Data Protection

Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
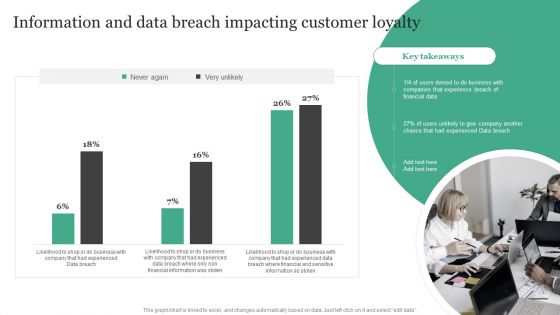
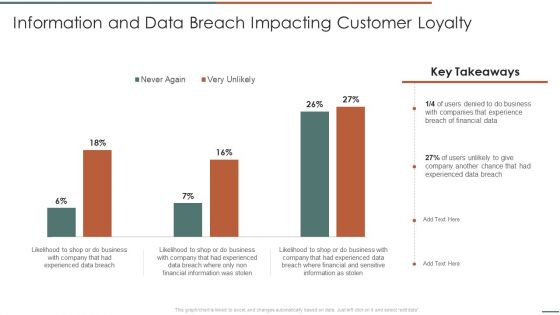
Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
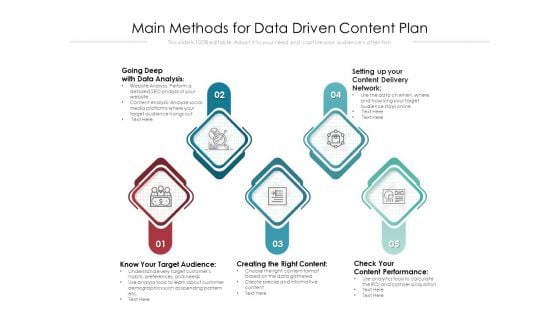
Main Methods For Data Driven Content Plan Ppt PowerPoint Presentation Professional Design Templates PDF
Presenting main methods for data driven content plan ppt powerpoint presentation professional design templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including going deep with data analysis, setting up your content delivery network, know your target audience, creating the right content, check your content performance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
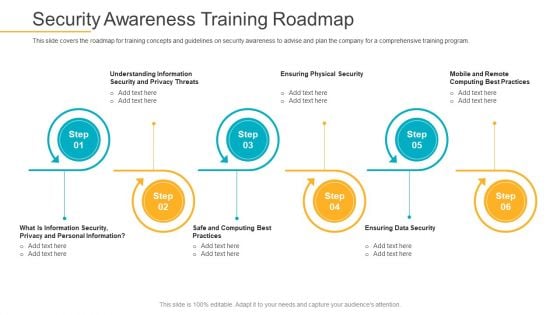
Data Breach Prevention Recognition Security Awareness Training Roadmap Ppt Gallery Graphics PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a data breach prevention recognition security awareness training roadmap ppt gallery graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threats, data security, information, awareness, roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
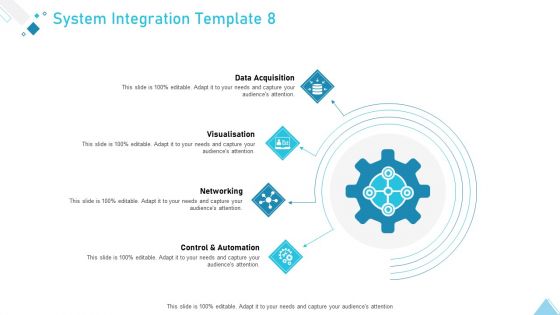
Business Strategy Planning Model System Integration Data Acquisition Ppt Gallery Microsoft PDF
This is a business strategy planning model system integration data acquisition ppt gallery microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data acquisition, visualisation, networking, control automation, system integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Put Right Gears For Data Security PowerPoint Templates Ppt Backgrounds For Slides 0713
Double your chances with our Put Right Gears For Data Security PowerPoint Templates PPT Backgrounds For Slides 0713. The value of your thoughts will increase two-fold. Charm the audience with your thoughts. Add our Technology PowerPoint Templates and they will be dotty for you. Double up our Gear wheels PowerPoint Templates with your thoughts. They will make an awesome pair. Make outstanding presentations with our Put Right Gears For Data Security PowerPoint Templates Ppt Backgrounds For Slides 0713. You'll always stay ahead of the game.
