Cybersecurity Icons

Cybersecurity Operations Cybersecops Table Of Content Summary PDF
Retrieve professionally designed Cybersecurity Operations Cybersecops Table Of Content Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
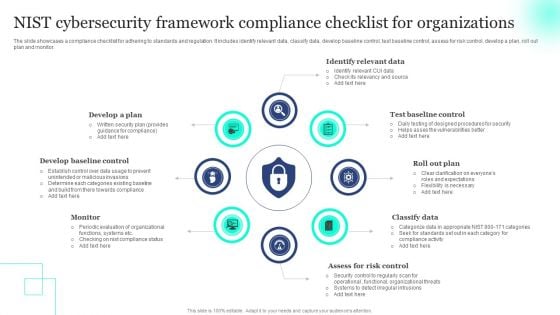
NIST Cybersecurity Framework Compliance Checklist For Organizations Inspiration PDF
The slide showcases a compliance checklist for adhering to standards and regulation. It includes identify relevant data, classify data, develop baseline control, test baseline control, assess for risk control, develop a plan, roll out plan and monitor. Presenting NIST Cybersecurity Framework Compliance Checklist For Organizations Inspiration PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Develop Baseline Control, Monitor, Classify Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
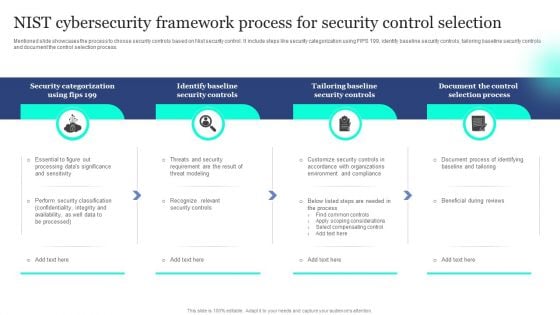
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
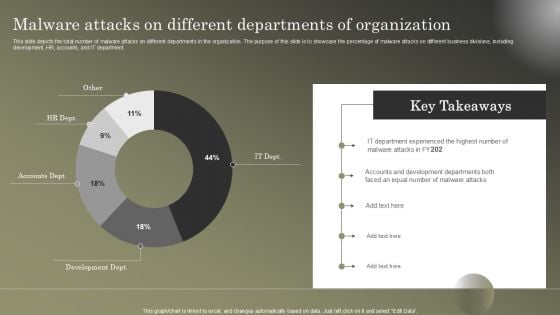
Cybersecurity Operations Cybersecops Malware Attacks On Different Departments Topics PDF
Cybersecurity Operations Cybersecops Vulnerabilities Tracking Dashboard For Secops Introduction PDF
This slide represents the vulnerabilities tracking dashboard for SecOps. The purpose of this slide is to demonstrate the tracking of vulnerabilities of an organizations assets, services with the most vulnerabilities, mean time to remediate, and the average age of vulnerabilities. This modern and well arranged Cybersecurity Operations Cybersecops Vulnerabilities Tracking Dashboard For Secops Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Incident Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this Cybersecurity Incident Ppt PowerPoint Presentation Complete Deck With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of fourteen slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps like identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Persuade your audience using this Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Recover, Respond, Detect, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
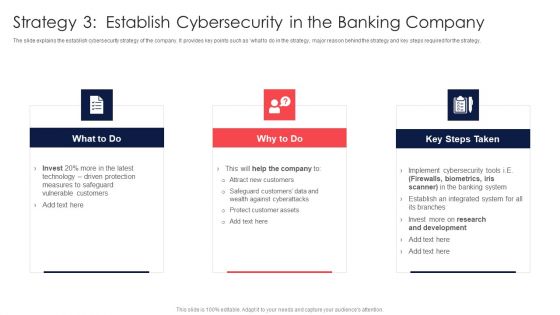
Digital Transformation Of Consumer Strategy 3 Establish Cybersecurity In The Banking Company Ideas PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy. Presenting Digital Transformation Of Consumer Strategy 3 Establish Cybersecurity In The Banking Company Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Driven Protection, Vulnerable Customers, Against Cyberattack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Aligning The Incident Management Policies Sample PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Presenting cybersecurity monitoring plan steps in detail aligning the incident management policies sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security monitoring solutions, ongoing management, incident logging, incident categorization, incident prioritization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cybersecurity Guidelines IT Post It Notes Ppt PowerPoint Presentation File Template PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Guidelines IT Post It Notes Ppt PowerPoint Presentation File Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
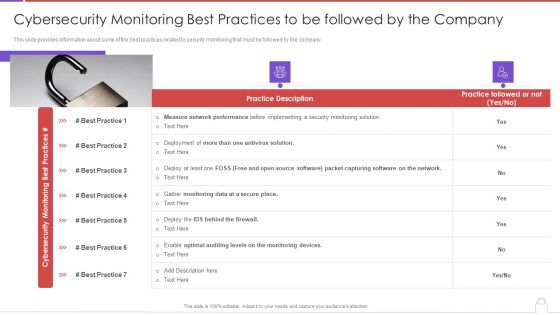
Methods To Develop Cybersecurity Monitoring Best Practices To Be Followed By The Company Demonstration PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Presenting methods to develop cybersecurity monitoring best practices to be followed by the company demonstration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like practice description, gather monitoring data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Approaches To Implement Advanced Cybersecurity Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fortyfour slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of seventy slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V
This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection. Are you searching for a Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V from Slidegeeks today. This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection.

Comprehensive Look At Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V
This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Retrieve professionally designed Comprehensive Look At Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts.

Visionary Guide To Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V
This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Slidegeeks has constructed Visionary Guide To Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts.

