Data Privacy

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
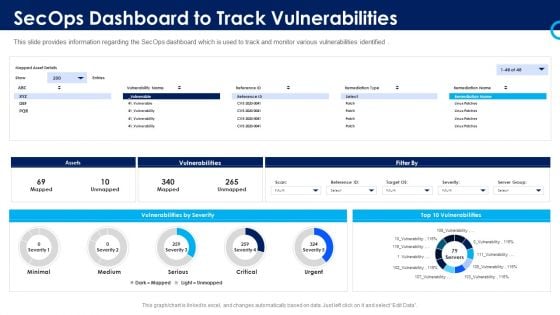
Organizational Security Solutions Secops Dashboard To Track Vulnerabilities Pictures PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this organizational security solutions secops dashboard to track vulnerabilities pictures pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
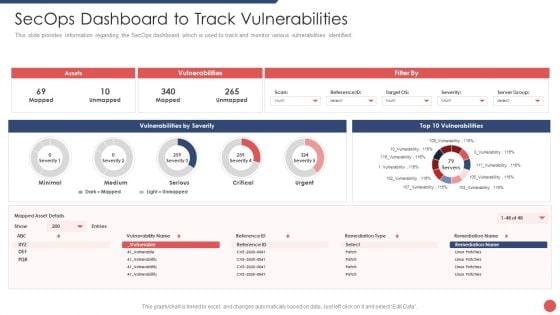
Security Functioning Centre Secops Dashboard To Track Vulnerabilities Portrait PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver an awe inspiring pitch with this creative security functioning centre secops dashboard to track vulnerabilities portrait pdf bundle. Topics like assets, vulnerabilities, vulnerabilities by severity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
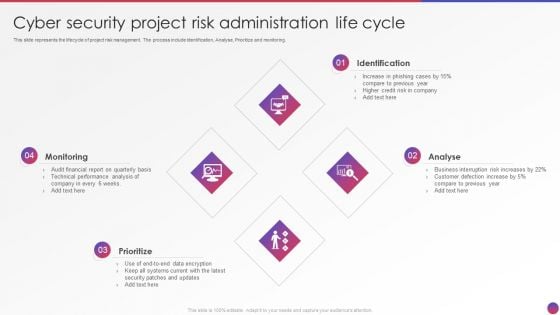
Cyber Security Project Risk Administration Life Cycle Summary PDF
This slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting Cyber Security Project Risk Administration Life Cycle Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitoring, Identification, Analyse, Prioritize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
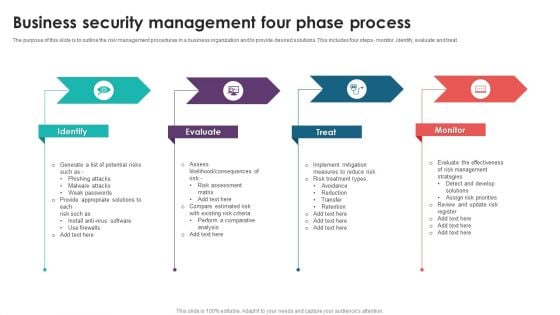
Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
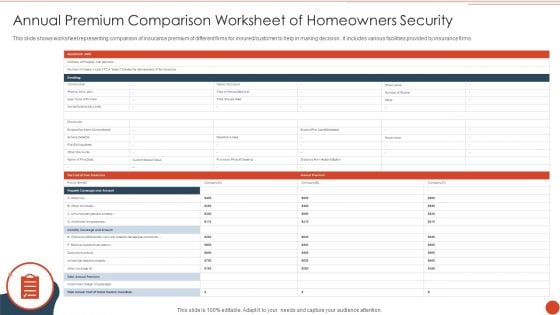
Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF
This slide shows worksheet representing comparison of insurance premium of different firms for insured or customer to help in making decision . it includes various facilities provided by insurance firms. Showcasing this set of slides titled Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF. The topics addressed in these templates are Purchase Price, Insurance, Medical Payments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
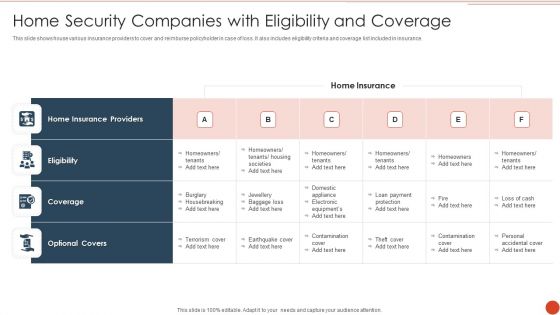
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

HR Security Training And Wellbeing KPI Dashboard Professional PDF
