Data Protection
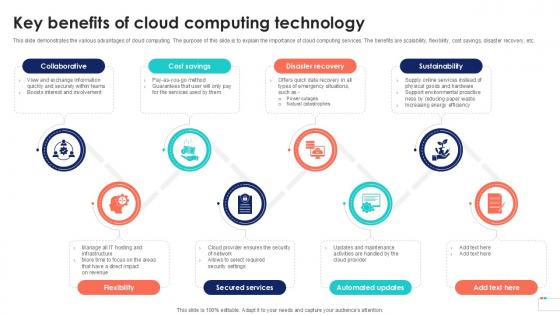
Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example. This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc.
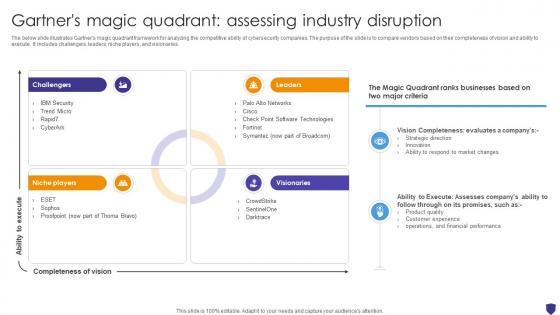
Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V
The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of cybersecurity companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries. Find highly impressive Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of cybersecurity companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries.
Stock Photo 3d Blue Folder With Lock For Data Security PowerPoint Slide
This power point image template has been crafted with graphic of 3d blue folder and lock. This image contains the concept of data security. Use this image PPT for your technology and security related presentations.
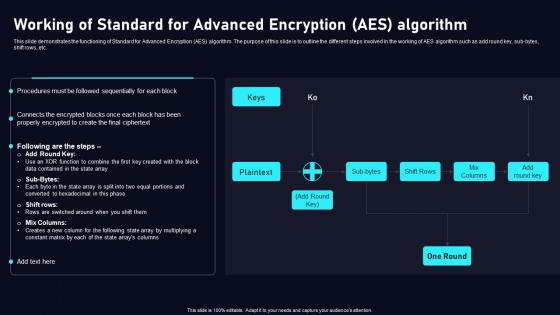
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.

About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. Create an editable About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
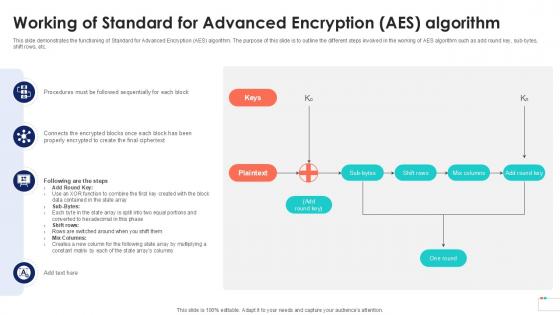
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.
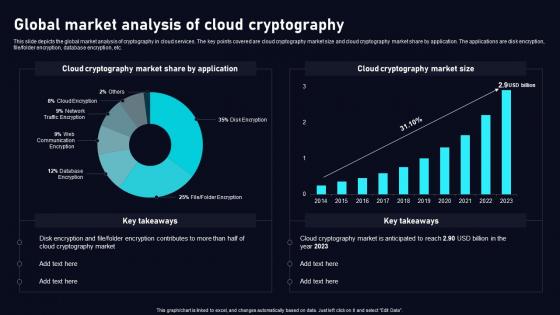
Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc. Do you know about Slidesgeeks Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers.

