Cybersecurity Icons
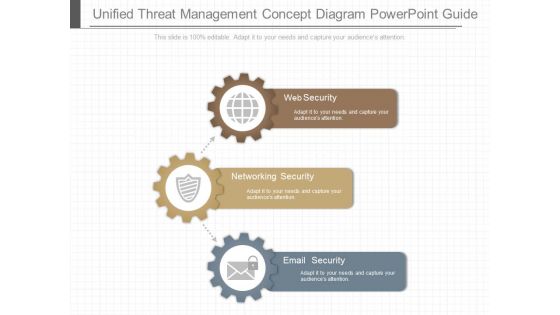
Unified Threat Management Concept Diagram Powerpoint Guide
This is a unified partnership in corporate development ppt powerpoint guide. This is a three stage process. The stages in this process are web security, networking security, email security.
Business Diagram Chart Hexagon PowerPoint Templates Backgrounds For Slides
We present our business diagram chart hexagon PowerPoint templates backgrounds for slides.Use our Hexagon PowerPoint Templates because Our Template designs are State of the Art. Download our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Marketing PowerPoint Templates because The marketplace is the merger of your dreams and your ability. Download our Process and Flows PowerPoint Templates because it shows the pyramid which is a symbol of the desire to reach the top in a steady manner. Use our Shapes PowerPoint Templates because you have good reasons to back up the strength of your belief.Use these PowerPoint slides for presentations relating to Attached, Backgrounds, Blue, Cell, Color, Component, Connect, Connection, Diagram, Elements, Geometric, Graphic, Group, Hexagon, Honeycomb, Icon, Illustration, Intricacy, Lines, Link, Map, Mesh, Model, Network, Science, Shape, Shiny, Strategy, Structure, Symbol, Teamwork, Technology. The prominent colors used in the PowerPoint template are Yellow, White, Gray. PowerPoint presentation experts tell us our business diagram chart hexagon PowerPoint templates backgrounds for slides are Elegant. Professionals tell us our Cell PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our business diagram chart hexagon PowerPoint templates backgrounds for slides have awesome images to get your point across. We assure you our Blue PowerPoint templates and PPT Slides are Fancy. PowerPoint presentation experts tell us our business diagram chart hexagon PowerPoint templates backgrounds for slides are Endearing. Professionals tell us our Blue PowerPoint templates and PPT Slides are Liberated. Our Business Diagram Chart Hexagon PowerPoint Templates Backgrounds For Slides are academically capable. They make learning a lot more fun.
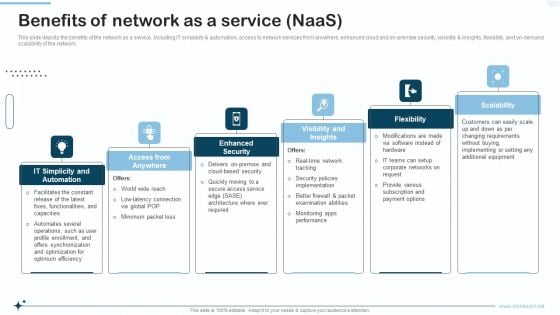
Naas Integrated Solution IT Benefits Of Network As A Service Naas Themes PDF
This slide depicts the benefits of the network as a service, including IT simplicity and automation, access to network services from anywhere, enhanced cloud and on premise security, visibility and insights, flexibility, and on-demand scalability of the network. This is a olution IT Benefits Of Network As A Service Naas Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Flexibility Scalability, Visibility And Insights. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
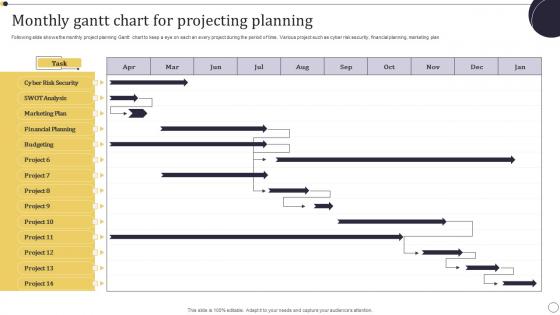
Monthly Gantt Chart For Projecting Planning Information Pdf
Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan Showcasing this set of slides titled Monthly Gantt Chart For Projecting Planning Information Pdf. The topics addressed in these templates are Marketing Plan, Financial Planning, Cyber Risk Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan

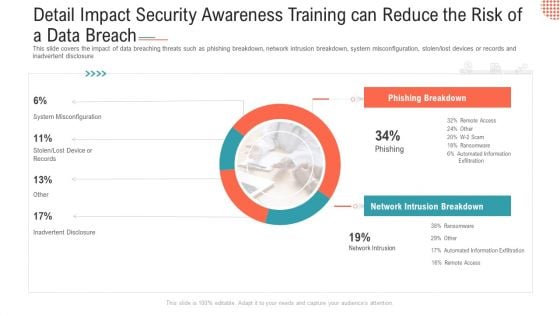
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Dashboard For Threat Tracking In IT Security IT Ppt Outline Examples PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative dashboard for threat tracking in it security it ppt outline examples pdf bundle. Topics like monthly threat status, threats by owners, risk by threats, current risk status, threats based on role, threat report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
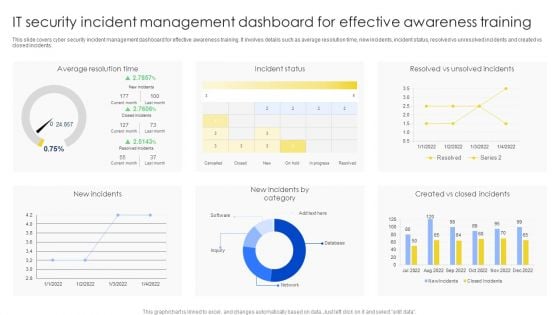
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
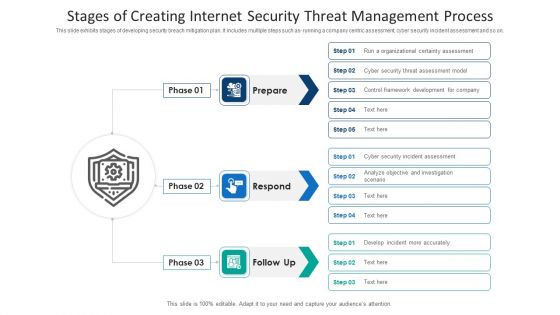
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Shared Responsibility Chart For Saas Cloud Security Services Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the responsibility chart for best application security services. It includes responsibilities such as data categorization and reporting, network control, end point safety etc. Showcasing this set of slides titled Shared Responsibility Chart For Saas Cloud Security Services Ppt PowerPoint Presentation File Outline PDF. The topics addressed in these templates are Application Level Controls, Cloud Customer, Data Categorization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
