Data Protection Strategy Template

Architecture Of Citrix Secure Web Gateway Proxy Solution Web Threat Protection System
This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Architecture Of Citrix Secure Web Gateway Proxy Solution Web Threat Protection System for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc.

Working Components Of Secure Web Gateway Architecture Web Threat Protection System
This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Components Of Secure Web Gateway Architecture Web Threat Protection System and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.

Roadmap To Integrate Secure Web Gateway Into Web Threat Protection System
This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Roadmap To Integrate Secure Web Gateway Into Web Threat Protection System to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Roadmap To Integrate Secure Web Gateway Into Web Threat Protection System. This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Best Practices For Secure Web Gateway Implementation Web Threat Protection System
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. There are so many reasons you need a Best Practices For Secure Web Gateway Implementation Web Threat Protection System. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Before Vs After Implementing Secure Web Gateway Web Threat Protection System
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Secure Web Gateway Web Threat Protection System can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
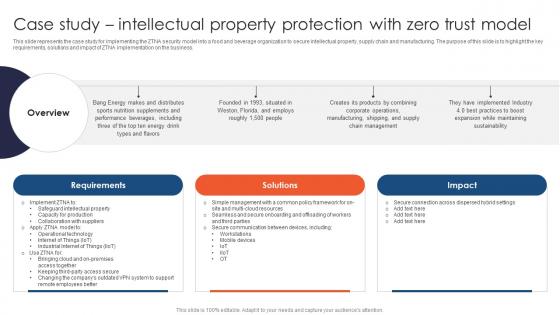
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Steps To Select Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Slidegeeks is here to make your presentations a breeze with Steps To Select Next Generation Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.

Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present like a pro with Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment.
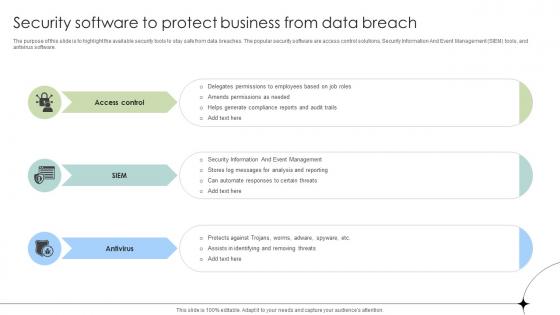
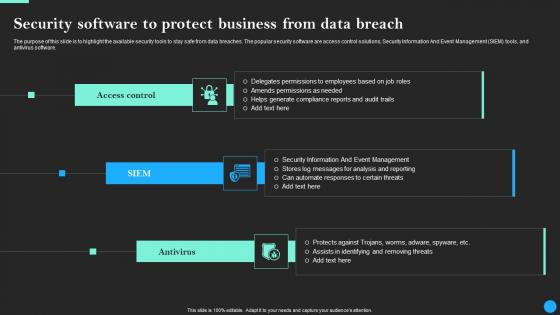
Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses
The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.
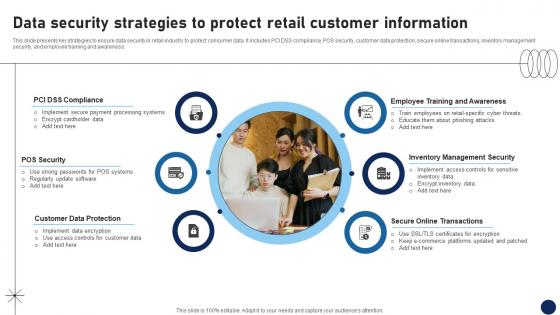
Data Security Strategies To Protect Retail Customer Information DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Information DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness.
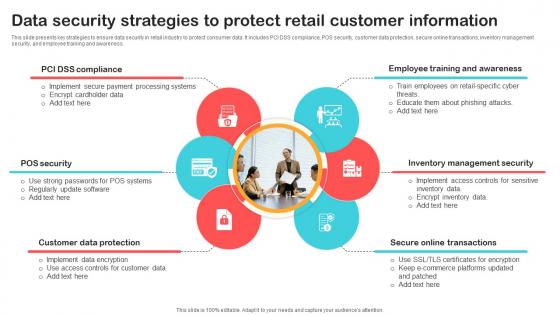
Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness.
