Cybersecurity Roadmap
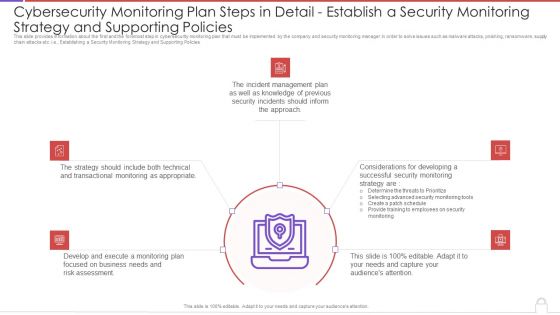
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
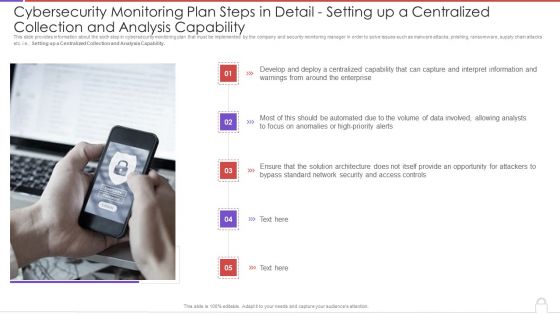
Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Elements PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Setting up a Centralized Collection and Analysis Capability. This is a cybersecurity monitoring plan steps in detail setting up a centralized collection and elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interpret information, high priority alerts, analysts, access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V
The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers.

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
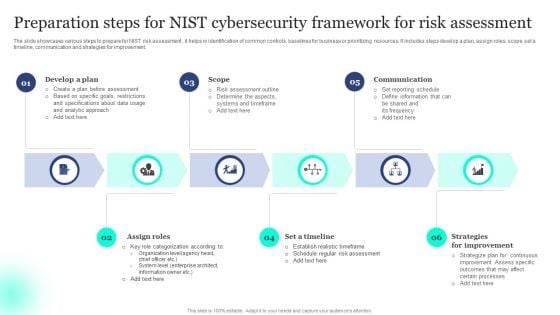
Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF
The slide showcases various steps to prepare for NIST risk assessment , it helps in identification of common controls, baselines for business or prioritizing resources. It includes steps develop a plan, assign roles, scope, set a timeline, communication and strategies for improvement. Presenting Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Scope, Communication, Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
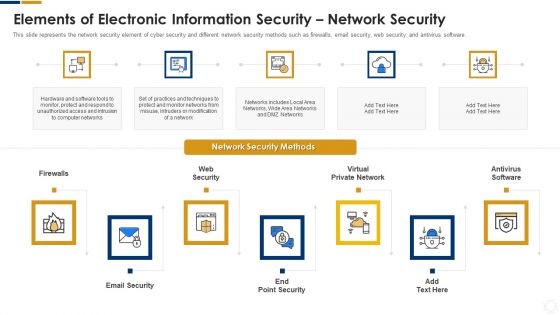
Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
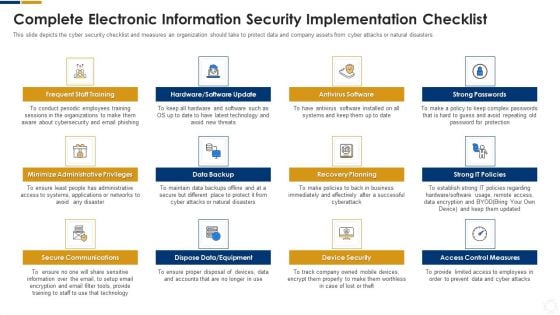
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Common Methods Used To Threaten Electronic Information Security Ppt Infographics Inspiration PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a cybersecurity common methods used to threaten electronic information security ppt infographics inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
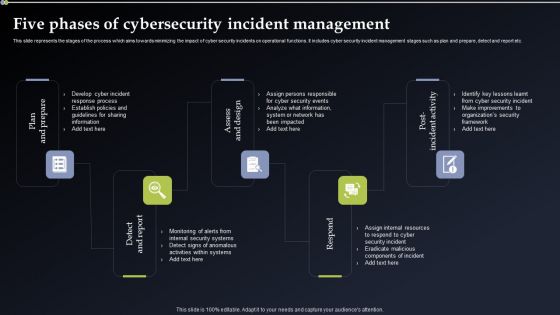
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
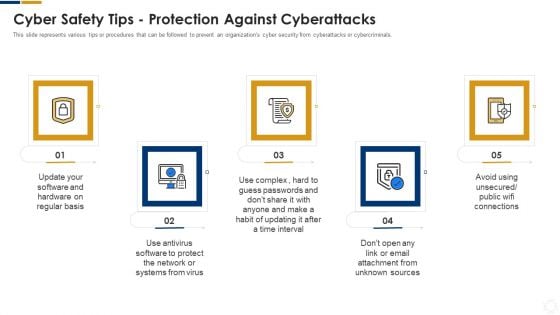
Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Elements Of Electronic Information Security Cloud Security Ppt Outline Background Designs PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a cybersecurity elements of electronic information security cloud security ppt outline background designs pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, risks, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

