Cybersecurity Roadmap
Cyber Security Event And Incident Flow Diagram Icons PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Event And Incident Flow Diagram Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
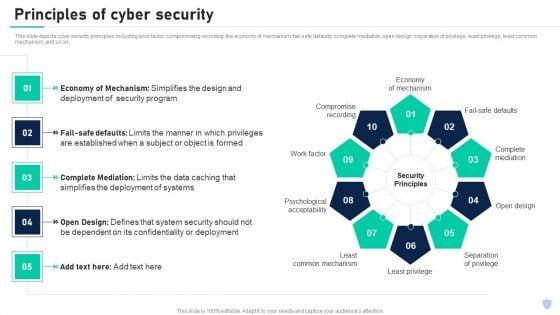
Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF
This slide depicts cyber security principles, including work factor, compromising recording, the economy of mechanism, fail-safe defaults, complete mediation, open design, separation of privilege, least privilege, least common mechanism, and so on. Get a simple yet stunning designed Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
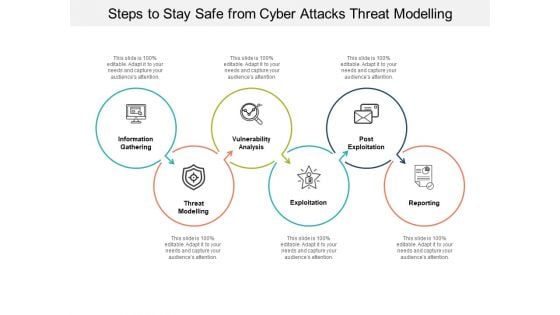
Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Network Diagrams PowerPoint Templates because It can Bubble and burst with your ideas. Use our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download and present our Signs PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience.Use these PowerPoint slides for presentations relating to One notebook with a login screen and a credit card, computer, technology, network diagrams, security, signs. The prominent colors used in the PowerPoint template are Blue, Gray, White. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Use our screen PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Customers tell us our with PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are second to none. People tell us our credit PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Evoke desires with our Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will have them enraptured.
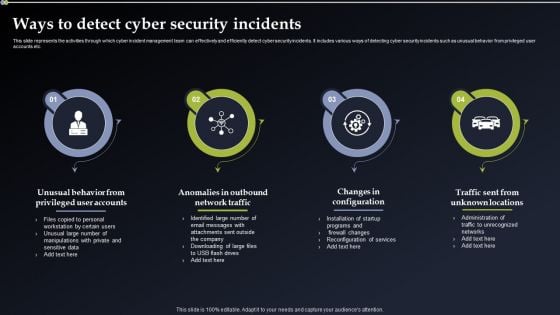
Deploying Cyber Security Incident Response Administration Ways To Detect Cyber Security Incidents Background PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Ways To Detect Cyber Security Incidents Background PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
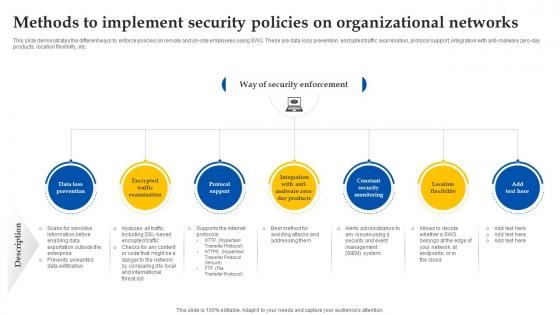
Web Access Control Solution Methods To Implement Security Policies On Organizational Networks
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Take your projects to the next level with our ultimate collection of Web Access Control Solution Methods To Implement Security Policies On Organizational Networks. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc.
