Data Protection Strategy Template

Post Implementation Challenges And Risks Of Saas Program Ppt PowerPoint Presentation File Graphics PDF
The following slide highlights the post implementation challenges and risks of SaaS platform illustrating key headings which includes control issues, version control, hard to switch and security issues. Presenting post implementation challenges and risks of saas program ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including control issues, version controls, hard to switch, security issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
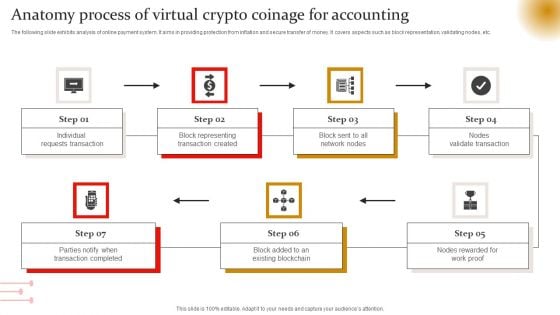
Anatomy Process Of Virtual Crypto Coinage For Accounting Themes PDF
The following slide exhibits analysis of online payment system. It aims in providing protection from inflation and secure transfer of money. It covers aspects such as block representation, validating nodes, etc. Showcasing this set of slides titled Anatomy Process Of Virtual Crypto Coinage For Accounting Themes PDF. The topics addressed in these templates are Individual Requests Transaction, Nodes Validate Transaction, Network Nodes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
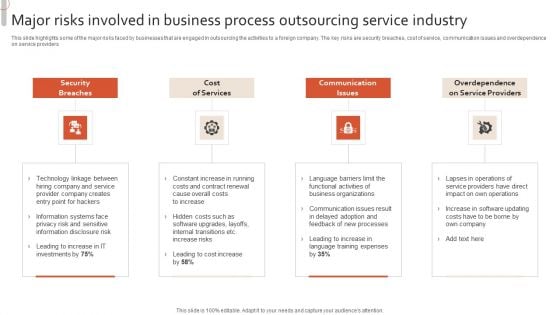
Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF
This slide highlights some of the major risks faced by businesses that are engaged in outsourcing the activities to a foreign company. The key risks are security breaches, cost of service, communication issues and overdependence on service providers. Presenting Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Breaches, Cost Services, Communicationi Ssues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Features And Disadvantages Of 5Th Generation System Wireless Technology Transformation Diagrams PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Features And Disadvantages Of 5Th Generation System Wireless Technology Transformation Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
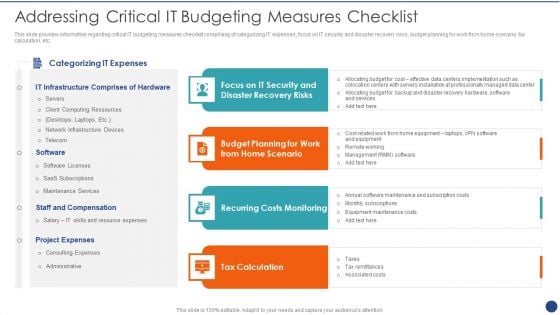
Cios Value Optimization Addressing Critical IT Budgeting Measures Checklist Formats PDF
This slide provides information regarding critical IT budgeting measures checklist comprising of categorizing IT expenses, focus on IT security and disaster recovery risks, budget planning for work from home scenario, tax calculation, etc. Presenting Cios Value Optimization Addressing Critical IT Budgeting Measures Checklist Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like IT Infrastructure, Project Expenses, Tax Calculation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Venture Digitial Transformation IT OT Roles And Competencies Ppt Icon Display PDF
In this slide we have Listed a variety of IT or OT integration competencies that suited certain types of roles. Presenting Smart Venture Digitial Transformation IT OT Roles And Competencies Ppt Icon Display PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like IT Roles, Technical Applications Architect, Chief Information, Security Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Role Of Automation In Improving ESO System Ppt PowerPoint Presentation File Graphics Tutorials PDF