Information Analytics And Ml Strategy Playbook Requirement Of Data Management In BI Projects Template PDF
This slide covers the reasons for data management in an organization such as minimizing the data movement and attention to data security. This is a Information Analytics And Ml Strategy Playbook Requirement Of Data Management In BI Projects Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Use Existing Skills, Minimize Data Movement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
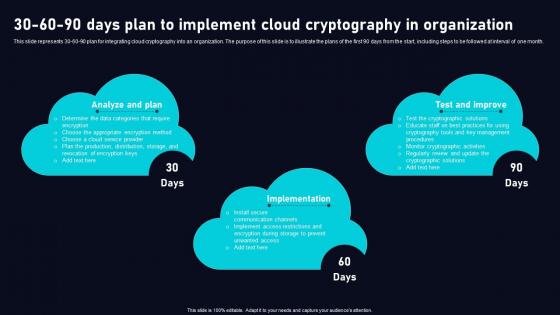
30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf
This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.

Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V
The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives.
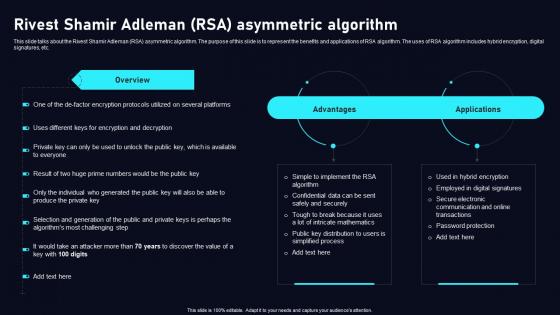
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
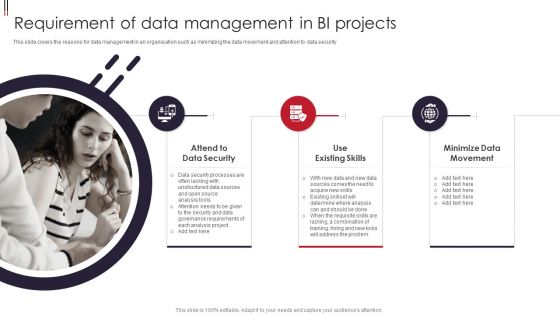
Information Visualizations Playbook Requirement Of Data Management In BI Projects Ideas PDF
This slide covers the reasons for data management in an organisation such as minimizing the data movement and attention to data security Presenting Information Visualizations Playbook Requirement Of Data Management In BI Projects Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Data Security, Use Existing Skills, Minimize Data Movement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
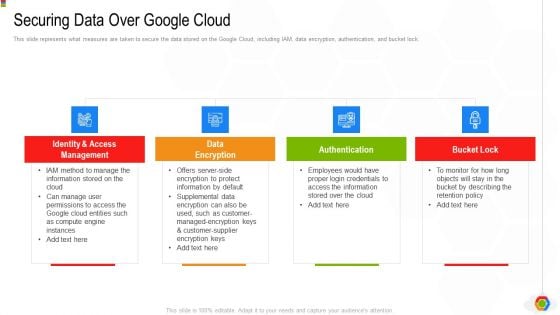
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
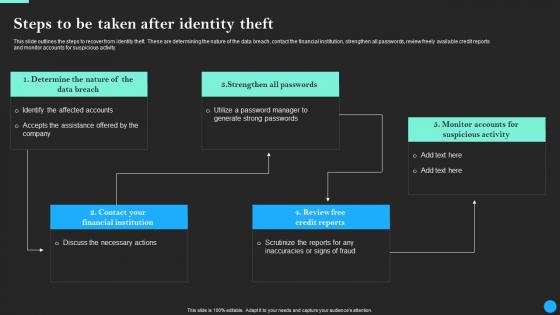
Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the steps to recover from identity theft. These are determining the nature of the data breach, contact the financial institution, strengthen all passwords, review freely available credit reports and monitor accounts for suspicious activity.

Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. Presenting Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Data Encryption, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
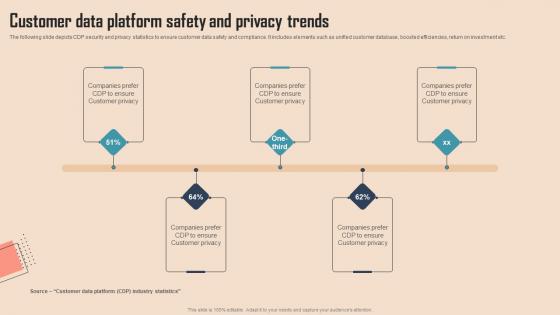
Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.