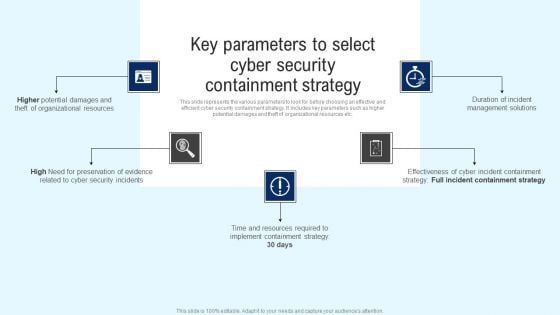
Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
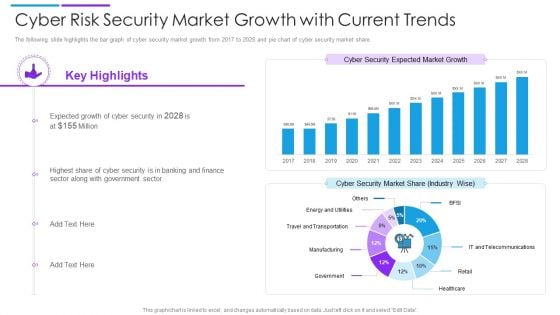
Cyber Risk Security Market Growth With Current Trends Summary PDF
The following slide highlights the bar graph of cyber security market growth from 2017 to 2028 and pie chart of cyber security market share. Showcasing this set of slides titled cyber risk security market growth with current trends summary pdf. The topics addressed in these templates are cyber security market share, cyber security expected market growth, banking and finance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Companys Data Safety Recognition Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative companys data safety recognition security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
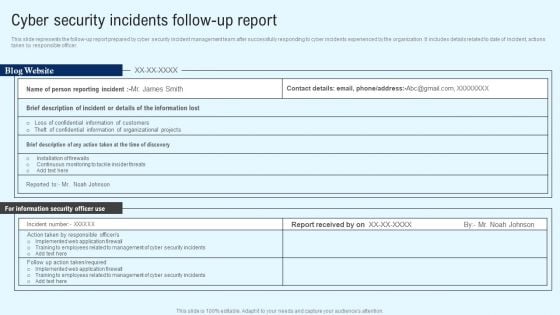
Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
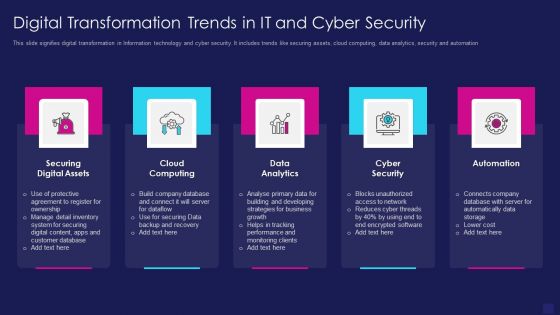
Digital Transformation Trends In It And Cyber Security Designs PDF
This slide signifies digital transformation in Information technology and cyber security. It includes trends like securing assets, cloud computing, data analytics, security and automation. Persuade your audience using this digital transformation trends in it and cyber security designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including securing digital assets, cloud computing, data analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Trends Ppt PowerPoint Presentation Show Structure Cpb
Presenting this set of slides with name cyber security trends ppt powerpoint presentation show structure cpb. This is an editable Powerpoint five stages graphic that deals with topics like cyber security trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
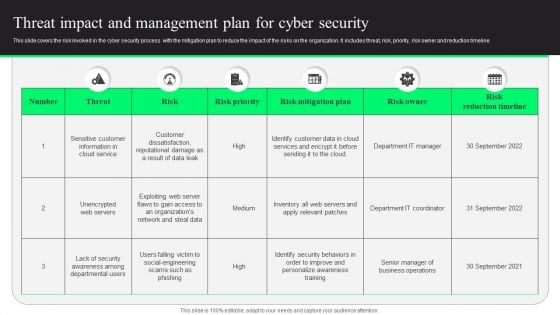
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
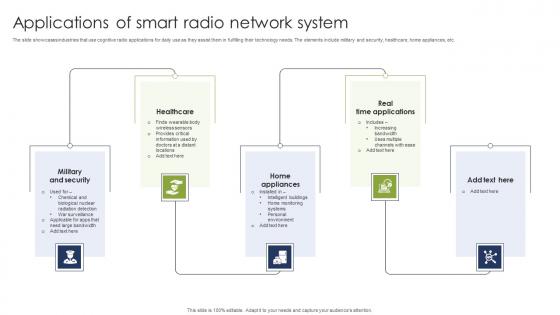
Applications Of Smart Radio Network System Summary Pdf
The slide showcases industries that use cognitive radio applications for daily use as they assist them in fulfilling their technology needs. The elements include military and security, healthcare, home appliances, etc. Showcasing this set of slides titled Applications Of Smart Radio Network System Summary Pdf. The topics addressed in these templates are Military Security, Healthcare, Home Appliances. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases industries that use cognitive radio applications for daily use as they assist them in fulfilling their technology needs. The elements include military and security, healthcare, home appliances, etc.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
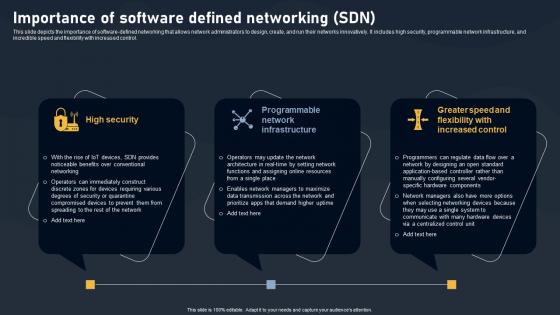
Importance Of Software Defined Networking SDN Building Blocks Topics Pdf
This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Create an editable Importance Of Software Defined Networking SDN Building Blocks Topics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Importance Of Software Defined Networking SDN Building Blocks Topics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control.
