Data Privacy
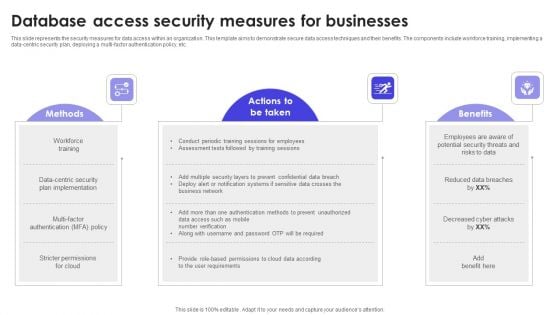
Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
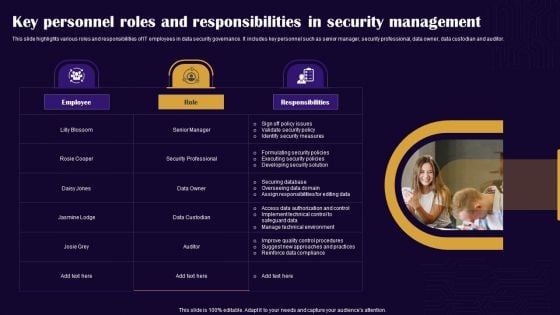
Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
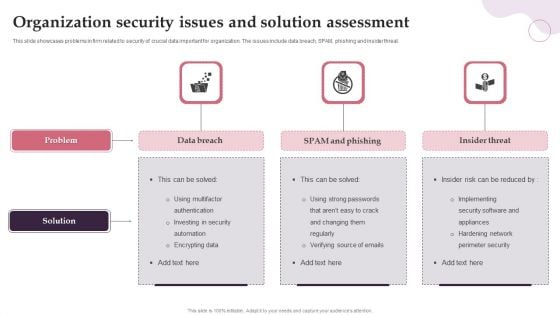
Organization Security Issues And Solution Assessment Ideas PDF
This slide showcases problems in firm related to security of crucial data important for organization. The issues include data breach, SPAM, phishing and insider threat. Persuade your audience using this Organization Security Issues And Solution Assessment Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breach, SPAM And Phishing, Insider Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SIEM Services Security Information And Event Management Services Ppt Ideas Design Ideas PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. This is a siem services security information and event management services ppt ideas design ideas pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data correlation, data aggregation, security alert, dashboards. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
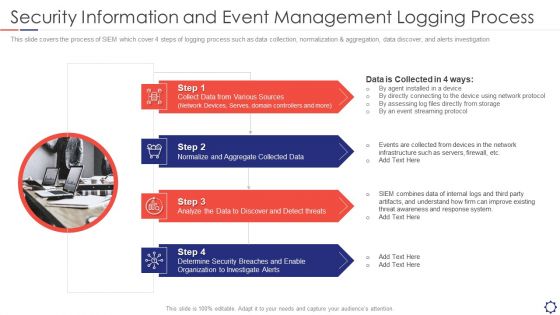
SIEM Security Information And Event Management Logging Process Ppt Slides Graphics Template PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. Presenting siem security information and event management logging process ppt slides graphics template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sources, Collected Data, Analyze threats, Security Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
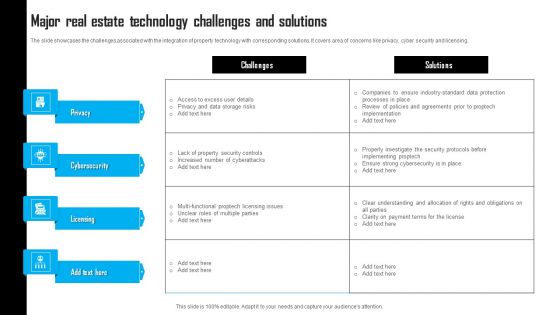
Major Real Estate Technology Challenges And Solutions Template PDF
The slide showcases the challenges associated with the integration of property technology with corresponding solutions. It covers area of concerns like privacy, cyber security and licensing. Pitch your topic with ease and precision using this Major Real Estate Technology Challenges And Solutions Template PDF. This layout presents information on Data Storage Risks, Property Security Controls, Payment Terms. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
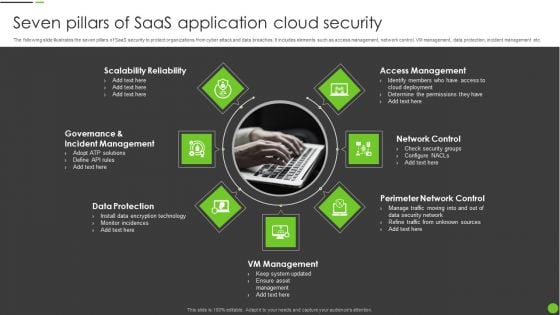
Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Stock Photo Blue Cloud With Code Lock PowerPoint Slide
Graphic of blue cloud and code lock has been used to design this PPT. This PPT contains the concept data safety on cloud technology. Use this image template for your cloud technology related presentation.
