Data Privacy
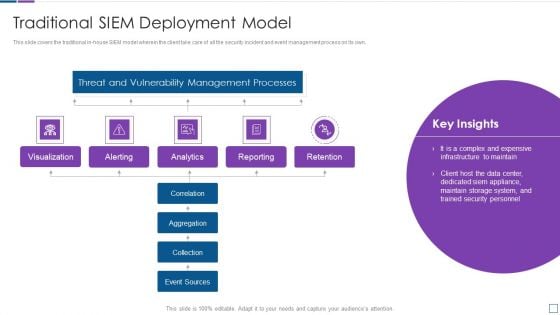
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
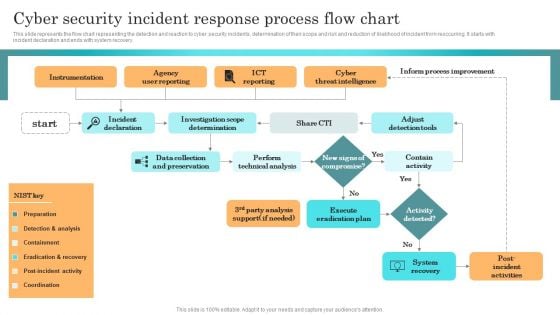
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.
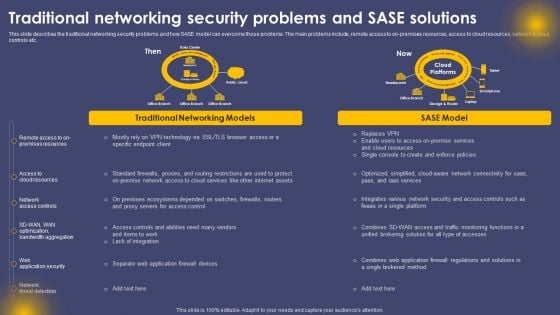
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.
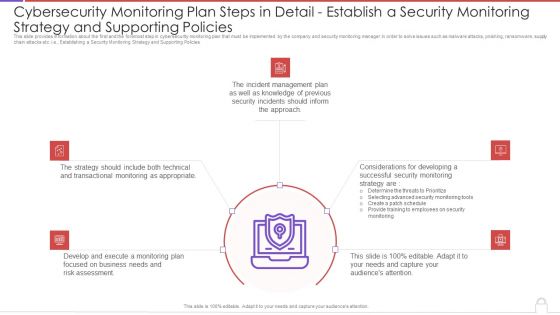
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
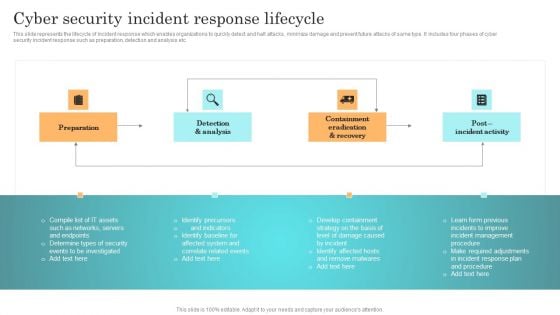
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Green Secure Word On Keyboard PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Green Secure Word On Keyboard PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Use our Business PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download and present our Shapes PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Download and present our Technology PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake.Use these PowerPoint slides for presentations relating to Green secure word on keyboard, Computer, Signs, Shapes, Technology, Business . The prominent colors used in the PowerPoint template are Green, Black, Gray. No matter how far you have to go. Our Green Secure Word On Keyboard PowerPoint Templates Ppt Backgrounds For Slides 0213 have the drive to get you there.
