Cybersecurity Roadmap
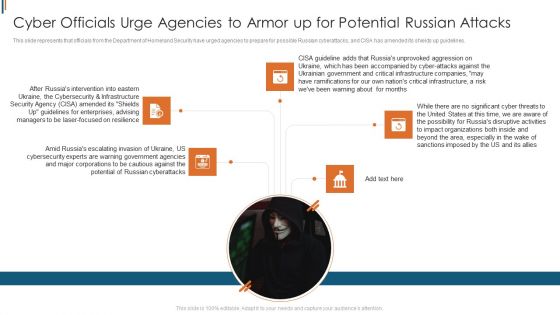
Ukraine Cyberwarfare Cyber Officials Urge Agencies To Armor Up For Potential Russian Attacks Guidelines Pdf
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting ukraine cyberwarfare cyber officials urge agencies to armor up for potential russian attacks guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like amid russias escalating invasion of ukraine, us cybersecurity experts are warning government agencies, major corporations to be cautious against the potential of russian cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
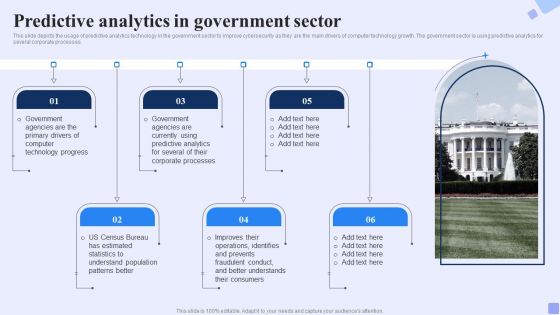
Predictive Analytics In Government Sector Forward Looking Analysis IT Download PDF
This slide depicts the usage of predictive analytics technology in the government sector to improve cybersecurity as they are the main drivers of computer technology growth. The government sector is using predictive analytics for several corporate processes. This Predictive Analytics In Government Sector Forward Looking Analysis IT Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Predictive Analytics In Government Sector Forward Looking Analysis IT Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
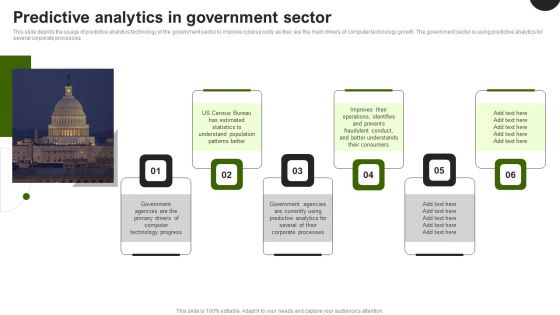
Predictive Analytics In The Age Of Big Data Predictive Analytics In Government Sector Brochure PDF
This slide depicts the usage of predictive analytics technology in the government sector to improve cybersecurity as they are the main drivers of computer technology growth. The government sector is using predictive analytics for several corporate processes. Explore a selection of the finest Predictive Analytics In The Age Of Big Data Predictive Analytics In Government Sector Brochure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Predictive Analytics In The Age Of Big Data Predictive Analytics In Government Sector Brochure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
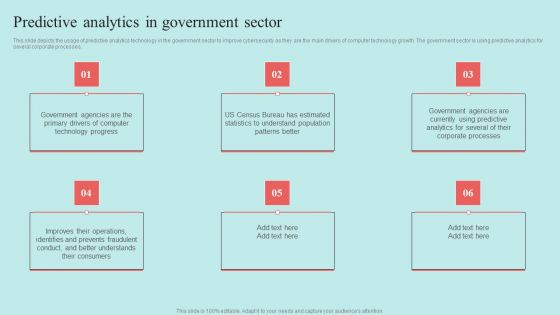
Predictive Data Model Predictive Analytics In Government Sector Graphics PDF
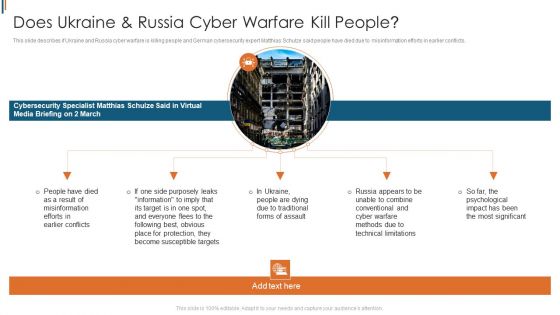
Ukraine Cyberwarfare Does Ukraine Russia Cyber Warfare Kill People Summary Pdf
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts. This is a ukraine cyberwarfare does ukraine russia cyber warfare kill people summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people have died as a result of misinformation efforts in earlier conflicts, in ukraine, people are dying due to traditional forms of assault, russia appears to be unable to combine conventional and cyber warfare methods due to technical limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
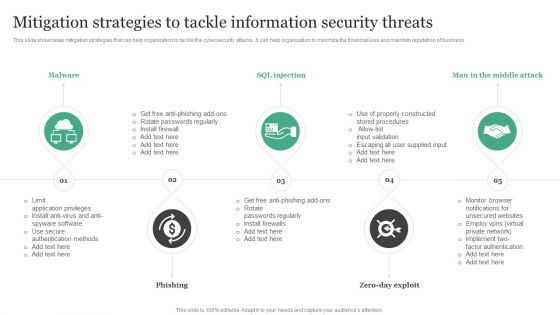
Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF.

