Data Privacy

Airtable Capital Funding Pitch Deck Our Solution Microsoft PDF
This slide covers key solutions offered by cloud based software company. It involves solutions such as transform workflows with AI, build on flexible data model and offers data security and compliance. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Airtable Capital Funding Pitch Deck Our Solution Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
CASB 2 0 IT Cloud Access Security Broker Use Cases
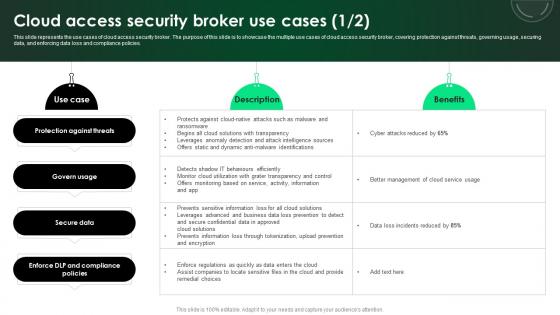
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies.
The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
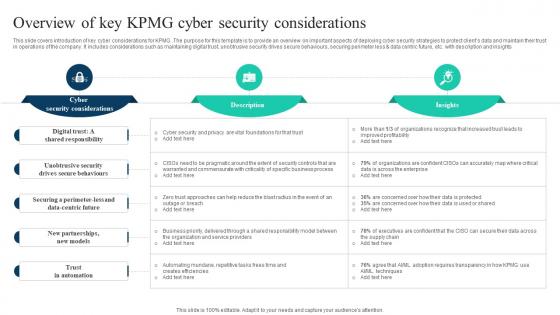
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
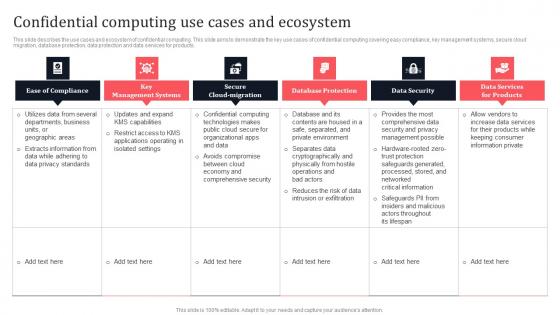
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
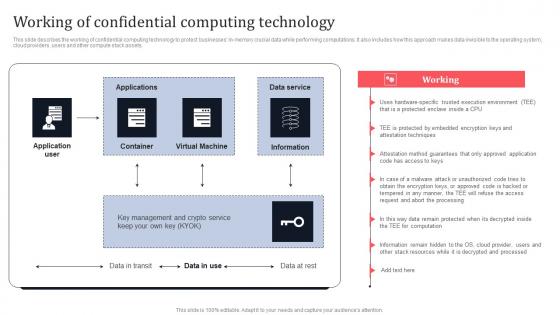
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
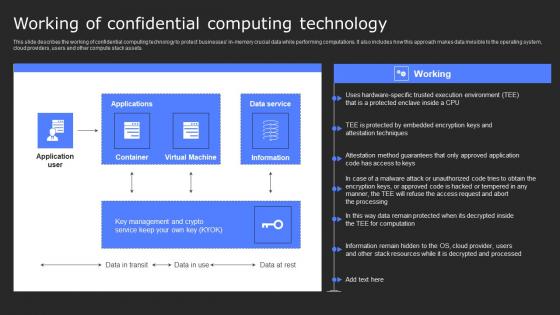
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
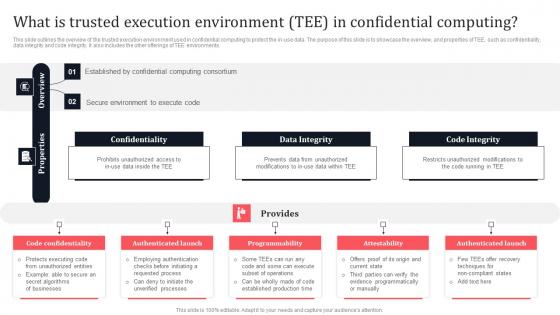
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
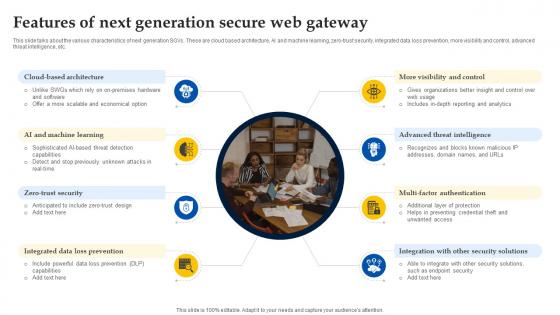
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.