This slide covers role of automation in improving enterprise security operation. It involves AI powered threat detection, integrated threat intelligence and alert validation and noise reduction. Presenting Role Of Automation In Improving ESO System Ppt PowerPoint Presentation File Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including AI Powered, Threat Detection, Integrated Threat Intelligence, Alert Validation, Noise Reduction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
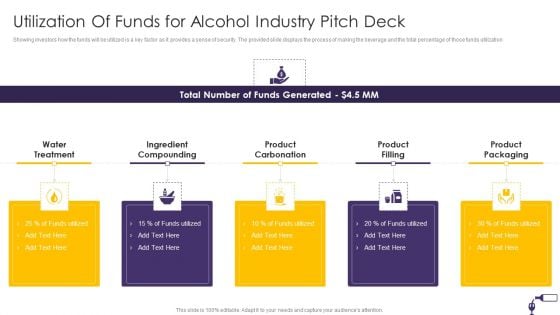
Utilization Of Funds For Alcohol Industry Pitch Deck Ppt Pictures Example File PDF
Showing investors how the funds will be utilized is a key factor as it provides a sense of security. The provided slide displays the process of making the beverage and the total percentage of those funds utilization. Presenting Utilization Of Funds For Alcohol Industry Pitch Deck Ppt Pictures Example File PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Water Treatment, Ingredient Compounding, Product Carbonation, Product Filling, Product Packaging. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
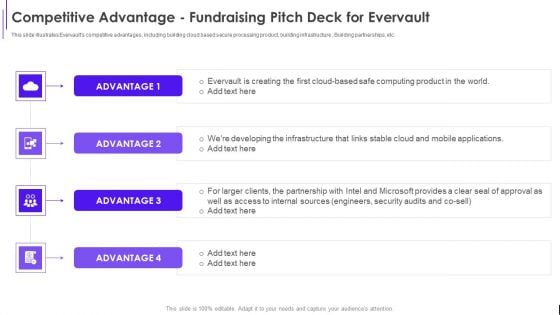
Competitive Advantage Fundraising Pitch Deck For Evervault Ppt Inspiration Background Images PDF
This slide illustrates Evervaults competitive advantages, including building cloud based secure processing product, building infrastructure , Building partnerships, etc. Presenting Competitive Advantage Fundraising Pitch Deck For Evervault Ppt Inspiration Background Images PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Evervault Creating, Cloud Based, Internal Sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Devops Configuration Management IT Addressing Various Trends Associated To Devops Implementation Mockup PDF
This slide provides information regarding various trends associated to DevOps implementation in terms of DevOps automation, using serverless architecture, etc. Presenting devops configuration management it addressing various trends associated to devops implementation mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like devops automation, serverless architecture, embedded security. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Quality Assurance Testing Methodologies Non Functional Icons PDF
This slide shows the non functional methodologies for Quality assurance testing. Methodologies covered in the slide are Vulnerability, usability testing, compatible testing and performance testing. Presenting quality assurance testing methodologies non functional icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like vulnerability security testing, usability testing, performance testing. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
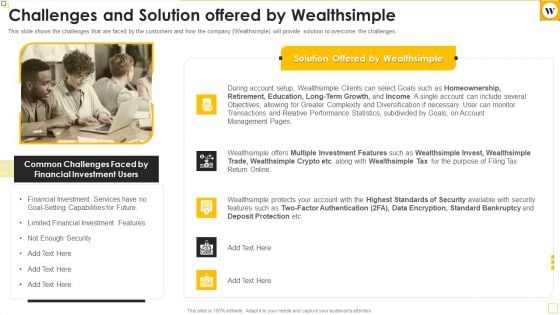
Wealthsimple Capital Raising Elevator Pitch Deck Challenges And Solution Offered By Wealthsimple Brochure Pdf
This slide shows the challenges that are faced by the customers and how the company Wealthsimple will provide solution to overcome the challenges. Presenting wealthsimple capital raising elevator pitch deck challenges and solution offered by wealthsimple brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like not enough security, limited financial investment features, financial investment services have no goal setting capabilities for future. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