Per Device Pricing Strategy For Managed Solutions Add More Services In The Organization Inspiration PDF
This slide covers the additional service which a company must introduce to grow in the industry such as cybersecurity services, network operation center monitoring, mobile device management solution, VoIP technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Per Device Pricing Strategy For Managed Solutions Add More Services In The Organization Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
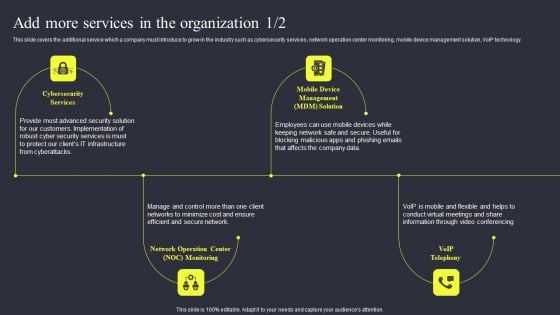
Strategies To Enhance Managed Service Business Add More Services In The Organization Diagrams PDF
This slide covers the additional service which a company must introduce to grow in the industry such as cybersecurity services, network operation center monitoring, mobile device management solution, VoIP technology. This modern and well arranged Strategies To Enhance Managed Service Business Add More Services In The Organization Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
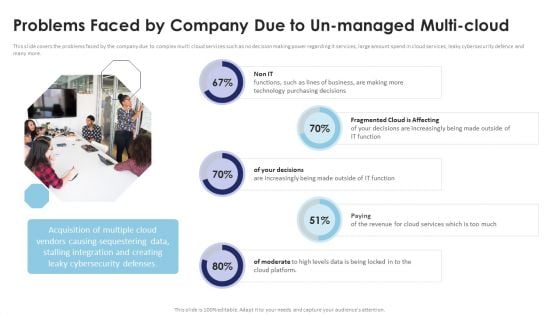
Multi Cloud Infrastructure Management Problems Faced By Company Due To Un Managed Multi Download PDF
This slide covers the problems faced by the company due to complex multi cloud services such as no decision making power regarding it services, large amount spend in cloud services, leaky cybersecurity defence and many more. The Multi Cloud Infrastructure Management Problems Faced By Company Due To Un Managed Multi Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Boosting Machine Learning 10 AI Trend In 2020 Ppt PowerPoint Presentation Show Graphic Tips PDF
Presenting this set of slides with name boosting machine learning 10 ai trend in 2020 ppt powerpoint presentation show graphic tips pdf. This is a ten stage process. The stages in this process are robotic process automation, ai healthcare more accurate, data modeling edge, ai come b2b, ai powered chatbots, automated business process, advanced cybersecurity, ai mediated media and entertainment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
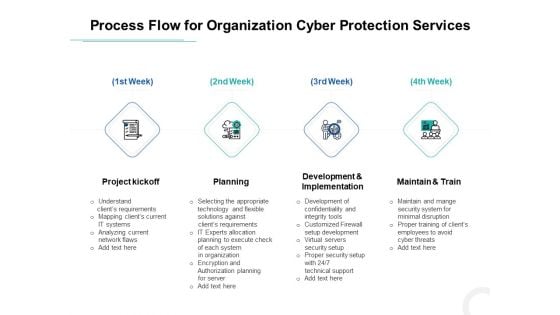
Develop Corporate Cyber Security Risk Mitigation Plan Process Flow For Organization Cyber Protection Services Background PDF
This is a develop corporate cyber security risk mitigation plan process flow for organization cyber protection services background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, maintain and train. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
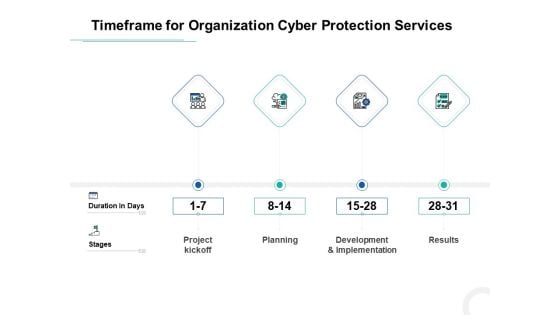
Develop Corporate Cyber Security Risk Mitigation Plan Timeframe For Organization Cyber Protection Services Structure PDF
This is a develop corporate cyber security risk mitigation plan timeframe for organization cyber protection services structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Develop Corporate Cyber Security Risk Mitigation 30 60 90 Days Plan For Organization Cyber Protection Proposal Mockup PDF
This is a develop corporate cyber security risk mitigation 30 60 90 days plan for organization cyber protection proposal mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