Colorful Keys Around Piggy Bank Success PowerPoint Templates And PowerPoint Themes 0812
Colorful Keys Around Piggy Bank Success PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with colorful keys around piggy bank Examine data with our Colorful Keys Around Piggy Bank Success PowerPoint Templates And PowerPoint Themes 0812. You will come out on top.

Growing Cyber Security Issues Portrait PDF
Deliver and pitch your topic in the best possible manner with this growing cyber security issues portrait pdf. Use them to share invaluable insights on unprecedented attacks, cyber espionage, data theft and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
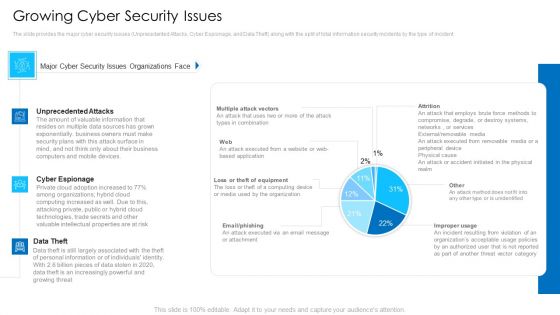
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
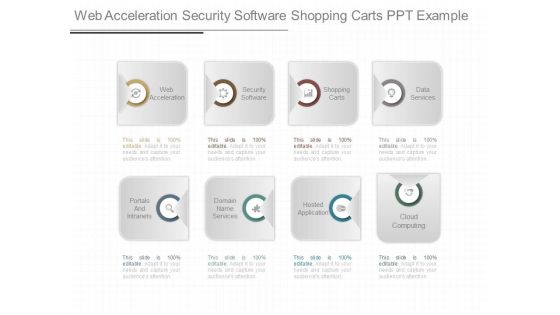
Web Acceleration Security Software Shopping Carts Ppt Example
This is a web acceleration security software shopping carts ppt example. This is a eight stage process. The stages in this process are web acceleration, security software, shopping carts, data services, portals and intranets, domain name services, hosted application, cloud computing.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Present Concerns Impeding Cybersecurity Clipart PDF
Presenting this set of slides with name cyber security implementation framework present concerns impeding cybersecurity clipart pdf. The topics discussed in these slides are data breaches and records exposed, reported financial losses due to increase cybercrimes, financial losses, cybercrimes incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
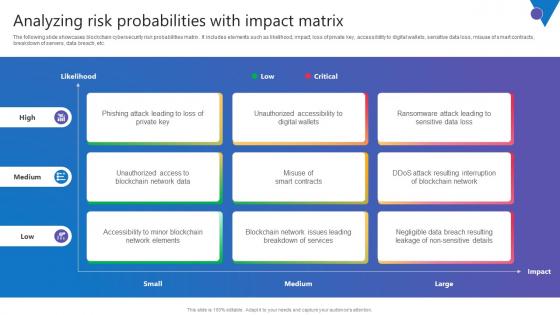
Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc.

