Data Privacy
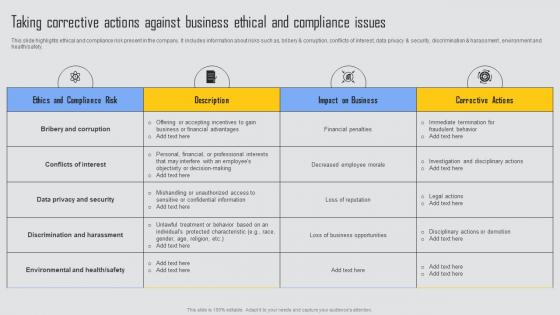
Taking Corrective Actions Managing Risks And Establishing Trust Through Efficient Background Pdf
This slide highlights ethical and compliance risk present in the company. It includes information about risks such as, bribery and corruption, conflicts of interest, data privacy and security, discrimination and harassment , environment and health safety. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Taking Corrective Actions Managing Risks And Establishing Trust Through Efficient Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Taking Corrective Actions Managing Risks And Establishing Trust Through Efficient Background Pdf today and make your presentation stand out from the rest This slide highlights ethical and compliance risk present in the company. It includes information about risks such as, bribery and corruption, conflicts of interest, data privacy and security, discrimination and harassment , environment and health safety.
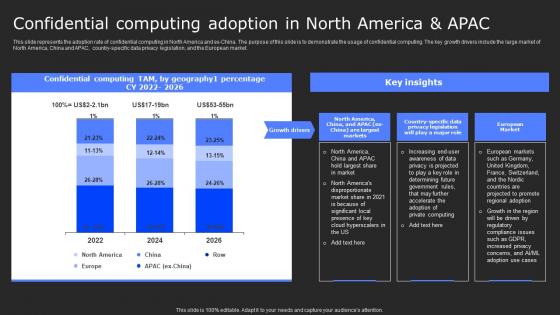
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
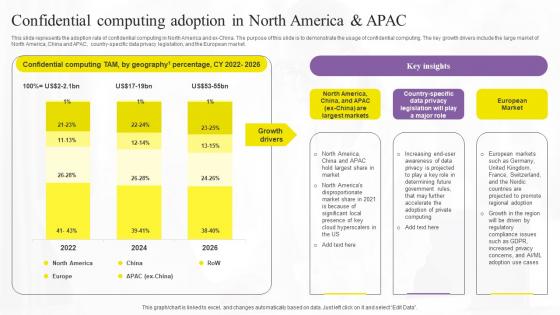
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
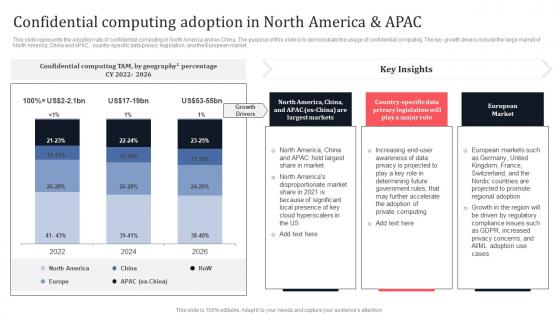
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.

CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model
This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Want to ace your presentation in front of a live audience Our CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc.
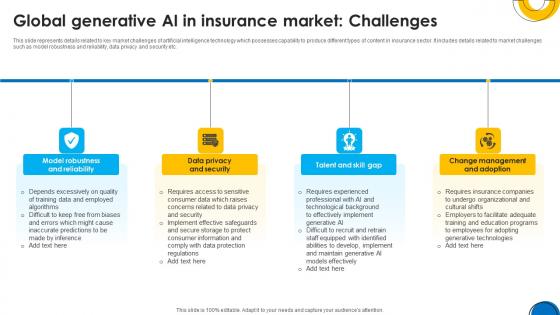
Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V
This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc.

Implementing ChatGpt In Insurance Key Limitations Of Using ChatGpt In Insurance ChatGpt SS V
This slide represents details related to limitations of using an artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to challenges of using ChatGPT in insurance such as data privacy and security, human expertise etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing ChatGpt In Insurance Key Limitations Of Using ChatGpt In Insurance ChatGpt SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents details related to limitations of using an artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to challenges of using ChatGPT in insurance such as data privacy and security, human expertise etc.