This slide showcases dashboard for HR safety training and wellbeing. This template aims to improve employee working efficiency and enhance working conditions to foster their working efficiency. It provides details regarding incidents reported, training programs implemented to reduce number of incidents, cost of providing training and level of employee satisfaction with training. Showcasing this set of slides titled HR Security Training And Wellbeing KPI Dashboard Professional PDF. The topics addressed in these templates are Severity, Injury Consequence, Employee Satisfaction Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
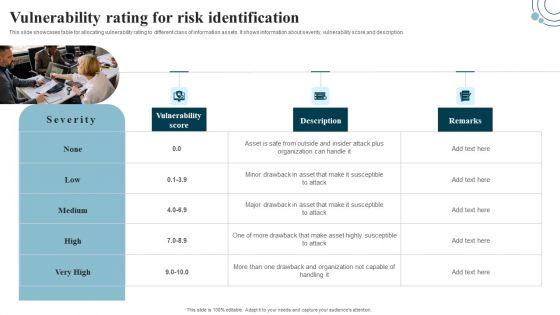
Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.
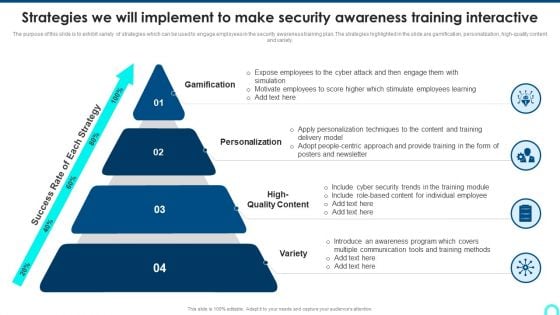
Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. This is a Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gamification, Personalization, High Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Program Challenges Ppt Styles Clipart PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Security Awareness Training Program Challenges Ppt Styles Clipart PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
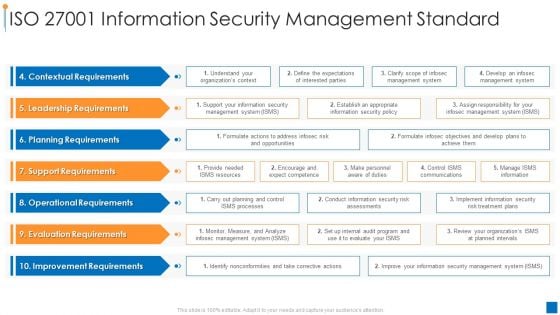
International Organization Standardization Iso 27001 Information Security Management Standard Elements PDF
Deliver an awe inspiring pitch with this creative international organization standardization why we need iso 27001 certification guidelines pdf bundle. Topics like contextual requirements, leadership requirements, planning requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
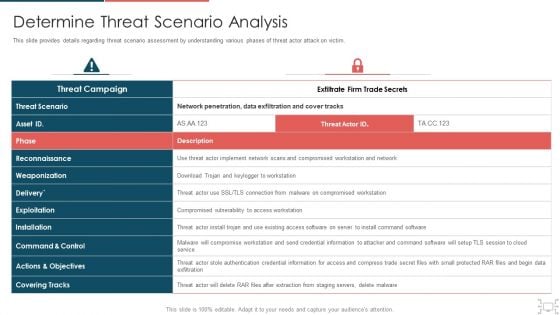
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
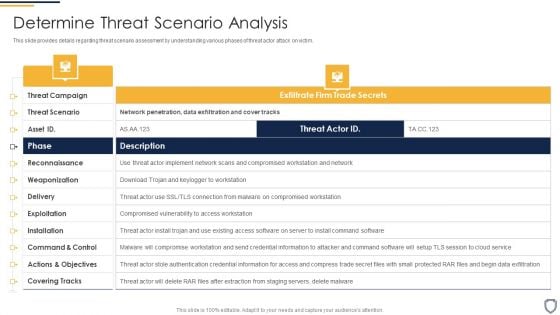
Corporate Security And Risk Management Determine Threat Scenario Analysis Formats PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative corporate security and risk management determine threat scenario analysis formats pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Illustration On Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Illustration On Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Communication PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Use our Services PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Download and present our Shapes PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit.Use these PowerPoint slides for presentations relating to lifebuoy on internet