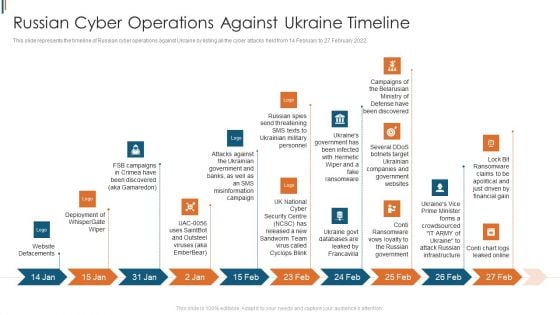
Ukraine Cyberwarfare Russian Cyber Operations Against Ukraine Timeline Portrait Pdf
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. Presenting ukraine cyberwarfare russian cyber operations against ukraine timeline portrait pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like deployment of whispergate wiper, website defacements, campaigns of the belarusian ministry of defense have been discovered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Strategies To Mitigate Cyber Security Risks 30 60 90 Days Plan Ppt Icon Picture PDF
Presenting this set of slides with name strategies to mitigate cyber security risks 30 60 90 days plan ppt icon picture pdf. This is a three stage process. The stages in this process are 30 60 90 days. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework 30 60 90 Days Plan Ppt PowerPoint Presentation Summary Background Image PDF
Presenting this set of slides with name cyber security implementation framework 30 60 90 days plan ppt powerpoint presentation summary background image pdf. This is a three stage process. The stages in this process are 30 60 90 days plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.
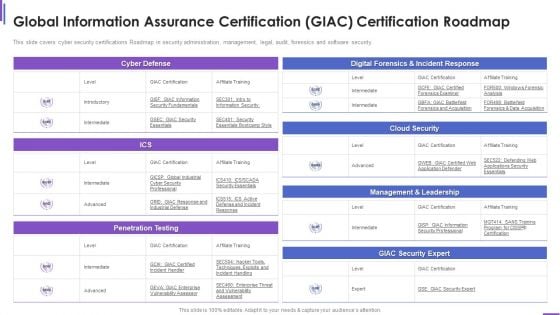
Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
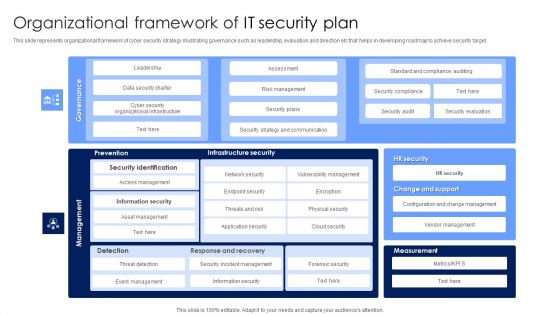
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
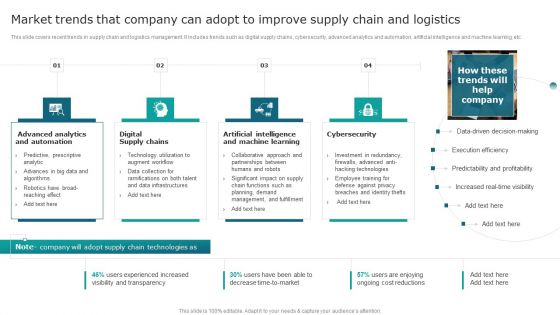
Market Trends That Company Can Adopt To Improve Supply Chain And Logistics Brochure PDF
This slide covers recent trends in supply chain and logistics management. It includes trends such as digital supply chains, cybersecurity, advanced analytics and automation, artificial intelligence and machine learning, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Market Trends That Company Can Adopt To Improve Supply Chain And Logistics Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF
This slide outlines safety measures for various hotels across hospitality sector. It involves measures such as surveillance cameras, cybersecurity, mobile room keys and providing staff training.Presenting Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cybersecurity, Security And Ensure, Staff Training This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
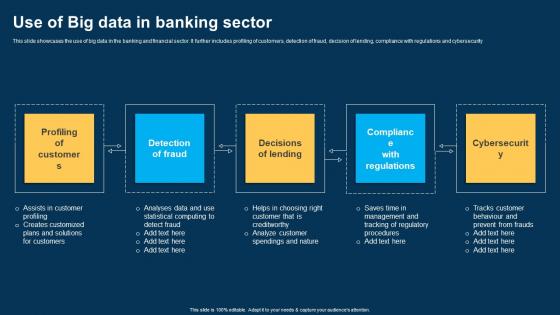
Use Of Big Data In Banking Sector Ppt Show Structure pdf
This slide showcases the use of big data in the banking and financial sector. It further includes profiling of customers, detection of fraud, decision of lending, compliance with regulations and cybersecurity. Showcasing this set of slides titled Use Of Big Data In Banking Sector Ppt Show Structure pdf. The topics addressed in these templates are Detection Fraud, Decisions Lending, Cybersecurity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the use of big data in the banking and financial sector. It further includes profiling of customers, detection of fraud, decision of lending, compliance with regulations and cybersecurity.