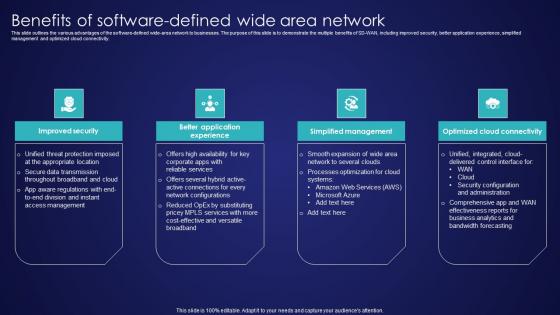
Benefits Of Software Defined Wide Area Network Wide Area Network Services Summary Pdf
This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Software Defined Wide Area Network Wide Area Network Services Summary Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity.
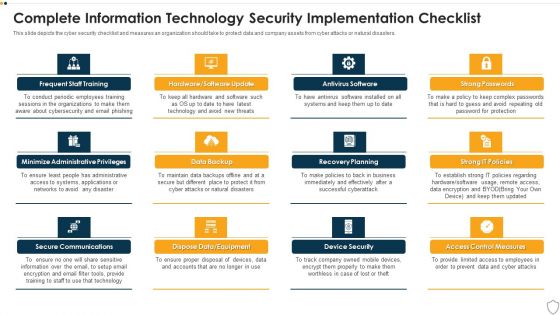
IT Security Complete Information Technology Security Implementation Checklist Ppt Inspiration Templates PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting it security complete information technology security implementation checklist ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like frequent staff training, secure communications, data backup, recovery planning, device security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
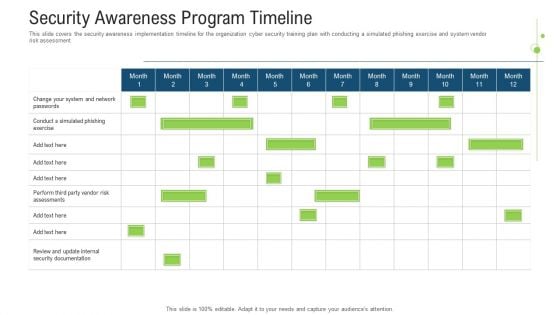
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
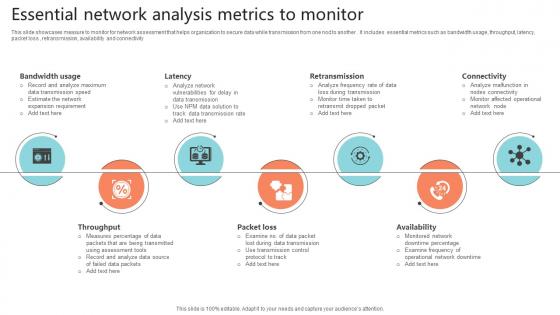
Essential Network Analysis Metrics To Monitor Portrait Pdf
This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity.Pitch your topic with ease and precision using this Essential Network Analysis Metrics To Monitor Portrait Pdf This layout presents information on Bandwidth Usage, Retransmission, Throughput It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity

Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf
This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation.
