Data Protection
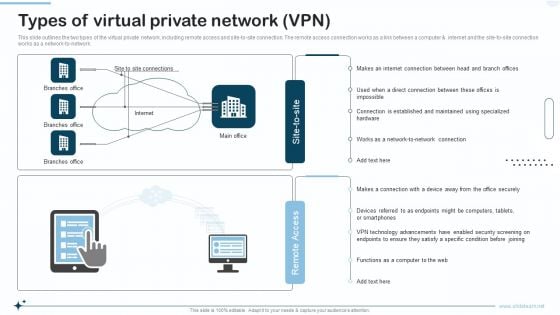
Naas Integrated Solution IT Types Of Virtual Private Network VPN Guidelines PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site to site connection works as a network to network. Deliver an awe inspiring pitch with this creative Naas Integrated Solution IT Types Of Virtual Private Network VPN Guidelines PDF bundle. Topics like Technology Advancements, Virtual Private Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
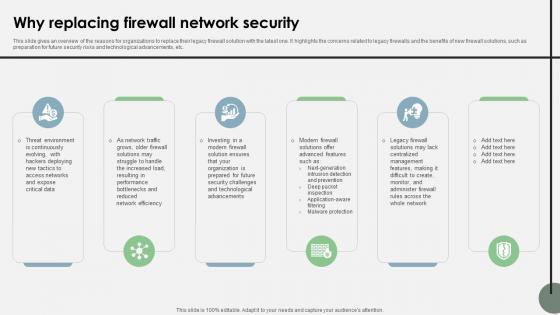
Why Replacing Firewall Network Security Cloud Security Firewall Proposal
This slide gives an overview of the reasons for organizations to replace their legacy firewall solution with the latest one. It highlights the concerns related to legacy firewalls and the benefits of new firewall solutions, such as preparation for future security risks and technological advancements, etc.Stand out from the crowd with our dynamic Why Replacing Firewall Network Security Cloud Security Firewall Proposal template. Designed to help you make a statement, this single-slide PPT template is fully customizable to suit your unique needs. With eye-catching visuals and seamless editing options, you can create impactful presentations in minutes. Say goodbye to boring slides and unlock your presentation potential with our top-notch template. This slide gives an overview of the reasons for organizations to replace their legacy firewall solution with the latest one. It highlights the concerns related to legacy firewalls and the benefits of new firewall solutions, such as preparation for future security risks and technological advancements, etc.
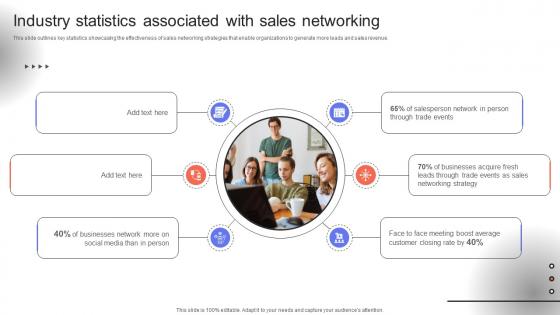
Trade Event Tactics To Boost Industry Statistics Associated With Sales Networking SA SS V
This slide outlines key statistics showcasing the effectiveness of sales networking strategies that enable organizations to generate more leads and sales revenue. Retrieve professionally designed Trade Event Tactics To Boost Industry Statistics Associated With Sales Networking SA SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines key statistics showcasing the effectiveness of sales networking strategies that enable organizations to generate more leads and sales revenue.
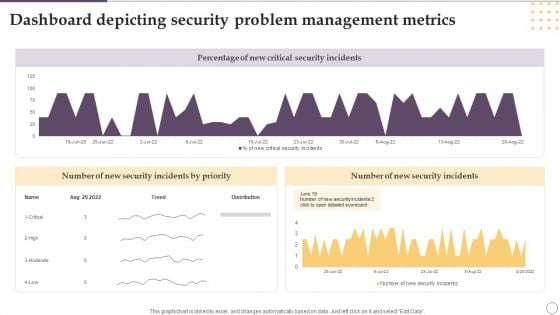
Dashboard Depicting Security Problem Management Metrics Ppt Gallery Designs PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Showcasing this set of slides titled Dashboard Depicting Security Problem Management Metrics Ppt Gallery Designs PDF. The topics addressed in these templates are Percentage, New Critical, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
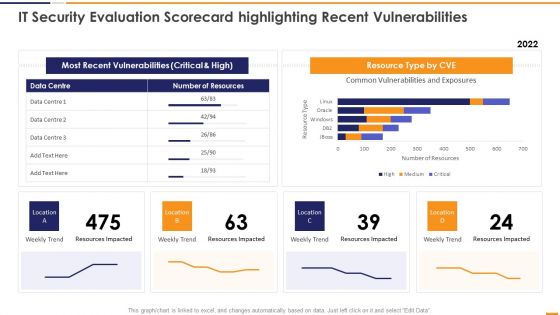
IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Importance Of 5G Network Security Policies Portrait Pdf
This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc. Showcasing this set of slides titled Importance Of 5G Network Security Policies Portrait Pdf. The topics addressed in these templates are Access Network Security, Core Network Security, Security Enablers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc.