Data Quality Vector Showing Authentication Document Icon Ppt PowerPoint Presentation Gallery Tips PDF
Presenting data quality vector showing authentication document icon ppt powerpoint presentation gallery tips pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data quality vector showing authentication document icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

ETL Repository Why Do You Need Data Management Ppt PowerPoint Presentation Styles Slideshow PDF
This slide covers the reasons for data management in an organisation such as minimizing the data movement and attention to data security.Presenting ETL Repository Why Do You Need Data Management Ppt PowerPoint Presentation Styles Slideshow PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Minimize Data, Existing Skills, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Virtual Private Network Tunnel Layout Showing Encrypted Data Ppt PowerPoint Presentation File Summary PDF
Persuade your audience using this virtual private network tunnel layout showing encrypted data ppt powerpoint presentation file summary pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network tunnel layout showing encrypted data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virtual Private Network Services For Smart Phone Data Safety Ppt Icon Sample PDF
Persuade your audience using this virtual private network services for smart phone data safety ppt icon sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network services for smart phone data safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.

Laptop With Keys Data Security PowerPoint Templates And PowerPoint Themes 0912
Laptop With Keys Data Security PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with laptop with keys-Laptop with keys, security, success, technology, computer, business Revitalize your team with our Laptop With Keys Data Security PowerPoint Templates And PowerPoint Themes 0912. Download without worries with our money back guaranteee.
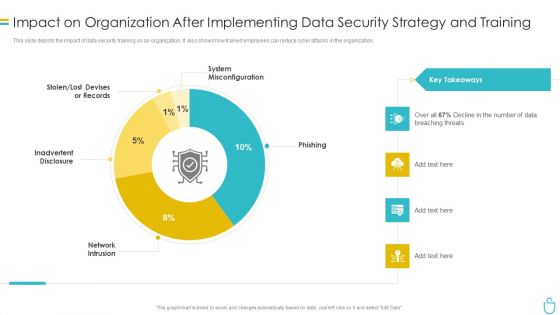
Information Security Impact On Organization After Implementing Data Security Strategy And Training Ppt Ideas Images PDF
This slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this information security impact on organization after implementing data security strategy and training ppt ideas images pdf. Use them to share invaluable insights on organization, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
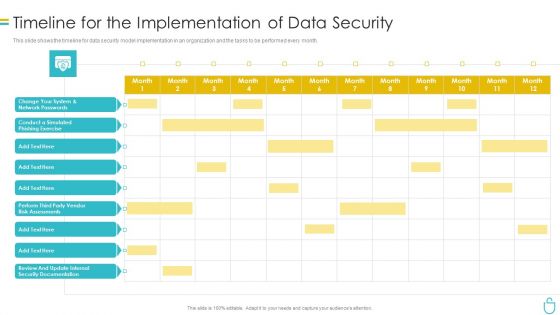
Information Security Timeline For The Implementation Of Data Security Ppt Gallery Topics PDF
This slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this information security timeline for the implementation of data security ppt gallery topics pdf. Use them to share invaluable insights on timeline for the implementation of data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information Security Compliance Dashboard Of Data Security Ppt Icon Vector PDF
This slide depicts the data security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative information security compliance dashboard of data security ppt icon vector pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
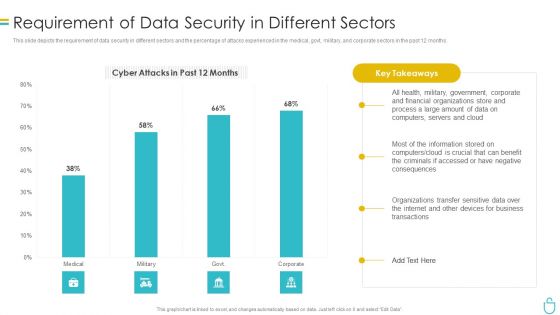
Information Security Requirement Of Data Security In Different Sectors Ppt File Infographic Template PDF
This slide depicts the requirement of data security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative information security requirement of data security in different sectors ppt file infographic template pdf bundle. Topics like process, financial, organizations, data, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Data Migration Vector For Virtual To Private Network Icon Ppt PowerPoint Presentation Portfolio Slides PDF
Pitch your topic with ease and precision using this data migration vector for virtual to private network icon ppt powerpoint presentation portfolio slides pdf. This layout presents information on vector for data migration process from database to folder. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Business Strategy Plan Template Open The Secured Data With Safety Concept Statement
Our business strategy plan template open the secured data with safety concept statement Powerpoint Templates Heighten Concentration. Your Audience Will Be On The Edge.