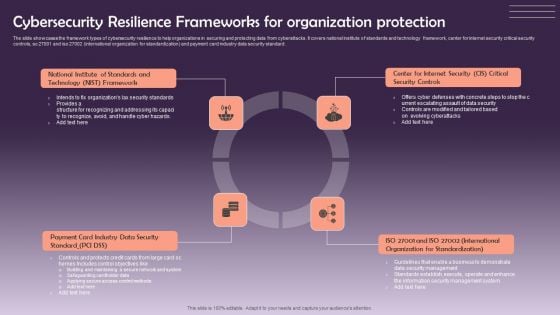
Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Intelligence Framework For Application Consumption Determining The Suitable Software For Organization Icons PDF
The slide provides the key features comparison of various software that will help the company to achieve its objective of process automation and data security. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption determining the suitable software for organization icons pdf. Use them to share invaluable insights on process automation, data security, improve productivity, process automation and data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Blockchain Technology Framework IT Pros And Cons Of Private Blockchain Brochure PDF
This slide represents the use case of blockchain in the government sector how it would benefit voting, data security, budgeting and corruption. This is a blockchain technology framework it blockchain technology in government sector designs pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital paperwork systems, interagency data control, fighting corruption, data security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Iot Digital Twin Technology Post Covid Expenditure Management Consideration Points Prior Implementing Digital Twins Rules PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. Presenting iot digital twin technology post covid expenditure management consideration points prior implementing digital twins rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, protocols, data, training, managing, quality . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
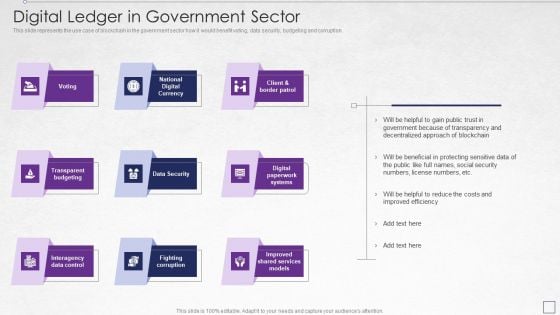
Digitized Record Book Technology Digital Ledger In Government Sector Designs PDF
This slide represents the use case of blockchain in the government sector how it would benefit voting, data security, budgeting and corruption. Presenting digitized record book technology digital ledger in government sector designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security, transparent budgeting, interagency data control, fighting corruption, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
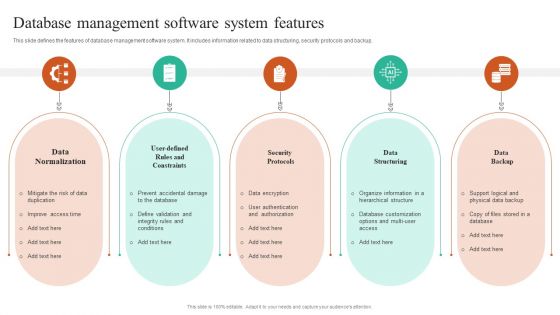
Database Management Software System Features Topics PDF
This slide defines the features of database management software system. It includes information related to data structuring, security protocols and backup. Persuade your audience using this Database Management Software System Features Topics PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Normalization, Security Protocols, Data Structuring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
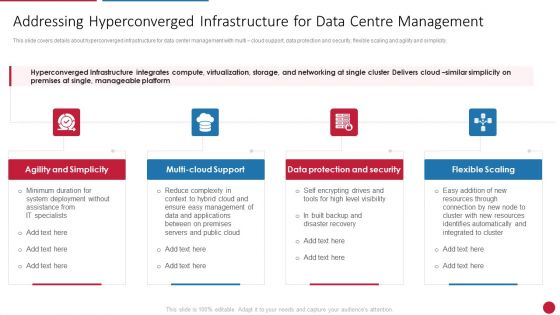
Facilitating IT Intelligence Architecture Addressing Hyperconverged Infrastructure Download PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Presenting Facilitating IT Intelligence Architecture Addressing Hyperconverged Infrastructure Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Agility And Simplicity, Multi Cloud Support, Data Protection And Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