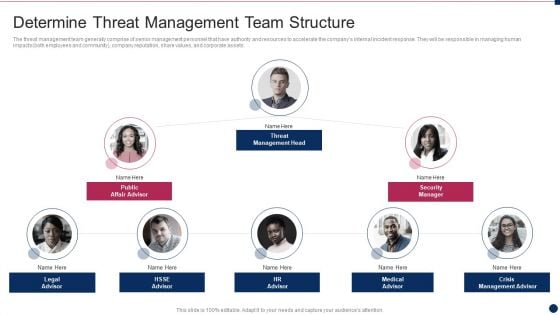
Threat Management At Workplace Determine Threat Management Team Structure Designs Pdf
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting threat management at workplace determine threat management team structure designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like threat management head, public affair advisor, security manager. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
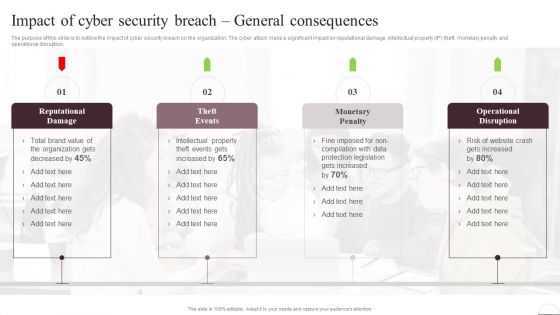
Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Amazon Tactical Plan How Amazon Secured Brand Position By Maintaining Leadership Microsoft PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features AND services, and subsidiaries. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Amazon Tactical Plan How Amazon Secured Brand Position By Maintaining Leadership Microsoft PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Mobile Device Management For Improving IT Operations Ensuring Checklist For Mobile Sample PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Mobile Device Management For Improving IT Operations Ensuring Checklist For Mobile Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Product Lifecycle Effective Influencing Factors Comprehensive Guide To Product Lifecycle Icons Pdf
This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc. Are you searching for a Product Lifecycle Effective Influencing Factors Comprehensive Guide To Product Lifecycle Icons Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Product Lifecycle Effective Influencing Factors Comprehensive Guide To Product Lifecycle Icons Pdf from Slidegeeks today. This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
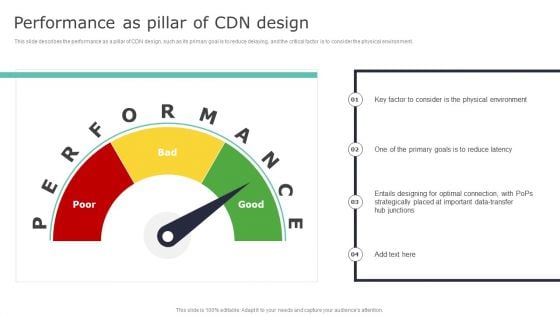
Deploying Content Distribution Network System Performance As Pillar Of CDN Design Introduction PDF
This slide describes the performance as a pillar of CDN design, such as its primary goal is to reduce delaying, and the critical factor is to consider the physical environment. Are you searching for a Deploying Content Distribution Network System Performance As Pillar Of CDN Design Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Content Distribution Network System Performance As Pillar Of CDN Design Introduction PDF from Slidegeeks today.

5G Network Applications And Features Core Architecture Of 5G Technology Overview Rules PDF
This slide talks about the overview of 5G core architecture and its components, including unified data convergence, control plane function group, information network, and user plane function. Welcome to our selection of the 5G Network Applications And Features Core Architecture Of 5G Technology Overview Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Security Management Plan Steps In Detail Training And Building Role Competencies Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Competition Petroleum Sector Issues Government Regulations That Affect The Oil And Gas Sector Themes PDF