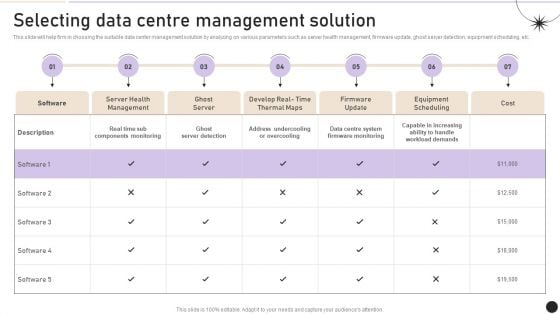
Selecting Data Centre Management Solution Workplace Security Management Program Information PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Selecting Data Centre Management Solution Workplace Security Management Program Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Enabling Data Security Risk Management Action Plan Ppt Slides Icon PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative enabling data security risk management action plan ppt slides icon pdf bundle. Topics like risk, security, information, measures, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives Key Security Controls To Be Addressed In The Program Summary PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative data safety initiatives key security controls to be addressed in the program summary pdf bundle. Topics like prevents attacks, limits extent of attacks, data recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Technology Guide For Serverless Computing Business Risk Related To Cloud Computing Data Portrait PDF
This is a technology guide for serverless computing business risk related to cloud computing data portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
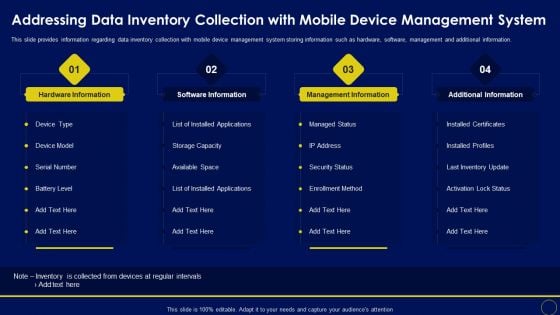
Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF
This slide provides information regarding data inventory collection with mobile device management system storing information such as hardware, software, management and additional information. Make sure to capture your audiences attention in your business displays with our gratis customizable Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
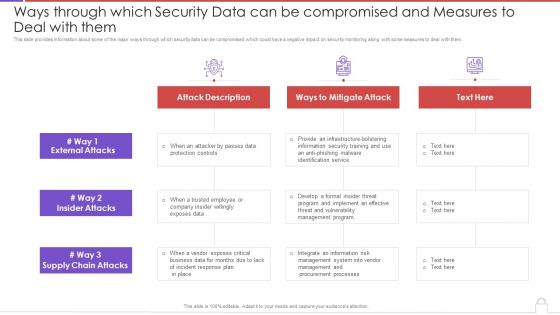
Ways Through Which Security Data Can Be Compromised And Measures To Deal With Them Professional PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative ways through which security data can be compromised and measures to deal with them professional pdf bundle. Topics like attack description, supply chain attacks, external attacks, insider attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For IT Data Services Certification Programs Rules PDF
