Data Protection

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.

Log Management Process In Application Security Testing Ppt Powerpoint Brochure
This slide showcases the introduction of log management in application security for decreasing the security threats. The Log Management Process In Application Security Testing Ppt Powerpoint Brochure is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases the introduction of log management in application security for decreasing the security threats.

Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Are you searching for a Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V from Slidegeeks today. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
Approved Probiotics In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Approved Probiotics In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Approved Probiotics that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Approved Probiotics In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
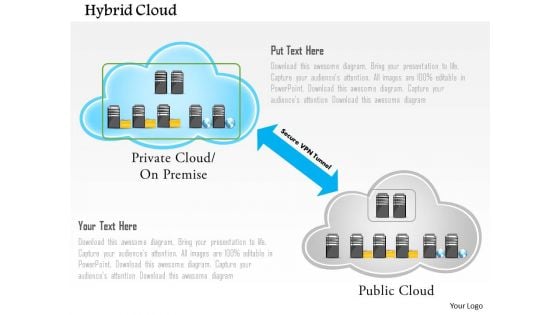
Hybrid Cloud With Public And Privet Cloud Networks And VPN Tunnel Powerpoint Template
This PowerPoint template contains graphic of hybrid cloud with public and privet cloud networks. You may use this PPT slide to exhibit how a VPN tunnel works. Use this technology template design to illustrate your ability.
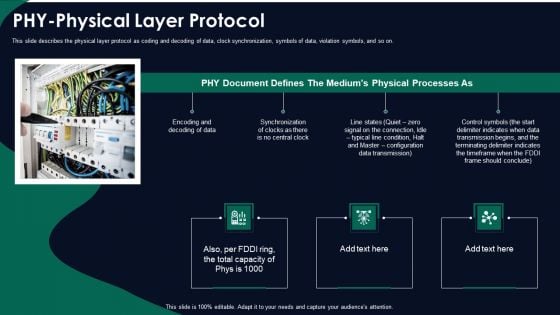
FDDI Network Standard IT Phy Physical Layer Protocol Ppt File Show PDF
This slide describes the physical layer protocol as coding and decoding of data, clock synchronization, symbols of data, violation symbols, and so on. Deliver an awe inspiring pitch with this creative fddi network standard it phy physical layer protocol ppt file show pdf bundle. Topics like phy physical layer protocol can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Books In Powerpoint And Google Slides Cpb
Introducing our well-designed Information Security Books In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Books. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Books In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Guide To Designing A Staff Handbook Information Pdf

Security Handbook For Corporate Personnel Information Pdf
Create an editable Security Handbook For Corporate Personnel Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Handbook For Corporate Personnel Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Following slide exhibits impact of effective internal communication on employee based on measurement performance indicators. It include elements such as engagement rate, turnover rate, productivity etc.

Two Factor Authentication Example Of Ppt Presentation
This is a two factor authentication example of ppt presentation. This is a two stage process. The stages in this process are something you know, something you have.

Keto Approved Fruit In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Keto Approved Fruit In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Keto Approved Fruit that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Keto Approved Fruit In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Laptop With Key And Chain Attached Success PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key And Chain Attached Success PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our Technology PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Download our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time.Use these PowerPoint slides for presentations relating to Laptop and key, business, computer, security, network diagrams, technology. The prominent colors used in the PowerPoint template are Yellows, Gray, Black. Achieve that festive atmosphere you desire. Festoon your address with our Laptop With Key And Chain Attached Success PowerPoint Templates Ppt Backgrounds For Slides 0213.