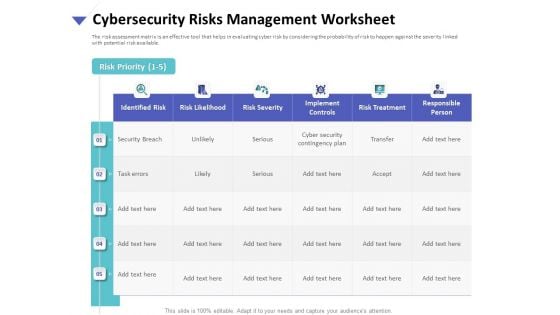
Strategies To Mitigate Cyber Security Risks Cybersecurity Risks Management Worksheet Ppt Gallery Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity risks management worksheet ppt gallery influencers pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Determining Firm Current Capabilities Ppt Inspiration Smartart PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining firm current capabilities ppt inspiration smartart pdf. The topics discussed in these slides are identify, protect, detect, response, recovery, key enablers, minimum standard, evolving strength. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Customized Plan For Security Guard Services Proposal Ppt Show Format PDF
Deliver and pitch your topic in the best possible manner with this customized plan for security guard services proposal ppt show format pdf. Use them to share invaluable insights on staffing, training and implementation, reporting and review, plan presentation and contract signing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slide For Security Guard Services Proposal Ppt Summary Design Inspiration PDF
Introducing our well-designed icons slide for security guard services proposal ppt summary design inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
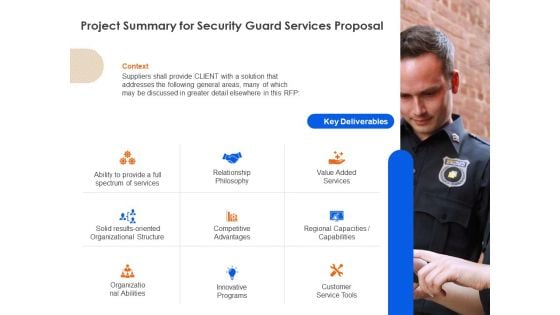
Project Summary For Security Guard Services Proposal Ppt Ideas Guide PDF
Deliver an awe-inspiring pitch with this creative project summary for security guard services proposal ppt ideas guide pdf bundle. Topics like organizational abilities, relationship philosophy, competitive advantages, innovative programs, value added services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Workforce Security Realization Coaching Plan Icons Slide Ppt Ideas Topics PDF
Introducing our well-designed workforce security realization coaching plan icons slide ppt ideas topics pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
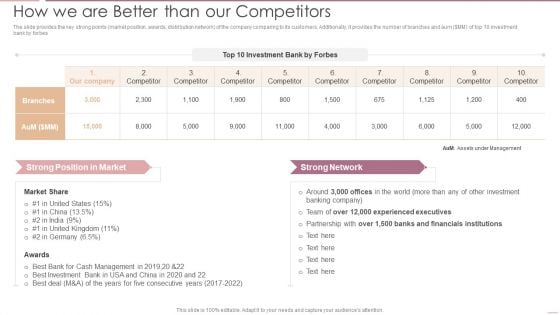
Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF
Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF bundle. Topics like Experienced Executives, Financials Institutions, Cash Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF
There are so many reasons you need a Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF. The first reason is you canot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Icon Slide For Security Control Techniques For Real Estate Project Clipart PDF
Presenting our innovatively structured Icon Slide For Security Control Techniques For Real Estate Project Clipart PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF
Introducing our well designed Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Present our Arrows PowerPoint Templates because You can Bind your ideas with our PowerPoint Templates and Slides. They will add great value to the worth of your package. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Finance PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Success PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level.Use these PowerPoint slides for presentations relating to Internet Virus, technology, arrows, signs, finance, success. The prominent colors used in the PowerPoint template are Yellow, Black, White. Professionals tell us our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. You can be sure our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 will make you look like a winner. PowerPoint presentation experts tell us our arrows PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Our Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113 are like angels. They take extraordinary care of your thoughts.

