Data Protection Strategy Template

Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware.This is a Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compromise Scams, Ransomware, Confidential Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
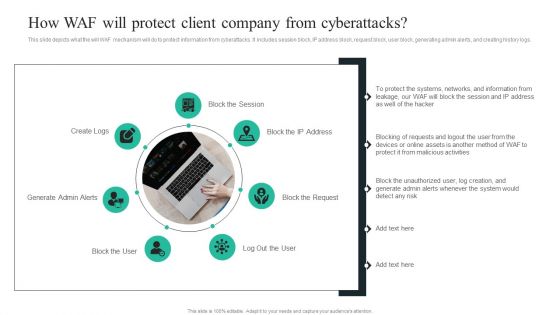
WAF Introduction How WAF Will Protect Client Company From Cyberattacks Microsoft PDF
This slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. This WAF Introduction How WAF Will Protect Client Company From Cyberattacks Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The WAF Introduction How WAF Will Protect Client Company From Cyberattacks Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Regulations Of Security Tokenization Strategies For Data Security PPT Template
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.
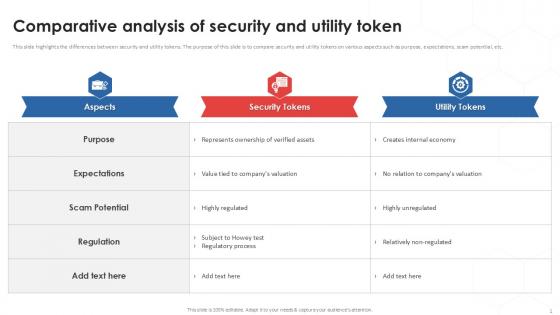
Comparative Analysis Of Tokenization Strategies For Data Security PPT Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Find a pre-designed and impeccable Comparative Analysis Of Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc.

Cloud Security Implementation Strategy Ppt Template
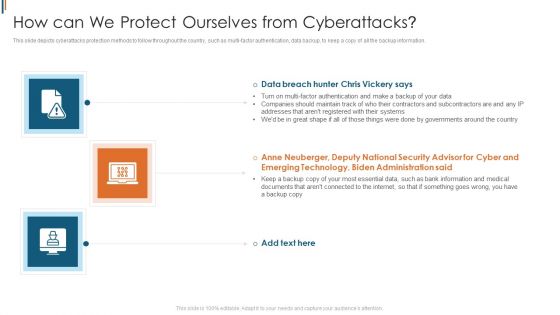
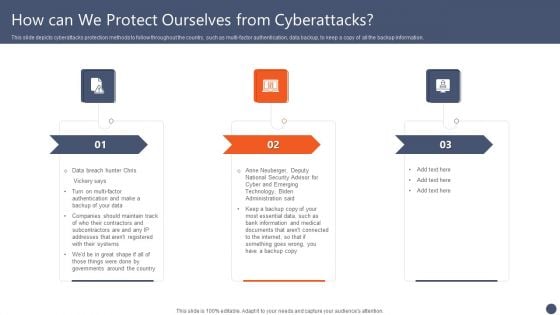
Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solutions To Protect Bitcoin Against Everything About Bitcoin PPT Sample Fin SS V
This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc. Explore a selection of the finest Solutions To Protect Bitcoin Against Everything About Bitcoin PPT Sample Fin SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Solutions To Protect Bitcoin Against Everything About Bitcoin PPT Sample Fin SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc.

Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc.
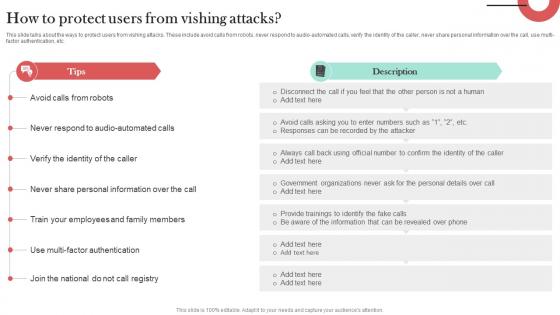
How To Protect Users From Vishing Attacks Man In The Middle Phishing IT
This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Are you searching for a How To Protect Users From Vishing Attacks Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How To Protect Users From Vishing Attacks Man In The Middle Phishing IT from Slidegeeks today. This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc.