Web Consulting Business Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. The Web Consulting Business Website Security Management Action Plan is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.
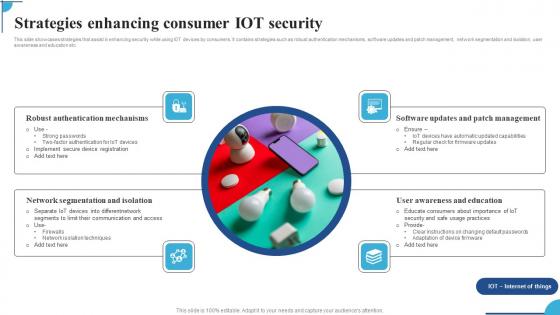
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout. This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc.
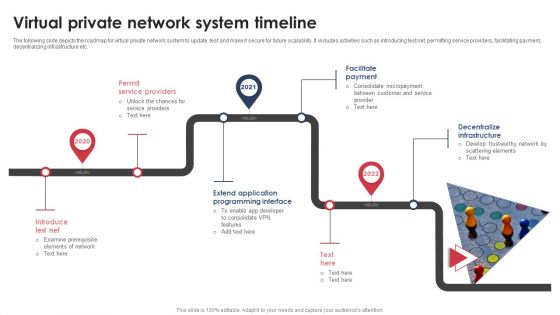
Virtual Private Network System Timeline Graphics PDF
The following slide depicts the roadmap for virtual private network system to update, test and make it secure for future scalability. It includes activities such as introducing test net, permitting service providers, facilitating payment, decentralizing infrastructure etc. Presenting Virtual Private Network System Timeline Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Permit Service Providers, Facilitate Payment, Decentralize Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
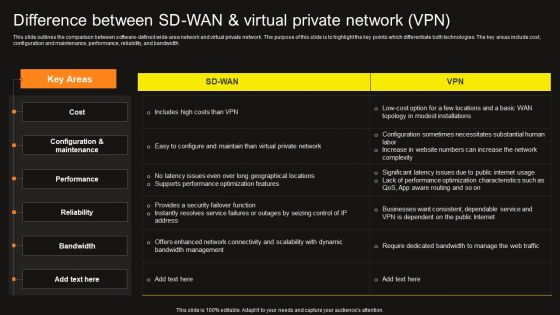
Virtual WAN Architecture Difference Between SD WAN And Virtual Private Network VPN Clipart PDF
This slide outlines the comparison between software-defined wide-area network and virtual private network. The purpose of this slide is to highlight the key points which differentiate both technologies. The key areas include cost, configuration and maintenance, performance, reliability, and bandwidth. This modern and well-arranged Virtual WAN Architecture Difference Between SD WAN And Virtual Private Network VPN Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Zero Trust Model Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Traditional Security Models Vs Zero Trust Network Access and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.