Confidential Computing Adoption In Confidential Computing Technologies Download Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In Confidential Computing Technologies Download Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In Confidential Computing Technologies Download Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
Action Measures To Build Staff HRM Software Assessment To Optimize Communication Elements Pdf
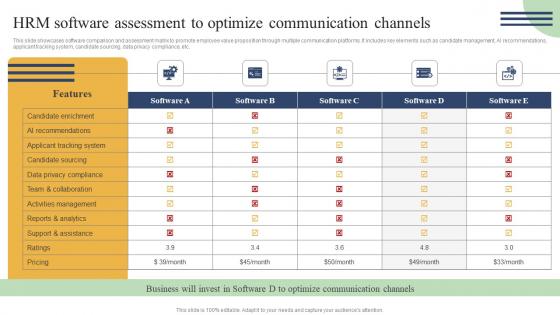
This slide showcases software comparison and assessment matrix to promote employee value proposition through multiple communication platforms. It includes key elements such as candidate management, AI recommendations, applicant tracking system, candidate sourcing, data privacy compliance, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Action Measures To Build Staff HRM Software Assessment To Optimize Communication Elements Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases software comparison and assessment matrix to promote employee value proposition through multiple communication platforms. It includes key elements such as candidate management, AI recommendations, applicant tracking system, candidate sourcing, data privacy compliance, etc.
Free Ad Supported Business Model Framework DT SS V
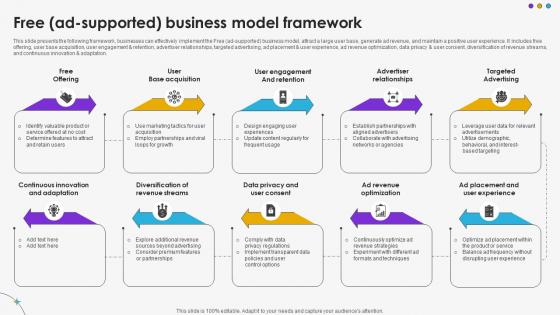
This slide presents the following framework, businesses can effectively implement the Free ad-supported business model, attract a large user base, generate ad revenue, and maintain a positive user experience. It includes free offering, user base acquisition, user engagement and retention, advertiser relationships, targeted advertising, ad placement and user experience, ad revenue optimization, data privacy and user consent, diversification of revenue streams, and continuous innovation and adaptation.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Free Ad Supported Business Model Framework DT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide presents the following framework, businesses can effectively implement the Free ad-supported business model, attract a large user base, generate ad revenue, and maintain a positive user experience. It includes free offering, user base acquisition, user engagement and retention, advertiser relationships, targeted advertising, ad placement and user experience, ad revenue optimization, data privacy and user consent, diversification of revenue streams, and continuous innovation and adaptation.
Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
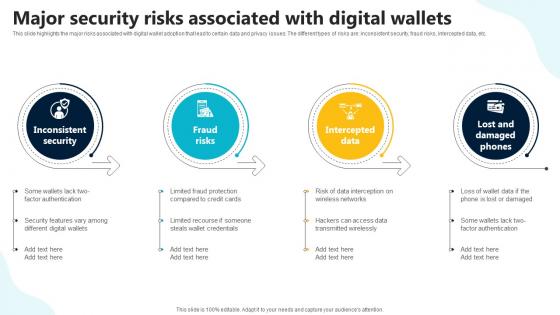
This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc. Boost your pitch with our creative Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc.