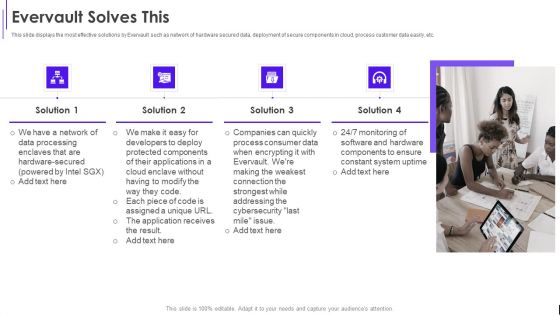
Fundraising Pitch Deck For Evervault Evervault Solves This Ppt Gallery Grid PDF
This slide displays the most effective solutions by Evervault such as network of hardware secured data, deployment of secure components in cloud, process customer data easily, etc. Presenting Fundraising Pitch Deck For Evervault Evervault Solves This Ppt Gallery Grid PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Processing, Protected Components, Monitoring Software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
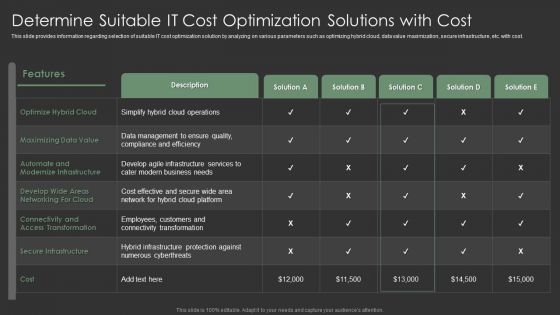
IT Spend Management Priorities By Cios Determine Suitable IT Cost Optimization Solutions With Cost Designs PDF
This slide provides information regarding selection of suitable IT cost optimization solution by analyzing on various parameters such as optimizing hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver an awe inspiring pitch with this creative IT Spend Management Priorities By Cios Determine Suitable IT Cost Optimization Solutions With Cost Designs PDF bundle. Topics like Secure Infrastructure, Maximizing Data Value, Data Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Strategy Basic IT Professional Skills Required For Digital Transformation Professional PDF
This slide shows the major skills that are possessed by an IT professional such as Machine Learning, Data Analysis, DevOps, Mobility Management, Digital Marketing, Data and Digital Security, Digital Literacy etc. This is a information technology strategy basic it professional skills required for digital transformation professional pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data analysis, machine learning, devops, mobility management, digital marketing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Transformation Organization Possible Barriers And Solution Pictures PDF
Mentioned slide describes various possible challenges that may be faced by the company while going for technology transformation. It includes barrier such as digitalization driven culture change and data management. It also shows the impact of each barrier on business and solution to overcome them. Presenting information technology transformation organization possible barriers and solution pictures pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like data management, data security, employee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
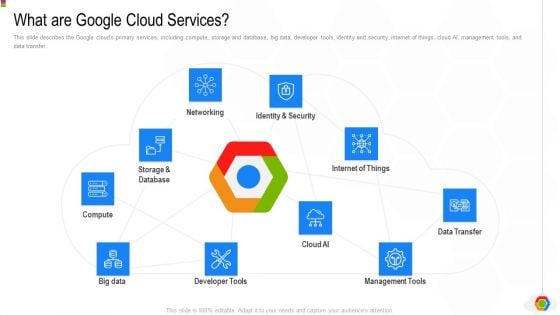
Google Cloud Console IT What Are Google Cloud Services Ppt Outline Deck PDF
This slide describes the Google clouds primary services, including compute, storage and database, big data, developer tools, identity and security, internet of things, cloud AI, management tools, and data transfer. This is a google cloud console it what are google cloud services ppt outline deck pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compute, developer tools, management tools, data transfer, networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Google Cloud Computing System What Are Google Cloud Services Designs PDF
