Data Security And Protection
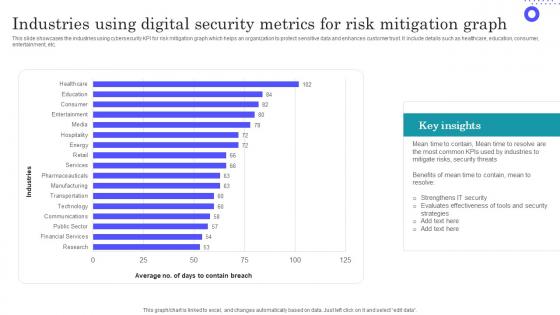
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.
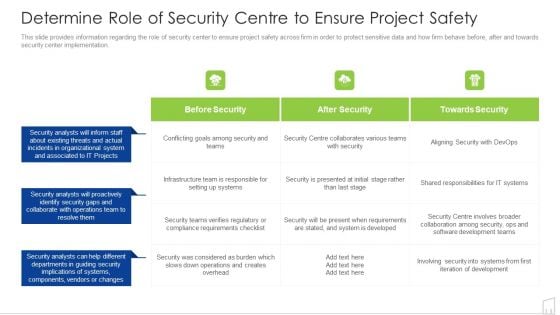
Determine Role Of Security Centre To Ensure Project Safety Ppt Professional Example PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative determine role of security centre to ensure project safety ppt professional example pdf bundle. Topics like security, system, developed, requirements, teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Get a simple yet stunning designed Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
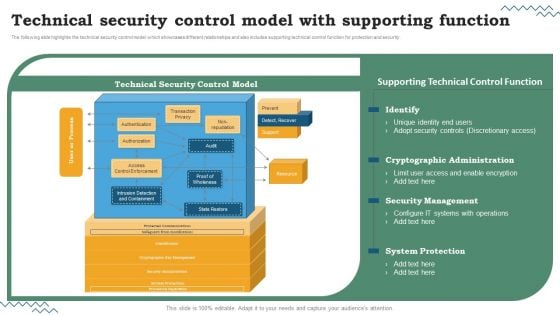
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.
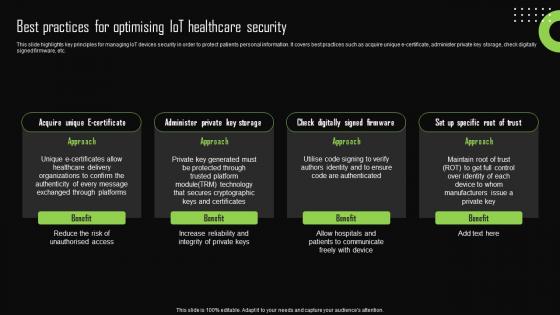
Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. There are so many reasons you need a Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.

Methods To Develop Advanced Essential Elements Of Security Monitoring Plan Formats PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver and pitch your topic in the best possible manner with this methods to develop advanced essential elements of security monitoring plan formats pdf. Use them to share invaluable insights on network security, critical infrastructure, cloud security, application security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
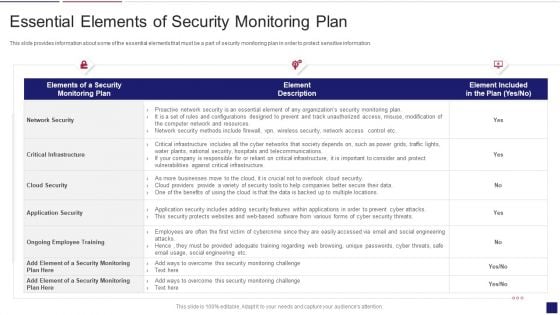
Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
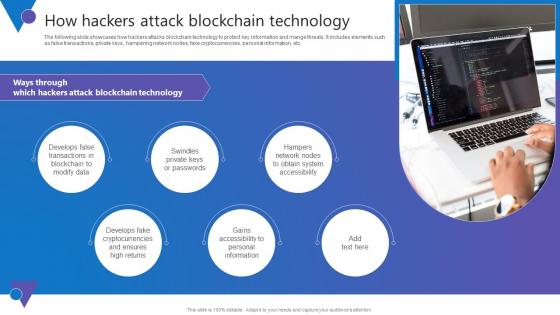
How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc.