How Is Automation Used In Cybersecurity IT Security IT Ppt Topics PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. This is a how is automation used in cybersecurity it security it ppt topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat detection, threat response, human augmentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
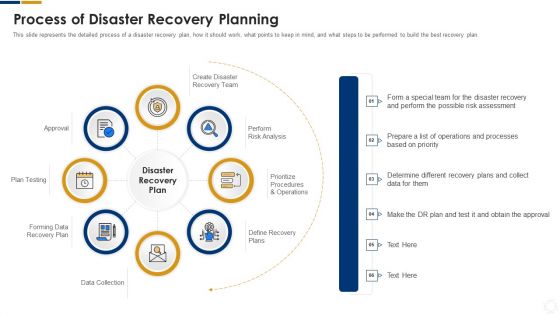
Cybersecurity Process Of Disaster Recovery Planning Ppt Infographic Template Elements PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a cybersecurity process of disaster recovery planning ppt infographic template elements pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recovery plan, recovery team, risk analysis, prioritize procedures, data collection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
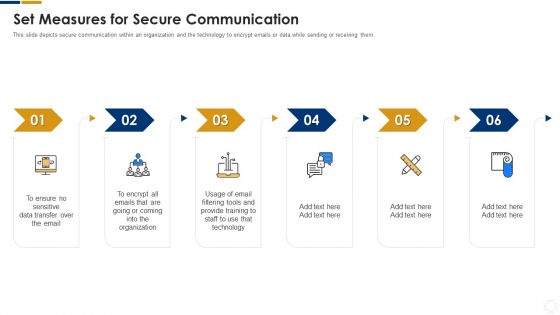
Cybersecurity Set Measures For Secure Communication Ppt Visual Aids Show PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting cybersecurity set measures for secure communication ppt visual aids show pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like organization, technology, email. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Strategies To Manage Cyber Risks Ppt Infographic Template Graphics Template PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a cybersecurity strategies to manage cyber risks ppt infographic template graphics template pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategic, risk, implementation, awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
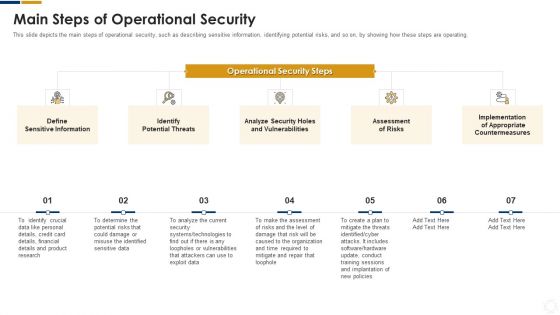
Cybersecurity Main Steps Of Operational Security Ppt Infographic Template Topics PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a cybersecurity main steps of operational security ppt infographic template topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine, potential, risks, technologies, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
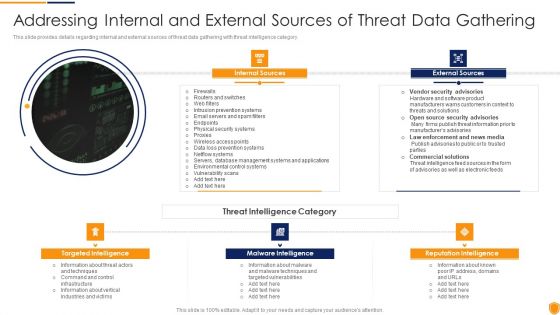
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Internal And External Clipart PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a mitigating cybersecurity threats and vulnerabilities addressing internal and external clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal sources, external sources, targeted intelligence, malware intelligence, reputation intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
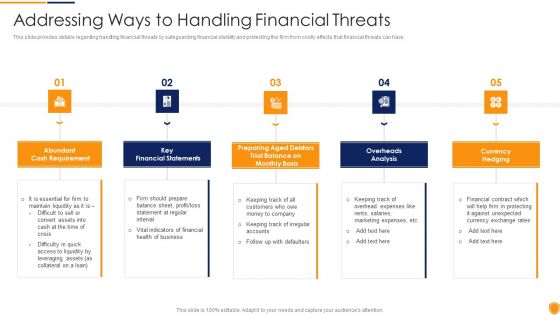
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Ways To Handling Professional PDF
