Data Security And Protection
Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF
Persuade your audience using this Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Online, Certificate Icon, Information Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
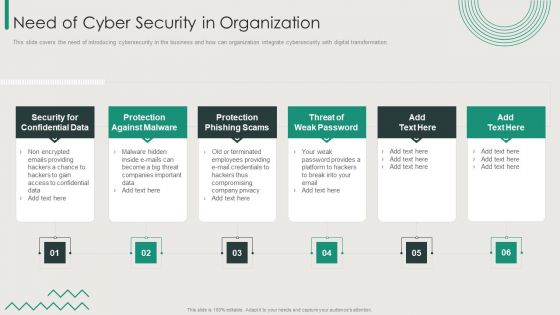
Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
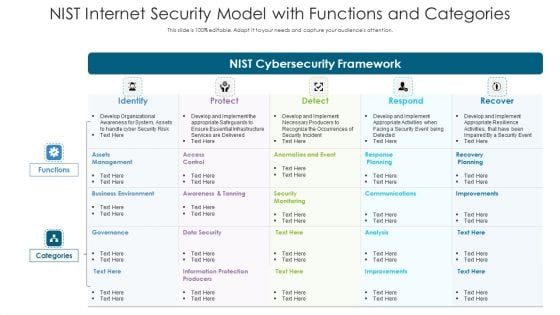
NIST Internet Security Model With Functions And Categories Ppt PowerPoint Presentation Model Show PDF
Showcasing this set of slides titled NIST internet security model with functions and categories ppt powerpoint presentation model show pdf. The topics addressed in these templates are assets management, recovery planning, information protection producers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Reasons For Poor Security Management In The Company Professional PDF
Deliver and pitch your topic in the best possible manner with this Major reasons for poor security management in the company professional pdf. Use them to share invaluable insights on evolving software, lack of recovery, improper protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Response Plan Secure Operations Data Breach Prevention Themes Pdf
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Welcome to our selection of the Data Breach Response Plan Secure Operations Data Breach Prevention Themes Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
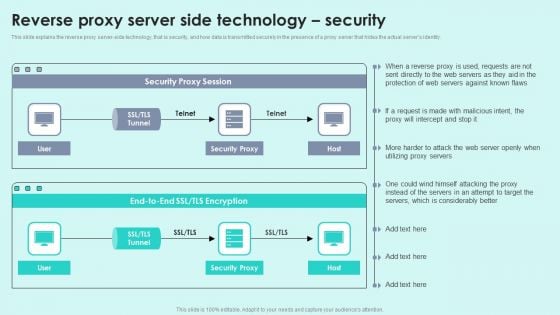
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Data Services Certification Programs Certified Data Professional Program CDP Structure PDF
This slide covers the CDP course details such as CDP Benefits, Who should become CDP, salary expectations, International Standards for CDP Program etc. This is a IT Data Services Certification Programs Certified Data Professional Program CDP Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like International Standards, Information Security, Data Protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
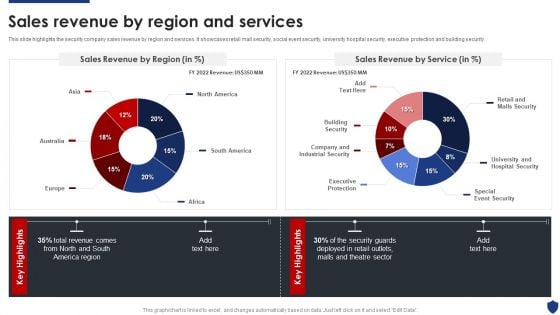
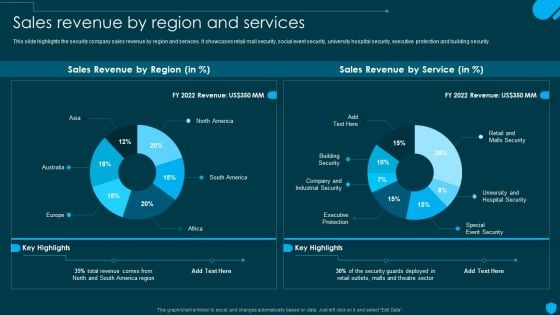
Security Officer Service Company Profile Sales Revenue By Region And Services Themes PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Sales Revenue By Region And Services Themes PDF bundle. Topics like Sales Revenue Region, Sales Revenue Service, Total Revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory.