Ecommerce Industry Key Challenges With Solution Ppt Pictures Background PDF
This slide exhibit various hurdles faced by ecommerce companies along with their solutions to overcome them. It includes challenges such as cyber and data security, online identity verification, cross-border ecommerce, elements placement and data privacy. Pitch your topic with ease and precision using this Ecommerce Industry Key Challenges With Solution Ppt Pictures Background PDF. This layout presents information on Online Identity Verification, Cross Border Ecommerce, Elements Placement. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
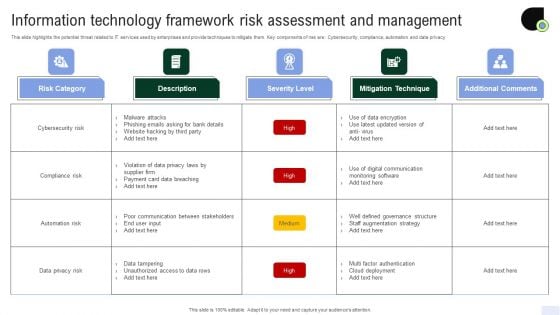
Information Technology Framework Risk Assessment And Management Diagrams PDF
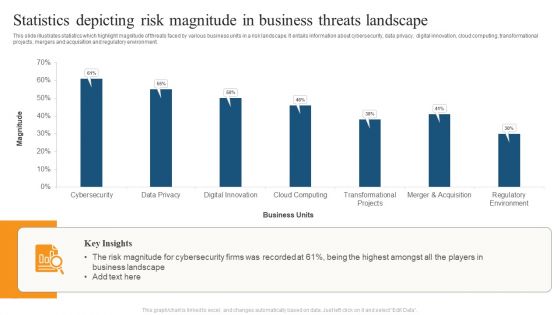
Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF
This slide illustrates statistics which highlight magnitude of threats faced by various business units in a risk landscape. It entails information about cybersecurity, data privacy, digital innovation, cloud computing, transformational projects, mergers and acquisition and regulatory environment. Pitch your topic with ease and precision using this Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF. This layout presents information on Business Units, Risk Magnitude, Business Landscape. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
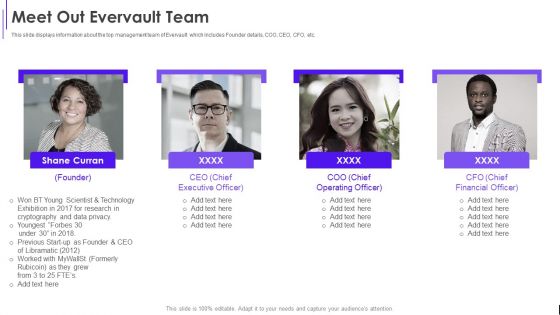
Fundraising Pitch Deck For Evervault Meet Out Evervault Team Ppt Pictures Templates PDF
This slide displays information about the top management team of Evervault which includes Founder details, COO, CEO, CFO, etc. This is a Fundraising Pitch Deck For Evervault Meet Out Evervault Team Ppt Pictures Templates PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Privacy, Technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Based Service Models Disadvantages Of Iaas Cloud Computing Layer Icons PDF
This slide depicts the disadvantages of the PaaS cloud Computing layer, including vendor lock-in, data privacy, and integration with the rest of the system applications.Presenting Cloud Based Service Models Disadvantages Of Iaas Cloud Computing Layer Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Increasing Complexity, Platform Transfer, Danger Of Compromised. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
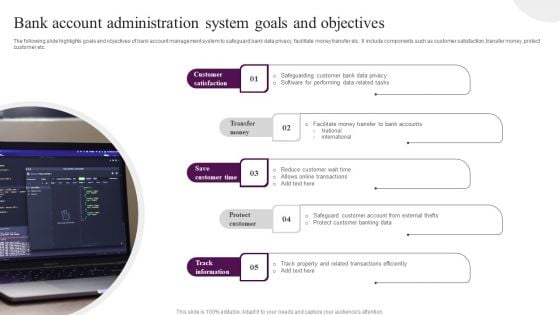
Bank Account Administration System Goals And Objectives Brochure PDF
The following slide highlights goals and objectives of bank account management system to safeguard bank data privacy, facilitate money transfer etc. It include components such as customer satisfaction, transfer money, protect customer etc. Presenting Bank Account Administration System Goals And Objectives Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Customer Satisfaction, Transfer Money, Save Customer Time . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
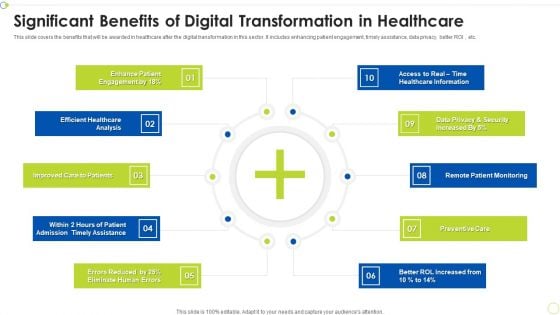
Significant Benefits Of Digital Transformation In Healthcare Ppt PowerPoint Presentation File Sample PDF
This slide covers the benefits that will be awarded in healthcare after the digital transformation in this sector. It includes enhancing patient engagement, timely assistance, data privacy, better ROI, etc. Presenting Significant Benefits Of Digital Transformation In Healthcare Ppt PowerPoint Presentation File Sample PDF to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including Efficient Healthcare, Preventive Care, Assistance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
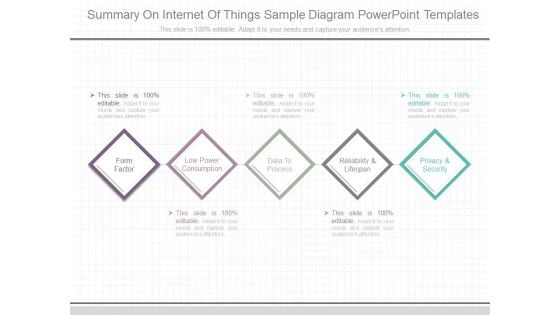
Summary On Internet Of Things Sample Diagram Powerpoint Templates
This is a summary on internet of things sample diagram powerpoint templates. This is a five stage process. The stages in this process are form factor, low power consumption, data to process, reliability and lifespan, privacy and security.