Folder And Alarm Clock Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Time Planning PowerPoint Templates because the vision of being the market leader is clear to you. Download our Internet PowerPoint Templates because there are a bucketful of brilliant ideas swirling around within your group. Download our Computer PowerPoint Templates because you can Transmit your thoughts via our slides and proud your team to action. Download and present our Success PowerPoint Templates because the success of your venture depends on the performance of every team member. Present our Business PowerPoint Templates because everybody knows The world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised.Use these PowerPoint slides for presentations relating to Alarm clock and folder, business, time planning, internet, computer, success. The prominent colors used in the PowerPoint template are Red, Yellow, White. Professionals tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Stylish. Use our folder PowerPoint templates and PPT Slides are Fantastic. We assure you our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficient. We assure you our time PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Presenters tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Reminiscent. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides are Cheerful. Analyze growth with our Folder And Alarm Clock Security PowerPoint Templates Ppt Backgrounds For Slides 1212. Download without worries with our money back guaranteee.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
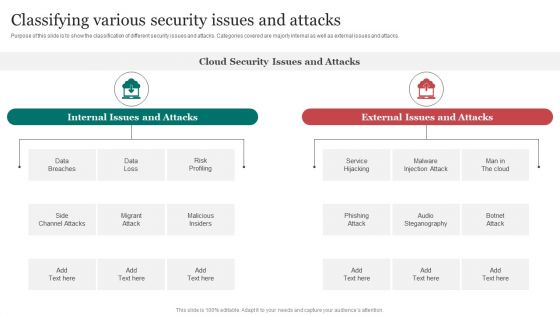
Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
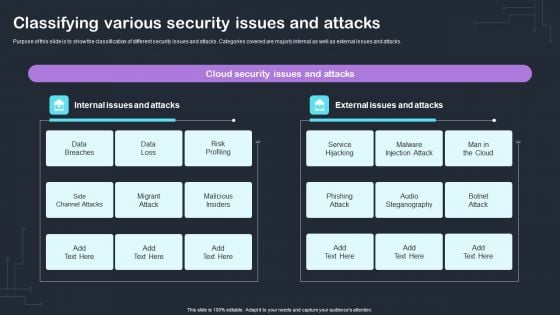
Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
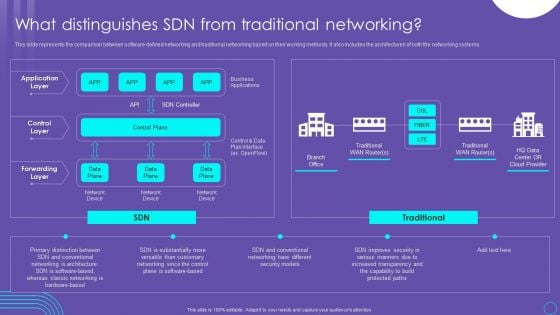
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
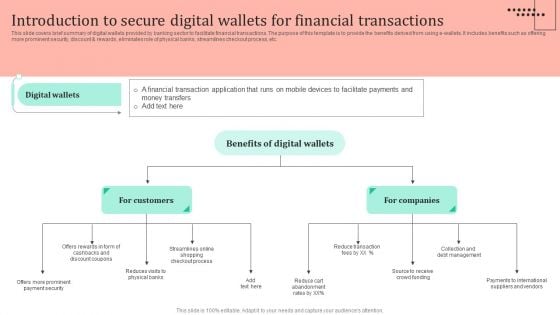
Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Welcome to our selection of the Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
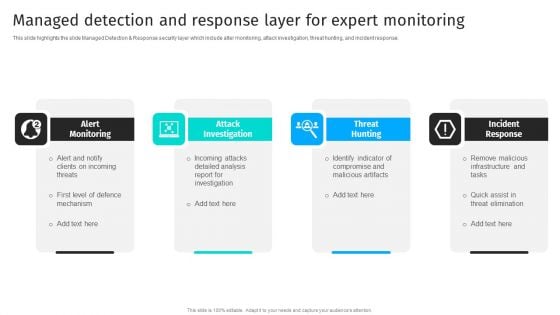
Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF
This slide highlights the slide Managed Detection Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Use Internet Security For Business PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Present our Globe PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Computer mouse is connected to a globe - surfing and browsing is blocked by a red do not enter sign that cuts the cable, technology, communication, signs, globe, business. The prominent colors used in the PowerPoint template are Blue, White, Black. Our Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413 will keep the faith. They will show allegiance to your thoughts.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
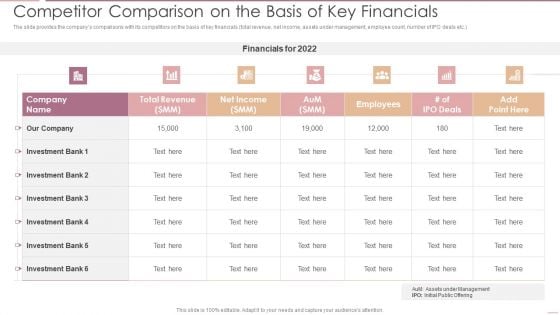
Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF
The slide provides the companys comparisons with its competitors on the basis of key financials total revenue, net income, assets under management, employee count, number of IPO deals etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF bundle. Topics like Total Revenue, Net Income, Investment Bank can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
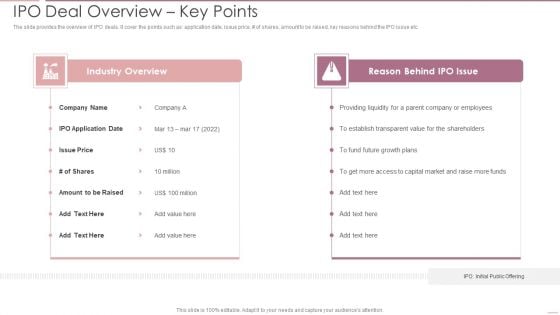
Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF
The slide provides the overview of IPO deals. It cover the points such as application date, issue price, of shares, amount to be raised, key reasons behind the IPO issue etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF bundle. Topics like Industry Overview, Reason Behind, Providing Liquidity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
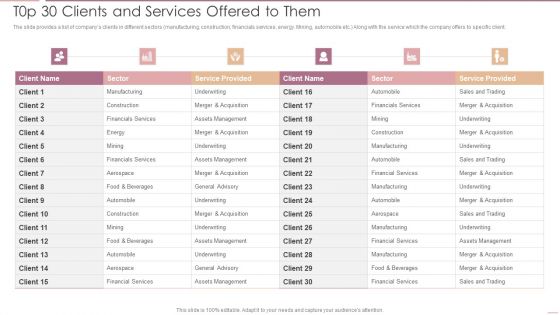
Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. Along with the service which the company offers to specific client.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF bundle. Topics like Financials Services, Assets Management, Underwriting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
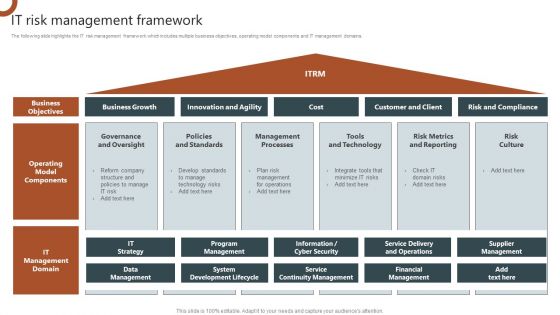
IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF
The following slide highlights the IT risk management framework which includes multiple business objectives, operating model components and IT management domains. There are so many reasons you need a IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