security, business, technology, shapes, services, communication. The prominent colors used in the PowerPoint template are Red, White, Yellow. Use our Illustration On Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. We assure you our shapes PowerPoint templates and PPT Slides are visually appealing. The feedback we get is that our Illustration On Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. Customers tell us our services PowerPoint templates and PPT Slides will make you look like a winner. The feedback we get is that our Illustration On Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. You can be sure our technology PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Our Illustration On Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113 are a great channel of communication. Your ideas will recieve excellent feedback.
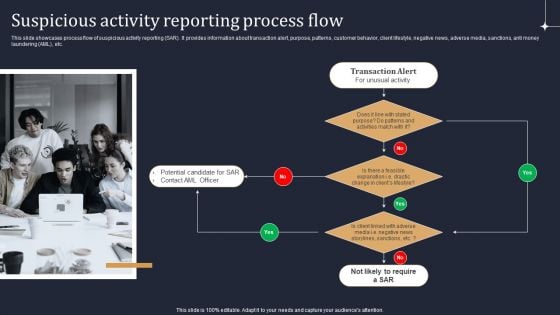
KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Pictograms To Specify Details Workplace Safety Protocol And Security Practices Download Pdf
This slide highlights the pictograms of chemical hazards which showcase health hazard, flame, exclamation mark, gas cylinder, exploding bomb, cross bones to alert the workers. This Pictograms To Specify Details Workplace Safety Protocol And Security Practices Download Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the pictograms of chemical hazards which showcase health hazard, flame, exclamation mark, gas cylinder, exploding bomb, cross bones to alert the workers.

Implementation Of Strong Password Policy IT Security IT Ppt Styles Topics PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Presenting implementation of strong password policy it security it ppt styles topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementation of strong password policy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Determine Staff Training Schedule For Skills Enhancement Infographics PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting developing firm security strategy plan determine staff training schedule for skills enhancement infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
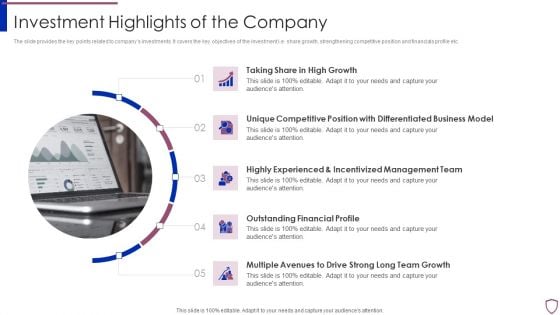
Financing Catalogue For Security Underwriting Agreement Investment Highlights Of The Company Sample PDF