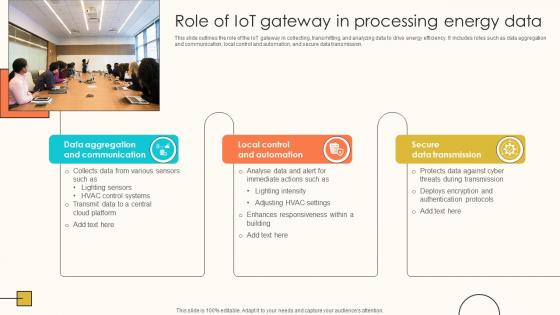
Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V
This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission. Do you know about Slidesgeeks Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission.
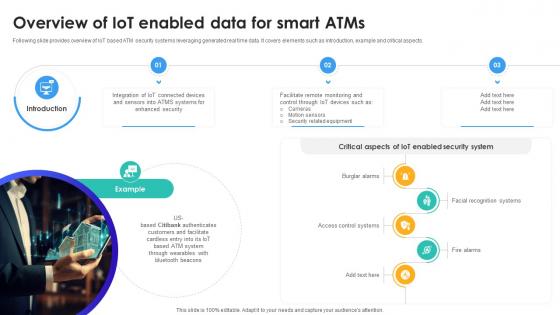
Overview Of IoT Enabled Data For Smart Atms IoT In Banking For Digital Future IoT SS V
Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects. Retrieve professionally designed Overview Of IoT Enabled Data For Smart Atms IoT In Banking For Digital Future IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects.
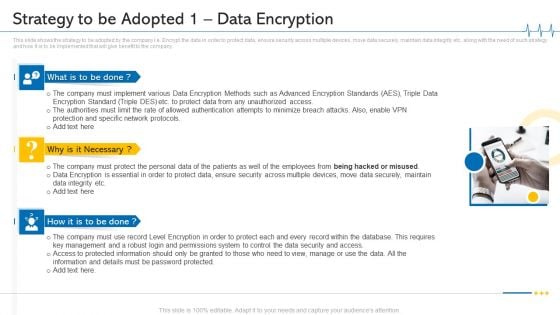
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
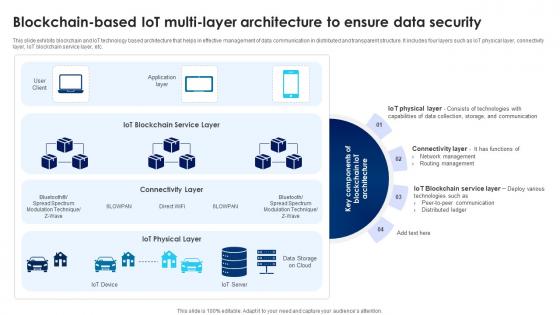
Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V
This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc. Get a simple yet stunning designed Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc.