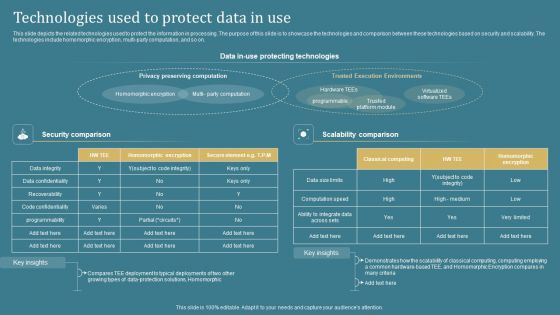
Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
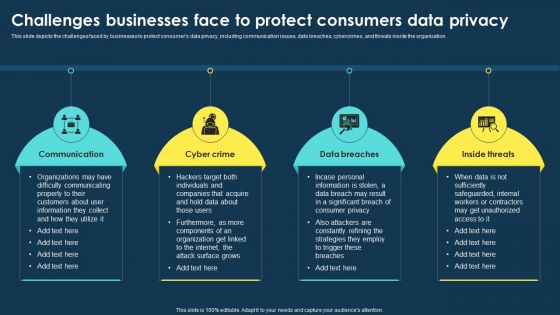
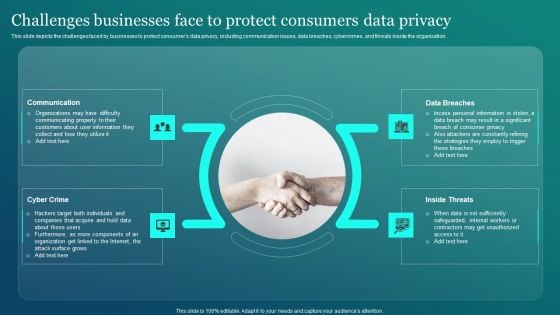
Integrating Data Privacy System Challenges Businesses Face To Protect Consumers Ppt Portfolio Influencers PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Integrating Data Privacy System Challenges Businesses Face To Protect Consumers Ppt Portfolio Influencers PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
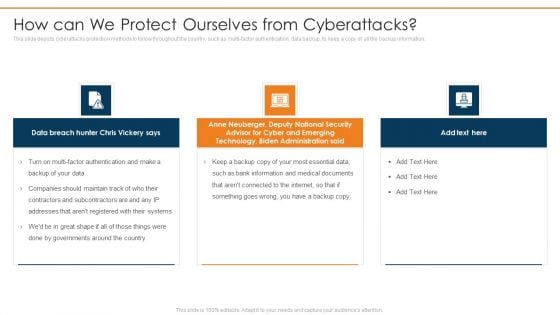
Data Wiper Spyware Attack How Can We Protect Ourselves From Cyberattacks Infographics PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information.This is a data wiper spyware attack how can we protect ourselves from cyberattacks infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like anne neuberger, advisor for cyber and emerging, technology, biden administration You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
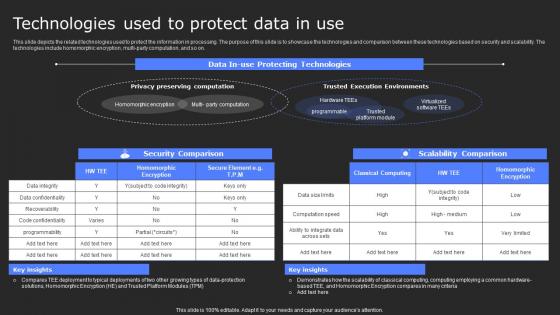
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
Security Software To Protect Business From Data Breach Prevention Elements Pdf
Want to ace your presentation in front of a live audience Our Security Software To Protect Business From Data Breach Prevention Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.