Presenting Table Of Contents For IT Data Services Certification Programs Rules PDF to provide visual cues and insights. Share and navigate important information on fifteen stages that need your due attention. This template can be used to pitch topics like Certified Data Professional, Systems Security Professional, Cisco Certified Internetwork Expert. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Securities Trading Platform Data Flow Charts Ppt PowerPoint Presentation Gallery Icons PDF
This Slides displays a thorough data flow chartsthat graphically illustrates the operations of a securities trading platform, as well as the sources and recipients of the information. It includes five processes such as open account, verify transaction, deposit cash, withdraw cash and place order. Presenting Securities Trading Platform Data Flow Charts Ppt PowerPoint Presentation Gallery Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Account, Transaction, Consumer Service Assistant, Client. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
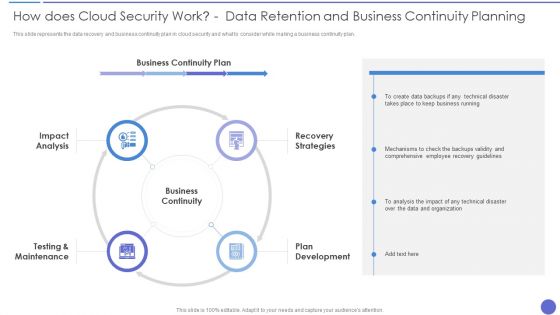
How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Presenting How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Continuity, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
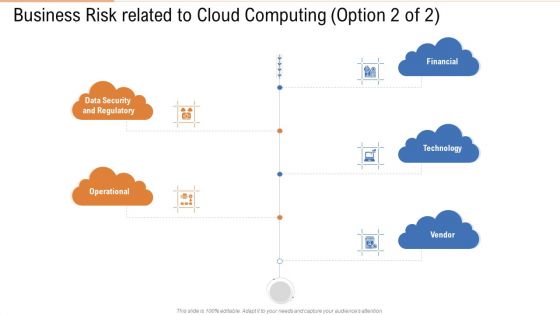
Business Risk Related To Cloud Computing Data Ppt Outline Slide Portrait PDF
This is a business risk related to cloud computing data ppt outline slide portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, technology, financial, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
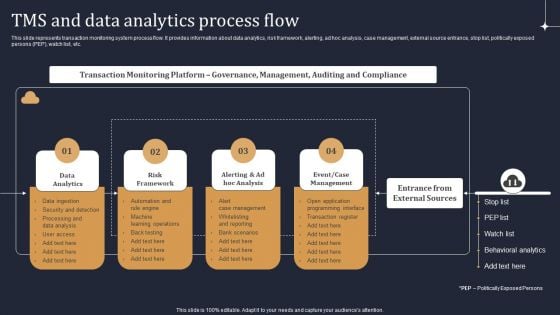
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
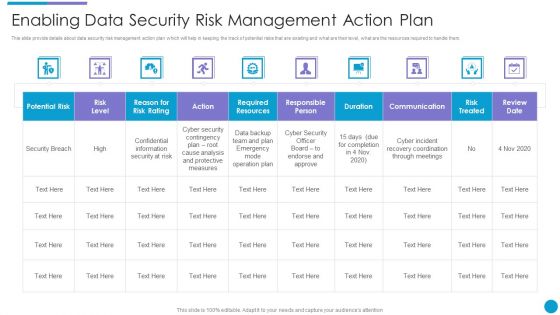
Major Techniques For Project Safety IT Enabling Data Security Risk Management Action Plan Template PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it enabling data security risk management action plan template pdf. Use them to share invaluable insights on communication, duration, risk treated, action, risk level and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
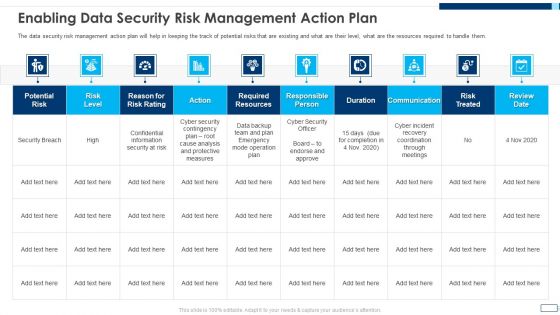
Evolving BI Infrastructure Enabling Data Security Risk Management Action Plan Background PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative evolving bi infrastructure enabling data security risk management action plan background pdf bundle. Topics like potential risk, risk level, action, duration, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