The slide provides the key acts regulations and regulated authorities related to oil and gas sector. Key regulations include The Clean Air Act, US Energy Policy, Health and Safety Standards etc. Deliver an awe inspiring pitch with this creative case competition petroleum sector issues government regulations that affect the oil and gas sector themes pdf bundle. Topics like growing company, producing and consuming that energy, regulatory authority, environmental protection agency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
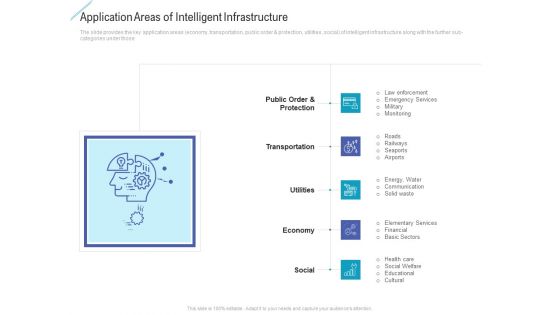
Application Areas Of Intelligent Infrastructure Clipart PDF
Presenting application areas of intelligent infrastructure clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like public order and protection, transportation, utilities, economy, social. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
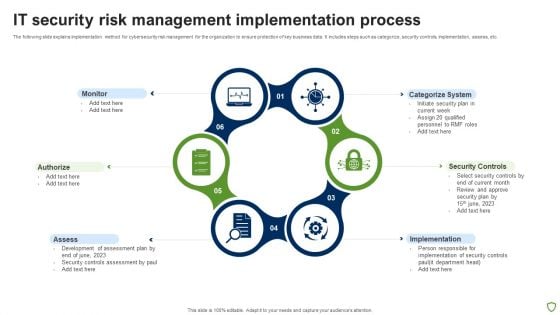
IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
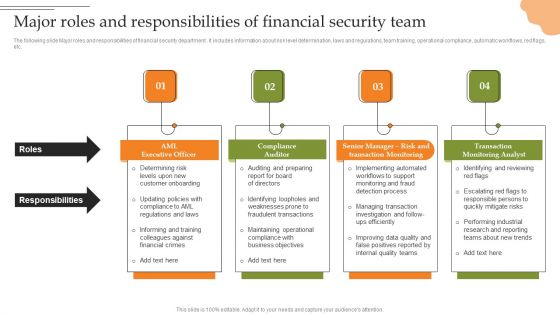
Creating Transaction Monitoring Major Roles And Responsibilities Of Financial Summary PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Welcome to our selection of the Creating Transaction Monitoring Major Roles And Responsibilities Of Financial Summary PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
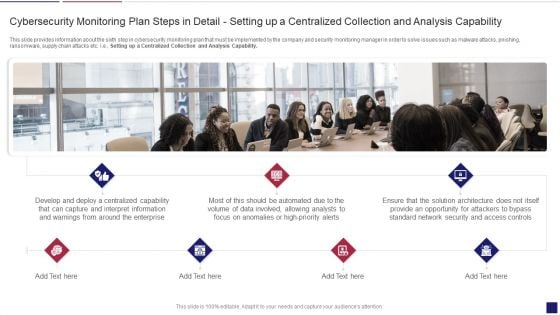
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
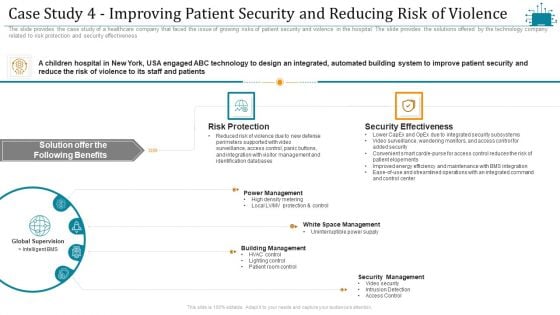
Cloud Intelligence Framework For Application Consumption Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like power management, building management, security management, security effectiveness, global supervision can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
Business Event Day Activities Standard Safety Equipment Required To Host Icons PDF
This slide provides an overview of safety equipments required at event premises. The equipments covered are temporary fencing, security personnel, first aid station and crowd control barriers. Are you searching for a Business Event Day Activities Standard Safety Equipment Required To Host Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Business Event Day Activities Standard Safety Equipment Required To Host Icons PDF from Slidegeeks today.

The Comprehensive Billing Solution Cost Management Cloud Computing Complexities And Solutions Professional PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services.Want to ace your presentation in front of a live audience Our The Comprehensive Billing Solution Cost Management Cloud Computing Complexities And Solutions Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
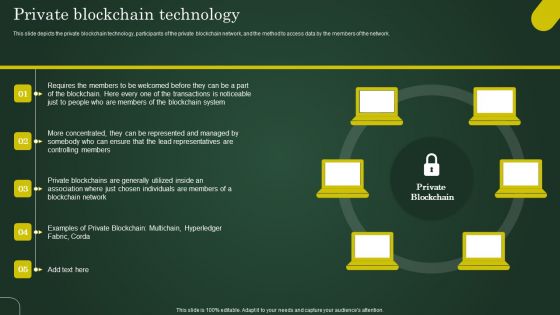
Private Blockchain Technology Involving Cryptographic Ledger To Enhance Ideas PDF
This slide depicts the private blockchain technology, participants of the private blockchain network, and the method to access data by the members of the network. Are you searching for a Private Blockchain Technology Involving Cryptographic Ledger To Enhance Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Private Blockchain Technology Involving Cryptographic Ledger To Enhance Ideas PDF from Slidegeeks today.

