Data Security And Protection
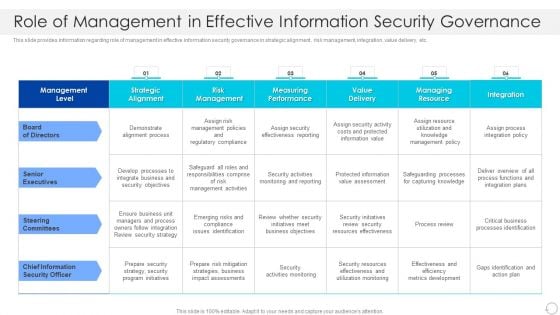
Role Of Management In Effective Information Security Governance Rules PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Role Of Management In Effective Information Security Governance Rules PDF bundle. Topics like Senior Executives, Steering Committees, Chief Information Security Officer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
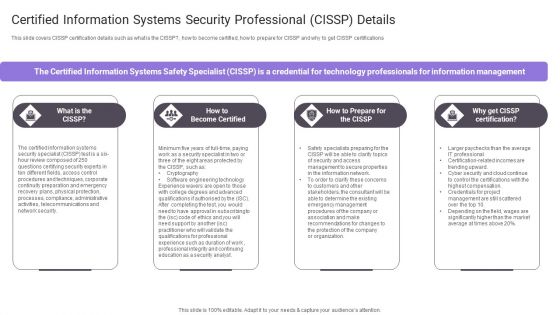
Certified Information Systems Security Professional Cissp Details Pictures PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications.Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional Cissp Details Pictures PDF bundle. Topics like Security Specialist, Certified Information, Certifying Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
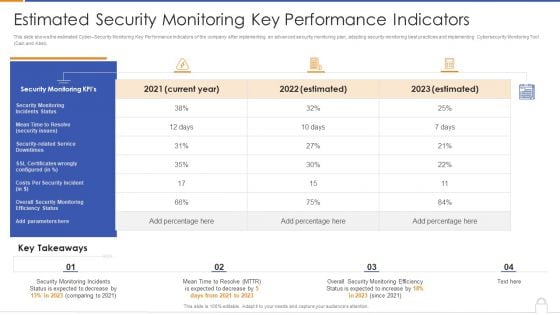
Estimated Security Monitoring Key Performance Indicators Diagrams PDF
Deliver and pitch your topic in the best possible manner with this estimated security monitoring key performance indicators diagrams pdf. Use them to share invaluable insights on security monitoring, security related service downtimes, overall security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
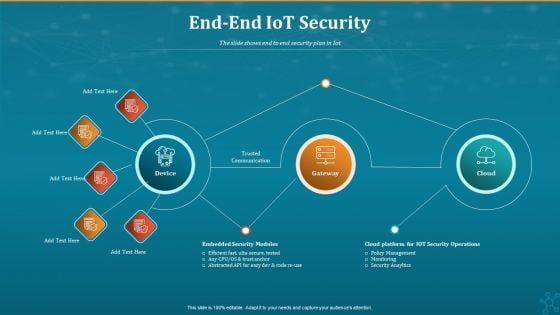
Machine To Machine Communication End End Iot Security Inspiration PDF
The slide shows end to end security plan in Iot.Deliver an awe-inspiring pitch with this creative machine to machine communication end end iot security inspiration pdf. bundle. Topics like trusted communication, gateway, embedded security modules, cloud platform for iot security operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Estimated Security Management Plan Critical Success Factors Infographics PDF
Deliver an awe inspiring pitch with this creative Estimated security management plan critical success factors infographics pdf bundle. Topics like security management, security incidents level, security implementation duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
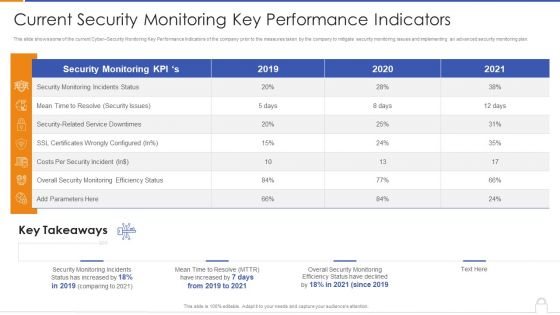
Current Security Monitoring Key Performance Indicators Formats PDF
Deliver and pitch your topic in the best possible manner with this current security monitoring key performance indicators formats pdf. Use them to share invaluable insights on security monitoring incidents, overall security monitoring, costs per security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Table Of Contents Application Security Testing Ppt Powerpoint Brochure
