Cybersecurity Icons
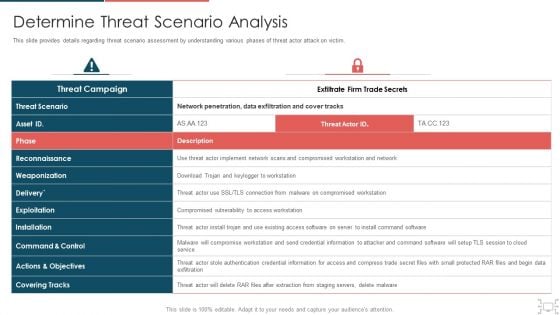
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
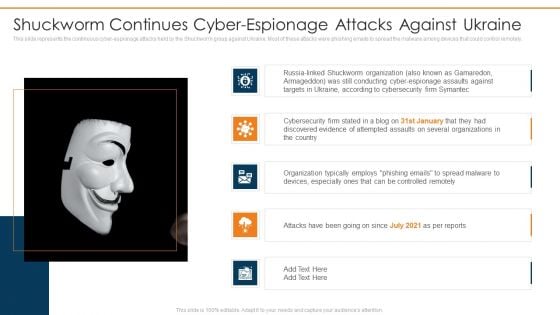
Data Wiper Spyware Attack Shuckworm Continues Cyber Espionage Attacks Against Ukraine Diagrams PDF
This slide represents the continuous cyber-espionage attacks held by the Shuckworm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely.Deliver an awe inspiring pitch with this creative data wiper spyware attack shuckworm continues cyber espionage attacks against ukraine diagrams pdf bundle. Topics like shuckworm continues cyber espionage attacks against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Impact On Organization After Implementing Information Technology Security Strategy And Training Ppt Slides Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this it security impact on organization after implementing information technology security strategy and training ppt slides deck pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
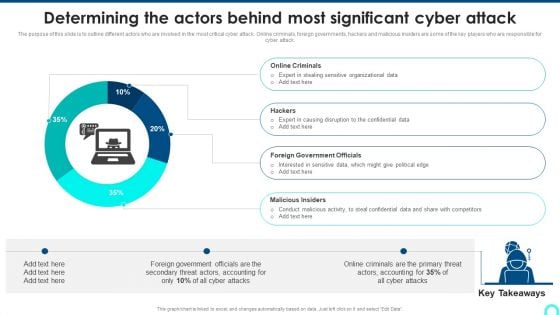
Determining The Actors Behind Most Significant Cyber Attack Download PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver and pitch your topic in the best possible manner with this Determining The Actors Behind Most Significant Cyber Attack Download PDF. Use them to share invaluable insights on Online Criminals, Causing Disruption, Government Officials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Russian Cyber Attacks On Ukraine IT Technical Analysis Of Ddos Attacks Structure PDF
This slide represents the technical analysis of DDoS attacks against Ukrainian websites by showing the internet traffic to the Oschad Bank website on 15-16 February 2022. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it technical analysis of ddos attacks structure pdf bundle. Topics like technical analysis of ddos attacks against ukrainian websites can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
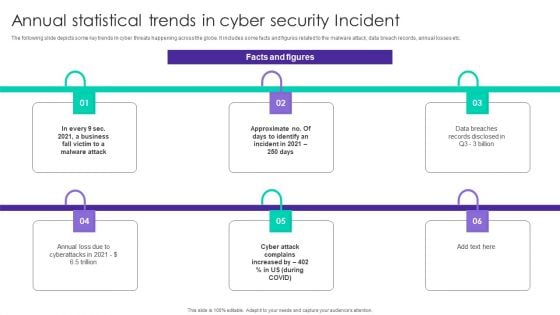
Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
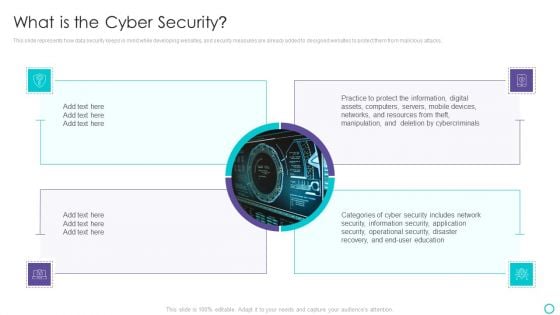
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
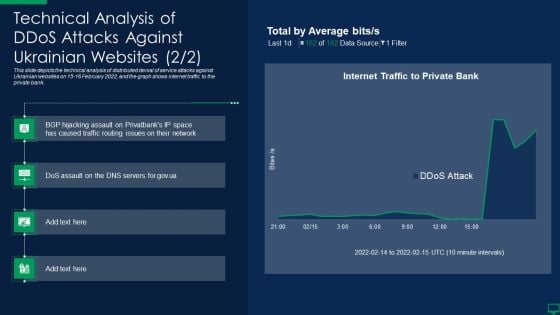
Russian Cyber Attacks On Ukraine IT Technical Analysis Of Ddos Attacks Against Designs PDF
This slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15 16 February 2022, and the graph shows internet traffic to the private bank. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it technical analysis of ddos attacks against designs pdf. Use them to share invaluable insights on technical analysis of ddos attacks against ukrainian websites and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
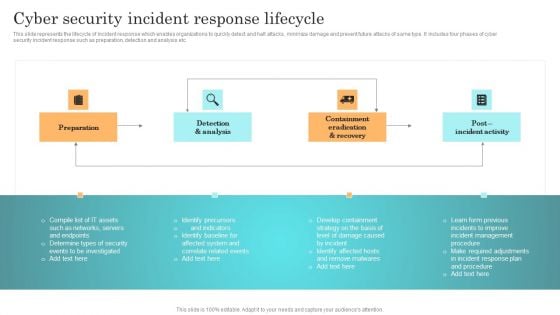
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
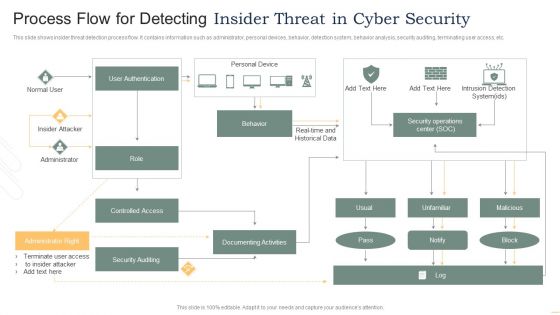
Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
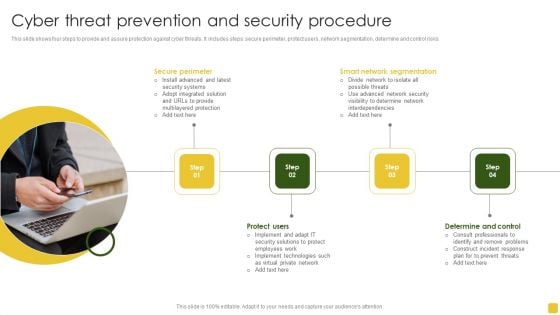
Cyber Threat Prevention And Security Procedure Elements PDF
This slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Presenting Cyber Threat Prevention And Security Procedure Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Control, Smart Network Segmentation, Secure Perimeter. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
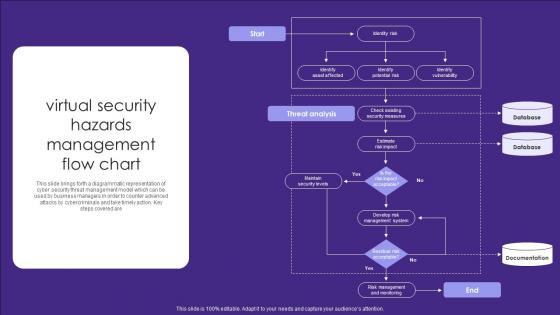