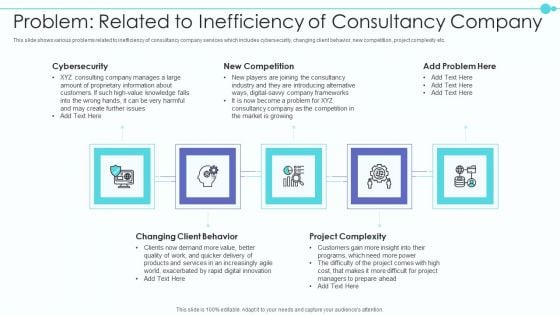
Problem Related To Inefficiency Of Consultancy Company Graphics PDF
This slide shows various problems related to inefficiency of consultancy company services which includes cybersecurity, changing client behavior, new competition, project complexity etc.This is a problem related to inefficiency of consultancy company graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project complexity, changing client behavior, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Business Model Of New Consultancy Firm Problem Related To Inefficiency Of Consultancy Company Slides PDF
This slide shows various problems related to inefficiency of consultancy company services which includes cybersecurity, changing client behavior, new competition, project complexity etc. This is a business model of new consultancy firm problem related to inefficiency of consultancy company slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, changing client behavior, project complexity, new competition. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
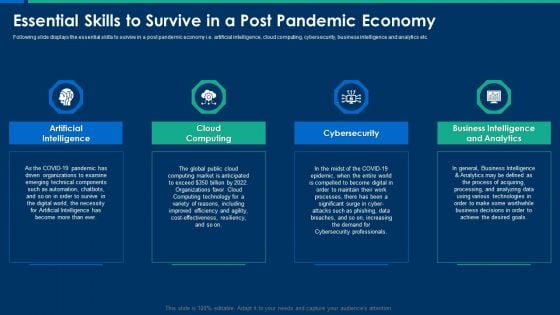
CIO Role In Digital Evolution Essential Skills To Survive In A Post Pandemic Economy Microsoft PDF
Following slide displays the essential skills to survive in a post pandemic economy i.e. artificial intelligence, cloud computing, cybersecurity, business intelligence and analytics etc. Presenting CIO Role In Digital Evolution Essential Skills To Survive In A Post Pandemic Economy Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Artificial Intelligence, Cloud Computing, Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
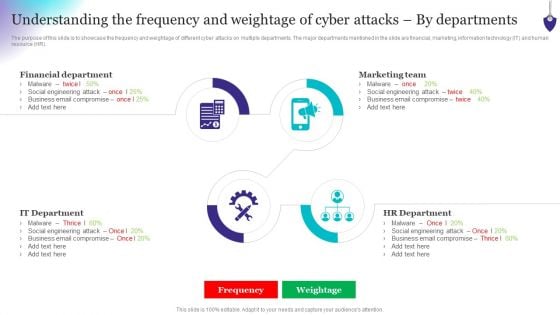
Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
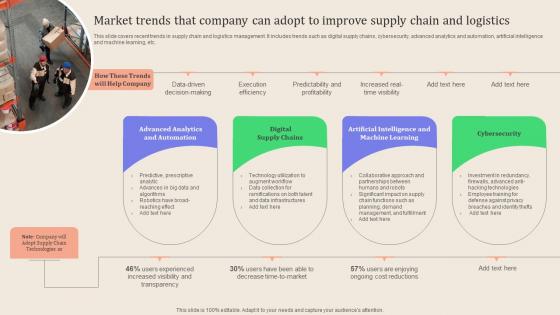
Leveraging Logistics Automation Market Trends That Company Can Adopt Inspiration Pdf
This slide covers recent trends in supply chain and logistics management. It includes trends such as digital supply chains, cybersecurity, advanced analytics and automation, artificial intelligence and machine learning, etc. Explore a selection of the finest Leveraging Logistics Automation Market Trends That Company Can Adopt Inspiration Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Leveraging Logistics Automation Market Trends That Company Can Adopt Inspiration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide covers recent trends in supply chain and logistics management. It includes trends such as digital supply chains, cybersecurity, advanced analytics and automation, artificial intelligence and machine learning, etc.