The slide provides the key points related to companys investments. It covers the key objectives of the investment i.e. share growth, strengthening competitive position and financials profile etc. Presenting financing catalogue for security underwriting agreement investment highlights of the company sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like growth, business, management, financial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
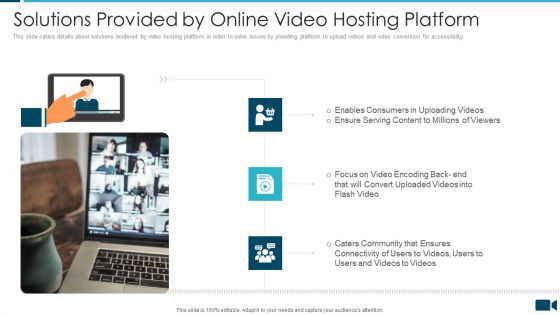
Secured Video Hosting Platform Investor Capital Funding Solutions Provided By Online Video Hosting Platform Introduction PDF
This slide caters details about solutions rendered by video hosting platform in order to solve issues by providing platform to upload videos and video conversion for accessibility. Presenting secured video hosting platform investor capital funding solutions provided by online video hosting platform introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like solutions provided by online video hosting platform. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
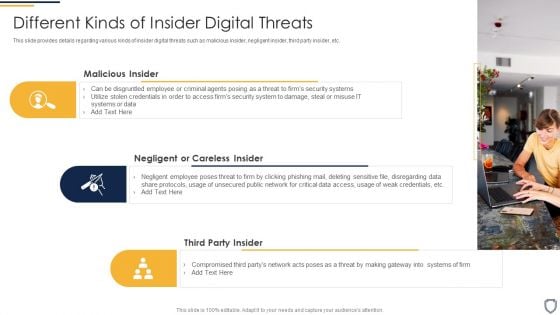
Corporate Security And Risk Management Different Kinds Of Insider Digital Threats Themes PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting corporate security and risk management different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Threat Management Action Plan Risk Portrait PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting corporate security and risk management threat management action plan risk portrait pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
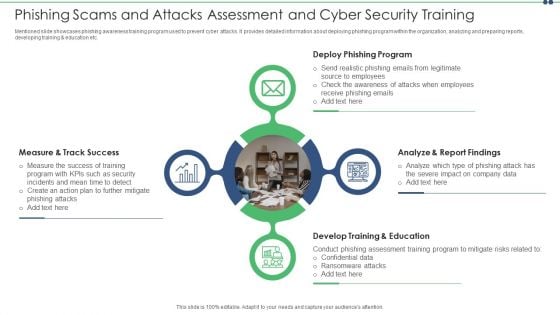
Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
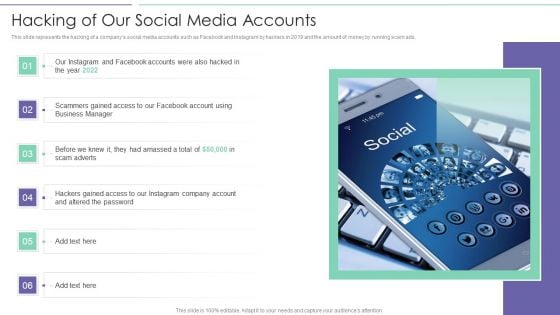
IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
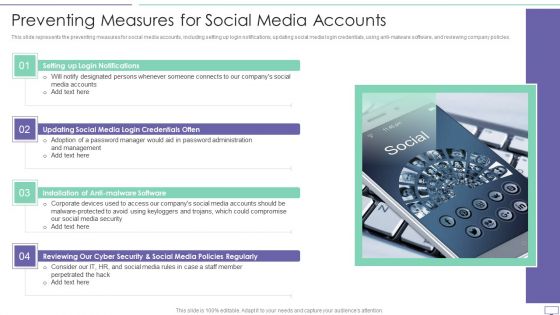
IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
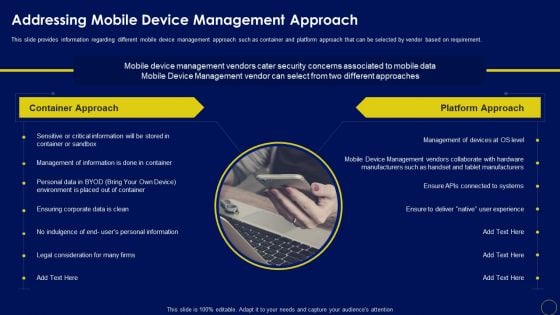
Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
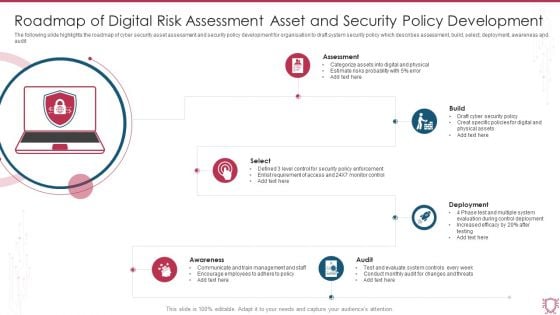
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Are you searching for a IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF from Slidegeeks today.