Laptop With Key And Lock Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key And Lock Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our Technology PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download our Shapes PowerPoint Templates because You should Kick up a storm with our PowerPoint Templates and Slides. The heads of your listeners will swirl with your ideas. Present our Business PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime.Use these PowerPoint slides for presentations relating to Protect your computer, Security, Technology, Business, Shapes, Computer. The prominent colors used in the PowerPoint template are Yellow, Gray, Blue. Get fascinated by our Laptop With Key And Lock Security PowerPoint Templates Ppt Backgrounds For Slides 0213. They will keep attracting your attention.
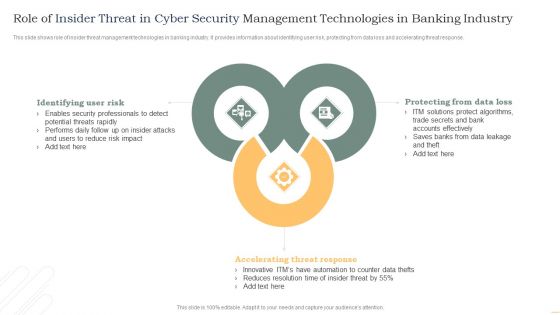
Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF
This slide shows role of insider threat management technologies in banking industry. It provides information about identifying user risk, protecting from data loss and accelerating threat response. Presenting Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying User Risk, Accelerating Threat Response, Protecting Data Loss. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
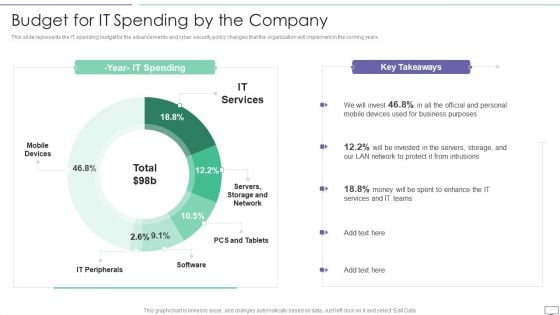
IT Security Hacker Budget For IT Spending By The Company Download PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years.Deliver an awe inspiring pitch with this creative IT Security Hacker Budget For IT Spending By The Company Download PDF bundle. Topics like Business Purposes, Protect Intrusions, Services Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
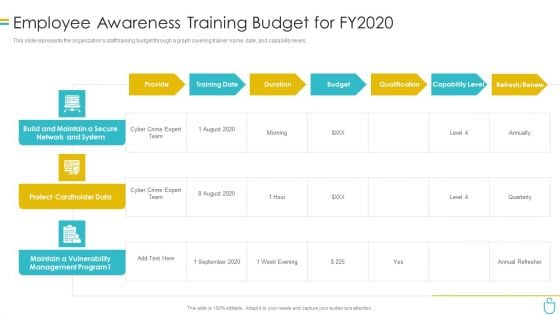
Information Security Employee Awareness Training Budget For Fy2020 Ppt File Portfolio PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative information security employee awareness training budget for fy2020 ppt file portfolio pdf bundle. Topics like budget, protect cardholder data, capability level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
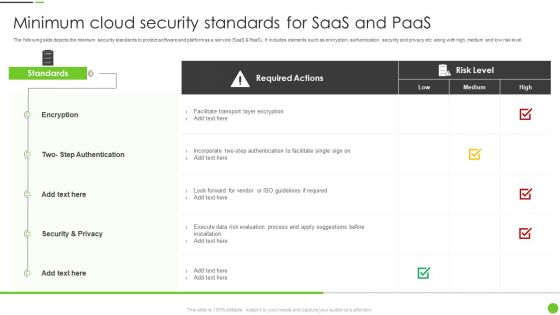
Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF
The following slide depicts the minimum security standards to protect software and platform as a service SaaS and PaaS. It includes elements such as encryption, authentication, security and privacy etc. along with high, medium and low risk level. Pitch your topic with ease and precision using this Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF. This layout presents information on Required Actions, Encryption, Security And Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