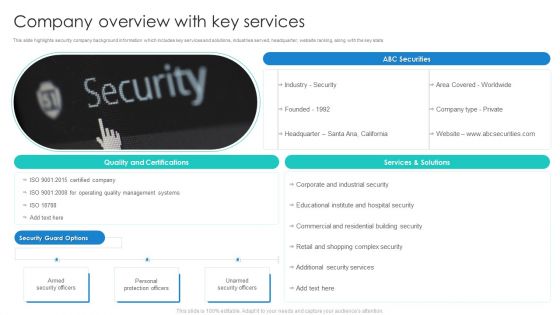
Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF bundle. Topics like Armed Security Officer, Personal Protection Officers, Unarmed Security Officers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
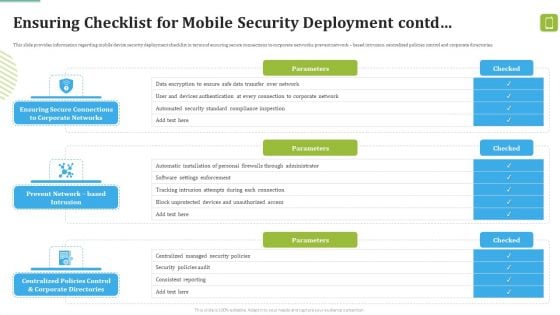
MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF. Use them to share invaluable insights on Against Malicious, Device Security, Automatic Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
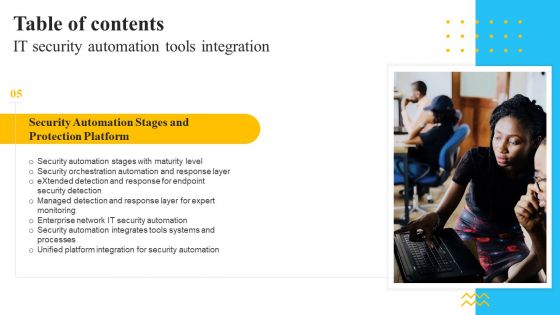
Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF
Presenting Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Automation Stages, Protection Platform, Security Orchestration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Share Your Secure Data In Business Data PowerPoint Templates Ppt Backgrounds For Slides 0713
Display your drive on our Share Your Secure Data In Business Data PowerPoint Templates PPT Backgrounds For Slides. Invigorate the audience with your fervour. Drive your team towards excellence. Steer them there with our Communication PowerPoint Templates. Drive your passion with our Business PowerPoint Templates. Steer yourself to achieve your aims. Environmental awareness is the call to answer. Our Share Your Secure Data In Business Data PowerPoint Templates Ppt Backgrounds For Slides 0713 will fit the bill.
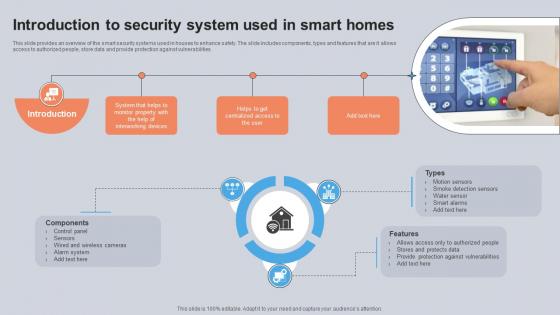
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.