Information Privacy IT Challenges Businesses Face To Protect Consumers Data Privacy Infographics PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. This is a information privacy it challenges businesses face to protect consumers data privacy infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, data breaches, inside threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack How To Protect Yourself From Ongoing Cybersecurity Attacks Download PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc.Presenting data wiper spyware attack how to protect yourself from ongoing cybersecurity attacks download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like choose a strong password, keep your antivirus, software up to date In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
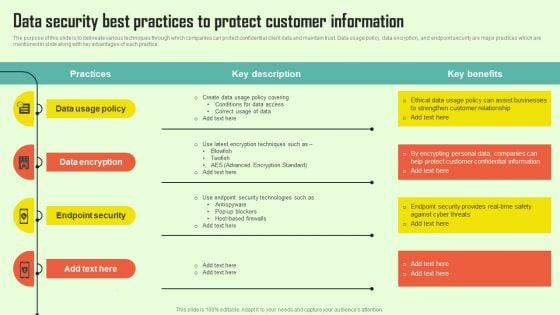
Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF
The purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Create an editable Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Develop Corporate Cyber Security Risk Mitigation 30 60 90 Days Plan For Organization Cyber Protection Proposal Mockup PDF
This is a develop corporate cyber security risk mitigation 30 60 90 days plan for organization cyber protection proposal mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
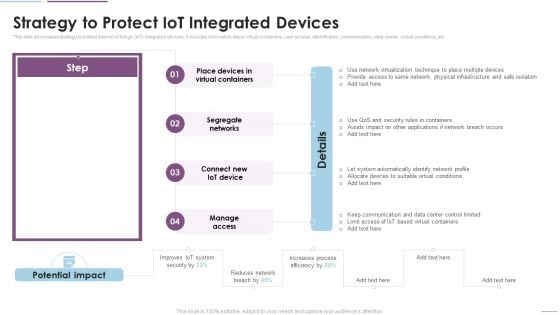
Supply Chain Management Strategy To Protect Iot Integrated Devices Infographics PDF
This slide showcases strategy to protect internet of things IoT integrated devices. It includes information about virtual containers, user access, identification, communication, data center, virtual conditions, etc. Deliver an awe inspiring pitch with this creative Supply Chain Management Strategy To Protect Iot Integrated Devices Infographics PDF bundle. Topics like Place Devices, Virtual Containers, Segregate Networks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Data Security Strategy Ppt PowerPoint Presentation Portfolio Infographic Template Cpb
Presenting this set of slides with name data security strategy ppt powerpoint presentation portfolio infographic template cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Key Phases For Data Center Management Consolidation Strategy Template PDF
This slide outlines phases of datacentre consolidation strategy aimed at downsizing servers, storage and networking systems, locations into efficient set of systems. It covers four stages evaluation, planning, designing, building and commission. Persuade your audience using this Key Phases For Data Center Management Consolidation Strategy Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Plan, Design. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
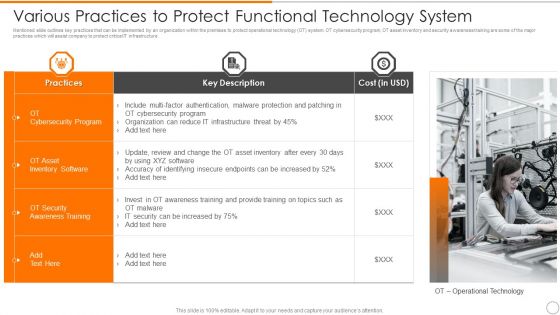
Various Practices To Protect Functional Technology System Information PDF