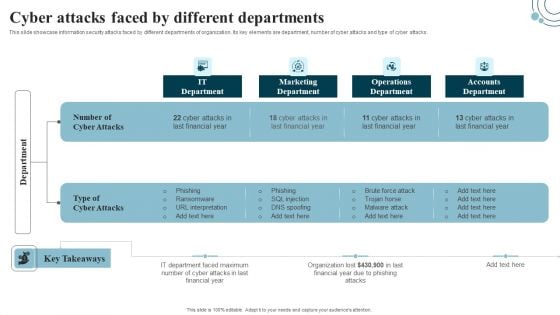
Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF from Slidegeeks today.
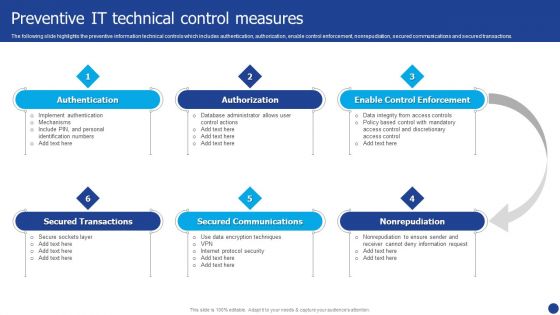
Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
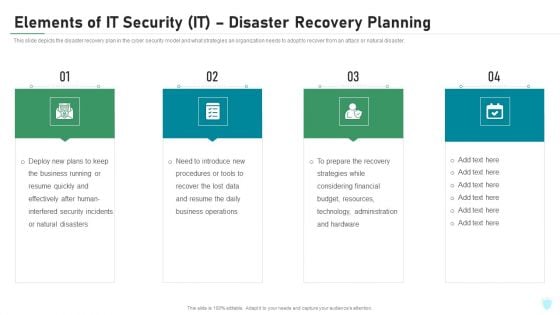
Elements Of IT Security IT Disaster Recovery Planning Ppt Styles Influencers PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting elements of it security it disaster recovery planning ppt styles influencers pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like effectively, business, technology, budget, resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
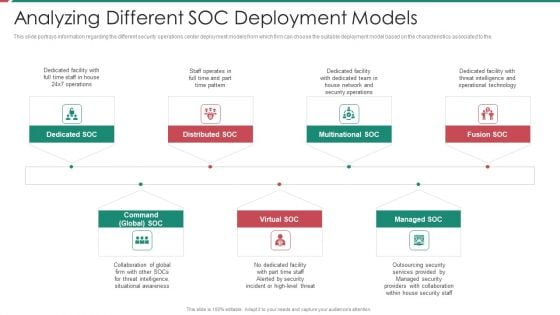
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
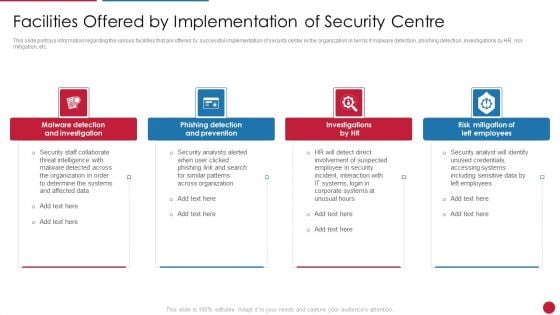
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
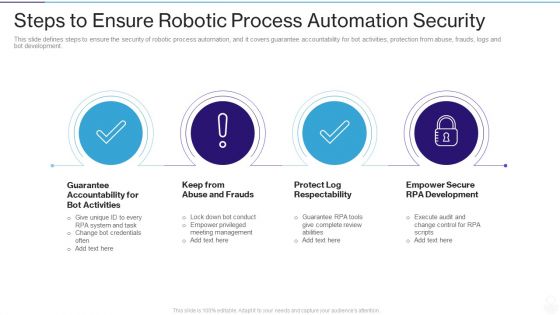
RPA IT Steps To Ensure Robotic Process Automation Security Ppt Layouts Layout Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a rpa it steps to ensure robotic process automation security ppt layouts layout ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like guarantee accountability for bot activities, keep from abuse and frauds, protect log respectability, empower secure rpa development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
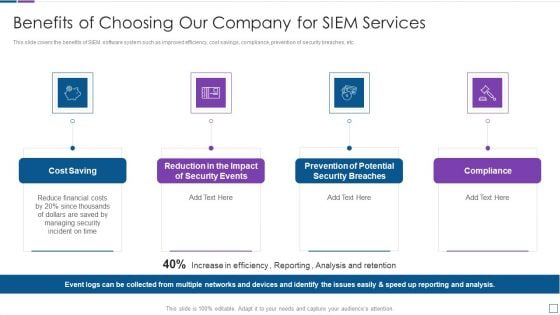
Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
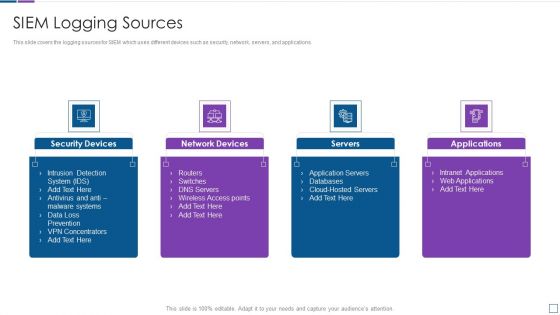
Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
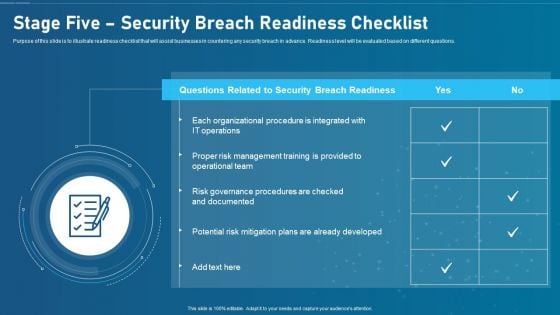