Overview Cybersecurity And Data Protection In Digital Transformation DT SS V
This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.Find highly impressive Overview Cybersecurity And Data Protection In Digital Transformation DT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Overview Cybersecurity And Data Protection In Digital Transformation DT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.
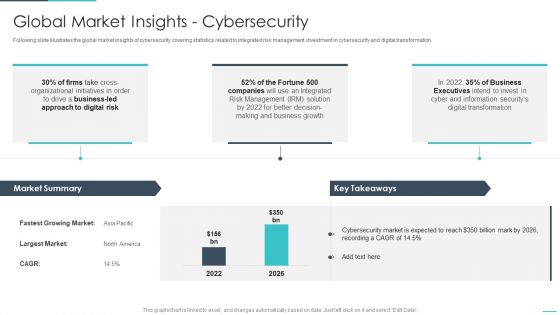
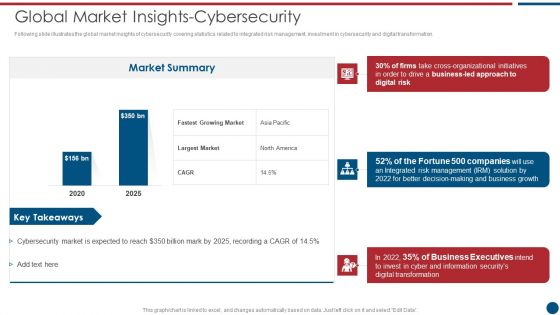
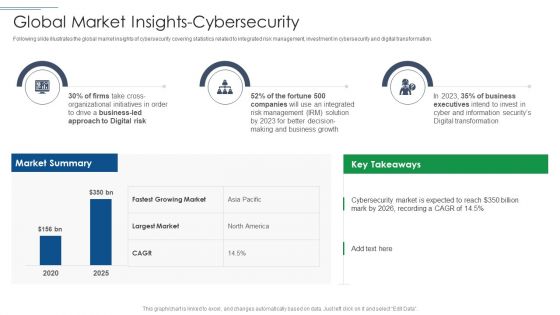
Handling Cyber Threats Digital Era Global Market Insights Cybersecurity Ppt Show Background Image PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative handling cyber threats digital era global market insights cybersecurity ppt show background image pdf bundle. Topics like global market insights cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V
The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding. This modern and well-arranged Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding.

Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V
This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players. If you are looking for a format to display your unique thoughts, then the professionally designed Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players.

Cybersecurity In Medical Industry Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative,then this Cybersecurity In Medical Industry Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the seventeen slides included in this sample template can be used to present a birds eye view of the topic. These slides are also fully editable,giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content,all other elements like color,design,theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this,you can use this PPT design in formats like PDF,PNG,and JPG once downloaded. Therefore,without any further ado,download and utilize this sample presentation as per your liking. Our Cybersecurity In Medical Industry Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Gallery Influencers PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt gallery influencers pdf bundle. Topics like costs incurred to process faulty cybersecurity transactions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

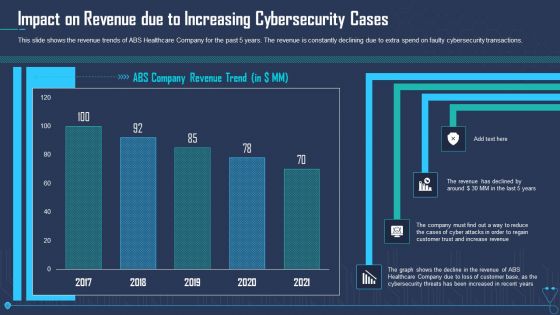
Impact On Revenue Due To Increasing Cybersecurity Cases Ppt Outline Styles PDF
This slide shows the revenue trends of ABS Healthcare Company for the past 5 years. The revenue is constantly declining due to extra spend on faulty cybersecurity transactions. Deliver an awe inspiring pitch with this creative impact on revenue due to increasing cybersecurity cases ppt outline styles pdf bundle. Topics like impact on revenue due to increasing cybersecurity cases can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
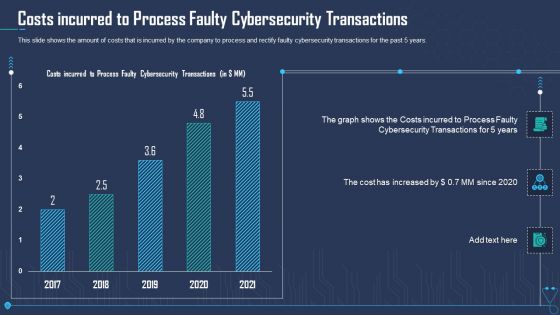
Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Infographics Smartart PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt infographics smartart pdf bundle. Topics like costs incurred to process faulty cybersecurity transactions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Impact On Revenue Due To Increasing Cybersecurity Cases Ppt Inspiration Infographics PDF
This slide shows the revenue trends of ABS Healthcare Company for the past 5 years. The revenue is constantly declining due to extra spend on faulty cybersecurity transactions. Deliver an awe inspiring pitch with this creative impact on revenue due to increasing cybersecurity cases ppt inspiration infographics pdf bundle. Topics like impact on revenue due to increasing cybersecurity cases can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF bundle. Topics like Market Summary, Largest Market, Business Led can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF bundle. Topics like Steps Required Demonstrating, Cybersecurity Risk Mitigation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

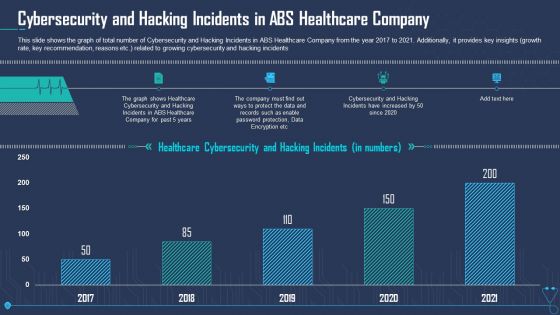
Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Styles Inspiration PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver and pitch your topic in the best possible manner with this cybersecurity and hacking incidents in ABS healthcare company ppt styles inspiration pdf. Use them to share invaluable insights on protection, data encryption, cybersecurity, 2017 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Information PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver an awe inspiring pitch with this creative cybersecurity and hacking incidents in abs healthcare company ppt information pdf bundle. Topics like cybersecurity and hacking incidents in abs healthcare company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Infographic Template Graphics Example PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver an awe inspiring pitch with this creative cybersecurity and hacking incidents in abs healthcare company ppt infographic template graphics example pdf bundle. Topics like cybersecurity and hacking incidents in abs healthcare company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.