Cyber Security Implementation Framework Analyzing IT Department On NIST Cybersecurity Framework Topics PDF
Presenting this set of slides with name cyber security implementation framework analyzing it department on nist cybersecurity framework topics pdf. This is a one stage process. The stages in this process are asset management, governance, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
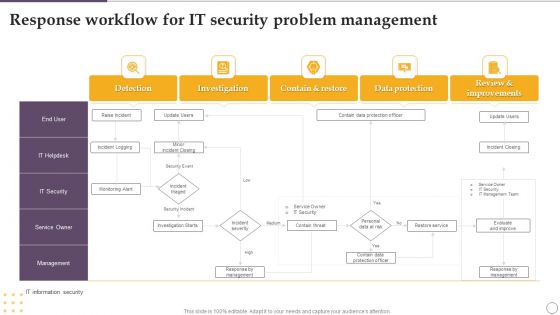
Response Workflow For IT Security Problem Management Ppt Outline Slide Download PDF
Showcasing this set of slides titled Response Workflow For IT Security Problem Management Ppt Outline Slide Download PDF. The topics addressed in these templates are Investigation, Contain And Restore, Data Protection, Detection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
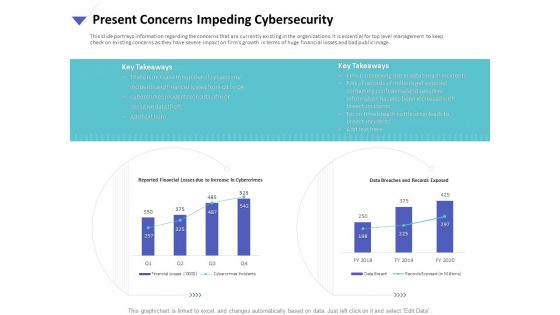
Strategies To Mitigate Cyber Security Risks Present Concerns Impeding Cybersecurity Ppt Show Objects PDF
Presenting this set of slides with name strategies to mitigate cyber security risks present concerns impeding cybersecurity ppt show objects pdf. The topics discussed in these slides are reported financial losses due increase cybercrimes, data breaches and records exposed, key takeaways. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
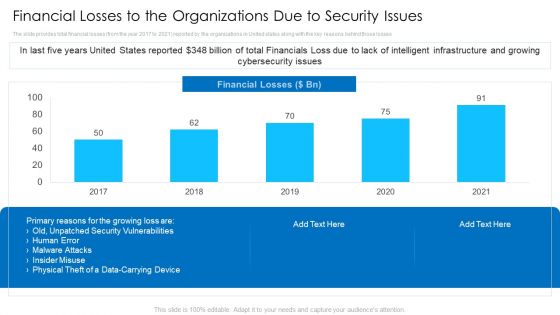
Financial Losses To The Organizations Due To Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues mockup pdf bundle. Topics like physical theft of a data carrying device, malware attacks, insider misuse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
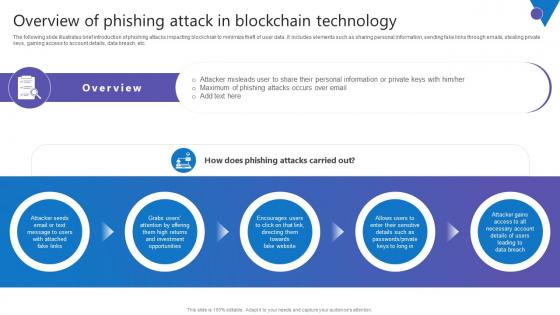
Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Presenting this PowerPoint presentation, titled Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Characteristics Of Software As A Service Saas Pictures PDF
Deliver an awe inspiring pitch with this creative mesh computing technology hybrid private public iaas paas saas workplan characteristics of software as a service saas pictures pdf bundle. Topics like high availability, elastic infrastructure, data security, application security, automated provisioning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
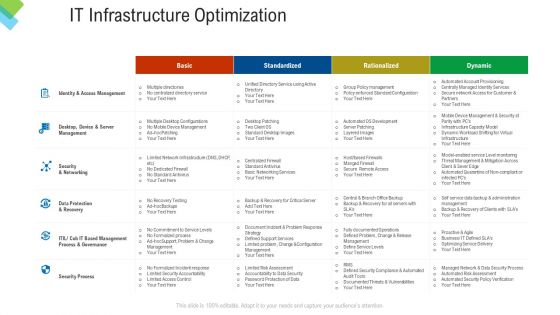
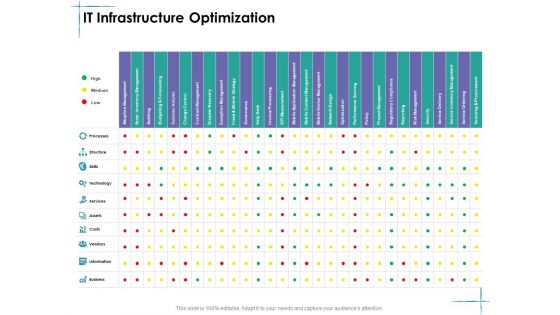
Construction Management Services IT Infrastructure Optimization Themes PDF
Deliver and pitch your topic in the best possible manner with this construction management services it infrastructure optimization themes pdf. Use them to share invaluable insights on security process, security and networking, management process, data protection, server management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
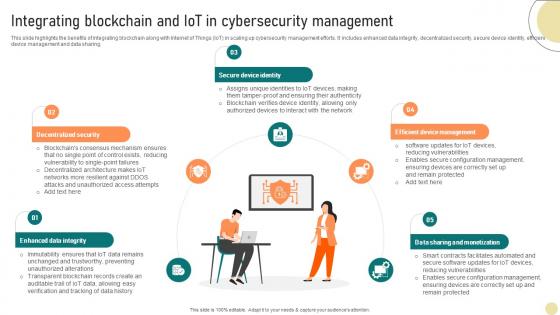
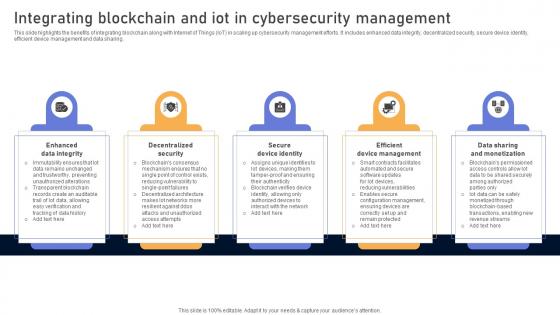
Visionary Guide To Blockchain Technologys Integrating Blockchain And IoT BCT SS V
This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing. Find highly impressive Visionary Guide To Blockchain Technologys Integrating Blockchain And IoT BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Technologys Integrating Blockchain And IoT BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing.
Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V
This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V today and make your presentation stand out from the rest This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing.

Developing Deploying Android Applications Competitive Analysis With Various Factors Information PDF
Presenting this set of slides with name developing deploying android applications competitive analysis with various factors information pdf. The topics discussed in these slides are price, engagement, data security, installation, superior quality. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Infrastructure Strategies IT Infrastructure Optimization Ppt Icon Information PDF
Deliver an awe inspiring pitch with this creative infrastructure strategies it infrastructure optimization ppt icon information pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
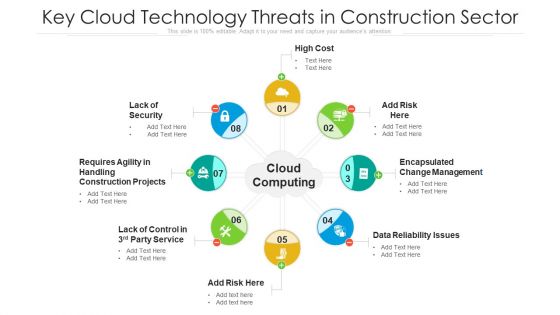
Key Cloud Technology Threats In Construction Sector Ppt PowerPoint Presentation File Example Introduction PDF
Presenting key cloud technology threats in construction sector ppt powerpoint presentation file example introduction pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including lack of security, high cost, data reliability issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
Facility Management IT Infrastructure Optimization Technology Ppt Slides Graphics Download PDF
Deliver an awe inspiring pitch with this creative facility management it infrastructure optimization technology ppt slides graphics download pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
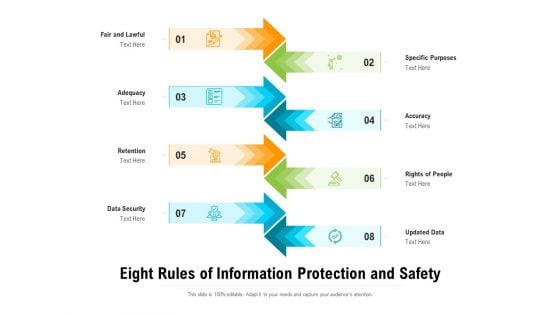
Eight Rules Of Information Protection And Safety Ppt PowerPoint Presentation Gallery Show PDF
Presenting eight rules of information protection and safety ppt powerpoint presentation gallery show pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including adequacy, retention, data security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
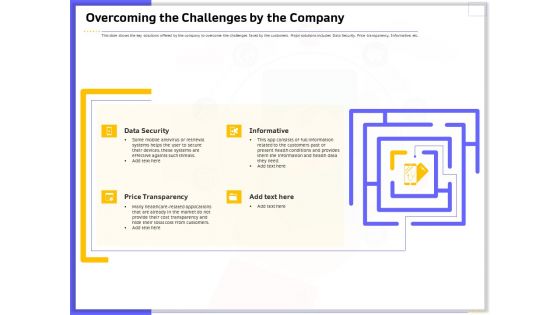
Developing Deploying Android Applications Overcoming The Challenges By The Company Diagrams PDF
Presenting this set of slides with name developing deploying android applications overcoming the challenges by the company diagrams pdf. This is a four stage process. The stages in this process are data security, price transparency, informative. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Key Issues Faced By Hospitality Sector Ppt PowerPoint Presentation Icon Example PDF
Showcasing this set of slides titled key issues faced by hospitality sector ppt powerpoint presentation icon example pdf. The topics addressed in these templates are management, data security, growth. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Android Framework For Apps Development And Deployment Competitive Analysis With Various Factors Icons PDF