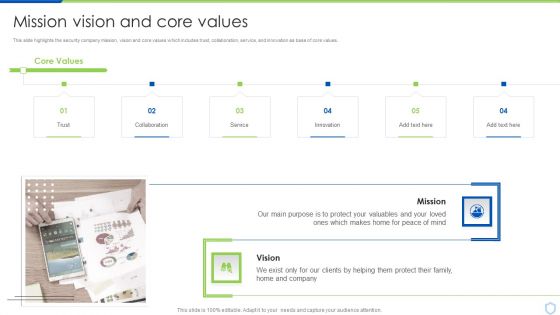
Security And Surveillance Company Profile Mission Vision And Core Values Clipart PDF
This slide highlights the security company mission, vision and core values which includes trust, collaboration, service, and innovation as base of core values.This is a Security And Surveillance Company Profile Mission Vision And Core Values Clipart PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Collaboration, Innovation, Protect Your Valuables . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
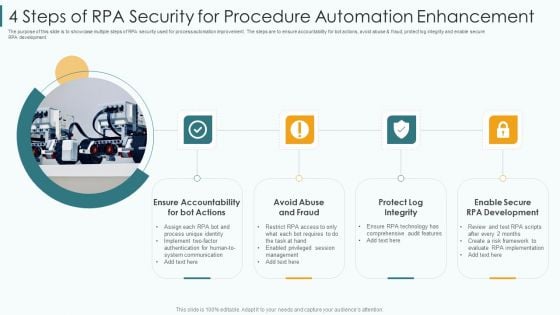
4 Steps Of RPA Security For Procedure Automation Enhancement Slides PDF
The purpose of this slide is to showcase multiple steps of RPA security used for process automation improvement. The steps are to ensure accountability for bot actions, avoid abuse and fraud, protect log integrity and enable secure RPA development. Presenting 4 steps of rpa security for procedure automation enhancement slides pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication, implement, requires. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
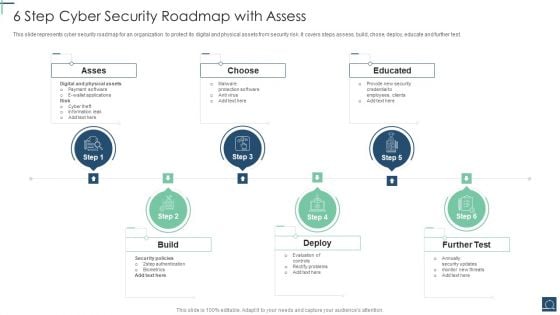
6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF
This slide represents cyber security roadmap for an organization to protect its digital and physical assets from security risk .It covers steps assess, build, chose, deploy, educate and further test. Persuade your audience using this 6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Asses, Choose, Educated, Build. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
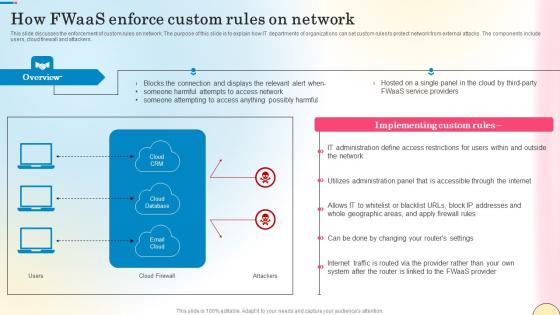
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.
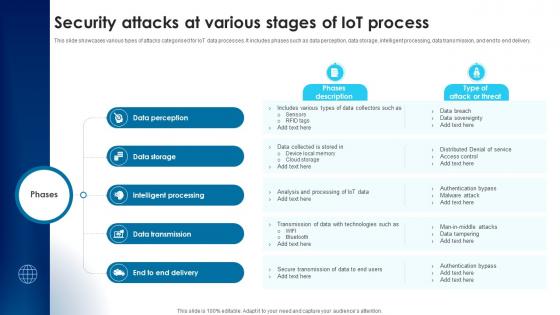
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.
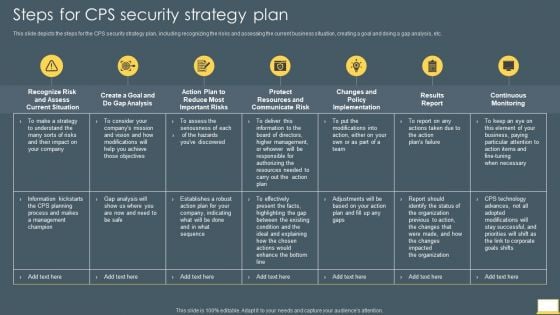
Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF. Use them to share invaluable insights on Gap Analysis, Protect Resources, Communicate Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF
The following slide showcases solution offered by IT company for its customers which are see the new network, know current threats and protect with high ROI. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Cybersecurity What Is Electronic Information Security And How Does It Work Ppt Model Shapes PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting cybersecurity what is electronic information security and how does it work ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, devices, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.