Drug Discovery And Development Process Step 3 Clinical Development Clipart PDF
This slide provides information about the third step in the drug discovery and development process i.e. clinical development. Clinical Development includes various elements such as dose escalation, single ascending, healthy volunteer study, biological samples collection, pharmacokinetic analysis, feces sample analysis for drug, patient protection etc. Deliver an awe inspiring pitch with this creative drug discovery and development process step 3 clinical development clipart pdf bundle. Topics like development, analysis, validation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
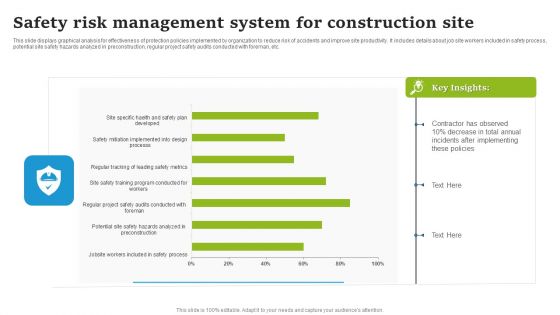
Safety Risk Management System For Construction Site Elements PDF
This slide displays graphical analysis for effectiveness of protection policies implemented by organization to reduce risk of accidents and improve site productivity. It includes details about job site workers included in safety process, potential site safety hazards analyzed in preconstruction, regular project safety audits conducted with foreman, etc. Showcasing this set of slides titled Safety Risk Management System For Construction Site Elements PDF. The topics addressed in these templates are Contractor Has Observed, Total Annual, Incidents After Implementing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
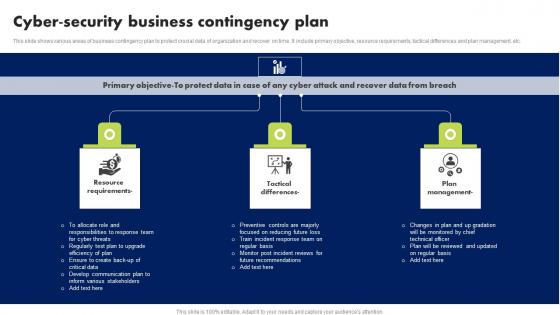
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.
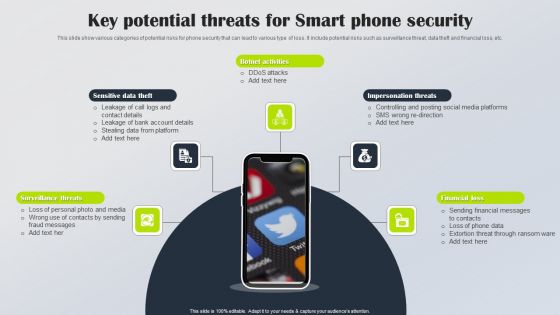
Key Potential Threats For Smart Phone Security Summary PDF
This slide show various categories of potential risks for phone security that can lead to various type of loss. It include potential risks such as surveillance threat, data theft and financial loss, etc. Persuade your audience using this Key Potential Threats For Smart Phone Security Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Botnet Activities, Impersonation Threats, Financial Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
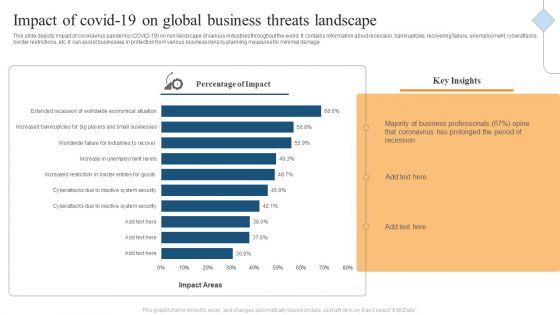
Impact Of Covid 19 On Global Business Threats Landscape Ppt Summary Ideas PDF
This slide depicts impact of coronavirus pandemic COVID-19 on risk landscape of various industries throughout the world. It contains information about recession, bankruptcies, recovering failure, unemployment, cyberattacks, border restrictions, etc. it can assist businesses in protection from various business risks by planning measures for minimal damage. Showcasing this set of slides titled Impact Of Covid 19 On Global Business Threats Landscape Ppt Summary Ideas PDF. The topics addressed in these templates are Percentage Impact, Key Insights, Business Professionals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
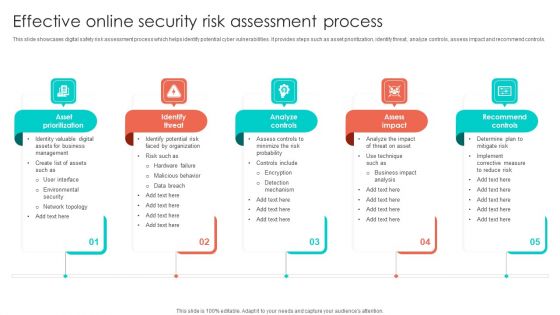
Effective Online Security Risk Assessment Process Inspiration PDF
This slide showcases digital safety risk assessment process which helps identify potential cyber vulnerabilities. It provides steps such as asset prioritization, identify threat, analyze controls, assess impact and recommend controls. Persuade your audience using this Effective Online Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Card Data Security, Cross Border Transactions, Payment Methods. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