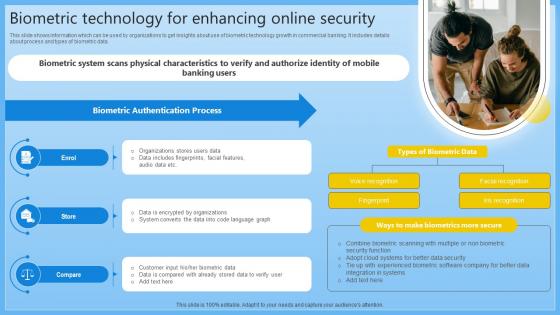
Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.
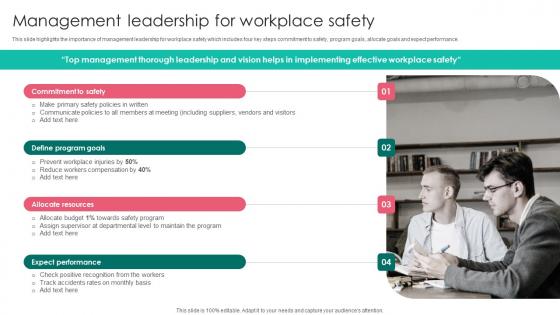
Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf
This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance. The Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance.
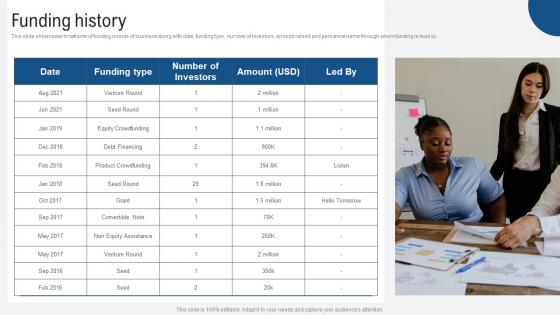
Funding History Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
This slide showcases timeframe of funding rounds of business along with date, funding type, number of investors, amount raised and personnel name through whom funding is lead by. The Funding History Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases timeframe of funding rounds of business along with date, funding type, number of investors, amount raised and personnel name through whom funding is lead by.
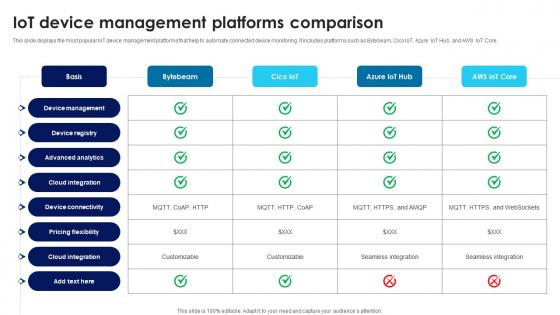
Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V
This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core. The Building Trust With IoT Security IoT Device Management Platforms Comparison IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
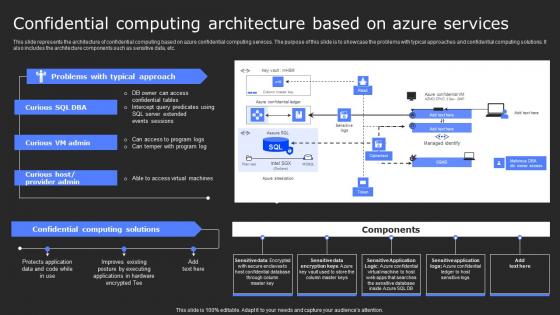
Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf
This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.