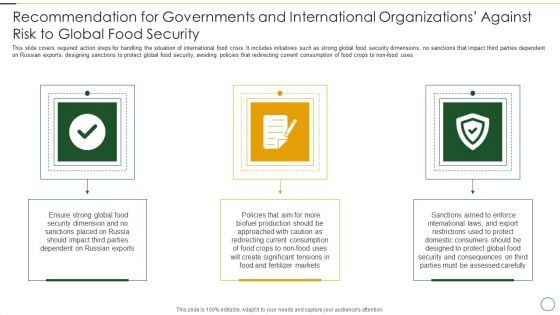
Recommendation For Governments And International Organizations Against Risk To Global Food Security Infographics PDF
This slide covers required action steps for handling the situation of international food crisis. It includes initiatives such as strong global food security dimensions, no sanctions that impact third parties dependent on Russian exports, designing sanctions to protect global food security, avoiding policies that redirecting current consumption of food crops to non food uses. Presenting recommendation for governments and international organizations against risk to global food security infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dependent on russian, ensure strong global, security dimension In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Integration Architecture To Manage Cyber Risk Pictures PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps such as identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Presenting Identify, Protect, Detect to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Data Integration Architecture To Manage Cyber Risk Pictures PDF. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
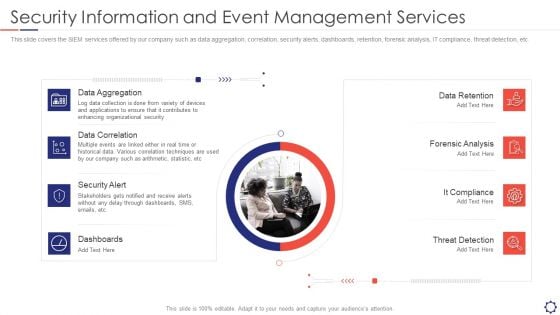
SIEM Security Information And Event Management Services Ppt Ideas Graphics Pictures PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. This is a siem security information and event management services ppt ideas graphics pictures pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Aggregation, Data Correlation, Security Alert, Dashboards, Data Retention. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
What Is IT Security IT And How Does IT Work Ppt Slides Gridlines PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a what is it security it and how does it work ppt slides gridlines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like techniques, computer systems, networks, servers, mobile devices, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
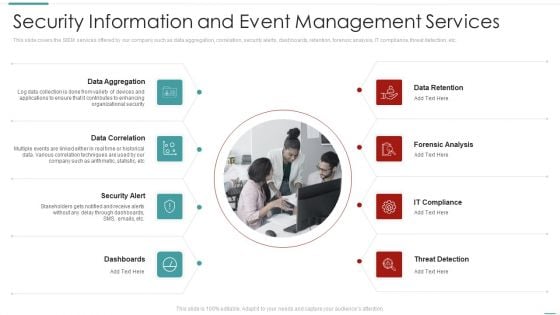
Risk Recognition Automation Security Information And Event Management Services Ppt Slides Demonstration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting risk recognition automation security information and event management services ppt slides demonstration pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
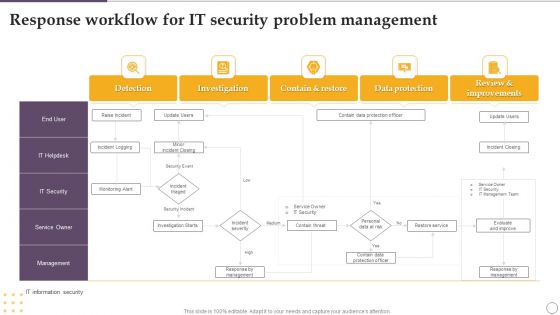
Response Workflow For IT Security Problem Management Ppt Outline Slide Download PDF
Showcasing this set of slides titled Response Workflow For IT Security Problem Management Ppt Outline Slide Download PDF. The topics addressed in these templates are Investigation, Contain And Restore, Data Protection, Detection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
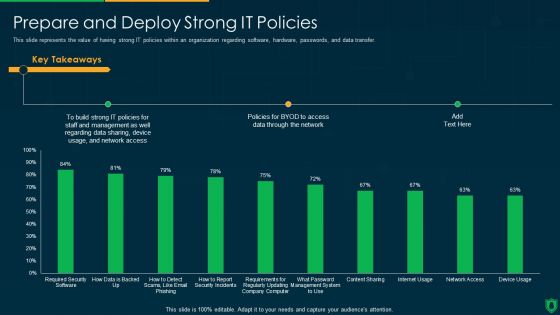
Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
VPN Privacy And Security Vector Icon Ppt PowerPoint Presentation Model Slides PDF
Presenting vpn privacy and security vector icon ppt powerpoint presentation model slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn privacy and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
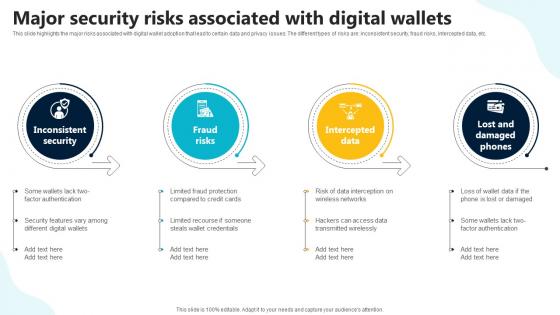
Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc. Boost your pitch with our creative Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc.