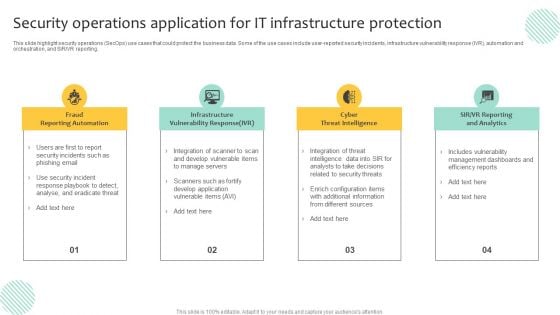
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
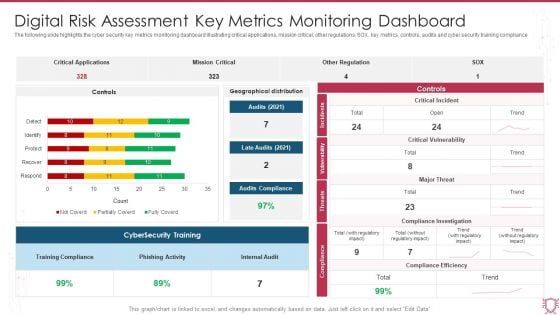
Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF
The following slide highlights the cyber security key metrics monitoring dashboard illustrating critical applications, mission critical, other regulations, SOX, key metrics, controls, audits and cyber security training compliance. Showcasing this set of slides titled Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF. The topics addressed in these templates are Critical Applications, Mission Critical, Other Regulation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
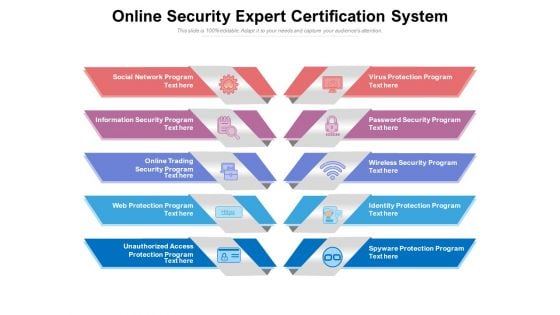
Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
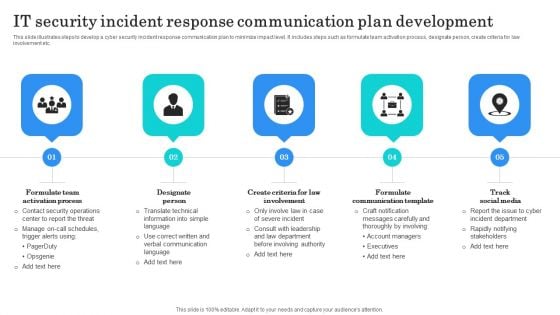
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
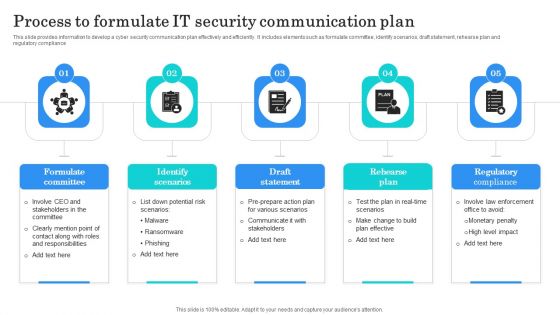
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
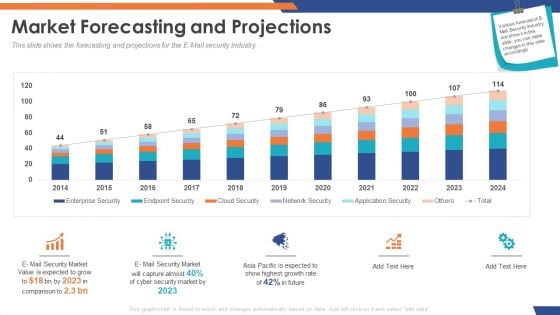
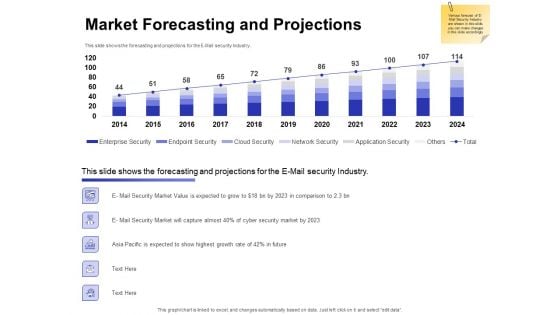
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Global Cloud Based Email Security Market Market Forecasting And Projections Professional PDF
Presenting this set of slides with name global cloud based email security market market forecasting and projections professional pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
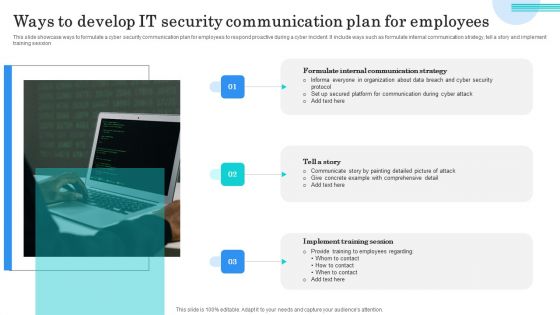
Ways To Develop IT Security Communication Plan For Employees Elements PDF
This slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting Ways To Develop IT Security Communication Plan For Employees Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Formulate Internal Communication, Tell Story, Implement Training Session. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Companys Data Safety Recognition Impact Of Security Awareness Training Demonstration PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative companys data safety recognition impact of security awareness training demonstration pdf bundle. Topics like system misconfiguration, inadvertent disclosure, network intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
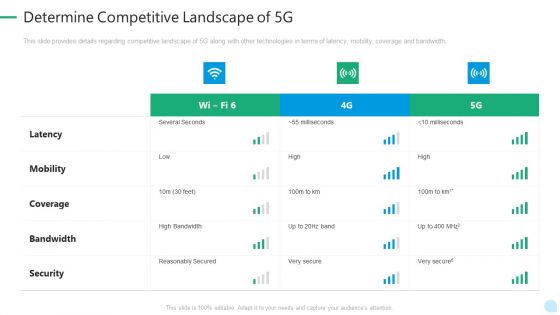
5G Network Technology Determine Competitive Landscape Of 5G Ppt Summary Visual Aids PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver and pitch your topic in the best possible manner with this 5g network technology determine competitive landscape of 5g ppt summary visual aids pdf. Use them to share invaluable insights on latency, mobility, coverage, bandwidth, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
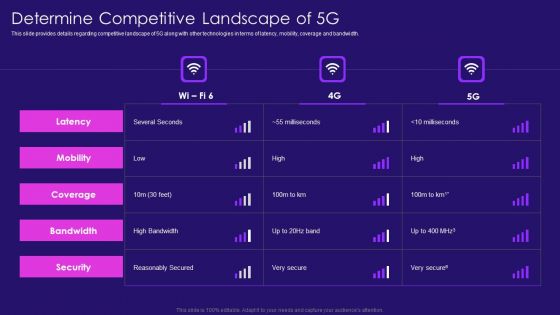
Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver an awe inspiring pitch with this creative Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF bundle. Topics like Bandwidth, Coverage, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
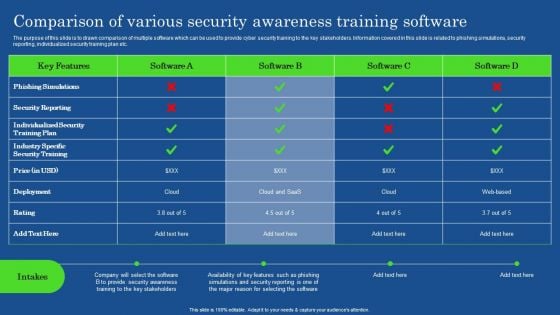
Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
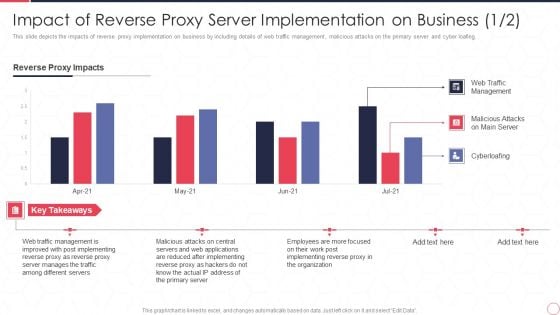
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy Server IT Ppt Professional Slides PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Deliver an awe inspiring pitch with this creative impact of reverse proxy server implementation on business reverse proxy server it ppt professional slides pdf bundle. Topics like reverse proxy impacts, web traffic management, malicious attacks on main server, cyberloafing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
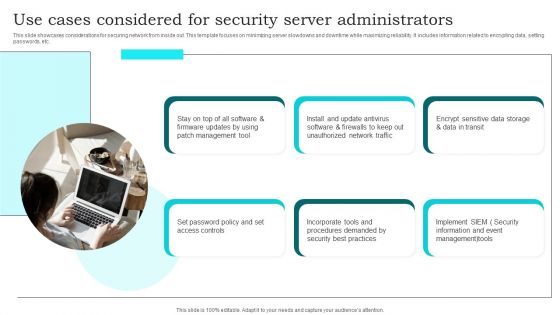
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
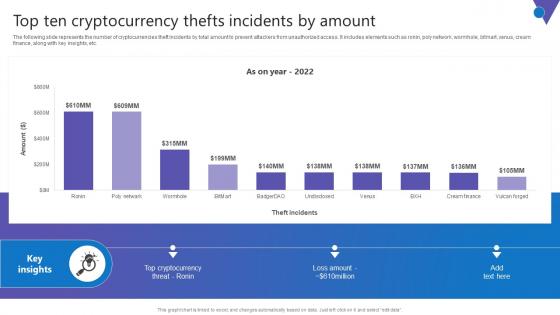
Top Ten Cryptocurrency Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc. Want to ace your presentation in front of a live audience Our Top Ten Cryptocurrency Comprehensive Guide To Blockchain Digital Security Clipart Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc.