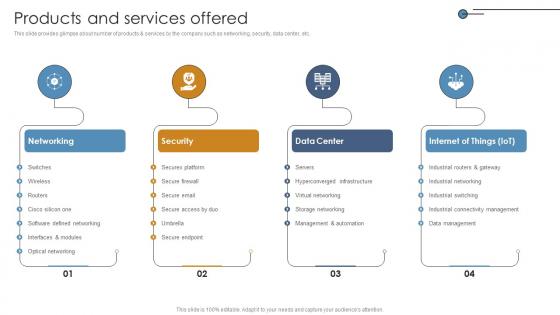
Products And Services Offered Networking Solutions Manufacturer Investor Funding Elevator Pitch Deck
This slide provides glimpse about number of products services by the company such as networking, security, data center, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Networking Solutions Manufacturer Investor Funding Elevator Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides glimpse about number of products services by the company such as networking, security, data center, etc.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
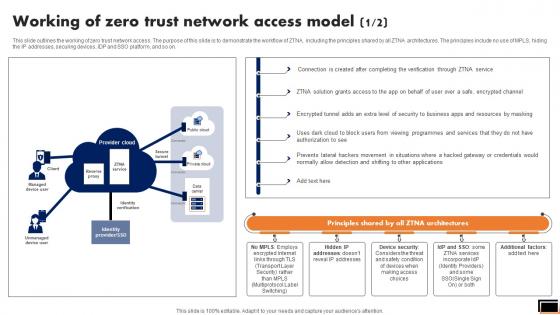
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.
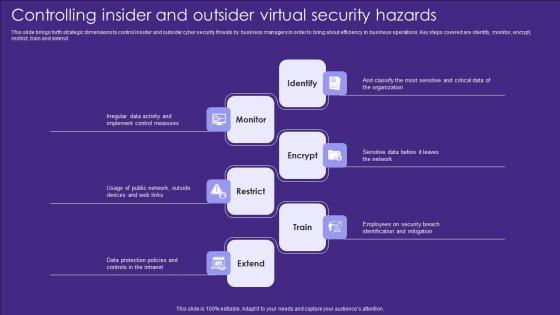
Controlling Insider And Outsider Virtual Security Hazards Designs Pdf
This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Showcasing this set of slides titled Controlling Insider And Outsider Virtual Security Hazards Designs Pdf. The topics addressed in these templates are Identify, Monitor, Encrypt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
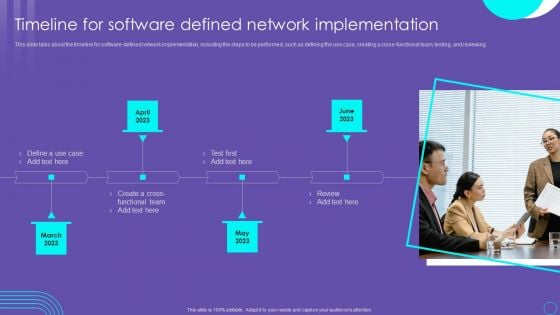
SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF
This slide talks about the timeline for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Want to ace your presentation in front of a live audience Our SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.

Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secure Internet Browser Networking PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Internet PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our Technology PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Communication PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate.Use these PowerPoint slides for presentations relating to Secure internet browser, internet, technology, security, communication, business. The prominent colors used in the PowerPoint template are Yellow, Orange, Gray. Report problems with our Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.
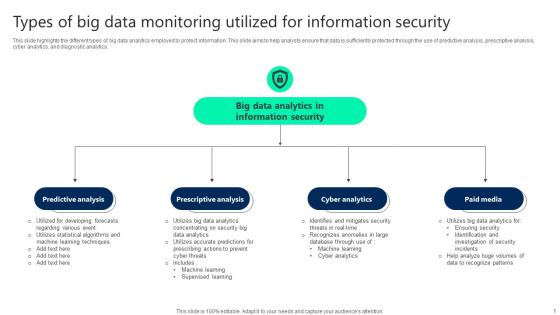
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics.