Electronic Learning Playbook Best Practices To Protect Technology Systems Formats PDF
This slide provides information regarding comparative assessment of various customized learning platforms, compared on various features such as easy to use interface, suite of collaborative tools, etc. Deliver and pitch your topic in the best possible manner with this electronic learning playbook best practices to protect technology systems formats pdf Use them to share invaluable insights on best practices to protect technology systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Unconventional Monetary Policy How Did Those Who Bought Cdos Protect Themselves Clipart PDF
Presenting unconventional monetary policy how did those who bought cdos protect themselves clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like traditional, protected, instruments, crisis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
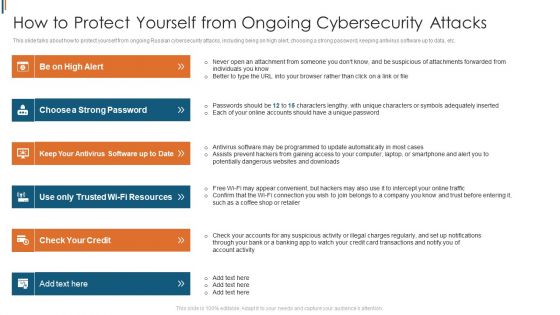
Ukraine Cyberwarfare How To Protect Yourself From Ongoing Cybersecurity Attacks Themes Pdf
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. This is a ukraine cyberwarfare how to protect yourself from ongoing cybersecurity attacks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like choose a strong password, keep your antivirus software up to date, use only trusted wi fi resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Remote Learning Playbook Best Practices To Protect Technology Systems Structure PDF
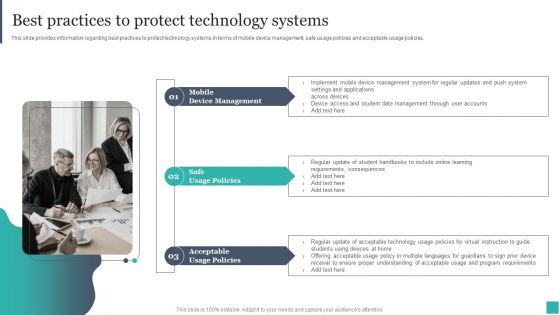
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. This is a Remote Learning Playbook Best Practices To Protect Technology Systems Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
E Learning Playbook Best Practices To Protect Technology Systems Icons PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Presenting E Learning Playbook Best Practices To Protect Technology Systems Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Acceptable Usage Policies, Safe Usage Policies, Mobile Device Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
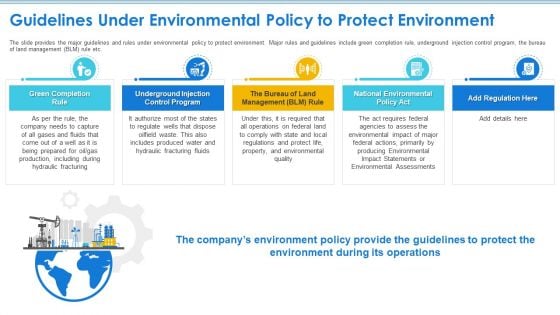
Case Competition Petroleum Sector Issues Guidelines Under Environmental Policy To Protect Environment Diagrams PDF
The slide provides the major guidelines and rules under environmental policy to protect environment. Major rules and guidelines include green completion rule, underground injection control program, the bureau of land management BLM rule etc. This is a case competition petroleum sector issues guidelines under environmental policy to protect environment diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control program, management, national environmental policy act, impact statements, environmental assessments. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
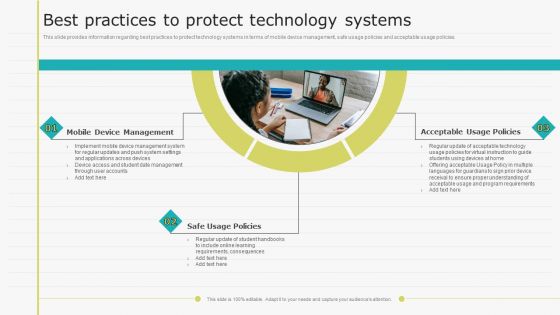
Virtual Learning Playbook Best Practices To Protect Technology Systems Slides PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Presenting Virtual Learning Playbook Best Practices To Protect Technology Systems Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Fraud Avoidance Playbook Addressing The Practices To Protect Business Against Fraud Infographics PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. This is a Fraud Avoidance Playbook Addressing The Practices To Protect Business Against Fraud Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like The Wi Fi Crack, Business Email Compromise Scams, Ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Nestle Csr Activities To Protect Natural Resources Packaged Food Business Download Pdf
This slide provides glimpse about different sustainable activities initiated by Nestle corporation to restore natural resources. It includes initiatives such as reduction in carbon emissions, planting trees, etc. Create an editable Nestle Csr Activities To Protect Natural Resources Packaged Food Business Download Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Nestle Csr Activities To Protect Natural Resources Packaged Food Business Download Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides glimpse about different sustainable activities initiated by Nestle corporation to restore natural resources. It includes initiatives such as reduction in carbon emissions, planting trees, etc.