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Table Of Contents Application Security Testing Ppt Powerpoint Brochure from Slidegeeks and deliver a wonderful presentation. Our Table Of Contents Application Security Testing Ppt Powerpoint Brochure are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
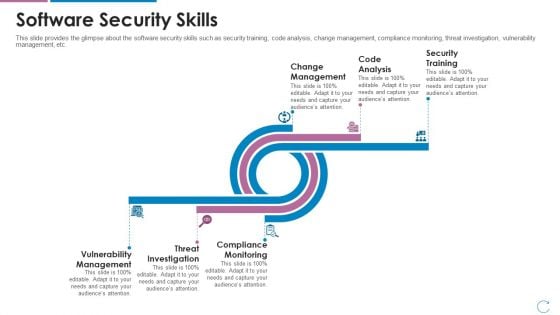
Devops Team Capabilities IT Software Security Skills Ppt Deck PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Deliver an awe inspiring pitch with this creative devops team capabilities it software security skills ppt deck pdf bundle. Topics like change management, code analysis, security training, vulnerability management, threat investigation, compliance monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
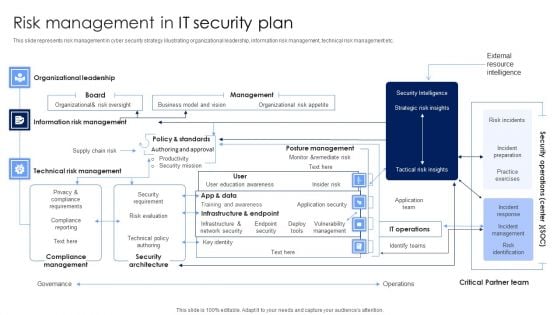
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
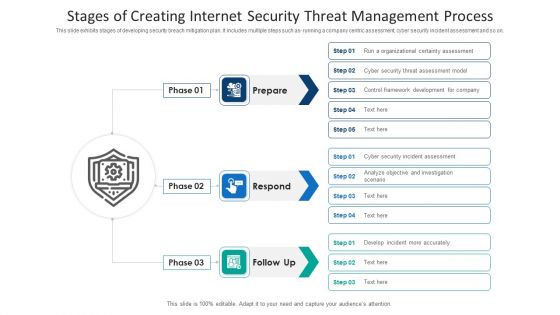
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
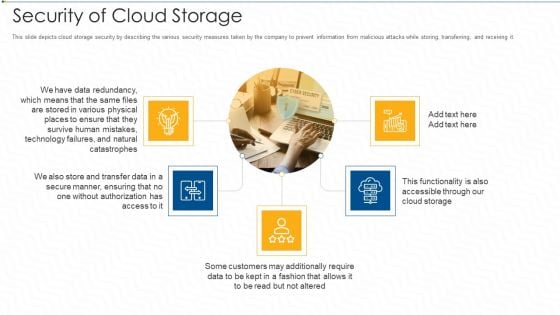
Security Of Cloud Storage Ppt Pictures Gridlines PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. This is a security of cloud storage ppt pictures gridlines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
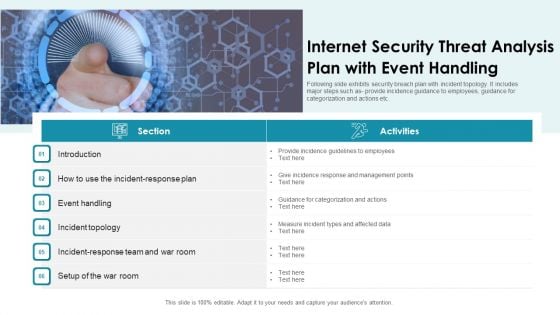
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
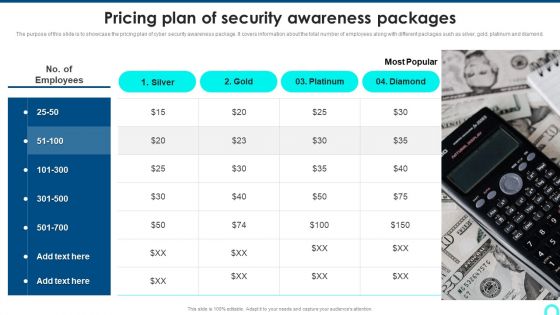
Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. This is a Pricing Plan Of Security Awareness Packages Elements PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Pricing Plan, Security Awareness, Packages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Information Technology Security Ppt Model Maker PDF
This is a agenda for information technology security ppt model maker pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, availability, integrity, information, strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
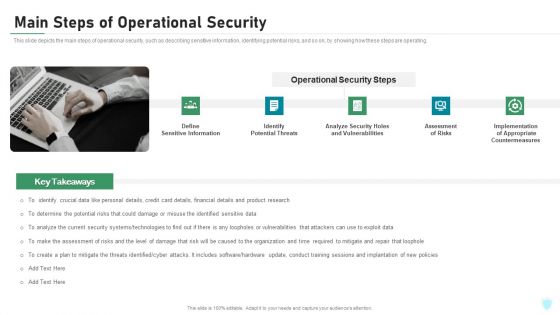
Main Steps Of Operational Security Ppt Ideas Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a main steps of operational security ppt ideas summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential threats, analyze security holes and vulnerabilities, assessment of risks, implementation of appropriate countermeasures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
