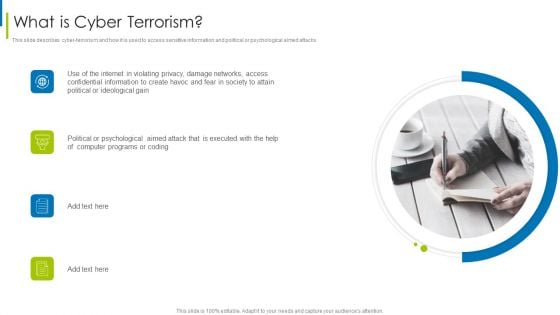
Cyber Terrorism Assault What Is Cyber Terrorism Elements PDF
Presenting cyber terrorism assault what is cyber terrorism elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like internet in violating, confidential information, political or ideological In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
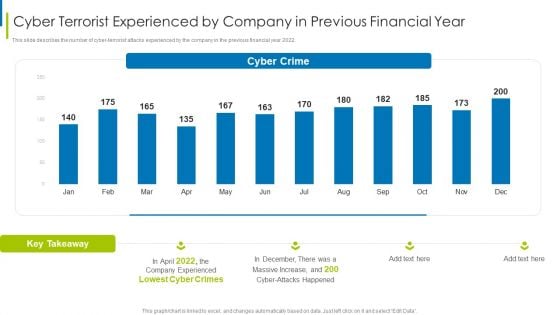
Cyber Terrorism Assault Cyber Terrorist Experienced By Company In Previous Financial Year Sample PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2022.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorist experienced by company in previous financial year sample pdf bundle. Topics like Increased Costs, Reputational Damage, Intellectual Property Theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Explore a selection of the finest Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents Cybersecurity Risk Assessment Program Dashboard to effectively track cyber security risk levels. This will provide a structured approach for organizations to review and mitigate cyber threats. It includes multiple threat agents, attack methods, and preventive controls implemented with detailed insights, and it shows critical metrics including risk scores, the number of infected systems, and detected vulnerabilities.
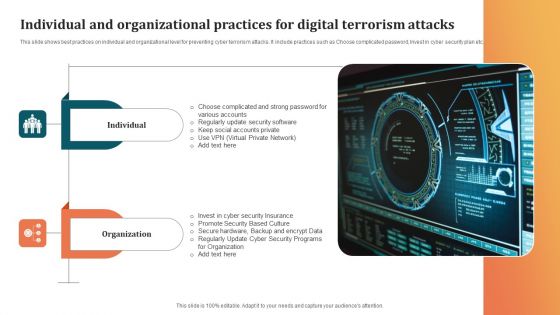
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
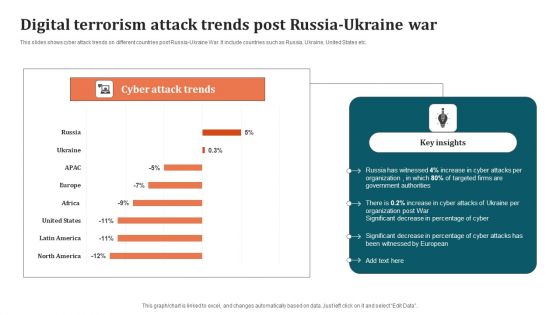
Digital Terrorism Attack Trends Post Russia Ukraine War Graphics PDF
This slides shows cyber attack trends on different countries post Russia-Ukraine War. It include countries such as Russia, Ukraine, United States etc. Pitch your topic with ease and precision using this Digital Terrorism Attack Trends Post Russia Ukraine War Graphics PDF. This layout presents information on Organization, Digital Terrorism Attack Trends. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
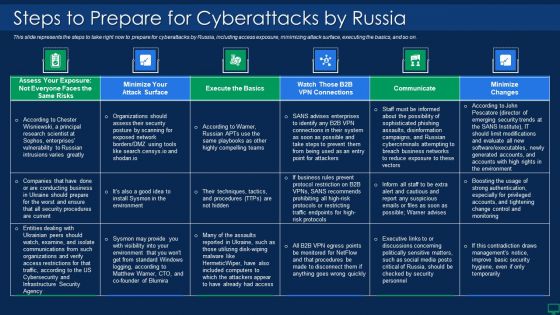
Russian Cyber Attacks On Ukraine IT Steps To Prepare For Cyberattacks Demonstration PDF
This slide represents the steps to take right now to prepare for cyberattacks by Russia, including access exposure, minimizing attack surface, executing the basics, and so on. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it steps to prepare for cyberattacks demonstration pdf bundle. Topics like organizations, network, system, enterprises, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