Icons Slide For Securing Your Data With Tokenization Ppt Slide
Download our innovative and attention grabbing Icons Slide For Securing Your Data With Tokenization Ppt Slide template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Securing Your Data With Tokenization Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf
Showcasing this set of slides titled Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf. The topics addressed in these templates are Encryption Techniques, IconSecuring, Big Data Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
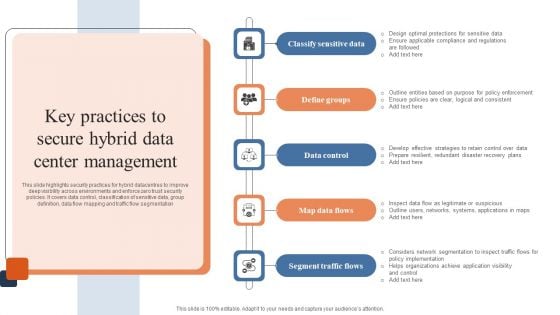
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
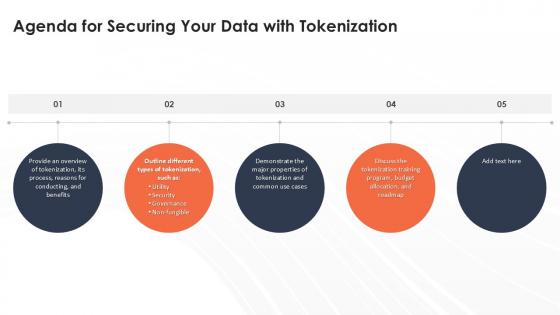
Agenda For Securing Your Data With Tokenization Ppt Template
Create an editable Agenda For Securing Your Data With Tokenization Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Securing Your Data With Tokenization Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Securing Your Data With Tokenization Ppt Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
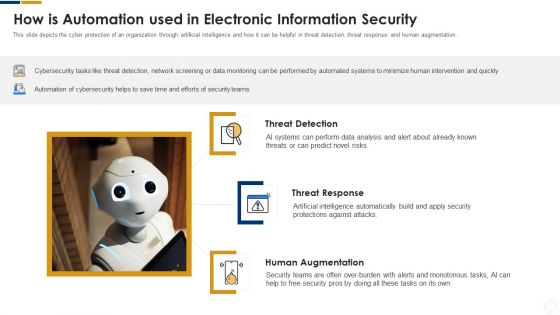
Cybersecurity How Is Automation Used In Electronic Information Security Ppt Ideas Elements PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Deliver an awe inspiring pitch with this creative cybersecurity how is automation used in electronic information security ppt ideas elements pdf bundle. Topics like threat detection, threat response, human augmentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
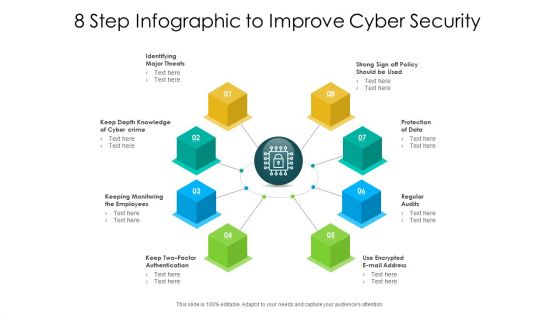
8 Step Infographic To Improve Cyber Security Ppt PowerPoint Presentation Layouts Themes PDF
Presenting 8 step infographic to improve cyber security ppt powerpoint presentation layouts themes pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including identifying major threats, keep depth knowledge of cyber crime, protection of data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
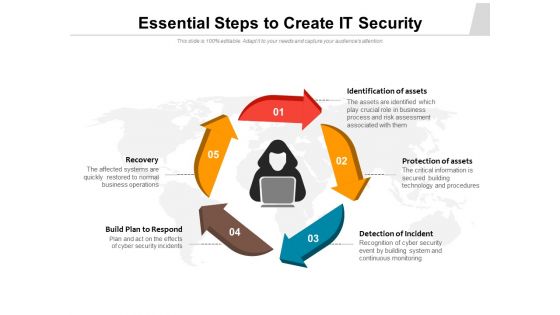
Essential Steps To Create IT Security Ppt PowerPoint Presentation Design Templates PDF
Presenting essential steps to create it security ppt powerpoint presentation design templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification of assets, protection of assets, detection of incident, recovery, build plan to respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Securing Your Data with Tokenization Powerpoint Presentation Slides PPT Example
Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb
Introducing our well designed Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cloud Secure Data Lifecycle. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
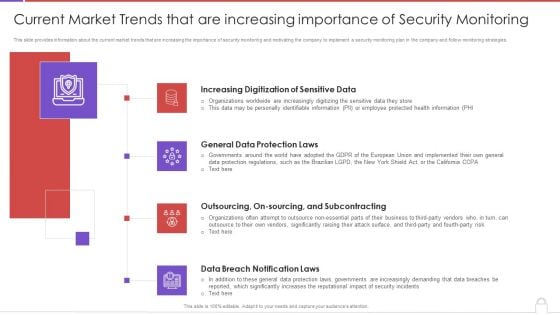
Methods To Develop Current Market Trends That Are Increasing Importance Of Security Portrait PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a methods to develop current market trends that are increasing importance of security portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization sensitive data, general data protection laws, outsourcing, on sourcing, and subcontracting, data breach notification laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Securing Your Data With Tokenization Table Of Contents Ppt Sample
Want to ace your presentation in front of a live audience Our Securing Your Data With Tokenization Table Of Contents Ppt Sample can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Our Securing Your Data With Tokenization Table Of Contents Ppt Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Technologies Used In Zero Trust Network Access Zero Trust Network Security Portrait Pdf
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Present like a pro with Technologies Used In Zero Trust Network Access Zero Trust Network Security Portrait Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.