Public And Private Cloud Network For Securing Data Stored From Various Source Icon Ppt PowerPoint Presentation Icon Backgrounds PDF
Presenting public and private cloud network for securing data stored from various source icon ppt powerpoint presentation icon backgrounds pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including public and private cloud network for securing data stored from various source icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Contd Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver an awe inspiring pitch with this creative major techniques for project safety it information security process to manage firms sensitive data contd summary pdf bundle. Topics like firewall audit checklist, vpn configuration, penetrating testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
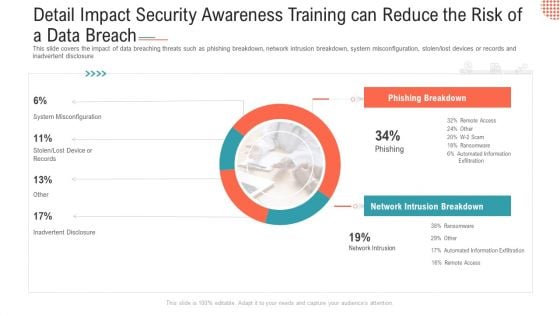
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
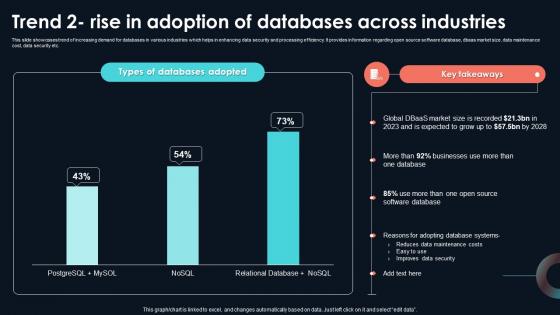
Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc. This Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Data Diagrams PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing data diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
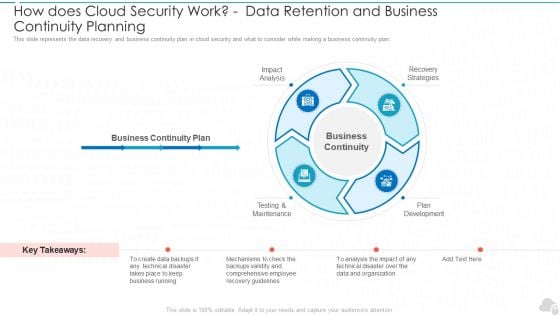
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
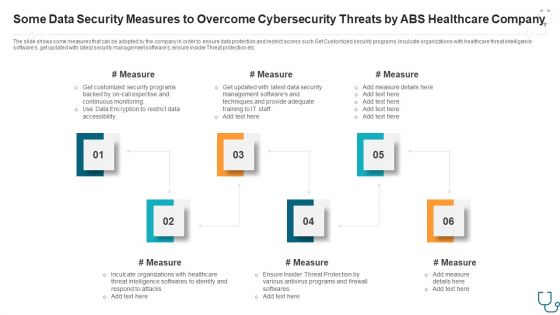
Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
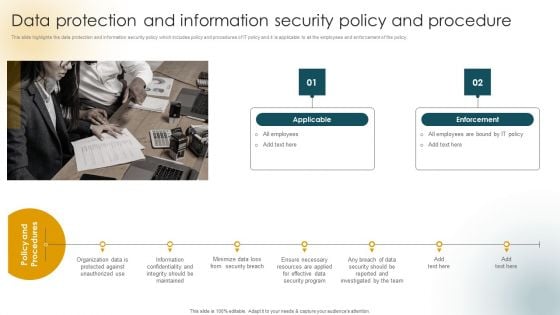
Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
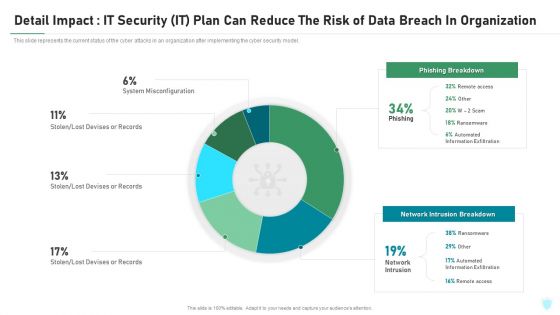
Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
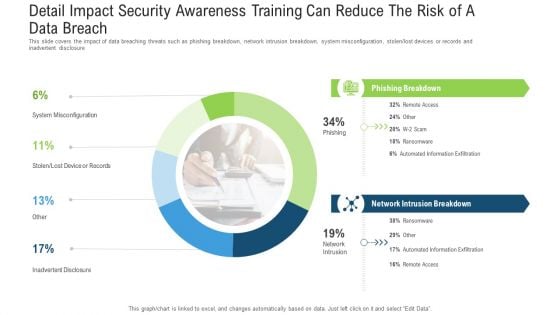
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
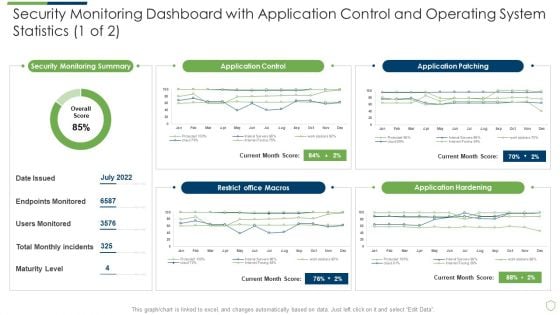