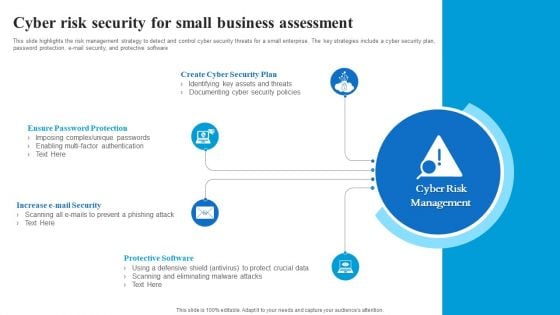
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
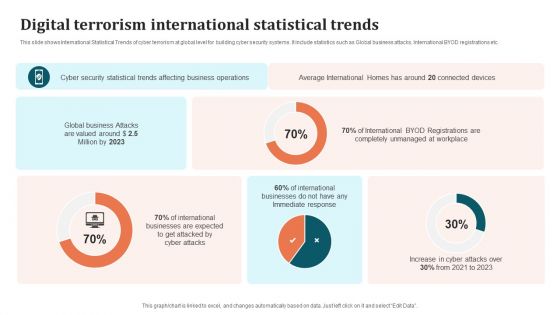
Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Process Compliance Ppt PowerPoint Presentation Ideas Inspiration Cpb
Presenting this set of slides with name cyber security process compliance ppt powerpoint presentation ideas inspiration cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security process compliance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
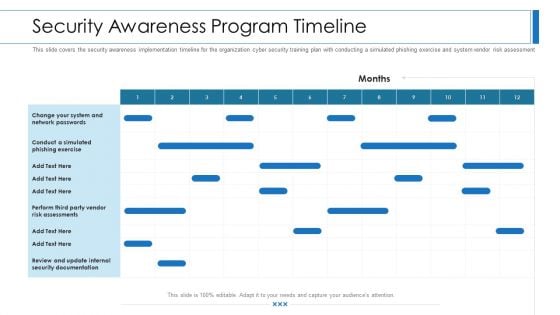
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Timeline For The Implementation Of Information Technology Security Structure PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative it security timeline for the implementation of information technology security structure pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
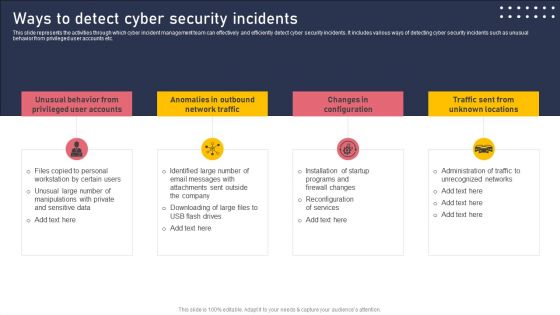
Ways To Detect Cyber Security Incidents Template PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Ways To Detect Cyber Security Incidents Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Ways To Detect Cyber Security Incidents Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Divisional Strategy To Improve Cyber Security Measures Icons PDF
This slide signifies information technology department to enhance cyber security measures. It also includes stages like identify, plan, execute and control. Presenting IT Divisional Strategy To Improve Cyber Security Measures Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Plan, Execute, Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
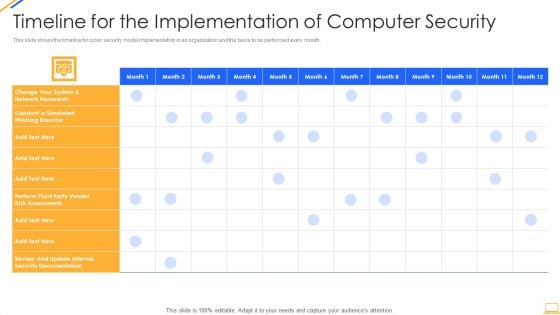
Desktop Security Management Timeline For The Implementation Of Computer Security Sample PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this desktop security management timeline for the implementation of computer security sample pdf. Use them to share invaluable insights on security documentation, system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
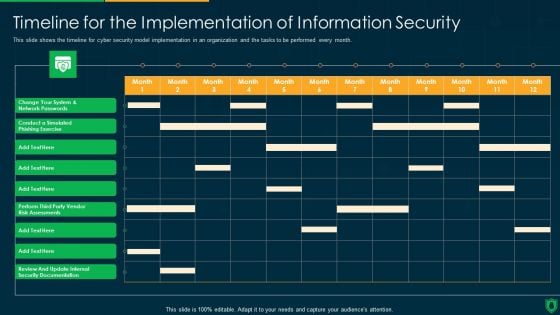
Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
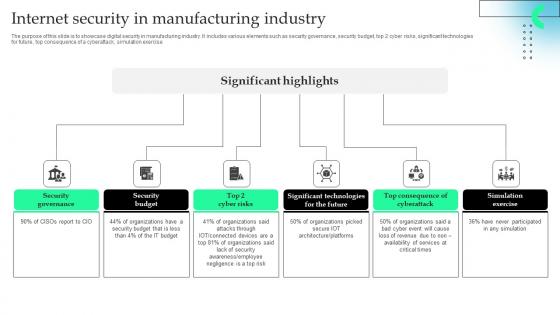
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.