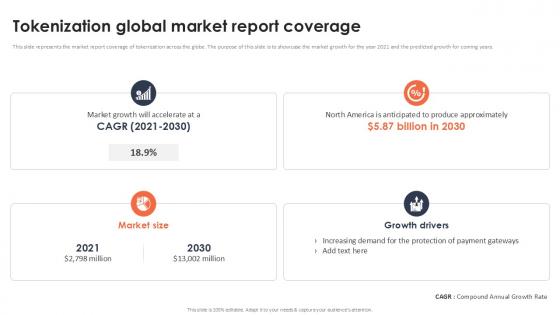
Tokenization Global Market Report Coverage Securing Your Data Ppt Slide
This slide represents the market report coverage of tokenization across the globe. The purpose of this slide is to showcase the market growth for the year 2021 and the predicted growth for coming years. Present like a pro with Tokenization Global Market Report Coverage Securing Your Data Ppt Slide Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the market report coverage of tokenization across the globe. The purpose of this slide is to showcase the market growth for the year 2021 and the predicted growth for coming years.
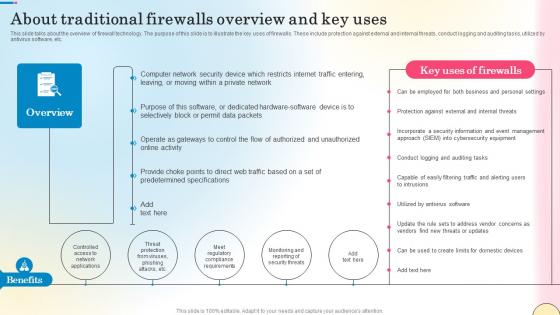
About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc.

Safely Securing Business Machine Readable Data Ppt Ideas Diagrams PDF
Presenting safely securing business machine readable data ppt ideas diagrams pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including safely securing business machine readable data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
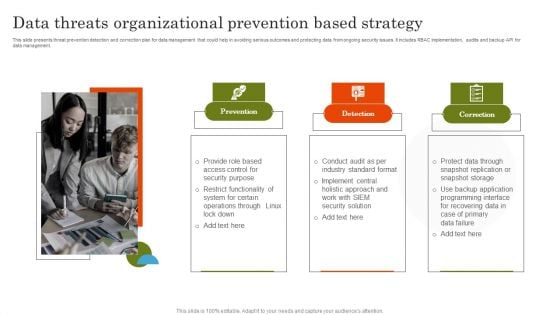
Data Threats Organizational Prevention Based Strategy Infographics PDF
This slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Increase audience engagement and knowledge by dispensing information using Data Threats Organizational Prevention Based Strategy Infographics PDF. This template helps you present information on three stages. You can also present information on Prevention, Detection, Correction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
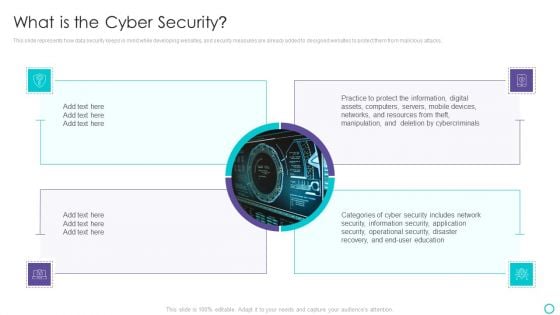
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Secure Data Access Ppt PowerPoint Presentation Inspiration Guidelines Cpb
Presenting this set of slides with name secure data access ppt powerpoint presentation inspiration guidelines cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure data access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Website Programming IT What Is The Cyber Security Ppt PowerPoint Presentation Gallery Example File PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks. This is a website programming it what is the cyber security ppt powerpoint presentation gallery example file pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, digital assets, computers, servers, mobile devices, networks, and resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enable Data Centre Management Through Hyper Converged Infrastructure Formats PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Explore a selection of the finest Enable Data Centre Management Through Hyper Converged Infrastructure Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Enable Data Centre Management Through Hyper Converged Infrastructure Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Enable Data Centre Management Through Hyper Converged Infrastructure Demonstration PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. This modern and well arranged Enable Data Centre Management Through Hyper Converged Infrastructure Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
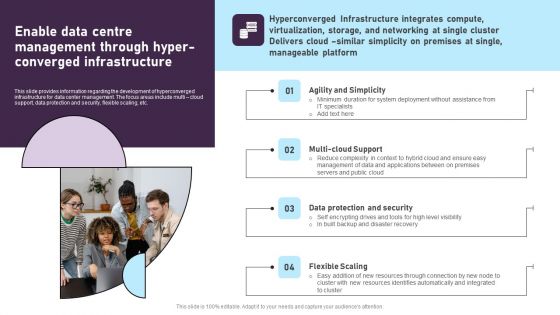
Enable Data Centre Management Through Hyper-Converged Infrastructure Template PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Enable Data Centre Management Through Hyper-Converged Infrastructure Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. The Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