5 Phase Procedure Infographics For Cybersecurity In Financial Services Ppt PowerPoint Presentation File Smartart PDF
Persuade your audience using this 5 phase procedure infographics for cybersecurity in financial services ppt powerpoint presentation file smartart pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 phase procedure infographics for cybersecurity in financial services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
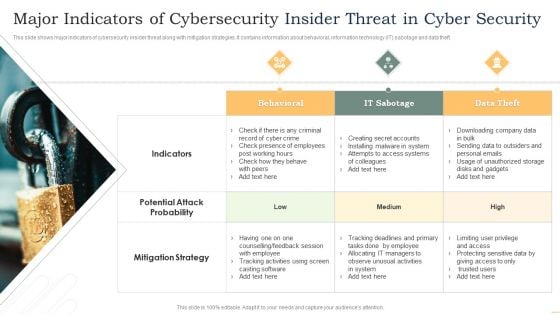
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
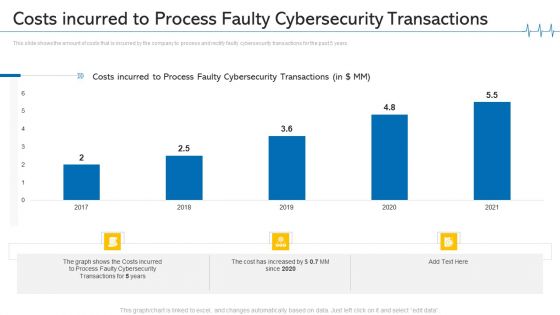
Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Portfolio Graphic Tips PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt portfolio graphic tips pdf bundle. Topics like costs incurred, process faulty, 2017 to 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt File Format PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver and pitch your topic in the best possible manner with this costs incurred to process faulty cybersecurity transactions ppt file format pdf. Use them to share invaluable insights on cost, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comprehensive Business Digitization Deck Steps Required To Demonstrating Cybersecurity Risk Mitigation Microsoft PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative comprehensive business digitization deck steps required to demonstrating cybersecurity risk mitigation microsoft pdf bundle. Topics like enforcing policy, providing appropriate funding, mandating awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
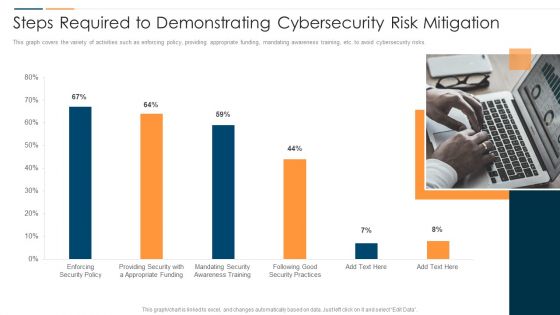
Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver and pitch your topic in the best possible manner with this Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF Use them to share invaluable insights on Practices Themselves, Awareness Training, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
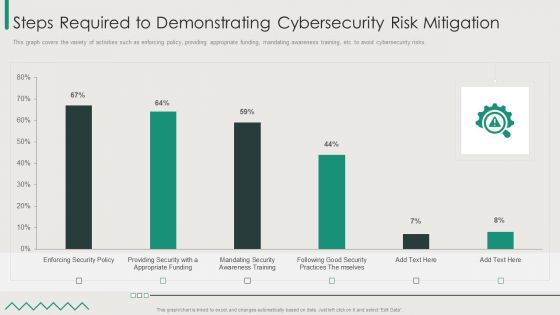
Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF
Explore a selection of the finest Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
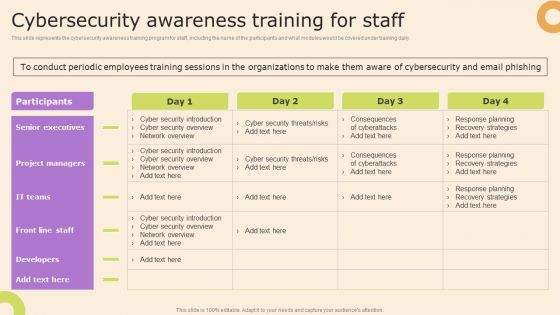
Information Technology Policy And Processes Cybersecurity Awareness Training For Staff Themes PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Technology Policy And Processes Cybersecurity Awareness Training For Staff Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Information Technology Policy And Processes Cybersecurity Awareness Training For Staff Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

A60 How Blockchain Is Reshaping Impact Of Blockchain Integration On Cybersecurity BCT SS V
This slide highlights the impact of integrating blockchain technology in healthcare systems on cybersecurity incidents reported by the organization. It includes four year analysis with relevant key insights. Slidegeeks has constructed A60 How Blockchain Is Reshaping Impact Of Blockchain Integration On Cybersecurity BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide highlights the impact of integrating blockchain technology in healthcare systems on cybersecurity incidents reported by the organization. It includes four year analysis with relevant key insights.