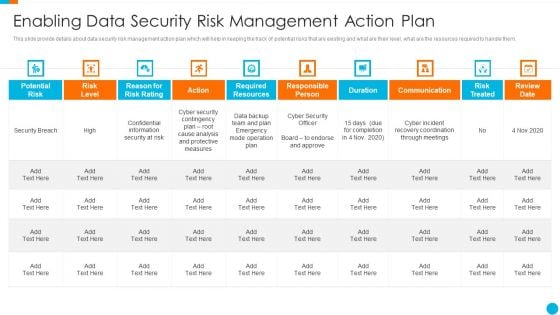
Upgrading Total Project Safety IT Enabling Data Security Risk Management Action Plan Template PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this upgrading total project safety it enabling data security risk management action plan template pdf. Use them to share invaluable insights on potential risk, risk level, reason for risk rating, action, required resources, communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
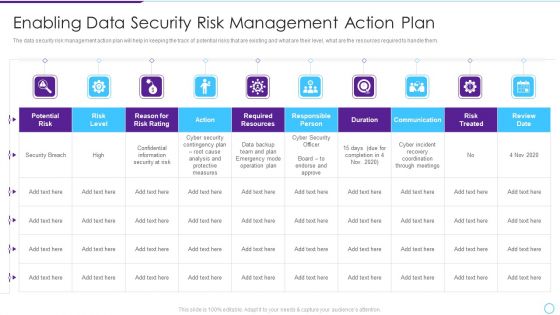
Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF bundle. Topics like Potential Risk, Risk Level, Action, Risk Treated, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
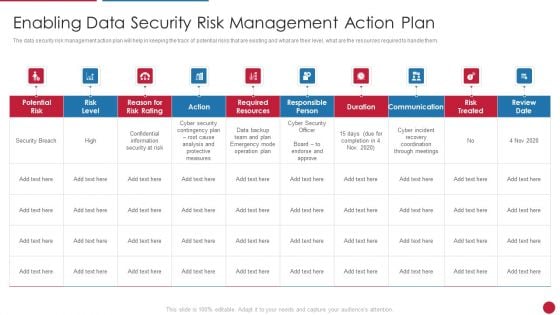
Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
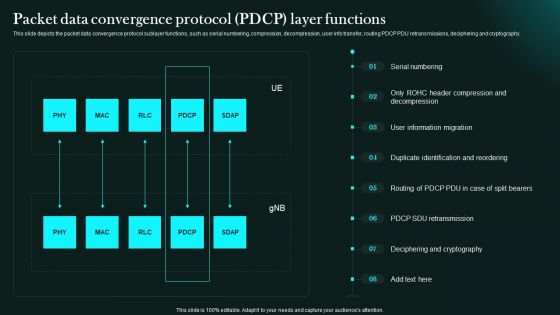
Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Functional Architecture Demonstration PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography.Explore a selection of the finest Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Functional Architecture Demonstration PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Functional Architecture Demonstration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF
The Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
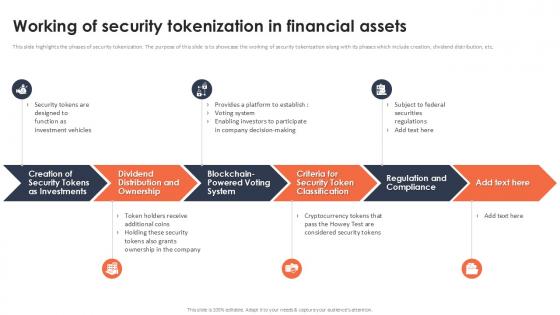
Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.
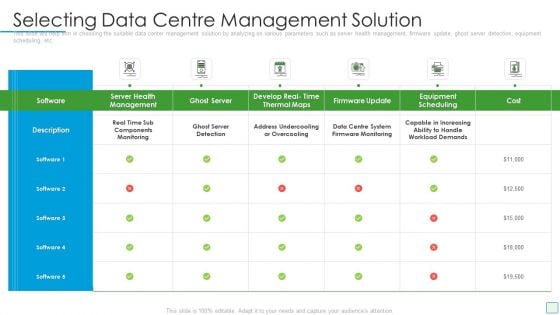
Developing Firm Security Strategy Plan Selecting Data Centre Management Solution Pictures PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan selecting data centre management solution pictures pdf. Use them to share invaluable insights on monitoring, management, develop, ghost server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals This Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals
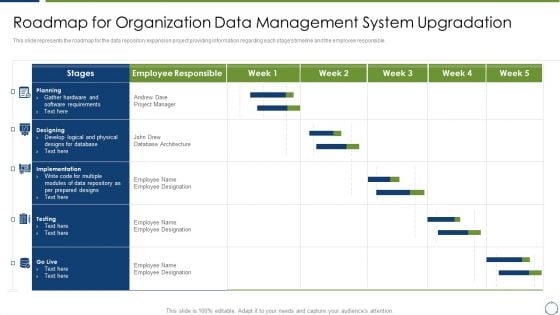
Horizontal Scaling Technique For Information Roadmap For Organization Data Management System Upgradation Rules PDF
This slide represents the roadmap for the data repository expansion project providing information regarding each stages timeline and the employee responsible. Deliver an awe inspiring pitch with this creative Horizontal Scaling Technique For Information Roadmap For Organization Data Management System Upgradation Rules PDF bundle. Topics like Requirement Analyst, Hardware Engineer, Information Security Engineer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