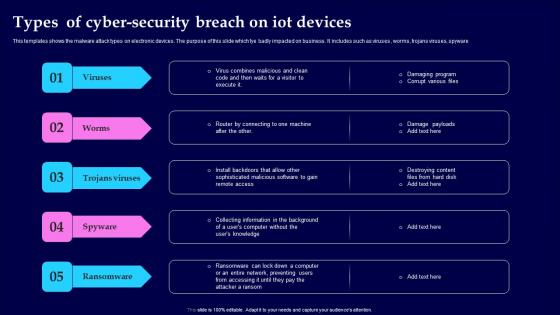
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware

Agenda For Application Security Testing Ppt Powerpoint Elements
Create an editable Agenda For Application Security Testing Ppt Powerpoint Elements that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Application Security Testing Ppt Powerpoint Elements is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Application Security Testing Ppt Powerpoint Elements are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
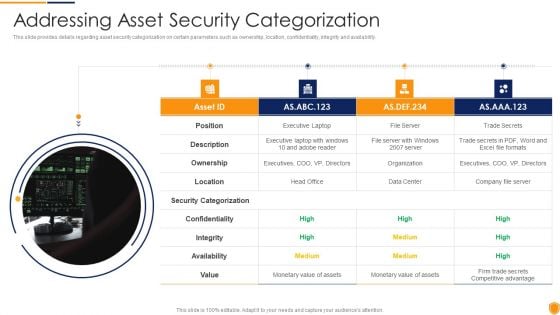
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Estimated Security Management Plan Critical Success Factors Microsoft PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors microsoft pdf. Use them to share invaluable insights on estimated security management plan critical success factors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Plan Critical Success Factors Formats PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this current security management plan critical success factors formats pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Designs PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors designs pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
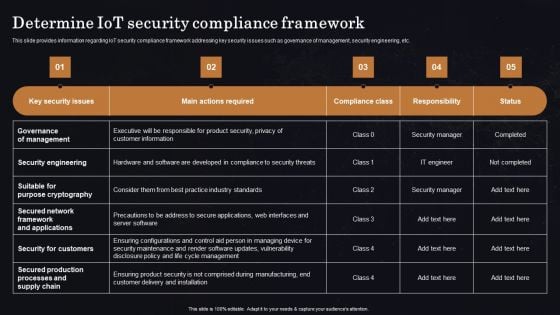
Determine Iot Security Compliance Framework Ppt Professional Vector PDF
This slide provides information regarding IoT security compliance framework addressing key security issues such as governance of management, security engineering, etc. Get a simple yet stunning designed Determine Iot Security Compliance Framework Ppt Professional Vector PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Iot Security Compliance Framework Ppt Professional Vector PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
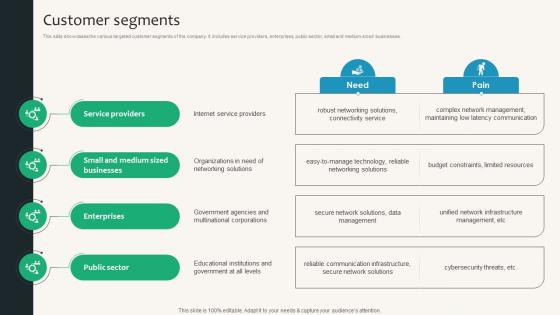
Customer Segments Security Service Provider Business Model BMC SS V
This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses. There are so many reasons you need a Customer Segments Security Service Provider Business Model BMC SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses.