Presenting this set of slides with name android framework for apps development and deployment competitive analysis with various factors icons pdf. The topics discussed in these slides are superior quality, low price, unique features, installation, data security, user engagement. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
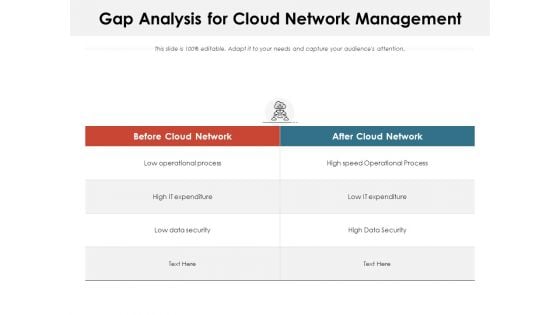
Gap Analysis For Cloud Network Management Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name gap analysis for cloud network management ppt powerpoint presentation file aids pdf. The topics discussed in these slides are process, data security, expenditure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
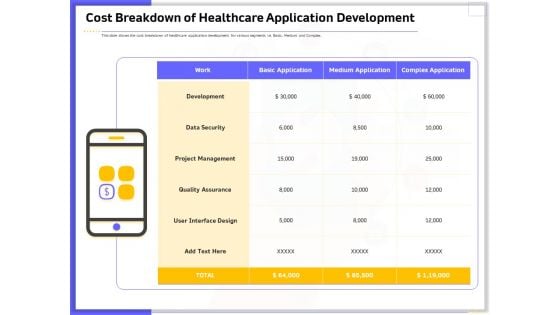
Developing Deploying Android Applications Cost Breakdown Of Healthcare Application Development Formats PDF
Presenting this set of slides with name developing deploying android applications cost breakdown of healthcare application development formats pdf. This is a one stage process. The stages in this process are development, data security, project management, quality assurance, interface design. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
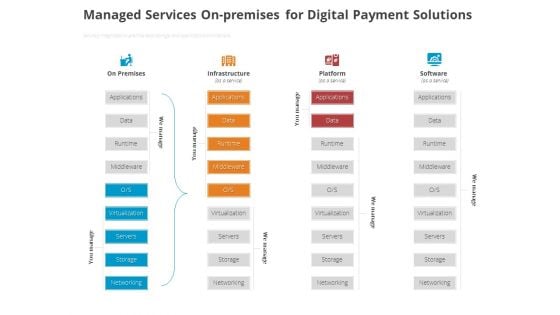
Online Settlement Revolution Managed Services Onpremises For Digital Payment Solutions Portrait PDF
Securely integrated on-premise data storage and applications architecture. Deliver an awe inspiring pitch with this creative online settlement revolution managed services onpremises for digital payment solutions portrait pdf bundle. Topics like on premises, infrastructure, platform, software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Three Level Business Continuity Diagram Ppt Slides
This is a three level business continuity diagram ppt slides. This is a three stage process. The stages in this process are business continuity planning, security management, disaster recovery, technology, roles, testing, risk management, data assessment, coordination, communicating plan, policy, technology, services, procedures, incident response.
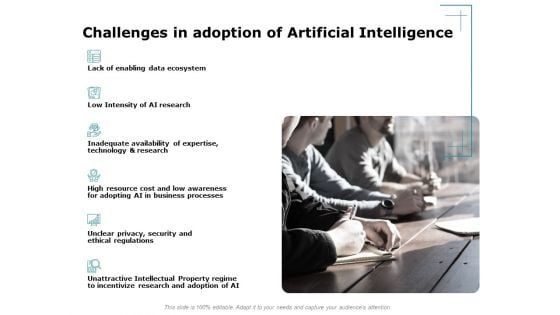
Artificial Intelligence Challenges In Adoption Of Artificial Intelligence Ppt Portfolio Designs PDF
Presenting this set of slides with name artificial intelligence challenges in adoption of artificial intelligence ppt portfolio designs pdf. This is a six stage process. The stages in this process are data ecosystem technology, business processes, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Smart Metering Management Diagram Good Ppt Example
This is a smart metering management diagram good ppt example. This is a eight stage process. The stages in this process are reporting, customer information system, billing system, asset management, network information system, security manager, dc persistency, monitoring and control, meter data management.