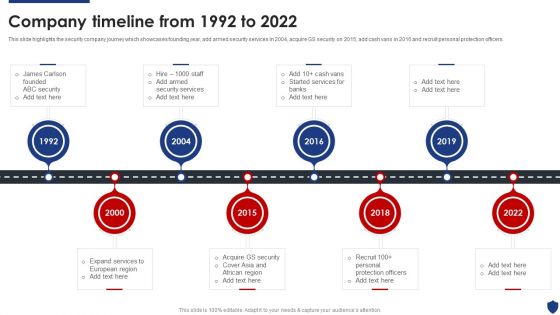
Security Officer Service Company Profile Company Timeline From 1992 To 2022 Themes PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Security Officer Service Company Profile Company Timeline From 1992 To 2022 Themes PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Expand Services, Acquire GS Security, Security Services, 1992 To 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Manpower Corporate Security Business Profile Sales Revenue By Region And Services Icons PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Sales Revenue By Region And Services Icons PDF. Use them to share invaluable insights on Sales Revenue, Region And Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V
This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc. Retrieve professionally designed Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc.
Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development.This is a Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Empower Secure, Log Respectability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness Deliver an awe inspiring pitch with this creative case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like building management, security management, security effectiveness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
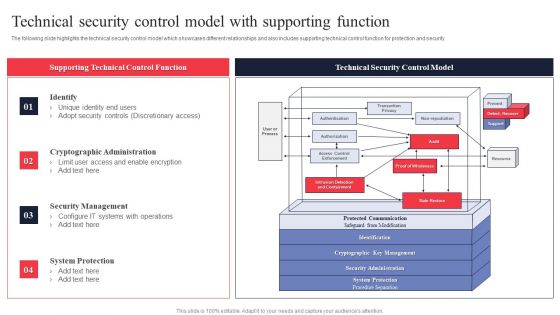
IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
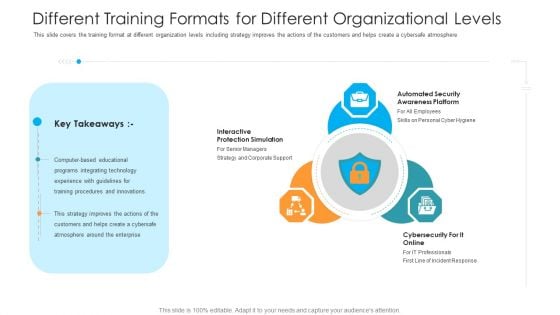
Different Training Formats For Different Organizational Levels Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a different training formats for different organizational levels hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity for it online. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Welcome to our selection of the Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Workforce Security Realization Coaching Plan Different Training Formats For Different Organizational Levels Icons PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting workforce security realization coaching plan different training formats for different organizational levels icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like interactive protection simulation, cybersecurity for it online, automated security awareness platform. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
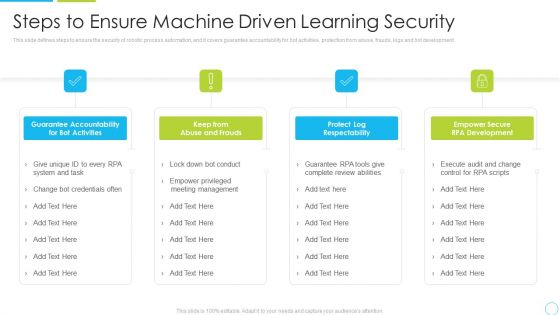
Steps To Ensure Machine Driven Learning Security Ppt Inspiration Structure PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Presenting steps to ensure machine driven learning security ppt inspiration structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like system, management, development, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Is Automation Used In Cybersecurity IT Security IT Ppt Topics PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. This is a how is automation used in cybersecurity it security it ppt topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat detection, threat response, human augmentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
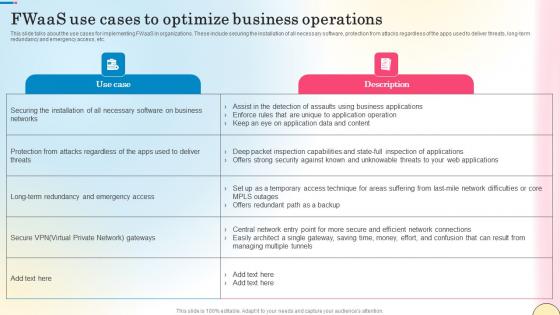
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness.