Detection And Prevention Of Management Security Controls Structure PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Create an editable Detection And Prevention Of Management Security Controls Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Detection And Prevention Of Management Security Controls Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
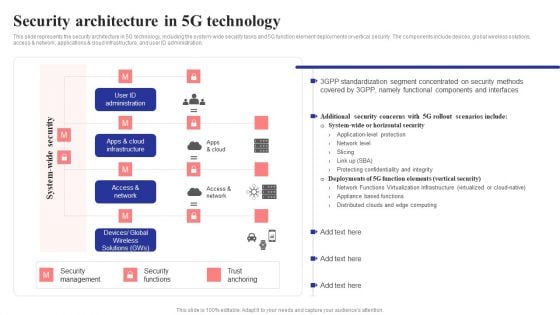
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
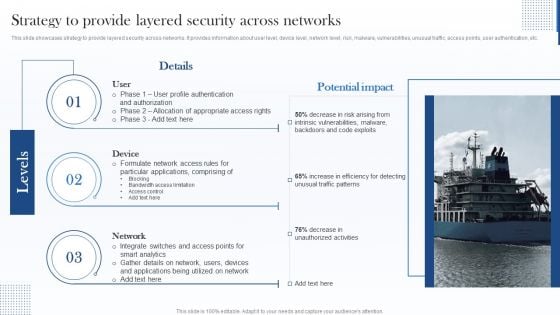
Strategy To Provide Layered Security Across Networks Microsoft PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an awe inspiring pitch with this creative Strategy To Provide Layered Security Across Networks Microsoft PDF bundle. Topics like Device, Network, Applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
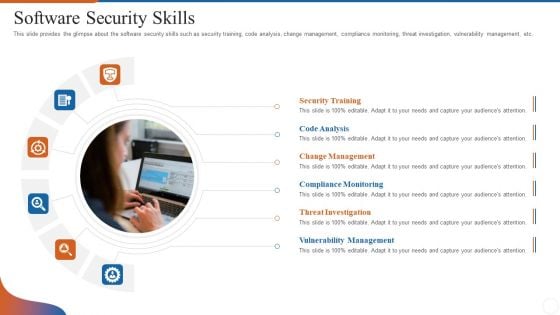
Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
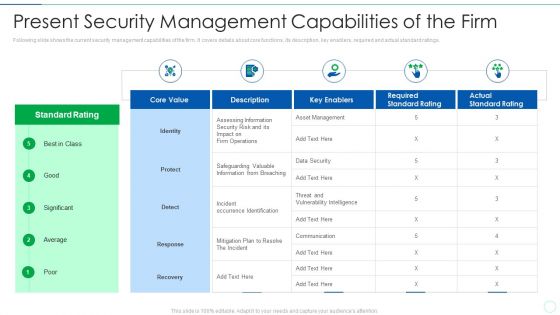
Effective IT Risk Management Process Present Security Management Formats PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this effective it risk management process present security management formats pdf. Use them to share invaluable insights on information, risk, security, plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
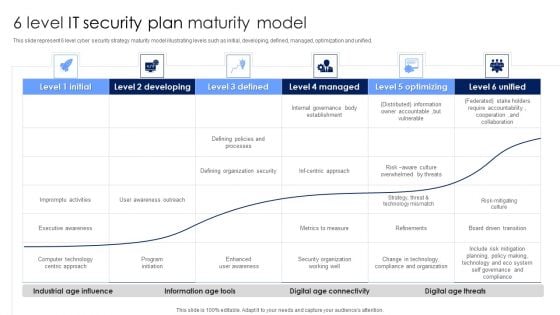
6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
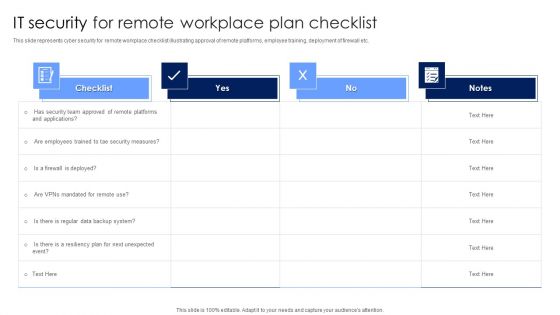
IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
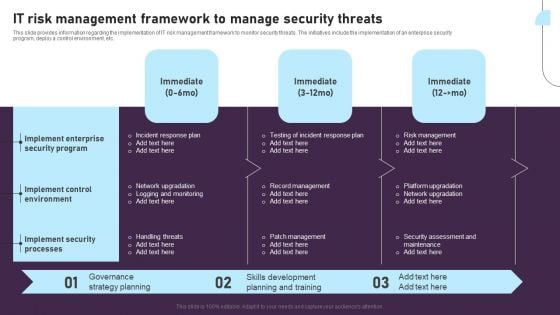
IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. There are so many reasons you need a IT Risk Management Framework To Manage Security Threats Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.