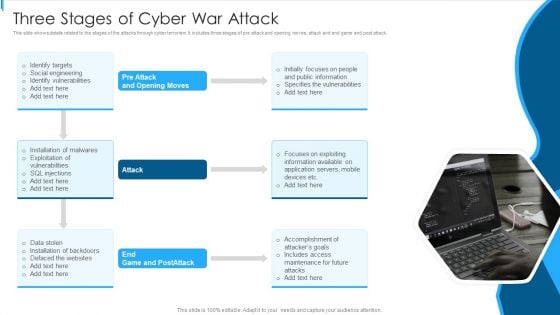
Three Stages Of Cyber War Attack Sample PDF
This slide shows details related to the stages of the attacks through cyber terrorism. It includes three stages of pre attack and opening moves, attack and end game and post attack.Persuade your audience using this Three Stages Of Cyber War Attack Sample PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Public Information, Specifies Vulnerabilities, Focuses Exploiting Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
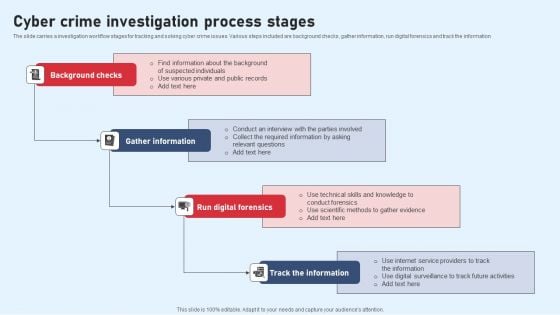
Cyber Crime Investigation Process Stages Pictures PDF
The slide carries a investigation workflow stages for tracking and solving cyber crime issues. Various steps included are background checks, gather information, run digital forensics and track the information Persuade your audience using this Cyber Crime Investigation Process Stages Pictures PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Background Checks, Gather Information, Run Digital Forensics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
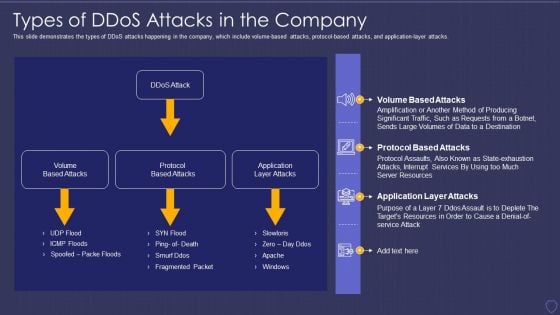
Global Cyber Terrorism Incidents On The Rise IT Types Of Ddos Attacks In The Company Elements PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application-layer attacks. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it types of ddos attacks in the company elements pdf. Use them to share invaluable insights on volume based attacks, protocol based attacks, application layer attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
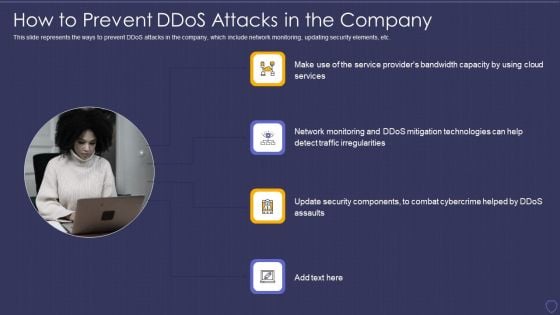
Global Cyber Terrorism Incidents On The Rise IT How To Prevent Ddos Attacks In The Company Designs PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Presenting global cyber terrorism incidents on the rise it how to prevent ddos attacks in the company designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mitigation technologies, service, traffic irregularities, network monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
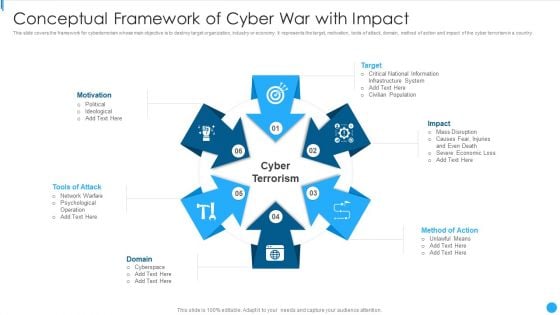
Conceptual Framework Of Cyber War With Impact Demonstration PDF