Showcasing this set of slides titled various practices to protect functional technology system information pdf. The topics addressed in these templates are inventory software, awareness training, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
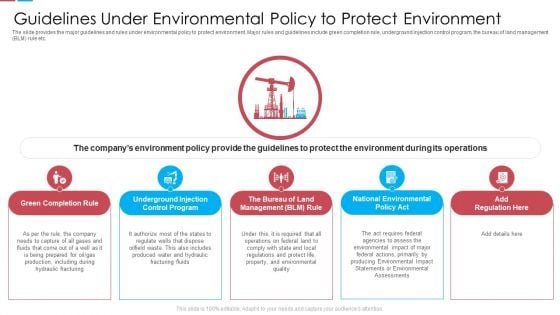
Guidelines Under Environmental Policy To Protect Environment Ppt Slides Template PDF
The slide provides the major guidelines and rules under environmental policy to protect environment. Major rules and guidelines include green completion rule, underground injection control program, the bureau of land management BLM rule etc. Presenting guidelines under environmental policy to protect environment ppt slides template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like green completion rule, underground injection control program, bureau of land management blm rule. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Carbon And Ecological Footprints Consumption Measures To Protect Environment Template PDF
This slide defines the measures taken under ecological and carbon footprint. The purpose of this template is to specify the measures to reduce the impact of human activity on the environment. It includes information related to recycle, reuse, waste management, and resource usage. Showcasing this set of slides titled Carbon And Ecological Footprints Consumption Measures To Protect Environment Template PDF. The topics addressed in these templates are Resource Usage, Reuse, Recycle And Reduce, Sharing Knowledge. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
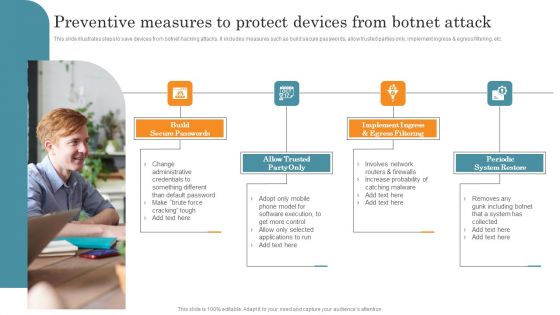
Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF
This slide illustrates steps to save devices from botnet hacking attacks. It includes measures such as build secure passwords, allow trusted parties only, implement ingress and egress filtering, etc. Presenting Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Build Secure Passwords, Allow Trusted Party Only, Implement Ingress. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
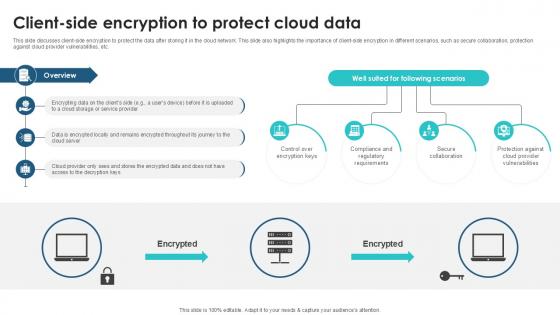
Client Side Encryption To Protect Client Side Encryption PPT Example
This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. There are so many reasons you need a Client Side Encryption To Protect Client Side Encryption PPT Example. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc.
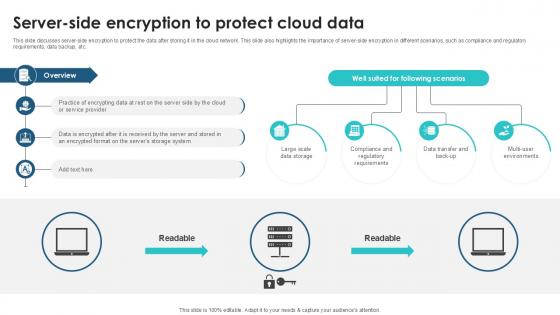
Server Side Encryption To Protect Client Side Encryption PPT Presentation
This slide discusses server-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server-side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc. Are you searching for a Server Side Encryption To Protect Client Side Encryption PPT Presentation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Server Side Encryption To Protect Client Side Encryption PPT Presentation from Slidegeeks today. This slide discusses server-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server-side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc.