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
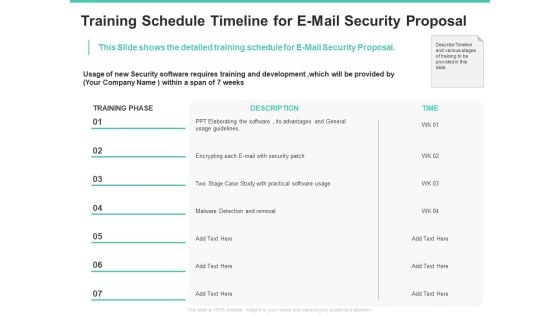
Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
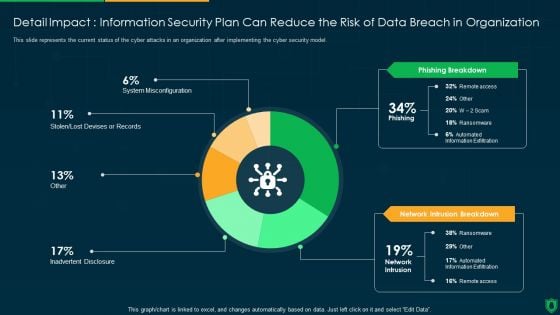
Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Poste It Notes Clipart PDF
This is a Executing security management program to mitigate threats and safeguard confidential organizational data poste it notes clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poste it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
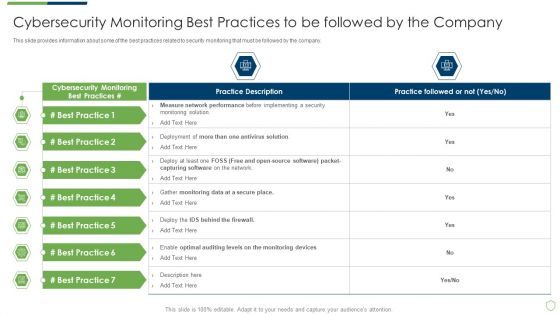
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data 30 60 90 Days Plan Brochure PDF
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data 30 60 90 days plan brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
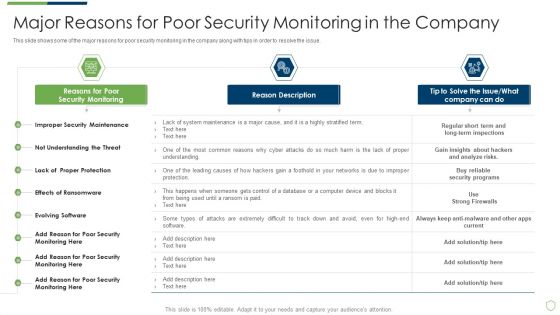
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
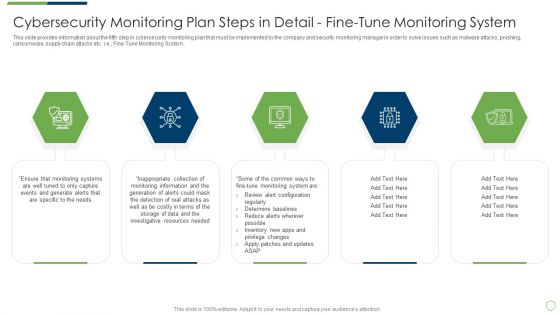
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
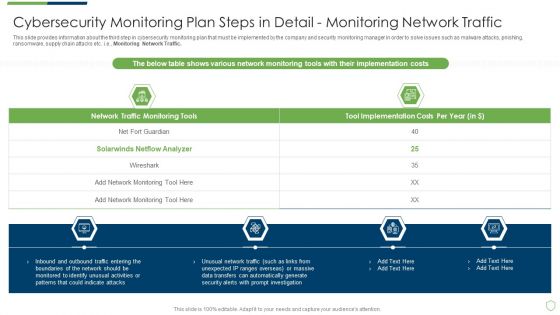
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
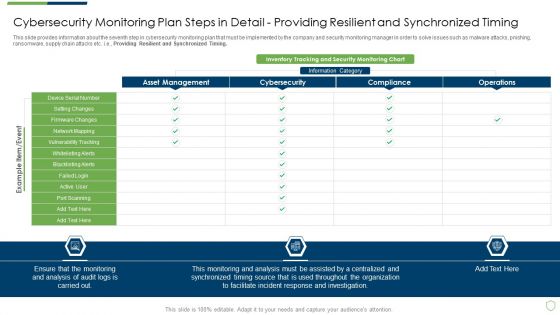
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
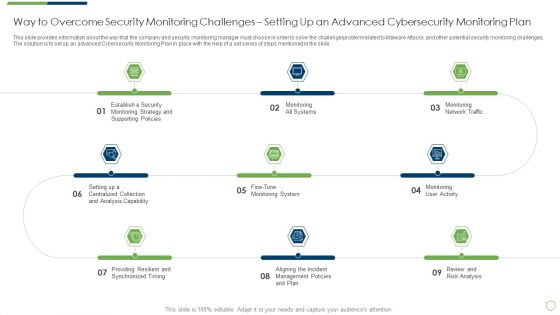
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
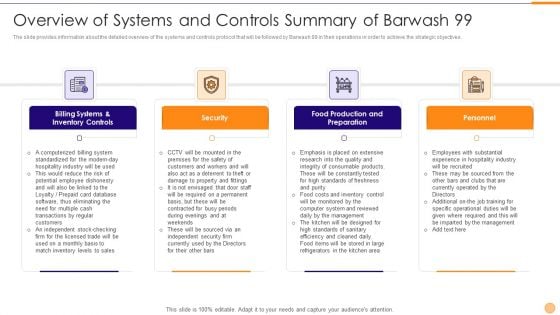
Classified Data Memo Record With Strategic Goals Overview Of Systems And Controls Summary Of Barwash 99 Rules PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting classified data memo record with strategic goals overview of systems and controls summary of barwash 99 rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems and inventory controls, security, food production and preparation, personnel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