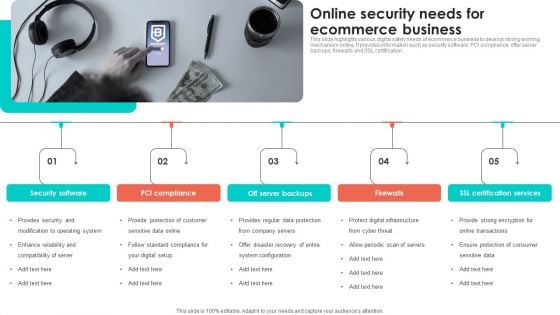
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
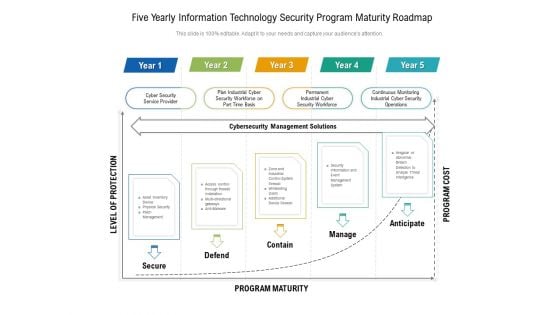
Five Yearly Information Technology Security Program Maturity Roadmap Information
Presenting the five yearly information technology security program maturity roadmap information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
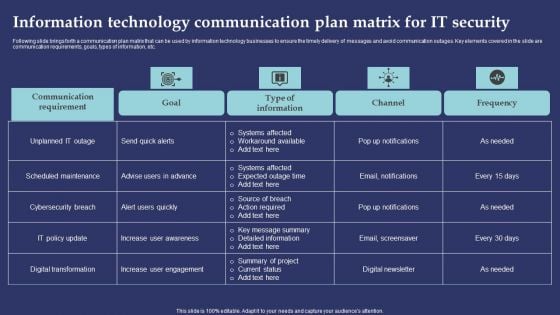
Information Technology Communication Plan Matrix For It Security Professional PDF
Following slide brings forth a communication plan matrix that can be used by information technology businesses to ensure the timely delivery of messages and avoid communication outages. Key elements covered in the slide are communication requirements, goals, types of information, etc. Showcasing this set of slides titled Information Technology Communication Plan Matrix For It Security Professional PDF. The topics addressed in these templates are Systems Affected, Workaround Available, Action Required. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Divisional Strategy To Improve Cyber Security Measures Icons PDF
This slide signifies information technology department to enhance cyber security measures. It also includes stages like identify, plan, execute and control. Presenting IT Divisional Strategy To Improve Cyber Security Measures Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Plan, Execute, Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
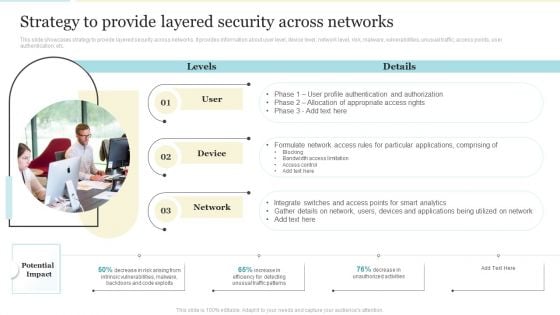