This slide describes the google clouds primary services, including compute, storage and database, big data, developer tools, identity and security, internet of things, cloud AI, management tools, and data transfer. This is a Google Cloud Computing System What Are Google Cloud Services Designs PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking, Management Tools, Data Transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CIO Role In Digital Evolution Basic IT Professional Skills Required For Digital Transformation Microsoft PDF
This slide shows the major skills that are possessed by an IT professional such as Machine Learning, Data Analysis, DevOps, Mobility Management, Digital Marketing, Data and Digital Security, Digital Literacy etc. Presenting CIO Role In Digital Evolution Basic IT Professional Skills Required For Digital Transformation Microsoft PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Digital Literacy, Data Analysis, Machine Learning. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
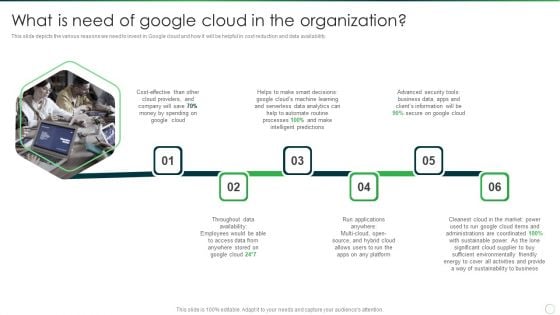
Google Cloud Computing System What Is Need Of Google Cloud In The Organization Guidelines PDF
This slide depicts the various reasons we need to invest in Google cloud and how it will be helpful in cost reduction and data availability. Presenting Google Cloud Computing System What Is Need Of Google Cloud In The Organization Guidelines PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Serverless Data Analytics, Business Data, Advanced Security Tools. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
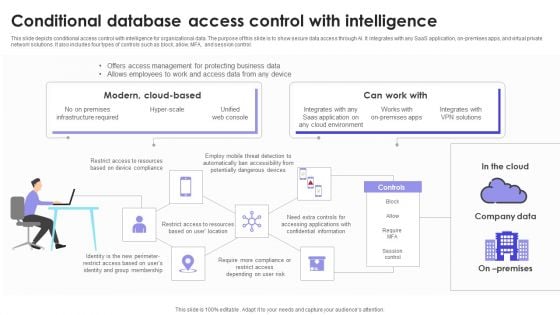
Conditional Database Access Control With Intelligence Download PDF
This slide depicts conditional access control with intelligence for organizational data. The purpose of this slide is to show secure data access through AI. It integrates with any SaaS application, on-premises apps, and virtual private network solutions. It also includes four types of controls such as block, allow, MFA, and session control. Pitch your topic with ease and precision using this Conditional Database Access Control With Intelligence Download PDF. This layout presents information on Company Data, Modern, Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Role Of Technical Competence In Organizational Basic It Professional Skills Pictures PDF
This slide shows the major skills that are possessed by an IT professional such as Machine Learning, Data Analysis, DevOps, Mobility Management, Digital Marketing, Data and Digital Security, Digital Literacy etc.Deliver and pitch your topic in the best possible manner with this Role Of Technical Competence In Organizational Basic It Professional Skills Pictures PDF Use them to share invaluable insights on Digital Literacy, Machine Learning, Data Analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
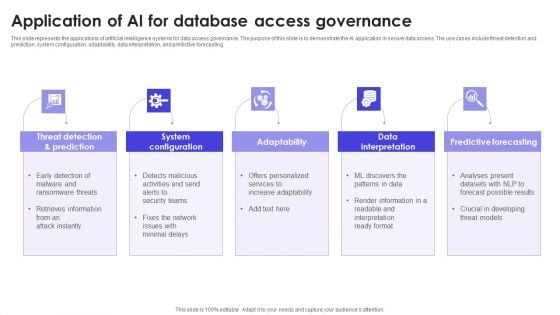
Application Of AI For Database Access Governance Summary PDF