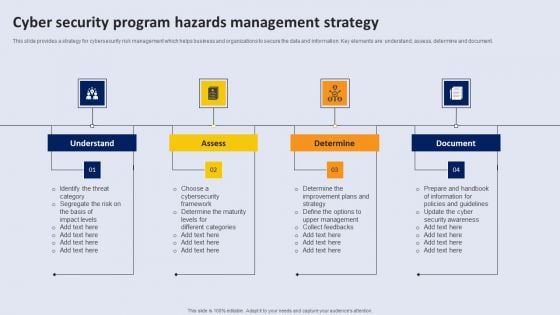
Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
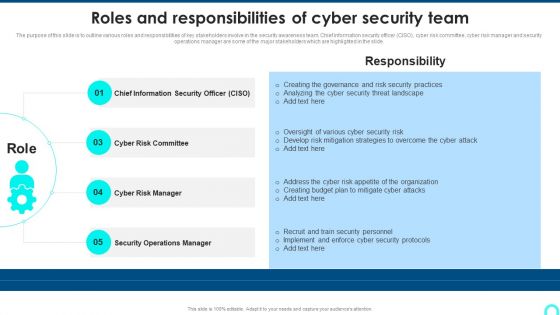
Roles And Responsibilities Of Cyber Security Team Designs PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide.This is a Roles And Responsibilities Of Cyber Security Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Operations Manager, Risk Manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
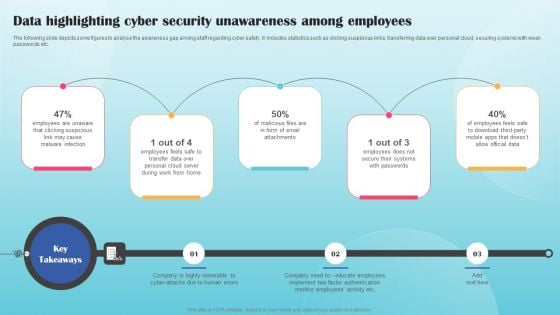
Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
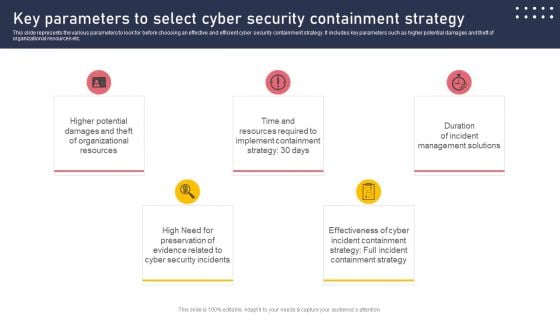
Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Key Parameters To Select Cyber Security Containment Strategy Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
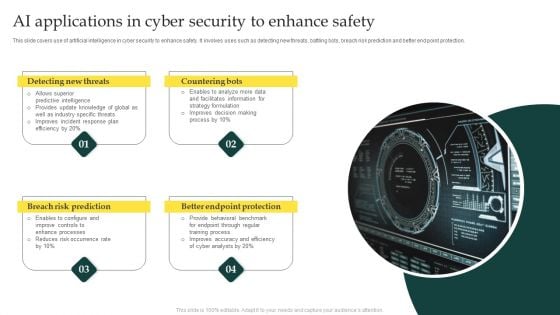
AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Eight Steps Infographics To Improve Cyber Security Icons PDF
Persuade your audience using this eight steps infographics to improve cyber security icons pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including threats, knowledge, monitoring, authentication, protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
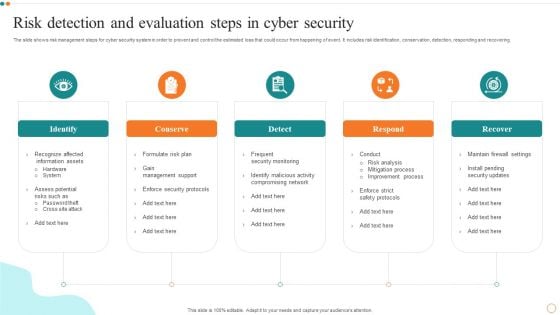
Risk Detection And Evaluation Steps In Cyber Security Designs PDF
Persuade your audience using this Risk Detection And Evaluation Steps In Cyber Security Designs PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Detection, Evaluation Steps. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
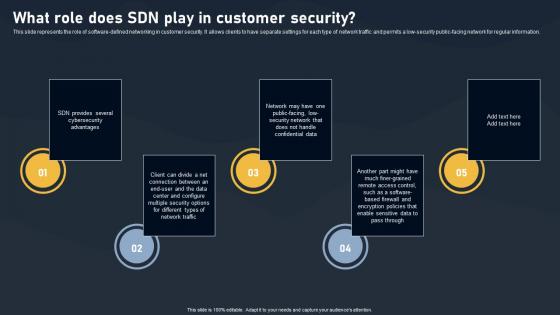
What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.This modern and well-arranged What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information.