Anti Virus Computer PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with modern mouse connected to word Anti-Virus Get an exceptional response with our Anti Virus Computer PowerPoint Templates And PowerPoint Backgrounds 0211. Your ideas will be applauded by one and all.

Anti Virus Computer PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with modern mouse connected to word Anti-Virus Award yourself with our Anti Virus Computer PowerPoint Themes And PowerPoint Slides 0211. Your thoughts deserve the distinction.
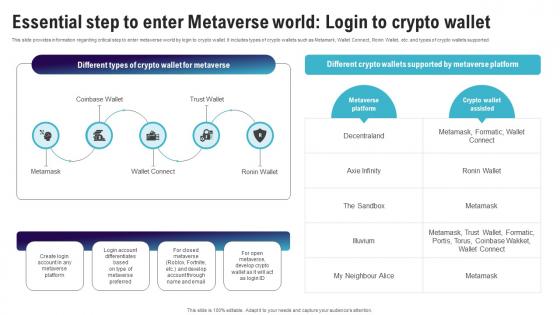
Essential Step To Enter Metaverse World Login Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding critical step to enter metaverse world by login to crypto wallet. It includes types of crypto wallets such as Metamark, Wallet Connect, Ronin Wallet, etc. and types of crypto wallets supported. Do you know about Slidesgeeks Essential Step To Enter Metaverse World Login Continuum Of Technology Revamping Business AI SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide provides information regarding critical step to enter metaverse world by login to crypto wallet. It includes types of crypto wallets such as Metamark, Wallet Connect, Ronin Wallet, etc. and types of crypto wallets supported.
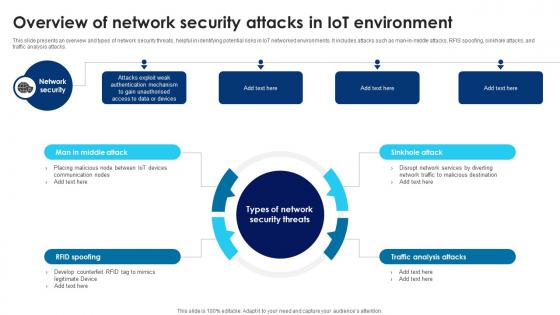
Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. There are so many reasons you need a Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks.
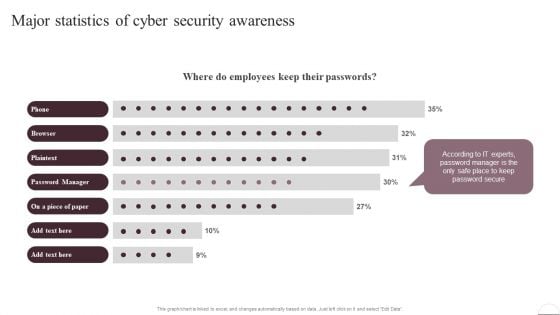
Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. There are so many reasons you need a Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
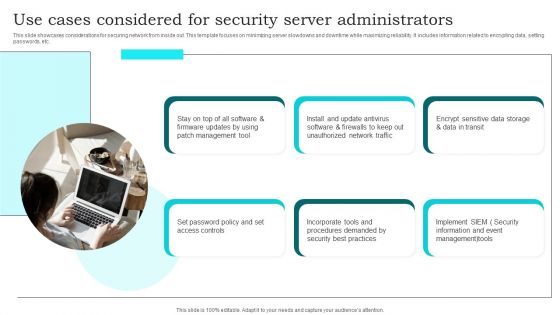
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Spyware Computer Virus Definition In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Computer Virus Definition In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Computer Virus Definition. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Spyware Computer Virus Definition In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
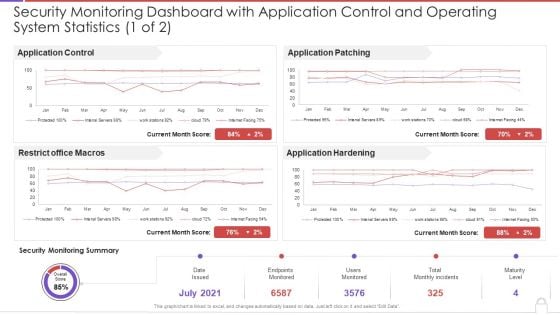