Strategy To Provide Layered Security Across Networks Elements PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Presenting Strategy To Provide Layered Security Across Networks Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Network, Applications, Device. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Document Vector Icon Ppt Styles Mockup PDF
Presenting information security document vector icon ppt styles mockup pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including information security document vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
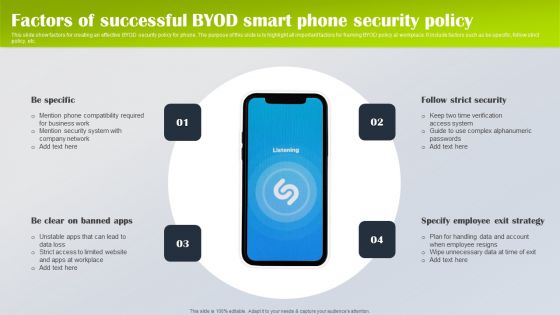
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
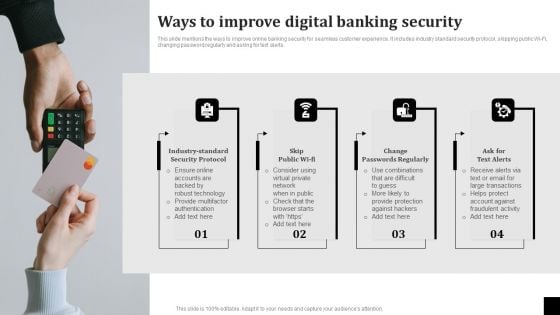
Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
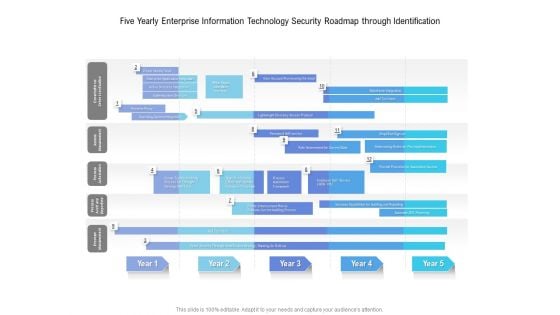
Five Yearly Enterprise Information Technology Security Roadmap Through Identification Sample
Introducing our five yearly enterprise information technology security roadmap through identification sample. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Half Yearly Information Technology Security Program Maturity Roadmap Microsoft
Introducing our half yearly information technology security program maturity roadmap microsoft. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
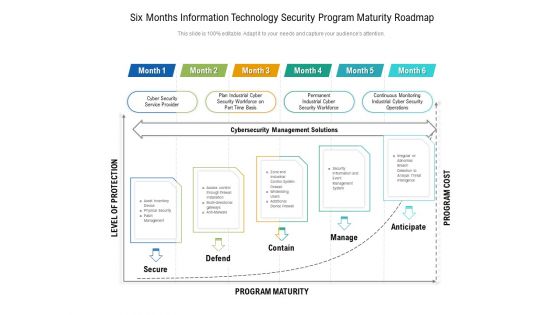
Six Months Information Technology Security Program Maturity Roadmap Infographics
Introducing our six months information technology security program maturity roadmap infographics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
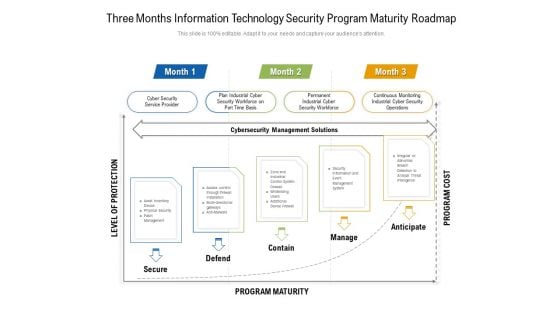
Three Months Information Technology Security Program Maturity Roadmap Pictures
Introducing our three months information technology security program maturity roadmap pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
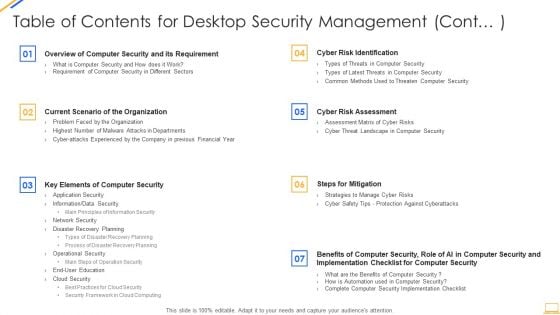