Key Benefits Of Implementing Online Security Management System Infographics PDF
This slide showcases key benefits of implementing digital safety management system which help focus on higher priority business tasks. It provides information regarding quality data, improves productivity, compliance requirements, minimize error and reporting and tracking. Presenting Key Benefits Of Implementing Online Security Management System Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Improves Productivity, Quality Data, Minimize Error. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making.
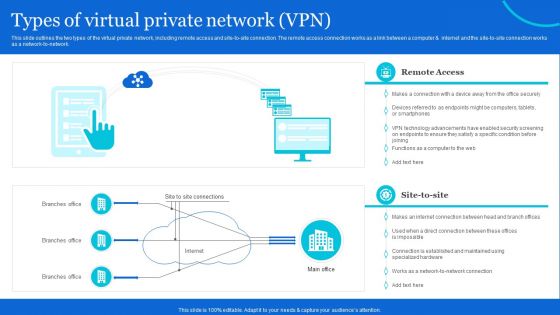
Naas Architectural Framework Types Of Virtual Private Network VPN Mockup PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site-to-site connection works as a network-to-network. Create an editable Naas Architectural Framework Types Of Virtual Private Network VPN Mockup PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Naas Architectural Framework Types Of Virtual Private Network VPN Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
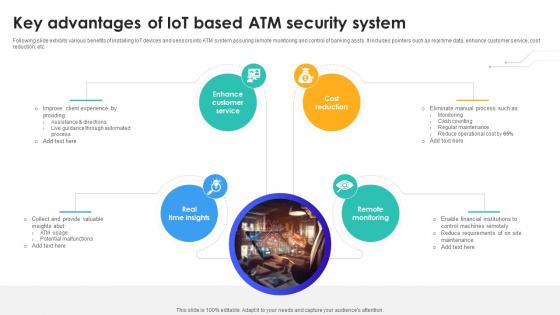
Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V
Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc. This modern and well-arranged Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc.
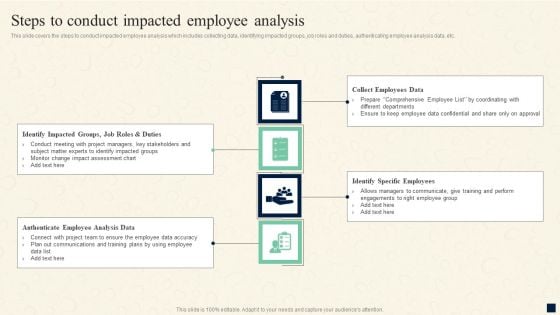
Change Management Process Steps To Conduct Impacted Employee Analysis Professional PDF
This slide covers the steps to conduct impacted employee analysis which includes collecting data, identifying impacted groups, job roles and duties, authenticating employee analysis data, etc. The Change Management Process Steps To Conduct Impacted Employee Analysis Professional PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Laptop With Lock Password Authentication Vector Icon Ppt Powerpoint Presentation Icon Summary
This is a laptop with lock password authentication vector icon ppt powerpoint presentation icon summary. This is a one stage process. The stages in this process are password, access approval, authentication icon.
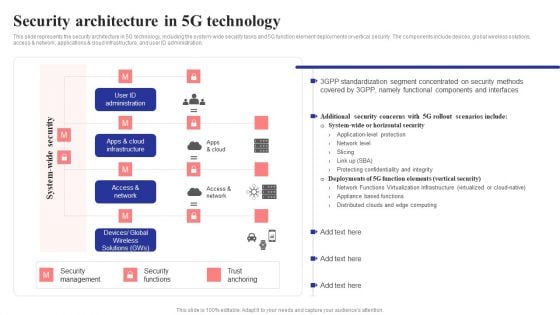
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
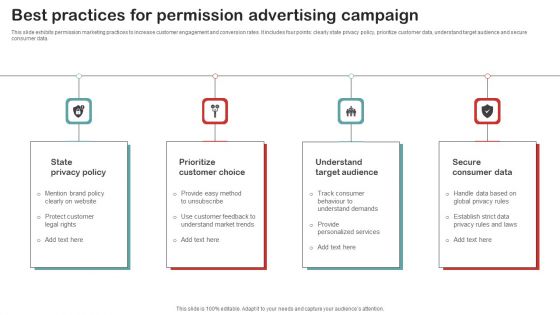
Best Practices For Permission Advertising Campaign Mockup PDF
This slide exhibits permission marketing practices to increase customer engagement and conversion rates. It includes four points clearly state privacy policy, prioritize customer data, understand target audience and secure consumer data. Presenting Best Practices For Permission Advertising Campaign Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Understand Target Audience, Secure Consumer Data, Prioritize Customer Choice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.