Artificial Intelligence Transformation Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a artificial intelligence transformation playbook stage five security breach readiness checklist topics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stage five security breach readiness checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incentive Scheme, Referral Partners, Sales Strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Company Journey From 2010 To 2022 Inspiration PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. This is a Security Camera System Company Profile Company Journey From 2010 To 2022 Inspiration PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond, Acquired Bluestone, Launched Integrated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Awards And Accolades Ppt PowerPoint Presentation Gallery Example PDF
This slide highlights the awards and allocates received by security company which includes best security company, community member award, great place to work and corporate excellence awards. This is a Security Officer Service Company Profile Awards And Accolades Ppt PowerPoint Presentation Gallery Example PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like SIA Awards, ASIS International, GPTW Institute, ICSI India. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
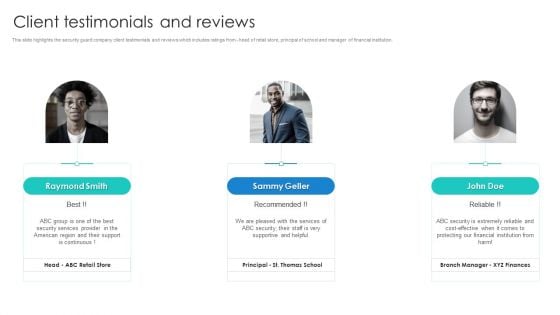
Manpower Corporate Security Business Profile Client Testimonials And Reviews Infographics PDF
This slide highlights the security guard company client testimonials and reviews which includes ratings from - head of retail store, principal of school and manager of financial institution. This is a Manpower Corporate Security Business Profile Client Testimonials And Reviews Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Financial Institution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