Challenges Faced By Shipment Services Companies Diagrams PDF
This slide shows the challenges faced by transportation industry. It includes supply chain integration, digital transformation, proactive cyber security, parking issues and traffic. Pitch your topic with ease and precision using this Challenges Faced By Shipment Services Companies Diagrams PDF. This layout presents information on Online Sales, Proactive Cyber Security, Workforce. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
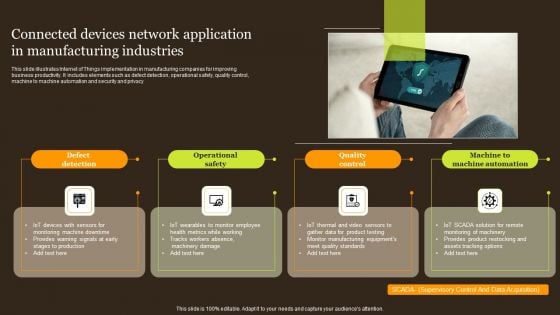
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Timeline Demonstration Of Years 2013 To 2019 PowerPoint Templates Ppt Slides Graphics
We present our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics.Download and present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Use our Timelines PowerPoint Templates because this slide is Designed to help bullet-point your views and thoughts. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Arrows PowerPoint Templates because you can Grab the attention of your team with this eye catching template signifying . Download and present our Time planning PowerPoint Templates because this Layout can explain the relevance of the different layers and stages in getting down to your core competence, ability and desired result.Use these PowerPoint slides for presentations relating to Art, Background, Button, Call, City, Colorful, Concept, Country, Destination, Editable, Flag, Fuel, Geography, Graphic, Home, Icon, Illustration, Journey, Land, Locate, Location, Macro, Map, Mapping, Mark, Navigate, Needle, Petrol, Pin, Pinpoint, Place, Pointing, Pump, Push, Pushpin, Restaurant, Road, Roadmap, Service, Set, Shiny, Space, Symbol, Town, Travel, Trip. The prominent colors used in the PowerPoint template are Green, Gray, Black. PowerPoint presentation experts tell us our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics are Energetic. Customers tell us our City PowerPoint templates and PPT Slides are Vintage. Customers tell us our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics are Magical. Customers tell us our Call PowerPoint templates and PPT Slides are Dazzling. PowerPoint presentation experts tell us our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics are Energetic. People tell us our Destination PowerPoint templates and PPT Slides are Tranquil. Our Timeline Demonstration Of Years 2013 To 2019 PowerPoint Templates Ppt Slides Graphics are really enterprising. They dig out ways to convey your ideas.

Assessing Contribution Of 5G To Global Economy 5G Network Architecture Instructions Microsoft PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Assessing Contribution Of 5G To Global Economy 5G Network Architecture Instructions Microsoft PDF. Use them to share invaluable insights on Digital Economy, Fast Telecommunication, Physical Infrastructures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
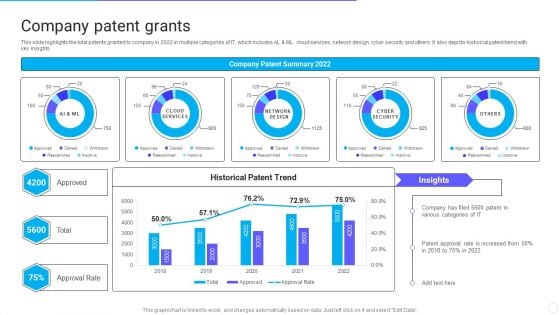
IT Application Services Company Outline Company Patent Grants Introduction PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative IT Application Services Company Outline Company Patent Grants Introduction PDF bundle. Topics like Approval Rate, Company Patent Grants can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
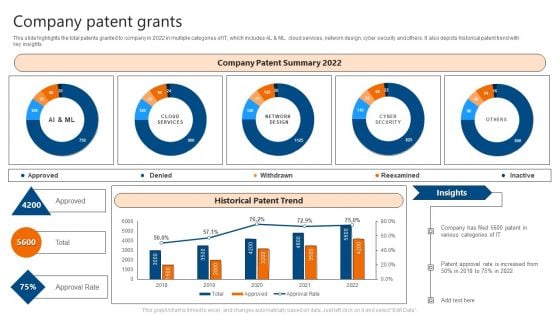
Company Patent Grants IT Software Development Company Profile Introduction PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver and pitch your topic in the best possible manner with this Company Patent Grants IT Software Development Company Profile Introduction PDF. Use them to share invaluable insights on Company Patent Summary, Historical Patent Trend and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Redis Cache Data Structure IT Secure Server Configuration With Server Configuration Lock Diagrams PDF
This slide describes the secure server configuration with server configuration lock, which guarantees only users have access. Presenting redis cache data structure it secure server configuration with server configuration lock diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like securing, programmer, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
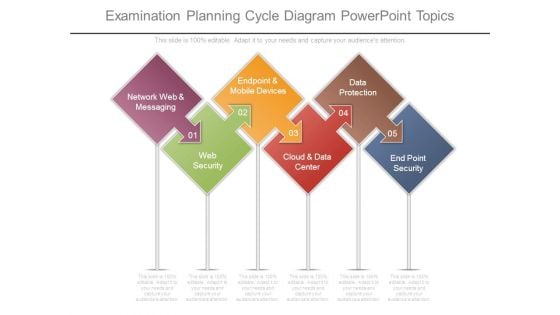
Examination Planning Cycle Diagram Powerpoint Topics
This is a examination planning cycle diagram powerpoint topics. This is a five stage process. The stages in this process are network web and messaging, web security, endpoint and mobile devices, cloud and data center, data protection, end point security.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
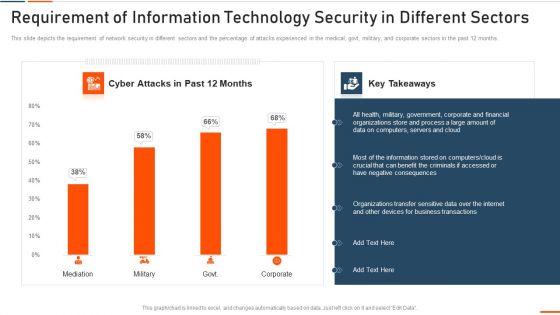
Requirement Of Information Technology Security In Different Sectors Ppt Ideas Shapes PDF
This slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with requirement of information technology security in different sectors ppt ideas shapes pdf bundle. Topics like requirement of information technology security in different sectors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
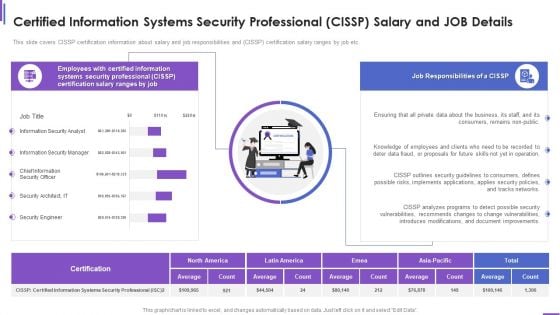
Certified Information Systems Security Professional Cissp Salary And Job Details Brochure PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver and pitch your topic in the best possible manner with this certified information systems security professional cissp salary and job details brochure pdf. Use them to share invaluable insights on consumers, security, document, networks, implements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
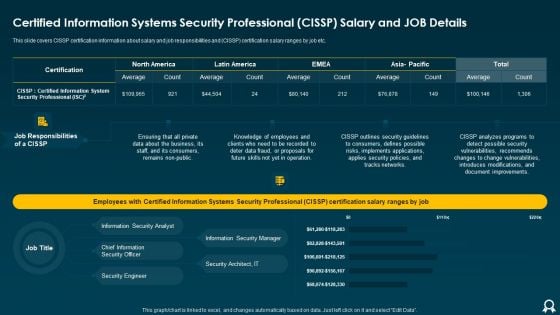
Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. Presenting this PowerPoint presentation, titled Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
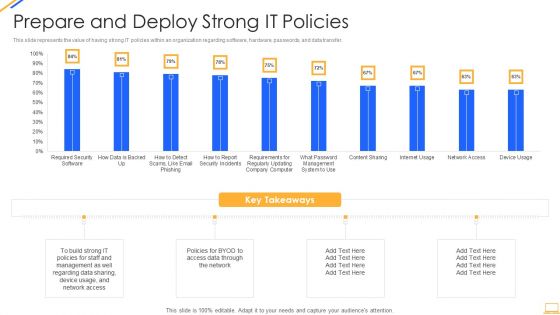
Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
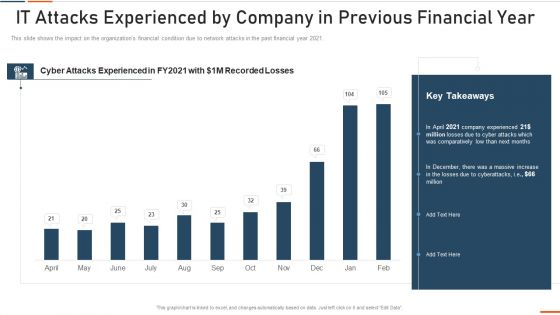
Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
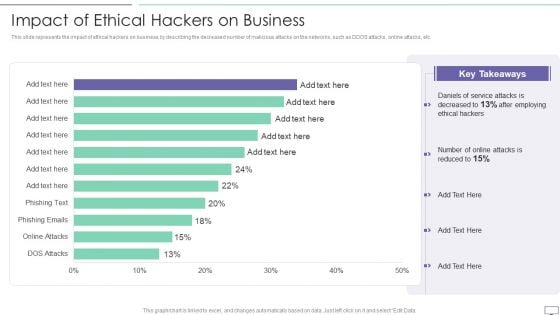
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Steady Way To Represent 7 Diverging Steps Cycle Network PowerPoint Slides
We present our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides.Present our Arrows PowerPoint Templates because you can Enlighten them with your brilliant understanding of mental health. Present our Flow Charts PowerPoint Templates because we provide the means to project your views. Present our Process and Flows PowerPoint Templates because readymade PowerPoint templates can prove best of your knowledge for your slides to show. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Shapes PowerPoint Templates because they help to lay the base of your trend of thought.Use these PowerPoint slides for presentations relating to Arrow, Background, Center, Chart, Clip, Communication, Competition, Computer, Concept, Connect, Connection, Diagram, Direction, Group, Illustration, Information, Network, Process, Progress, Purpose, Strategy, Symbol, Target. The prominent colors used in the PowerPoint template are Pink, Gray, White. People tell us our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides are Attractive. People tell us our Communication PowerPoint templates and PPT Slides will impress their bosses and teams. The feedback we get is that our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides are Majestic. Presenters tell us our Computer PowerPoint templates and PPT Slides are Amazing. Customers tell us our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides are Romantic. The feedback we get is that our Computer PowerPoint templates and PPT Slides are second to none. Clear out the confusion with your views. Expound on your decisions with our Steady Way To Represent 7 Diverging Steps Cycle Network PowerPoint Slides.