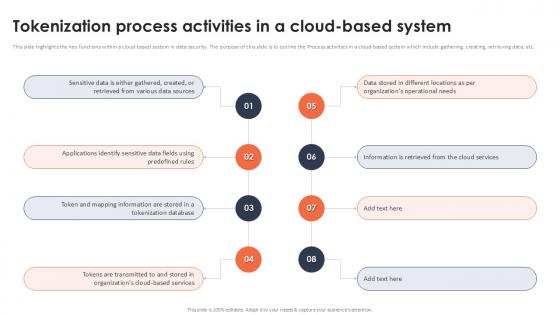
Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint
This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc.
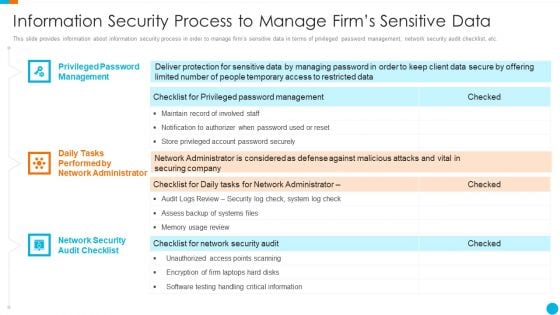
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Cloud Security Checklist Backup And Data Recovery Diagrams PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting Cloud Security Assessment Cloud Security Checklist Backup And Data Recovery Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Provider, Effective Plans, Natural Disasters In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
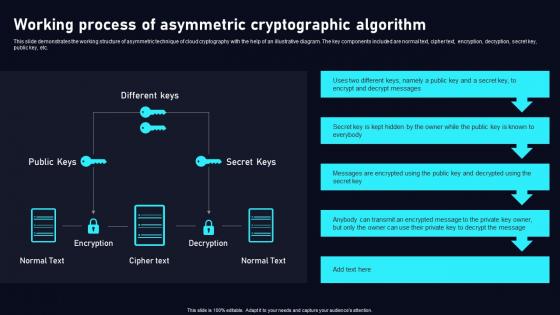
Working Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulateWorking Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
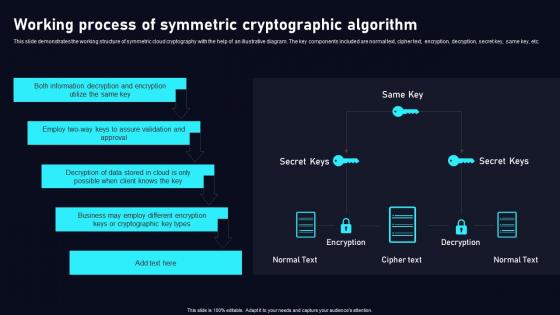
Working Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Want to ace your presentation in front of a live audience OurWorking Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.
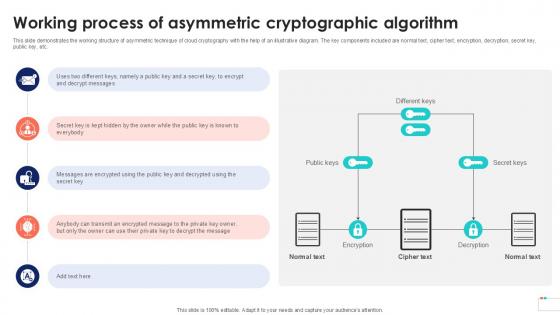
Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement.