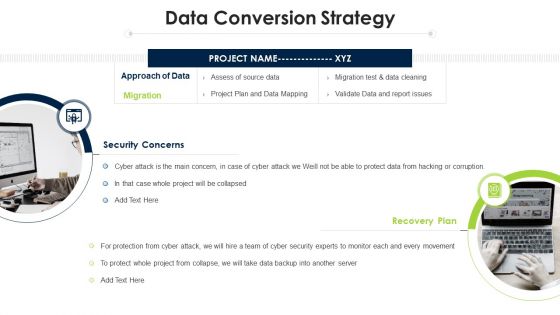
Program Evaluation Templates Bundle Data Conversion Strategy Ppt Portfolio Example Topics PDF
Presenting program evaluation templates bundle data conversion strategy ppt portfolio example topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like recovery plan, security concerns, approach of data, project. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
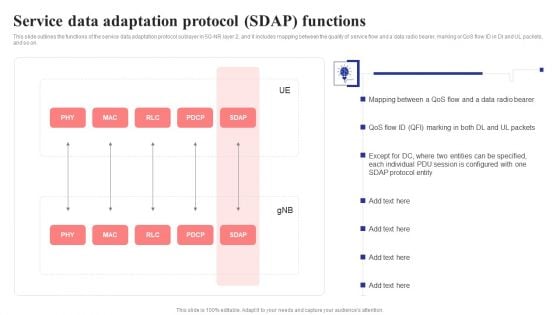
Service Data Adaptation Protocol Sdap Functions 5G Network Structure Mockup PDF
This slide outlines the functions of the service data adaptation protocol sublayer in 5G-NR layer 2, and it includes mapping between the quality of service flow and a data radio bearer, marking or QoS flow ID in Dl and UL packets, and so on.Slidegeeks has constructed Service Data Adaptation Protocol Sdap Functions 5G Network Structure Mockup PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
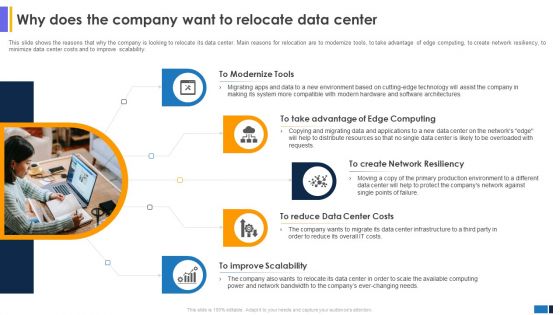
Why Does The Company Want To Data Center Migration For Information Brochure PDF
This slide shows the reasons that why the company is looking to relocate its data center. Main reasons for relocation are to modernize tools, to take advantage of edge computing, to create network resiliency, to minimize data center costs and to improve scalability. Explore a selection of the finest Why Does The Company Want To Data Center Migration For Information Brochure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Does The Company Want To Data Center Migration For Information Brochure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
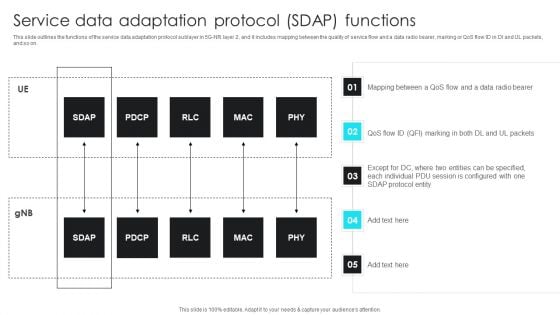
5G Network Operations Service Data Adaptation Protocol SDAP Functions Themes PDF
This slide outlines the functions of the service data adaptation protocol sublayer in 5G-NR layer 2, and it includes mapping between the quality of service flow and a data radio bearer, marking or QoS flow ID in Dl and UL packets, and so on. This 5G Network Operations Service Data Adaptation Protocol SDAP Functions Themes PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
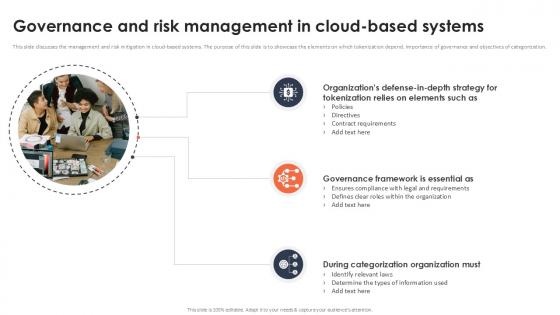
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.