Operational Risks Events Forecasting In 2021 Ppt PowerPoint Presentation Ideas Picture PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.Deliver an awe-inspiring pitch with this creative operational risks events forecasting in 2021 ppt powerpoint presentation ideas picture pdf. bundle. Topics like operational risks events forecasting in 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
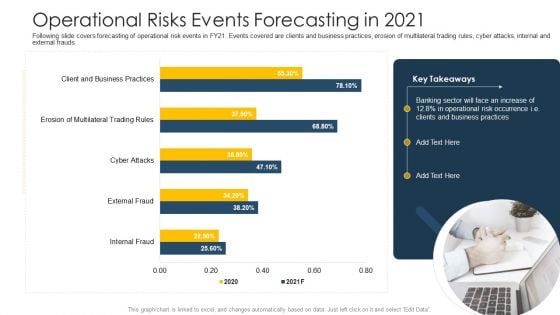
Establishing Operational Risk Framework Banking Operational Risks Events Forecasting In 2021 Portrait PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this establishing operational risk framework banking operational risks events forecasting in 2021 portrait pdf. Use them to share invaluable insights on business practices, operational risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
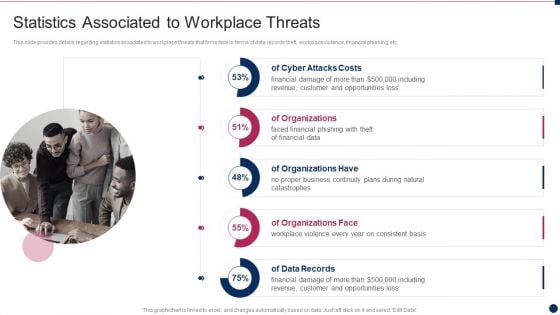
Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
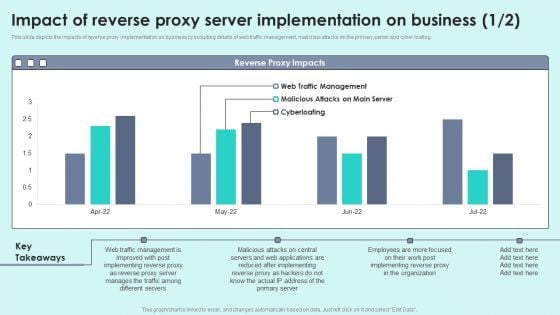
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing.Deliver an awe inspiring pitch with this creative Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF bundle. Topics like After Implementing, Manages Traffic, Different Servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
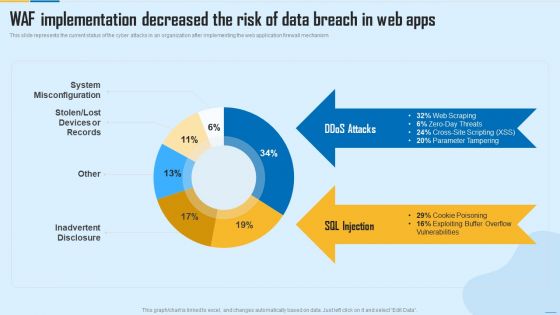
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
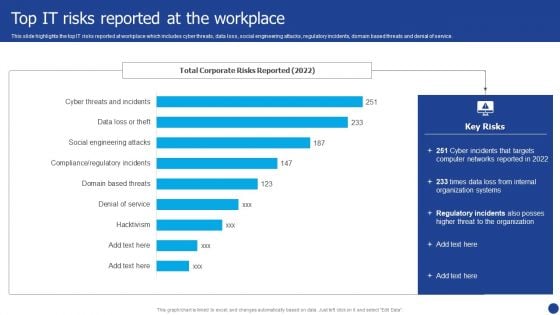
Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
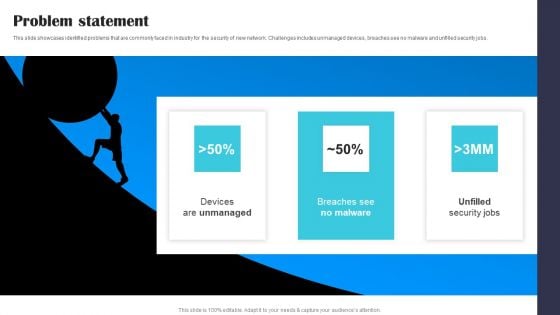
Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF
This slide showcases identified problems that are commonly faced in industry for the security of new network. Challenges includes unmanaged devices, breaches see no malware and unfilled security jobs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
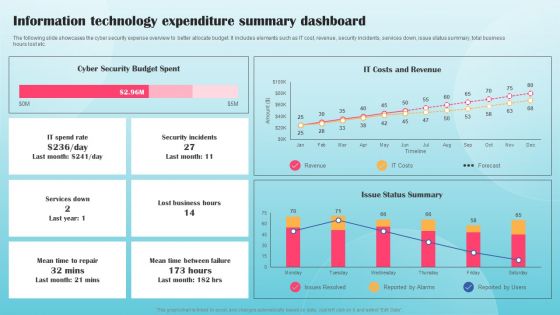
Information Technology Expenditure Summary Dashboard Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. This Information Technology Expenditure Summary Dashboard Ppt PowerPoint Presentation Diagram Graph Charts PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
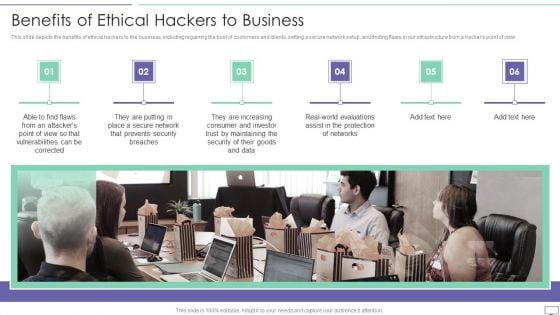
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Dashboard For Threat Tracking In Information Technology Security Ppt Portfolio Shapes PDF
This slide depicts the dashboard for threat tracking in network security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver and pitch your topic in the best possible manner with this dashboard for threat tracking in information technology security ppt portfolio shapes pdf. Use them to share invaluable insights on dashboard for threat tracking in information technology security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Impact On Organization After Implementing Information Technology Security Ppt Infographic Template Examples PDF
This slide depicts the hardware software update measure under the network security model. It also tells the current status of the devices that need to update in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information technology security ppt infographic template examples pdf. Use them to share invaluable insights on hardware and software update in company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
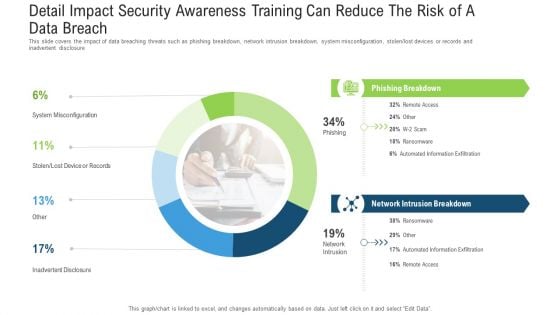
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Efficiency Administration Software Investor Financing Different Phases Depicting Progressive Professional PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a efficiency administration software investor financing different phases depicting progressive professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application, networking, services, secured digital. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
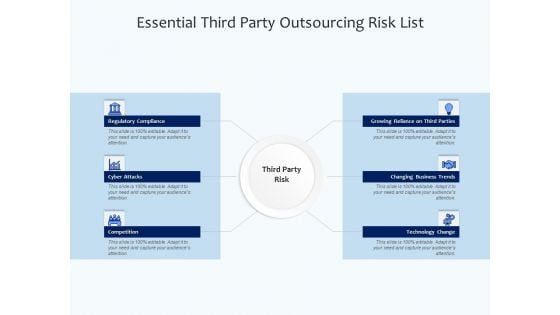
Essential Third Party Outsourcing Risk List Ppt PowerPoint Presentation File Sample PDF
Presenting essential third party outsourcing risk list ppt powerpoint presentation file sample pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including regulatory compliance, cyber attacks, competition, changing business trends, technology change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
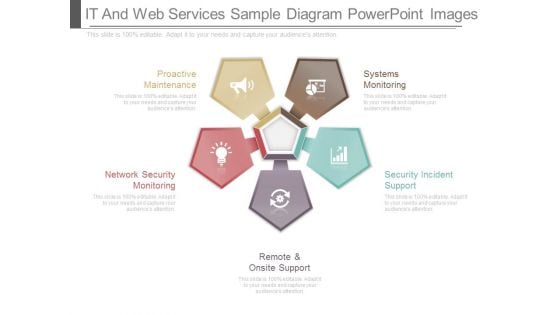
It And Web Services Sample Diagram Powerpoint Images
This is a it and web services sample diagram powerpoint images. This is a five stage process. The stages in this process are systems monitoring, security incident support, remote and onsite support, network security monitoring, proactive maintenance.