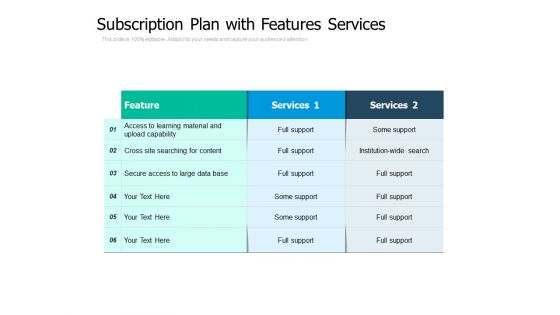
Subscription Plan With Features Services Ppt PowerPoint Presentation Infographic Template Aids
Presenting this set of slides with name subscription plan with features services ppt powerpoint presentation infographic template aids. The topics discussed in these slides are feature, services, secure access to large data base, cross site searching for content. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
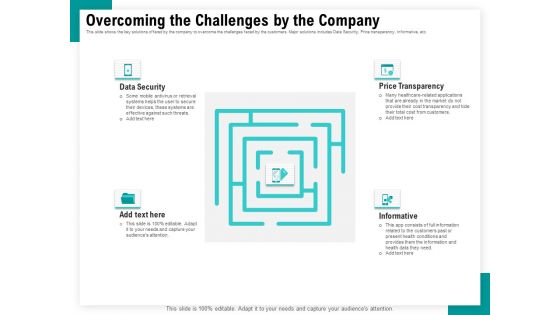
Android Framework For Apps Development And Deployment Overcoming The Challenges By The Company Inspiration PDF
Presenting this set of slides with name android framework for apps development and deployment overcoming the challenges by the company inspiration pdf. This is a four stage process. The stages in this process are data security, price transparency, informative. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
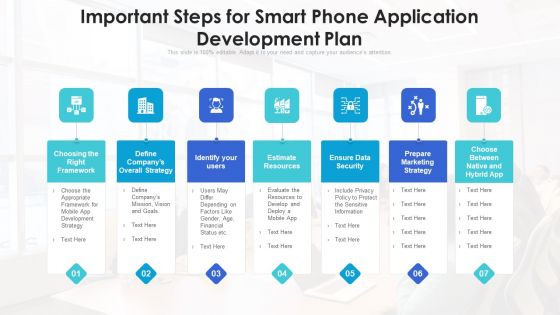
Important Steps For Smart Phone Application Development Plan Ppt Styles Graphics Template PDF
Pitch your topic with ease and precision using this important steps for smart phone application development plan ppt styles graphics template pdf. This layout presents information on strategy, data security, marketing strategy, resources, framework. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
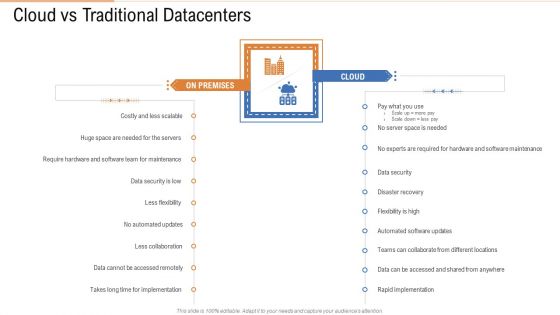
Cloud Vs Traditional Datacenters Ppt Slides Example PDF
Presenting cloud vs traditional datacenters ppt slides example pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like software, require, data security, teams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Advantages Of Cloud Storage In Business With Flexibility Ppt PowerPoint Presentation Icon Microsoft
Presenting this set of slides with name advantages of cloud storage in business with flexibility ppt powerpoint presentation icon microsoft. This is a five stage process. The stages in this process are increased resource sharing, data security, better backup, flexibility, business agility. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
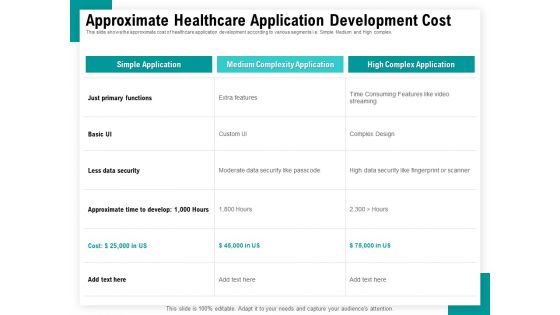
Android Framework For Apps Development And Deployment Approximate Healthcare Application Development Cost Structure PDF
Presenting this set of slides with name android framework for apps development and deployment approximate healthcare application development cost structure pdf. The topics discussed in these slides are simple application, medium complexity application, high complex application, extra features, moderate data security like passcode. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