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are
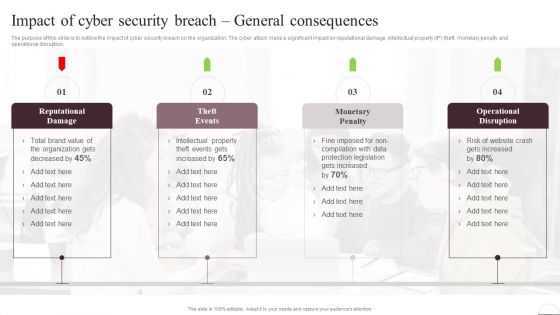
Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
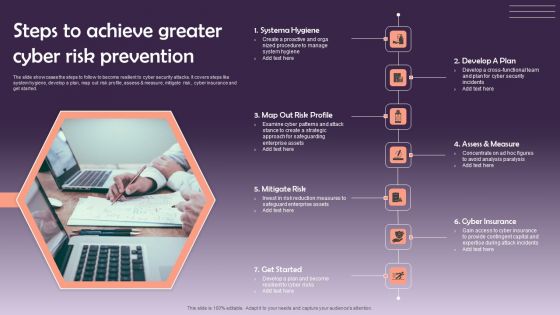
Steps To Achieve Greater Cyber Risk Prevention Infographics PDF
The slide showcases the steps to follow to become resilient to cyber security attacks. It covers steps like system hygiene, develop a plan, map out risk profile, assess and measure, mitigate risk, cyber insurance and get started. Presenting Steps To Achieve Greater Cyber Risk Prevention Infographics PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Systema Hygiene, Develop A Plan, Mitigate Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
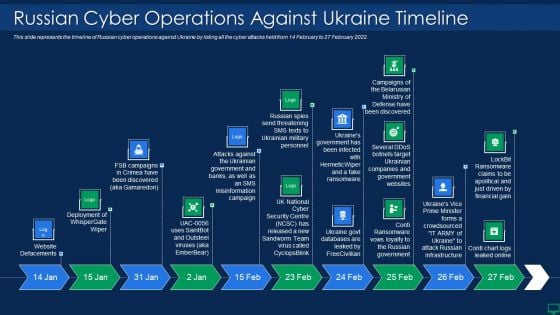
Russian Cyber Attacks On Ukraine IT Russian Cyber Operations Against Themes PDF
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. This is a russian cyber attacks on ukraine it russian cyber operations against themes pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like russian cyber operations against ukraine timeline. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Loss Due To Different Cyber Attacks Designs PDF
This slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative cyber exploitation it loss due to different cyber attacks designs pdf bundle. Topics like loss due to different cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
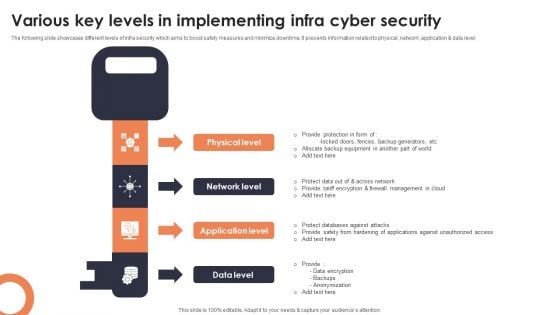
Various Key Levels In Implementing Infra Cyber Security Mockup PDF
The following slide showcases different levels of infra security which aims to boost safety measures and minimize downtime. It presents information related to physical, network, application and data level. Presenting Various Key Levels In Implementing Infra Cyber Security Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Physical Level, Network Level, Application Level. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
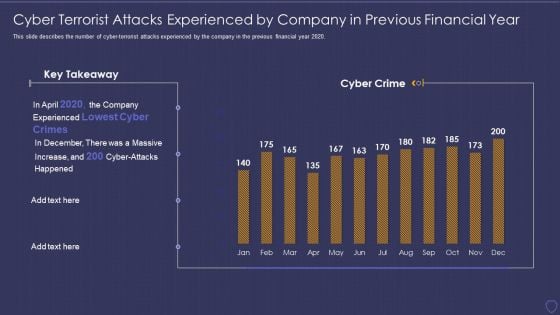
Global Cyber Terrorism Incidents On The Rise IT Cyber Terrorist Attacks Experienced Formats PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2020. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it cyber terrorist attacks experienced formats pdf bundle. Topics like cyber terrorist attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
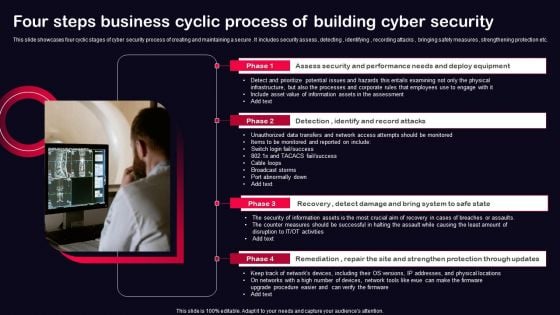
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
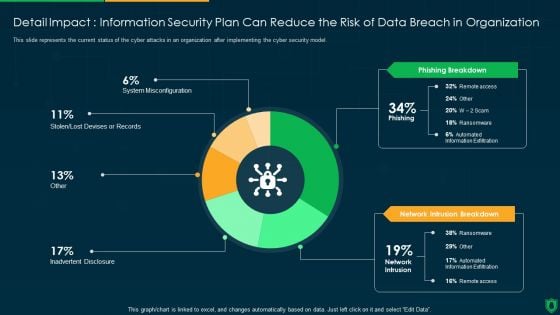
Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
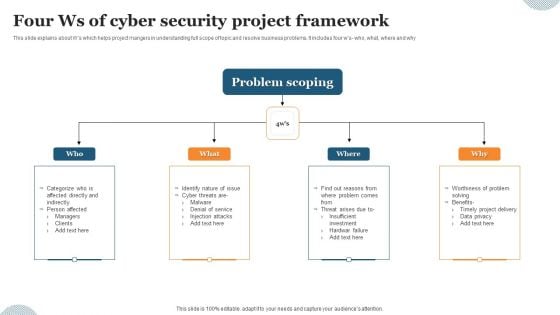
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Laptop With Key And Chain Attached Success PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key And Chain Attached Success PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our Technology PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Download our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time.Use these PowerPoint slides for presentations relating to Laptop and key, business, computer, security, network diagrams, technology. The prominent colors used in the PowerPoint template are Yellows, Gray, Black. Achieve that festive atmosphere you desire. Festoon your address with our Laptop With Key And Chain Attached Success PowerPoint Templates Ppt Backgrounds For Slides 0213.

Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF
This slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Retrieve professionally designed Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
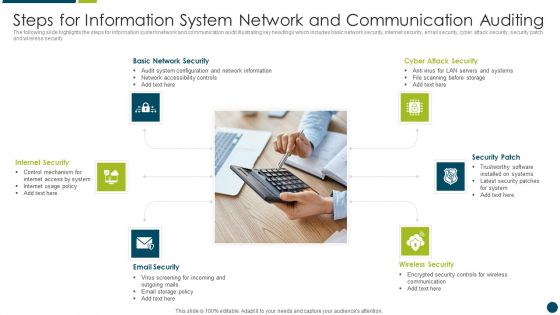
Steps For Information System Network And Communication Auditing Topics PDF
The following slide highlights the steps for information system network and communication audit illustrating key headings which includes basic network security, internet security, email security, cyber attack security, security patch and wireless security Presenting Steps For Information System Network And Communication Auditing Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Basic Network Security, Internet Security, Security Patch. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
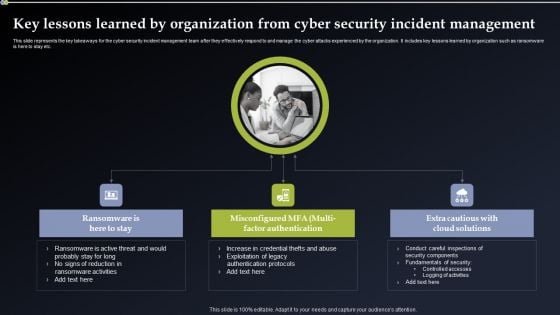
Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF can be your best option for delivering a presentation. Represent everything in detail using Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
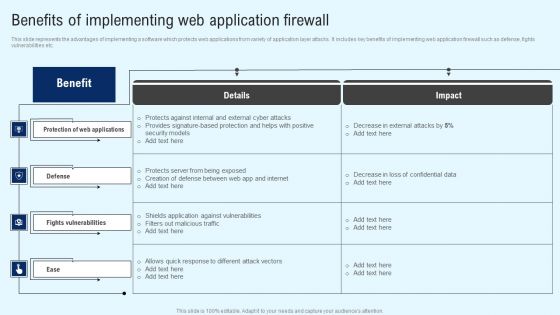
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
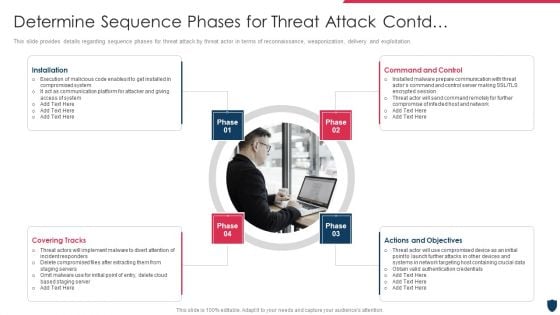
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
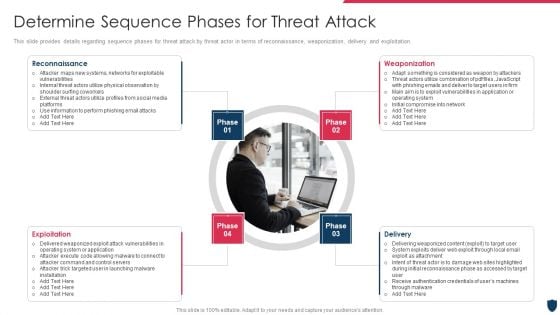
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
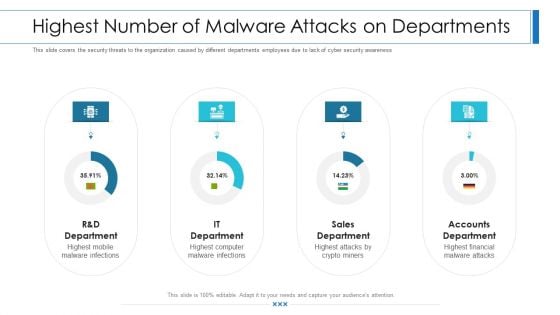
Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
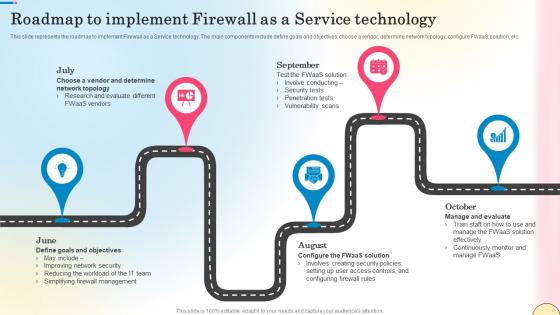
Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf
This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
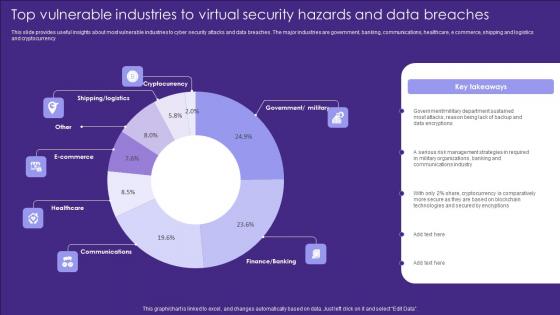
Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf
This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Pitch your topic with ease and precision using this Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf. This layout presents information on Cryptocurrency, Ecommerce, Healthcare. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency
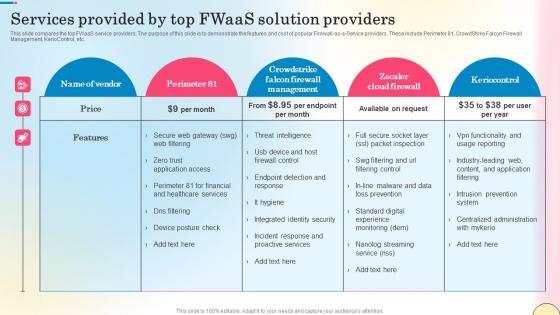
Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf
This slide compares the top FWaaS service providers. The purpose of this slide is to demonstrate the features and cost of popular Firewall-as-a-Service providers. These include Perimeter 81, CrowdStrike Falcon Firewall Management, KerioControl, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide compares the top FWaaS service providers. The purpose of this slide is to demonstrate the features and cost of popular Firewall-as-a-Service providers. These include Perimeter 81, CrowdStrike Falcon Firewall Management, KerioControl, etc.
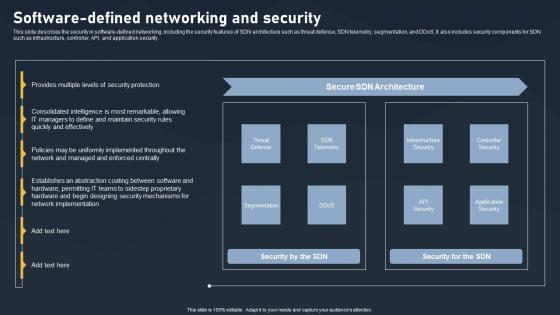
Software Defined Networking And Security SDN Building Blocks Portrait Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking And Security SDN Building Blocks Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking And Security SDN Building Blocks Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.

Secure Internet Browser PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secure Internet Browser PowerPoint Templates PPT Backgrounds For Slides 0313.Use our Network diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Technology PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script.Use these PowerPoint slides for presentations relating to Secure Internet Browser, network diagrams, security, technology, signs, shapes. The prominent colors used in the PowerPoint template are Gray, Yellow, Black. Take flight with our Secure Internet Browser PowerPoint Templates Ppt Backgrounds For Slides 0313. Just download, type and present.
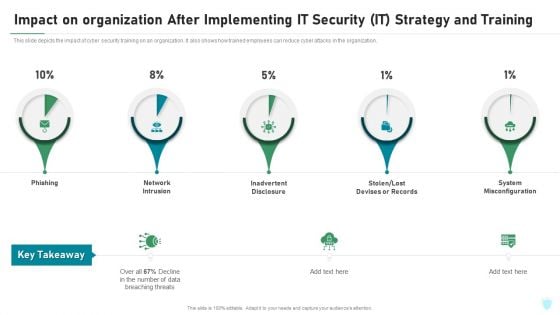
Impact On Organization After Implementing IT Security IT Strategy And Training Ppt File Portrait PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing it security it strategy and training ppt file portrait pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure, stolen or lost devises or records, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
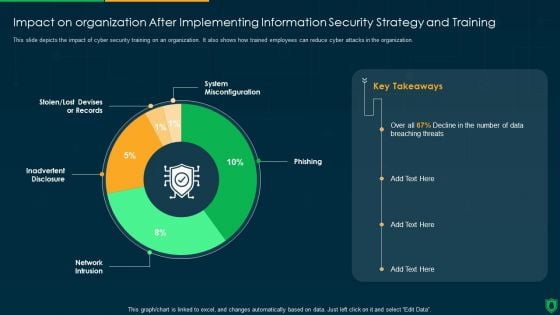
Impact On Organization After Implementing Information Security Strategy Ppt PowerPoint Presentation Gallery Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information security strategy ppt powerpoint presentation gallery deck pdf. Use them to share invaluable insights on system misconfiguration, phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
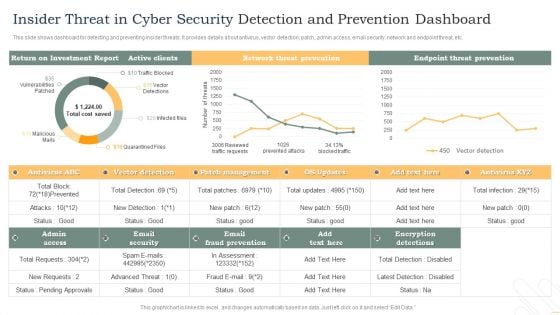
Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
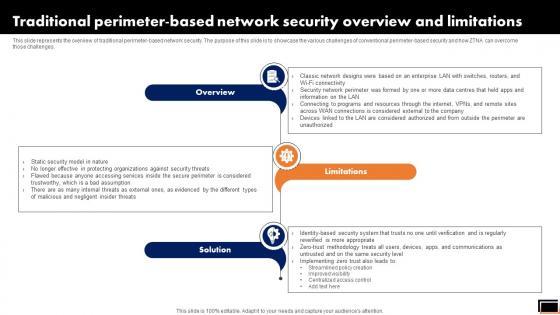
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Laptop With Lock Information Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Lock Information Security PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Use our Technology PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Download our Security PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Use our Network Diagrams PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to 3d illustration of laptop with lock, business, computer, security, network diagrams, technology . The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. Your career will soar away. Our Laptop With Lock Information Security PowerPoint Templates Ppt Backgrounds For Slides 0213 will give it wings.