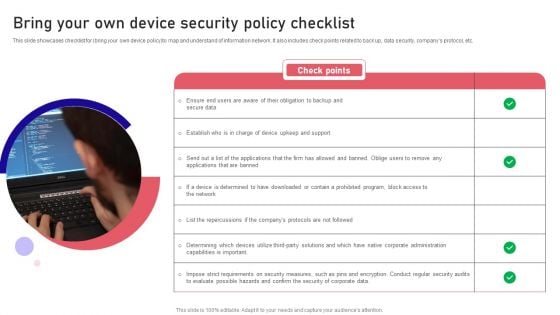
Bring Your Own Device Security Policy Checklist Graphics PDF
This slide showcases checklist for bring your own device policy to map and understand of information network. It also includes check points related to back up, data security, companys protocol, etc. Presenting Bring Your Own Device Security Policy Checklist Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Check Points, Checklist, Device. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
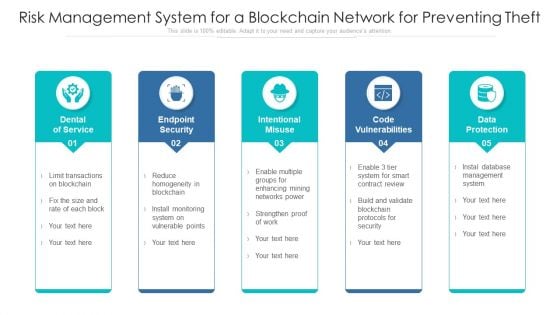
Risk Management System For A Blockchain Network For Preventing Theft Ppt PowerPoint Presentation Layouts Deck PDF
Presenting risk management system for a blockchain network for preventing theft ppt powerpoint presentation layouts deck pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including endpoint security, intentional misuse, code vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF
This slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Get a simple yet stunning designed Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
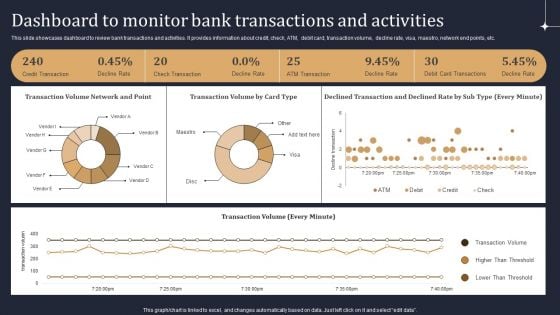
KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF
This slide showcases dashboard to review bank transactions and activities. It provides information about credit, check, ATM, debit card, transaction volume, decline rate, visa, maestro, network end points, etc. This KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
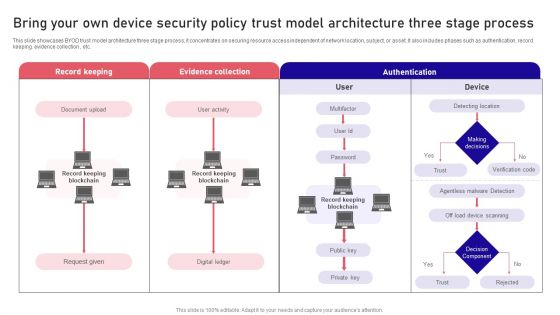
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
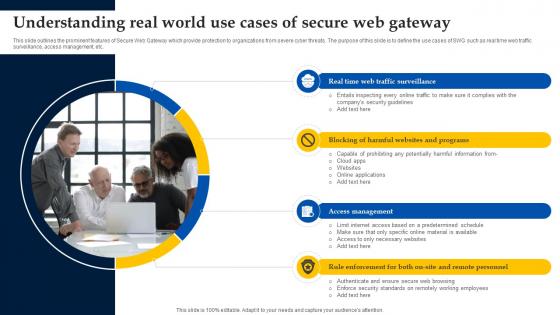
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
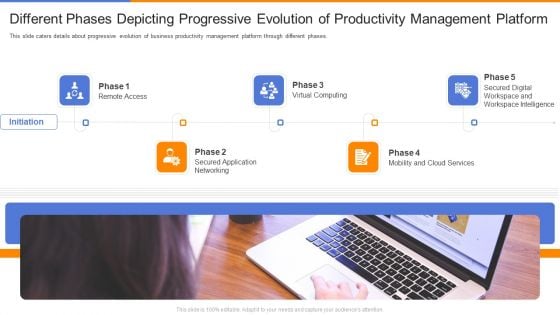
Organizational Productivity Administration Software Different Phases Depicting Progressive Evolution Microsoft PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. Presenting organizational productivity administration software different phases depicting progressive evolution microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secured application networking, virtual computing, mobility and cloud services, remote access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
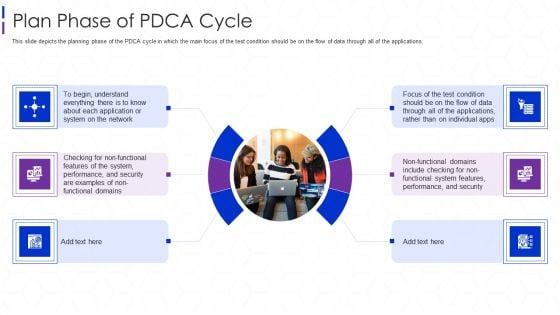
Software Interoperability Examination IT Plan Phase Of PDCA Cycle Clipart PDF
This slide depicts the planning phase of the PDCA cycle in which the main focus of the test condition should be on the flow of data through all of the applications. This is a software interoperability examination it plan phase of pdca cycle clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, system, security, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
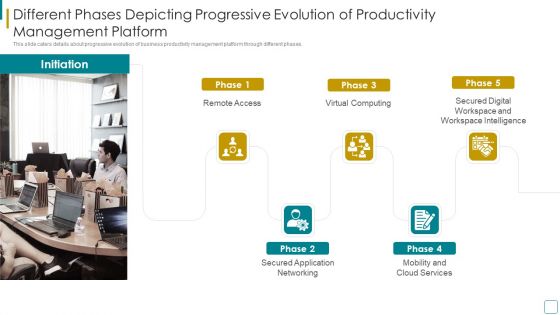
Strategic Business Efficiency Administration Tool Investor Financing Elevator Pitch Deck Different Phases Depicting Graphics PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a strategic business efficiency administration tool investor financing elevator pitch deck different phases depicting graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like remote access, virtual computing, secured application networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Multi Cloud Infrastructure Management Strategies For Every Phase Of The Cloud Journey Sample PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Retrieve professionally designed Multi Cloud Infrastructure Management Strategies For Every Phase Of The Cloud Journey Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
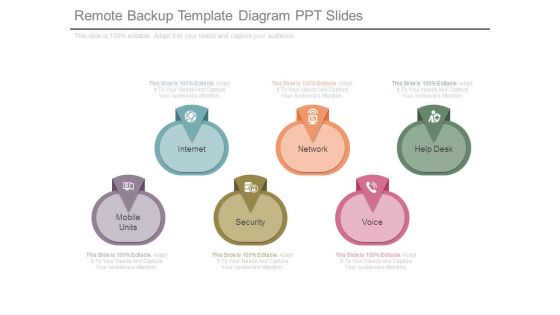
Remote Backup Template Diagram Ppt Slides
This is a remote backup template diagram ppt slides. This is a six stage process. The stages in this process are mobile units, internet, network, help desk, security, voice.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
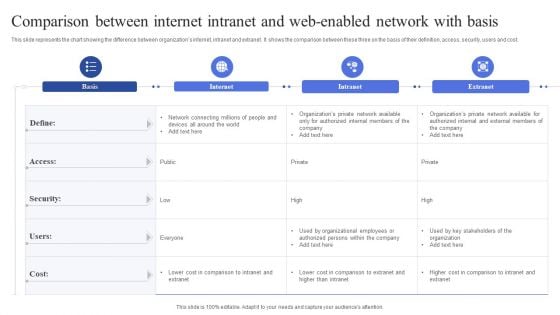
Comparison Between Internet Intranet And Web Enabled Network With Basis Summary PDF