Security Monitoring Dashboard With Application Control And Operating System Statistics Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this security monitoring dashboard with application control and operating system statistics template pdf. Use them to share invaluable insights on application control, restrict office macros, application patching, application hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
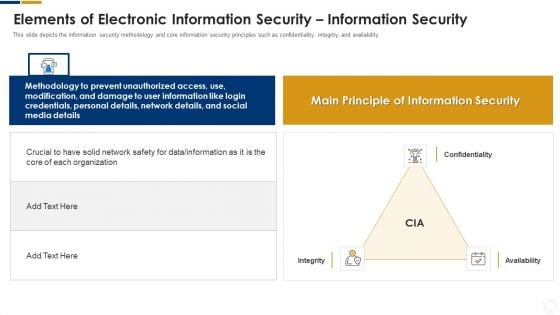
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
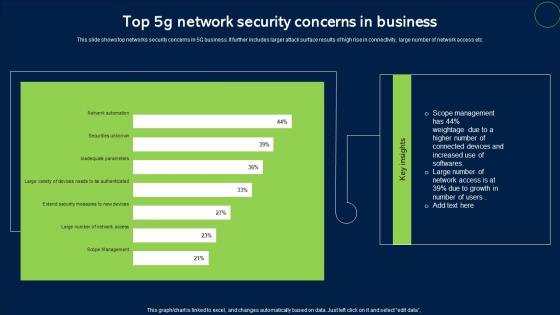
Top 5G Network Security Concerns In Business Sample Pdf
This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc. Pitch your topic with ease and precision using this Top 5G Network Security Concerns In Business Sample Pdf. This layout presents information on Network Security, Concerns In Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc.
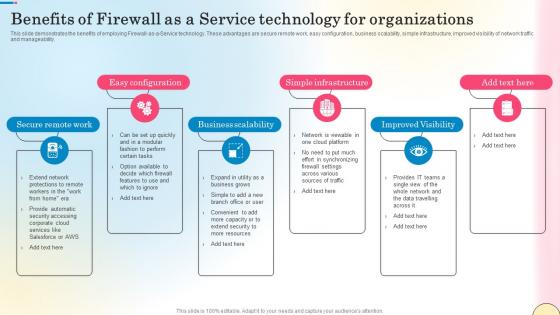
Benefits Of Firewall As A Service Technology For Network Security Inspiration Pdf
This slide demonstrates the benefits of employing Firewall-as-a-Service technology. These advantages are secure remote work, easy configuration, business scalability, simple infrastructure, improved visibility of network traffic and manageability. There are so many reasons you need a Benefits Of Firewall As A Service Technology For Network Security Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the benefits of employing Firewall-as-a-Service technology. These advantages are secure remote work, easy configuration, business scalability, simple infrastructure, improved visibility of network traffic and manageability.
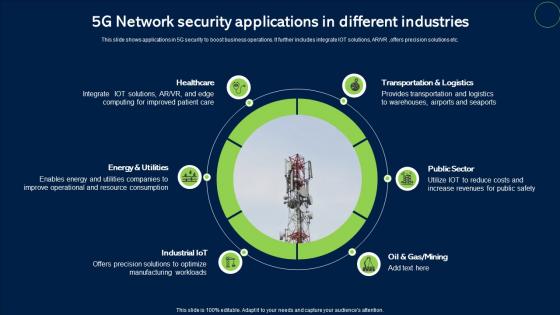
5G Network Security Applications In Different Industries Infographics Pdf
This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc. Showcasing this set of slides titled 5G Network Security Applications In Different Industries Infographics Pdf. The topics addressed in these templates are Healthcare, Public Sector, Transportation And Logistics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc.