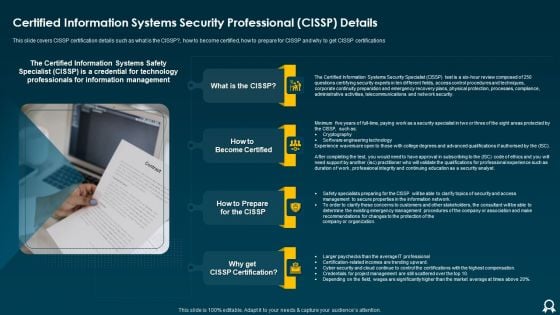
IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Software Engineering Technology, Network Security, Telecommunications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Services Best Practices Marketing Plan Agenda Determine Your Cloud Journey With Us Data Template PDF
Presenting cloud services best practices marketing plan agenda determine your cloud journey with us data template pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data center, cloud strategy, management, secure, modernize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
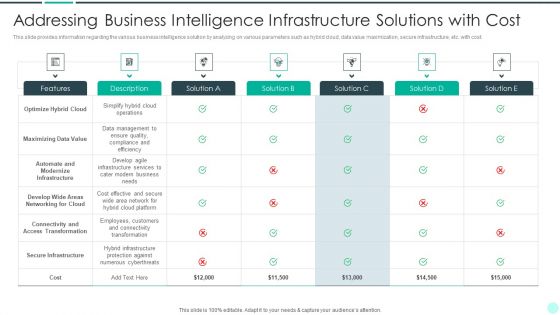
Executing Advance Data Analytics At Workspace Addressing Business Intelligence Formats PDF
This slide provides information regarding the various business intelligence solution by analyzing on various parameters such as hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace addressing business intelligence formats pdf. Use them to share invaluable insights on addressing business intelligence infrastructure solutions with cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
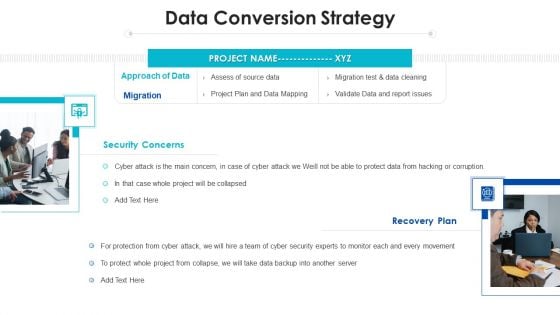
Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF
Presenting Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Approach Data, Recovery Plan, Cyber Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Threat Management At Workplace Addressing Internal And External Sources Of Threat Data Microsoft Pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing internal and external sources of threat data microsoft pdf. Use them to share invaluable insights on vendor security advisories, law enforcement and news media, commercial solutions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
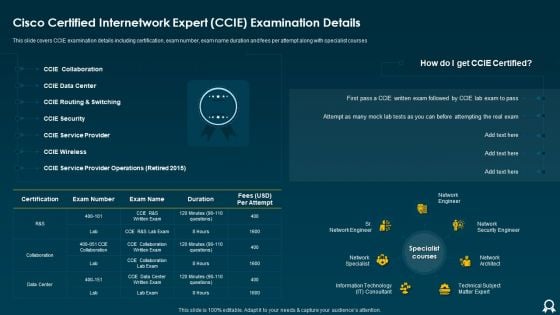
IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses. Deliver and pitch your topic in the best possible manner with this IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF. Use them to share invaluable insights on Data Center, Service Provider, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
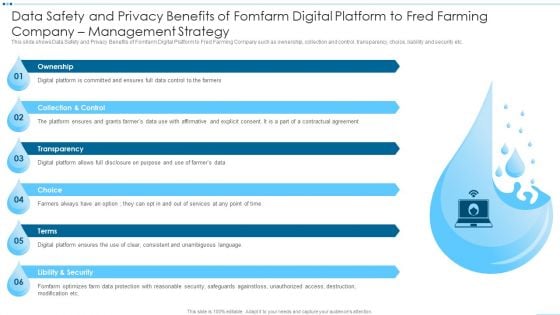
Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF
This slide shows Data Safety and Privacy Benefits of Fomfarm Digital Platform to Fred Farming Company such as ownership, collection and control, transparency, choice, liability and security etc. Deliver an awe inspiring pitch with this creative Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF bundle. Topics like Ownership, Collection And Control, Transparency, Choice can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
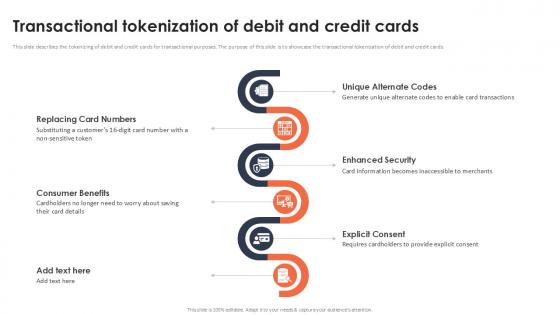
Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide
This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards.
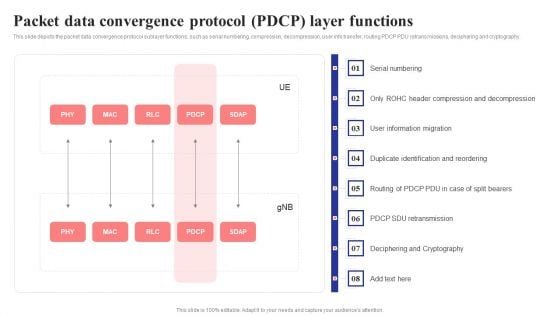
Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Structure Introduction PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography.Welcome to our selection of the Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Structure Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
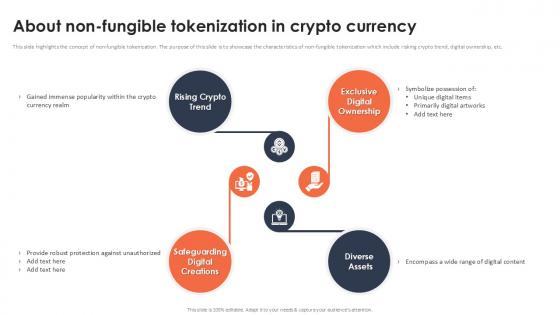
About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide
This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Boost your pitch with our creative About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc.

Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint
This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint from Slidegeeks and deliver a wonderful presentation. This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc.
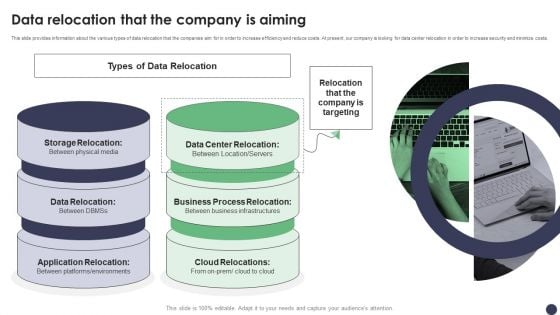
Data Relocation That The Company Is Aiming Ppt PowerPoint Presentation Diagram Lists PDF
This slide provides information about the various types of data relocation that the companies aim for in order to increase efficiency and reduce costs. At present, our company is looking for data center relocation in order to increase security and minimize costs. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Data Relocation That The Company Is Aiming Ppt PowerPoint Presentation Diagram Lists PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Data Relocation That The Company Is Aiming Ppt PowerPoint Presentation Diagram Lists PDF today and make your presentation stand out from the rest.
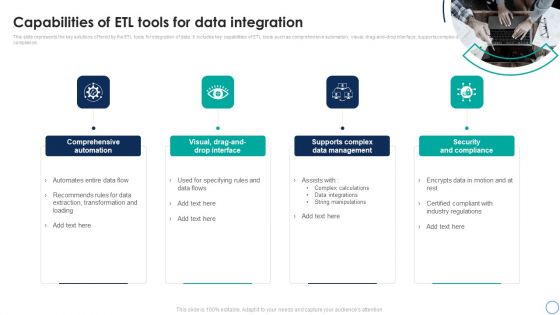
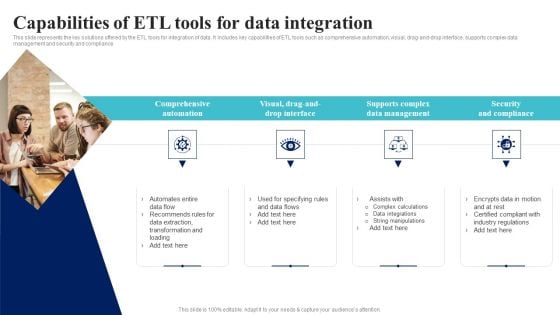
Business Analytics Application Capabilities Of ETL Tools For Data Integration Inspiration PDF
This slide represents the key solutions offered by the ETL tools for integration of data. It includes key capabilities of ETL tools such as comprehensive automation, visual, drag-and-drop interface, supports complex data management and security and compliance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Business Analytics Application Capabilities Of ETL Tools For Data Integration Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Business Analytics Application Capabilities Of ETL Tools For Data Integration Inspiration PDF today and make your presentation stand out from the rest.