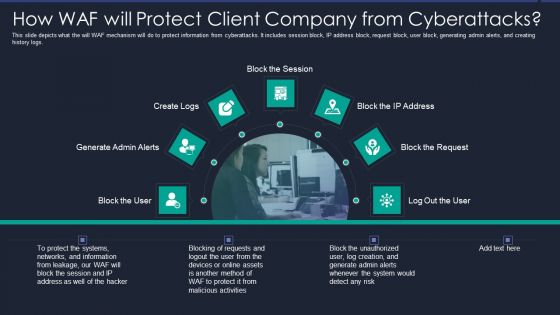
Web App Firewall Services IT How WAF Will Protect Client Company From Cyberattacks Elements PDF
This slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. Presenting web app firewall services it how waf will protect client company from cyberattacks elements pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like information, systems, networks, method. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Technology Mediated Learning Playbook Best Practices To Protect Technology Systems Microsoft PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Technology Mediated Learning Playbook Best Practices To Protect Technology Systems Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Digital Coaching And Learning Playbook Best Practices To Protect Technology Systems Designs PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Digital Coaching And Learning Playbook Best Practices To Protect Technology Systems Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Electronic Learning Playbook Best Practices To Protect Technology Systems Cont Introduction PDF
This slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Deliver an awe inspiring pitch with this creative electronic learning playbook best practices to protect technology systems cont introduction pdf bundle. Topics like deploy internet content, approve applications websites, suitable school devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Strategy To Be Adopted 1 Data Encryption Ppt Outline PDF
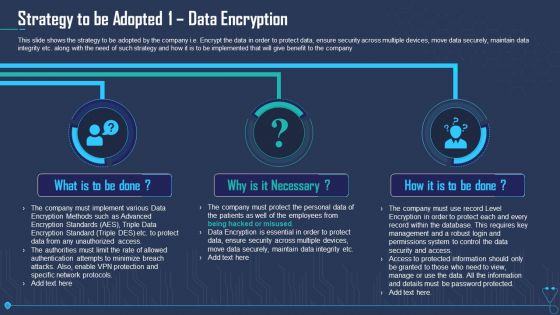
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt outline pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Data Center Risks And Mitigation Strategies For Data Center Relocation Template PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. This modern and well-arranged Deploying Data Center Risks And Mitigation Strategies For Data Center Relocation Template PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Data Threats Organizational Prevention Based Strategy Infographics PDF
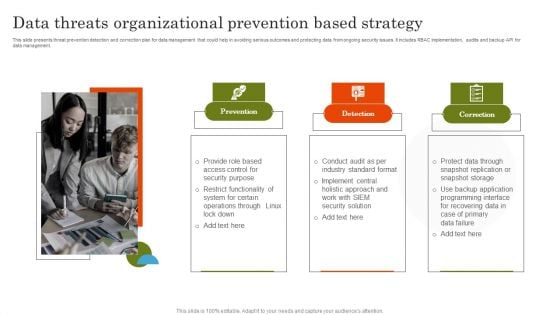
This slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Increase audience engagement and knowledge by dispensing information using Data Threats Organizational Prevention Based Strategy Infographics PDF. This template helps you present information on three stages. You can also present information on Prevention, Detection, Correction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

Protecting The Data Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Download and present our shapes PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download and present our Technology PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake.Use these PowerPoint slides for presentations relating to Folder and file security concept, business, shapes, computer, signs, technology. The prominent colors used in the PowerPoint template are Blue, White, Black. PowerPoint presentation experts tell us our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. You can be sure our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are readymade to fit into any presentation structure. PowerPoint presentation experts tell us our concept PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Presenters tell us our Protecting The Data Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. PowerPoint presentation experts tell us our concept PowerPoint templates and PPT Slides are visually appealing. Edit plans with our Protecting The Data Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.