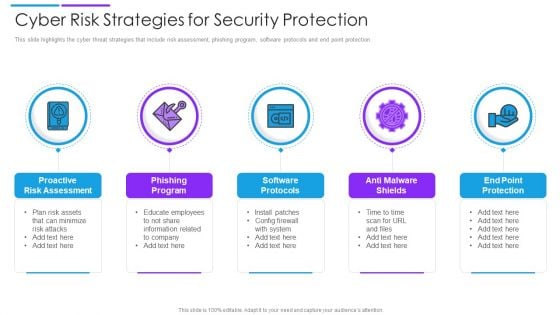
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
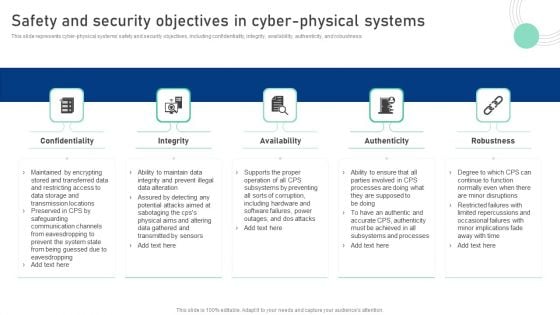
Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF
This slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present like a pro with Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
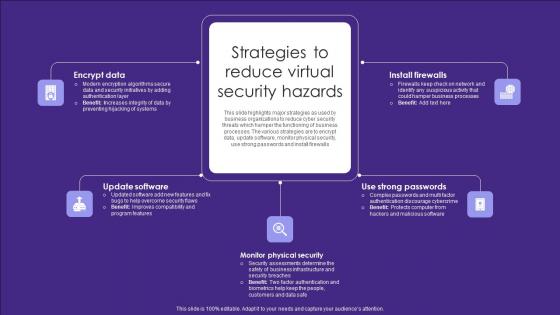
Strategies To Reduce Virtual Security Hazards Summary Pdf
This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Showcasing this set of slides titled Strategies To Reduce Virtual Security Hazards Summary Pdf. The topics addressed in these templates are Install Firewalls, Strong Passwords, Physical Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls
Building Data Analytics And Cyber Security Strategy Framework Icons PDF
This slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Persuade your audience using this Building Data Analytics And Cyber Security Strategy Framework Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Expansion, Standardize And Automate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
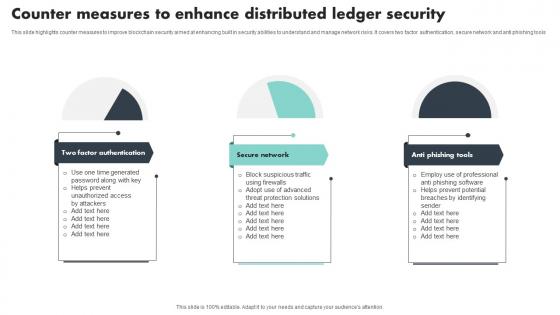
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools


 Continue with Email
Continue with Email

 Home
Home


