Laptop With Security Key Savings PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Security Key Savings PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Computer PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Download our Technology PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Download our Security PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Download and present our Network Diagrams PowerPoint Templates because You can safely bank on our PowerPoint Templates and Slides. They will provide a growth factor to your valuable thoughts. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind.Use these PowerPoint slides for presentations relating to Key and a Laptop, business, computer, security, network diagrams, technology . The prominent colors used in the PowerPoint template are Blue, Gray, Red. Improve your organization with our Laptop With Security Key Savings PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.
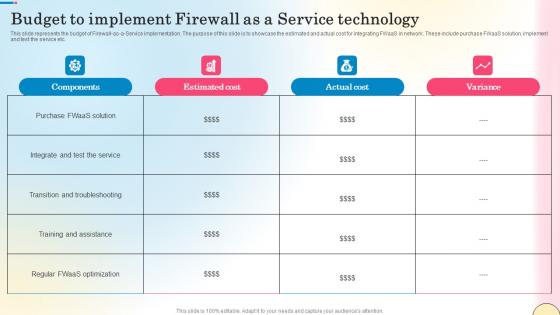
Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf
This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc. Get a simple yet stunning designed Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc.

Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Network Diagrams PowerPoint Templates because It can Bubble and burst with your ideas. Use our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download and present our Signs PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience.Use these PowerPoint slides for presentations relating to One notebook with a login screen and a credit card, computer, technology, network diagrams, security, signs. The prominent colors used in the PowerPoint template are Blue, Gray, White. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Use our screen PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Customers tell us our with PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are second to none. People tell us our credit PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Evoke desires with our Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will have them enraptured.
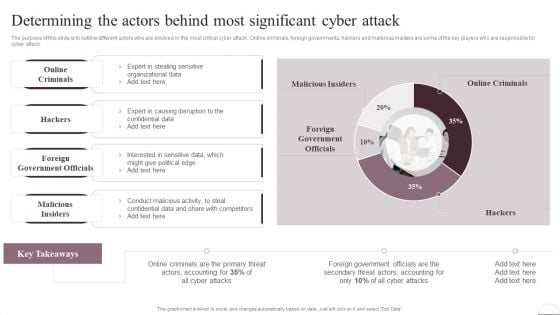
Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Illustration Depicting Brass Key On Laptop PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are designed to help you succeed. They have all the ingredients you need. Present our Technology PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download and present our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one.Use these PowerPoint slides for presentations relating to A pair of Keys and a Laptop, computer, technology, security, network diagrams, success. The prominent colors used in the PowerPoint template are Blue navy, Black, Red. Professionals tell us our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our and PowerPoint templates and PPT Slides are designed by professionals You can be sure our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our and PowerPoint templates and PPT Slides are designed by professionals We assure you our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113 will get their audience's attention. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides will impress their bosses and teams. Our Illustration Depicting Brass Key On Laptop PowerPoint Templates Ppt Backgrounds For Slides 0113 are eclectic by nature. They are acceptable to different cultures.

Cyber Terrorism Assault IT Infrastructure Cyber Security Budget Against Cyber Terrorism FY19 20 Themes PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault it infrastructure cyber security budget against cyber terrorism fy19 20 themes pdf Use them to share invaluable insights on cloud security, integrated risk management, identify access management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Stock Photo 3d Globe With Social Web For Data Protection Concept PowerPoint Slide
Graphic of 3d globe and web has been used to craft this power point image template. This PPT contains the concept of data protection and social network. Use this PPT and build quality presentation for your viewers.
Stock Photo Yellow Folders And Server On It For Data Storage Image Graphics For PowerPoint Slide
This image slide displays yellow folder with computer server for technology. This image slide has been designed with graphic of computer server on yellow data folder. Use this image, in your presentations to express views on client server, computing, data storage and backup. This image will enhance the quality of your presentations.

Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Technology PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Internet PowerPoint Templates because It can Bubble and burst with your ideas. Use our Computer PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download and present our Shapes PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download our Network diagrams PowerPoint Templates because You should Press the right buttons with our PowerPoint Templates and Slides. They will take your ideas down the perfect channel.Use these PowerPoint slides for presentations relating to protect your computer, security concept, network diagrams, technology, computer, internet, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. PowerPoint presentation experts tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our network PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. You can be sure our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our computer PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Presenters tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our security PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Publicize your views with our Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
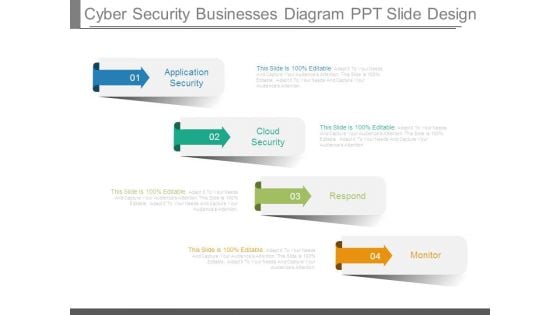
Cyber Security Businesses Diagram Ppt Slide Design
This is a cyber security businesses diagram ppt slide design. This is a four stage process. The stages in this process are application security, cloud security, respond, monitor.
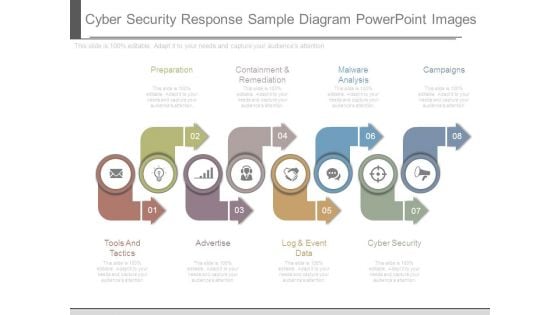
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.

Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.

Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf today and make your presentation stand out from the rest This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data.
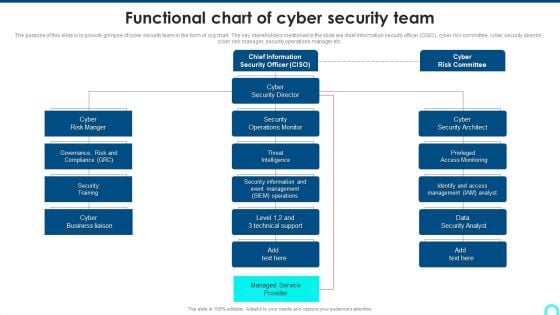
Functional Chart Of Cyber Security Team Diagrams PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc.Deliver an awe inspiring pitch with this creative Functional Chart Of Cyber Security Team Diagrams PDF bundle. Topics like Access Monitoring, Security Architect, Security Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security
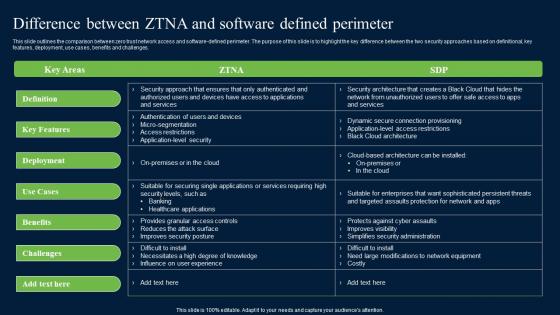
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
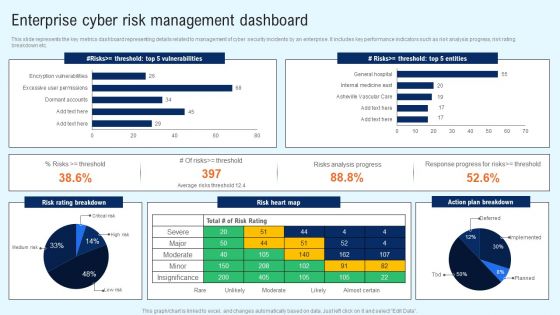
Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
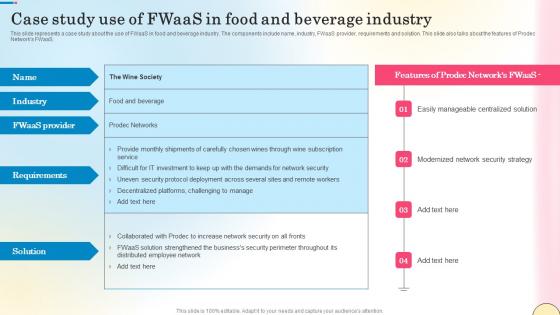
Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf
This slide represents a case study about the use of FWaaS in food and beverage industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the features of Prodec Networks FWaaS. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf can be your best option for delivering a presentation. Represent everything in detail using Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents a case study about the use of FWaaS in food and beverage industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the features of Prodec Networks FWaaS.