Key Elements Of Data Center Management Optimization Strategy Professional PDF
This slide outlines elements for datacentre optimization strategy aimed at weaving organizations data infrastructure to maximize return on optimization efforts. It covers use of physical space, virtualization, external cloud computing, maximize storage and network requirements and optimizing power use. Presenting Key Elements Of Data Center Management Optimization Strategy Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtualization, Optimized Power Use, Use Physical Space. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Flowchart For Data Breach Incident Communication Response Strategy Pictures PDF
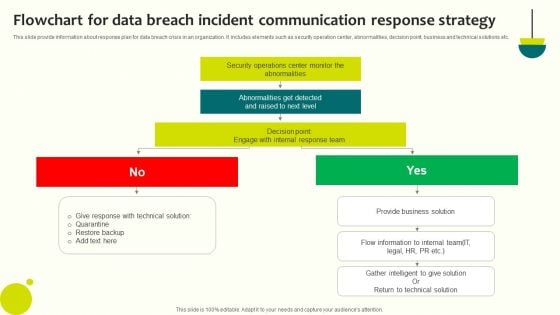
This slide provide information about response plan for data breach crisis in an organization. It includes elements such as security operation center, abnormalities, decision point, business and technical solutions etc. Presenting Flowchart For Data Breach Incident Communication Response Strategy Pictures PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Technical Solution, Response Team, Level. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
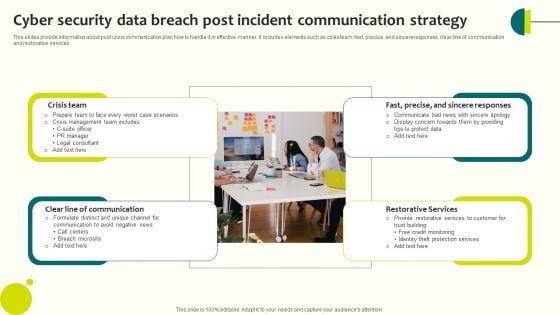
Cyber Security Data Breach Post Incident Communication Strategy Slides PDF
This slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services Presenting Cyber Security Data Breach Post Incident Communication Strategy Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Crisis Team, Communication, Restorative Services. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Building Data Analytics And Cyber Security Strategy Framework Icons PDF
This slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Persuade your audience using this Building Data Analytics And Cyber Security Strategy Framework Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Expansion, Standardize And Automate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Breach Incident Communication Strategy With Solutions Themes PDF
This slide illustrate communication plan along with solution to overcome, types of data breaches in an organization. It includes types of data breaches such as ransomware, password guessing, phishing and virus Pitch your topic with ease and precision using this Data Breach Incident Communication Strategy With Solutions Themes PDF. This layout presents information on Description, Communication Channel, Responsible Person. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icons Slide For Cloud Data Security Template PDF
Presenting our innovatively structured Icons Slide For Cloud Data Security Template PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
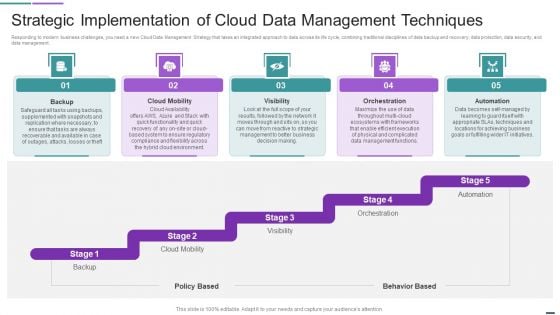
Strategic Implementation Of Cloud Data Management Techniques Template PDF