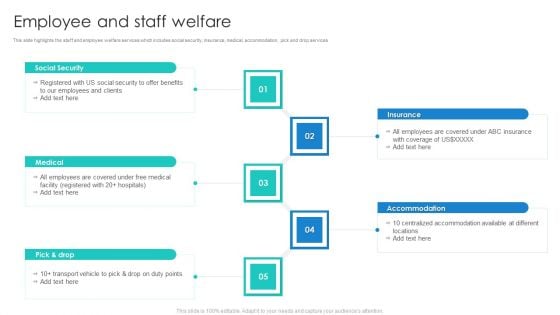
Manpower Corporate Security Business Profile Employee And Staff Welfare Designs PDF
This slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. This is a Manpower Corporate Security Business Profile Employee And Staff Welfare Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Medical, Social Security, Insurance, Accommodation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
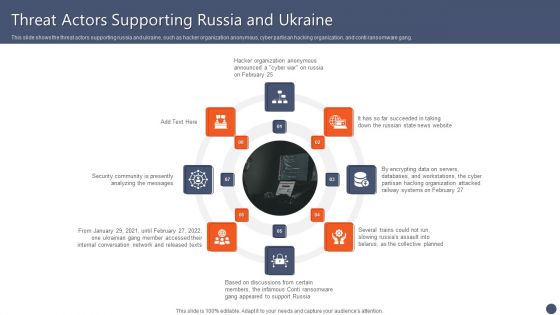
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
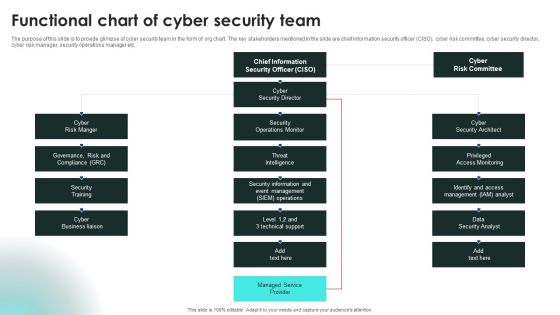
Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Multi Aspect Verification Secure Access Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this multi aspect verification secure access ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Composite Strategy Database Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this composite strategy database security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
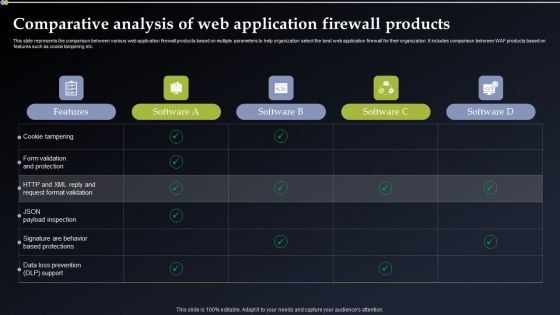
Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
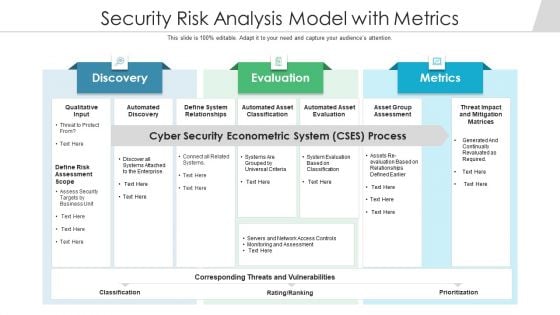
Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Businessman With Innovative Idea Vector Icon Ppt PowerPoint Presentation Ideas Outfit PDF
Presenting this set of slides with name bright bulb lock with key vector icon ppt powerpoint presentation infographic template brochure pdf. This is a three stage process. The stages in this process are businessman with innovative idea vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