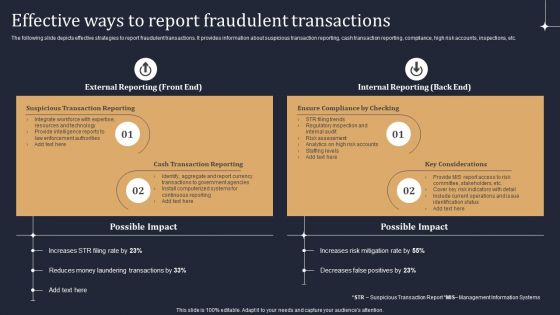
KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF from Slidegeeks and deliver a wonderful presentation.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Determine Project Safety Management Team Structure Sample PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a project security administration it determine project safety management team structure sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like public affair advisor, security manager, legal advisor, medical advisor, crisis management advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
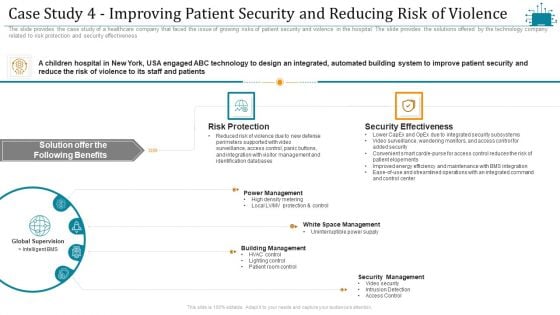
Cloud Intelligence Framework For Application Consumption Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like power management, building management, security management, security effectiveness, global supervision can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
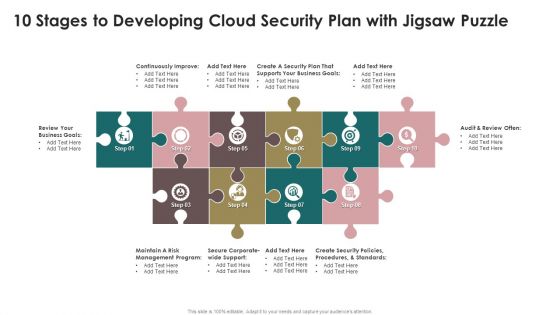
10 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Themes PDF
Presenting 10 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Themes PDF to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
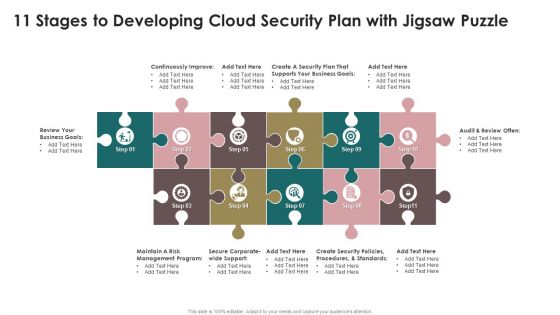
11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF
Presenting 11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF to dispense important information. This template comprises eleven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
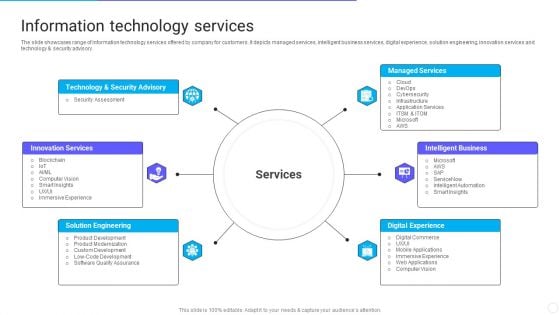
IT Application Services Company Outline Information Technology Services Ideas PDF
The slide showcases range of information technology services offered by company for customers. It depicts managed services, intelligent business services, digital experience, solution engineering, innovation services and technology and security advisory. Presenting IT Application Services Company Outline Information Technology Services Ideas PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Advisory, Managed Services, Intelligent Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
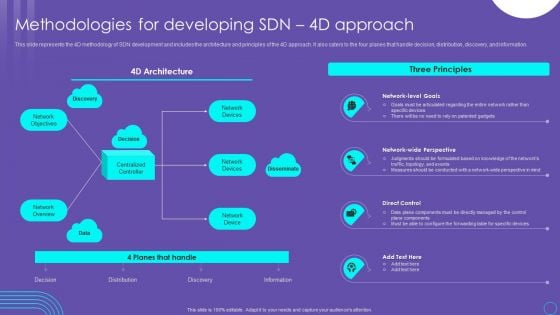
SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF
This slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF.