Prevention Of Information Key Statistics Showing The Impact Of Security Awareness Infographics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. This modern and well-arranged Prevention Of Information Key Statistics Showing The Impact Of Security Awareness Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Various Strategies To Ensure Food Safety Food Security Excellence Ppt Icon Slide PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety food security excellence ppt icon slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
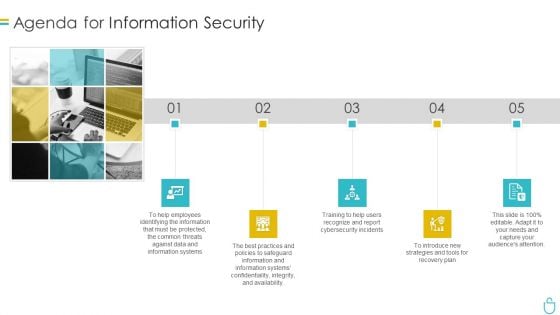
Agenda For Information Security Ppt Professional Good PDF
This is a agenda for information security ppt professional good pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, systems, data, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf
Are you searching for a Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf from Slidegeeks today. Our Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
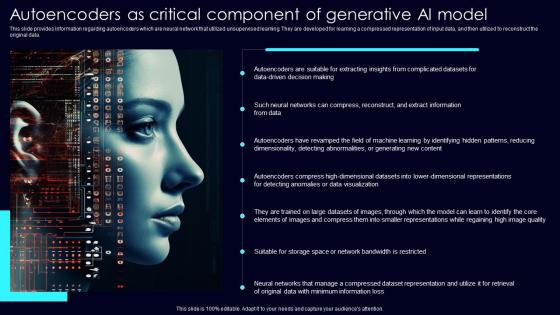
Autoencoders As Critical Exploring Rise Of Generative AI In Artificial Intelligence Guidelines Pdf
This slide provides information regarding autoencoders which are neural network that utilized unsupervised learning. They are developed for learning a compressed representation of input data, and then utilized to reconstruct the original data. Present like a pro with Autoencoders As Critical Exploring Rise Of Generative AI In Artificial Intelligence Guidelines Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides information regarding autoencoders which are neural network that utilized unsupervised learning. They are developed for learning a compressed representation of input data, and then utilized to reconstruct the original data.
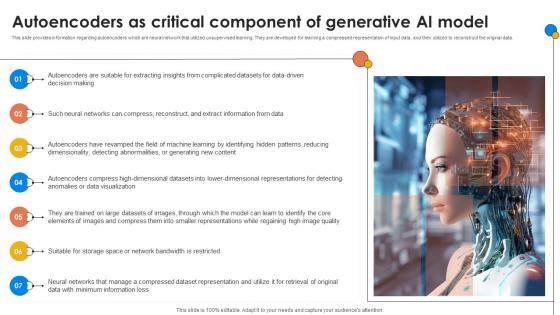
Autoencoders As Critical Component Of Generative AI For Better Productivity AI SS V
This slide provides information regarding autoencoders which are neural network that utilized unsupervised learning. They are developed for learning a compressed representation of input data, and then utilized to reconstruct the original data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Autoencoders As Critical Component Of Generative AI For Better Productivity AI SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides information regarding autoencoders which are neural network that utilized unsupervised learning. They are developed for learning a compressed representation of input data, and then utilized to reconstruct the original data.