This slide represents the chart showing the difference between organizations internet, intranet and extranet. It shows the comparison between these three on the basis of their definition, access, security, users and cost. Showcasing this set of slides titled Comparison Between Internet Intranet And Web Enabled Network With Basis Summary PDF. The topics addressed in these templates are Internet, Extranet, Public. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
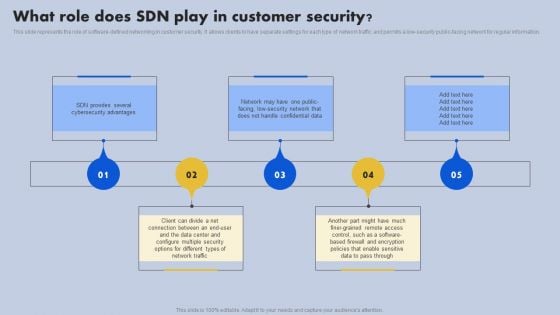
What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
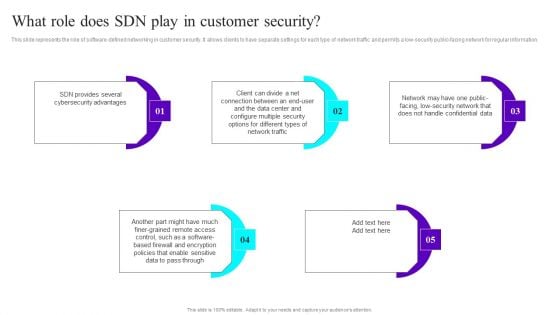
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Cloud Based Computing Analysis Strategies For Every Phase Of The Cloud Journey Clipart PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security. Do you know about Slidesgeeks Cloud Based Computing Analysis Strategies For Every Phase Of The Cloud Journey Clipart PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
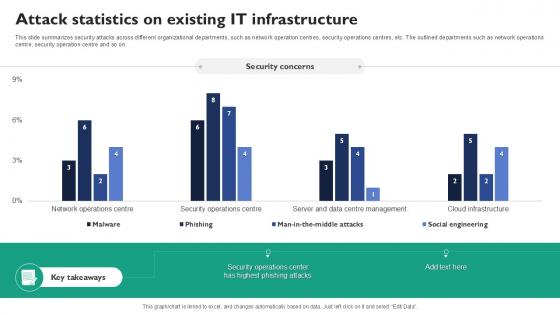
Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
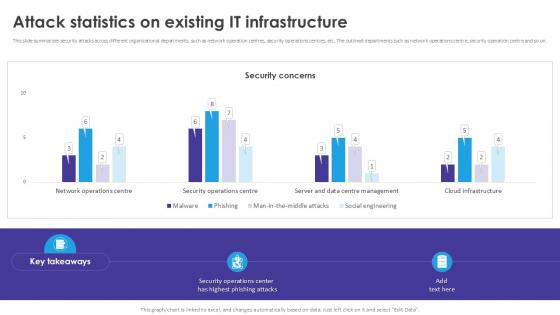
Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
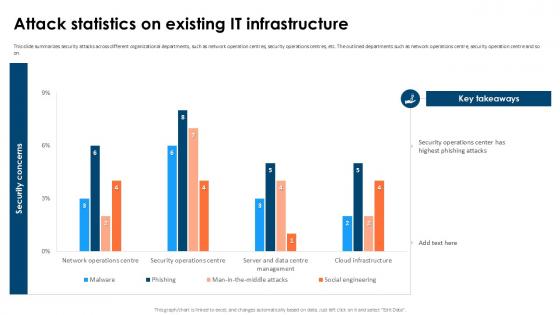
Attack Statistics On Partial Regression Testing For A Best PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Partial Regression Testing For A Best PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
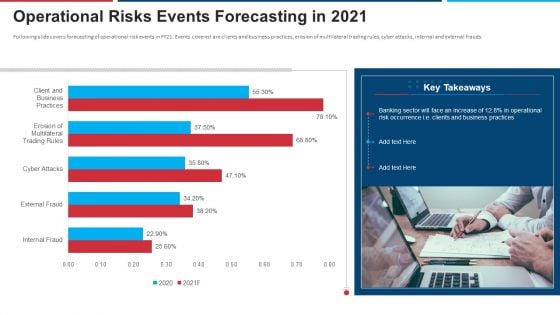
Mitigation Strategies For Operational Threat Operational Risks Events Forecasting In 2021 Ppt Infographic Template Microsoft PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks events forecasting in 2021 ppt infographic template microsoft pdf. Use them to share invaluable insights on banking, operational risk, occurrence, business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
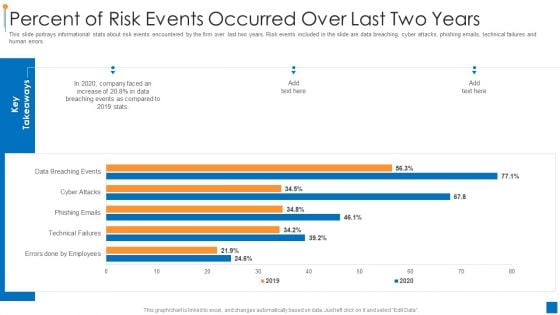
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
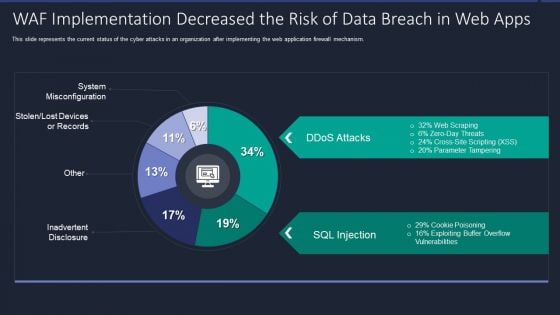
Web App Firewall Services IT WAF Implementation Decreased The Risk Of Data Breach In Web Apps Portrait PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this web app firewall services it waf implementation decreased the risk of data breach in web apps portrait pdf. Use them to share invaluable insights on waf implementation decreased the risk of data breach in web apps and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
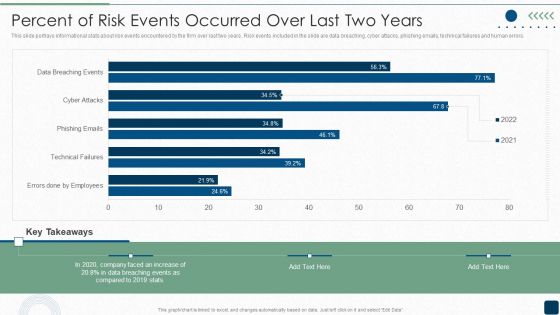
Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
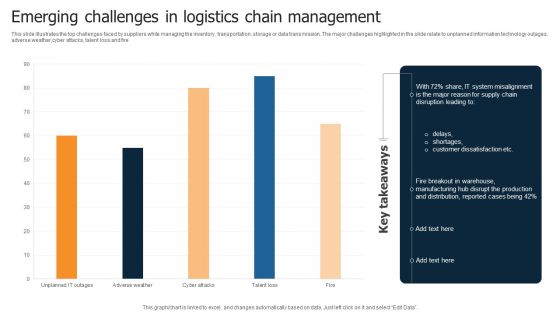
Emerging Challenges In Logistics Chain Management Infographics PDF
This slide illustrates the top challenges faced by suppliers while managing the inventory, transportation, storage or data transmission. The major challenges highlighted in the slide relate to unplanned information technology outages, adverse weather,cyber attacks, talent loss and fire Showcasing this set of slides titled Emerging Challenges In Logistics Chain Management Infographics PDF. The topics addressed in these templates are System Misalignment, Disruption Leading, Customer Dissatisfaction. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
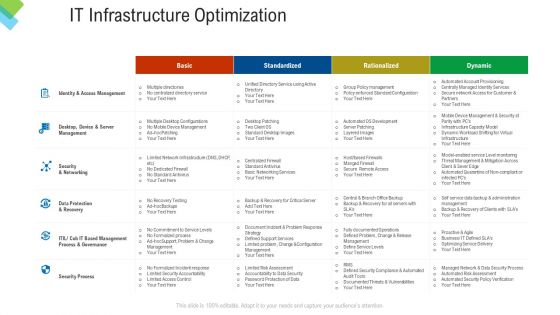
Construction Management Services IT Infrastructure Optimization Themes PDF
Deliver and pitch your topic in the best possible manner with this construction management services it infrastructure optimization themes pdf. Use them to share invaluable insights on security process, security and networking, management process, data protection, server management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
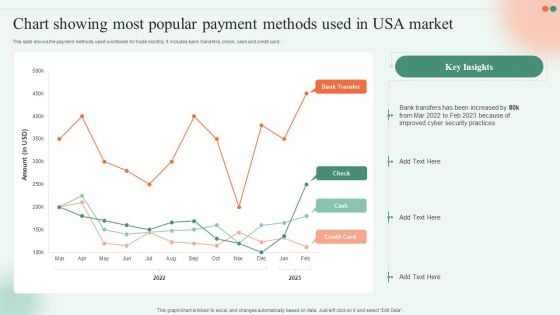
Chart Showing Most Popular Payment Methods Used In USA Market Ppt File Deck PDF
This slide shows the payment methods used worldwide for trade monthly. It includes bank transfers, check, cash and credit card. Showcasing this set of slides titled Chart Showing Most Popular Payment Methods Used In USA Market Ppt File Deck PDF. The topics addressed in these templates are Cyber Security Practices, Bank Transfers, 2022 To 2023. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
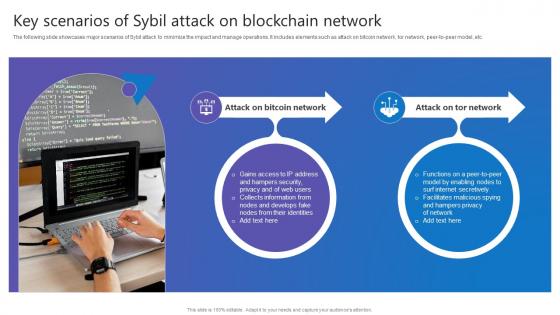
Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc.