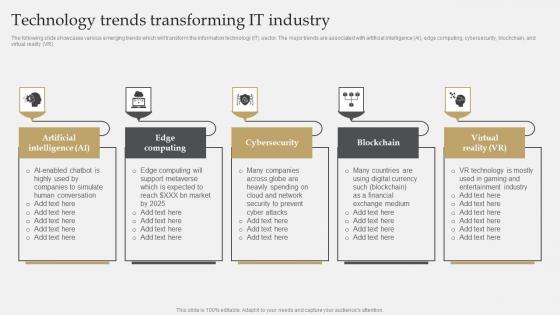
IT Industry Market Research Technology Trends Transforming It Industry Infographics Pdf
The following slide showcases various emerging trends which will transform the information technology IT sector. The major trends are associated with artificial intelligence AI, edge computing, cybersecurity, blockchain, and virtual reality VR. Welcome to our selection of the IT Industry Market Research Technology Trends Transforming It Industry Infographics Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The following slide showcases various emerging trends which will transform the information technology IT sector. The major trends are associated with artificial intelligence AI, edge computing, cybersecurity, blockchain, and virtual reality VR.
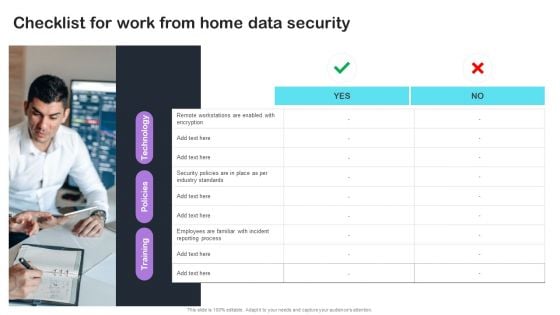
Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Zero Trust Network Security Introduction Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
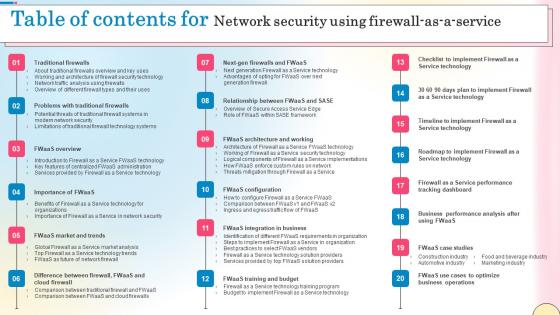
Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Back Propagation Program AI 10 AI Trend In 2020 Ppt Pictures Graphics Download PDF
This is a back propagation program ai 10 ai trend in 2020 ppt pictures graphics download pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like robotic process automation, advanced cybersecurity, ai powered chatbots, data modeling move, automated business process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
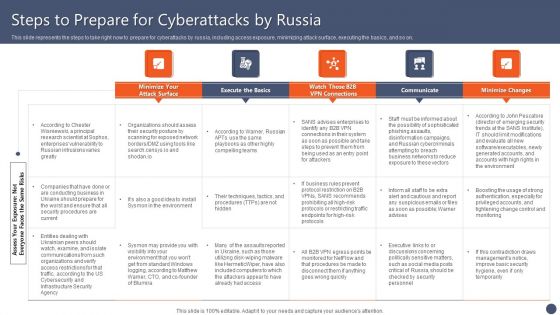
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Implementation And Analyzing Impact Of Artificial Intelligence On Organization 10 AI Trend In 2020 Icons
Presenting this set of slides with name implementation and analyzing impact of artificial intelligence on organization 10 ai trend in 2020 icons. This is a ten stage process. The stages in this process are robotic process automation, more accurate, data modeling b2b, automated business process, advanced cybersecurity, media and entertainment, operations controlled ai. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
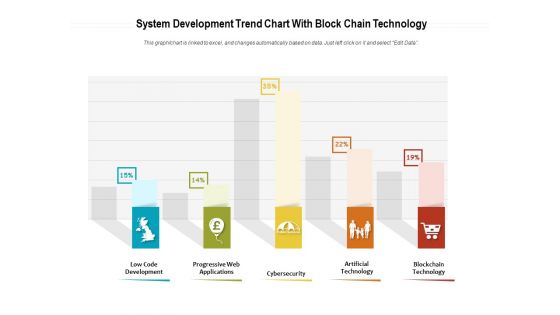
System Development Trend Chart With Block Chain Technology Ppt PowerPoint Presentation File Background Images PDF
Showcasing this set of slides titled system development trend chart with block chain technology ppt powerpoint presentation file background images pdf. The topics addressed in these templates are low code development, progressive web applications, cybersecurity, artificial technology, blockchain technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Key Tech Trends In A Post Covid 19 World Icons PDF
Presenting key tech trends in a post covid 19 world icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like artificial intelligence, cloud computing, cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Issues Faced By IT Professionals Ppt PowerPoint Presentation File Outfit PDF
Persuade your audience using this key issues faced by it professionals ppt powerpoint presentation file outfit pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including cybersecurity, skills gaps, digital transformation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
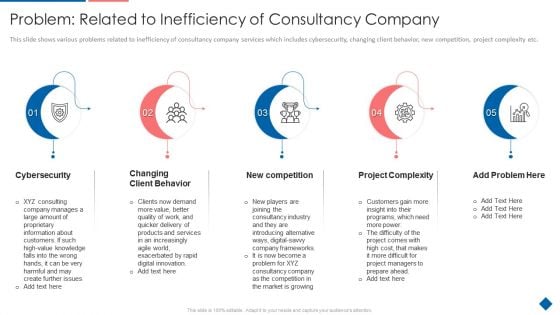
Problem Related To Inefficiency Of Consultancy Company Mockup PDF