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Presenting mitigating cybersecurity threats and vulnerabilities addressing ways to handling professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cash requirement, key financial statements, overheads analysis, currency hedging. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
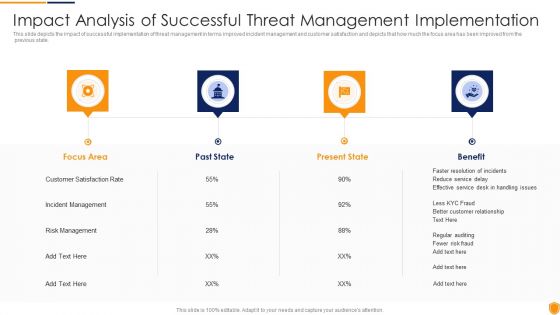
Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis Of Successful Threat Slides PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Presenting mitigating cybersecurity threats and vulnerabilities impact analysis of successful threat slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like focus area, past state, present state, benefit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Various Types Of Workplace Download PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a mitigating cybersecurity threats and vulnerabilities various types of workplace download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threatening behavior, stalking, assault harassment, property damage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cybersecurity Guidelines IT Overview Of Information Retention Policy For Employees Microsoft PDF
This slide talks about the data retention policy, including the involved data types such as documents, customer records, transactional information, email communication, and contracts. Find a pre-designed and impeccable Cybersecurity Guidelines IT Overview Of Information Retention Policy For Employees Microsoft PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
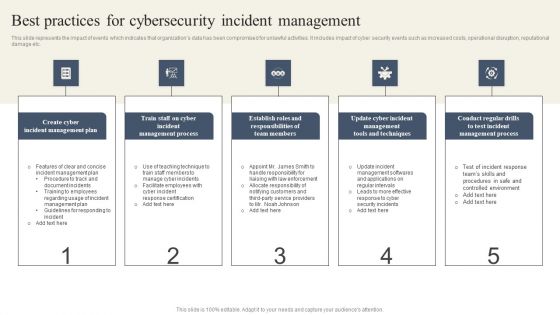
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
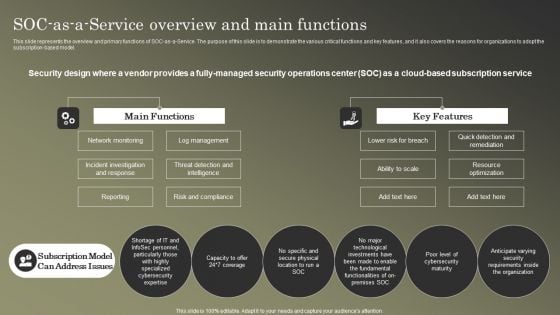
Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF
This slide represents the overview and primary functions of SOC-as-a-Service. The purpose of this slide is to demonstrate the various critical functions and key features, and it also covers the reasons for organizations to adopt the subscription-based model. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
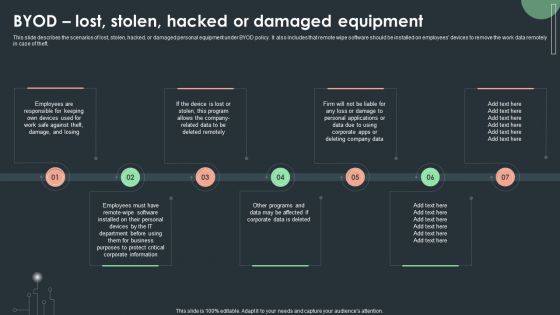
Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF
This slide represents the company stipend for BYOD policy, including the stats for 2022, such as percent the age of employees using their personal devices, BYOD generated value of each worker per year, and so on. Present like a pro with Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc.Welcome to our selection of the Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF
This slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF
This slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
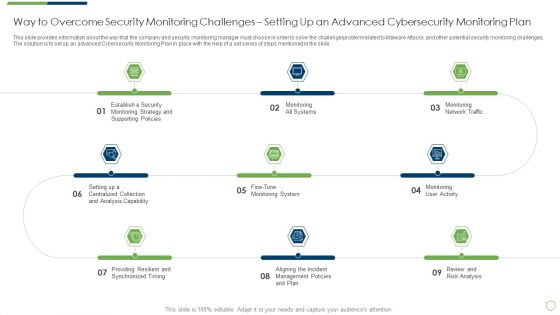
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
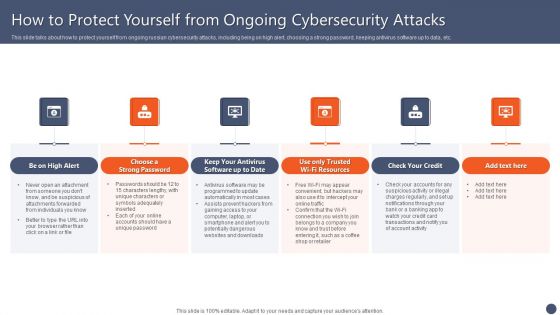
Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
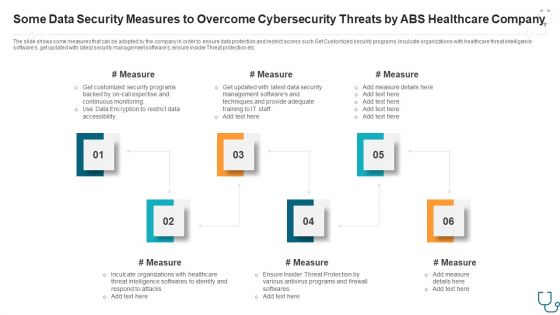
Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
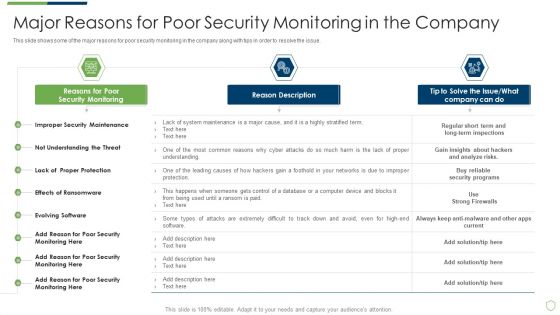
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
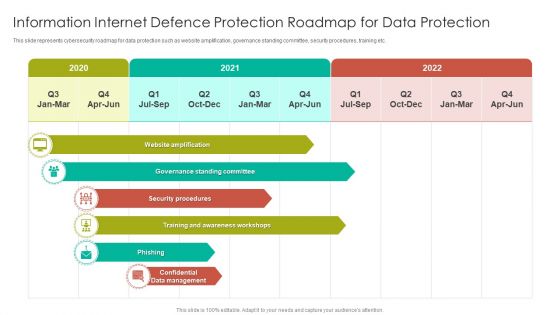
Information Internet Defence Protection Roadmap For Data Protection Topics PDF
This slide represents cybersecurity roadmap for data protection such as website amplification, governance standing committee, security procedures, training etc. Showcasing this set of slides titled Information Internet Defence Protection Roadmap For Data Protection Topics PDF. The topics addressed in these templates are Governance Standing, Security Procedures, Awareness Workshops. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting
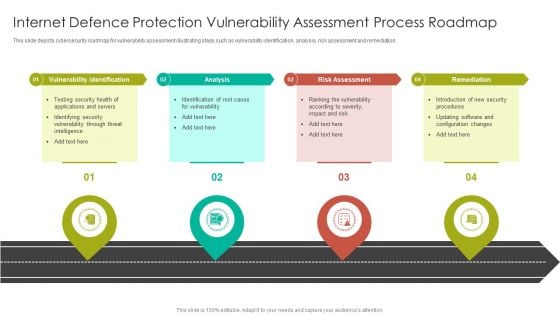
Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF
This slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation.Presenting Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Identification, Risk Assessment, Remediation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly Internet Defence Protection Evolution And Metrics Roadmap Sample PDF
This slide exhibits quarterly based cybersecurity roadmap showcasing evolution and metrics such as access control, vulnerability management, assessment and testing etc.Presenting Quarterly Internet Defence Protection Evolution And Metrics Roadmap Sample PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Auditing Documentation, Penetration Test, Administrative Privileges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
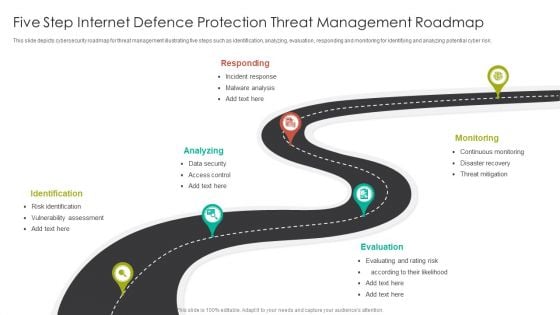
Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF
This slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk.Persuade your audience using this Five Step Internet Defence Protection Threat Management Roadmap Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Analyzing, Responding. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