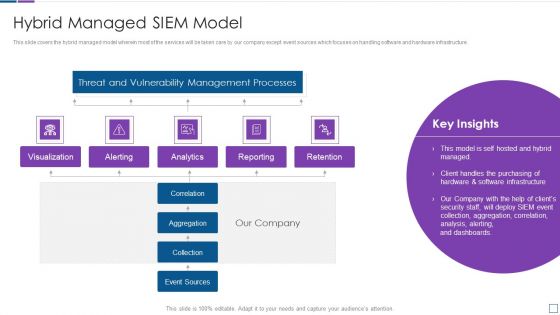
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
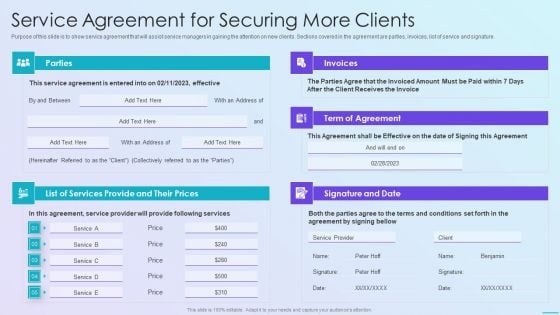
Playbook For Application Developers Service Agreement For Securing More Clients Ideas PDF
Purpose of this slide is to show service agreement that will assist service managers in gaining the attention on new clients. Sections covered in the agreement are parties, invoices, list of service and signature.Deliver and pitch your topic in the best possible manner with this playbook for application developers service agreement for securing more clients ideas pdf Use them to share invaluable insights on term of agreement, signature and date, invoices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF
The slide provides the key players in the industry by companys size top large companies, mid market companies, small or boutique companies etc.. It has also mentioned the companys major competitors.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF Use them to share invaluable insights on Investment Banks, Boutique Investment, Large Investment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
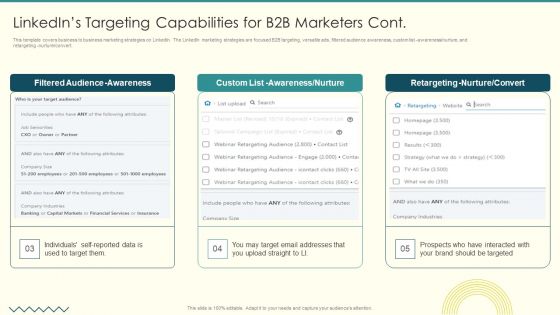
Security And Performance Digital Marketing Linkedins Targeting Capabilities For B2B Marketers Cont Graphics PDF
This template covers business to business marketing strategies on LinkedIn. The LinkedIn marketing strategies are focused B2B targeting, versatile ads, filtered audience awareness, custom list awareness nurture, and retargeting nurture convert.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Linkedins Targeting Capabilities For B2B Marketers Cont Graphics PDF bundle. Topics like Filtered Audience, Awareness Nurture, Retargeting Nurture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
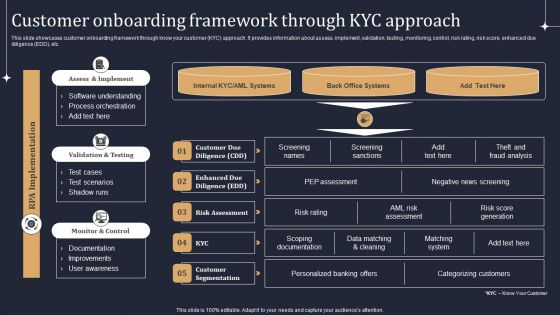
KYC Transaction Monitoring System Business Security Customer Onboarding Framework Introduction PDF
Welcome to our selection of the KYC Transaction Monitoring System Business Security Customer Onboarding Framework Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
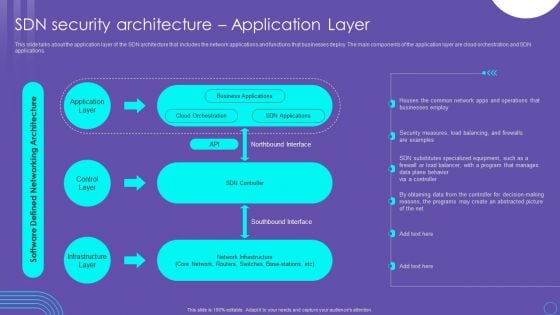
SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF
This slide talks about the application layer of the SDN architecture that includes the network applications and functions that businesses deploy. The main components of the application layer are cloud orchestration and SDN applications. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
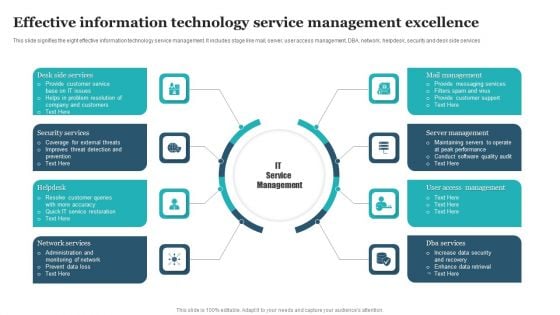
Effective Information Technology Service Management Excellence Rules PDF
This slide signifies the eight effective information technology service management. It includes stage like mail, server, user access management, DBA, network, helpdesk, security and desk side services. Presenting Effective Information Technology Service Management Excellence Rules PDF to dispense important information. This template comprises Eight stages. It also presents valuable insights into the topics including Desk Side Services, Mail Management, Security Services, Server Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
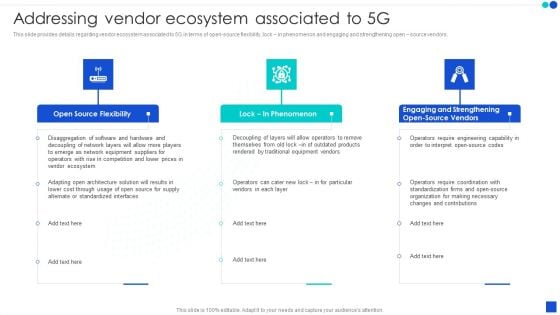
5G Technology Development For Digital Transformation Addressing Vendor Ecosystem Associated To 5G Mockup PDF
This slide provides details regarding vendor ecosystem associated to 5G in terms of open source flexibility, lock in phenomenon and engaging and strengthening open source vendors. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our 5G Technology Development For Digital Transformation Addressing Vendor Ecosystem Associated To 5G Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into 5G Technology Development For Digital Transformation Addressing Vendor Ecosystem Associated To 5G Mockup PDF.
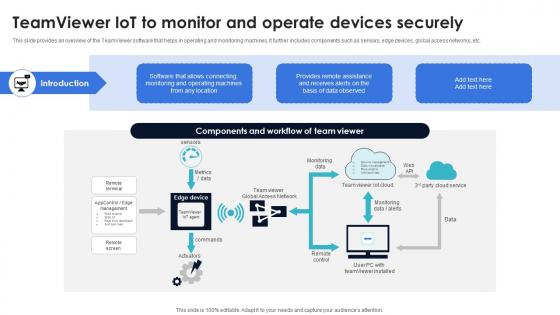
Optimization Of IoT Remote Monitoring Teamviewer IoT To Monitor And Operate Devices Securely IoT SS V
This slide provides an overview of the TeamViewer software that helps in operating and monitoring machines. It further includes components such as sensors, edge devices, global access networks, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Optimization Of IoT Remote Monitoring Teamviewer IoT To Monitor And Operate Devices Securely IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Optimization Of IoT Remote Monitoring Teamviewer IoT To Monitor And Operate Devices Securely IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides an overview of the TeamViewer software that helps in operating and monitoring machines. It further includes components such as sensors, edge devices, global access networks, etc.