This slide represents the applications of artificial intelligence systems for data access governance. The purpose of this slide is to demonstrate the AI application in secure data access. The use cases include threat detection and prediction, system configuration, adaptability, data interpretation, and predictive forecasting. Presenting Application Of AI For Database Access Governance Summary PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prediction, System Configuration, Adaptability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Role IT Team Digital Transformation Basic It Professional Skills Required For Digital Transformation Template PDF
This slide shows the major skills that are possessed by an IT professional such as Machine Learning, Data Analysis, DevOps, Mobility Management, Digital Marketing, Data and Digital Security, Digital Presenting role it team digital transformation basic it professional skills required for digital transformation template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like digital literacy, data analysis, machine learning. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Stream Processing Challenges And Solutions To Overcome Themes PDF
The following slide outlines various data ingestion challenges faced by the company. The key challenges are manual data ingestion process, high budget, and security issue. It also covers information about multiple solutions which can be used to overcome the challenges. Presenting Major Stream Processing Challenges And Solutions To Overcome Themes PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Challenges, Solutions, Manual Data, Ingestion Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
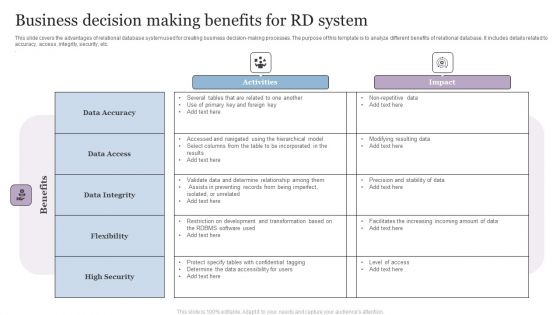
Business Decision Making Benefits For RD System Background PDF
This slide covers the advantages of relational database system used for creating business decision-making processes. The purpose of this template is to analyze different benefits of relational database. It includes details related to accuracy, access, integrity, security, etc.Showcasing this set of slides titled Business Decision Making Benefits For RD System Background PDF. The topics addressed in these templates are Data Accuracy, Data Access, Data Integrity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
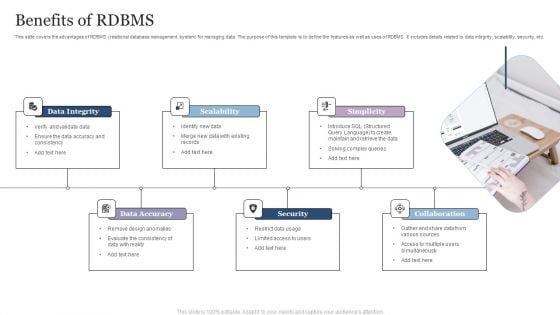
Benefits Of RDBMS Summary PDF
This slide covers the advantages of RDBMS relational database management system for managing data. The purpose of this template is to define the features as well as uses of RDBMS. It includes details related to data integrity, scalability, security, etc.Persuade your audience using this v. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integrity, Scalability, Simplicity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
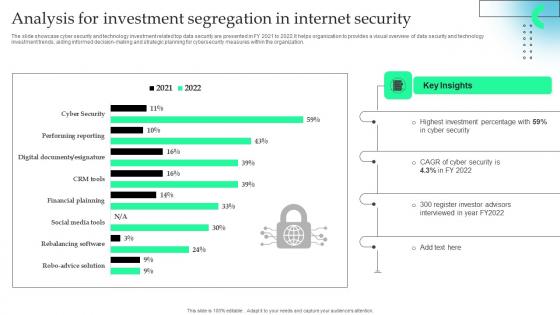
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
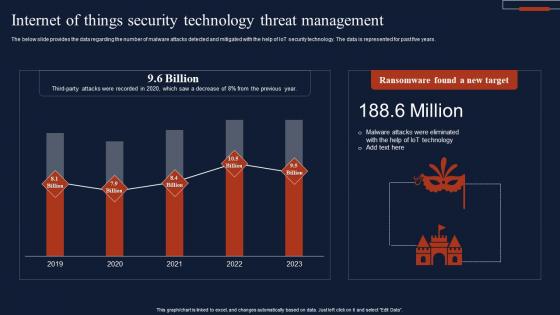
Internet Of Things Security Technology Threat Management Summary Pdf
The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Pitch your topic with ease and precision using this Internet Of Things Security Technology Threat Management Summary Pdf This layout presents information on Ransomware Found, New Target, Threat Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years.