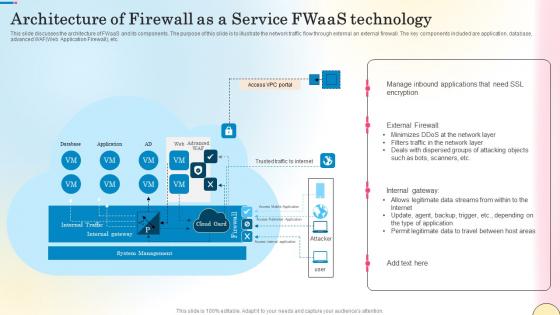
Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf
This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Want to ace your presentation in front of a live audience Our Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc.
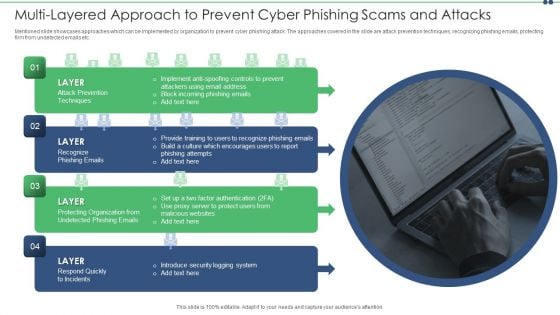
Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
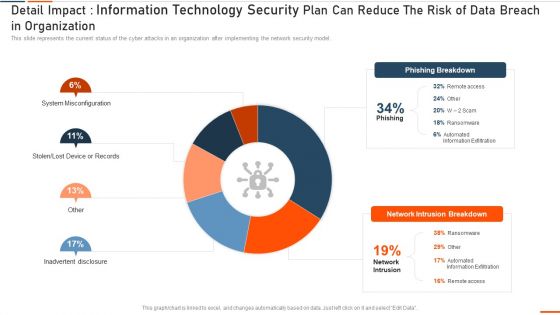
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc.
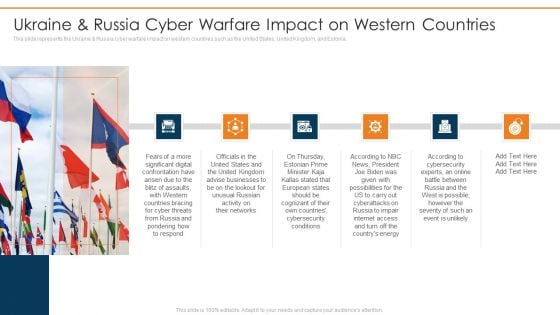
Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Impact On Western Countries Themes PDF
This slide represents the Ukraine and Russia cyber warfare impact on western countries such as the United States, United Kingdom, and Estonia.Deliver an awe inspiring pitch with this creative data wiper spyware attack ukraine and russia cyber warfare impact on western countries themes pdf bundle. Topics like united kingdom advise, businesses lookout for unusual, russian activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
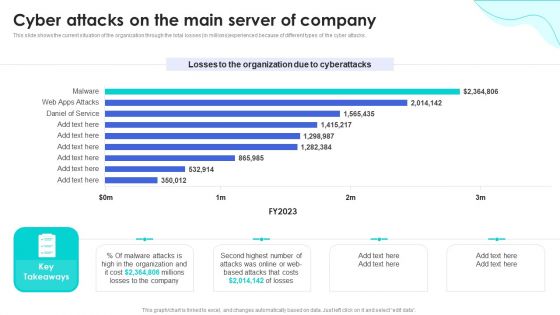
Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF
This slide shows the current situation of the organization through the total losses in millions experienced because of different types of the cyber attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF can be your best option for delivering a presentation. Represent everything in detail using Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Phishing Scams And Attacks Dashboard With Improvement Curve Sample PDF
Mentioned slide showcases a comprehensive dashboard used to measure the cyber phishing attacks. Information covered in this slide is related to organization health risk, attack vendors, most vulnerable employees to attacks, improvement curve. Pitch your topic with ease and precision using this cyber phishing scams and attacks dashboard with improvement curve sample pdf. This layout presents information on cyber phishing scams and attacks dashboard with improvement curve. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
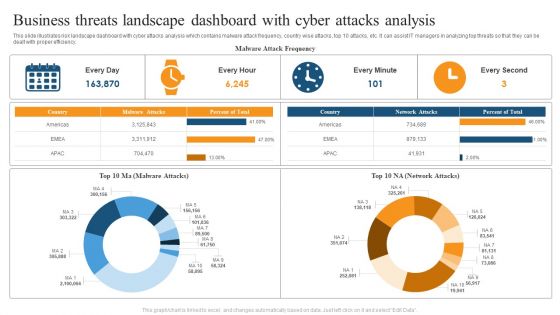
Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF
This slide illustrates risk landscape dashboard with cyber attacks analysis which contains malware attack frequency, country wise attacks, top 10 attacks, etc. It can assist IT managers in analyzing top threats so that they can be dealt with proper efficiency. Pitch your topic with ease and precision using this Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF. This layout presents information on Malware Attack Frequency, Every Minute, Every Second. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
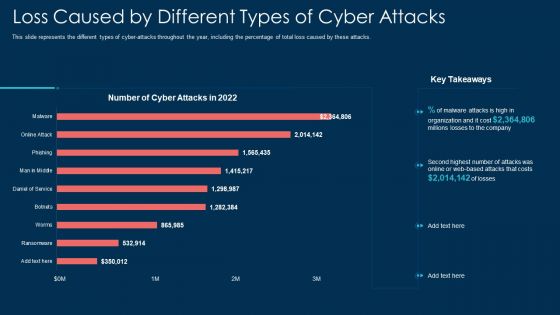
Loss Caused By Different Types Of Cyber Attacks Ppt File Good PDF
This slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative loss caused by different types of cyber attacks ppt file good pdf bundle. Topics like organization, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
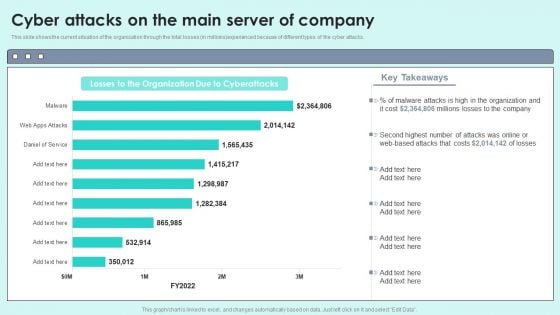
Cyber Attacks On The Main Server Of Company Reverse Proxy For Load Balancing Mockup PDF
This slide shows the current situation of the organization through the total losses in millionsexperienced because of different types of the cyber attacks.Deliver an awe inspiring pitch with this creative Cyber Attacks On The Main Server Of Company Reverse Proxy For Load Balancing Mockup PDF bundle. Topics like Losses Organization, Due Cyberattacks, Based Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
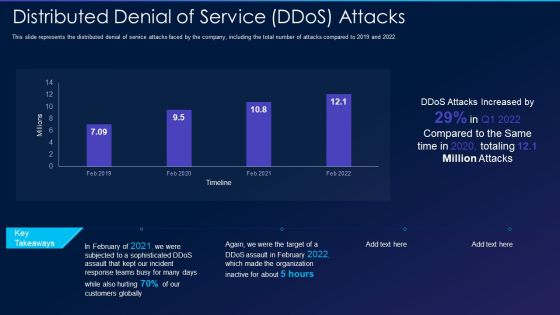