Initiatives Taken To Protect Identity Fraud Professional PDF
This slide showcases scenarios in which different strategies can be undertaken to prevent identity fraud. This template focuses on reducing tendency of crime related to identity theft. It includes information related to protecting banks, computer, etc. Showcasing this set of slides titled Initiatives Taken To Protect Identity Fraud Professional PDF. The topics addressed in these templates are Protect Phone, Protect Bank Accounts, Protect Computer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
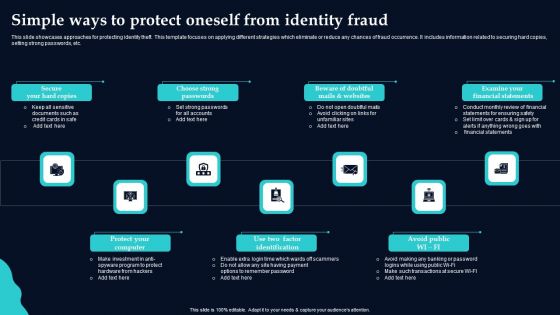
Simple Ways To Protect Oneself From Identity Fraud Diagrams PDF
This slide showcases approaches for protecting identity theft. This template focuses on applying different strategies which eliminate or reduce any chances of fraud occurrence. It includes information related to securing hard copies, setting strong passwords, etc. Presenting Simple Ways To Protect Oneself From Identity Fraud Diagrams PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Choose Strong Passwords, Beware Doubtful, Examine Financial Statements. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Password Protect In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Protect In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Protect. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Protect In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Guidelines Under Environmental Policy To Protect Environment Sample PDF
The slide provides the major guidelines and rules under environmental policy to protect environment. Major rules and guidelines include green completion rule, underground injection control program, the bureau of land management BLM rule etc.Presenting guidelines under environmental policy to protect environment sample pdf. to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like green completion rule, management software, power and cooling. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
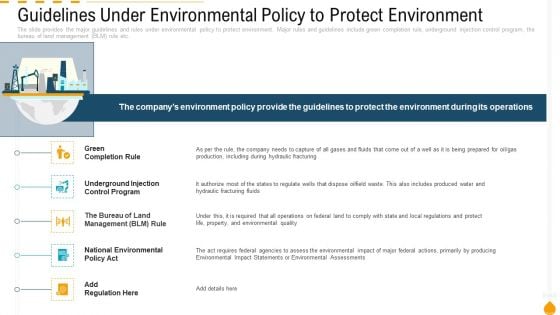
Guidelines Under Environmental Policy To Protect Environment Inspiration PDF
Presenting guidelines under environmental policy to protect environment inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like green completion rule, underground injection control program, the bureau of land management blm rule. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
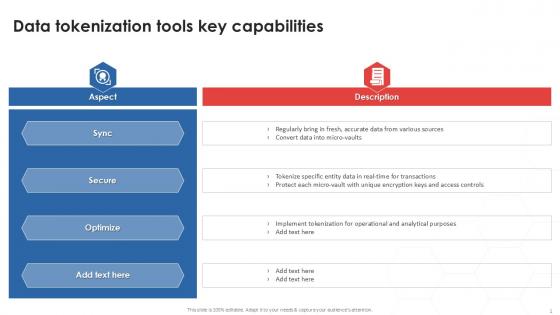
Data Tokenization Tools Tokenization Strategies For Data Security PPT Template
Boost your pitch with our creative Data Tokenization Tools Tokenization Strategies For Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Data Tokenization Tools Tokenization Strategies For Data Security PPT Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
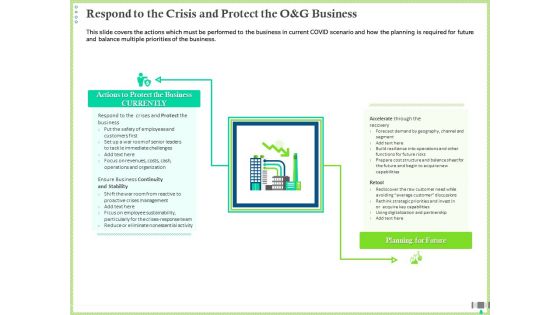
Post COVID Recovery Strategy Oil Gas Industry Respond To The Crisis And Protect The O And G Business Mockup PDF
This slide covers the actions which must be performed to the business in current COVID scenario and how the planning is required for future and balance multiple priorities of the business. Deliver and pitch your topic in the best possible manner with this post covid recovery strategy oil gas industry respond to the crisis and protect the o and g business mockup pdf. Use them to share invaluable insights on actions to protect the business currently, planning for future and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

COVID Business Survive Adapt Post Recovery Strategy Cinemas Protecting Employee Health Workplace Policies Template PDF
This slide covers the protecting employee health workplace policies voluntary health and safety guidelines for united states movie theater owners. This is a covid business survive adapt post recovery strategy cinemas protecting employee health workplace policies template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting employee health workplace policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Program Icon For Protecting Client Data Ideas PDF
Persuade your audience using this IT Security Program Icon For Protecting Client Data Ideas PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including It Security, Program Icon, Protecting Client Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
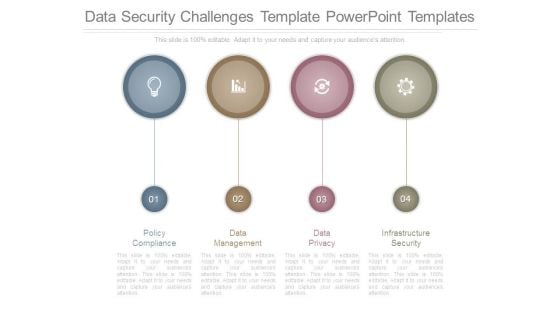
Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.