Digital Technology Adoption In Banking Industry Case Competition Strategy 3 Establish Cybersecurity Guidelines PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy Presenting Digital Technology Adoption In Banking Industry Case Competition Strategy 3 Establish Cybersecurity Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Technology Driven Protection Measures, Safeguard Vulnerable Customers, Establish An Integrated System In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Portrait PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Are you searching for a Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Portrait PDF from Slidegeeks today.

Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Brochure PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
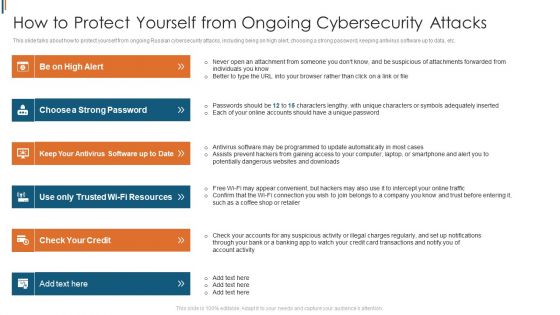
Ukraine Cyberwarfare How To Protect Yourself From Ongoing Cybersecurity Attacks Themes Pdf
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. This is a ukraine cyberwarfare how to protect yourself from ongoing cybersecurity attacks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like choose a strong password, keep your antivirus software up to date, use only trusted wi fi resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
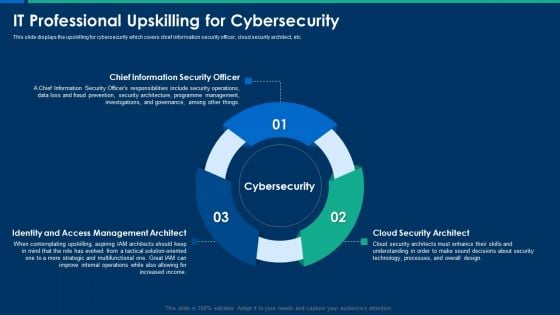
CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF
This slide represents risk assessment software dashboard for cybersecurity. It includes risk percentage, number of risks, risk analysis progress, risk response progress, risk rating etc. Showcasing this set of slides titled Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF. The topics addressed in these templates are Risk Rating Breakdown, Action Plan Breakdown, Top 5 Entities Prone To Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
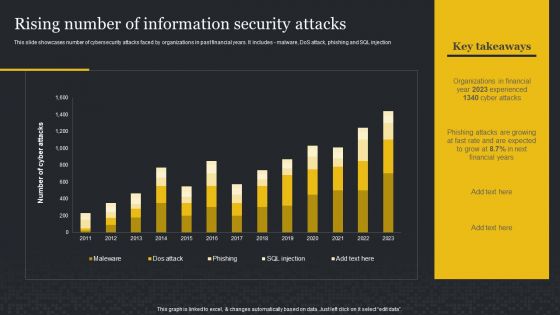
Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Guidelines IT Idea Generation Ppt PowerPoint Presentation File Designs PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Guidelines IT Idea Generation Ppt PowerPoint Presentation File Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Guidelines IT Idea Generation Ppt PowerPoint Presentation File Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
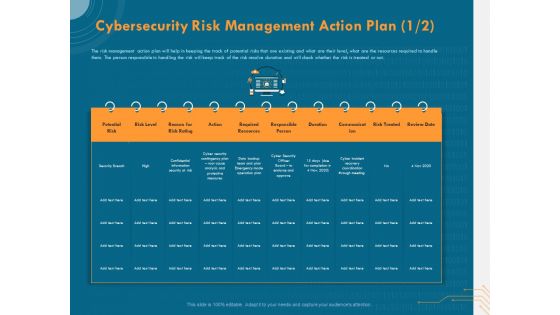
Cyber Security Implementation Framework Cybersecurity Risk Management Action Plan Potential Diagrams PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity risk management action plan potential diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason risk rating, action, required resources, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
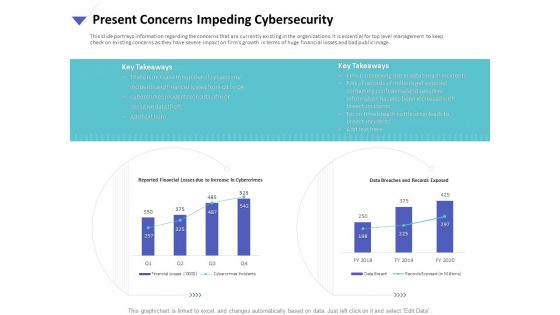
Strategies To Mitigate Cyber Security Risks Present Concerns Impeding Cybersecurity Ppt Show Objects PDF
Presenting this set of slides with name strategies to mitigate cyber security risks present concerns impeding cybersecurity ppt show objects pdf. The topics discussed in these slides are reported financial losses due increase cybercrimes, data breaches and records exposed, key takeaways. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Impact Analysis Implementing Cybersecurity Framework Ppt Show Graphics PDF
Presenting this set of slides with name cyber security implementation framework impact analysis implementing cybersecurity framework ppt show graphics pdf. The topics discussed in these slides are csf metric, controls met, nist core functions, target, trend. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