This slide covers the framework for cyberterrorism whose main objective is to destroy target organization, industry or economy. It represents the target, motivation, tools of attack, domain, method of action and impact of the cyber terrorism in a country.Presenting Conceptual Framework Of Cyber War With Impact Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including National Information, Infrastructure System, Civilian Population This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Terrorism Assault Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism Template PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts.Presenting cyber terrorism assault roadmap to implement cyber security to mitigate cyber terrorism template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating personal accounts, awareness training, keep the hardware In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Terrorism Assault IT Infrastructure Cyber Security Budget Against Cyber Terrorism FY19 20 Themes PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault it infrastructure cyber security budget against cyber terrorism fy19 20 themes pdf Use them to share invaluable insights on cloud security, integrated risk management, identify access management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
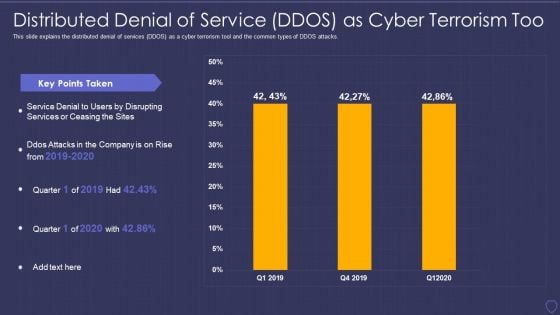
Global Cyber Terrorism Incidents On The Rise IT Distributed Denial Of Service Template PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it distributed denial of service template pdf bundle. Topics like distributed denial of service ddos as cyber terrorism too can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
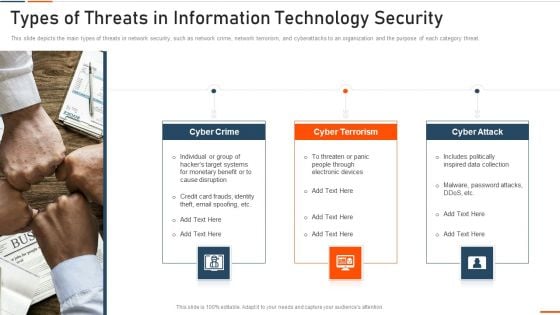
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
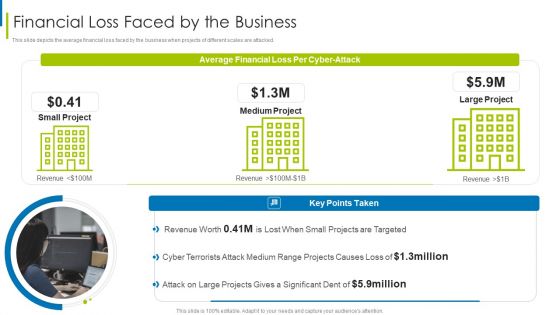
Cyber Terrorism Assault Financial Loss Faced By The Business Summary PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked.This is a cyber terrorism assault financial loss faced by the business summary pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like projects are targeted, cyber terrorists, attack on large You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
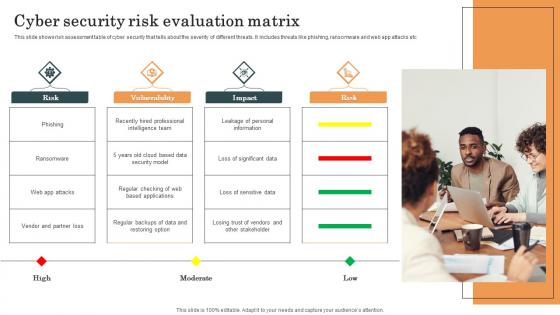
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.