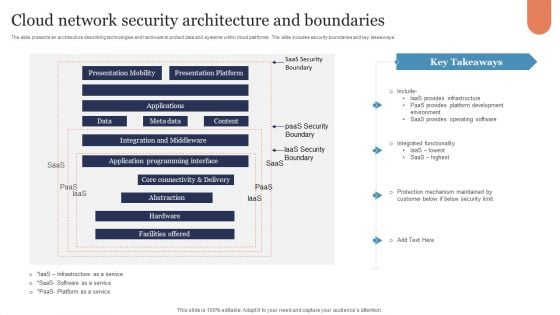
Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Automobile Insurance Coverage And Legal Requirements Guidelines PDF
This slide illustrates legal requirements and protection cover offered by automobile insurance companies. It includes liability coverage for bodily injury, liability coverage for property damage etc. Persuade your audience using this Automobile Insurance Coverage And Legal Requirements Guidelines PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Automobile Insurance, Coverage And Legal Requirements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. Explore a selection of the finest IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Improving Technology Based Cloud Recruitment Technology Overview Benefits And Stats Slides PDF
This slide showcases overview of cloud based recruitment technology which can guide HR professionals in streamlining hiring process. It also provides details about remote work, workflows, security, efficiency, e-recruitment, connectivity, operational costs, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Improving Technology Based Cloud Recruitment Technology Overview Benefits And Stats Slides PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
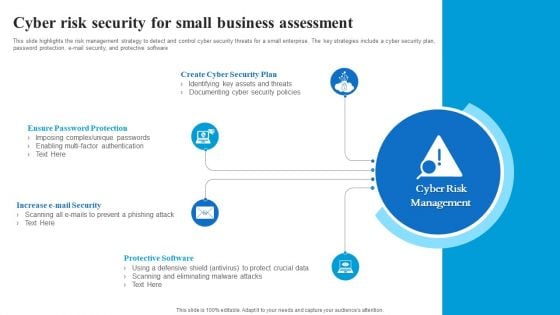
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Checklist Networking Cloud Computing Security IT Ppt Show Samples PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting cloud security checklist networking cloud computing security it ppt show samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, mechanisms, security, critical data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.
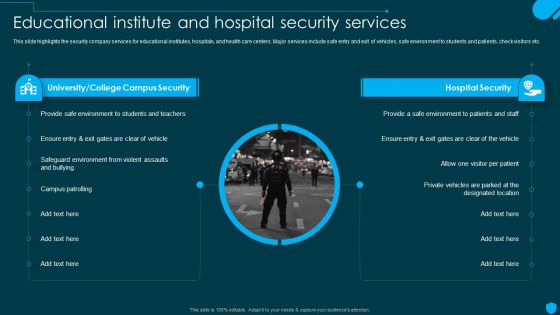
Security And Human Resource Services Business Profile Educational Institute And Hospital Structure PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. Find highly impressive Security And Human Resource Services Business Profile Educational Institute And Hospital Structure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security And Human Resource Services Business Profile Educational Institute And Hospital Structure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For IT Threats Response Playbook Slide Structure PDF
Presenting Table Of Contents For IT Threats Response Playbook Slide Structure PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Responsibilities Incident, Asset Protection, Risk Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
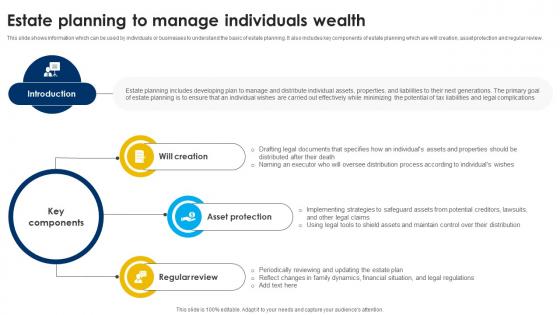
Estate Planning To Manage Individuals Wealth Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be used by individuals or businesses to understand the basic of estate planning. It also includes key components of estate planning which are will creation, asset protection and regular review. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Estate Planning To Manage Individuals Wealth Strategic Wealth Management And Financial Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Estate Planning To Manage Individuals Wealth Strategic Wealth Management And Financial Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by individuals or businesses to understand the basic of estate planning. It also includes key components of estate planning which are will creation, asset protection and regular review.