Presenting problem related to inefficiency of consultancy company mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cybersecurity, changing client behavior, new competition, project complexity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
AI High Tech PowerPoint Templates 7 Steps Of Machine Learning Ppt Model Graphics Pictures PDF
Presenting this set of slides with name ai high tech powerpoint templates 7 steps of machine learning ppt model graphics pictures pdf. This is a ten stage process. The stages in this process are automated business process, advanced cybersecurity, robotic process automation, data modeling will move to the edge, aerospace and flight operations controlled by ai. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

COVID 19 Mitigating Impact On High Tech Industry COVID 19 Created New Revenue Opportunities For Tech Businesses Mockup PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry covid 19 created new revenue opportunities for tech businesses mockup pdf. This is a three stage process. The stages in this process are new work paradigm, heightened cybersecurity, innovative opportunities, technology, opportunity. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
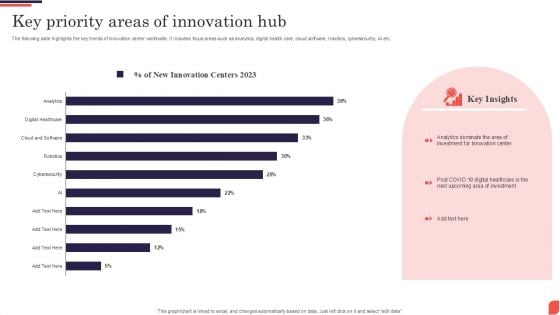
Key Priority Areas Of Innovation Hub Template PDF
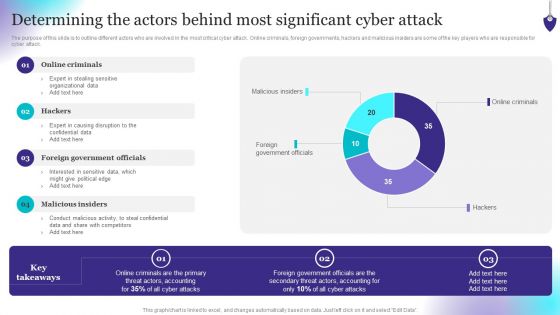
Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Diverging Flow Chart Consisting 11 Stages Business Target Network PowerPoint Slides
We present our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides.Present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Circle Charts PowerPoint Templates because they have fired the dreams of many fertile minds. Download and present our Arrows PowerPoint Templates because you have a good idea of the roadmap to your desired destination. Download and present our Shapes PowerPoint Templates because it helps you to get your team in the desired sequence into the bracket. Use our Flow charts PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Use these PowerPoint slides for presentations relating to Arrows, blank, business, central, centralized, chart, circle, circular, circulation concept, conceptual, converging, design, diagram, empty, executive, icon, idea illustration, management, map, mapping, moa, model, numbers, organization outwards, pointing, procedure, process, radial, radiating, relationship, resource sequence, sequential, seven, square, strategy, template. The prominent colors used in the PowerPoint template are Yellow, Gray, White. Presenters tell us our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides are Efficient. Presenters tell us our central PowerPoint templates and PPT Slides are Fantastic. PowerPoint presentation experts tell us our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides are Fantastic. We assure you our centralized PowerPoint templates and PPT Slides are Reminiscent. Customers tell us our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides are Excellent. People tell us our centralized PowerPoint templates and PPT Slides are Stylish. Our Diverging Flow Chart Consisting 11 Stages Business Target Network PowerPoint Slides help figure it out. Address the core aspects and dig up answers.