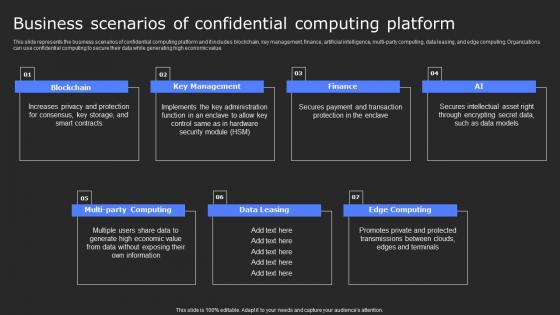
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
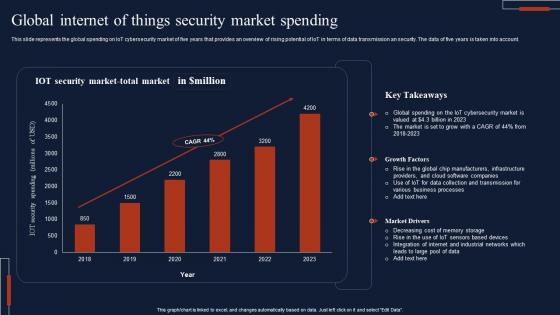
Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account.
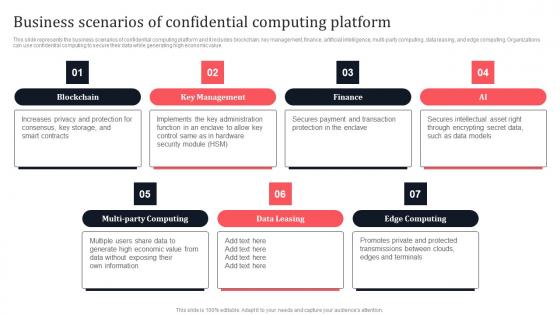
Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Boost your pitch with our creative Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
Cloud Computing Wifi Safety Upload Social Network Ppt Slides Graphics
This power point icon template has been designed with graphic of cloud computing, wifi and social network. These icons can be used for data upload safety features and social networking. Use these icons for social network and technology related presentations.
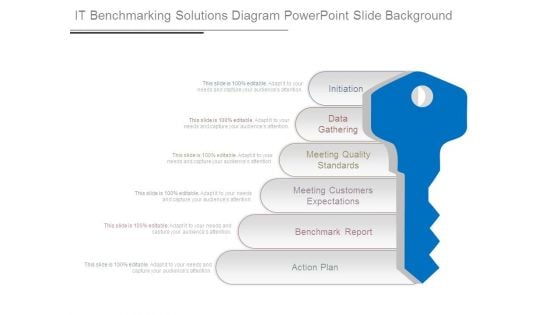
It Benchmarking Solutions Diagram Powerpoint Slide Background
This is a it benchmarking solutions diagram powerpoint slide background. This is a six stage process. The stages in this process are initiation, data gathering, meeting quality standards, meeting customers expectations, benchmark report, action plan.

Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with cyber security network data monitor as abstract Factor it all in with our Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511. They account for every element.

Security Methodology Diagram Powerpoint Topics
This is a security methodology diagram powerpoint topics. This is a six stage process. The stages in this process are device protection, data separation, security operation, security organization, leak protection, sharing protection.

Digital Archive Mouse PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with digital archived data symbol for databases Get the nod for your plans with our Digital Archive Mouse PowerPoint Templates And PowerPoint Backgrounds 0311. You will be at the top of your game.

Digital Files Security PowerPoint Template 1110
3d illustration of transparent binary and html data revolving around an open file folder Examine every deatail with our Digital Files Security PowerPoint Template 1110. Put each element to the test.
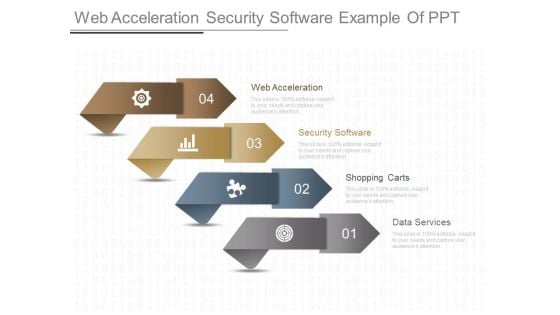
Web Acceleration Security Software Example Of Ppt
This is a web acceleration security software example of ppt. This is a four stage process. The stages in this process are web acceleration, security software, shopping carts, data services.
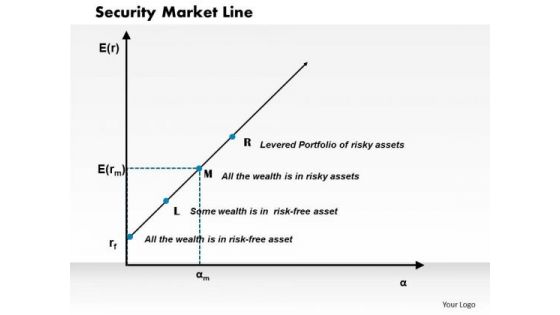
Business Framework Security Market Line PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.