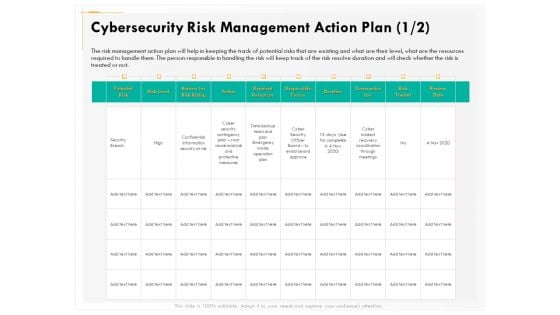
Computer Security Incident Handling Cybersecurity Risk Management Action Plan Diagrams PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Analyzing IT Department On Nist Cybersecurity Framework Introduction PDF
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
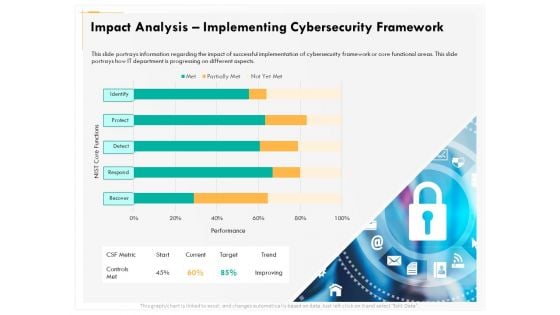
Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
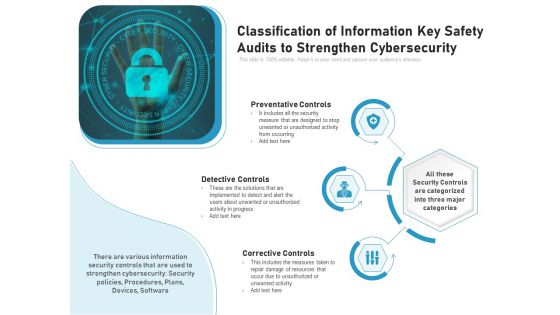
Classification Of Information Key Safety Audits To Strengthen Cybersecurity Ppt PowerPoint Presentation File Formats PDF
Presenting classification of information key safety audits to strengthen cybersecurity ppt powerpoint presentation file formats pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including preventative controls, detective controls, corrective controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V
The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V can be your best option for delivering a presentation. Represent everything in detail using Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments.
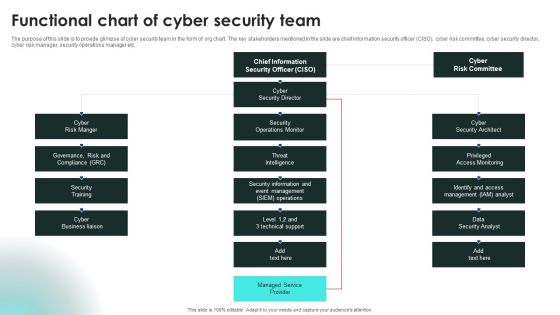
Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF from Slidegeeks today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Create an editable Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
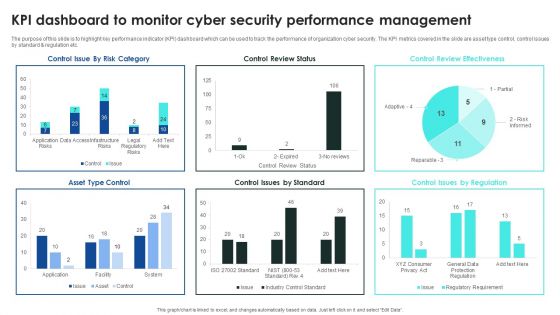
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
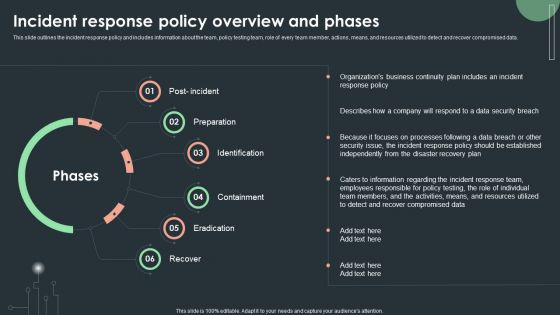
Cybersecurity Guidelines IT Incident Response Policy Overview And Phases Template PDF
This slide outlines the incident response policy and includes information about the team, policy testing team, role of every team member, actions, means, and resources utilized to detect and recover compromised data. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Guidelines IT Incident Response Policy Overview And Phases Template PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Guidelines IT Incident Response Policy Overview And Phases Template PDF.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF from Slidegeeks today.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
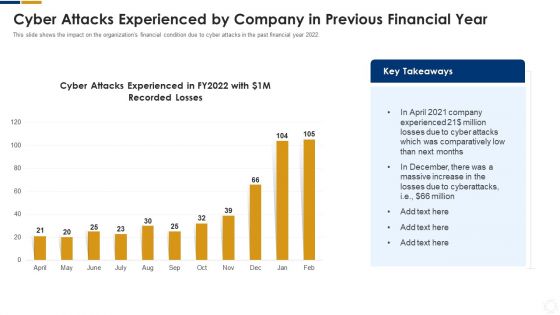
Cybersecurity Cyber Attacks Experienced By Company In Previous Financial Year Ppt Layouts Infographic Template PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver and pitch your topic in the best possible manner with this cybersecurity cyber attacks experienced by company in previous financial year ppt layouts infographic template pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
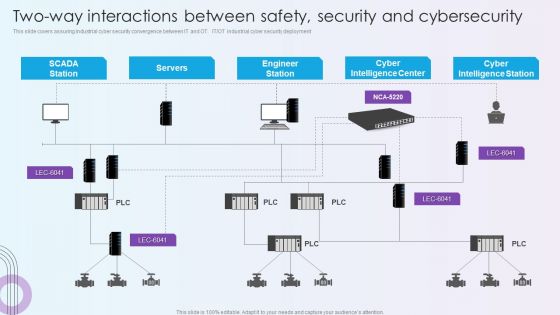
Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF
This slide covers assuring industrial cyber security convergence between IT and OT. IT or OT industrial cyber security deployment. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF. Use them to share invaluable insights on Cyber Intelligence Center, Cyber Intelligence Station, Engineer Station and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Find highly impressive Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF for your upcoming presentation. All the presentation templates are 100 parcent editable and you can change the color and personalize the content accordingly. Download now.

Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Find highly impressive Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
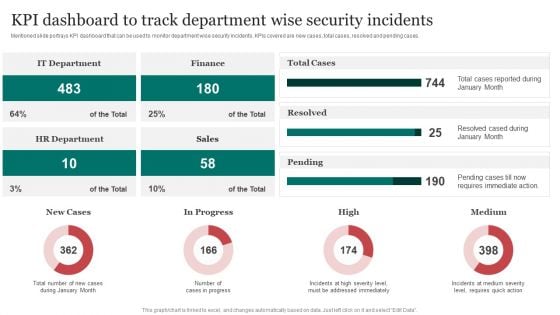
Kpi Dashboard To Track Department Wise Improving Cybersecurity With Incident Guidelines PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.This Kpi Dashboard To Track Department Wise Improving Cybersecurity With Incident Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Kpi Dashboard To Track Department Wise Improving Cybersecurity With Incident Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
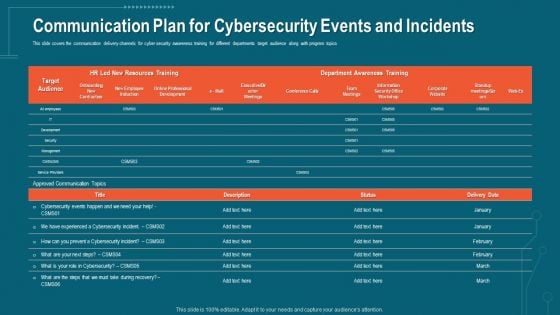
Companys Data Safety Recognition Communication Plan For Cybersecurity Events And Incidents Themes PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative companys data safety recognition communication plan for cybersecurity events and incidents themes pdf bundle. Topics like department awareness training, resources training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
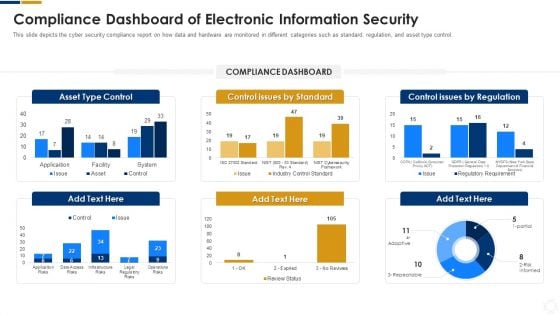
Cybersecurity Compliance Dashboard Of Electronic Information Security Ppt Outline Graphic Tips PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative cybersecurity compliance dashboard of electronic information security ppt outline graphic tips pdf bundle. Topics like compliance dashboard of electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
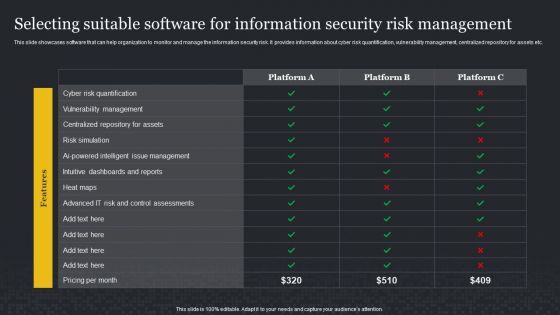
Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Themes PDF
Presenting cybersecurity monitoring plan steps in detail monitoring user activity themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like accidental misuse of systems, regulatory constraints, suspicious activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
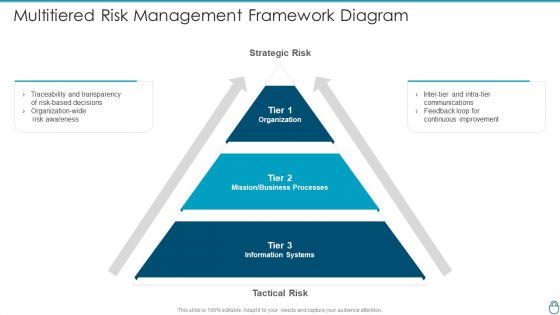
Cybersecurity Risk Administration Plan Multitiered Risk Management Framework Diagram Microsoft PDF
Presenting Cybersecurity Risk Administration Plan Multitiered Risk Management Framework Diagram Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Organization, Mission Or Business Processes, Information Systems In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
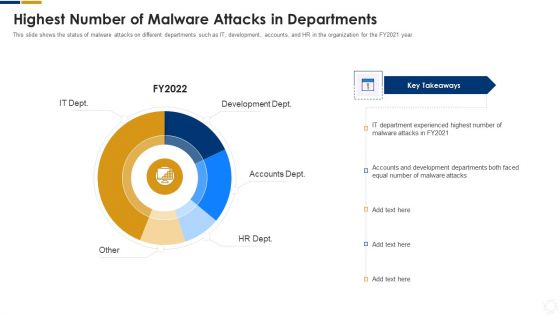
Cybersecurity Highest Number Of Malware Attacks In Departments Ppt Styles Graphic Images PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an awe inspiring pitch with this creative cybersecurity highest number of malware attacks in departments ppt styles graphic images pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Prepare And Deploy Strong IT Policies Ppt Pictures Slides PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this cybersecurity prepare and deploy strong it policies ppt pictures slides pdf. Use them to share invaluable insights on management, device, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
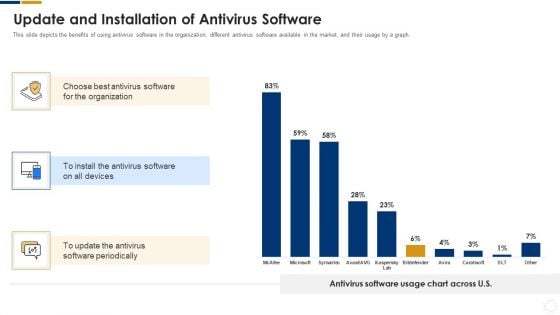
Cybersecurity Update And Installation Of Antivirus Software Ppt Pictures Images PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an awe inspiring pitch with this creative cybersecurity update and installation of antivirus software ppt pictures images pdf bundle. Topics like update and installation of antivirus software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