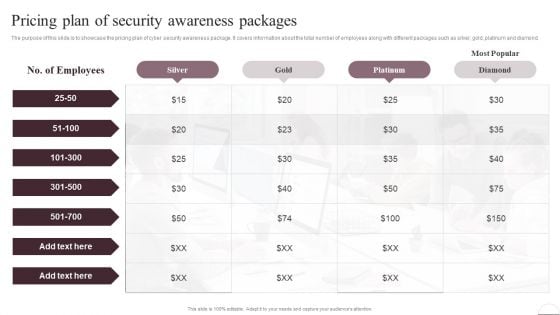
Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
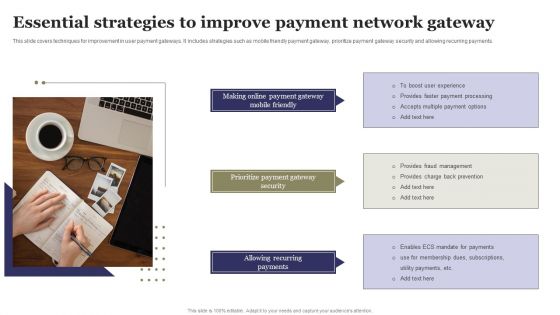
Essential Strategies To Improve Payment Network Gateway Ppt Gallery Background Designs PDF
This slide covers techniques for improvement in user payment gateways. It includes strategies such as mobile friendly payment gateway, prioritize payment gateway security and allowing recurring payments. Presenting Essential Strategies To Improve Payment Network Gateway Ppt Gallery Background Designs PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Making Online, Payment Gateway, Prioritize Payment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
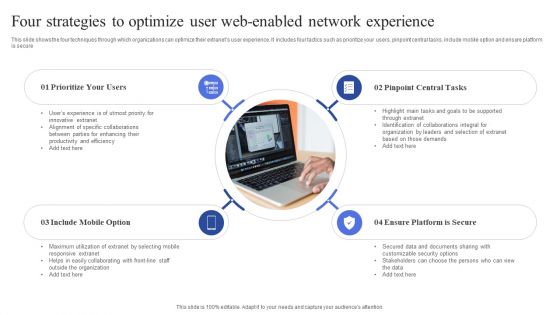
Four Strategies To Optimize User Web Enabled Network Experience Structure PDF
This slide shows the four techniques through which organizations can optimize their extranets user experience. It includes four tactics such as prioritize your users, pinpoint central tasks, include mobile option and ensure platform is secure. Presenting Four Strategies To Optimize User Web Enabled Network Experience Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Prioritize Your Users, Include Mobile Option, Pinpoint Central Tasks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
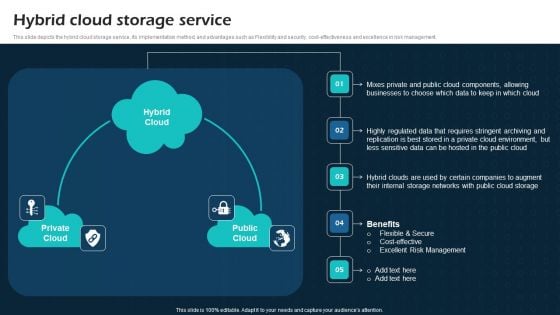
Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost effectiveness and excellence in risk management. If you are looking for a format to display your unique thoughts, then the professionally designed Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Hybrid Cloud Storage Service Virtual Cloud Network IT Ppt Inspiration Objects PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
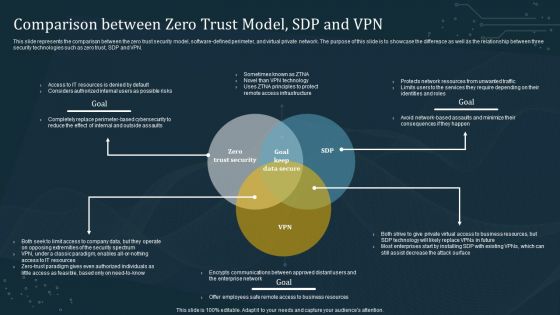
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
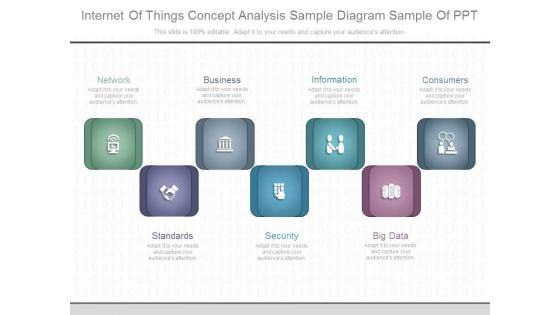
Internet Of Things Concept Analysis Sample Diagram Sample Of Ppt
This is a internet of things concept analysis sample diagram sample of ppt. This is a seven stage process. The stages in this process are network, business, information, consumers, standards, security, big data.
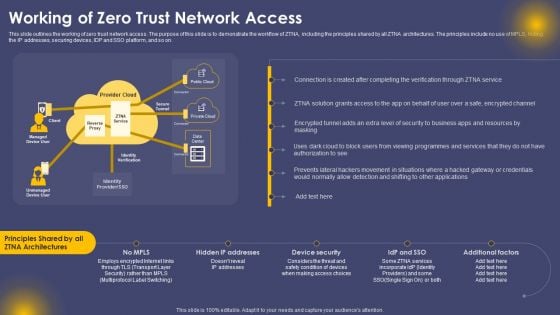
Working Of Zero Trust Network Access Ppt Professional File Formats PDF
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Are you searching for a Working Of Zero Trust Network Access Ppt Professional File Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Working Of Zero Trust Network Access Ppt Professional File Formats PDF from Slidegeeks today.