Responding to modern business challenges, you need a new Cloud Data Management Strategy that takes an integrated approach to data across its life cycle, combining traditional disciplines of data backup and recovery, data protection, data security, and data management. This is a Strategic Implementation Of Cloud Data Management Techniques Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Mobility, Orchestration, Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
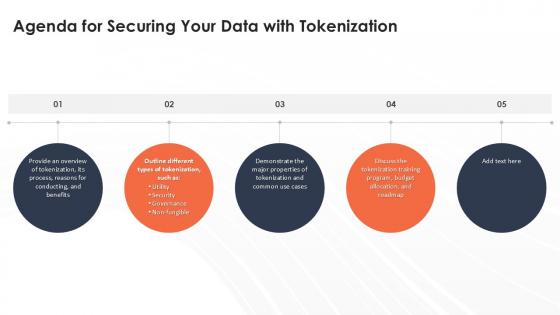
Agenda For Securing Your Data With Tokenization Ppt Template
Create an editable Agenda For Securing Your Data With Tokenization Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Securing Your Data With Tokenization Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Securing Your Data With Tokenization Ppt Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
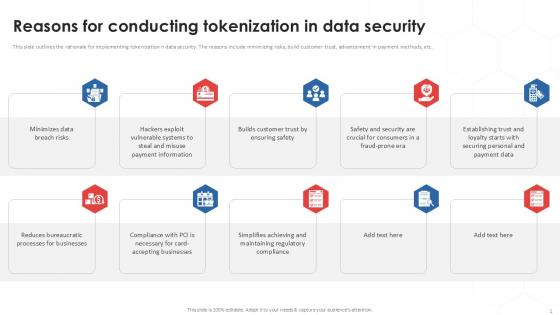
Reasons For Conducting Tokenization In Data Security PPT Template
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Boost your pitch with our creative Reasons For Conducting Tokenization In Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.

Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
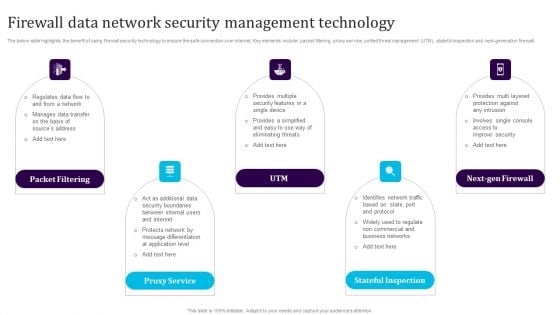
Firewall Data Network Security Management Technology Template PDF
The below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Persuade your audience using this Firewall Data Network Security Management Technology Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Packet Filtering, Proxy Service, Utm, Next Gen Firewall, Stateful Inspection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
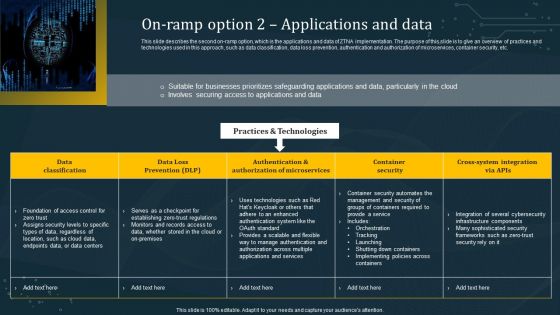
On Ramp Option 2 Applications And Data Template PDF
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Take your projects to the next level with our ultimate collection of On Ramp Option 2 Applications And Data Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Data Security Statistics Ppt PowerPoint Presentation Infographic Template Cpb
Presenting this set of slides with name data security statistics ppt powerpoint presentation infographic template cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security statistics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Medical Data Security Ppt PowerPoint Presentation Infographic Template Cpb
Presenting this set of slides with name medical data security ppt powerpoint presentation infographic template cpb. This is an editable Powerpoint two stages graphic that deals with topics like medical data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Breach Prevention Recognition Security Awareness Program Checklist Template PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
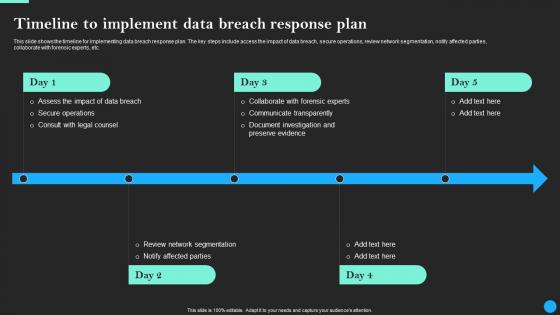
Timeline To Implement Data Breach Response Plan Data Breach Prevention Template Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Breach Prevention Template Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc.

Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses
This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc.
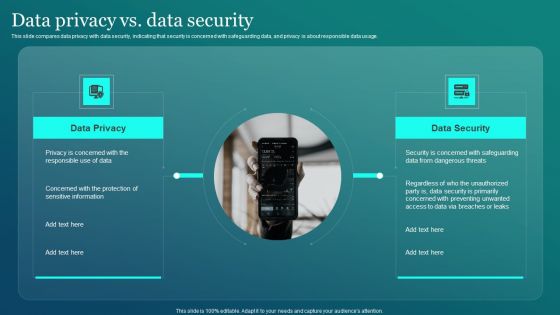
Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
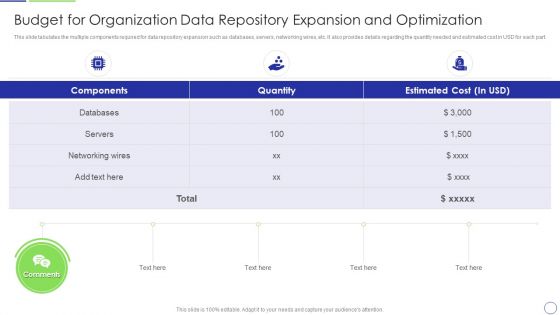
Developing Organization Primary Data Storage Action Plan Budget For Organization Data Repository Expansion Template PDF
This slide tabulates the multiple components required for data repository expansion such as databases, servers, networking wires, etc. It also provides details regarding the quantity needed and estimated cost in USD for each part. Deliver and pitch your topic in the best possible manner with this developing organization primary data storage action plan budget for organization data repository expansion template pdf. Use them to share invaluable insights on budget for organization data repository expansion and optimization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
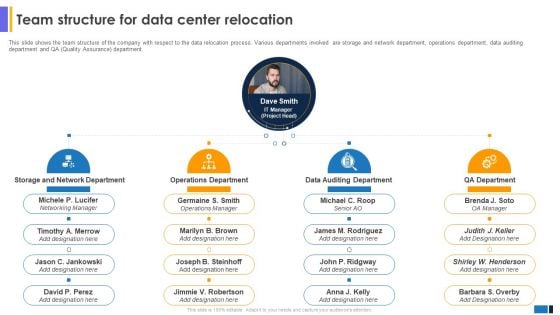
Team Structure For Data Center Relocation Data Center Migration Information Technology Template PDF
This slide shows the team structure of the company with respect to the data relocation process. Various departments involved are storage and network department, operations department, data auditing department and QA Quality Assurance department.This Team Structure For Data Center Relocation Data Center Migration Information Technology Template PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Team Structure For Data Center Relocation Data Center Migration Information Technology Template PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Data Services Market Data Pricing Analytics Ppt PowerPoint Presentation Slides Template Cpb Pdf
Presenting this set of slides with name data services market data pricing analytics ppt powerpoint presentation slides template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data security financial services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
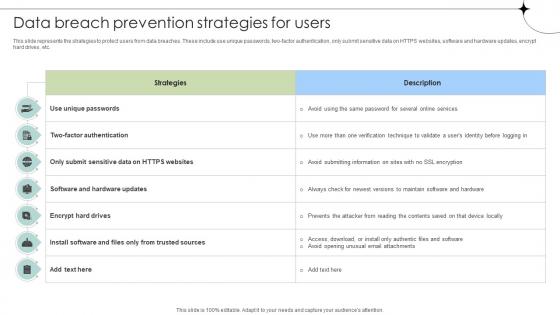
Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.