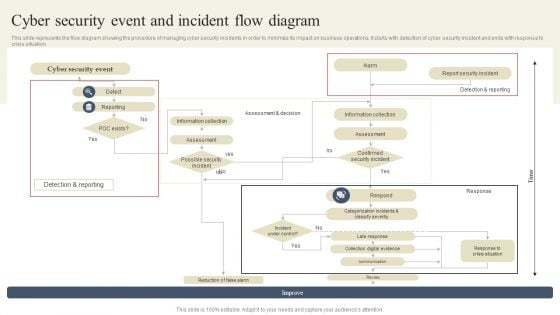
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
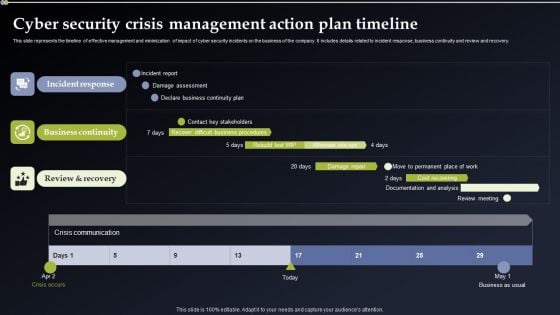
Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
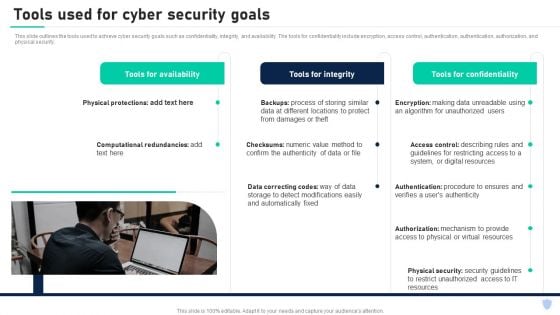
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
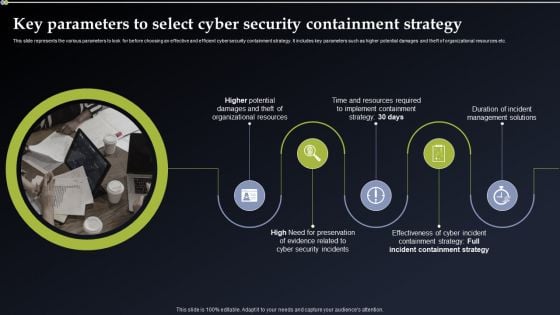
Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
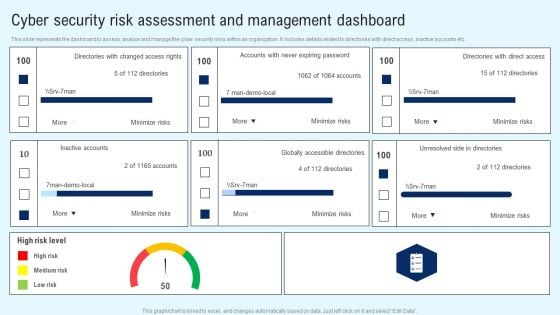
Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Running Cyber Security Awareness Campaign For Employees Background PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Running Cyber Security Awareness Campaign For Employees Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
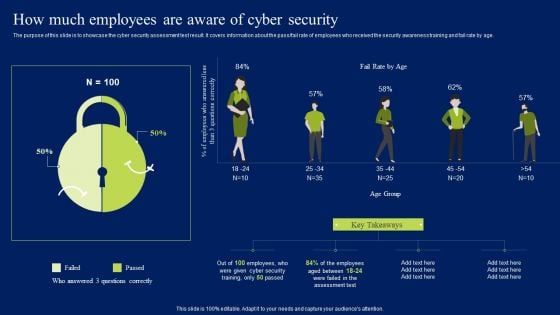
How Much Employees Are Aware Of Cyber Security Ppt Ideas Portrait PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. How Much Employees Are Aware Of Cyber Security Ppt Ideas Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
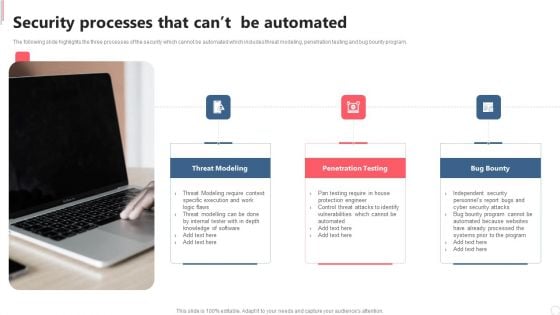
Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
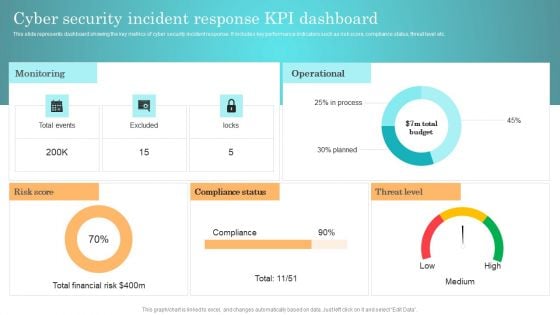
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
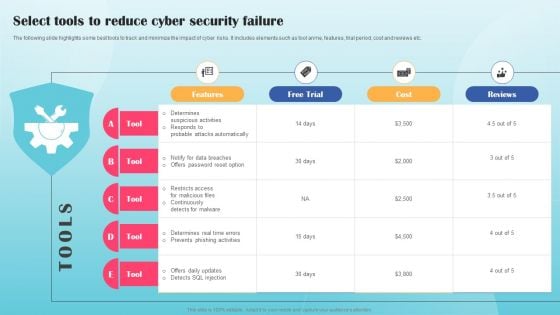