Cyber Exploitation IT Distributed Denial Of Service Ddos Attacks Professional PDF
This slide represents the distributed denial of service attacks faced by the company, including the total number of attacks compared to 2019 and 2022. Deliver and pitch your topic in the best possible manner with this cyber exploitation it distributed denial of service ddos attacks professional pdf. Use them to share invaluable insights on distributed denial of service ddos attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
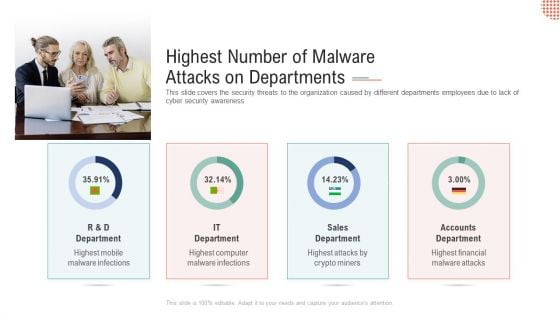
Highest Number Of Malware Attacks On Departments Ppt Inspiration Deck PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver an awe-inspiring pitch with this creative highest number of malware attacks on departments ppt inspiration deck pdf. bundle. Topics like r ans d department, sales department, accounts department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
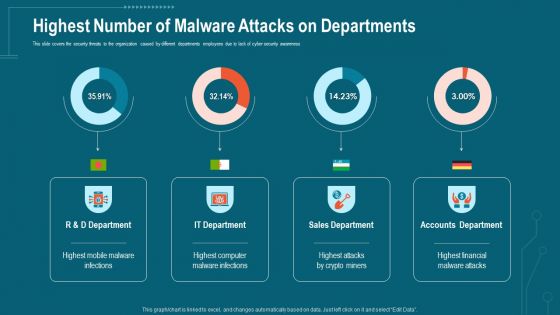
Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
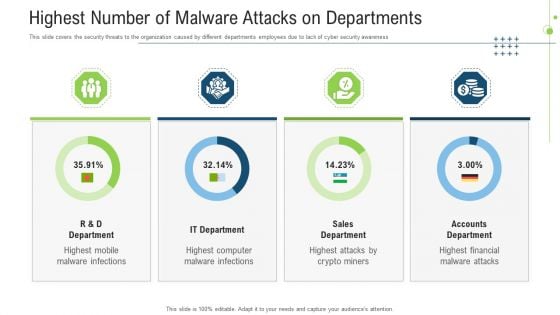
Highest Number Of Malware Attacks On Departments Ppt Gallery Ideas PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative highest number of malware attacks on departments ppt gallery ideas pdf bundle. Topics like accounts department, sales department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
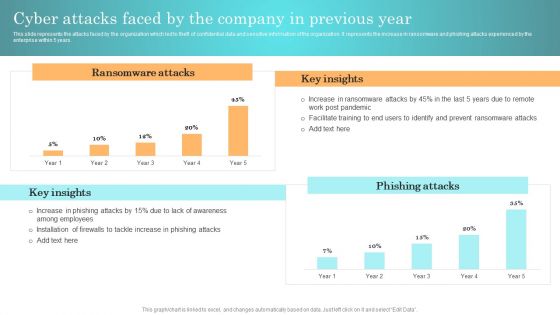
Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
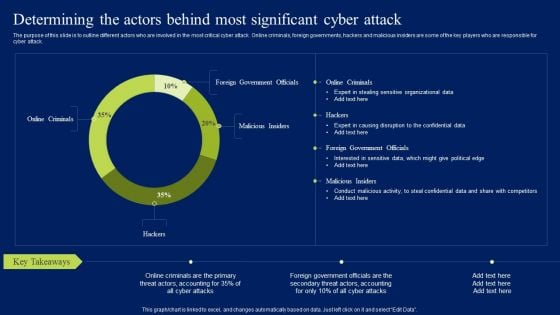
Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Want to ace your presentation in front of a live audience Our Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
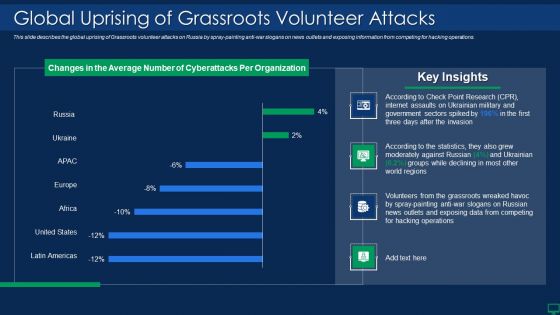
Russian Cyber Attacks On Ukraine IT Global Uprising Of Grassroots Microsoft PDF
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it global uprising of grassroots microsoft pdf bundle. Topics like internet, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
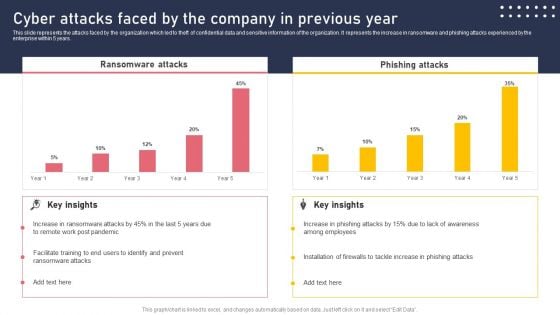
Cyber Attacks Faced By The Company In Previous Year Portrait PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Attacks Faced By The Company In Previous Year Portrait PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
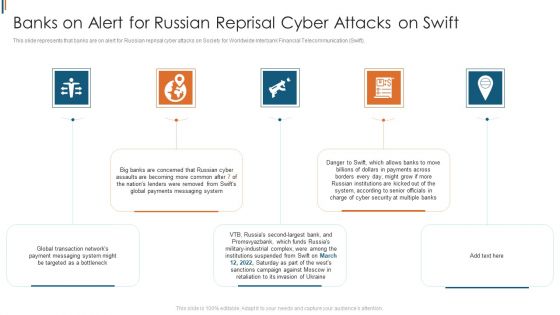
Ukraine Cyberwarfare Banks On Alert For Russian Reprisal Cyber Attacks On Swift Diagrams Pdf
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a ukraine cyberwarfare banks on alert for russian reprisal cyber attacks on swift diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global transaction networks payment messaging system might be targeted as a bottleneck, big banks are concerned that russian cyber assaults are becoming more common after seven of the nations, lenders were removed from swifts global payments messaging system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
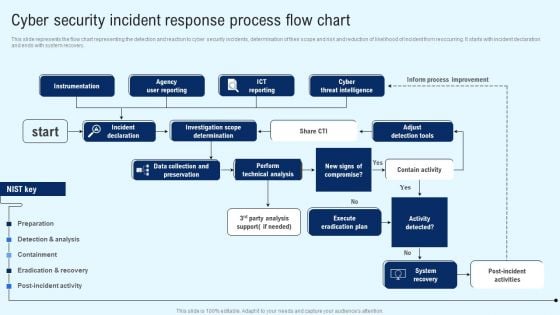
Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Explore a selection of the finest Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
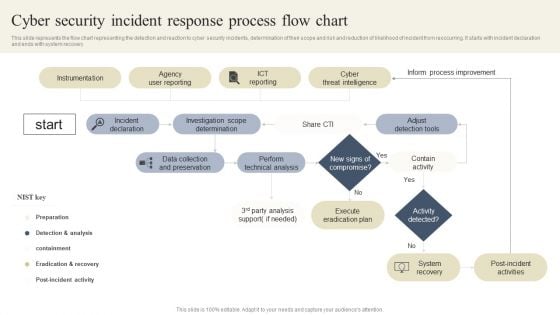
CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
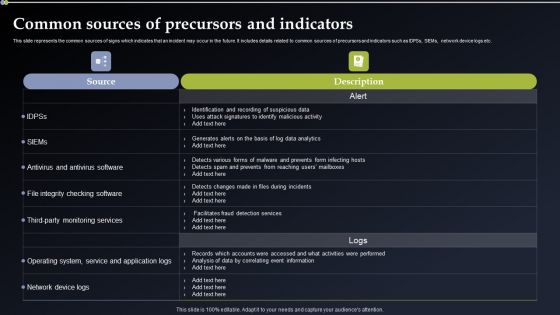
Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
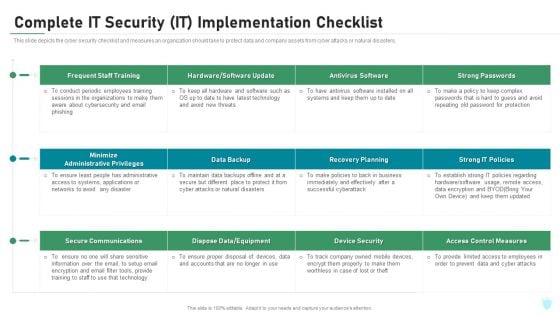
Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
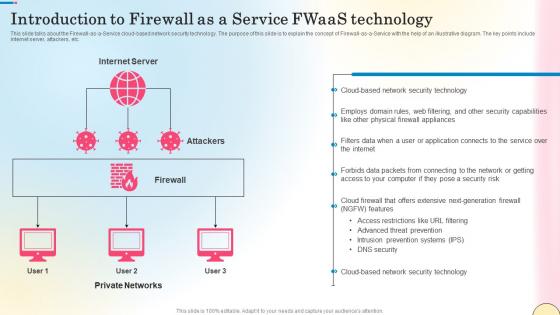
Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf
This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc. Retrieve professionally designed Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc.