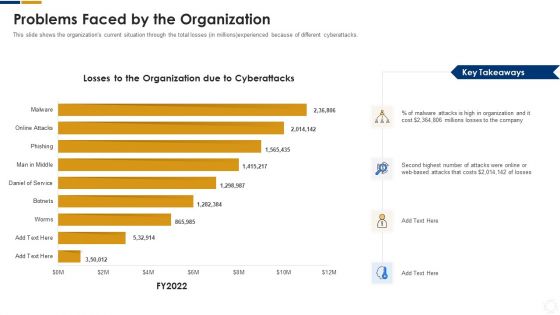
Cybersecurity Problems Faced By The Organization Ppt Portfolio Clipart Images PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative cybersecurity problems faced by the organization ppt portfolio clipart images pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
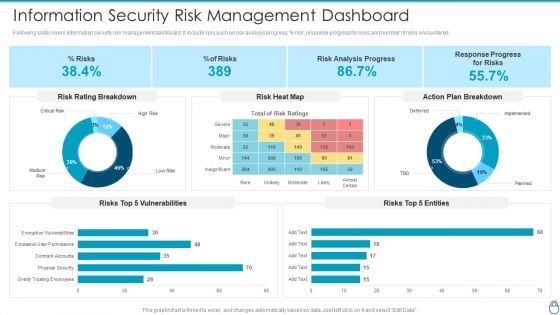
Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
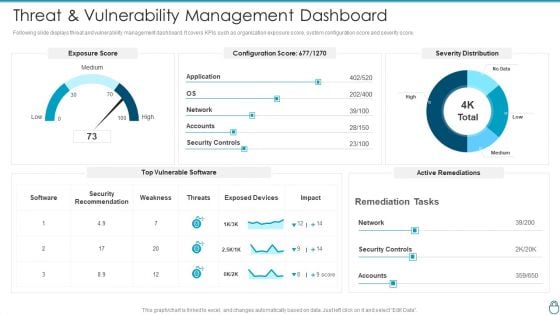
Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF Use them to share invaluable insights on Exposure Score, Remediation Tasks, Severity Distribution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Guidelines IT Data Classification Policy Overview And Approaches Sample PDF
This slide represents the data classification policy overview and approaches. Approaches include highly restricted, restricted, and internal use and types of data each approach will include. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Guidelines IT Data Classification Policy Overview And Approaches Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Guidelines IT Data Classification Policy Overview And Approaches Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
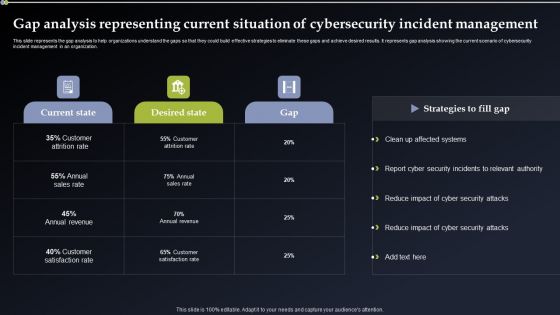
Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Brochure PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF
This slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Are you searching for a Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF from Slidegeeks today.
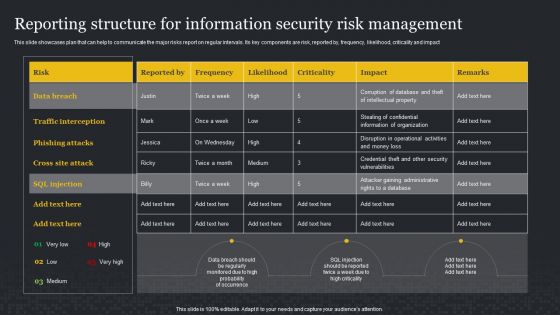
Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
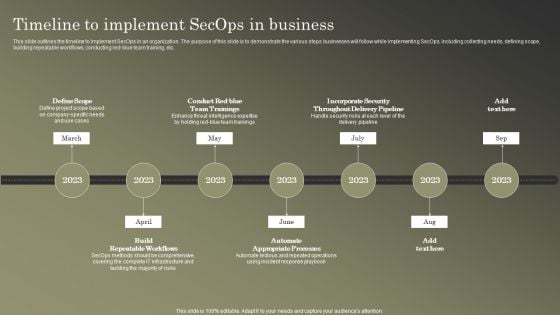
Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF
This slide outlines the timeline to implement SecOps in an organization. The purpose of this slide is to demonstrate the various steps businesses will follow while implementing SecOps, including collecting needs, defining scope, building repeatable workflows, conducting red-blue team training, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
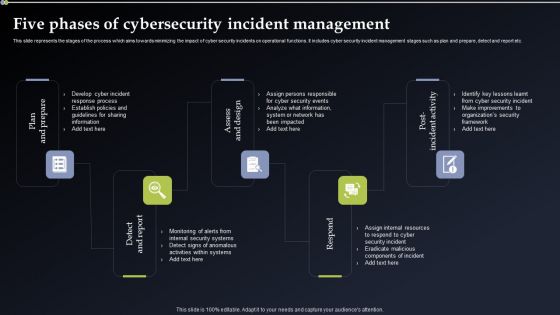
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
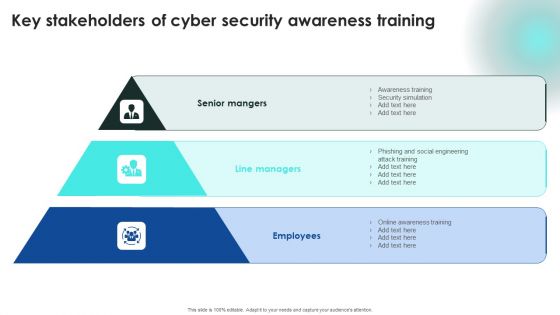
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF
Welcome to our selection of the Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Requirement Of Electronic Information Security In Different Sectors Ppt Slides Summary PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this cybersecurity requirement of electronic information security in different sectors ppt slides summary pdf. Use them to share invaluable insights on financial, organizations, process, information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cybersecurity Dashboard For Threat Tracking In Electronic Information Security Ppt Ideas Graphics PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cybersecurity dashboard for threat tracking in electronic information security ppt ideas graphics pdf bundle. Topics like dashboard for threat tracking in electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