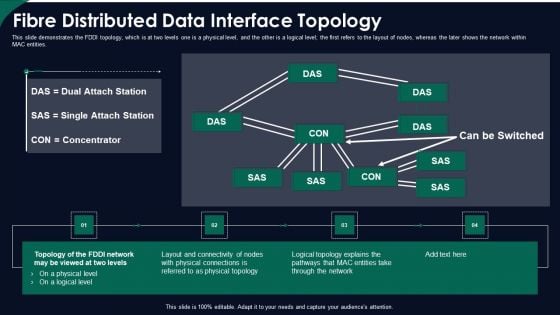
FDDI Network Standard IT Fibre Distributed Data Interface Topology Ppt Professional Graphics Design PDF
This slide demonstrates the FDDI topology, which is at two levels one is a physical level, and the other is a logical level the first refers to the layout of nodes, whereas the later shows the network within MAC entities. Deliver an awe inspiring pitch with this creative fddi network standard it fibre distributed data interface topology ppt professional graphics design pdf bundle. Topics like fibre distributed data interface topology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
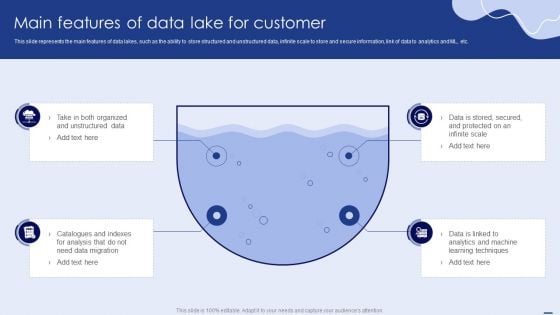
Main Features Of Data Lake For Customer Ppt PowerPoint Presentation Diagram PDF
This slide represents the main features of data lakes, such as the ability to store structured and unstructured data, infinite scale to store and secure information, link of data to analytics and ML, etc. Slidegeeks has constructed Main Features Of Data Lake For Customer Ppt PowerPoint Presentation Diagram PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
Deliver and pitch your topic in the best possible manner with this table of contents modern security observation plan to eradicate cybersecurity risk and data breach information pdf. Use them to share invaluable insights on essential elements of security, compromised and measures, performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. This modern and well-arranged Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
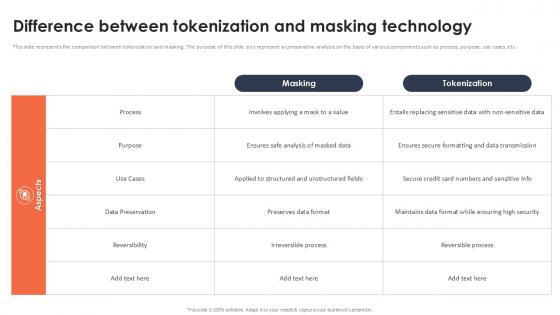
Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint
This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc.
BI Implementation To Enhance Hiring Process Capabi Lities Of Etl Tools For Data Integration Ideas PDF
This slide represents the key solutions offered by the ETL tools for integration of data. It includes key capabilities of ETL tools such as comprehensive automation, visual, drag-and-drop interface, supports complex data management and security and compliance.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than BI Implementation To Enhance Hiring Process Capabi Lities Of Etl Tools For Data Integration Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab BI Implementation To Enhance Hiring Process Capabi Lities Of Etl Tools For Data Integration Ideas PDF today and make your presentation stand out from the rest.

Current Information And Data Security Capabilities Of Firm Information Security Risk Administration Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating.Do you know about Slidesgeeks Current Information And Data Security Capabilities Of Firm Information Security Risk Administration Designs PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF
Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF bundle. Topics like Companies Experience, Financial Information, Breach Of Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
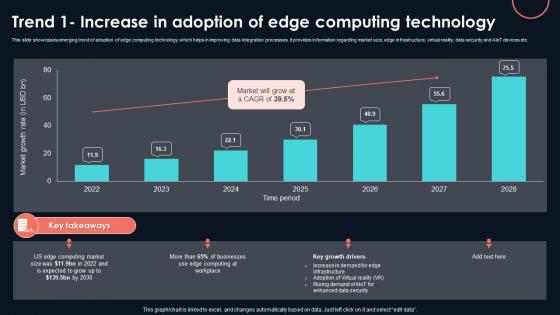
Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V. This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc.

Table Of Contents For Integrating Data Privacy System To Enhance Securitys Sample PDF
There are so many reasons you need a Table Of Contents For Integrating Data Privacy System To Enhance Securitys Sample PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
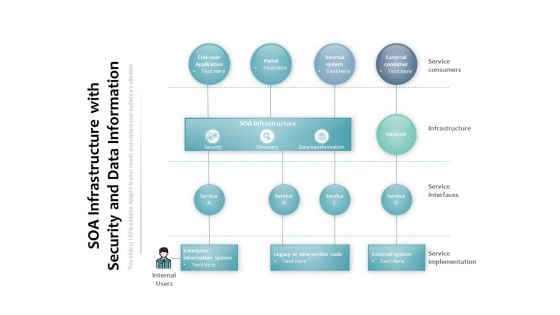
SOA Infrastructure With Security And Data Information Ppt PowerPoint Presentation Pictures Images
Presenting this set of slides with name soa infrastructure with security and data information ppt powerpoint presentation pictures images. The topics discussed in these slides are soa infrastructure, enterprise information system, external consumer, service consumers, infrastructure, service interfaces, service implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF. Use them to share invaluable insights on Facilities And Equipment, Software Application, At Personnel Level, Monetary Loss, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