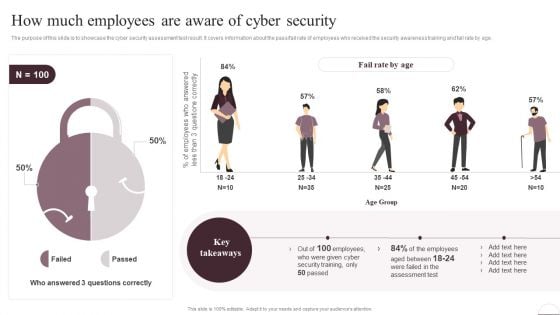
Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Working Of Ran And Core Networks Revolutionizing Mobile Networks Topics PDF
This slide represents the working of the Radio Access Network and core network. RAN is a visible part attached to towers and helps send and receive signals to and from phones, and it is the ultimate connection to the network. Create an editable Working Of Ran And Core Networks Revolutionizing Mobile Networks Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Of Ran And Core Networks Revolutionizing Mobile Networks Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the working of the Radio Access Network and core network. RAN is a visible part attached to towers and helps send and receive signals to and from phones, and it is the ultimate connection to the network.

Mobile Device Management Determining Roles And Responsibilities For Risk Handling Microsoft PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Mobile Device Management Determining Roles And Responsibilities For Risk Handling Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Integrating AML And Transaction Major Roles And Responsibilities Of Financial Sample PDF
The following slide Major roles and responsibilities of financial security department. It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Integrating AML And Transaction Major Roles And Responsibilities Of Financial Sample PDF from Slidegeeks and deliver a wonderful presentation.
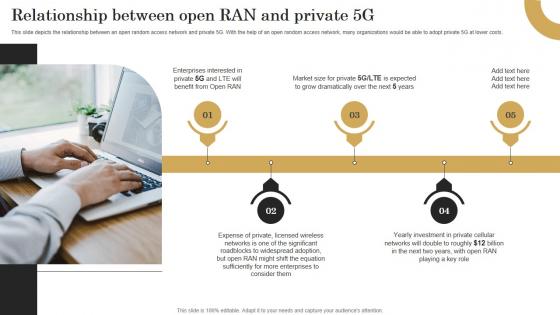
Relationship Between Open Ran And Private 5G Revolutionizing Mobile Networks Background PDF
This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs. This Relationship Between Open Ran And Private 5G Revolutionizing Mobile Networks Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Relationship Between Open Ran And Private 5G Revolutionizing Mobile Networks Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs.
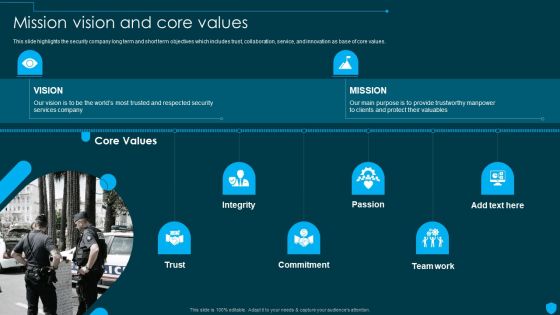
Security And Human Resource Services Business Profile Mission Vision And Core Values Pictures PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security And Human Resource Services Business Profile Mission Vision And Core Values Pictures PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security And Human Resource Services Business Profile Mission Vision And Core Values Pictures PDF.
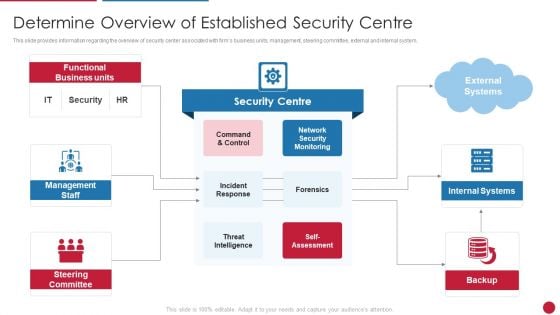
Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