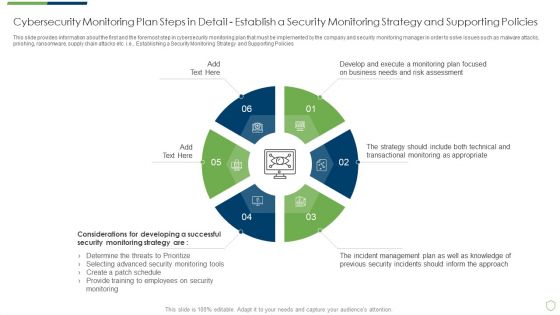
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
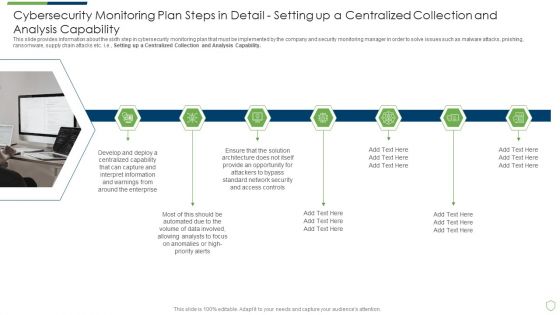
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This modern security observation plan to eradicate cybersecurity risk and data breach ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Ppt PowerPoint Presentation Complete Deck
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Marketing Information Management System To Improve Sales Background PDF
This slide covers marketing information management system to enhance sales and customer service. It involves key features such as well organized marketing information, better customer understanding and data privacy and regulations. This Marketing Information Management System To Improve Sales Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Marketing Information Management System To Improve Sales Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Implementing Ecommerce Marketing Services Plan Email Marketing Trends For Business Growth Information PDF
This slide focuses on the email marketing trends for business growth such as personalization, artificial intelligence, interactivity, data privacy and adding videos. Get a simple yet stunning designed Implementing Ecommerce Marketing Services Plan Email Marketing Trends For Business Growth Information PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Ecommerce Marketing Services Plan Email Marketing Trends For Business Growth Information PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.


 Continue with Email
Continue with Email

 Home
Home


