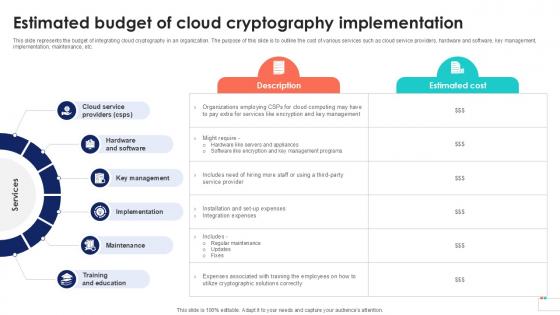
Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide from Slidegeeks and deliver a wonderful presentation. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
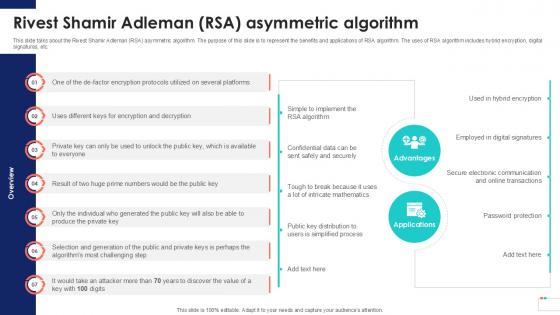
Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Want to ace your presentation in front of a live audience Our Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
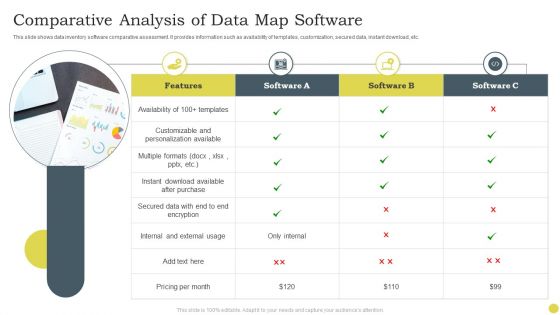
Comparative Analysis Of Data Map Software Ppt PowerPoint Presentation File Objects PDF
This slide shows data inventory software comparative assessment. It provides information such as availability of templates, customization, secured data, instant download, etc. Presenting Comparative Analysis Of Data Map Software Ppt PowerPoint Presentation File Objects PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Multiple Formats, Secured Data, External Usage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
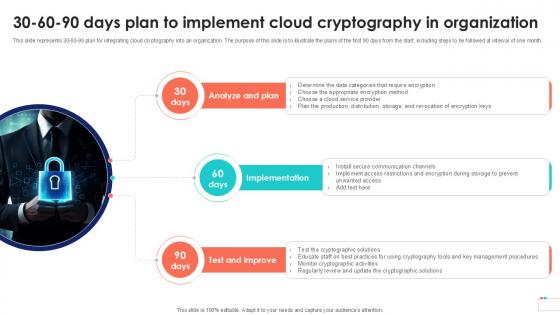
30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
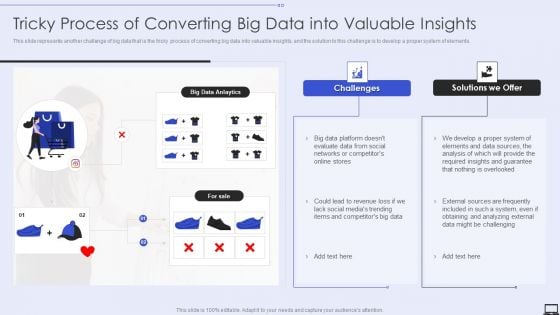
Tricky Process Of Converting Big Data Into Valuable Insights Ppt PowerPoint Presentation File Diagrams PDF
Deliver an awe inspiring pitch with this creative Tricky Process Of Converting Big Data Into Valuable Insights Ppt PowerPoint Presentation File Diagrams PDF bundle. Topics like Social Networks, Evaluate Data, Data Sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Stock Photo Server In Lifesaving Ring For Data Security PowerPoint Slide
This image has been crafted with computer servers in life saving ring. This professional image contains server with lifesaver depicting data security. Make a place in viewers heart with this amazing graphic image.