Select Tools To Reduce Cyber Security Failure Ppt PowerPoint Presentation File Show PDF
The following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Select Tools To Reduce Cyber Security Failure Ppt PowerPoint Presentation File Show PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
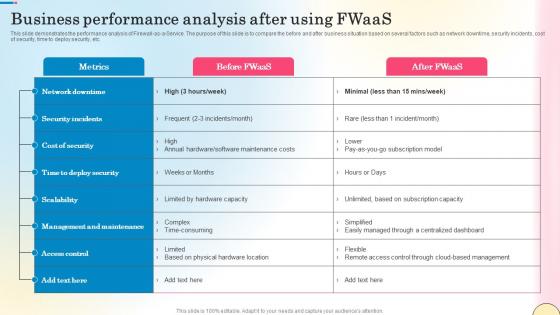
Business Performance Analysis After Using Fwaas Network Security Sample Pdf
This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Performance Analysis After Using Fwaas Network Security Sample Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
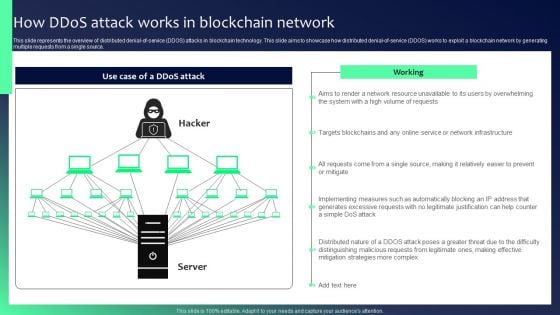
Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
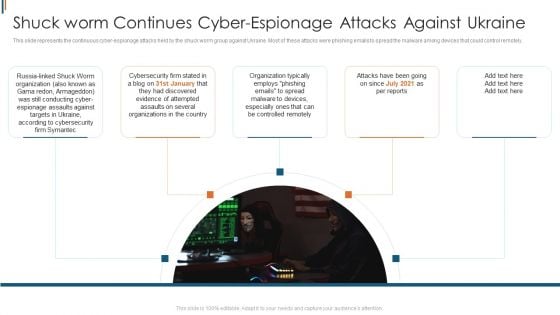
Ukraine Cyberwarfare Shuck Worm Continues Cyber Espionage Attacks Against Ukraine Pictures Pdf
This slide represents the continuous cyber espionage attacks held by the shuck worm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Presenting ukraine cyberwarfare shuck worm continues cyber espionage attacks against ukraine pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization typically, cybersecurity, evidence of attempted assaults. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