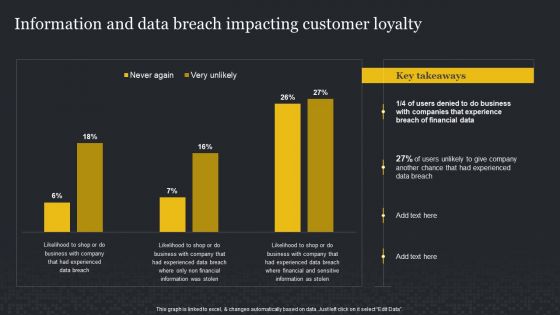
Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF
Retrieve professionally designed Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Asset Criticality Of Identified System Improving Cybersecurity With Incident Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Asset Criticality Of Identified System Improving Cybersecurity With Incident Themes PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Guidelines IT Termination Of Employment And Violation Of Byod Policy Themes PDF
This slide talks about the termination of employment and violation of BYOD policy. Both include the actions to be performed if any employee leaves or violates the BYOD policy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cybersecurity Guidelines IT Termination Of Employment And Violation Of Byod Policy Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
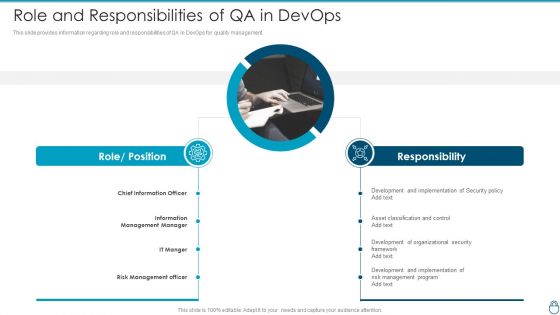
Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF
This slide provides information regarding role and responsibilities of QA in DevOps for quality management. This is a Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development And Implementation, Asset Classification And Control, Development Of Organizational You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
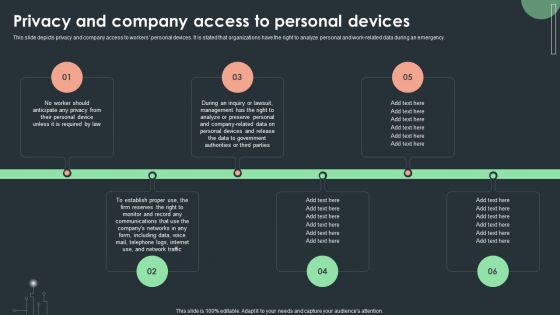
Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF
This slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Want to ace your presentation in front of a live audience Our Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
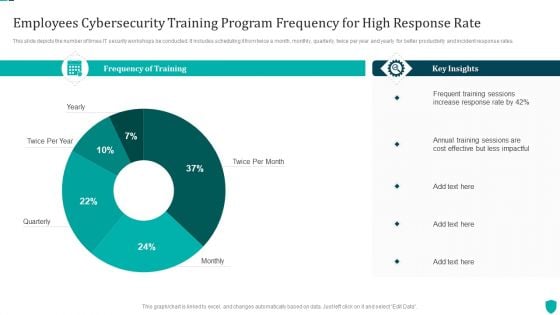
Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF
This slide depicts the number of times IT security workshops be conducted. It includes scheduling it from twice a month, monthly, quarterly, twice per year and yearly for better productivity and incident response rates.Showcasing this set of slides titled Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF. The topics addressed in these templates are Frequency Of Training, Key Insights, Frequent Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF
This slide illustrates impact of security training programs on workforces incident report rate. It includes mass mailed phishing , targeted mails, malware and social media scams.Pitch your topic with ease and precision using this Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF. This layout presents information on Training Sessions, Phishing Identification, Malware Reporting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF
This modern and well arranged Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Implementing Cybersecurity Awareness Program To Prevent Attacks Social Engineering Attack Prevention Techniques Topics PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Social Engineering Attack Prevention Techniques Topics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
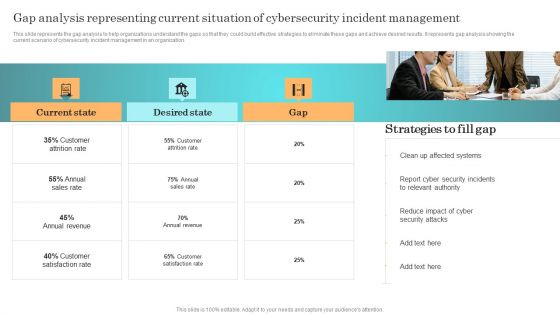
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

 Home
Home