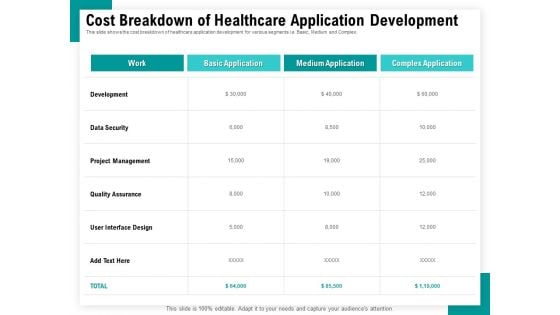
Android Framework For Apps Development And Deployment Cost Breakdown Of Healthcare Application Development Ideas PDF
Presenting this set of slides with name android framework for apps development and deployment cost breakdown of healthcare application development ideas pdf. The topics discussed in these slides are development, data security, project management, quality assurance, work, basic application, medium application, complex application. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
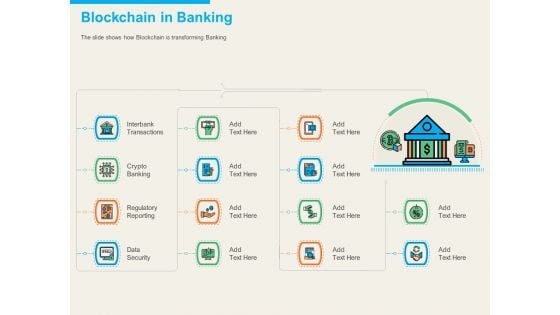
Understanding Blockchain Basics Use Cases Blockchain In Banking Ppt Slides Smartart PDF
Presenting this set of slides with name understanding blockchain basics use cases blockchain in banking ppt slides smartart pdf. The topics discussed in these slides are interbank transactions, crypto banking, regulatory reporting, data security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
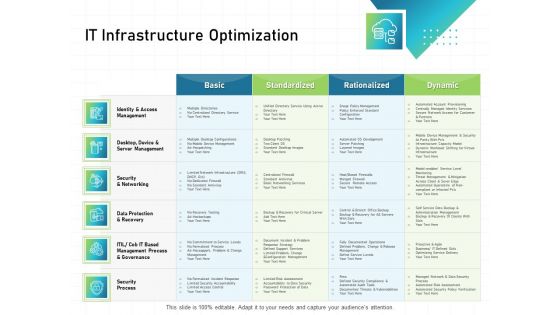
IT Infrastructure Administration IT Infrastructure Optimization Ppt Summary Example File PDF
Deliver an awe inspiring pitch with this creative it infrastructure administration it infrastructure optimization ppt summary example file pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
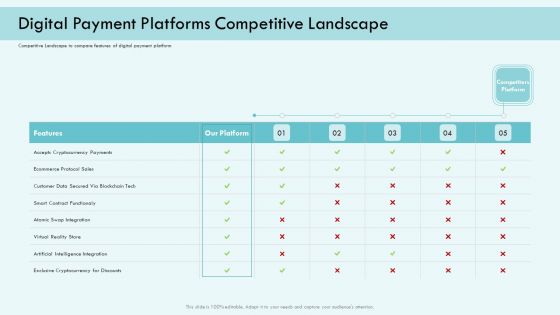
E Payment Transaction System Digital Payment Platforms Competitive Landscape Ppt Slides Structure PDF
Deliver and pitch your topic in the best possible manner with this E payment transaction system digital payment platforms competitive landscape ppt slides structure pdf. Use them to share invaluable insights on accepts cryptocurrency payments, customer data secured via blockchain tech, exclusive cryptocurrency for discounts and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
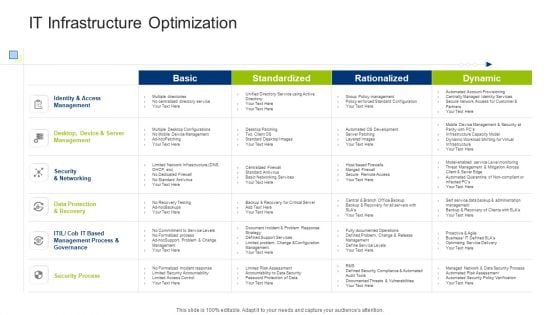
Infrastructure Building Administration IT Infrastructure Optimization Formats PDF
Deliver and pitch your topic in the best possible manner with this infrastructure building administration it infrastructure optimization formats pdf. Use them to share invaluable insights on identity and access management, security and networking, data protection and recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
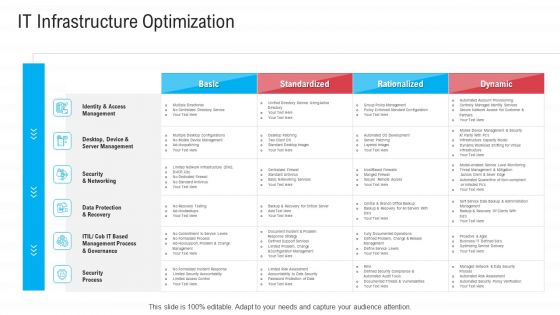
Infrastructure Designing And Administration IT Infrastructure Optimization Portrait PDF
Deliver an awe inspiring pitch with this creative infrastructure designing and administration it infrastructure optimization portrait pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Support Services Management IT Infrastructure Optimization Ppt Pictures Brochure PDF