Table Of Contents For Desktop Security Management Cont Ideas PDF
Deliver an awe inspiring pitch with this creative table of contents for desktop security management cont ideas pdf bundle. Topics like security implementation, security budget, dashboards, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
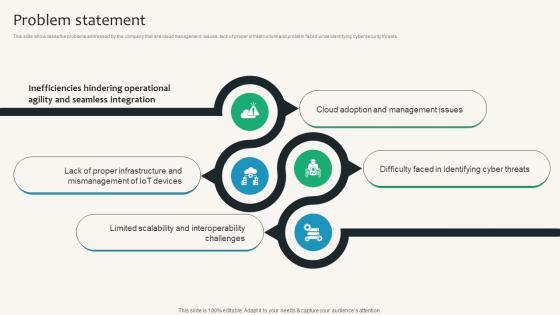
Problem Statement Security Service Provider Business Model BMC SS V
This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Security Service Provider Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Security Service Provider Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats.
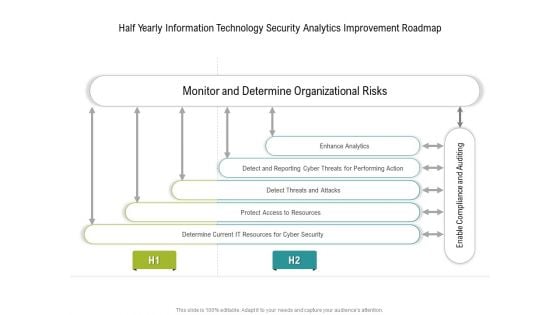
Half Yearly Information Technology Security Analytics Improvement Roadmap Slides
Presenting our innovatively structured half yearly information technology security analytics improvement roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
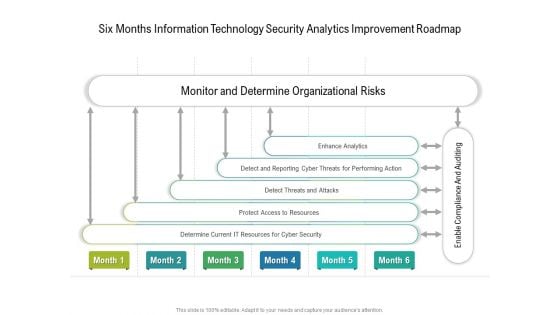
Six Months Information Technology Security Analytics Improvement Roadmap Background
Presenting our innovatively structured six months information technology security analytics improvement roadmap background Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
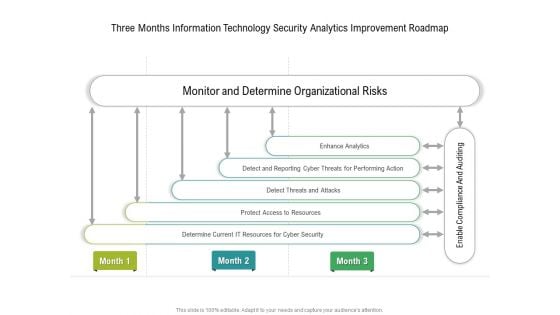
Three Months Information Technology Security Analytics Improvement Roadmap Inspiration
Presenting our innovatively structured three months information technology security analytics improvement roadmap inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
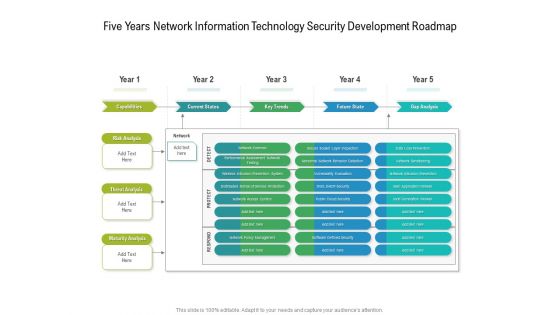
Five Years Network Information Technology Security Development Roadmap Mockup