Icons Slide For Cloud Security Firewall Proposal
Elevate your presentations with our intuitive Icons Slide For Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. Our Icons Slide For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
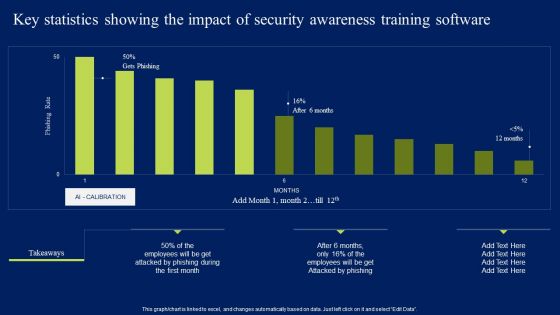
Key Statistics Showing The Impact Of Security Awareness Training Software Elements PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Statistics Showing The Impact Of Security Awareness Training Software Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
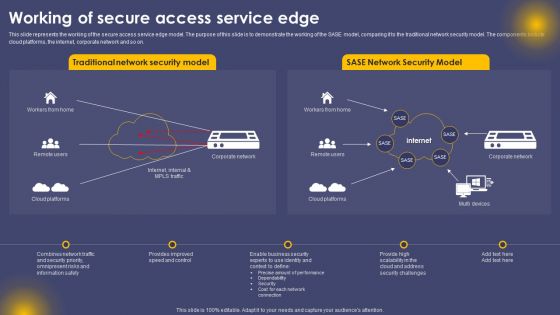
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
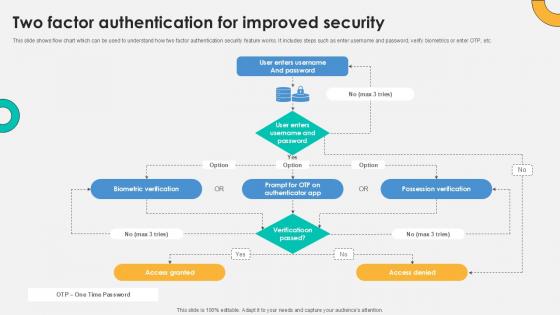
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
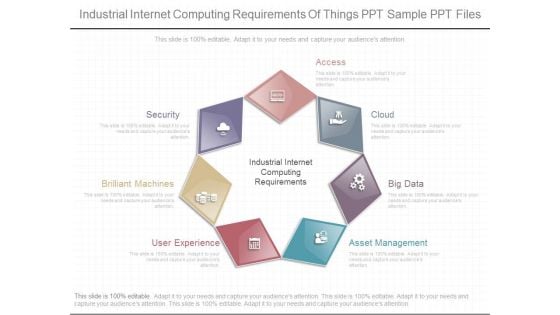
Industrial Internet Computing Requirements Of Things Ppt Sample Ppt Files
This is a industrial internet computing requirements of things ppt sample ppt files. This is a seven stage process. The stages in this process are industrial internet computing requirements, brilliant machines, user experience, asset management, big data, cloud, access, security.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
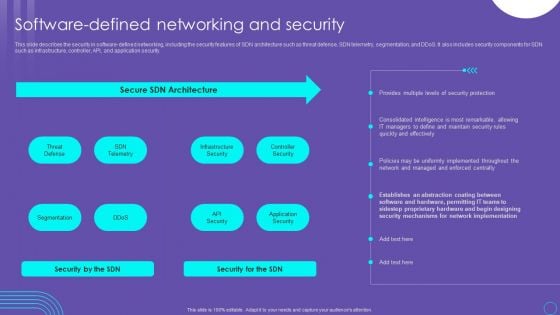
SDN Security Architecture Software Defined Networking And Security Guidelines PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate SDN Security Architecture Software Defined Networking And Security Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Touch Screen Login Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with brass key protruding out of a silver touch screen tablet computer You will find our Touch Screen Login Security PowerPoint Templates And PowerPoint Backgrounds 0211 fighting fit. They will give you able-bodied assistance.
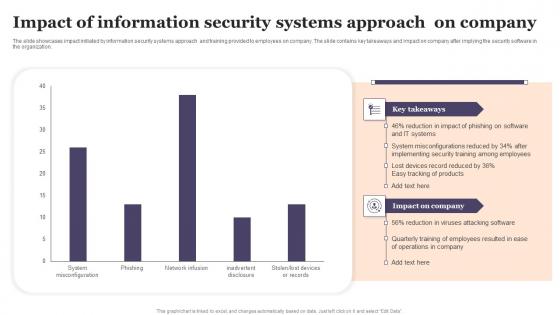
Impact Of Information Security Systems Approach On Company Designs Pdf
The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Showcasing this set of slides titled Impact Of Information Security Systems Approach On Company Designs Pdf The topics addressed in these templates are Impact Of Information, Security Systems, Approach On Company All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization.

Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secure Internet Browser Networking PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Internet PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our Technology PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Communication PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate.Use these PowerPoint slides for presentations relating to Secure internet browser, internet, technology, security, communication, business. The prominent colors used in the PowerPoint template are Yellow, Orange, Gray. Report problems with our Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.

Searching Password Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with the metallic magnifying glass hovering in front of a flat panel computer display monitor with a large brass metallic key on it on a black reflective surface Conduct yourself creditably with our Searching Password Security PowerPoint Backgrounds And Templates 1210. They will let you dominate the dais.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.

Business People 3d Man With Recycle Bin Reuse PowerPoint Templates Ppt Backgrounds For Slides
We present our business people 3d man with recycle bin reuse PowerPoint templates PPT backgrounds for slides.Present our Technology PowerPoint Templates because It will get your audience in sync. Download and present our Success PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Present our Business PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please.Use these PowerPoint slides for presentations relating to 3d, Bin, Cap, Child, Clean, Concept, Conservation, Container, Eco, Ecologic, Ecological, Ecology, Empty, Environment, Environmental, Female, Garbage, Girl, Holding, Isolated, Male, Open, People, Person, Plastic, Protect, Recyclable, Recycle, Recycling, Recycling Bin, Red, Responsibility, Reusable, Reuse, Rubbish, Stand, Symbol, Thumb Up, Trash, Waste, White, Woman, Young. The prominent colors used in the PowerPoint template are Red, Gray, Black. Stand on your own feet with our Business People 3d Man With Recycle Bin Reuse PowerPoint Templates Ppt Backgrounds For Slides. They will deliver all the assistance you need.
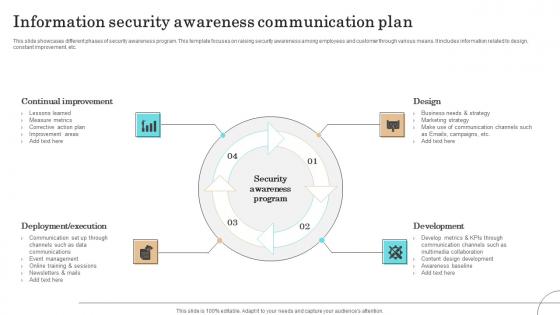
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.
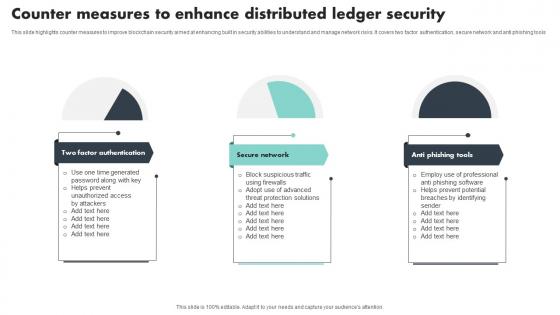
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools

Information Security Policy In Powerpoint And Google Slides Cpb
Introducing our well designed Information Security Policy In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Policy. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Policy In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
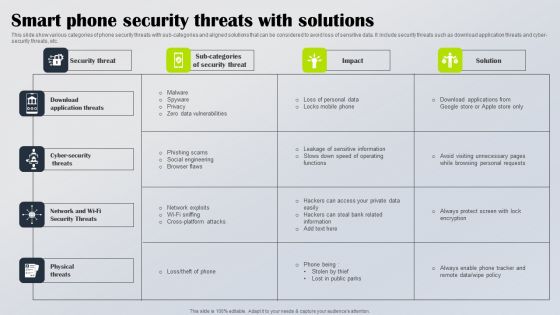
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Facility Operations Contol 4 Dimensions Of Infrastructure Security Brochure PDF
Presenting this set of slides with name facility operations contol 4 dimensions of infrastructure security brochure pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Construction Production Facilities 4 Dimensions Of Infrastructure Security Icons PDF
Presenting this set of slides with name construction production facilities 4 dimensions of infrastructure security icons pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
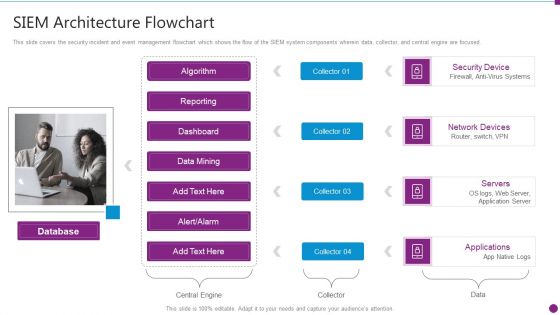
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