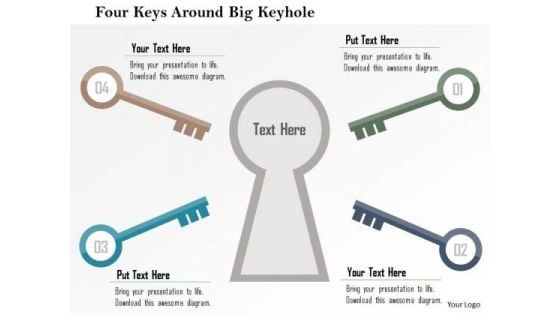
Business Diagram Four Keys Around Big Keyhole Presentation Template
Our above slide contains graphics of keys around big keyhole. It helps to exhibit finding possible solutions. Use this diagram to impart more clarity to data and to create more sound impact on viewers.
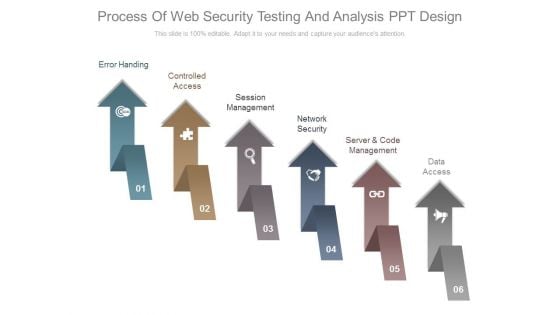
Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.

Cloud Computing Project Analysis Diagram Powerpoint Template
Our above PPT slide contains graphics of cloud with technology icons. This PowerPoint template may be used for project related to cloud computing. Use this diagram to impart more clarity to data and to create more sound impact on viewers.

Unified Security Management Ppt Template Example Of Ppt Presentation
This is a unified security management ppt template example of ppt presentation. This is a four stage process. The stages in this process are assess the network, find threats, data loss prevention, gateway anti virus.
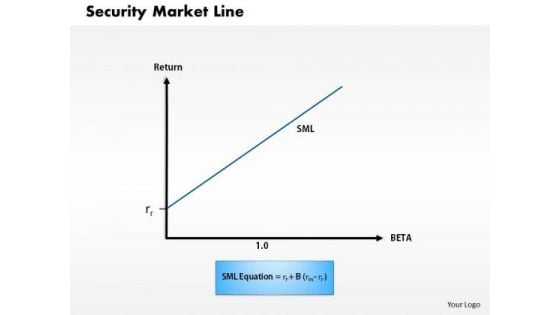
Business Framework Security Market Line 1 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.
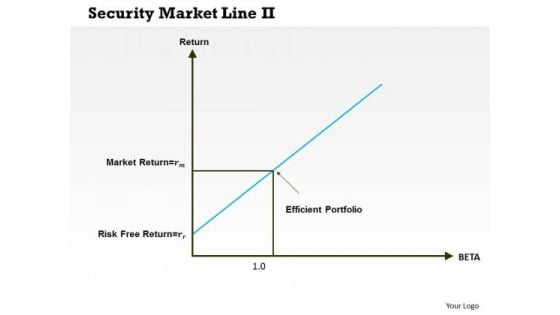
Business Framework Security Market Line 11 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.
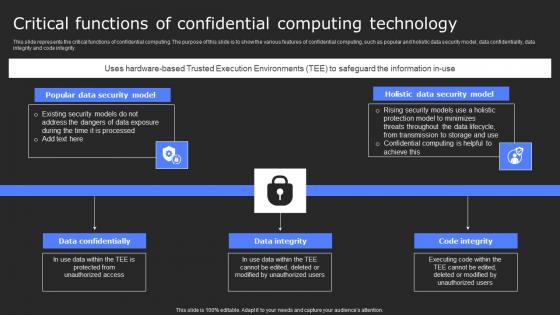
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.