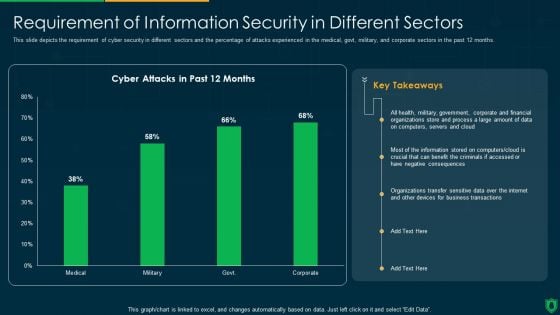
Info Security Requirement Of Information Security In Different Sectors Ppt PowerPoint Presentation File Grid PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative info security requirement of information security in different sectors ppt powerpoint presentation file grid pdf bundle. Topics like cyber attacks, past 12 months, organizations transfer, sensitive data over internet can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Access To Protect Cyber Threat System Ppt PowerPoint Presentation Visual Aids Diagrams PDF
Presenting security access to protect cyber threat system ppt powerpoint presentation visual aids diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security access to protect cyber threat system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
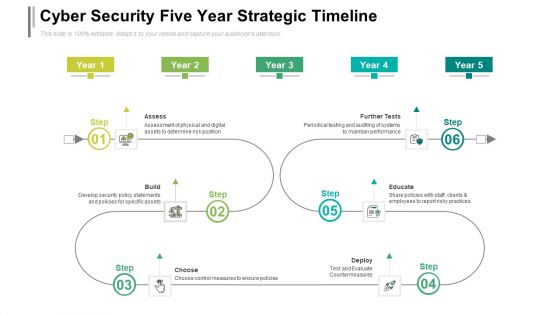
Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
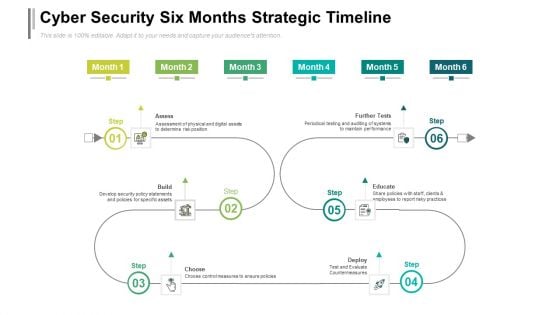
Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
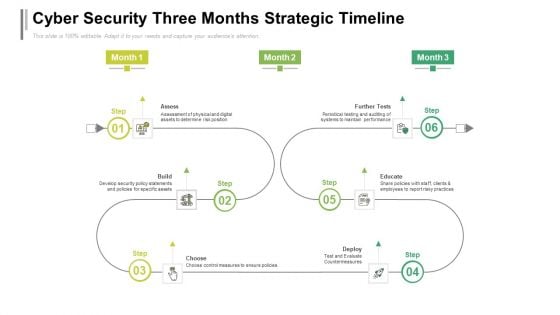
Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
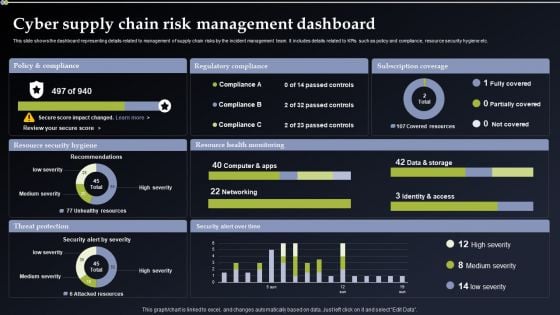
Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF today and make your presentation stand out from the rest.
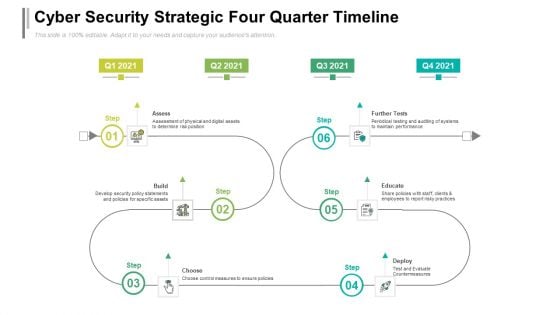
Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
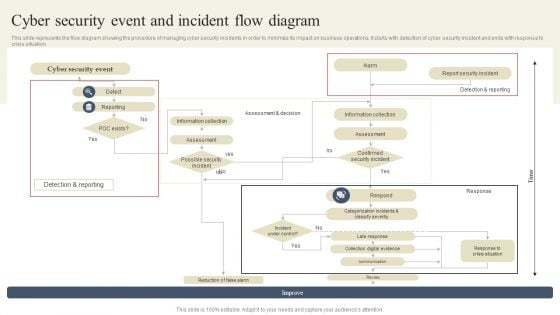
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Implementing Cyber Security Incident Cyber Security Incident Handler Contact Information Diagrams PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Want to ace your presentation in front of a live audience Our Implementing Cyber Security Incident Cyber Security Incident Handler Contact Information Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
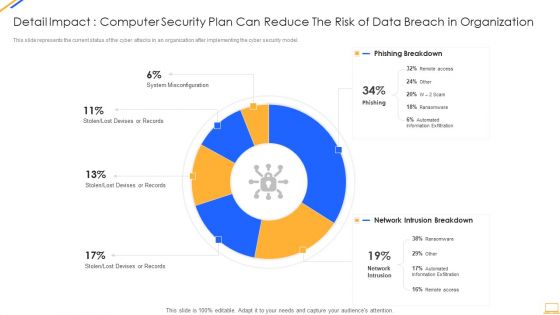
Desktop Security Management Detail Impact Computer Designs PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this desktop security management detail impact computer designs pdf. Use them to share invaluable insights on detail impact computer security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
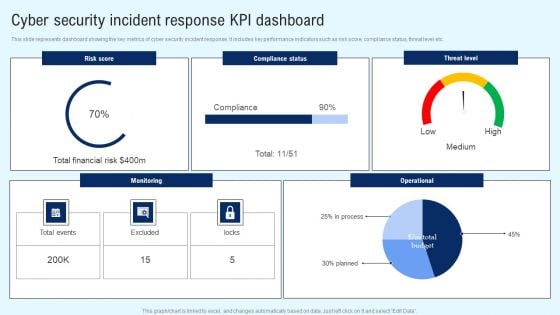
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
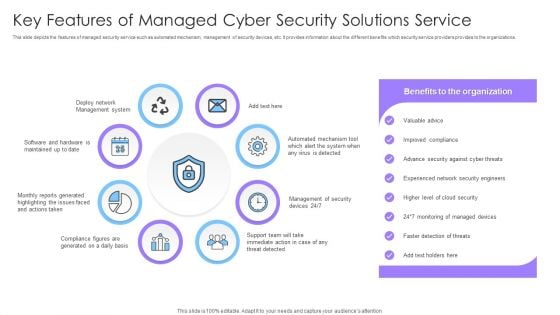
Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