Deliver an awe inspiring pitch with this creative support services management it infrastructure optimization ppt pictures brochure pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determining The Suitable Software For Organization Professional PDF
Deliver and pitch your topic in the best possible manner with this determining the suitable software for organization professional pdf. Use them to share invaluable insights on process automation, improve productivity, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
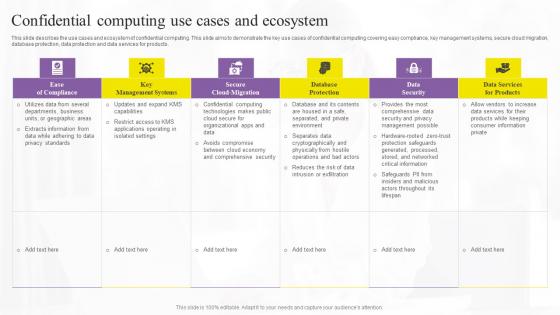
Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Slidegeeks has constructed Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.

Mobile Cloud Computing Overview And Benefits Application Areas Of Mobile Cloud Computing
The given slide showcases an overview of integrating cloud solutions in mobile applications along with the benefits. It includes flexibility, platform support, real-time data availability, and data security. Presenting this PowerPoint presentation, titled Mobile Cloud Computing Overview And Benefits Application Areas Of Mobile Cloud Computing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mobile Cloud Computing Overview And Benefits Application Areas Of Mobile Cloud Computing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mobile Cloud Computing Overview And Benefits Application Areas Of Mobile Cloud Computing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The given slide showcases an overview of integrating cloud solutions in mobile applications along with the benefits. It includes flexibility, platform support, real-time data availability, and data security

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
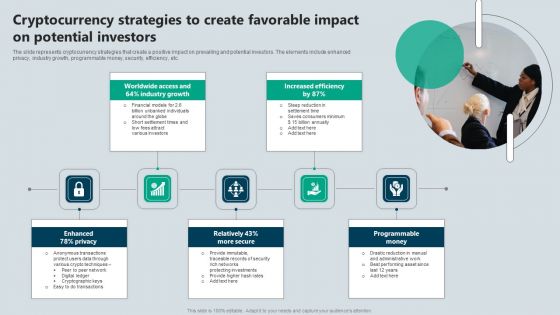
Cryptocurrency Strategies To Create Favorable Impact On Potential Investors Elements PDF
The slide represents cryptocurrency strategies that create a positive impact on prevailing and potential investors. The elements include enhanced privacy, industry growth, programmable money, security, efficiency, etc. Presenting Cryptocurrency Strategies To Create Favorable Impact On Potential Investors Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Privacy, Secure, Money. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
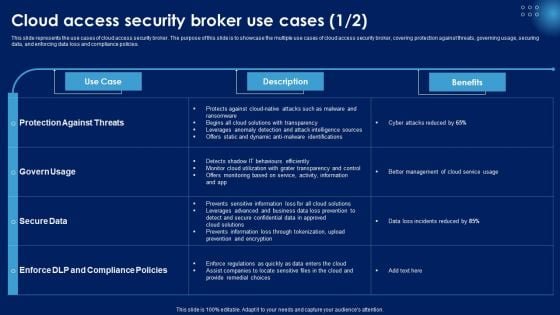
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.


 Continue with Email
Continue with Email

 Home
Home


