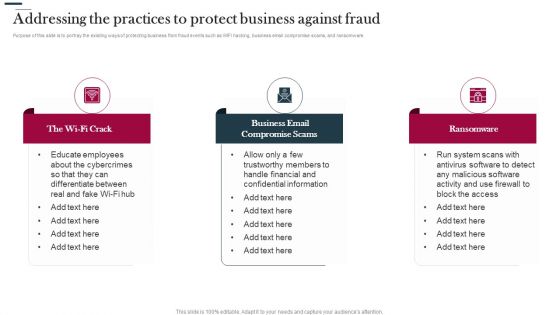
Various Strategies To Prevent Business Addressing The Practices To Protect Business Against Fraud Graphics PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Presenting Various Strategies To Prevent Business Addressing The Practices To Protect Business Against Fraud Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Business Email, Compromise Scams, Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
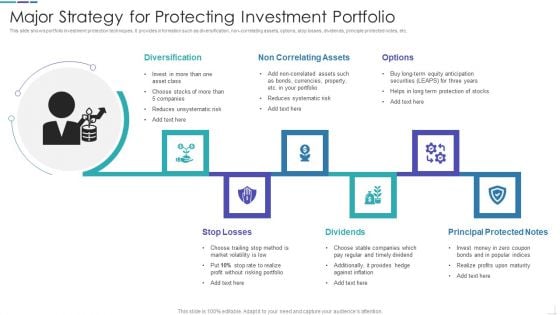
Major Strategy For Protecting Investment Portfolio Mockup PDF
This slide shows portfolio investment protection techniques. It provides information such as diversification, non-correlating assets, options, stop losses, dividends, principle protected notes, etc.Persuade your audience using this Major Strategy For Protecting Investment Portfolio Mockup PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Diversification, Principal Protected, Notes Dividends Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Strategy Plan Template Open The Secured Data With Safety Concept Statement
Our business strategy plan template open the secured data with safety concept statement Powerpoint Templates Heighten Concentration. Your Audience Will Be On The Edge.
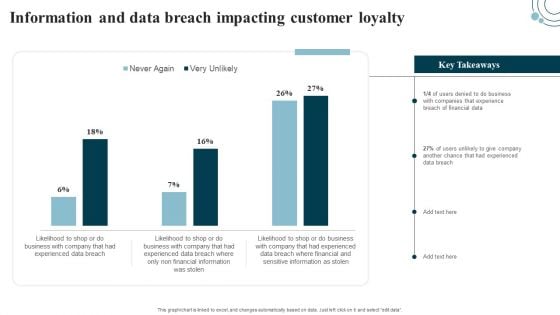
Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Get a simple yet stunning designed Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Information Analytics And Ml Strategy Playbook Requirement Of Data Management In BI Projects Template PDF
This slide covers the reasons for data management in an organization such as minimizing the data movement and attention to data security. This is a Information Analytics And Ml Strategy Playbook Requirement Of Data Management In BI Projects Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Use Existing Skills, Minimize Data Movement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Protect Business From Financial Crisis PowerPoint Templates Ppt Backgrounds For Slides 0513
Plan your storyboard with our Protect Business From Financial Crisis PowerPoint Templates Umbrellas Backgrounds For Slide. Give an outline to the solutions you have. Give power to your elbow with our Protect Business From Financial Crisis PowerPoint Templates Ppt Backgrounds For Slides 0513 PowerPoint Templates. Get that extra information you need. Drum up support with our Arrows PowerPoint Templates. They will come in droves to stand by you. Feel the ' chi ' with our Protect Business From Financial Crisis PowerPoint Templates Ppt Backgrounds For Slides 0513. Your inner energies will be on the rise.