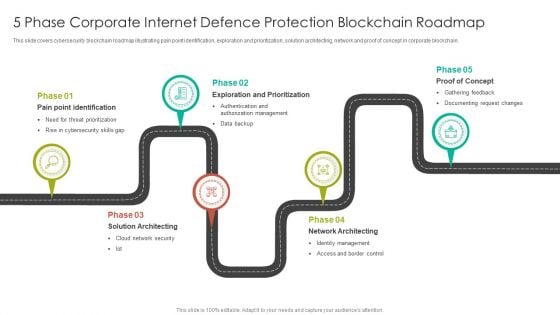
5 Phase Corporate Internet Defence Protection Blockchain Roadmap Mockup PDF
This slide covers cybersecurity blockchain roadmap illustrating pain point identification, exploration and prioritization, solution architecting, network and proof of concept in corporate blockchain.Presenting 5 Phase Corporate Internet Defence Protection Blockchain Roadmap Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Exploration And Prioritization, Proof Of Concept, Network Architecting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
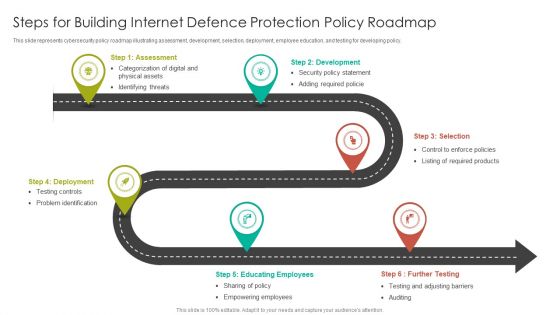
Steps For Building Internet Defence Protection Policy Roadmap Elements PDF
This slide represents cybersecurity policy roadmap illustrating assessment, development, selection, deployment, employee education, and testing for developing policy.Presenting Steps For Building Internet Defence Protection Policy Roadmap Elements PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Assessment, Development, Educating Employees. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Defence Protection Certification Roadmap For Career Advancement Information PDF
This slide represents cybersecurity certification roadmap illustrating certificates such as CompTIA ITFplus, CompTIA Aplus, CompTIA Network plus etc for professional growth.Pitch your topic with ease and precision using this Internet Defence Protection Certification Roadmap For Career Advancement Information PDF. This layout presents information on Intermediate Level, Information Security, Data Specialist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
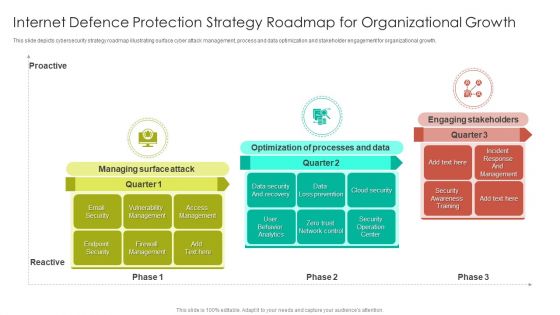
Internet Defence Protection Strategy Roadmap For Organizational Growth Demonstration PDF
This slide depicts cybersecurity strategy roadmap illustrating surface cyber attack management, process and data optimization and stakeholder engagement for organizational growth.Persuade your audience using this Internet Defence Protection Strategy Roadmap For Organizational Growth Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Optimization Processes, Engaging Stakeholders, Vulnerability Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
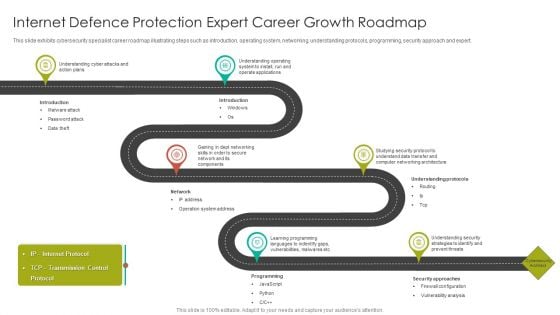
Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