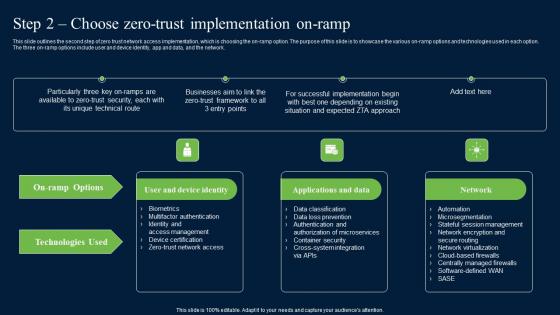
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
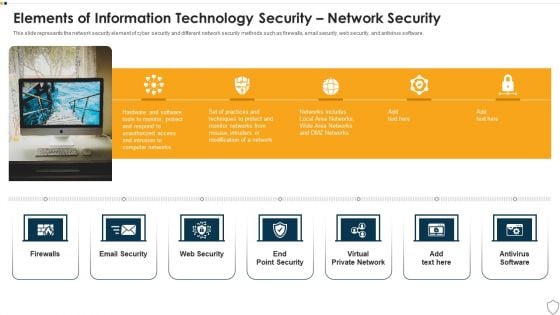
IT Security Elements Of Information Technology Security Network Security Ppt Pictures Graphics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting it security elements of information technology security network security ppt pictures graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like web security, end point security, virtual private network, email security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
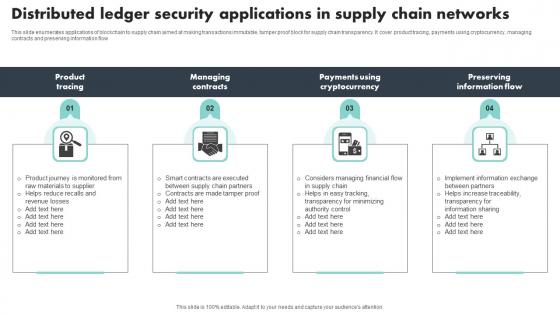
Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf
This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow Pitch your topic with ease and precision using this Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf This layout presents information on Product Tracing, Managing Contracts, Preserving Information Flow It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow
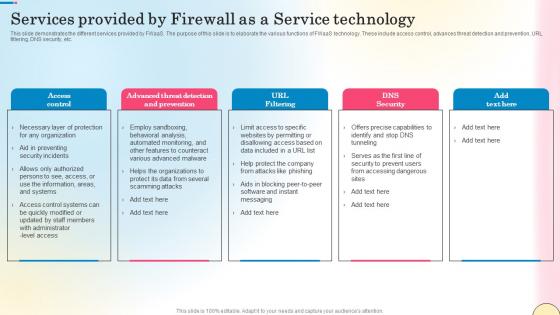
Services Provided By Firewall As A Service Technology Network Security Infographics Pdf
This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc. There are so many reasons you need a Services Provided By Firewall As A Service Technology Network Security Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc.
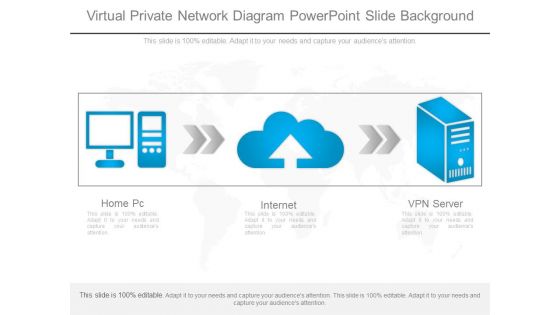
Virtual Private Network Diagram Powerpoint Slide Background
This is a virtual private network diagram powerpoint slide background. This is a three stage process. The stages in this process are home pc, internet, vpn server.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway. This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment.
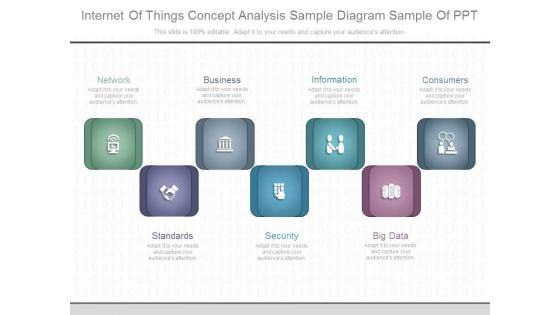
Internet Of Things Concept Analysis Sample Diagram Sample Of Ppt
This is a internet of things concept analysis sample diagram sample of ppt. This is a seven stage process. The stages in this process are network, business, information, consumers, standards, security, big data.