Protect Your Savings Fom Market PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Protect Your Savings Fom Market PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download our Finance PowerPoint Templates because You can Bask in the warmth of our PowerPoint Templates and Slides. Enjoy the heartfelt glowing response of your listeners. Download and present our Umbrellas PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let your ideas bloom. Create a bed of roses for your audience. Download and present our Services PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Financial piggy bank with umbrella protect, money, finance, umbrellas, security, services. The prominent colors used in the PowerPoint template are Red, Yellow, Blue. With our Protect Your Savings Fom Market PowerPoint Templates Ppt Backgrounds For Slides 0413 your plans will never fall apart. They assist in maintaining close control.

Piggy In Lifesaver Protect Finance Business PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Piggy In Lifesaver Protect Finance Business PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download and present our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind. Present our Success PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to Piggy bank with the lifebuoy concept, business, security, finance, marketing, success. The prominent colors used in the PowerPoint template are Red, White, Black. Feast away on our Piggy In Lifesaver Protect Finance Business PowerPoint Templates Ppt Backgrounds For Slides 0313. Your eyes will get all the excitement they desire.

Protect Your Money For Future PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Protect Your Money For Future PowerPoint Templates PPT Backgrounds For Slides 0413.Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Money PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Use our Business PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way.Use these PowerPoint slides for presentations relating to Firewall, business, money, signs, security, shapes. The prominent colors used in the PowerPoint template are Blue, Red, Black. Show enterprise in your plans. Put them forth on our Protect Your Money For Future PowerPoint Templates Ppt Backgrounds For Slides 0413.

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder Approve plans with our Data Is Secure Internet PowerPoint Template 1110. You will come out on top.
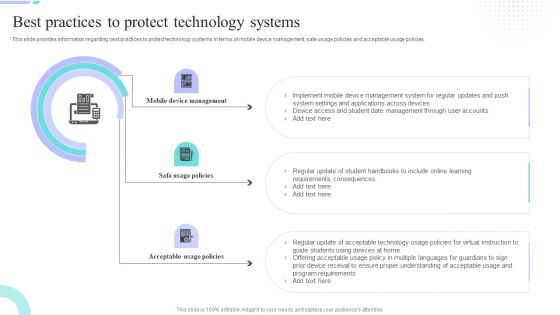
Distance Coaching Playbook Best Practices To Protect Technology Systems Summary PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Deliver an awe inspiring pitch with this creative Distance Coaching Playbook Best Practices To Protect Technology Systems Summary PDF bundle. Topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Initiatives To Protect The Fitness Industry From Outbreak Brochure PDF
This slide covers information about the major steps taken by the authorities and gym owners to protect the fitness industry from outbreak.Deliver and pitch your topic in the best possible manner with this key initiatives to protect the fitness industry from outbreak brochure pdf. Use them to share invaluable insights on memberships starting, outreach and awareness raising, promoting positive social attitudes and behavior and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
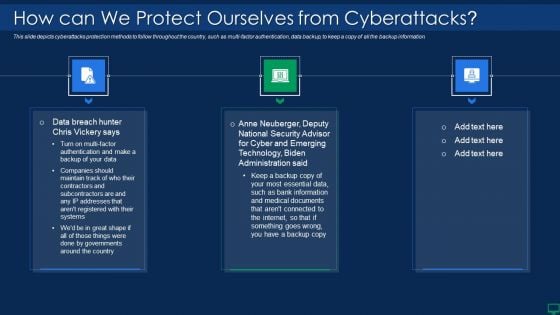
Russian Cyber Attacks On Ukraine IT How Can We Protect Ourselves Rules PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. This is a russian cyber attacks on ukraine it how can we protect ourselves rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internet, documents, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc.
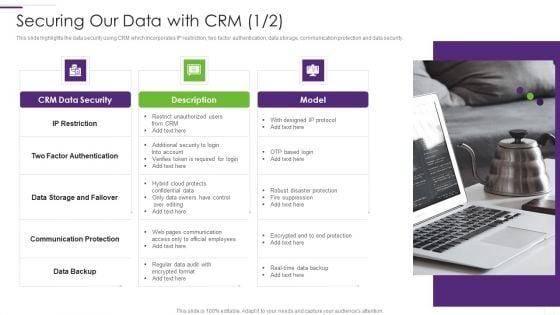
CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