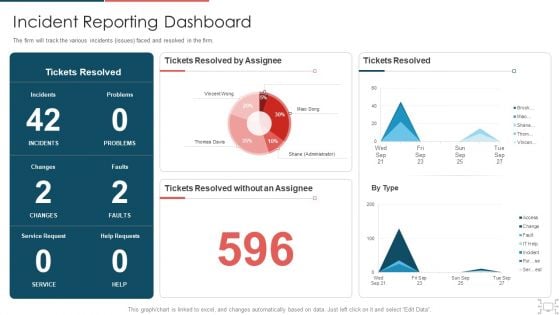
Cyber Security Administration In Organization Incident Reporting Dashboard Diagrams PDF
The firm will track the various incidents issues faced and resolved in the firm. Deliver an awe inspiring pitch with this creative cyber security administration in organization incident reporting dashboard diagrams pdf bundle. Topics like incident reporting dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
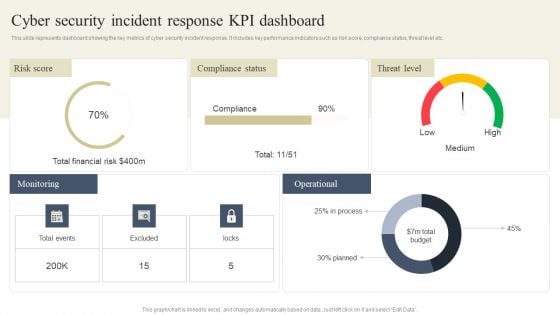
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
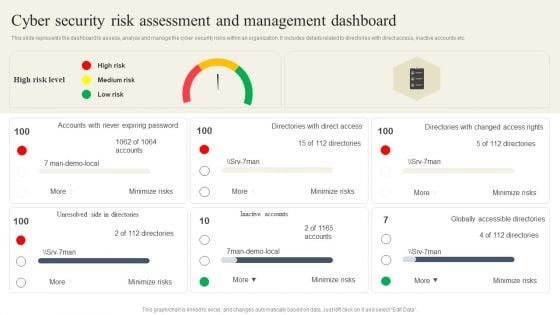
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
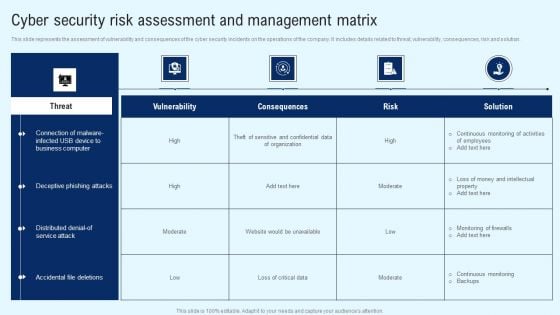
Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Get a simple yet stunning designed Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
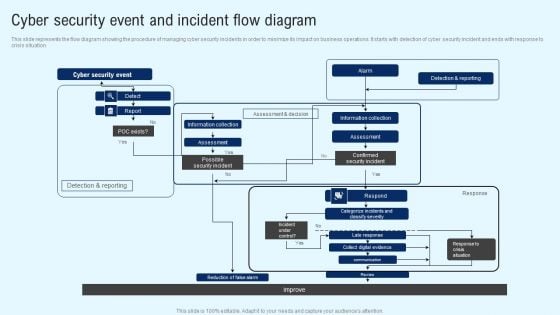
Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
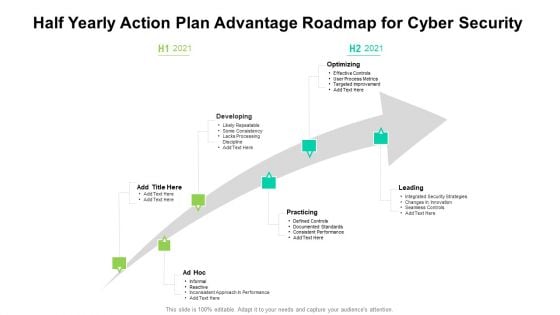
Half Yearly Action Plan Advantage Roadmap For Cyber Security Themes
We present our half yearly action plan advantage roadmap for cyber security themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly action plan advantage roadmap for cyber security themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
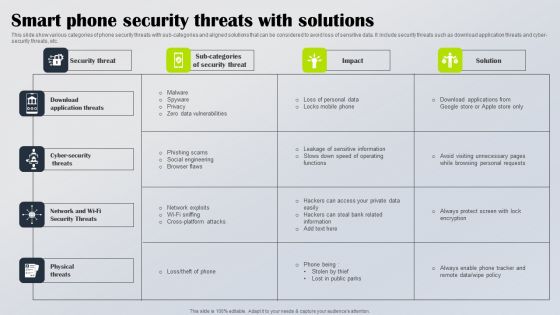
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
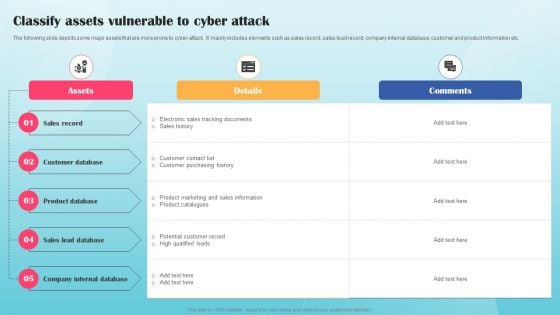
Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF
The following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. If you are looking for a format to display your unique thoughts, then the professionally designed Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
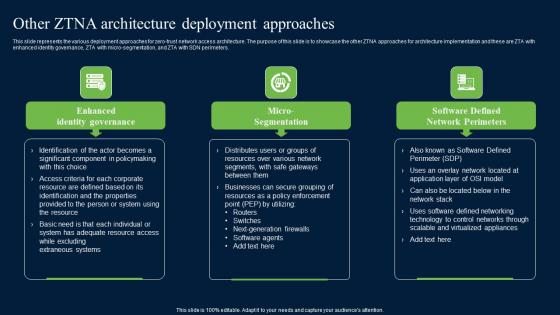
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
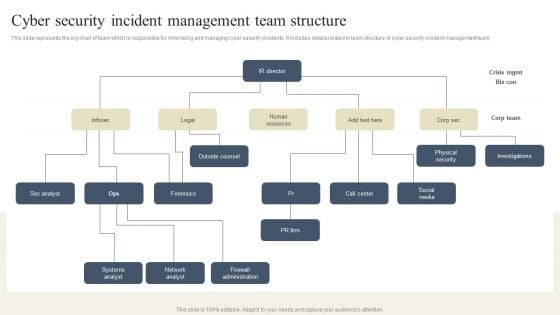
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
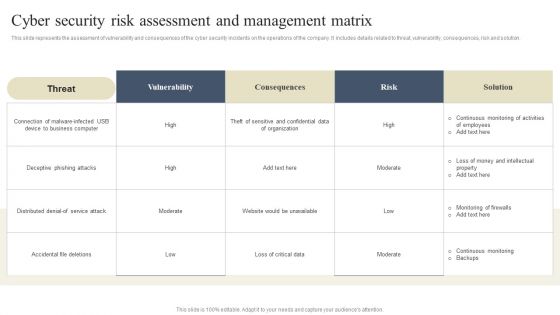
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
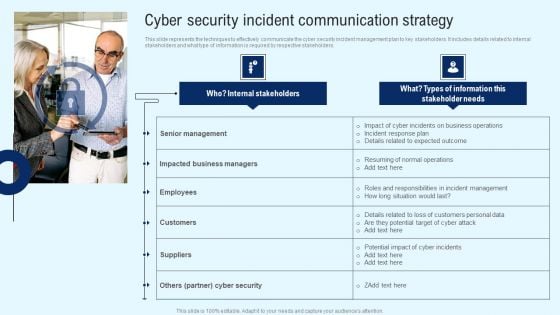
Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
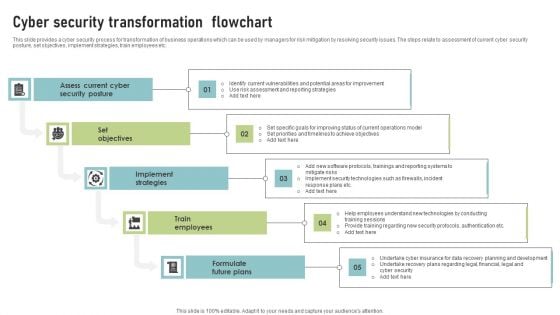
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
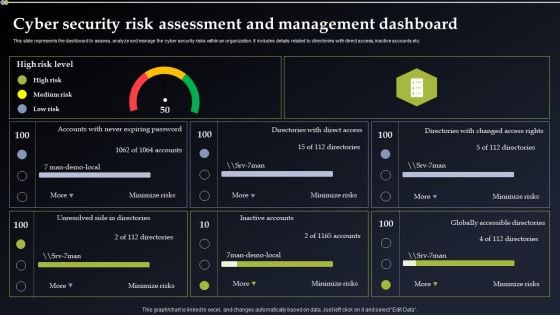
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
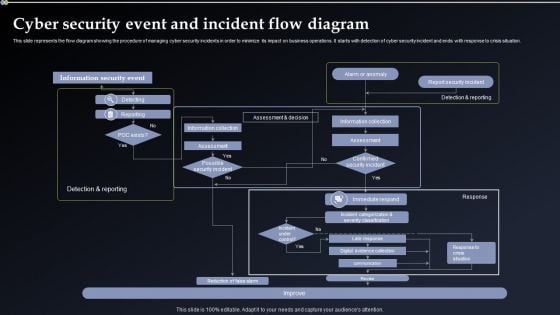
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

 Home
Home