Golden Key Email Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Golden Key Email Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Download and present our Business PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience.Use these PowerPoint slides for presentations relating to Email sign protected with key, security, business, signs, success, internet. The prominent colors used in the PowerPoint template are Blue, White, Orange. Use our Golden Key Email Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 look good visually. Professionals tell us our signs PowerPoint templates and PPT Slides will help them to explain complicated concepts. Professionals tell us our Golden Key Email Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Customers tell us our key PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Customers tell us our Golden Key Email Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. We assure you our key PowerPoint templates and PPT Slides are second to none. Lick the cream with our Golden Key Email Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113.They will be the icing on the cake.
Common Network Security Threats Vector Icon Ppt PowerPoint Presentation Ideas Elements PDF
Presenting common network security threats vector icon ppt powerpoint presentation ideas elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including common network security threats vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Network Security Vector Icon Ppt PowerPoint Presentation File Layouts PDF
Presenting business network security vector icon ppt powerpoint presentation file layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business network security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Wireless Network Security System To Prevent Unauthorized Access To Internet Elements PDF
Presenting wireless network security system to prevent unauthorized access to internet elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system to prevent unauthorized access to internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

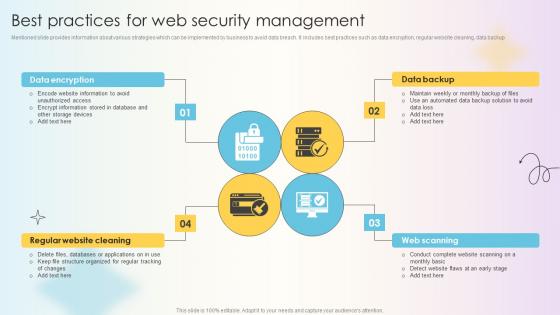
Comprehensive Guide For Website Development Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup This modern and well-arranged Comprehensive Guide For Website Development Best Practices For Web Security Management provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
Managing Technical And Non Technical Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup Present like a pro with Managing Technical And Non Technical Best Practices For Web Security Management. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup

Dollar Bills Locked With Key Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Dollar Bills Locked With Key Security PowerPoint Templates PPT Backgrounds For Slides 0213.Present our security PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Download our Success PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download our Shapes PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience. Use our Finance PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter.Use these PowerPoint slides for presentations relating to Dollar under lock and key, security, business, success, shapes, finance. The prominent colors used in the PowerPoint template are Orange, Gray, White. Examine data with our Dollar Bills Locked With Key Security PowerPoint Templates Ppt Backgrounds For Slides 0213. You will come out on top.

Piggy Bank With Lock And Dollar Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Piggy Bank With Lock And Dollar Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Use our Money PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire.Use these PowerPoint slides for presentations relating to Piggy bank key and coin, security, success, business, money, finance. The prominent colors used in the PowerPoint template are Green, Black, Yellow. Crunch the data with our Piggy Bank With Lock And Dollar Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Derive accurate conclusions with your ideas.
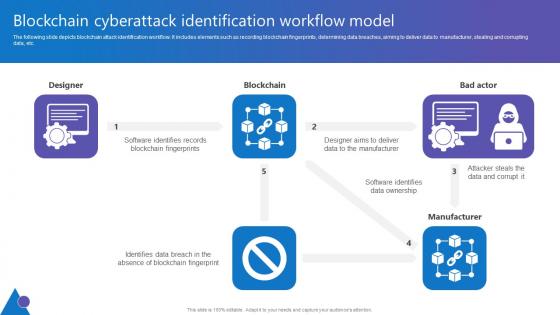
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.