Doctor Wearing Protective Equipment To Stop COVID Infection Ppt Infographic Template Slides PDF
Showcasing this set of slides titled doctor wearing protective equipment to stop COVID infection ppt infographic template slides pdf. The topics addressed in these templates are doctor wearing protective equipment to stop covid infection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organization Emergency Action Strategy For Power Outage Template PDF
This slide presents workplace emergency action plan for power outage, helpful in protecting staff and infrastructure from undesirable disruptions in office. It includes avoiding panic , turning-off electric equipment and informing power supply company. Pitch your topic with ease and precision using this Organization Emergency Action Strategy For Power Outage Template PDF. This layout presents information on Communication Devices, Critical Systems, Human Resource Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CRM Solutions Implementation Strategy Securing Our Data With CRM Structure PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.Deliver and pitch your topic in the best possible manner with this CRM Solutions Implementation Strategy Securing Our Data With CRM Structure PDF Use them to share invaluable insights on Factor Authentication, Communication Protection, Storage And Failover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Development Strategy Template Show The Key Concept
Our business development strategy template show the key concept Powerpoint Templates Team Are A Dogged Lot. They Keep At It Till They Get It Right.

Business Diagram Lock With Puzzle Strategy Concept Presentation Template
This business diagram template has been crafted with graphic of puzzle. This diagram contains the concept of strategy building and safety. Use this diagram for your business and security related presentations.
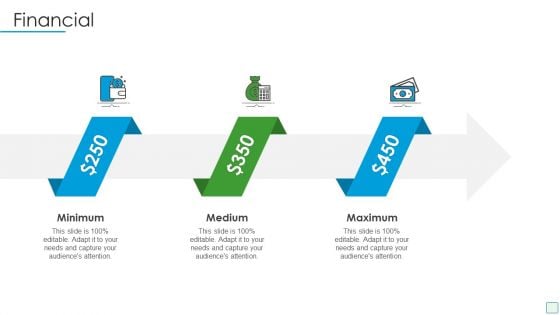
Developing Firm Security Strategy Plan Financial Template PDF
Presenting developing firm security strategy plan financial template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
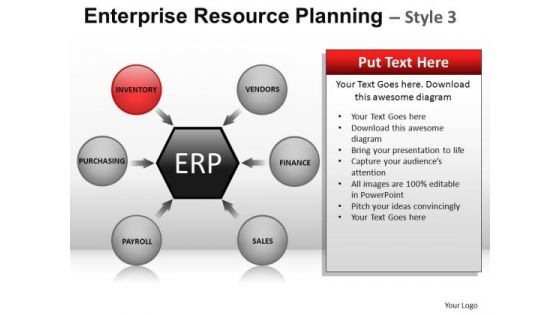
PowerPoint Template Business Strategy Targets Enterprise Resource Planning Ppt Slide
PowerPoint Template Business Strategy Targets Enterprise Resource Planning PPT Slide-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Our PowerPoint Template Business Strategy Targets Enterprise Resource Planning Ppt Slide are high fidelity. They accurately convey your thoughts to your listeners.

Stock Photo Business Strategy Plan Template Girl With Umbrella Images
Our stock photo business strategy plan template girl with umbrella stock photo images Powerpoint Templates Allow You To Do It With Ease. Just Like Picking The Low Hanging Fruit. Boil The Ocean With Your Thoughts. Our umbrellas Powerpoint Templates Will Help Create Waves.
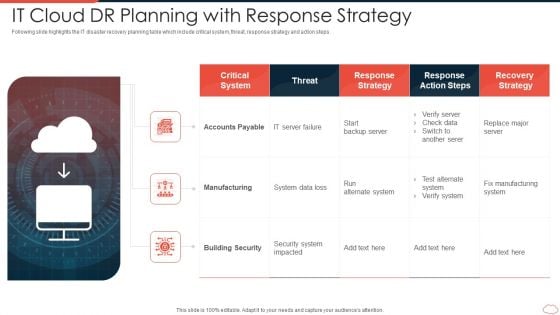
IT Cloud DR Planning With Response Strategy Template PDF
Following slide highlights the IT disaster recovery planning table which include critical system, threat, response strategy and action steps. Showcasing this set of slides titled it cloud dr planning with response strategy template pdf. The topics addressed in these templates are accounts payable, manufacturing, building security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