Presenting our jaw dropping five years network information technology security development roadmap mockup. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
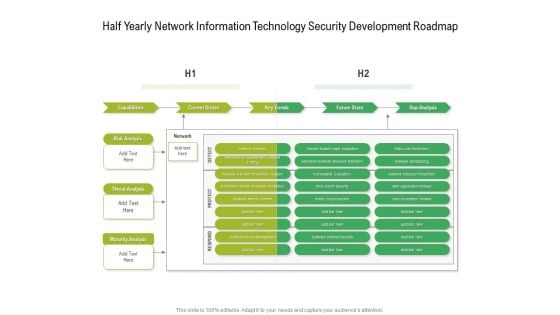
Half Yearly Network Information Technology Security Development Roadmap Rules
Presenting our jaw dropping half yearly network information technology security development roadmap rules. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
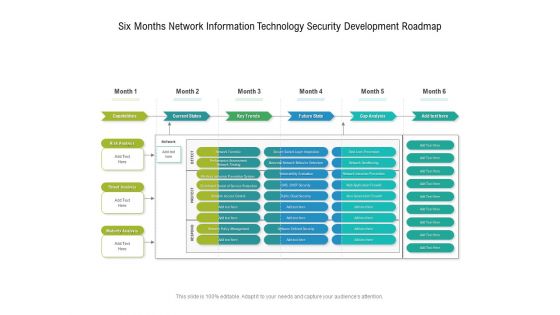
Six Months Network Information Technology Security Development Roadmap Slides
Presenting our jaw dropping six months network information technology security development roadmap slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Three Months Network Information Technology Security Development Roadmap Icons
Presenting our jaw dropping three months network information technology security development roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
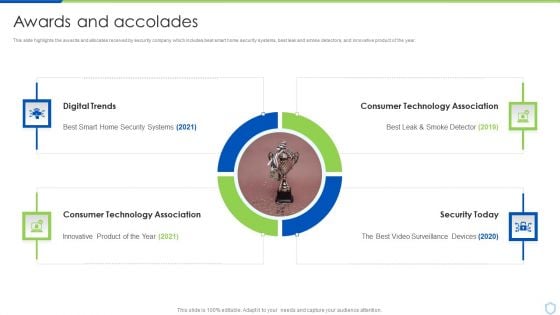
Security And Surveillance Company Profile Awards And Accolades Structure PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year.This is a Security And Surveillance Company Profile Awards And Accolades Structure PDF template with various stages. Focus and dispense information on Four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Digital Trends, Consumer Technology, Technology Association. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
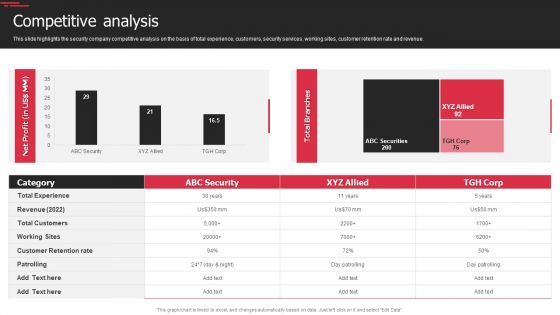
Security Agency Business Profile Competitive Analysis Designs PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Competitive Analysis Designs PDF bundle. Topics like Revenue, Customer Retention Rate, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