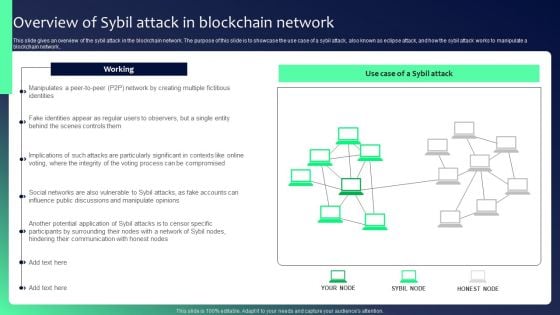
Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Tech Support Services Cost And Pricing Agenda For Pricing IT Services Ppt PowerPoint Presentation Summary Diagrams
Presenting this set of slides with name tech support services cost and pricing agenda for pricing it services ppt powerpoint presentation summary diagrams. The topics discussed in these slides are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
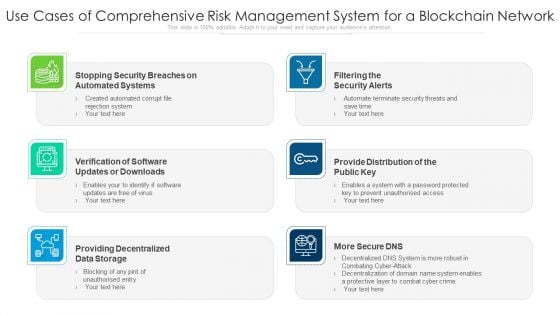
Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

AI Applications In Banking And Financial Services Formats PDF
This slide covers use of artificial intelligence in banking and financial services. It involves applications such as customer engagement, predictive analytics, cyber security and credit scoring.Presenting AI Applications In Banking And Financial Services Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Customer Engagement, Predictive Analytics, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Products Company Outline SWOT Analysis Diagrams PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Find highly impressive Digital Products Company Outline SWOT Analysis Diagrams PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Products Company Outline SWOT Analysis Diagrams PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Tech Support Services Cost And Pricing Effect After Implementing IT Services Ppt PowerPoint Presentation Summary Background
Presenting this set of slides with name tech support services cost and pricing effect after implementing it services ppt powerpoint presentation summary background. The topics discussed in these slides are cyber security, infrastructure, technological, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
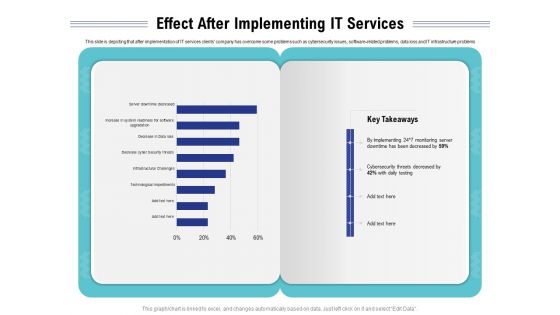
Cloud Managed Services Pricing Guide Effect After Implementing IT Services Ppt Styles Mockup PDF
Presenting this set of slides with name cloud managed services pricing guide effect after implementing it services ppt styles mockup pdf. The topics discussed in these slides are technological, cyber security, implementing, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
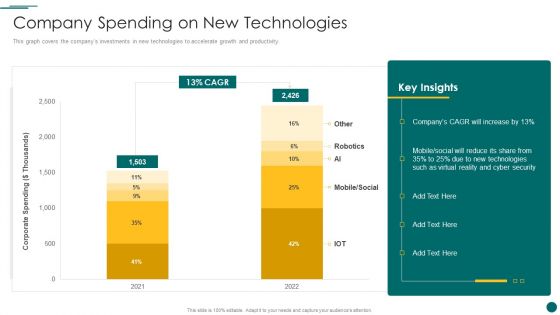
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
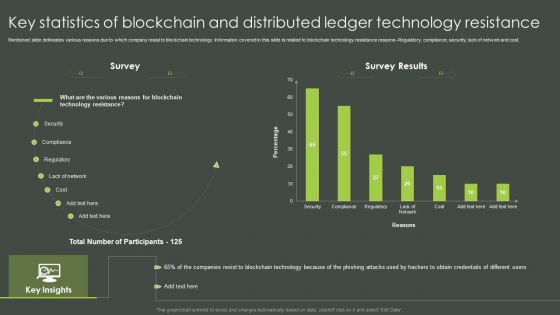
Key Statistics Of Blockchain And Distributed Ledger Technology Resistance Themes PDF
Mentioned slide delineates various reasons due to which company resist to blockchain technology. Information covered in this slide is related to blockchain technology resistance reasons -Regulatory, compliance, security, lack of network and cost. Showcasing this set of slides titled Key Statistics Of Blockchain And Distributed Ledger Technology Resistance Themes PDF. The topics addressed in these templates are Blockchain, Technology Resistance, Total Number Participants. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
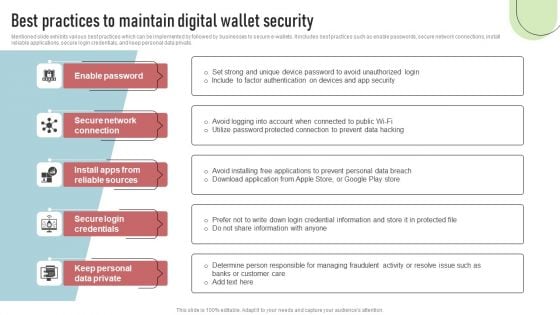
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
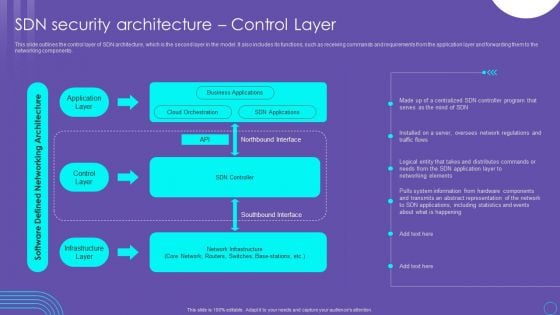
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
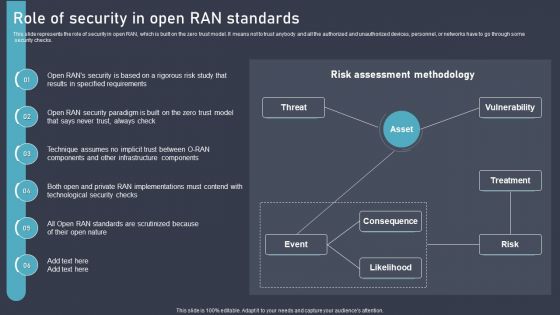
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
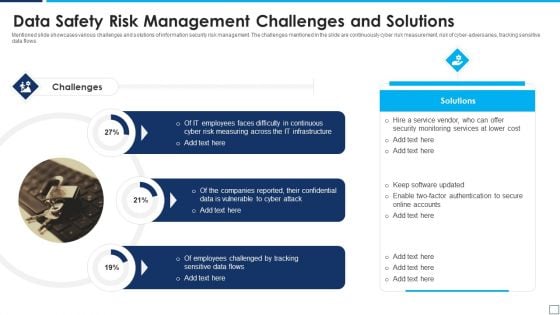
Data Safety Risk Management Challenges And Solutions Clipart PDF
Mentioned slide showcases various challenges and solutions of information security risk management. The challenges mentioned in the slide are continuously cyber risk measurement, risk of cyber-adversaries, tracking sensitive data flows. Showcasing this set of slides titled y risk management challenges and solutions clipart pdf. The topics addressed in these templates are data safety risk management challenges and solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
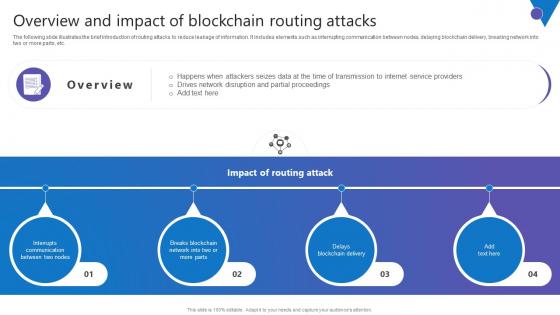
Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf
The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Retrieve professionally designed Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc.
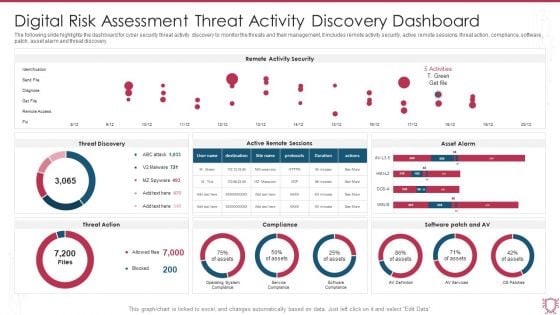
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
Key Trends On Effective Information Technology Service Excellence Themes PDF
This slide signifies the effective information technology recent and future trends. It includes stages like artificial intelligence, block chain, cyber security and customer data platform. Persuade your audience using this Key Trends On Effective Information Technology Service Excellence Themes PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analytics, Distributed Enterprise, Enterprise Service Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home