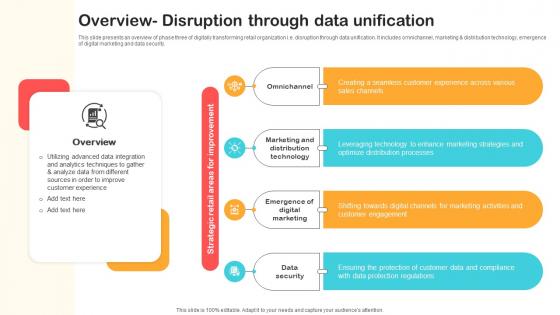
Overview Disruption Through Data Unification Optimizing Retail Operations With Digital DT SS V
This slide presents an overview of phase three of digitally transforming retail organization i.e. disruption through data unification. It includes omnichannel, marketing and distribution technology, emergence of digital marketing and data security.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Overview Disruption Through Data Unification Optimizing Retail Operations With Digital DT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide presents an overview of phase three of digitally transforming retail organization i.e. disruption through data unification. It includes omnichannel, marketing and distribution technology, emergence of digital marketing and data security.
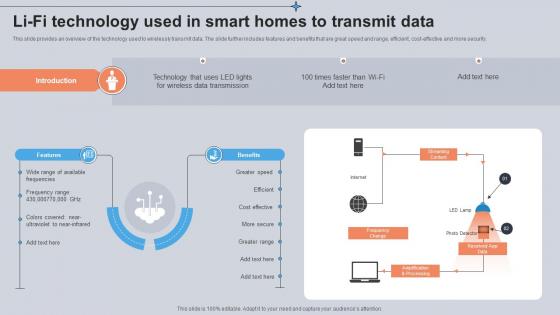
Li Fi Technology Used In Smart Homes To Transmit Data Utilizing Smart Appliances IoT SS V
This slide provides an overview of the technology used to wirelessly transmit data. The slide further includes features and benefits that are great speed and range, efficient, cost-effective and more security. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Li Fi Technology Used In Smart Homes To Transmit Data Utilizing Smart Appliances IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides an overview of the technology used to wirelessly transmit data. The slide further includes features and benefits that are great speed and range, efficient, cost-effective and more security.
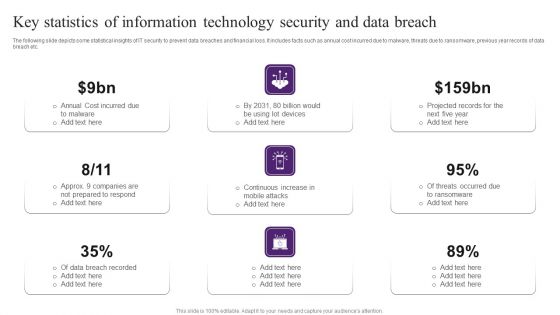
Key Statistics Of Information Technology Security And Data Breach Brochure PDF
The following slide depicts some statistical insights of IT security to prevent data breaches and financial loss. It includes facts such as annual cost incurred due to malware, threats due to ransomware, previous year records of data breach etc. Persuade your audience using this Key Statistics Of Information Technology Security And Data Breach Brochure PDF. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including Cost Incurred, Data Breach Recorded, Projected Records. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
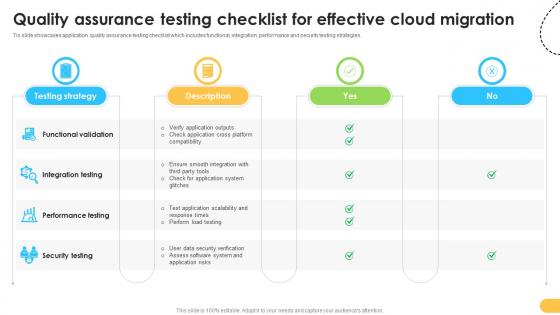
Quality Assurance Testing Checklist For Effective Data Migration From On Premises
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. The Quality Assurance Testing Checklist For Effective Data Migration From On Premises is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.

Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. If you are looking for a format to display your unique thoughts, then the professionally designed Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.
Circuit Sign For Data Safety And Security Vector Icon Ppt Pictures Brochure PDF
Presenting circuit sign for data safety and security vector icon ppt pictures brochure pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including circuit sign for data safety and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF
Presenting Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benefit Of Block Chain, Technology For Securing, Confidential Data Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface.

Woman Using VPN App For Data Safety Ppt PowerPoint Presentation File Objects PDF
Persuade your audience using this woman using vpn app for data safety ppt powerpoint presentation file objects pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including woman using vpn app for data safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
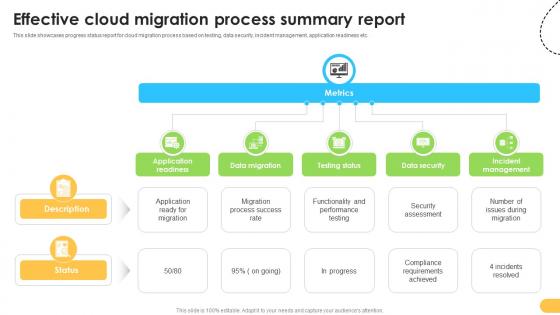
Effective Cloud Migration Process Summary Report Data Migration From On Premises
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Cloud Migration Process Summary Report Data Migration From On Premises and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc.
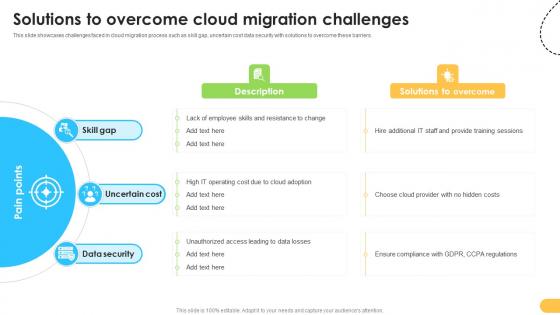
Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks has constructed Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers.

Prepare Data Backup For Sensitive Information IT Security IT Ppt Infographics Clipart PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative prepare data backup for sensitive information it security it ppt infographics clipart pdf bundle. Topics like manipulation, secure, disasters, cloud services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Shield With Lock Sigh For Data Security Vector Icon Ppt PowerPoint Presentation File Samples PDF
Presenting shield with lock sigh for data security vector icon ppt powerpoint presentation file samples pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including shield with lock sigh for data security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Ransomware Hacking And Data Loss Threat Ppt PowerPoint Presentation File Formats PDF
Persuade your audience using this internet security ransomware hacking and data loss threat ppt powerpoint presentation file formats pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including internet security ransomware hacking and data loss threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Data Folder Security Vector Icon Ppt PowerPoint Presentation File Rules PDF
Persuade your audience using this data folder security vector icon ppt powerpoint presentation file rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data folder security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
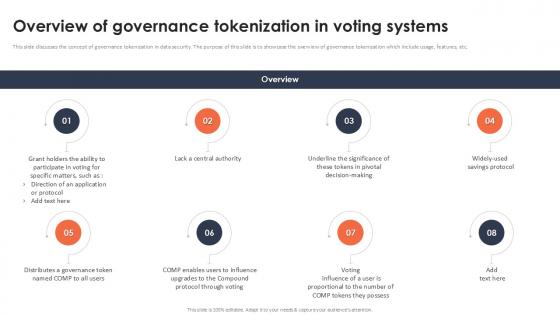
Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint
This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc. Presenting this PowerPoint presentation, titled Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc.


 Continue with Email
Continue with Email

 Home
Home


