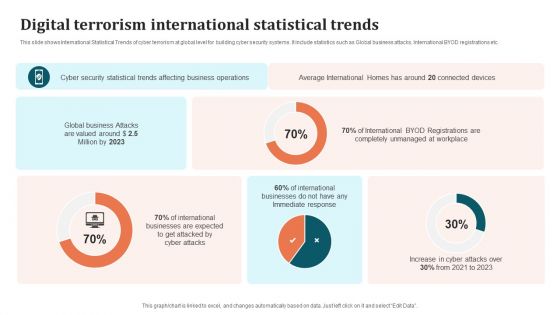
Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda For Cyber Terrorism Assault Professional PDF
This is a agenda for cyber terrorism assault professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
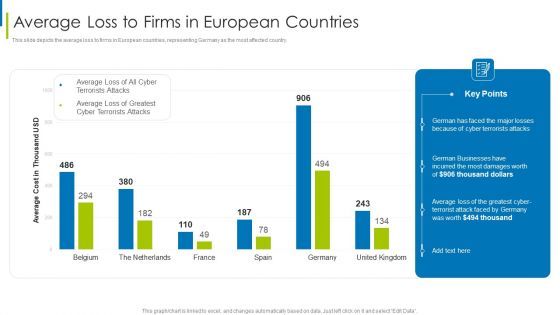
Cyber Terrorism Assault Average Loss To Firms In European Countries Slides PDF
This slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault average loss to firms in european countries slides pdf Use them to share invaluable insights on German businesses, average loss , cyber terrorist attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
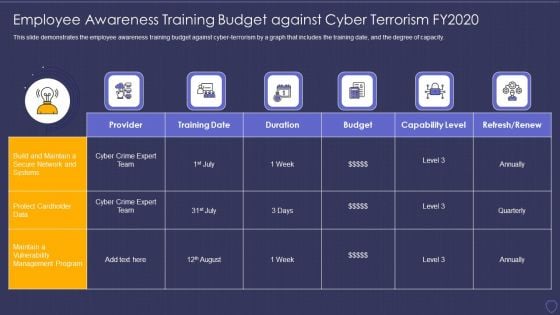
Global Cyber Terrorism Incidents On The Rise IT Employee Awareness Training Graphics PDF
This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it employee awareness training graphics pdf bundle. Topics like provider, training date, duration, budget, capability level, refresh or renew can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
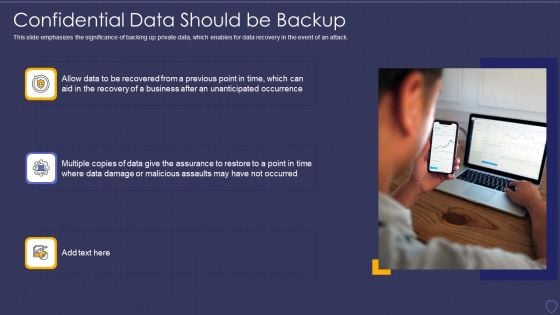
Global Cyber Terrorism Incidents On The Rise IT Confidential Data Should Be Backup Structure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
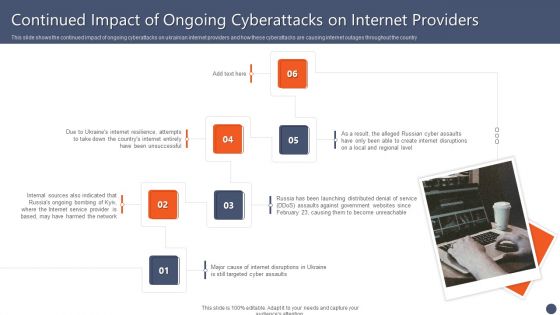
Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Series Of Cyber Security Attacks Against Ukraine 2022 Should We Be Concerned About Russian Cyberattacks Information PDF
This slide shows that US citizens should not be concerned about russian cyberattacks as nothing has happened so far. However, the US department of homeland security issued a warning to organizations to look for russian cyberattacks. Make sure to capture your audiences attention in your business displays with our gratis customizable Series Of Cyber Security Attacks Against Ukraine 2022 Should We Be Concerned About Russian Cyberattacks Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
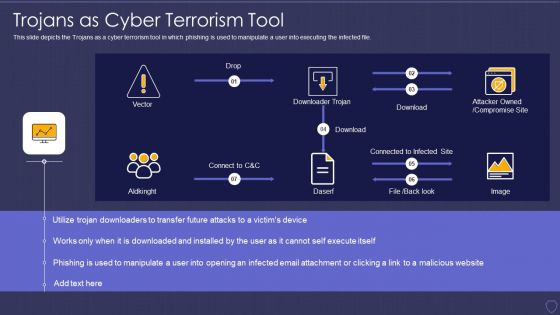
Global Cyber Terrorism Incidents On The Rise IT Trojans As Cyber Terrorism Tool Graphics PDF
This slide depicts the Trojans as a cyber terrorism tool in which phishing is used to manipulate a user into executing the infected file. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it trojans as cyber terrorism tool graphics pdf bundle. Topics like trojans as cyber terrorism tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
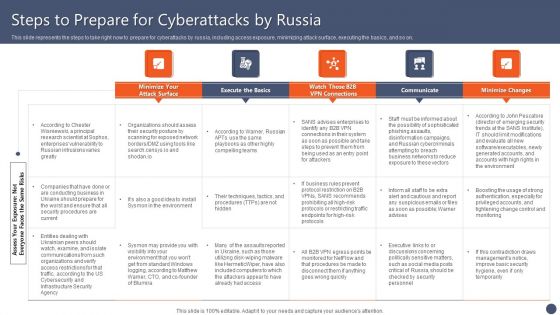
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.


 Continue with Email
Continue with Email

 Home
Home


