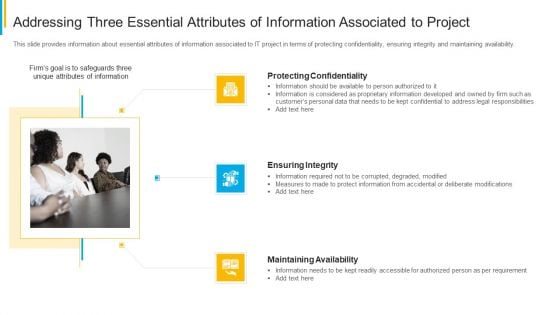
Project Security Administration IT Addressing Three Essential Attributes Of Information Associated To Project Topics PDF
This slide provides information about essential attributes of information associated to IT project in terms of protecting confidentiality, ensuring integrity and maintaining availability. This is a project security administration it addressing three essential attributes of information associated to project topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting confidentiality, ensuring integrity, maintaining availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
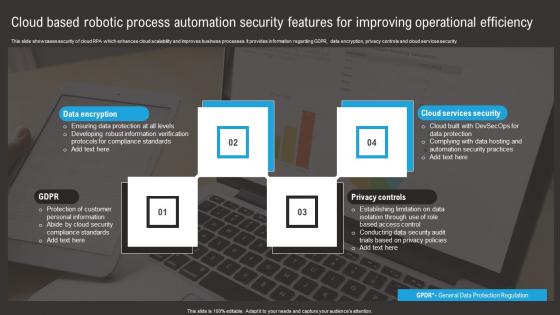
Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf
This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security. Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf. This layout presents information on Data Encryption, Privacy Controls, Cloud Services Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security.
Malware For IT Security Vector Icon Ppt PowerPoint Presentation File Mockup PDF
Presenting malware for it security vector icon ppt powerpoint presentation file mockup pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware for it security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Client Profile And Information Security Vector Icon Ppt PowerPoint Presentation File Good PDF
Persuade your audience using this client profile and information security vector icon ppt powerpoint presentation file good pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including client profile and information security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Keyboard Symbol With Key Security PowerPoint Templates And PowerPoint Themes 0912
Keyboard Symbol With Key Security PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with computer keyboard with two security keys -Computer keyboard with two security keys, technology computer, internet, security, success Win trust with our Keyboard Symbol With Key Security PowerPoint Templates And PowerPoint Themes 0912. You will come out on top.
Icon Of Wireless Network Security System With Lock And Globe Grid Demonstration PDF
Presenting icon of wireless network security system with lock and globe grid demonstration pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including icon of wireless network security system with lock and globe grid. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
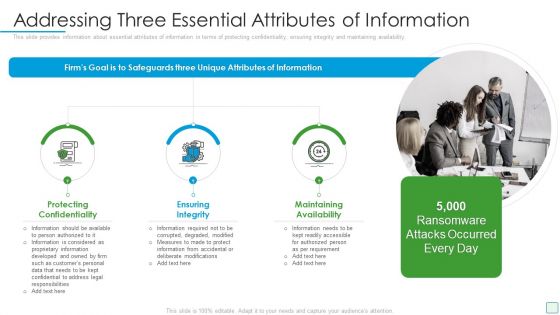
Developing Firm Security Strategy Plan Addressing Three Essential Attributes Of Information Summary PDF
This slide provides information about essential attributes of information in terms of protecting confidentiality, ensuring integrity and maintaining availability. This is a developing firm security strategy plan addressing three essential attributes of information summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting confidentiality, ensuring integrity, maintaining availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Emerging Threats In Cyber Security Ppt PowerPoint Presentation Model Images PDF
Presenting emerging threats in cyber security ppt powerpoint presentation model images pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including emerging threats in cyber security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Security Shield Vector Icon Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud security shield vector icon ppt powerpoint presentation icon background images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud security shield vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Internet Security Vector Icon Ppt PowerPoint Presentation File Graphics PDF
Presenting smart phone internet security vector icon ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone internet security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Database Inventory Security Vector Icon Ppt PowerPoint Presentation File Graphic Images PDF
Presenting business database inventory security vector icon ppt powerpoint presentation file graphic images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business database inventory security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Biometric Device For Security Access System Icon Ppt PowerPoint Presentation Ideas Picture PDF
Presenting biometric device for security access system icon ppt powerpoint presentation ideas picture pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including biometric device for security access system icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Parked Vehicles With Barrier Security Access Ppt PowerPoint Presentation Gallery Portfolio PDF
Presenting parked vehicles with barrier security access ppt powerpoint presentation gallery portfolio pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including parked vehicles with barrier security access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