Cloud Security Assessment Why Cloud Security Is Important Pictures PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Why Cloud Security Is Important Pictures PDF bundle. Topics like Centralized Security, Cost Effective, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
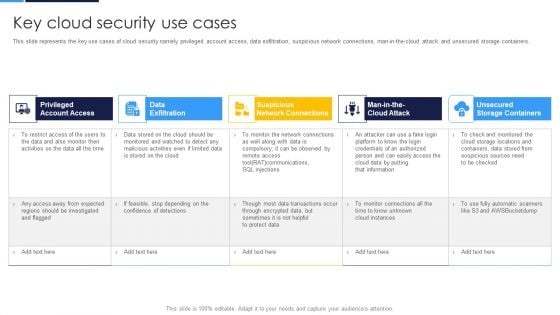
Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF Use them to share invaluable insights on Account Access, Data Exfiltration, Network Connections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc.
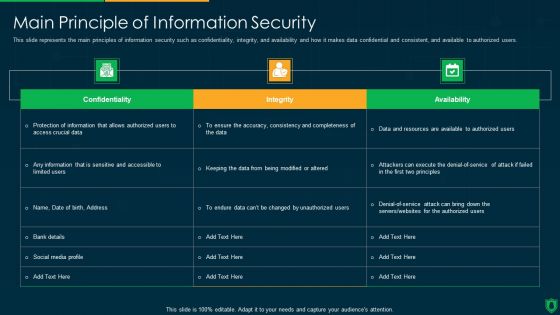
Info Security Main Principle Of Information Security Ppt PowerPoint Presentation File Background Designs PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative info security main principle of information security ppt powerpoint presentation file background designs pdf bundle. Topics like integrity, confidentiality, availability, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
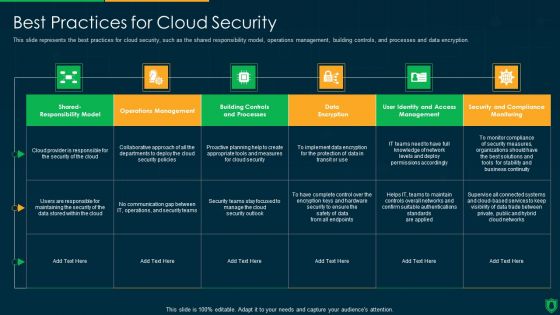
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
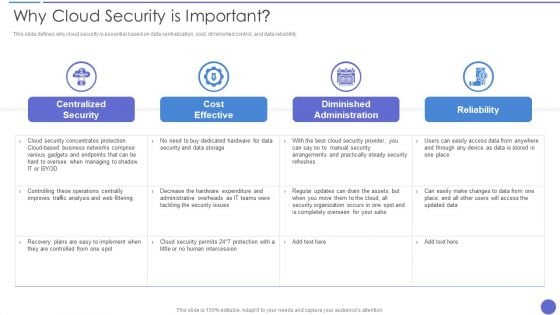
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
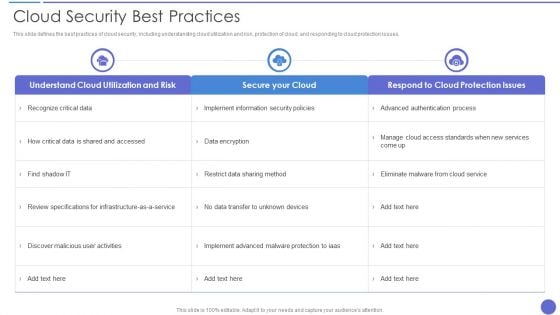
Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Architecture Of Cloud Security Ppt Outline Graphics Design PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Cloud Information Security Architecture Of Cloud Security Ppt Outline Graphics Design PDF bundle. Topics like Providers Responsibility, Application Security, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
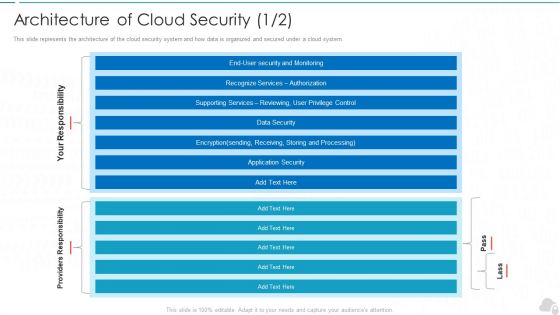
Architecture Of Cloud Security Authorization Cloud Computing Security IT Ppt Model Sample PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative architecture of cloud security authorization cloud computing security it ppt model sample pdf bundle. Topics like monitoring, security, authorization, services, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