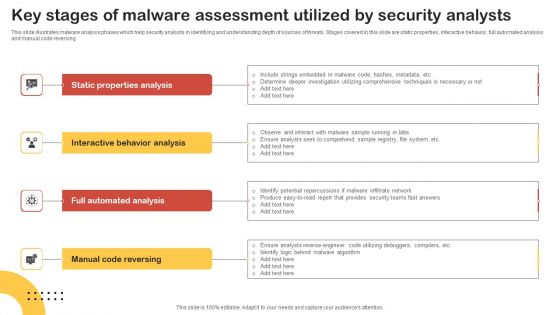
Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Impact On Food Demand And Food Security Due To Covid Crisis Ppt Pictures Layout PDF
This template covers Impact On Food Demand And Food Security such as demand of food has affected due to reduction in income and purchasing capacity. It also covers the impact of school closure on childrens who are dependent on school meal programs. This is a impact on food demand and food security due to covid crisis ppt pictures layout pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management strategy, price, source, services, production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
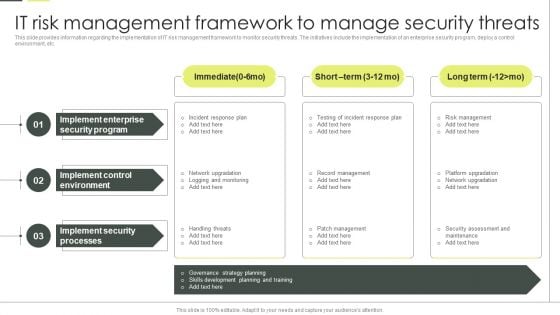
Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
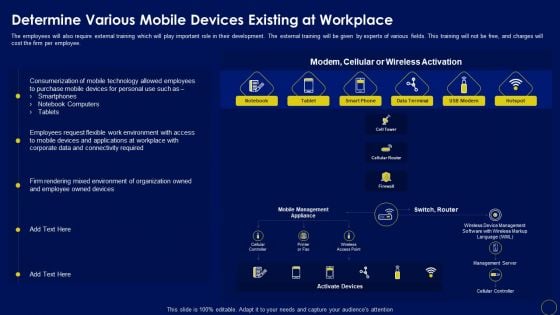
Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
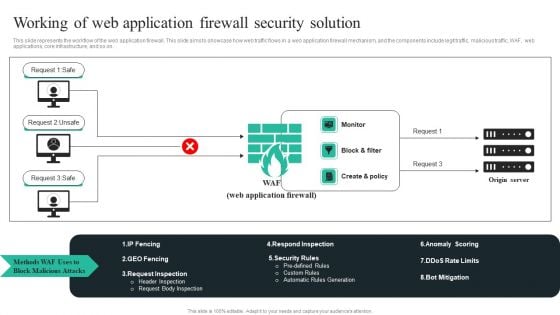
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Problem Related Drug Alcohol Abuse Workplace Safety Protocol And Security Practices Brochure Pdf
The following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work. Take your projects to the next level with our ultimate collection of Problem Related Drug Alcohol Abuse Workplace Safety Protocol And Security Practices Brochure Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work.
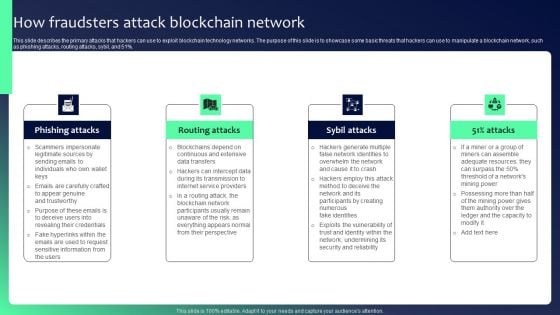
Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents For Web Development Clipart PDF
This is a Table Of Contents For Web Development Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Technique, Embedded Web Development, Security Web Development You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
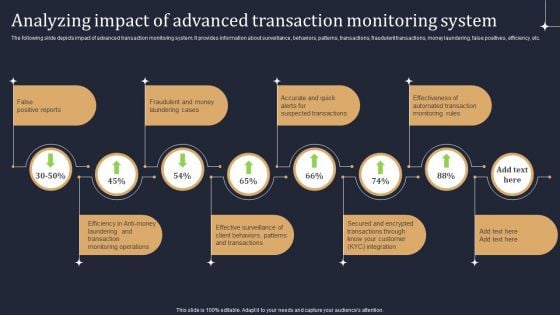
KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
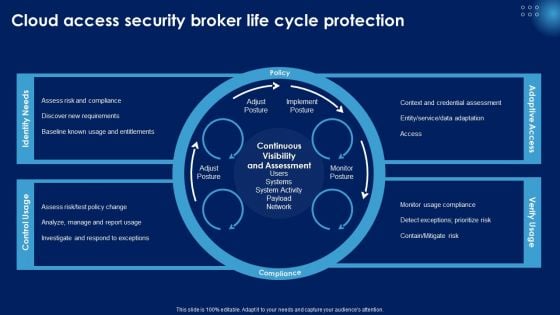
Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.


 Continue with Email
Continue with Email

 Home
Home


