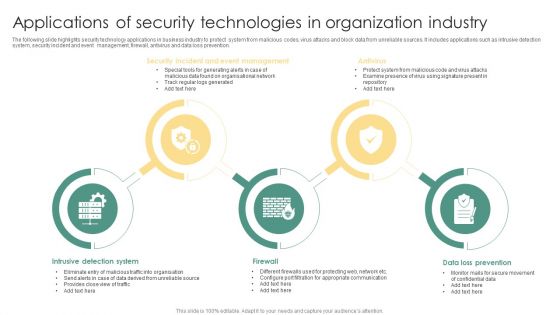
Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF
The following slide highlights security technology applications in business industry to protect system from malicious codes, virus attacks and block data from unreliable sources. It includes applications such as intrusive detection system, security incident and event management, firewall, antivirus and data loss prevention. Presenting Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Incident, Event Management, Antivirus, Firewall. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
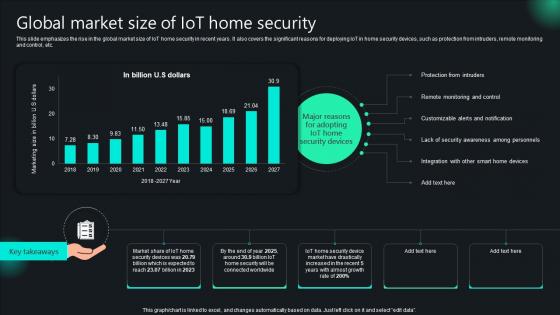
Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V
This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc. The Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc.
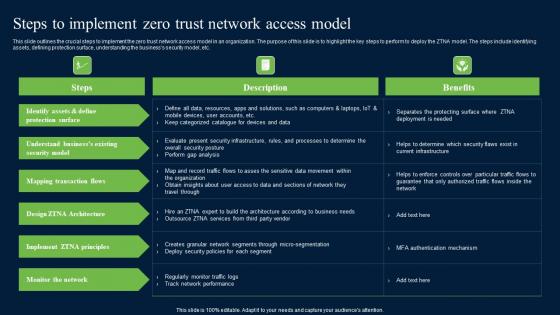
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
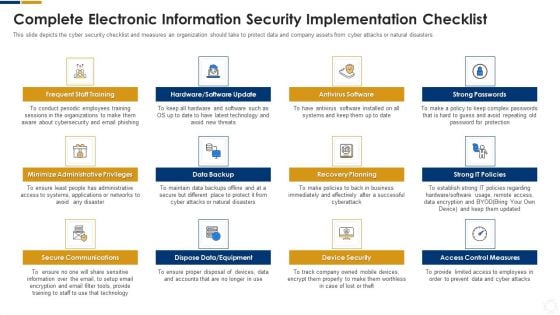
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Is The Cyber Security Role Web Designing User Engagement Rules PDF
Boost your pitch with our creative What Is The Cyber Security Role Web Designing User Engagement Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.
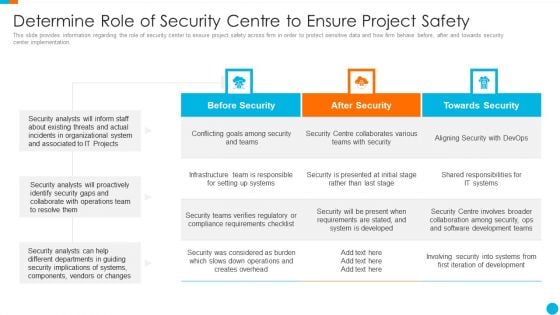
Upgrading Total Project Safety IT Determine Role Of Security Centre To Ensure Project Safety Download PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative upgrading total project safety it determine role of security centre to ensure project safety download pdf bundle. Topics like before security, after security, towards security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