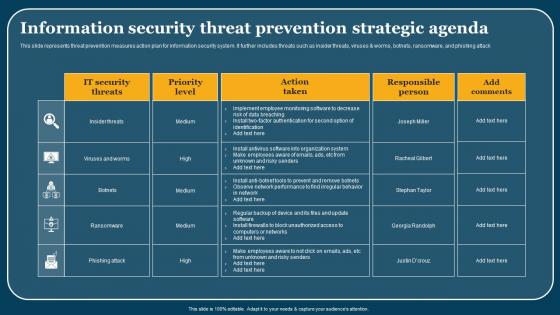
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
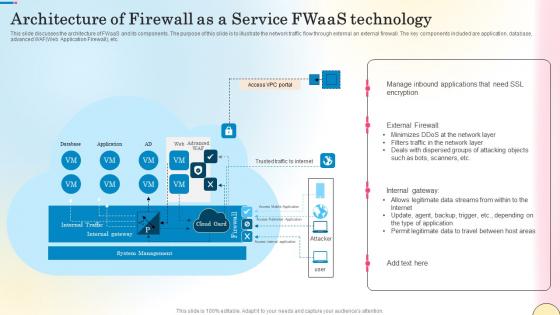
Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf
This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Want to ace your presentation in front of a live audience Our Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc.
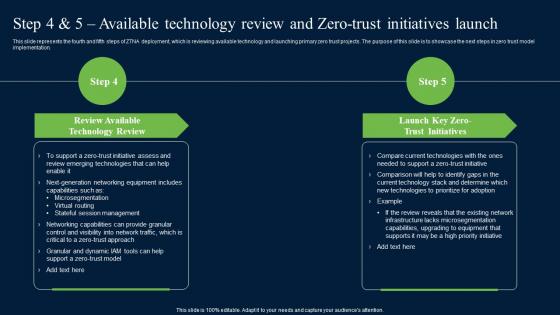
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
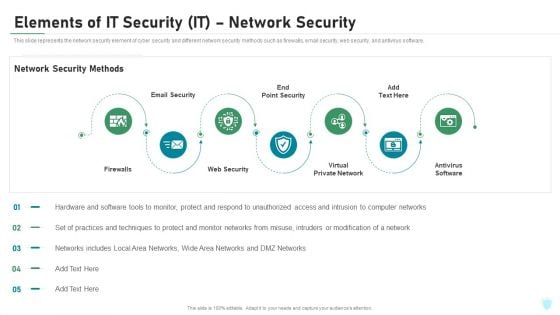
Elements Of IT Security IT Network Security Ppt Pictures Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a elements of it security it network security ppt pictures ideas pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like firewalls, email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Model Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Model Zero Trust Network Access System Use Cases that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Zero Trust Network Access System Use Cases from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
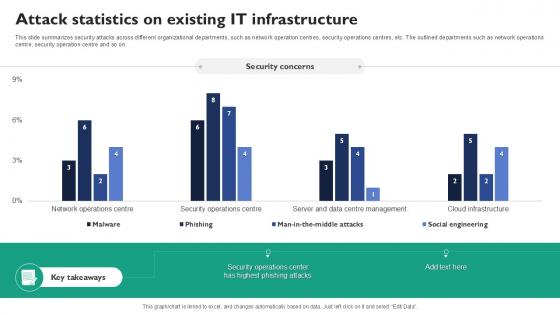
Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
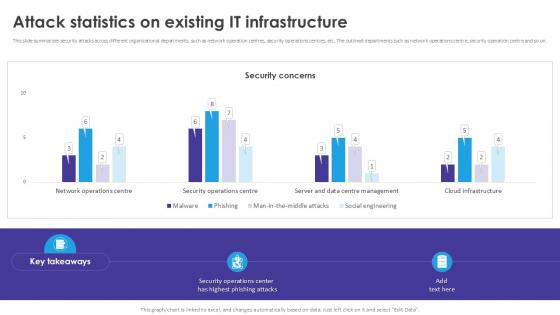
Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
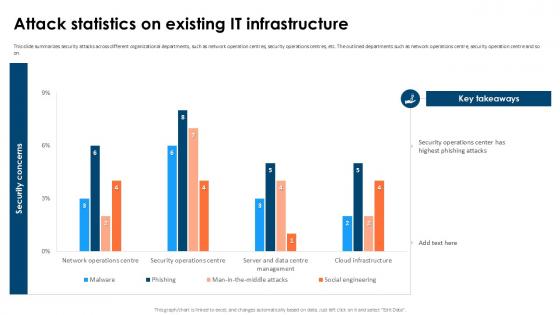
Attack Statistics On Partial Regression Testing For A Best PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Partial Regression Testing For A Best PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.

Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fiveteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now. Our Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
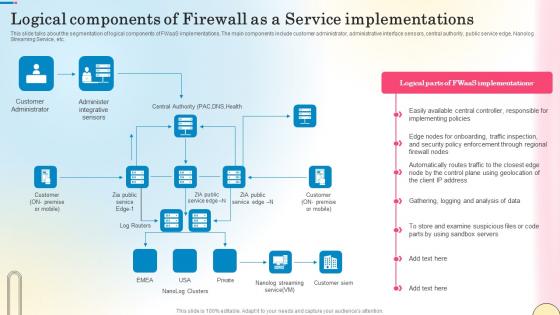
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.
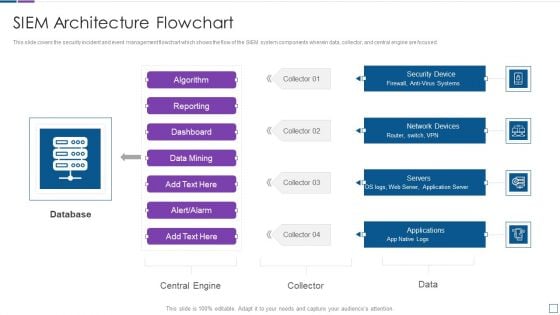
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Slidegeeks is here to make your presentations a breeze with Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
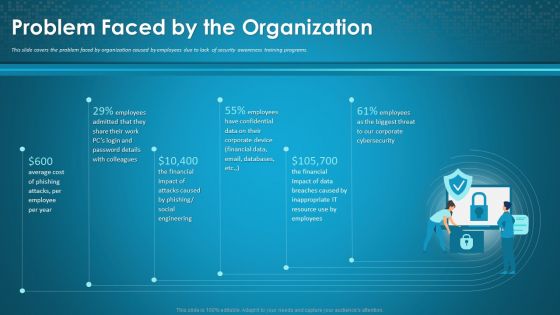
Organizational Network Staff Learning Problem Faced By The Organization Topics PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a organizational network staff learning problem faced by the organization topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, financial data, resource use by employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Application Security Testing Ppt Powerpoint Designs
The Table Of Contents For Application Security Testing Ppt Powerpoint Designs is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Our Table Of Contents For Application Security Testing Ppt Powerpoint Designs are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
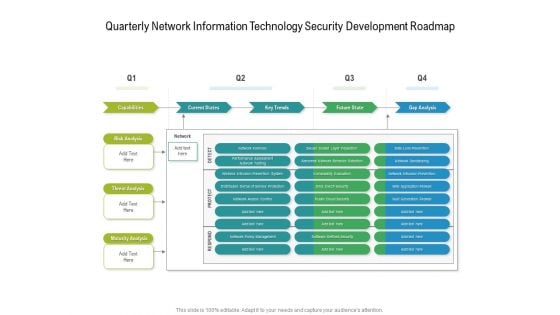
Quarterly Network Information Technology Security Development Roadmap Diagrams
Presenting our jaw dropping quarterly network information technology security development roadmap diagrams. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
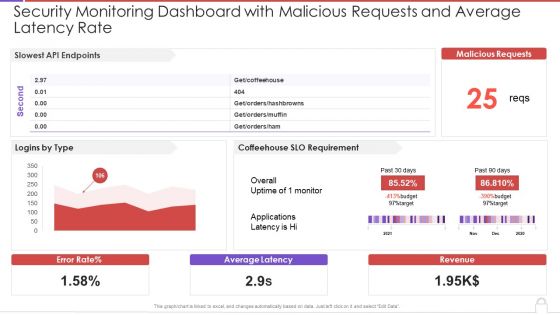
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Topics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate topics pdf bundle. Topics like slowest api endpoints, malicious requests, coffeehouse slo can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
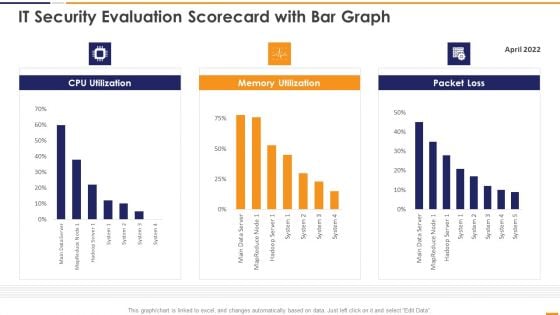
IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF. Use them to share invaluable insights on CPU Utilization Memory, Utilization Packet Loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
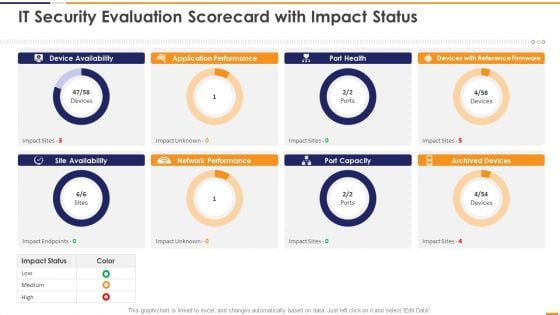
IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF. Use them to share invaluable insights on Device Availability Application, Performance Port Health, Devices Reference Firmware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
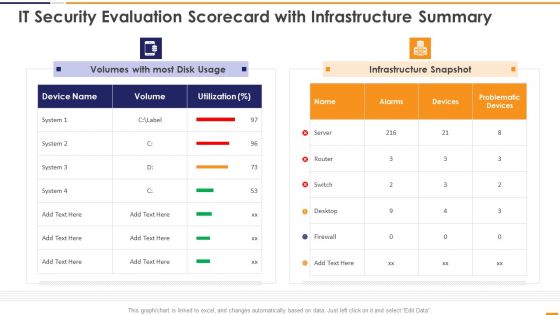
IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF bundle. Topics like Volumes Most Disk, Usage Infrastructure Snapshot can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
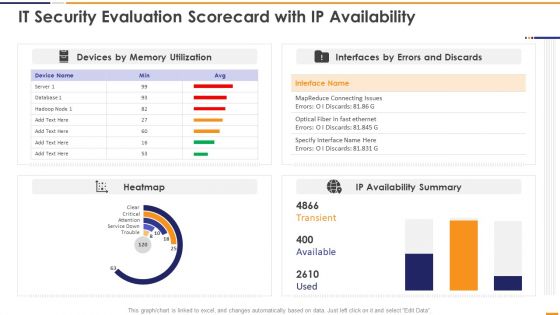
IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
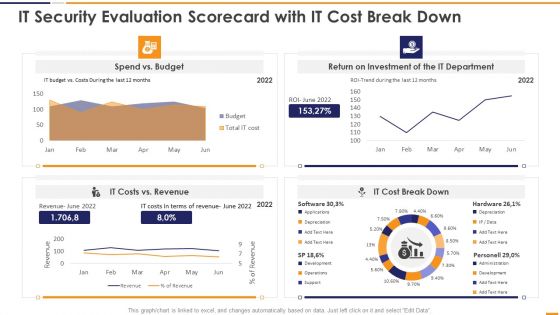
IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF bundle. Topics like Spend Vs Budget, Return On Investment, IT Department Revenue, IT Costs Vs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
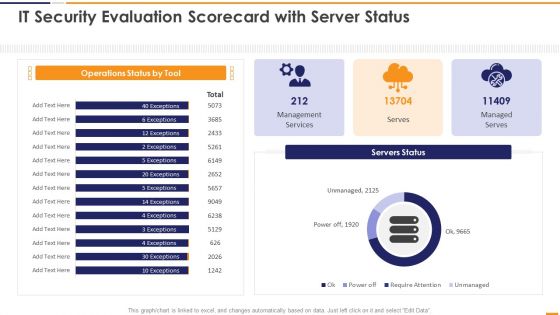
IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
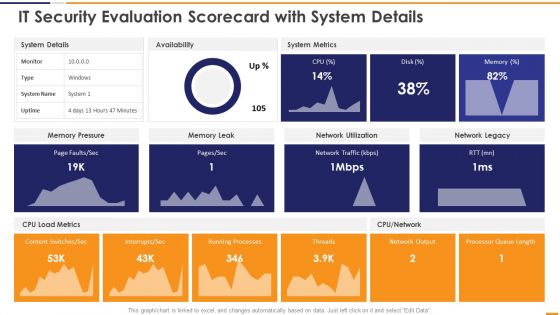
IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF. Use them to share invaluable insights on System Details Availability, System Metrics Memory, Pressure Memory Leak and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
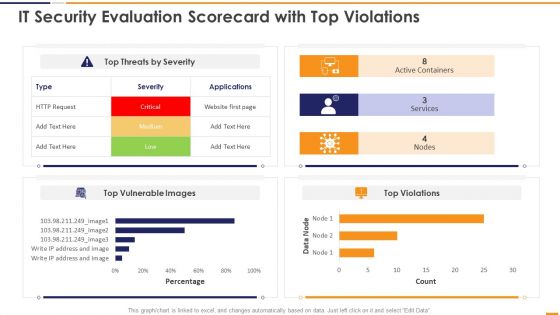
IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
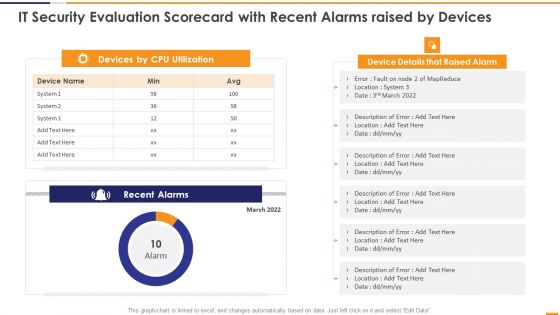
IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF bundle. Topics like Devices CPU Utilization, Device Details Raised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF. Use them to share invaluable insights on Response Time 2022, Disk Utilization Availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF bundle. Topics like IT Support Employee, Per Thousand End, user Over Time, Uptime And Downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Best Vpn Traveling Abroad In Powerpoint And Google Slides Cpb
Introducing our well-designed Best Vpn Traveling Abroad In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Vpn Traveling Abroad. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Best Vpn Traveling Abroad In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
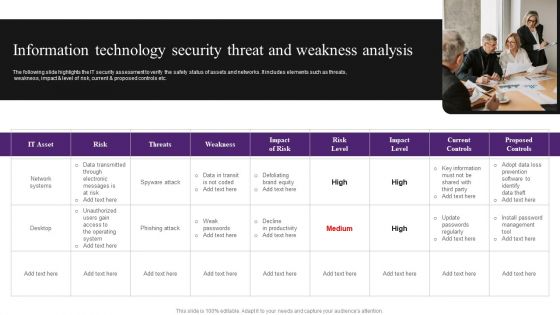
Information Technology Security Threat And Weakness Analysis Diagrams PDF
The following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Persuade your audience using this Information Technology Security Threat And Weakness Analysis Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Risk, Network Systems, Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
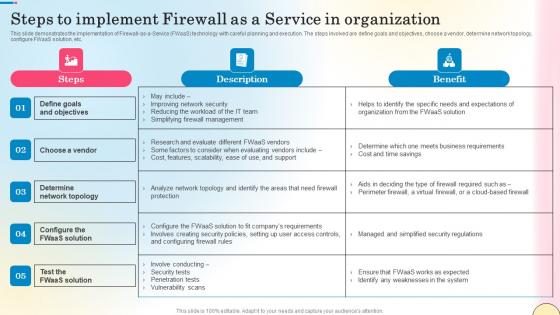
Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf
This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Get a simple yet stunning designed Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
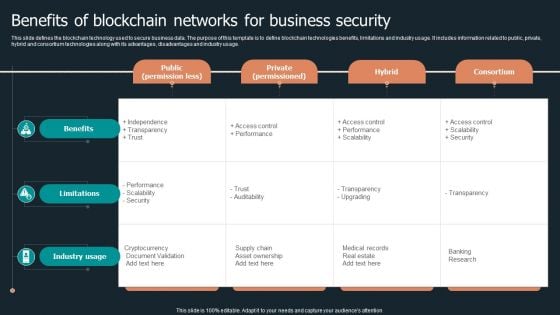
Benefits Of Blockchain Networks For Business Security Structure PDF
This slide defines the blockchain technology used to secure business data. The purpose of this template is to define blockchain technologies benefits, limitations and industry usage. It includes information related to public, private, hybrid and consortium technologies along with its advantages, disadvantages and industry usage. Pitch your topic with ease and precision using this Benefits Of Blockchain Networks For Business Security Structure PDF. This layout presents information on Public Permission Less, Private Permissioned, Hybrid Consortium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
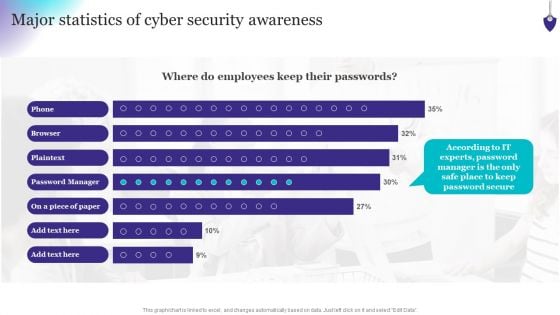
Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Welcome to our selection of the Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf
The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc.
How Install Vpn My Router In Powerpoint And Google Slides Cpb
Introducing our well-designed How Install Vpn My Router In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like How Install Vpn My Router As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our How Install Vpn My Router In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































